Secure Routing in WSNs and VANETs Security Improved






















- Slides: 44

Secure Routing in WSNs and VANETs: Security Improved Geographic Routing and Implicit Geographic Routing Presented by Da Teng, Yufei Xu, Xin Wu

Outline n n n n Introduction Background Related attacks SIGF routing in WSNs Resilient geographic routing in WSNs Secure GF routing in VANETs Conclusion Reference 2

Introduction n In the recent year, the technology of multi-path ad hoc networks has become an attractive topic. A number of potential application fields have emerged, such as: n n Wireless sensor networks (WSNs) Vehicular ad hoc networks (VANETs) 3

Introduction (cont) n In this area, some protocols are proposed, for example: n n n Geographic forwarding (GF) Implicit geographic forwarding (IGF) According to such protocols, some attacks exist, which are listed as: n Sybil attacks, Black hole attacks, selective forwarding attacks, CTS replay attack 4

Background n Geographic Forwarding and localization Geographic Forwarding Ø Ø Ø Location based data relaying mechanism Need to construct a neighbourhood based on received beacons Next-hop is selected based on predefined rules i. e. shortest dist. to dest. Localization Mechanism Ø Ø Ø A set of anchors with knowing position are pre-deployed Each node estimates its distance to an anchor node through certain mechanisms i. e. the signal strength, TDA A node’s coordinates can be determined through three such estimation 5

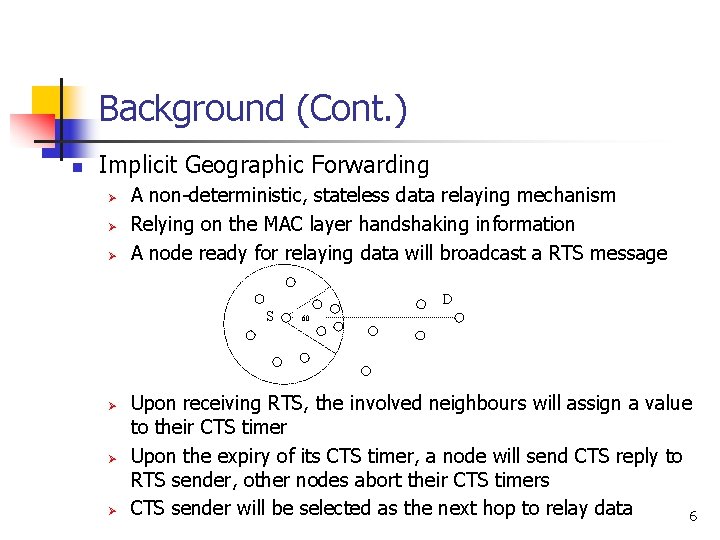
Background (Cont. ) n Implicit Geographic Forwarding Ø Ø Ø A non-deterministic, stateless data relaying mechanism Relying on the MAC layer handshaking information A node ready for relaying data will broadcast a RTS message D S Ø Ø Ø 60 Upon receiving RTS, the involved neighbours will assign a value to their CTS timer Upon the expiry of its CTS timer, a node will send CTS reply to RTS sender, other nodes abort their CTS timers CTS sender will be selected as the next hop to relay data 6

Background (Cont. ) n Wireless Sensor Network Ø Ø Ø A set of low cost radio device so called sensors Each sensor is supplied with limited amount of resources i. e. memory, computational capability, and energy supply The sensed data is forwarded to a base station through multi-hop path. 7

Background (Cont. ) n Vehicular Ad Hoc Network (VANETs) Ø Ø Enables the inter-communication between mobile vehicles Characterized by high dynamic network topology due to car mobility 8

Related Attacks n GF Related Attacks Ø Ø Ø Location falsification: A node claims a faked position to pretend to be optimal than other candidates. Black hole/Slective forwarding: A node has the ability to lure all data around an area through itself, then simply discards all data or only forwards portion of received data. Sybil attack: A node creates a number of virtual clones of itself, each claims a faked position to gain a high probability to be selected as the data forwarder. 9

Related Attacks (Cont. ) n IGF Related Attack Ø Ø Ø Black hole/Selective forwarding by CTS rushing: A malicious node, once receiving RTS broadcast, replies an CTS response immediately. Other legitimate nodes will abort their CTS timer accordingly. Hence, that node can lure all the data through itself and may either drop completely or partially forward them. Sybil attack: almost same as previously described. Deny of service attack by RTS or CTS replay RTS replay: a malicious record an old RTS message and repeatedly broadcast it to cause the channel available for legitimate data traffic. CTS replay: similar to RTS replay but an old CTS is sent repeatedly which causes subsequent RTS sender to relay data to a unacknowledged node. It finally may cause RTS sender to drop data. 10

SIGF routing in WSNs Authors’ consideration n Facts in WSNs: n n n 1) security is critical for wireless network applications, and 2) the limitation of resources of sensor nodes is severe. Goal: to find resource bound security solutions. Their approach: to have minimal active security protection. Results in: high performance and minimal resource consumption when no attacks are going. But when upon detecting an attack or if the system designers want to heighten the security level, the appropriate security mechanism is activated. SIGF (Secure IGF) is presented by authors after studied the impacts of different attacks on wireless sensor networks, such as black hole, Sybil attack. 11

SIGF routing in WSNs (cont. ) Brief description about SIGF n n n n SIGF is based on IGF, a nondeterministic Network/MAC hybrid routing protocol which is entirely stateless. Although IGF has an inherent ability to handle network dynamics effortlessly, it is vulnerable in the local neighborhood even to a simple CTS rushing attack. SIGF extends IGF and almost eliminates the gap between full statelessness and traditional shared-state security. It consists of three protocols, from SIGF-0 to SIGF-2. Similar to IGF, SIGF-0 does not keep any states but utilizes nondeterminism and candidates sampling to get high packet delivery ratios. SIGF-1 keeps local state by building reputations for its neighbor nodes to help select the next hop. However, SIGF-2 maintains state shared with neighbors to support a cryptographic mechanism for authentication and integrity, therefore provides a strong defense against attacks, but at a great cost. Each protocol is derived from the previous, adding more mechanisms to defend against more sophisticated attacks. 12

SIGF routing in WSNs (cont. ) How does each protocol works n SIGF-0, stateless secure IGF, is the basis of other protocols. Without keeping forwarding history or information about neighbors, it chooses the next hop node dynamically and randomly when it really forwards a packet. n Steps: n n it broadcast an ORTS packet, which may contain the information about source, destination and desired forwarding area, and then waits for responses in a fixed period of time, which is called collection window. Among these candidates, it will select one according to a certain criterion as the next relay. There are 4 parameters impacting the performance. n n Forwarding Area = the area in which the candidate may be chosen. Collection Window = how long a node should wait for responses. Forwarding Candidate Choice = the criterion upon which the next hop is selected. Its value can be set to “first”, “priority”, “random” and “multiple”. Omit Location = whether the receivers of ORTS can know the destination. This is useful when an attacker wants to fabricate a virtual node near the path from source to destination. 13

SIGF routing in WSNs (cont. ) n SIGF-1, local-state secure IGF, lets each node maintain some information collected by itself, concerning the behavior and reputation about its neighbors. n By analyze such information, a node can know which neighbor works better and has a good performance. This is helpful when choose the next hop. n Some data should be stored in a node, for example, N_sent = number of message sent to neighbor N forward. n Finally, a variable R, standing for reputation, is calculated according to some kinds of statistic data. n When this value of a node is less than a certain threshold, R_threshold, it won’t be considered as the next hop. n By doing so, even Sybil attack can be defended. 14

SIGF routing in WSNs (cont. ) n SIGF-2, shared-states secure IGF, can deal with some attacks by using state that is shared among neighbors for cryptographic operations. n This provides guarantees for authenticity, confidentiality and freshness. n Besides the inherited configuration options from SIGF-0 and SIGF-1, SIGF-2 has some additional options. n Message Authentication = what kind of packets should be authenticated. n Message Sequencing = whether a sequence number should be used in each n Payload Encryption = whether the contents in packets should be encrypted. packet. 15

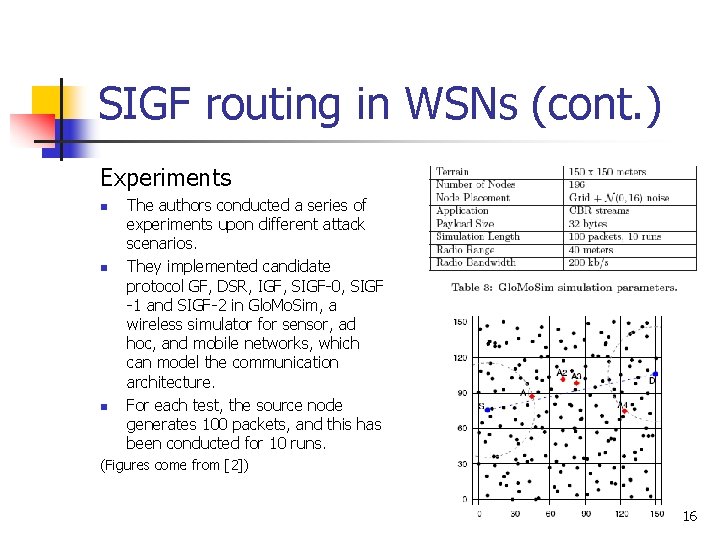
SIGF routing in WSNs (cont. ) Experiments n n n The authors conducted a series of experiments upon different attack scenarios. They implemented candidate protocol GF, DSR, IGF, SIGF-0, SIGF -1 and SIGF-2 in Glo. Mo. Sim, a wireless simulator for sensor, ad hoc, and mobile networks, which can model the communication architecture. For each test, the source node generates 100 packets, and this has been conducted for 10 runs. (Figures come from [2]) 16

SIGF routing in WSNs (cont. ) Experimental results black hole attack n n the data flow from source to destination is set to 6 packets per second. SIGF-0 is implemented in 2 versions: n n n random: to choose the next hop randomly among several candidates; priority: to select one that responses first to ORTS packet. SIGF-1 also has 2 versions: n n n random: has the same meaning as SIGF-0 -random; reputation: chooses the remaining node with the highest routing priority. In both protocols, if no nodes have reputations above threshold, the node with the highest reputation is chosen. 17

SIGF routing in WSNs (cont. ) black hole attack (cont. ) n n the packet delivery ratio (PDR) of IGF becomes 0. It can not deliver a single packet since the attacker is always the first responder. When the attacker is near the optimal path from source to destination, SIGF-0 priority performs very poorly, with 0 PDR, because it always chooses the attacker as the next hop. When the attacker is not near the optimal route, only SIGF-0 -random and SIGF 1 -random suffer from attacks since they may choose attackers due to probabilism. In summary, SIGF protocols continue to deliver packets successfully. SIGF-0 provides some defense with low PDRs (0 -43%), SIGF-1 provides moderate PDRs (70 -99%), and SIGF-2 reaches the best result (100%). 18

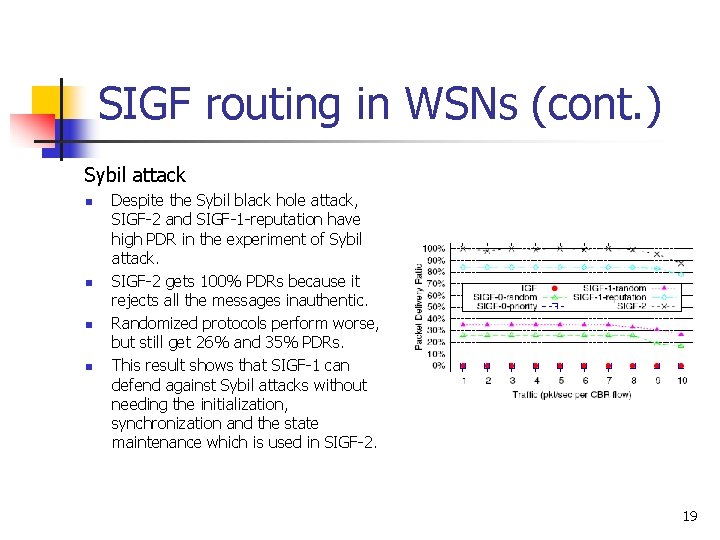
SIGF routing in WSNs (cont. ) Sybil attack n n Despite the Sybil black hole attack, SIGF-2 and SIGF-1 -reputation have high PDR in the experiment of Sybil attack. SIGF-2 gets 100% PDRs because it rejects all the messages inauthentic. Randomized protocols perform worse, but still get 26% and 35% PDRs. This result shows that SIGF-1 can defend against Sybil attacks without needing the initialization, synchronization and the state maintenance which is used in SIGF-2. 19

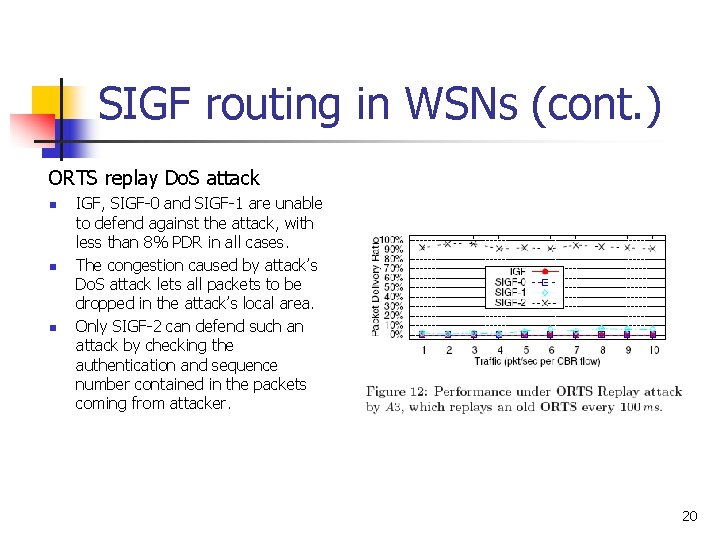
SIGF routing in WSNs (cont. ) ORTS replay Do. S attack n n n IGF, SIGF-0 and SIGF-1 are unable to defend against the attack, with less than 8% PDR in all cases. The congestion caused by attack’s Do. S attack lets all packets to be dropped in the attack’s local area. Only SIGF-2 can defend such an attack by checking the authentication and sequence number contained in the packets coming from attacker. 20

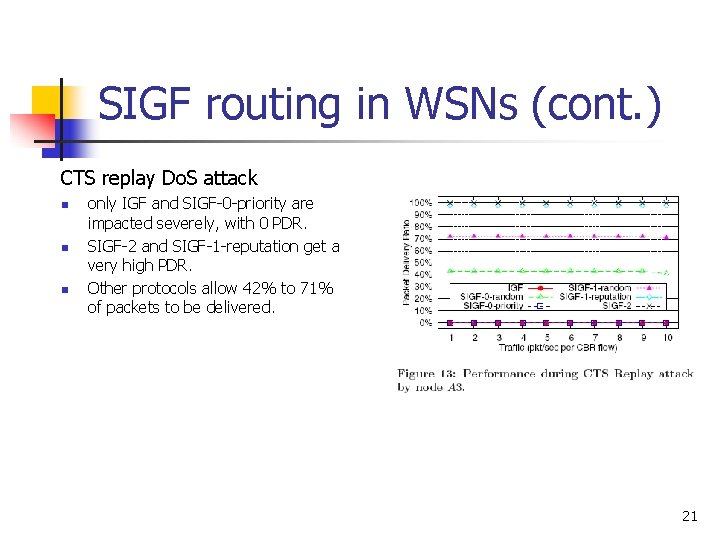
SIGF routing in WSNs (cont. ) CTS replay Do. S attack n n n only IGF and SIGF-0 -priority are impacted severely, with 0 PDR. SIGF-2 and SIGF-1 -reputation get a very high PDR. Other protocols allow 42% to 71% of packets to be delivered. 21

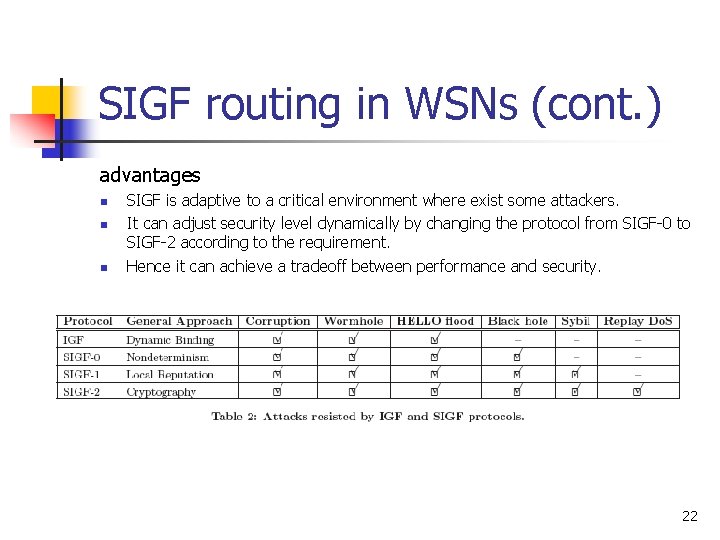
SIGF routing in WSNs (cont. ) advantages n n n SIGF is adaptive to a critical environment where exist some attackers. It can adjust security level dynamically by changing the protocol from SIGF-0 to SIGF-2 according to the requirement. Hence it can achieve a tradeoff between performance and security. 22

SIGF routing in WSNs (cont. ) disadvantages n n n When the density of nodes in the terrain is low, the probability of choosing attackers as the next hop will increase obviously. Hence the packets delivery rations of the nodes near the attacker will drop down below an acceptable level. When the attacker is a compromised node, and it has two or more downstream accomplices, even SIGF-2 can not detect such an attack since the chief instigator behaviors as a normal node, forwarding to other nodes (accomplice) and hence keeping a good reputation. Because the IGF, from which derives the SIGF, has a failure-recovery mechanism by shifting the forwarding angle and re-sending, the authors in this paper did not discuss how this mechanism will impact SIGF family. our improvements n n For 1, a feasible solution is taking a stricter selection standard. In other words, a node does not select any candidates when their reputations are all below the threshold. Instead, it can change its forwarding area and try again. For 2, maybe a possible way is to check whether a node always sends packets to a recognized bad node. And then this information is broadcasted to other nodes to help them evaluate neighbors. 23

Resilient geographic routing in WSNs Security Enhancement n Assumptions: n n n Two kinds of nodes: anchor nodes, sensor nodes Sensor nodes have one hop neighbors All nodes have unique IDs Algorithm can use efficient encryption and decryption system No physical or MAC layer attacks 24

Resilient geographic routing in WSNs (cont. ) Security Enhancement (cont) n n Location Verification Algorithm n a sensor first generates a localization request n anchors estimate the distance or angle from the sensor n the anchors exchange the information to compute the location of the sensor via triangulation Trust management n three parameters, trust levels, specified step sizes and predefined penalties, compute the credit of a sensor node n If the node successfully forwards a packet, its credit will be increased, or decreased. 25

Resilient geographic routing in WSNs (cont. ) Security Enhancement (cont) n Resilient geographic routing protocol n n n at the beginning, the source node and its one hope neighbors communicate to build connection the source adds the information of those nodes to a routing table if it the connection is successful the source node selects k verified neighbors in terms of the probability Pi of sending a packet calculated by the trust management and the threshold parameter to forward the packet and overhears them updates their trust levels according to the results of the forwarding the procedure is applied recursively 26

Resilient geographic routing in WSNs (cont. ) Evaluation and Improvement n localization broadcast manipulation: the sensor node maybe broadcast its location information with different power or at different time in order to influence the wireless sensor network system n n n can be detected by consensus since the anchors can exchange their information about its location then find the inconsistency. hard for an individual anchor to detect this kind of attack If any two circles with radii di+f and dj+f intersect, allowing for localization tolerances, the inconsistency will be detected. 27

Resilient geographic routing in WSNs (cont. ) Evaluation and Improvement(cont) n multiple unicast packet attack: a kind of attack preventing consensus between the anchor nodes by forwarding different packets to them n n sequential attack: forward different packets to different anchors sequentially, one at a time. The anchor nodes can detect that the packets are different via the clock skew with a tolerance of the beacon packet length at the same time. Concurrent attack: forward different packets concurrently from multiple sending radios to the different anchors. It is hard to be detected via the clock skew, but it can be detected by the MAC layer authentication. 28

Resilient geographic routing in WSNs (cont. ) Evaluation and Improvement (cont) n mobile attack: a node moves to a new location after it gain valid location verification. n It can be prevented, but it can be reduced by periodically requesting fresh certificates. n Furthermore, trusted node can be used to sample the non-trust nodes and compute their distance. Reconciling the computed distance with node’s claimed location information can detect the mobility attacks dynamically. 29

Resilient geographic routing in WSNs (cont. ) Evaluation and Improvement(cont) n n based on the assumption that the anchor nodes are trusted n can hardly prevent compromised or malicious nodes to disrupt the geographic routing consumption in the multipath routing protocol n the energy consumption may be k times compared to the consumption when it chooses only one neighbor to forward the packet n all the candidate nodes in the routing table. If the transmission fails, we choose another node 30

Secure GF in VANETs n GF is very suitable to serve as a routing protocol in VANETs Ø Ø Ø The dynamically changing topology does not allow a route to be pre-determined. A next hop has to be found at instant of data replaying. Nowadays GPS positioning system is commonly employed in a car, which facilitates localization. Some envisioned application VANETs requires location-awareness. § Location Verification in VANETs Ø Ø Location verification should not based on infrastructure. Location verification should not introduce any dedicated hardware 31

Secure GF in VANETs (Cont. ) Autonomous position verification system n Ø Ø Ø Software-based position verification system for detecting false position claim of a neighbour node Consists of a set of sensors (software algorithm) which operate in an independent manner Such sensors can be classified as: v v v Ø Threshold-based sensors i. e. ART, MGT, MDT Map-based sensor Overhearing sensor Upon arrival of position beacon, those sensors are activated and produce their own evaluation independently of each other to produce their individual trust ranking for the position claim. 32

Secure GF in VANETs (Cont. ) Ø Functional Sensors v q q q Threshold-based sensors ART: based on the assumption that one can not receive message out of its range. MGT: based on the observation that a car normally can’t exceed the speed limit. MDT: based on the observation that node density of a limited area can’t exceed a threshold value due the physical dimension of a car. 33

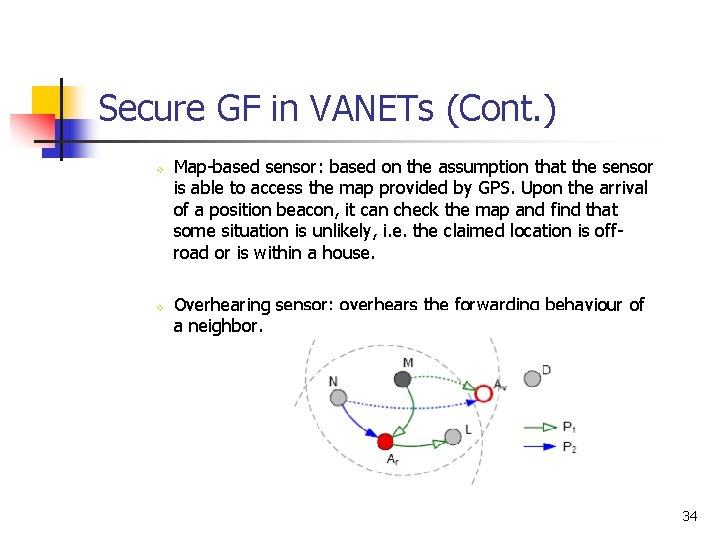
Secure GF in VANETs (Cont. ) v v Map-based sensor: based on the assumption that the sensor is able to access the map provided by GPS. Upon the arrival of a position beacon, it can check the map and find that some situation is unlikely, i. e. the claimed location is offroad or is within a house. Overhearing sensor: overhears the forwarding behaviour of a neighbor. 34

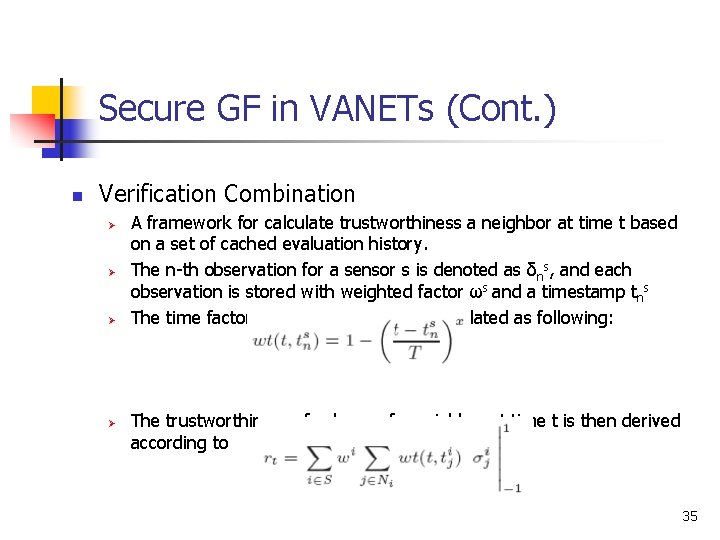
Secure GF in VANETs (Cont. ) n Verification Combination Ø Ø A framework for calculate trustworthiness a neighbor at time t based on a set of cached evaluation history. The n-th observation for a sensor s is denoted as δns, and each observation is stored with weighted factor ωs and a timestamp tns The time factor of an observation δns calculated as following: The trustworthiness of value rt of a neighbor at time t is then derived according to 35

Secure GF in VANETs (Cont. ) Ø At the time to pick a next hop forwarding data, neighbours with negative trustworthiness are excluded from the consideration. The rest remains in neighbourhood table is considered based on the defined protocol rule. § Effectiveness Validation Ø Simulation environment v v v APT and MGT sensors, and the trust system are implemented based on ns-2 simulator. GF routing uses a greedy paradigm in which a node with the smallest dest. to destination will be selected. Attack falsifies its location by select a random position within a circle centered at real node and has a radius of 500 m. Upon received data, it can either forward or drop based on parameter setup. 36

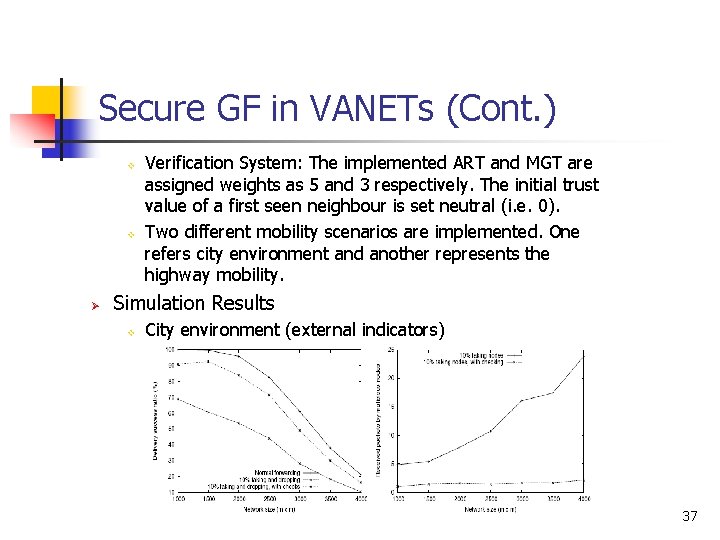
Secure GF in VANETs (Cont. ) v v Ø Verification System: The implemented ART and MGT are assigned weights as 5 and 3 respectively. The initial trust value of a first seen neighbour is set neutral (i. e. 0). Two different mobility scenarios are implemented. One refers city environment and another represents the highway mobility. Simulation Results v City environment (external indicators) 37

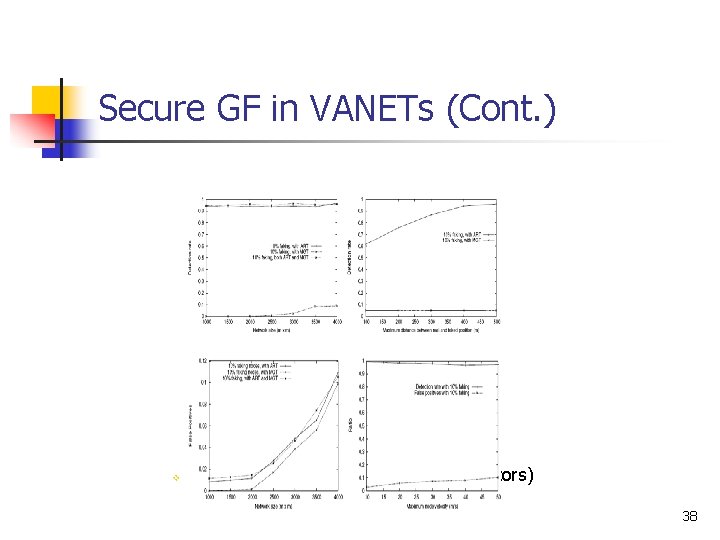
Secure GF in VANETs (Cont. ) v City environment Cont. (internal indicators) 38

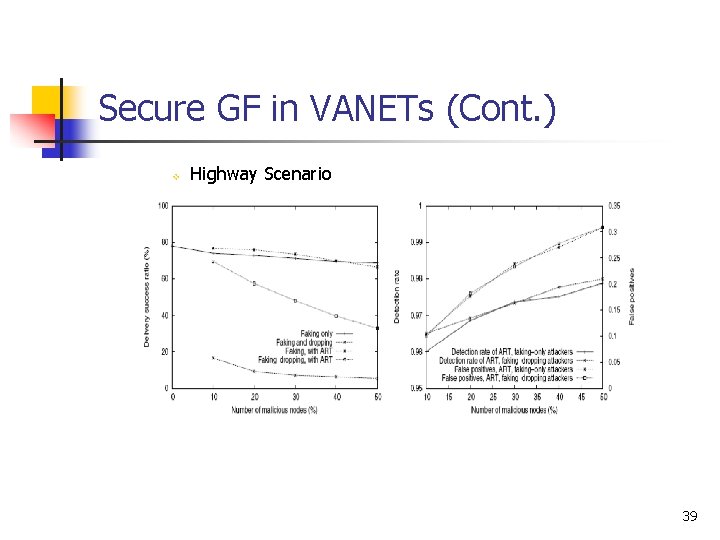
Secure GF in VANETs (Cont. ) v Highway Scenario 39

Secure GF in VANETs (Cont. ) n Evaluation and Possible Improvement Ø Ø Enable local communication between sensors may leads to selfconfigurable verification system. For example, map-based sensor, in addition to performing position verification, can inform ART and MGT to adjust their threshold values when a car switches from one moving scenario to another. Pre-exclusion of neighbours decreases the node density and affects the network connectivity. To deal with this problem, our approach is to still keep them in the forwarding set but assign a weight to trustworthiness. On the other hand, each neighbour’s distance to the final destination is also weighted. By summing over these two weighted component, the overall value will be used to determine which neighbour is to the optimal to serve as the next hop. 40

Secure GF in VANETs (Cont. ) n Evaluation and Possible Improvement (Cont. ) Ø Defending against Sybil attack through a trust third parity Authenticating position claim through third parity requires infrastructure which contradicts with requirement of VANETs. Our approach is based on the public key cryptography system where private key is used to ensure the authenticity. Each clone may have the same key as its parent or have none. The later case can be easily detected through authentication. The former may be detected by other sensors such as MGT. But, efficient key generation and distribution in NAVETs is complex and remains in future research field. 41

Conclusion n In this survey we reviewed the nature of Geographical Forwarding routing protocols used in multi-hop ad hoc networks. n the security of wireless network communication is very important since such a network may be deployed in a crucial environment. n To defend against attacks effectively, there is a requirement for GF routing to have defense mechanisms, and to be more resilient to failures. n n Through investigation we can see that in general, many approaches proposed in literature provide means of location validation, authentication, and even cryptography, enabling ad hoc networks to defend various attacks. Although these approaches have remarkable contributions in the area of ad hoc network security, they still have some weaknesses. By addressing these problems we think those methods could be improved farther. 42

Reference n n Tim Leinmuller, Christian Maihvfer, Elmar Schoch, Frank Kargl. "Improved Security in Geographic Ad hoc Routing through Autonomous Position Verification", September 2006 Proceedings of the 3 rd international workshop on Vehicular ad hoc networks VANET '06, page(s): 57 -66 Anthony D. Wood, Lei Fang, John A. Stankovic, Tian He. "SIGF: A Family of Configurable, Secure Routing Protocols for Wireless Sensor Networks", October 2006 Proceedings of the fourth ACM workshop on Security of ad hoc and sensor networks SASN '06, page(s): 35 -48 n Nael Abu-Ghazaleh, Kyoung-Don Kang, Ke Liu, "Towards Resilient Geographic Routing in WSNs", October 2005 Proceedings of the 1 st ACM international workshop on Quality of service & security in wireless and mobile networks Q 2 SWinet '05, page(s): 71 -78 43

Question n ? +? =? ? x? =? 44