Segment Routing SDWAN 1 Source routing IP routing





- Slides: 21

Segment Routing SD-WAN 1

Source routing IP routing is based on destination addresses (and perhaps DSCP) but sometimes we need control over the precise path a packet travels to its destination For example • in DCs we need to ensure packets traverse nodes (in order) • for security we may need to avoid a particular router • policy-based routing enables overriding default routing • we may need paths with special characteristics (e. g. , low delay) IP protocols provide mechanisms called Source Routing • IPv 4 source routing options (Loose SR, Strict SR) • IPv 6 type 0 routing header extension (Rh 0) SR inserts sequences of router addresses into packet headers SD-WAN 2

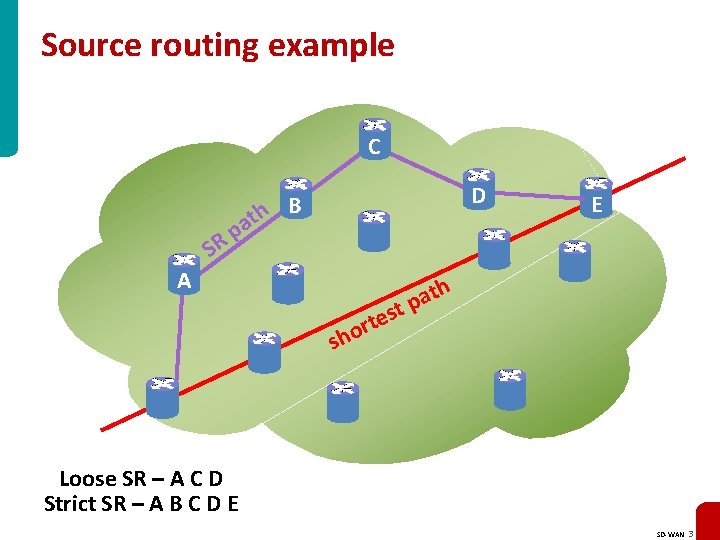
Source routing example C D h B t a p SR A E h t a p st e t r ho s Loose SR – A C D Strict SR – A B C D E SD-WAN 3

Source routing is evil Yet source routing is problematic There are several reasons why source routing is evil • complicated processing for core routers • Do. S attack – attacker forces packets to traverse selected routers, thus overloading them • amplified Do. S attack – attacker forces packet to oscillate between 2 selected routers • infiltration attack – attacker bypasses ACLs by forwarding through a permitted waypoint The IETF has not yet completely deprecated it but highly recommends that it be disabled Core Internet routers drop packets with options (Linux kernels no longer process Source Routing) SD-WAN 4

Safe policy-based routing But without SR, how can we achieve policy based routing? There are 2 alternatives Software Defined Networking SDN give the network administer full control over routing particular flows can be configured to traverse arbitrary paths CE with NMS, and MPLS-TE with PCE are essentially the same But SDN • requires relatively large architectural changes • enables attacks (and plain bugs) at control plane level Segment Routing Segment routing is similar to Source Routing, but the path is specified by an ingress router, not by the source host thus blocking Source Routing attacks (unless a router is compromised) SD-WAN 5

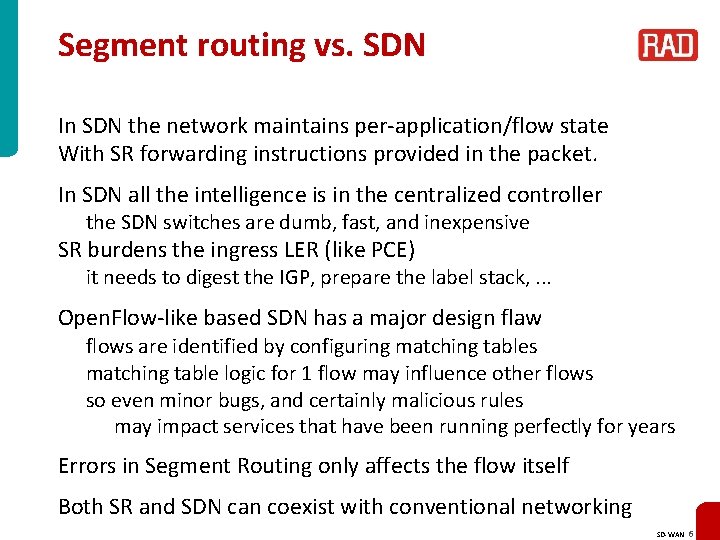
Segment routing vs. SDN In SDN the network maintains per-application/flow state With SR forwarding instructions provided in the packet. In SDN all the intelligence is in the centralized controller the SDN switches are dumb, fast, and inexpensive SR burdens the ingress LER (like PCE) it needs to digest the IGP, prepare the label stack, . . . Open. Flow-like based SDN has a major design flaw flows are identified by configuring matching tables matching table logic for 1 flow may influence other flows so even minor bugs, and certainly malicious rules may impact services that have been running perfectly for years Errors in Segment Routing only affects the flow itself Both SR and SDN can coexist with conventional networking SD-WAN 6

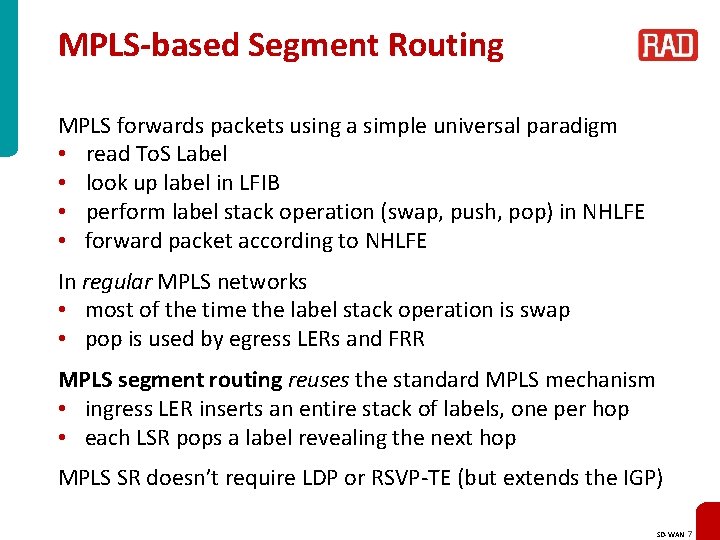
MPLS-based Segment Routing MPLS forwards packets using a simple universal paradigm • read To. S Label • look up label in LFIB • perform label stack operation (swap, push, pop) in NHLFE • forward packet according to NHLFE In regular MPLS networks • most of the time the label stack operation is swap • pop is used by egress LERs and FRR MPLS segment routing reuses the standard MPLS mechanism • ingress LER inserts an entire stack of labels, one per hop • each LSR pops a label revealing the next hop MPLS SR doesn’t require LDP or RSVP-TE (but extends the IGP) SD-WAN 7

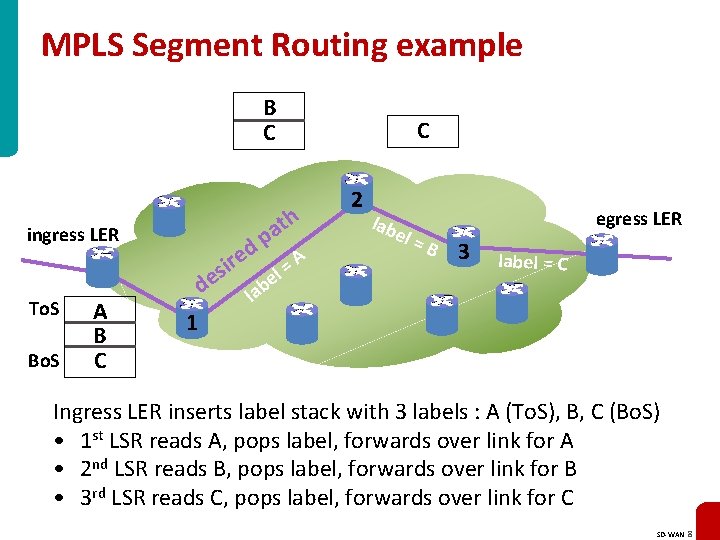
MPLS Segment Routing example B C h ingress LER To. S Bo. S A B C C d ri e s e d 1 t a p l e lab =A 2 lab el = egress LER B 3 label = C Ingress LER inserts label stack with 3 labels : A (To. S), B, C (Bo. S) • 1 st LSR reads A, pops label, forwards over link for A • 2 nd LSR reads B, pops label, forwards over link for B • 3 rd LSR reads C, pops label, forwards over link for C SD-WAN 8

Global and local segments In Segment Routing the labels are called Segment IDs (SIDs) in MPLS SR the SID is the 20 -bit label and in IPv 6 SR (SRv 6) it is a 128 -bit address There are 2 main types of SIDs : An adjacency SID (local SID) refers to a link (port) it has local significance (like normal MPLS labels) only the LSR advertising it can use it with that meaning A node SID (prefix SID, global SID) refers to a destination node if has global significance (unique, like IP addresses) the network forwards over the shortest path to the node every LSR has the same entry in its LFIB WARNING: this is a simplification SD-WAN 9

Label distribution The ingress LER learns nodes and adjacencies from the Interior Gateway Protocol (e. g. , OSPF or IS-IS) Hence, it can select each node and link to be traversed along the desired path The source LSR can insert (global) node SIDs (either direct or loose) or adjacency SIDs or combinations But how does the source LSR know the labels that indicates to an LSR to forward over a desired link? Segment Routing augments the IGP with label information (LDP is no longer needed) SD-WAN 10

Segments as instructions Constructing a segment routing label stack is similar to programming in a low-level language Each label can be considered to be an instruction (op-code) The ingress LER encodes the list of instructions (SIDs) and each LSR interprets and executes one instruction thus making the networking into a giant processor Segment instructions can be: • Forward over link L • Go to node N using the shortest path • Apply service S SD-WAN 11

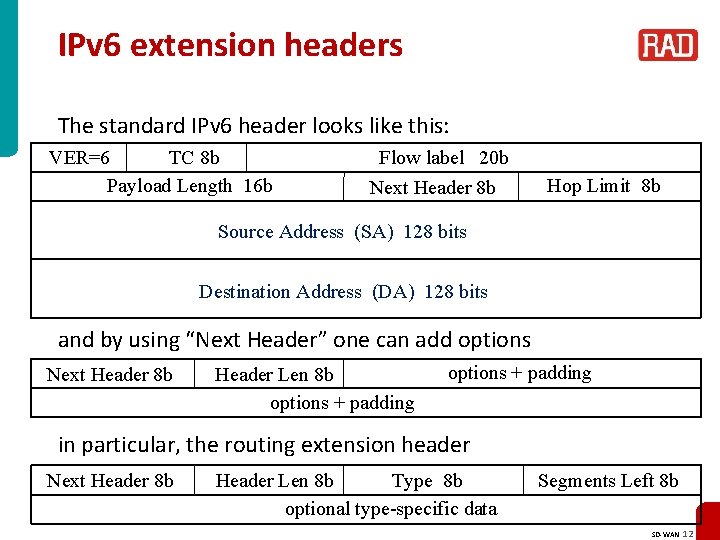
IPv 6 extension headers The standard IPv 6 header looks like this: TC 8 b VER=6 Payload Length 16 b Flow label 20 b Next Header 8 b Hop Limit 8 b Source Address (SA) 128 bits Destination Address (DA) 128 bits and by using “Next Header” one can add options Next Header 8 b Header Len 8 b options + padding in particular, the routing extension header Next Header 8 b Header Len 8 b Type 8 b optional type-specific data Segments Left 8 b SD-WAN 12

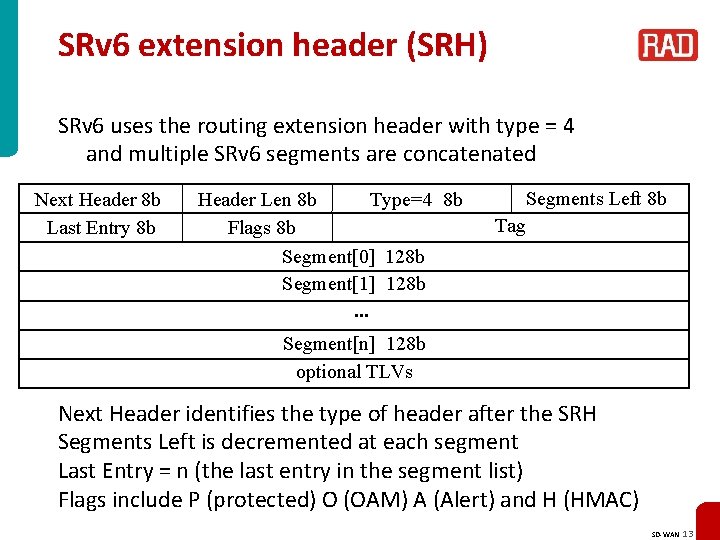
SRv 6 extension header (SRH) SRv 6 uses the routing extension header with type = 4 and multiple SRv 6 segments are concatenated Next Header 8 b Last Entry 8 b Type=4 8 b Header Len 8 b Flags 8 b Segment[0] 128 b Segment[1] 128 b. . . Segments Left 8 b Tag Segment[n] 128 b optional TLVs Next Header identifies the type of header after the SRH Segments Left is decremented at each segment Last Entry = n (the last entry in the segment list) Flags include P (protected) O (OAM) A (Alert) and H (HMAC) SD-WAN 13

Unified-IP-SR There is another encapsulation for SR in IP networks RFC 7510 defines MPLS-in-UDP for IPv 4 or IPv 6 networks This encapsulation may be better than RFC 4023 MPLS-in-IP MPLS-in-GRE-in-IP since it enables fine grain load balancing using ECMP for IPv 4 by using the UDP port for entropy (IPv 6 already has the flow label) Unified-IP-SR exploits MPLS-in-UDP to carry MPLS SR Routers must be capable of this new type of forwarding and must advertise this capability in the IGP but Unified-IP-SR can function with a mixture of unified-IP-SR capable and legacy routers SD-WAN 14

FRR and LFA One of the deficiencies of SDN is the lack of resilience methods Open. Flow provides a mechanism via group tables Segment routing enables new resilience methods that do not require signaling that do not require maintaining massive network state that avoid looping One such method is Topology Independent Loop Free Alternatives – TI-LFA In order to understand TI-LFA we need to first review • MPLS Fast Re. Route - FRR • IP Loop Free Alternatives - LFA • MPLS LFA SD-WAN 15

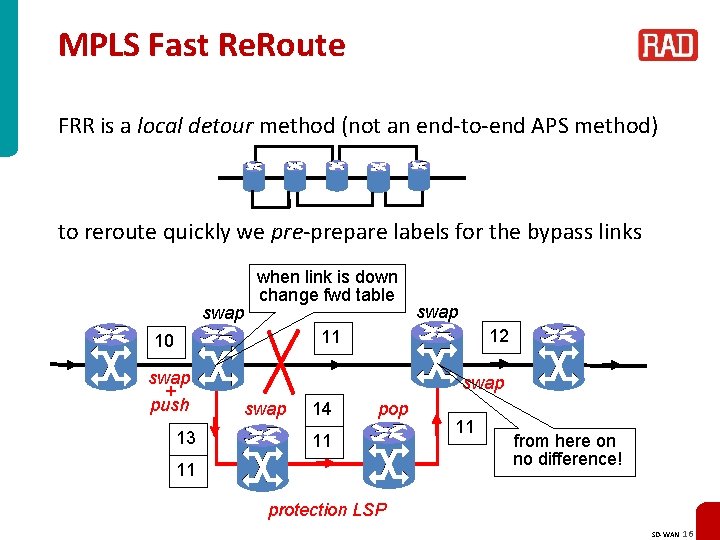
MPLS Fast Re. Route FRR is a local detour method (not an end-to-end APS method) to reroute quickly we pre-prepare labels for the bypass links swap when link is down change fwd table swap 12 11 10 swap + push 13 swap 14 pop 11 11 11 from here on no difference! protection LSP SD-WAN 16

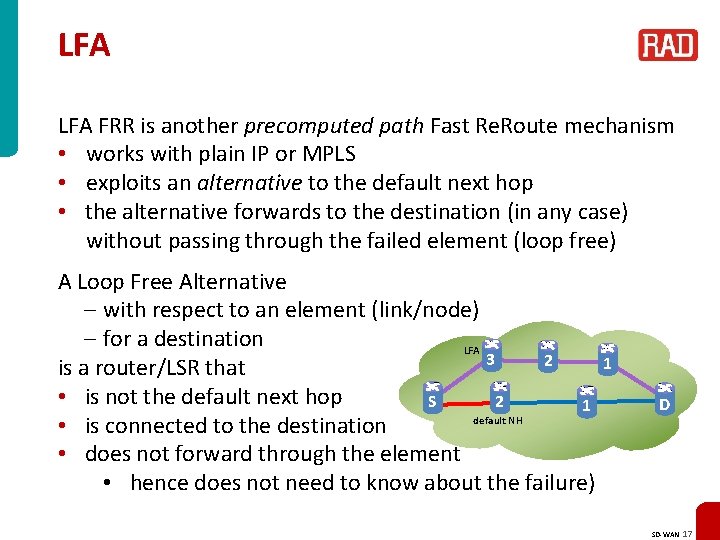
LFA FRR is another precomputed path Fast Re. Route mechanism • works with plain IP or MPLS • exploits an alternative to the default next hop • the alternative forwards to the destination (in any case) without passing through the failed element (loop free) A Loop Free Alternative – with respect to an element (link/node) – for a destination LFA 3 2 is a router/LSR that • is not the default next hop S 2 1 default NH • is connected to the destination • does not forward through the element • hence does not need to know about the failure) 1 D SD-WAN 17

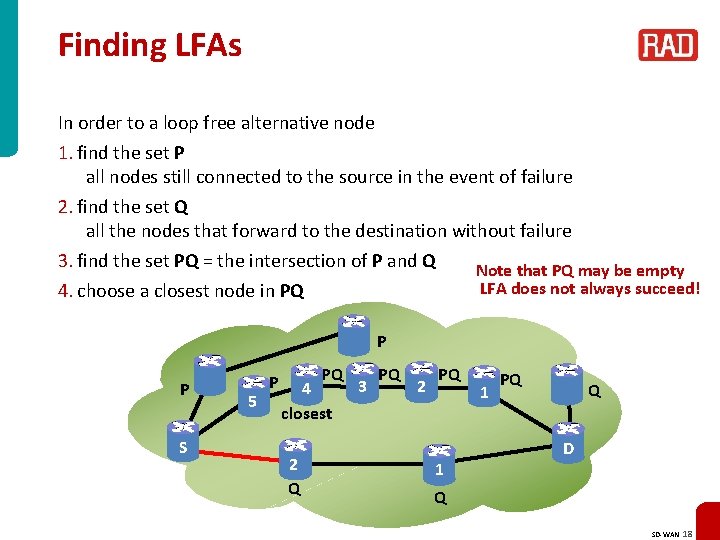
Finding LFAs In order to a loop free alternative node 1. find the set P all nodes still connected to the source in the event of failure 2. find the set Q all the nodes that forward to the destination without failure 3. find the set PQ = the intersection of P and Q Note that PQ may be empty LFA does not always succeed! 4. choose a closest node in PQ P P S 5 P PQ 4 closest 2 Q 3 PQ 2 PQ 1 1 PQ Q D Q SD-WAN 18

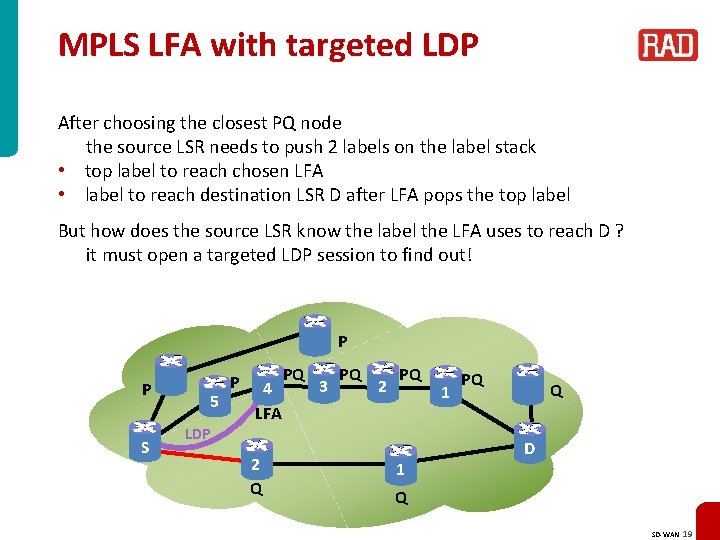
MPLS LFA with targeted LDP After choosing the closest PQ node the source LSR needs to push 2 labels on the label stack • top label to reach chosen LFA • label to reach destination LSR D after LFA pops the top label But how does the source LSR know the label the LFA uses to reach D ? it must open a targeted LDP session to find out! P P S 5 P 4 LFA PQ 3 PQ 2 PQ LDP 2 Q 1 1 PQ Q D Q SD-WAN 19

TI-LFA exploits MPLS SR to avoid having to open targeted LDP sessions The source LSR knows all the labels from the IGP and can build the MPLS SR label stack accordingly using any PQ node This capability is Topology Independent in the sense that a loop free backup path is found irrespective of the topologies before and after the failure Using deeper label stacks affords more flexibility Immediately upon discovering the failure the source LSR can use the new SR label stack so the protection switch time is minimal SD-WAN 20

Thank You For Your Attention www. rad. com SD-WAN 21