AJAX Security Issues Kim Giglia CSC 682 Asynchronous


















- Slides: 25

AJAX Security Issues Kim Giglia CSC 682

Asynchronous Java. Script And XML (AJAX) Not a new technology – a synergy of existing technologies • Java. Script • DOM (Document Object Model) • XML, JSON and XSLT • DHTML, XHTML, and CSS • XHR (XMLHttp. Request) Object

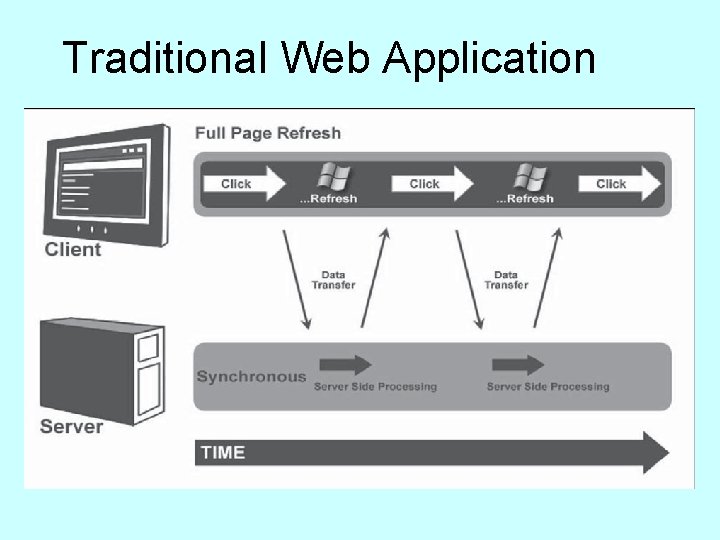
Traditional Web Application

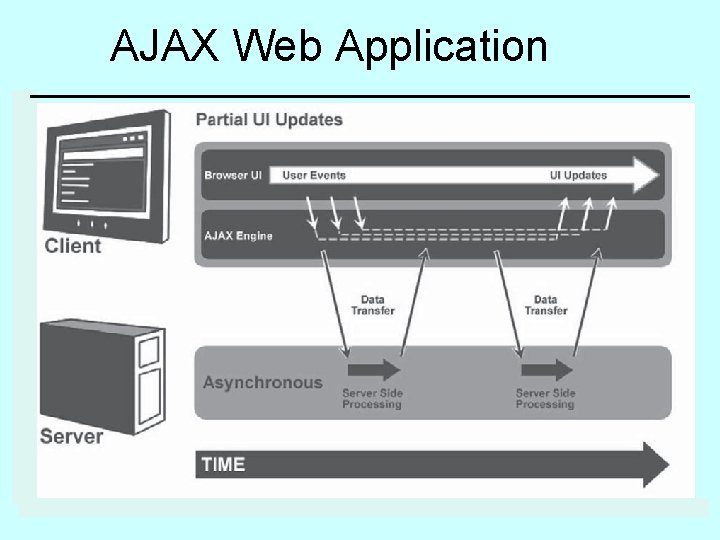
AJAX Web Application

Security Issues – General • Ajax applications are more complex • Hard to find knowledgeable developers • More LOC and varied parts • Ajax applications are transparent • Messages between the client/server intercepted and understood (HTTP) • Application is accessible to anyone • Some application logic stored on client

Specific Security Issues • XSS and CSRF • XML poisoning • Malicious Ajax Code Injection • RSS/Atom Injection • WSDL scanning and enumeration • Client Side validation routines • Web Services Routing Issues

Specific Security Issues • Parameter manipulation with SOAP • XPATH injection • RIA client binary manipulation • XSS Prototype Hijacking • HTTP Request Splitting • Mashup site security problems • Aggregate or Ajax portal site problems • Race Conditions

Why do issues arise? • Tight deadlines • Limited opportunity for training • Predeveloped frameworks

Specific Attacks Illustrated Malicious Ajax Code Injection – Theoretical Attack • Hacker in a place with wireless connection • Travel Agency site – High. Tech. Vacations. net • Agency has coupon array and crypto functions on clientside – oops! • Agency doesn’t validate all client-side input for queries and uses client-side data transformation– oops! • Agency stores both user and admin functions in a common. js file including – Ajax. Calls. admin. add. User – oops!

Specific Attacks Illustrated XSS and CSRF – Theoretical Attack • Hacker in a place with wireless find bank. com with an XSS vulnerability • Hacker crafts a URL pointing to real bank. com site, but contains a Java. Script payload in the query string • Hacker e-mails link to bank. com customers and asks them to come check out new website • User follows link and logs in – Hacker now has id and password • Java. Script load now uses XHR object to request account balance

Specific Attacks Illustrated XSS and CSRF – Theoretical Attack • After account balance extracted XHR object is used to request transfer of funds • Bank requires confirmation of transfer – XHR object extracts out randomized token (nonce) and returns a confirmation – funds transfer • Remember user never sees any activity as DOM is not updated • This type of CSRF not possible before Ajax, because attacker could not extract response from XHR object – only blind attacks were possible

Specific Attacks Illustrated XSS and CSRF – Real Attack Samy worm on myspace. com • Inserted Java. Script into his profile • Worm re-directs browser to view from www. myspace. com instead of profile. myspace. com • Uses XHR obj to retrieve and modify friendslist and user profile • Site asks for confirmation of profile update – XHR object used to extract token and confirm

Specific Attacks Illustrated XSS Prototype Hijacking • Wrapper function for XHR object var xmlhttp = XMLHttp. Request; XMLHttp. Request = function( ) { this. xml = new xmlhttp(); return this; } • Now attacker has access to control the xml attribute • Attacker sets up sniff() function which will be used to send the victim’s data to attacker’s site • Finally attacker wraps XHR send() function to include the sniff() function and maybe even tamper with parameters sent to real site

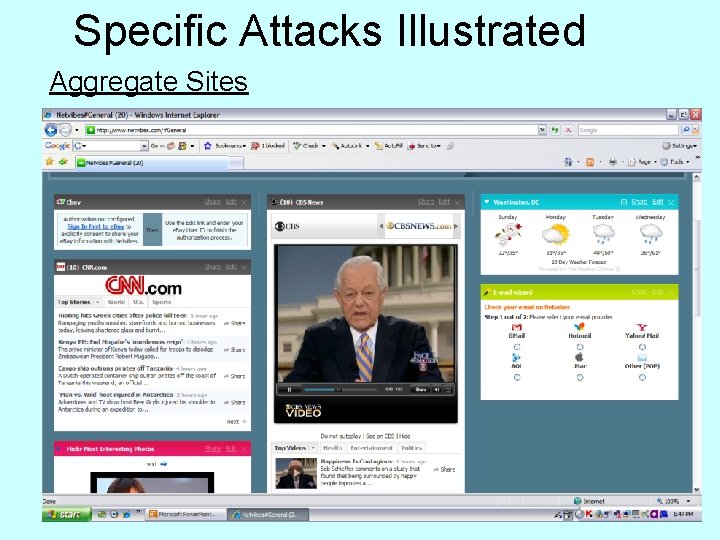
Specific Attacks Illustrated Aggregate Sites

Specific Attacks Illustrated Aggregate Sites • Data aggregated from multiple untrustworthy sites • Everything running in same security domain • IFrame jails can be used, but those can still be compromised by adding a new iframe inside one jail to point to another iframe outside of the jail. • Net. Vibes. com specifically allows widgets to make POSTs to /save/user. Data. php – so unless you extend iframe jails to server – no protection • Session hijacking if iframe jails can access session ID

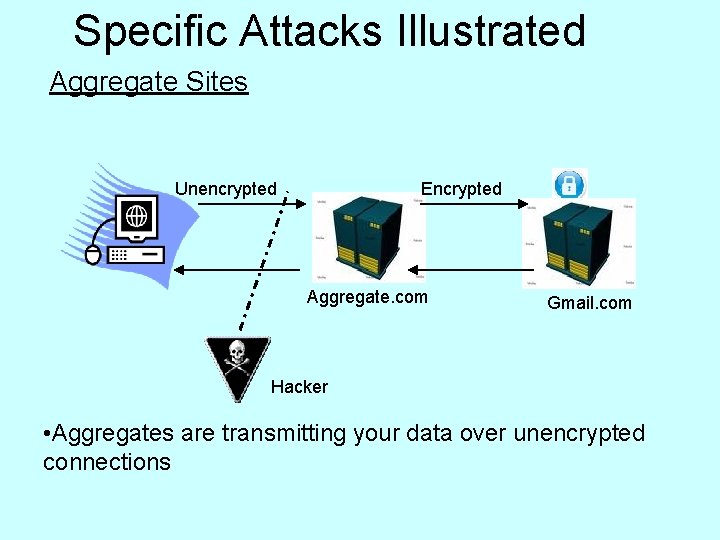
Specific Attacks Illustrated Aggregate Sites Unencrypted Encrypted Aggregate. com Gmail. com Hacker • Aggregates are transmitting your data over unencrypted connections

Not an attack – still a problem Race conditions • Alice banks has direct deposit and banks online • Alice transfers $2 k from savings to checking online • Simultaneously her direct deposit of $10 k is occurring • Before transfer and direct deposit her checking acct bal was $2 k • After both execute her checking acct bal is $4 k – what? !@%&? • A race condition has occurred and only the $2 k transfer updated – the web app developers failed to account for race conditions with other processes

Solutions to Security Issues General recommendations • Developer training and secure coding practices • Specifically validate all data input • Get a corporate management buy-in to foster a secure development environment

Solutions to Security Issues Specific solutions • Code migration framework to Ajax • Develop in Java – • Access to strong IDE • Developers more familiar than Java. Script • Use static/dynamic analysis to catch vulnerabilities • Use XMLVM and XSL style sheet mappings to automatically convert to Java. Script • Prototype program was developed to test feasibility • This approach cannot support multi-threaded apps

Solutions to Security Issues Specific solutions • Automatic Partitioning • Code in Jif 3. 0 • Developer focused on one language • Jif code compiled into Web. IL • Separates code into 2 programs – client and server according to security constraints • Compile both programs into Java • Use GWT to transform client-side into Java. Script • Six small prototype apps tested – no real world apps tested • Labels require getting used to

Solutions to Security Issues Specific solutions • Construction frameworks to protect against injection • Extension of same origin policy • Identify every UI widget as a principal • Sandbox the principal w. r. to Java. Script • Modify browser to collect list of principals as it walks DOM tree • Modify development framework to attach principal annotations when HTML generated • Problems handling UI’s dependent upon other UI’s • No testing submitted by authors

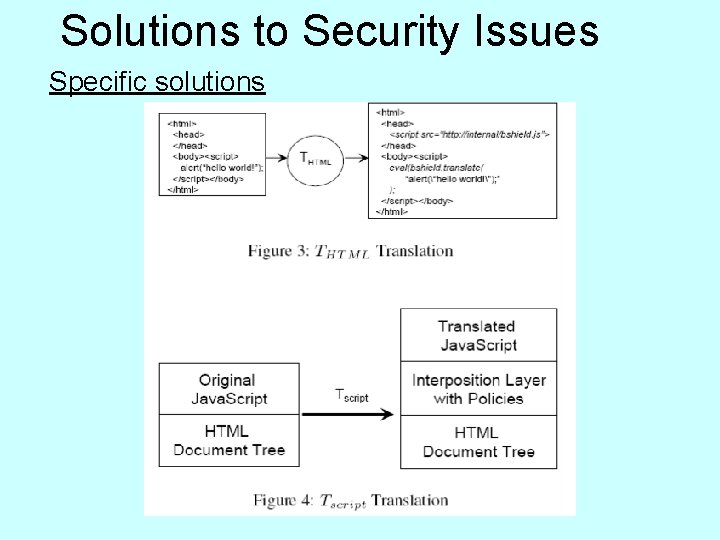
Solutions to Security Issues Specific solutions • Browser. Shield • Re-write web pages to filter for malicious content • THTML • Tokenizes HTML-modifies per sec policies • Tags script elements w/ bshield. translate() • TSCRIPT • Re-writes all Java. Script at runtime per policies and feeds through Interposition Layer • Interposition Layer controls all DOM manipulations

Solutions to Security Issues Specific solutions

Solutions to Security Issues Specific solutions • Browser. Shield • Authors built a prototype and tested against all critical vulnerabilities for which IE released patches in 2005 • 12 vulnerabilities related to HTML, script, and Active. X – 100% caught by Browser. Shield

Conclusions • Developing secure Ajax applications is a work in progress • Continued developer education and awareness is needed • Some changes in corporate culture may have to happen • If Ajax applications are developed willy-nilly and people are attacked – they may decide to stop using the web – this could stifle certain industries • Above all – developers should scrub data inputs