Princess Nora University Faculty of Computer Information Systems
















- Slides: 62

Princess Nora University Faculty of Computer & Information Systems Computer science Department Operating Systems (CS 340 D) Dr. Abeer Mahmoud

(Chapter-8) Memory Management Strategies

Chapter 8: Memory Management Strategies 1. Background 2. Swapping 3. Contiguous Memory Allocation 4. Paging 5. Structure of the Page Table 6. Segmentation 3 Dr. Abeer Mahmoud

OBJECTIVES: Ø To provide a detailed description of various ways of organizing memory hardware Ø To discuss various memory-management techniques, including paging and segmentation 4 Dr. Abeer Mahmoud

Overview 5 Dr. Abeer Mahmoud

Overview ü Memory is central to the operation of a modern computer system. ü Memory consists of a large array of words or bytes, each with its own address ü Selection of a memory-management method for a specific system depends on many factors, especially on the hardware design of the system. 6 Dr. Abeer Mahmoud

Basic Hardware n n n Main memory , registers and cash are ONLY storage CPU can access directly Program must be brought (from disk) into memory and placed within a process for it to be run Huge problem because of the frequency of memory accesses. Direct storage access time: �Register access in one CPU clock (or less) �Main memory can take many cycles (i. e. slowly) �Solution: Cache (fast memory) sits between main memory and CPU registers 7 Dr. Abeer Mahmoud

Basic Hardware n Protection of memory: �Protection of memory is necessary to ensure correct operation �Types of Protection 1. protect the operating system from access by user processes 2. protect user processes from one another. �This protection must be provided by the hardware & can be implemented in several ways. �One method : use 8 Base and Limit Registers Dr. Abeer Mahmoud

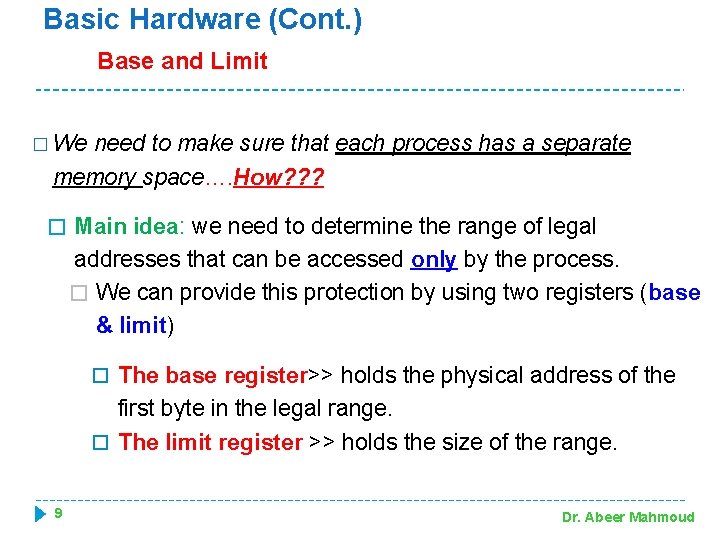
Basic Hardware (Cont. ) Base and Limit � We need to make sure that each process has a separate memory space…. How? ? ? � Main idea: we need to determine the range of legal addresses that can be accessed only by the process. � We can provide this protection by using two registers (base & limit) The base register>> holds the physical address of the first byte in the legal range. The limit register >> holds the size of the range. 9 Dr. Abeer Mahmoud

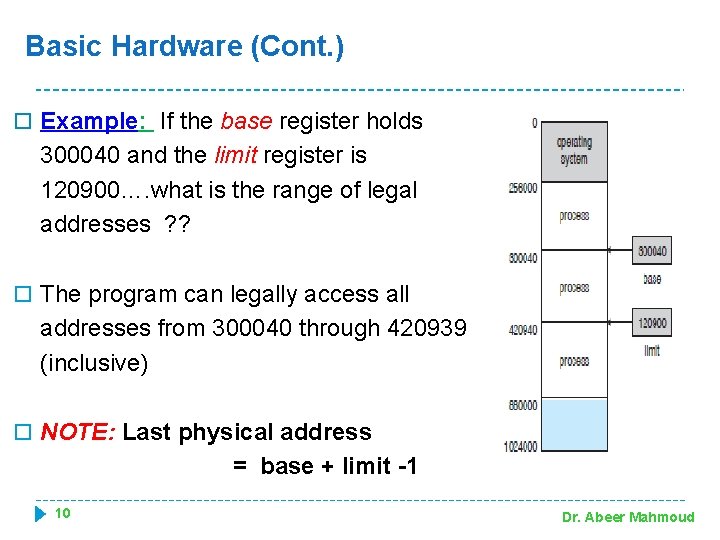
Basic Hardware (Cont. ) Example: If the base register holds 300040 and the limit register is 120900…. what is the range of legal addresses ? ? The program can legally access all addresses from 300040 through 420939 (inclusive) NOTE: Last physical address = base + limit -1 10 Dr. Abeer Mahmoud

Basic Hardware (Cont. ) � How base & limit registers help to provide memory protection? ? � By applying (2) procedures: Procedure (1): The CPU hardware compare every address generated in user mode with the registers. Procedure (2): restrict the ability to load base & limit registers only to OS. . 11 Dr. Abeer Mahmoud

Basic Hardware (Cont. ) � Procedure (1): The CPU hardware compare every address generated in user mode with the registers. � � If (CPU generated address ≥ base) & (CPU generated address < base +limit) … Then …. . the CPU generated address is legal and allowed to access the memory Else…… the CPU generated address is illegal and NOT allowed to access the memory…. . (causing a trap (/error) to OS) This scheme prevents a user program from (accidentally or deliberately) modifying the code or data structures of either the operating system or other users…. . (solution to protection problem) 12 Dr. Abeer Mahmoud

Basic Hardware (Cont. ) Hardware address protection with base and limit registers 13 Dr. Abeer Mahmoud

Basic Hardware (Cont. ) n Procedure (2): restrict the ability to load base & limit registers ONLY to OS. � This restriction applied by using a special privileged instruction. � Since privileged instructions can be executed only in kernel mode, and since only the operating system executes in kernel mode…. . So, ONLY the operating system can load the base and limit registers. � This scheme allows the operating system to change the value of the registers but prevents user programs from changing the registers’ contents. 14 Dr. Abeer Mahmoud

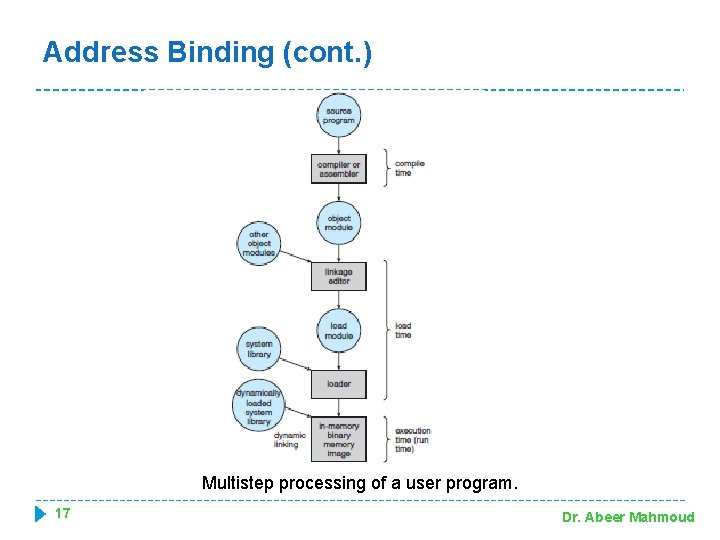
Address Binding � Address binding( or relocation): The process of associating program instructions and data to physical memory addresses �A user program will go through several steps -some of which may be optional-before being executed …. . steps are: 1. Compiling 2. Linking 3. Execution 15 Dr. Abeer Mahmoud

Address Binding � Addresses may be represented in different ways during these steps. o Addresses in the source program are generally symbolic (such as count, sum). o A compiler will typically bind these symbolic addresses to re-locatable addresses (such as "14 bytes from the beginning of this module"). o The linkage editor or loader will in turn bind the relocatable addresses to absolute addresses (physical address) (such as 74014). � Each binding is a mapping from one address space to 16 Dr. Abeer Mahmoud another.

Address Binding (cont. ) Multistep processing of a user program. 17 Dr. Abeer Mahmoud

Logical vs. Physical Address Space � Logical/virtual address: address generated by CPU � Physical address: address seen by memory hardware Ø Compile-time / load-time binding logical address = physical address Ø Run-time binding logical address ≠ physical address 18 Dr. Abeer Mahmoud

Logical vs. Physical Address Space � Logical address space: is the set of all logical addresses generated by a program � Physical address space: is the set of all physical addresses corresponding to these logical addresses. � MMU (Memory-Management Unit ): h/w device that maps virtual addresses to physical addresses at run time � Different methods of address mapping (/memory management strategies): v. Continuous memory allocation v. Paging vsegmentation 19 Dr. Abeer Mahmoud

Simple Address Mapping Method � For NOW, we illustrate address mapping with a simple MMU scheme: � The base register is now called a relocation register. � Basic methodology Physical address= logical address + relocation register 20 Dr. Abeer Mahmoud

Example of Simple Address Mapping Method q Base register contains 14000 If logical address =0 then Physical address= 0+14000=14000 o If logical address =346 Physical address= 346+14000=14346 o � The user program never sees the real physical addresses. The user program deals with logical addresses. � MMU converts logical addresses into physical addresses. 21 Dr. Abeer Mahmoud

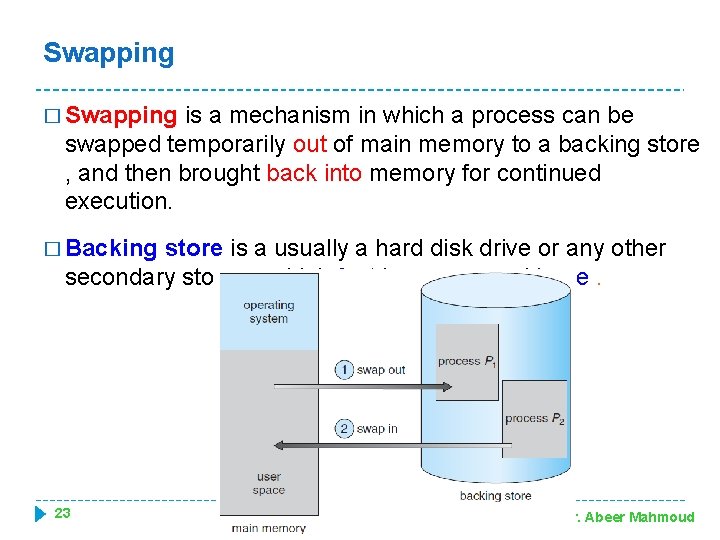
Swapping 22 Dr. Abeer Mahmoud

Swapping � Swapping is a mechanism in which a process can be swapped temporarily out of main memory to a backing store , and then brought back into memory for continued execution. � Backing store is a usually a hard disk drive or any other secondary storage which fast in access and large. 23 Dr. Abeer Mahmoud

Swapping (Cont. ) � How swapping performed? ? ? � The system maintains a ready queue consisting of all processes whose memory images are on the backing store or in memory and are ready to run. � Whenever the CPU scheduler decides to execute a process, it calls the dispatcher. � The dispatcher checks to see whether the next process in the queue is in memory. � If it is not, and if there is no free memory region, the dispatcher swaps out a process currently in memory and swaps in the desired process. 24 Dr. Abeer Mahmoud

Basic Memory Management Methods 25 Dr. Abeer Mahmoud

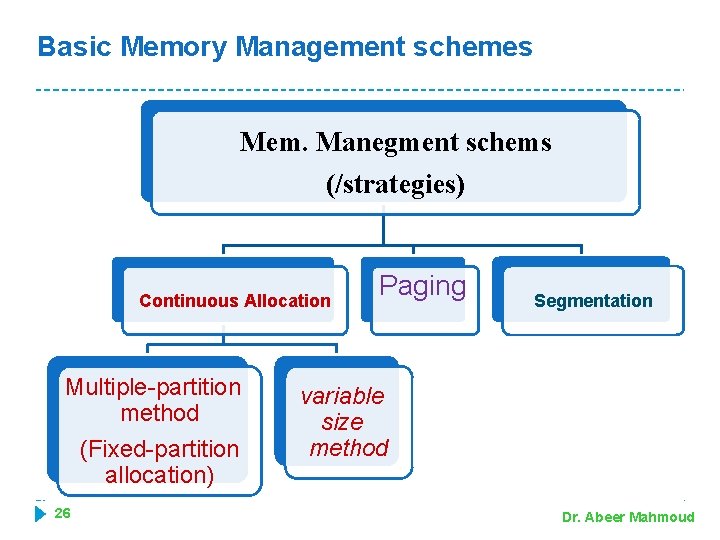
Basic Memory Management schemes Mem. Manegment schems (/strategies) Continuous Allocation Multiple-partition method (Fixed-partition allocation) 26 Paging Segmentation variable size method Dr. Abeer Mahmoud

Continuous Allocation 27 Dr. Abeer Mahmoud

Contiguous Memory Allocation (CMA) n The memory is usually divided into two partitions: l l One for the resident OS One for the user processes. n We can place the OS in either low memory or high memory. n Basic methodology: l Each process is contained in a single contiguous section of memory. n CMA strategy can be applied in (2) methods: l l 28 Multiple-partition method/(Fixed-partition allocation) method variable-partition allocation method Dr. Abeer Mahmoud

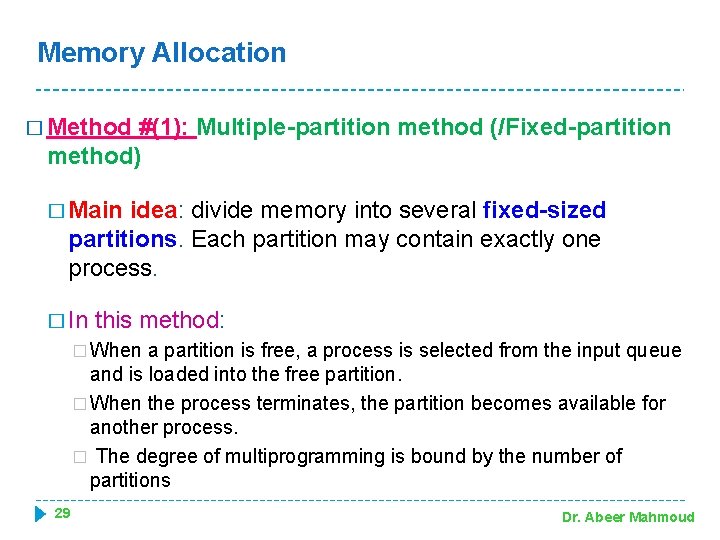
Memory Allocation � Method #(1): Multiple-partition method (/Fixed-partition method) � Main idea: divide memory into several fixed-sized partitions. Each partition may contain exactly one process. � In this method: � When a partition is free, a process is selected from the input queue and is loaded into the free partition. � When the process terminates, the partition becomes available for another process. � The degree of multiprogramming is bound by the number of partitions 29 Dr. Abeer Mahmoud

Memory Allocation (cont. ) � Method o o o 30 #(2): variable-partition method: Memory is divided into variable-sized partitions OS maintains a list of allocated / free partitions (holes) When a process arrives, it is allocated memory from a hole large enough to accommodate it Memory is allocated to processes until requirements of next process in queue cannot be met OS may skip down the queue to allocate memory to a smaller process that fits in available memory When process exits, memory is returned to the set of holes and merged with adjacent holes, if any Dr. Abeer Mahmoud

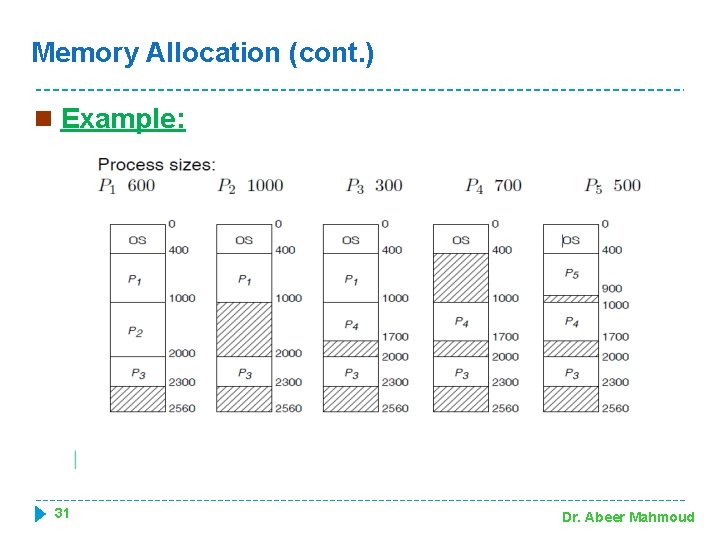
Memory Allocation (cont. ) n Example: 31 Dr. Abeer Mahmoud

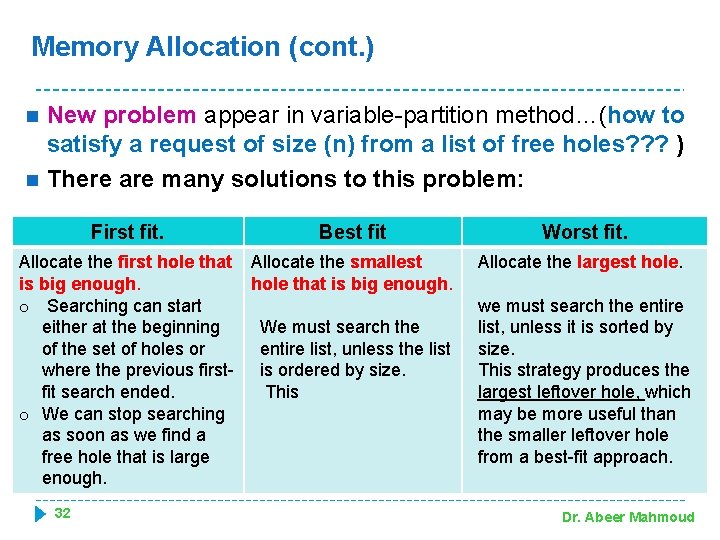
Memory Allocation (cont. ) n n New problem appear in variable-partition method…(how to satisfy a request of size (n) from a list of free holes? ? ? ) There are many solutions to this problem: First fit. Best fit Allocate the first hole that Allocate the smallest is big enough. hole that is big enough. o Searching can start either at the beginning We must search the of the set of holes or entire list, unless the list where the previous first- is ordered by size. fit search ended. This o We can stop searching as soon as we find a free hole that is large enough. 32 Worst fit. Allocate the largest hole. we must search the entire list, unless it is sorted by size. This strategy produces the largest leftover hole, which may be more useful than the smaller leftover hole from a best-fit approach. Dr. Abeer Mahmoud

Memory Allocation (cont. ) � Exercise (8. 16): Given five memory partitions of 100 KB, 500 KB, 200 KB, 300 KB, and 600 KB (in order), how would each of the first-fit, best-fit, and worst-fit algorithms place processes of 212 KB, 417 KB, 112 KB, and 426 KB (in order)? Which algorithm makes the most efficient use of memory? >>> Let p 1, p 2, p 3 & p 4 are the names of the processes First-fit: Best-fit: P 1>>> 100, 500, 200, 300, 600 P 2>>> 100, 500, 200, 88, 600 P 2>>> 100, 288, 200, 300, 600 P 3>>> 100, 83, 200, 88, 600 final set P 3>>> 100, 288, 200, 300, 183 of holes P 4>>> 100, 83, 88, 600 100, 116, 200, 300, 183 100, 83, 88, 174 P 4 (426 K) must wait Worst-fit: P 1>>> 100, 500, 200, 300, 600 P 2>>> 100, 500, 200, 388 P 3>>> 100, 83, 200, 388 100, 83, 200, 300, 276 << final set of hole P 4 (426 K) must wait In this example, Best-fit turns out to be the best because there is no wait processes. 33 Dr. Abeer Mahmoud

Fragmentation � Fragmentation is a problem appears in memory allocation censers about unusable memory space. � Fragmentation types: External fragmentation : memory space to satisfy a request is available, but is not contiguous (i. e. storage is fragmented into a large number of small holes) Internal Fragmentation : allocated memory may be larger than requested memory…. (i. e. some memory within partition may be left unused) o Both the first-fit and best-fit strategies for memory allocation suffer from external fragmentation. 34 Dr. Abeer Mahmoud

Fragmentation (Cont. ) n External fragmentation solution: l Compaction: Memory contents shuffled to place all free memory together in one large block (expensive) l Permit the logical address space of the processes to be non-contiguous, thus allowing a process to be allocated physical memory wherever it is available. �Two techniques achieve this solution: Paging Segmentation 35 Dr. Abeer Mahmoud

Fragmentation in Continuous memory allocation scheme fixed-partition method suffer from internal fragmentation 36 variable-partition method suffer from external fragmentation Dr. Abeer Mahmoud

Paging 37 Dr. Abeer Mahmoud

Paging � Paging is a memory-management scheme that permits the physical address space of a process to be non-contiguous. � Because of its advantages, paging in its various forms is commonly used in most OSs. � Recent designs have implemented paging by closely integrating the hardware and OS, especially on 64 -bit microprocessors. � Paging method also used to manage backing store (e. g. hard disk). 38 Dr. Abeer Mahmoud

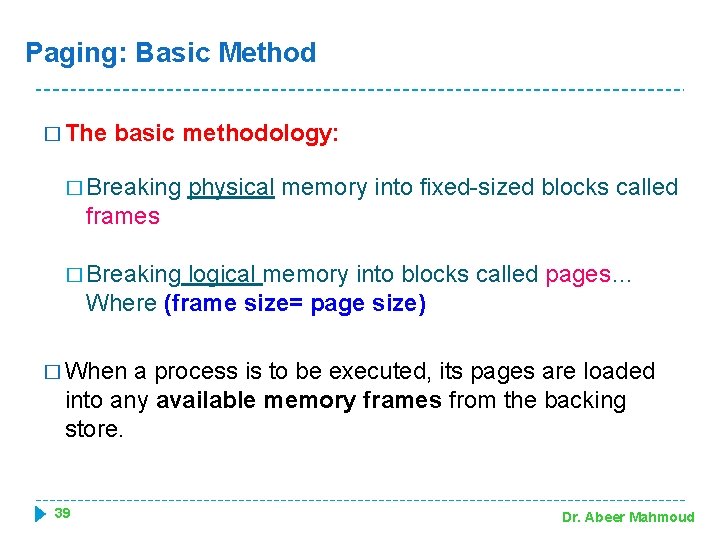
Paging: Basic Method � The basic methodology: � Breaking physical memory into fixed-sized blocks called frames � Breaking logical memory into blocks called pages… Where (frame size= page size) � When a process is to be executed, its pages are loaded into any available memory frames from the backing store. 39 Dr. Abeer Mahmoud

Paging: Basic Method � The backing store is divided into fixed-sized blocks that are of the same size as the memory frames. � OS keeps track of free frames. � Page table translates logical page to physical frame addresses � Frame size: � Defined by hardware � Should be power of 2 � Usually between 512 byte- 16 MB 40 Dr. Abeer Mahmoud

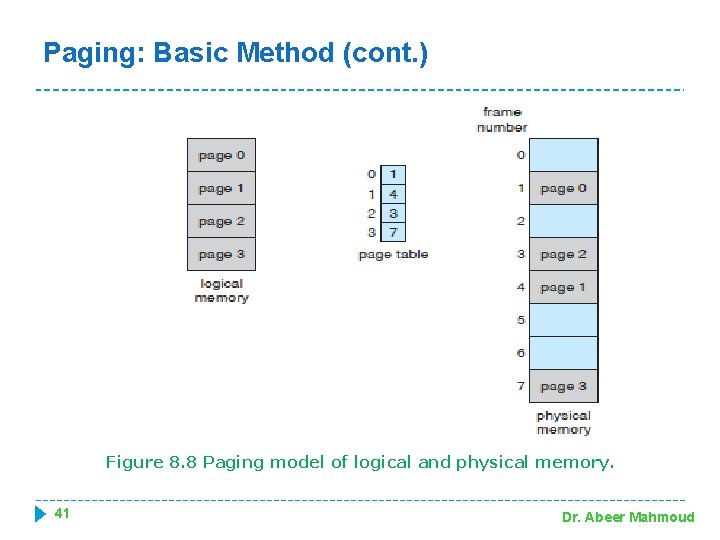
Paging: Basic Method (cont. ) Figure 8. 8 Paging model of logical and physical memory. 41 Dr. Abeer Mahmoud

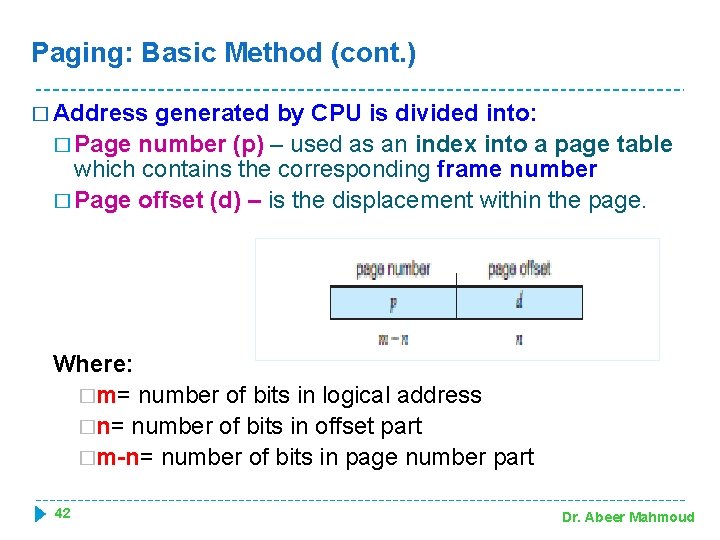
Paging: Basic Method (cont. ) � Address generated by CPU is divided into: � Page number (p) – used as an index into a page table which contains the corresponding frame number � Page offset (d) – is the displacement within the page. Where: �m= number of bits in logical address �n= number of bits in offset part �m-n= number of bits in page number part 42 Dr. Abeer Mahmoud

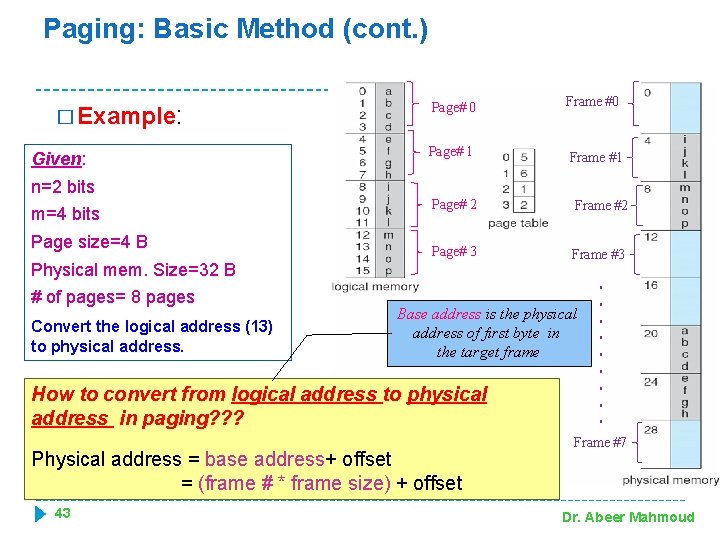
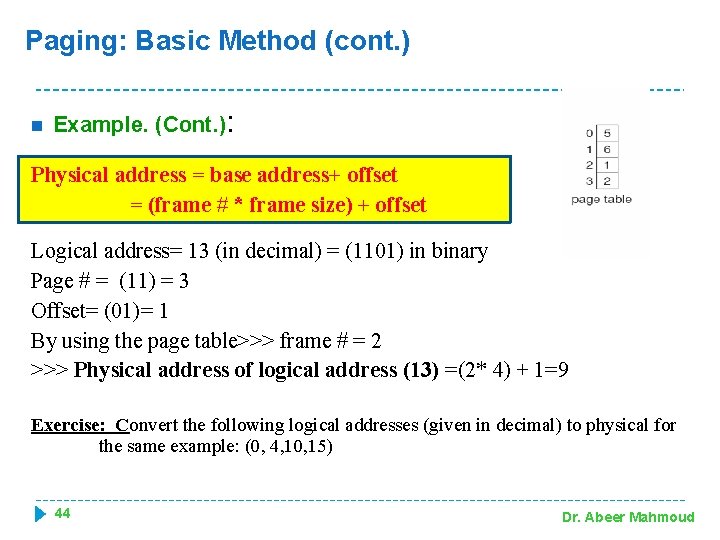
Paging: Basic Method (cont. ) � Example: Given: n=2 bits m=4 bits Page size=4 B Page# 0 Frame #0 Page# 1 Frame #1 Page# 2 Frame #2 Page# 3 Frame #3 Physical mem. Size=32 B # of pages= 8 pages Convert the logical address (13) to physical address. Base address is the physical address of first byte in the target frame How to convert from logical address to physical address in paging? ? ? Physical address = base address+ offset = (frame # * frame size) + offset 43 . . Frame #7 Dr. Abeer Mahmoud

Paging: Basic Method (cont. ) n Example. (Cont. ): Physical address = base address+ offset = (frame # * frame size) + offset Logical address= 13 (in decimal) = (1101) in binary Page # = (11) = 3 Offset= (01)= 1 By using the page table>>> frame # = 2 >>> Physical address of logical address (13) =(2* 4) + 1=9 Exercise: Convert the following logical addresses (given in decimal) to physical for the same example: (0, 4, 10, 15) 44 Dr. Abeer Mahmoud

Paging Arithmetic Laws n Page size = frame size n Logical address space (/size) = 2 m n Physical address space (/size) = 2 x (where x is the number of bits in physical address) n Logical address space (/size) = # of pages × page size n Physical address space (/size) = # of frames × frame size n Page size= frame size= 2 n n # of pages= 2 m-n n # of entries (records)in page table = # of pages n Required number of pages for a process = process size/ page size (Rounded up) 45 Dr. Abeer Mahmoud

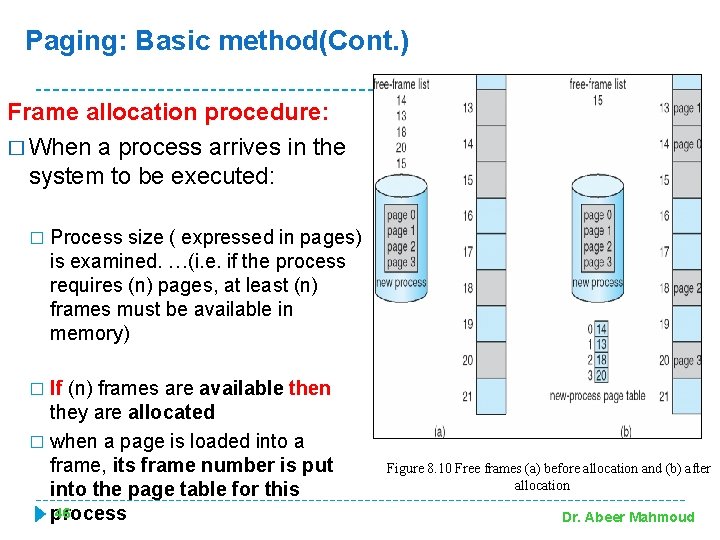
Paging: Basic method(Cont. ) Frame allocation procedure: � When a process arrives in the system to be executed: � Process size ( expressed in pages) is examined. …(i. e. if the process requires (n) pages, at least (n) frames must be available in memory) If (n) frames are available then they are allocated � when a page is loaded into a frame, its frame number is put into the page table for this 46 process � Figure 8. 10 Free frames (a) before allocation and (b) after allocation Dr. Abeer Mahmoud

Paging: Basic Method (cont. ) � Paging scheme has NO external fragmentation but it has an internal fragmentation � Example: If process (p 1) size= 1030 B , page size= 512 B How many pages P 1 will occupied? ? � Required # of pages= 1030/512≈ 2. 01 3 pages � Notice that the last page is almost empty…. (506 bytes are allocated and unused)……. (Internal fragmentation)…. what is the solution? ? � Make page size small to reduce the internal fragmentation Unsuitable solution because: (Page table size will 47 increased…(more memory consumption & moreover head ) Dr. Abeer Mahmoud

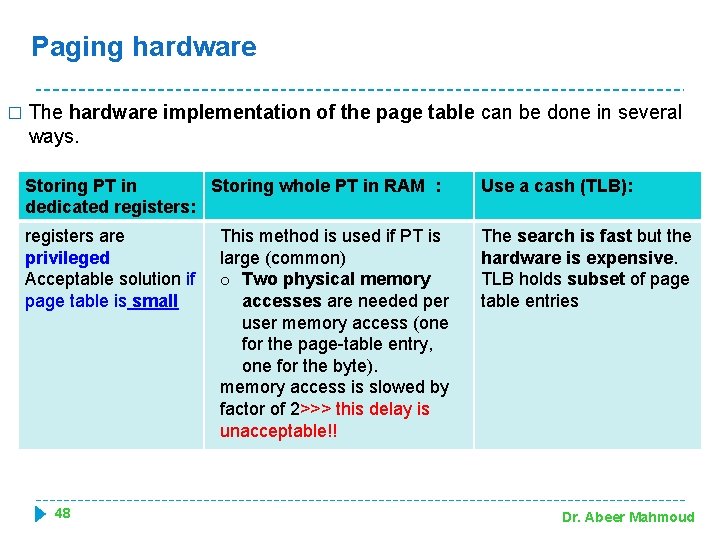
Paging hardware � The hardware implementation of the page table can be done in several ways. Storing PT in Storing whole PT in RAM : dedicated registers: Use a cash (TLB): registers are privileged Acceptable solution if page table is small The search is fast but the hardware is expensive. TLB holds subset of page table entries 48 This method is used if PT is large (common) o Two physical memory accesses are needed per user memory access (one for the page-table entry, one for the byte). memory access is slowed by factor of 2>>> this delay is unacceptable!! Dr. Abeer Mahmoud

Paging hardware (cont. ) � Hit ratio: percentage of times that a page # is found in TLB � Effective memory access time : average time for a memory access (including TLB lookup) Figure 8. 11 : Paging hardware with TLB. 49 Dr. Abeer Mahmoud

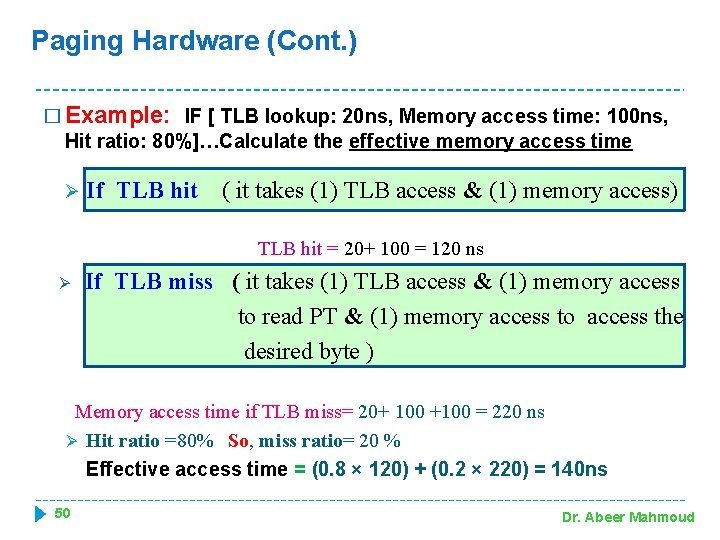
Paging Hardware (Cont. ) � Example: IF [ TLB lookup: 20 ns, Memory access time: 100 ns, Hit ratio: 80%]…Calculate the effective memory access time Ø If TLB hit ( it takes (1) TLB access & (1) memory access) TLB hit = 20+ 100 = 120 ns Ø If TLB miss ( it takes (1) TLB access & (1) memory access to read PT & (1) memory access to access the desired byte ) Memory access time if TLB miss= 20+ 100 +100 = 220 ns Ø Hit ratio =80% So, miss ratio= 20 % Effective access time = (0. 8 × 120) + (0. 2 × 220) = 140 ns 50 Dr. Abeer Mahmoud

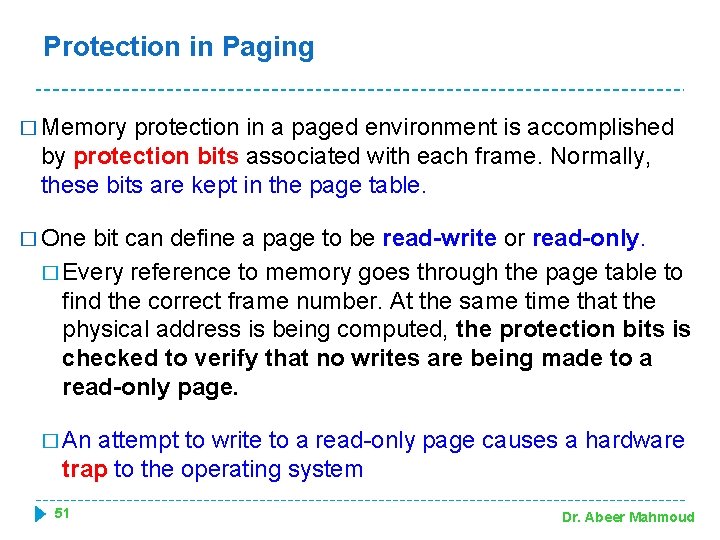
Protection in Paging � Memory protection in a paged environment is accomplished by protection bits associated with each frame. Normally, these bits are kept in the page table. � One bit can define a page to be read-write or read-only. � Every reference to memory goes through the page table to find the correct frame number. At the same time that the physical address is being computed, the protection bits is checked to verify that no writes are being made to a read-only page. � An attempt to write to a read-only page causes a hardware trap to the operating system 51 Dr. Abeer Mahmoud

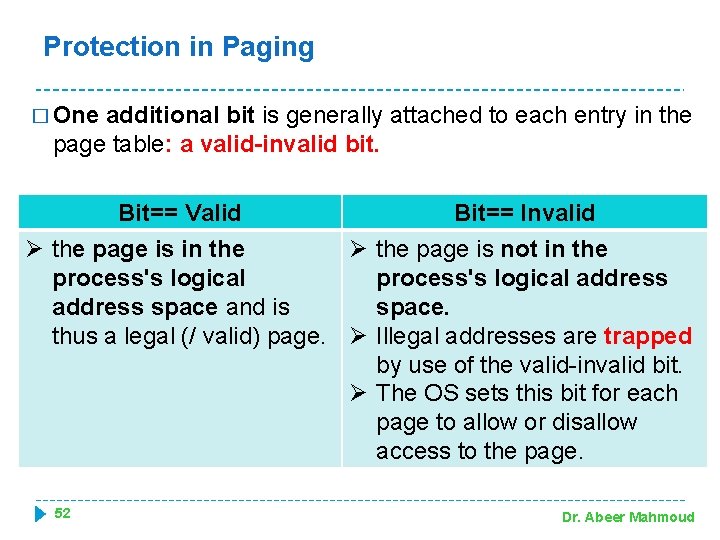
Protection in Paging � One additional bit is generally attached to each entry in the page table: a valid-invalid bit. Bit== Valid Bit== Invalid Ø the page is in the Ø the page is not in the process's logical address space and is space. thus a legal (/ valid) page. Ø Illegal addresses are trapped by use of the valid-invalid bit. Ø The OS sets this bit for each page to allow or disallow access to the page. 52 Dr. Abeer Mahmoud

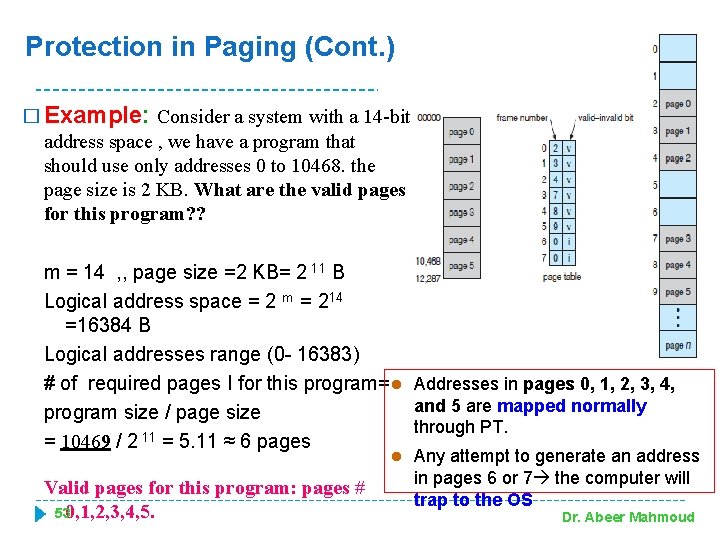
Protection in Paging (Cont. ) � Example: Consider a system with a 14 -bit address space , we have a program that should use only addresses 0 to 10468. the page size is 2 KB. What are the valid pages for this program? ? m = 14 , , page size =2 KB= 2 11 B Logical address space = 2 m = 214 =16384 B Logical addresses range (0 - 16383) # of required pages I for this program= l Addresses in pages 0, 1, 2, 3, 4, and 5 are mapped normally program size / page size through PT. = 10469 / 2 11 = 5. 11 ≈ 6 pages l Valid pages for this program: pages # 530, 1, 2, 3, 4, 5. Any attempt to generate an address in pages 6 or 7 the computer will trap to the OS Dr. Abeer Mahmoud

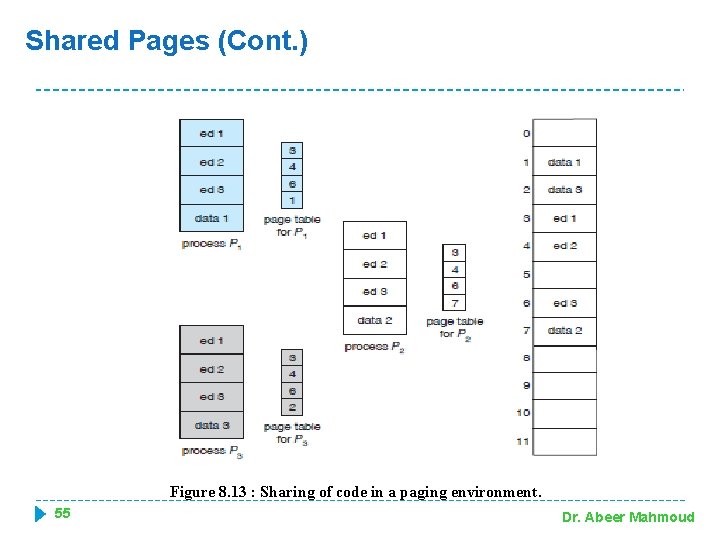
Shared Pages � An advantage of paging is the possibility of sharing common code. This is particularly important in a time-sharing environment. � Example: � Consider a system that supports 40 users, each of whom executes a text editor �If the text editor consists of 150 KB of code and 50 KB of data space we need 8, 000 KB to support the 40 users. �If the code shared the required memory space =2, 150 KB � Only one copy of the editor need be kept in RAM. Each user's page table maps onto the same physical copy of the editor, but data pages are mapped onto different frames. 54 Dr. Abeer Mahmoud

Shared Pages (Cont. ) Figure 8. 13 : Sharing of code in a paging environment. 55 Dr. Abeer Mahmoud

Segmentation 56 Dr. Abeer Mahmoud

Segmentation � Users prefer to view memory as a collection of variable-sized segments, with no necessary ordering among segments. � Address space is made up of variable -sized logical segments e. g. main function, subroutines, some data structures (list, array, stack, etc. ), . . . � Segmentation is a memory-management scheme that supports the user view of memory where a logical address space is a collection of segments. 57 Dr. Abeer Mahmoud

Segmentation (cont. ) � Each segment has a name and a length. � The addresses specify both the segment name and the offset within the segment. � The user therefore specifies each address by two quantities: 1. a segment name …. (replaced by segment # for simplicity) 2. an offset � Logical addresses specify < segment identifier, offset > � Segmentation 58 suffer from external fragmentation Dr. Abeer Mahmoud

Segmentation: Hardware � Segment Table: used to convert from logical to physical addresses � Segment table entry = ( segment base, segment limit ) v Base = starting physical address of segment in memory v Limit = size of segment � Logical address consist of : v Segment number (s) -- used as an index into a segment table. v Segment offset (d)- is added to base address to define the physical memory address v The 59 offset of the logical address must be between 0 and the segment limit. If it is not, we trap to the OS (logical Dr. Abeer Mahmoud addressing attempt beyond end of segment).

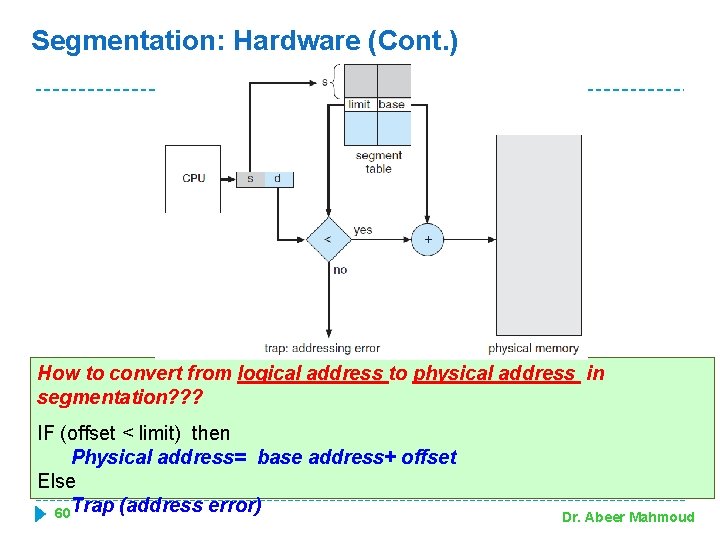
Segmentation: Hardware (Cont. ) How to convert from logical address to physical address in segmentation? ? ? IF (offset < limit) then Figure 8. 19: Segmentation hardware Physical address= base address+ offset Else 60 Trap (address error) Dr. Abeer Mahmoud

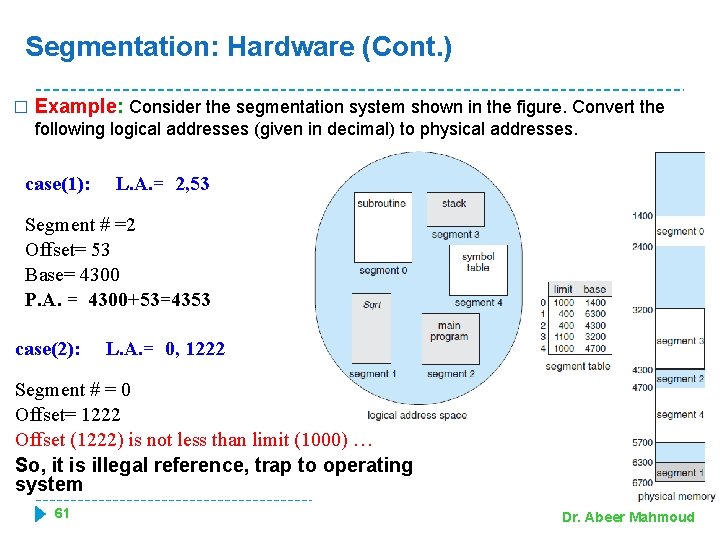
Segmentation: Hardware (Cont. ) � Example: Consider the segmentation system shown in the figure. Convert the following logical addresses (given in decimal) to physical addresses. case(1): L. A. = 2, 53 Segment # =2 Offset= 53 Base= 4300 P. A. = 4300+53=4353 case(2): L. A. = 0, 1222 Segment # = 0 Offset= 1222 Offset (1222) is not less than limit (1000) … So, it is illegal reference, trap to operating system 61 Dr. Abeer Mahmoud

Thank you End of Chapter 8 62 Dr. Abeer Mahmoud
 Gstt johor
Gstt johor Princess nora university
Princess nora university University of bridgeport computer science
University of bridgeport computer science University of bridgeport computer science faculty
University of bridgeport computer science faculty Fsu cs faculty
Fsu cs faculty Brown university computer science faculty
Brown university computer science faculty Herszon kherson maritime college of merchant marine fleet
Herszon kherson maritime college of merchant marine fleet Hubert kairuki memorial university faculty of medicine
Hubert kairuki memorial university faculty of medicine Hyperparathyreosis
Hyperparathyreosis King abdulaziz university faculty of medicine
King abdulaziz university faculty of medicine Mendel university faculty of business and economics
Mendel university faculty of business and economics Singularity executive program
Singularity executive program Agnes csaki semmelweis
Agnes csaki semmelweis Masaryk university medical faculty
Masaryk university medical faculty Feup university of porto
Feup university of porto Charles university faculty of humanities
Charles university faculty of humanities Faculty of veterinary medicine cairo university logo
Faculty of veterinary medicine cairo university logo Faculty of law of the university of zagreb
Faculty of law of the university of zagreb University of montenegro faculty of law
University of montenegro faculty of law University of kragujevac faculty of technical sciences
University of kragujevac faculty of technical sciences University of cologne faculty of management
University of cologne faculty of management Leading university teacher
Leading university teacher Hacettepe university faculty of medicine
Hacettepe university faculty of medicine Conus arteriosus
Conus arteriosus Semmelweis university faculty of medicine
Semmelweis university faculty of medicine Ulfg2
Ulfg2 York university my file
York university my file University of debrecen faculty of economics and business
University of debrecen faculty of economics and business Clemson university electrical engineering
Clemson university electrical engineering Faculty of veterinary medicine cairo university
Faculty of veterinary medicine cairo university Faculty of mechanical engineering thammasat university
Faculty of mechanical engineering thammasat university Mendel university faculty of business and economics
Mendel university faculty of business and economics Masaryk university medical faculty
Masaryk university medical faculty Faculty of public health mahidol university
Faculty of public health mahidol university Trypanosoma bruzi
Trypanosoma bruzi Faculty of education khon kaen university
Faculty of education khon kaen university นิเทศ จุฬา
นิเทศ จุฬา Cairo university faculty of veterinary medicine
Cairo university faculty of veterinary medicine The protection of information in computer systems
The protection of information in computer systems Ucl university computer science
Ucl university computer science Unt faculty information system
Unt faculty information system Compare torvald and nora's attitude towards money
Compare torvald and nora's attitude towards money The ancent
The ancent Nora egan
Nora egan Nora middleware
Nora middleware Nora schindler
Nora schindler Non obvious relationship awareness
Non obvious relationship awareness Warty nora
Warty nora Noravines
Noravines Dr laura schubert
Dr laura schubert Manner fabrik führung
Manner fabrik führung Nora vartanyan
Nora vartanyan Nora henriksen
Nora henriksen Nora liesenfeld
Nora liesenfeld Ylöskirjaus
Ylöskirjaus Biografia de antonio skarmeta
Biografia de antonio skarmeta Serat wulangreh kedadean saka saka
Serat wulangreh kedadean saka saka Nora el internado
Nora el internado Nora mulvaney
Nora mulvaney Nora ntu
Nora ntu I.i.s.s. michele de nora
I.i.s.s. michele de nora Nora edmond
Nora edmond Cascading problem in dynamic cmos logic
Cascading problem in dynamic cmos logic