Network Design and Management Copyright 2005 John Wiley
















- Slides: 67

Network Design and Management Copyright 2005 John Wiley & Sons, Inc 1

Traditional Network Design • A structured systems analysis and design process – Network analysis phase • Meeting with users to determine the needs and applications • Estimating data traffic on each part of the network • Designing circuits needed to support this traffic and obtains cost estimates – Implementation phase: • Building and implementing the network • Takes place a year or two later • Works well for static and slowly evolving networks (although costly and time consuming) Copyright 2005 John Wiley & Sons, Inc 2

Inadequacy of Traditional Design • Forces making the traditional design approach less appropriate for many of today’s networks: – Rapidly changing technology of computers, networking devices and the circuits • More powerful devices, much faster circuits – Rapidly growing network traffic • Difficulty of estimating demand growth – Shorter planning periods (3 years) – Dramatic change in the balance of costs • Before: Equipment; now: staff • Design goal: Minimize the staff time to operate (not the hardware costs) – E. g. , use similar standardized equipment for the ease of management Copyright 2005 John Wiley & Sons, Inc 3

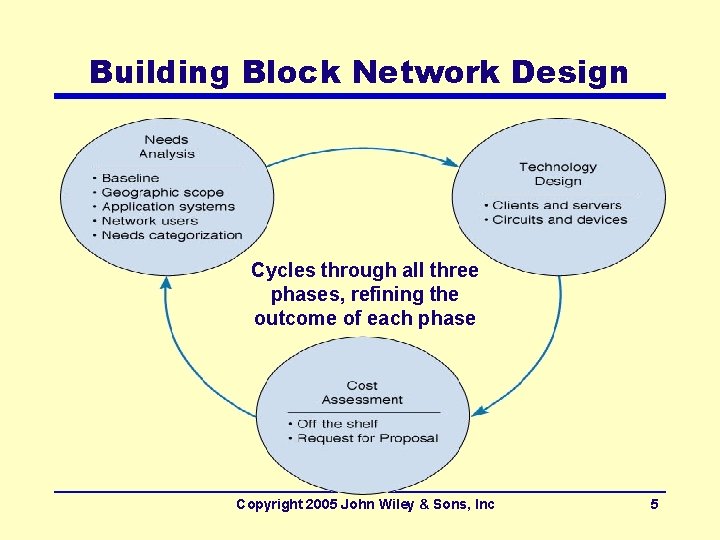
Building Block Network Design • A simpler new approach • Key concept: – Network that use a few standard components are cheaper than (in the long run) the networks that use many different components • Start with a few standard components with ample capacity (without extensive traffic analysis) – Called: narrow and deep (few types of devices, used over and over) – Result: simpler design process, easily managed network • Phases of design – Needs analysis, Technology design, and Cost assessment – Cycles through, refining the outcome of each phase Copyright 2005 John Wiley & Sons, Inc 4

Building Block Network Design Cycles through all three phases, refining the outcome of each phase Copyright 2005 John Wiley & Sons, Inc 5

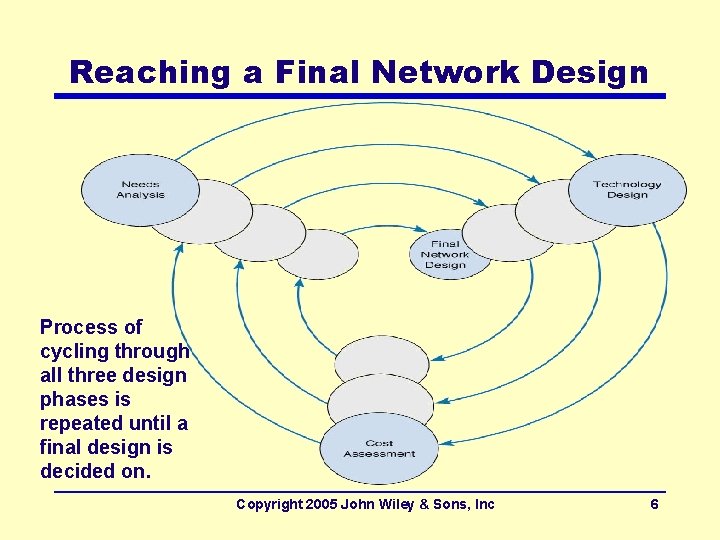
Reaching a Final Network Design Process of cycling through all three design phases is repeated until a final design is decided on. Copyright 2005 John Wiley & Sons, Inc 6

Needs Analysis • To understand why the network is being built and what users and applications it will support – – To improve poor performance? To enable new applications? To upgrade, replace old equipment? or To standardize equipment (one type, one protocol, etc) • Goals differ depending on the network – LAN and BN (everything owned by the organization) • Design over capacity – Little additional cost after the initial cost – MAN/WAN (mostly rely on leased circuits) • Design under capacity – Lease additional circuits if necessary Copyright 2005 John Wiley & Sons, Inc 7

Baselining • Gain an understanding of the current operations (applications and messages) – Most projects today involve upgrades and not new network designs: • A good understanding of the needs already exist – Provides baselining against future needs – Clear picture of • Sequence of operations, processing times, • Work volumes • Current network • Existing cost • User/management needs Copyright 2005 John Wiley & Sons, Inc 8

Objective of Needs Analysis • Objectives – Define the geographic scope of the network – Define applications and users that will use the network • The goal: – To produce a logical network design that • Describes what network elements will be needed to meet the organization’s needs • Specifies no technologies nor products at this stage • Focuses on functionality (e. g. , high speed access network) Copyright 2005 John Wiley & Sons, Inc 9

First Step in Needs Analysis • Break the network into three conceptual parts (based on their geographic and logical scope): – Access layer • Lies closest to the user; often a LAN – Distribution layer • Connects the access layer to the rest of the network; often a backbone network – Core layer • Connects the different parts of the distribution layer together; often a WAN • Not all layers present in all networks – Small networks may not have a distribution layer Copyright 2005 John Wiley & Sons, Inc 10

Next Step in Needs Analysis • Identify basic technical constraint at each layer – Examples: If access layer is • A MAN; then users need to use dial up lines • A LAN; no need to use T 1 lines • Identify constraints imposed by the current network infrastructure – Example: adding a new building to an existing office complex that use 100 Base-T • Probably choose the same for new building Copyright 2005 John Wiley & Sons, Inc 11

Design Process • Start with the highest level – Begin by drawing a WAN connecting locations • Next draw individual locations connected to WAN – Usually a series of diagrams, one for each location • Gather information and characteristics of the environment – Legal requirements, regulations, building codes Copyright 2005 John Wiley & Sons, Inc 12

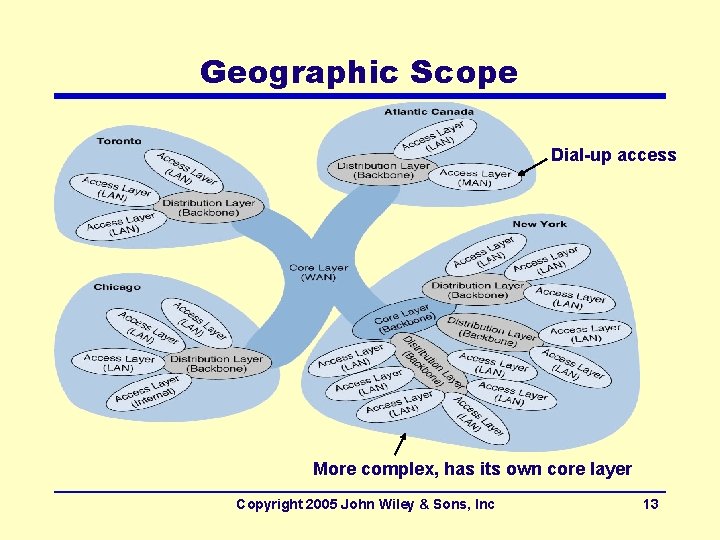
Geographic Scope Dial-up access More complex, has its own core layer Copyright 2005 John Wiley & Sons, Inc 13

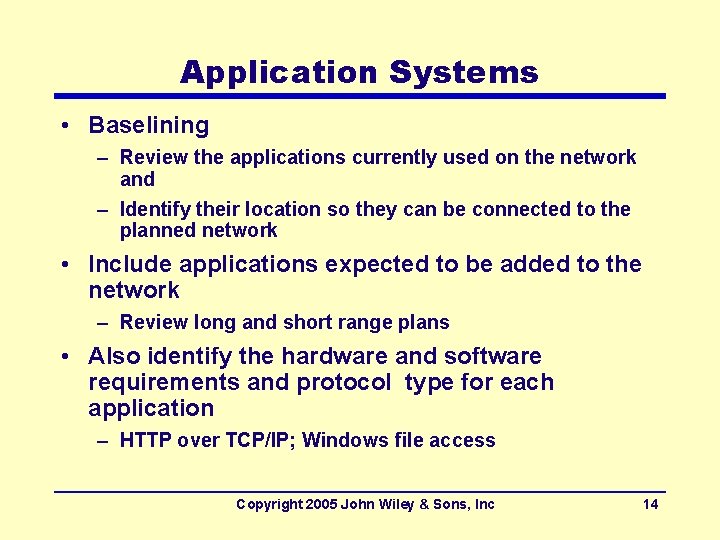
Application Systems • Baselining – Review the applications currently used on the network and – Identify their location so they can be connected to the planned network • Include applications expected to be added to the network – Review long and short range plans • Also identify the hardware and software requirements and protocol type for each application – HTTP over TCP/IP; Windows file access Copyright 2005 John Wiley & Sons, Inc 14

Network Users • Assess the number and type of users that will generate network traffic – Much network traffic comes from Internet use (i. e. , e-mail and WWW) • In the past, application systems accounted for the majority of network traffic – Future network upgrades will require understanding of the use of new applications • Effect of video on network traffic Copyright 2005 John Wiley & Sons, Inc 15

Categorizing Network Needs • Assess the traffic generated in each segment (for each application and user) – Based on an estimate of the relative magnitude of network needs (i. e. typical vs. high volume) – Can be problematic, but the goal is a relative understanding of network needs • E. g, multimedia applications: high volume • Organize network requirements into – Mandatory, Desirable, and Wish-list requirements – Enables development of a minimum level containing mandatory requirements (if cost is a constraint) Copyright 2005 John Wiley & Sons, Inc 16

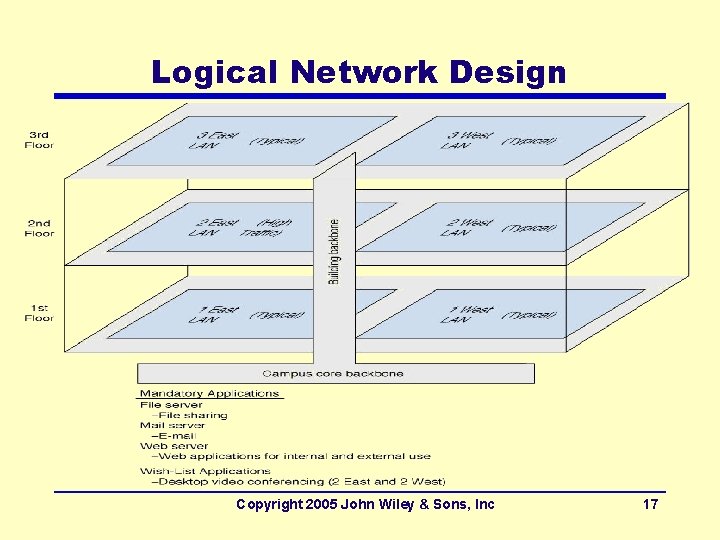
Logical Network Design Copyright 2005 John Wiley & Sons, Inc 17

Technology Design • Development of a physical network (or set of possible designs) – Specify the computers (Clients and servers) needed to support applications and users • New computers • Upgrades – Specify circuits and devices (routers, gateways) to connect the computers Copyright 2005 John Wiley & Sons, Inc 18

Designing Clients and Servers • Specification of the computers needed in terms of standard units – Allocate “base level” client computers to “typical” users – Allocate “base level” servers to typical applications – Assign “advanced” computers to “high volume” users and servers – Beware of the definition for a “typical” unit • Keeps changing as hardware costs continue to fall, and capabilities/capacities continue to increase Copyright 2005 John Wiley & Sons, Inc 19

Designing Circuits and Devices • Deciding on the fundamental technology and protocols – e. g. , Ethernet, ATM, TCP/IP • Choosing the capacity each circuit will operate at – e. g. , 10 Mbps, 1000 Mbps – Requires capacity planning • Assess current and future “circuit loading” – Amount of data to be transmitted on a circuit – Focus on either average or peak circuit traffic » Ideal: Peak traffic • Estimate size and type of “standard” and “advanced” circuits for each LAN, BN, WAN – Should “standard” LAN circuit be 10 Base-T or higher Copyright 2005 John Wiley & Sons, Inc 20

Estimating Circuit Traffic • Average traffic: – Estimate total characters transmitted per day per circuit • Peak traffic – Estimate maximum number of characters transmitted per two second interval • Estimating Message volume – Count messages in a current network and multiply it with a growth rate – Use analyzers if an existing network • Precision not a major concern – Stair step nature of communication circuit (lease another line, or upgrade to 100 Base-T) – Uncertainty to project future needs Copyright 2005 John Wiley & Sons, Inc 21

Capacity Overbuilding Dilemma • Cost of extra capacity vs. Cost of upgrading a network – Upgrading costs 50 -80% more (than building it right at the first time) – Majority complains about being under capacity, not over capacity • Most organizations intentionally overbuild – Rapid growth in demand • 5 -50% annual growth factor, sometimes 100% – Difficulty in accurate prediction • Most end up using overcapacity within 3 years – Turnpike effect: when the network is efficient and provides good service, it becomes heavily used Copyright 2005 John Wiley & Sons, Inc 22

Network Design Tools • Used mostly in the technology design process • First step: Enter a diagram of the existing network – Created from scratch (as required by some tools), or – Discovered automatically (by some tools) • Once the diagram is complete – Add information about the expected network traffic and – See if the expected level of traffic can be supported • May be accomplished through simulation models • Once simulation is complete – Examine results to see estimated delays and throughput – Change the design if necessary and rerun simulations Copyright 2005 John Wiley & Sons, Inc 23

Deliverables • A set of physical network designs – General specifications for the hardware and software required – Several alternative designs to do cost-benefit analysis • The crucial issue: – Design of the network circuits and devices • A new network designed from scratch – Important to define clients computers with care • A major part of the total cost Copyright 2005 John Wiley & Sons, Inc 24

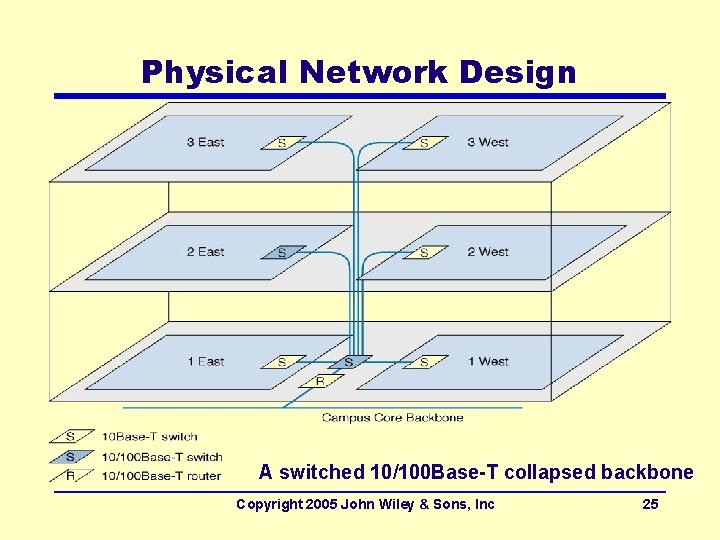
Physical Network Design A switched 10/100 Base-T collapsed backbone Copyright 2005 John Wiley & Sons, Inc 25

Cost Assessment • Assessment of the costs of various physical network design alternatives • Complex process; many factors; consider: – – Circuit costs (leased circuits and purchased cabling) Internetworking devices (switches and routers) Hardware costs (servers, hubs, NICs & UPSs) Software costs (network operating systems, application software and middleware) – Network management costs including special hardware, software, and training needed for network management – Test and maintenance costs for monitoring equipment and supporting onsite repairs – Operations costs to run the network Copyright 2005 John Wiley & Sons, Inc 26

Deliverables • An RFP – Issued to potential vendors. • Revised set of physical network diagrams – Done after the vendor(s) selected – Final technology design – Selected components (exact products and costs) • Business case – To support the network design – Expressed in terms of business objectives Copyright 2005 John Wiley & Sons, Inc 27

Designing for Network Performance • Several higher level concepts used to design network for the best performance – Managed networks • Network management software and standards • Policy-based management – Network circuits • Traffic analysis • Service level agreements – Network devices • Device latency and device memory • Load Balancing – Minimizing network traffic • Content caching and content Delivery Copyright 2005 John Wiley & Sons, Inc 28

Managed Networks • Network that uses managed devices – Managed device: standard devices that can (in addition to performing its basic functions (switching and routing)) • Monitors traffic flows, • Monitors its status and other devices connected to • Records various data on messages it processes • Sends these data to manager’s computer (on a request) • Sends alarms if a critical situation detected (such as a failing device, or unusual increase in traffic) – Problems detected and reported by devices themselves before problems become serious • Requires both hardware and software – Hardware: monitor, collect, transmit – Software: store, organize, analyze Copyright 2005 John Wiley & Sons, Inc 29

Network Management Software • Device (point) management software – Provide specific information about a device • Configuration, traffic, error conditions, etc • System management software – aka, enterprise management software – Provide analysis device info to diagnose patterns • Prevents alarm storms (for a failure on a circuit, many connected devices sending alarms) – Software analyze these and correlates them and generates a single alarm to the manager • Application management software – Monitor applications based on device info – Focus on delays and application layer packets Copyright 2005 John Wiley & Sons, Inc 30

Network Management Standards • Application layer protocols defining type of information collected and format of control messages – Simple Network Management Protocol (SNMP) • Developed for Internet and LANs • Components of SNMP – Agent: collects device info and responds requests from the manager – Management Information Base (MIB): database at device stored by the agent – Network Management Station (NMS): Access MIB, sends control messages to agent – Common Management Interface Protocol (CMIP) • Developed for OSI type networks Copyright 2005 John Wiley & Sons, Inc 31

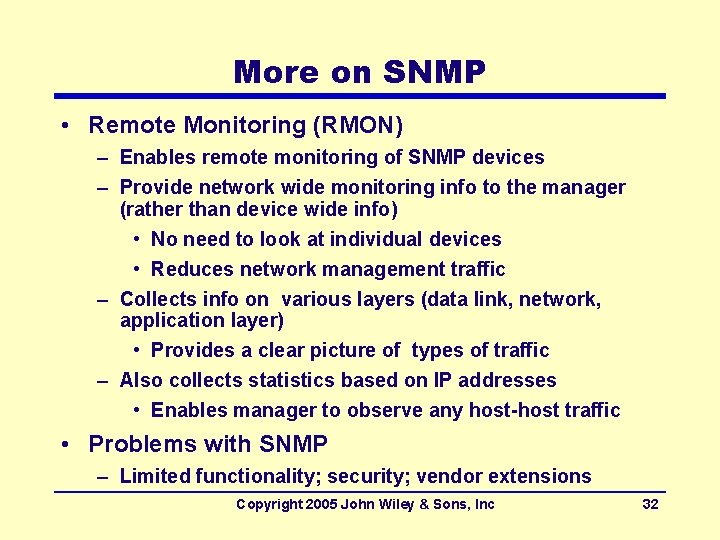
More on SNMP • Remote Monitoring (RMON) – Enables remote monitoring of SNMP devices – Provide network wide monitoring info to the manager (rather than device wide info) • No need to look at individual devices • Reduces network management traffic – Collects info on various layers (data link, network, application layer) • Provides a clear picture of types of traffic – Also collects statistics based on IP addresses • Enables manager to observe any host-host traffic • Problems with SNMP – Limited functionality; security; vendor extensions Copyright 2005 John Wiley & Sons, Inc 32

Policy-Based Management • Enables managers to set priority policies for traffic (to take effect when congested) – Example: • Manager: order processing to have the highest priority • Software: configure devices using Qo. S capabilities in ATM, TCP/IP, etc to give this application the highest priority • Expected to become more important Copyright 2005 John Wiley & Sons, Inc 33

Network Circuits • Play a critical role in designing network for maximum performance • Important to size the circuit and place them to match the traffic • Areas of concern: – Circuit loading and capacity planning (already discussed before) – Traffic analysis, and – Service level agreements especially for MAN and WAN Copyright 2005 John Wiley & Sons, Inc 34

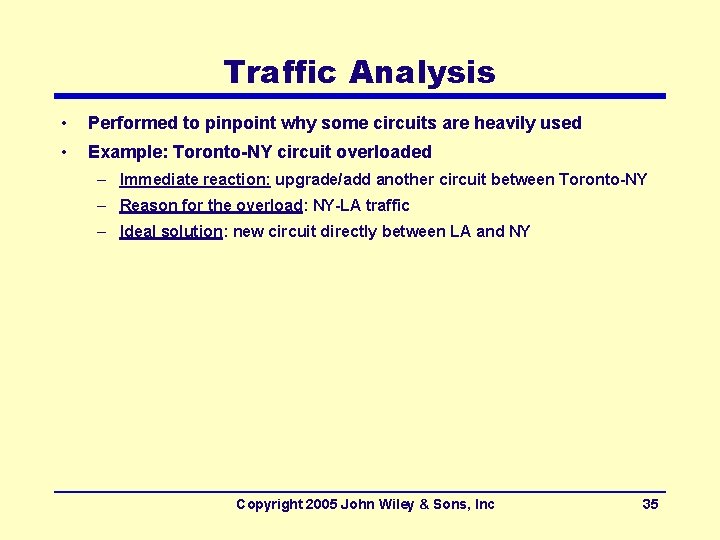
Traffic Analysis • Performed to pinpoint why some circuits are heavily used • Example: Toronto-NY circuit overloaded – Immediate reaction: upgrade/add another circuit between Toronto-NY – Reason for the overload: NY-LA traffic – Ideal solution: new circuit directly between LA and NY Copyright 2005 John Wiley & Sons, Inc 35

Service Level Agreements • Established between organizations and common carrier and ISPs • Specify the exact type of performance that common carrier will provide – Availability • 99% can be down 3. 65 days per year with no penalty • 99. 9% can be down 8. 76 hours per year with no penalty – Also includes maximum response time and other parameters • Specify penalties if the desired performance is not provided Copyright 2005 John Wiley & Sons, Inc 36

Network Devices • Network devices from different vendors provide different capabilities – Some faster, some more reliable, etc, . • Factors important in network performance – Device latency • Delay imposed by device in processing messages – Device memory • Size of memory in device – Load Balancing • Capability in sharing the network load Copyright 2005 John Wiley & Sons, Inc 37

Minimizing Network Traffic • Another approach in improving network performance • Attempts to move most commonly used data closer to user reduces traffic elsewhere – Providing servers with duplicate copies at points closer to users • Approaches in reducing traffic – Content caching – Content delivery Copyright 2005 John Wiley & Sons, Inc 38

Content Caching • Basic idea: Store other people’s Web data closer to your users – Install a content engine (aka, cache engine) close to your Internet connection – Install special content management software on the router • Operations – Stores requests and responses (mostly static files) – Examines each outgoing request; if it requires a file already in cache, it responds immediately (without going to the requested site) • Stores contents form most commonly accessed sites (updates them frequently) • Must operate at wire speeds (otherwise degrade performance) • Reduces traffic between Internet and Organization less circuits to lease Copyright 2005 John Wiley & Sons, Inc 39

Content Delivery • A special type of Internet service provided by “content delivery providers (CDPs)” – A CDP stores Web files for its client closer to the client’s potential users – Akamai, a CDP, operates 10, 000 servers located near busiest NAPs and MAEs • Servers contain most commonly requested web info for some busiest sites like yahoo. com • When a user access a client’s site, a software in client’s server looks for an Akamai server (closer to the user) • Akamai server sends the static files, the client’s server sends the dynamic files of the site Copyright 2005 John Wiley & Sons, Inc 40

Implications for Management • Develop strong relationships with only few vendors – Use a building block approach in designing networks – Use a few common, standardized technologies everywhere in the network • Purchase technologies that will provide strong network management capabilities – Cost to operate is now much more expensive than the cost to purchase • Use powerful design and management tools – Saves money in the long run Copyright 2005 John Wiley & Sons, Inc 41

Network management Introduction • Network management – Process of operating, monitoring and controlling the network to ensure that • Networking properly (efficient data exchange) • Providing value to its users • A lack of planning and organization – Managers spend their time firefighting (reactive mode) • Dealing with breakdowns and immediate problems • Main areas of network management function: – – Configuration management Performance and fault management End user support Cost management Copyright 2005 John Wiley & Sons, Inc 42

Organizing Network Management Function • Special organizations problems presented by networking functions – Decentralized • Developers, gatherers, and users of data – Centralized • Traditional management of voice and data networks – Networks and servers owned and operated by centralized IT department • Factors impacting organization of management functions – Shift to LANs and Internet – Integrating LANs, WANs, and Internet – Integrating voice and data communications Copyright 2005 John Wiley & Sons, Inc 43

Shift to LANs and the Internet • Large scale move from using mainframes and terminals to PCs, LANs and the Internet. – Future of network management: • Successful management of multiple clients and servers over LANs, BN, s and Internet • Focus on integration of organizational networks and applications. Main problems: – Not all LANs use the same architecture – More types of network technology used, the more complex network management becomes • Staff must be familiar with many different types of devices Copyright 2005 John Wiley & Sons, Inc 44

Integrating LANs, WANs and Internet • Keys integrating them into one organization – Both LAN/Web and WAN managers to recognize that they no longer have power • No more independent decision without considering the impact on other parts • Single overall goal that best meets the needs of the entire organizations • Require some managers to compromise on policies that may not be in the best interest of its own network – Must adopt a written charter to • Define its purpose, operational philosophy, and long range goals – Must develop individual procedures to implement policies Copyright 2005 John Wiley & Sons, Inc 45

Integrating Voice & Data • Traditional voice and data networks (e. g. , POTS and LANs) handled by separate managers – Voice Communication Manager (Facilities department): • Supervise telephone switchboard, ; coordinate installation and maintenance of the voice network – Data Communication Manager (IT department): • Install own data circuit; install and maintain computers • Benefits of Integrating voice and data – Simplifies the network, and can lower network costs – Eliminates one department – Will likely happen within the next few years Copyright 2005 John Wiley & Sons, Inc 46

Configuration Management • Major functions: – Management of the network’s hardware and software and – Documenting that configuration and – Ensuring that they are updated when there is a change in the configuration Copyright 2005 John Wiley & Sons, Inc 47

Configuring Network and Clients • Adding and deleting user accounts – New user addition • Categorized as a member of a group – With corresponding privileges • Given a standard login script – Commands to run when user logs in • Updating software on client computers – Usually done automatically by Electronic Software Distribution (ESD) over the network at predefined time • Reduces cost of configuration management (long run) • Eliminates manual updates for each client • Produces accurate documents and reports • Being standardized: Desktop Management Interface (DMI) Copyright 2005 John Wiley & Sons, Inc 48

Performance & Fault Management • Performance management – Ensuring the network is operating as efficiently as possible • Fault management – Preventing, detecting, and correcting faults in the network circuits, hardware, and software • Both require – Network monitoring • Tracking the operation of network circuits and devices – Determining how heavily circuits and devices are being used – Ensuring circuits and devices are operating properly Copyright 2005 John Wiley & Sons, Inc 49

Network Monitoring • Done by network management software • Involves Network Operations Centers (NOCs) – A centralized place enabling managers to monitor the network and respond to problems before users complain • Collect operational statistics from devices – Physical network statistics • Come from modems, multiplexers, and circuits linking hardware devices – Logical network information: • Come from performance measurement systems – User response times, traffic volume on a specific circuit, the destinations of network packets, and other indices showing the network’s service level Copyright 2005 John Wiley & Sons, Inc 50

Failure Control Function • Requires developing a central control process for problem reporting and troubleshooting – Maintain a central phone number for users to report problems – Establish a central troubleshooting group • Functions include contacting hardware, software vendors or common carriers • Detecting and reporting network problems – By the help desk or NOC; by the user; and – By managed devices • Record data on messages processed and send this info back to a central database • Detect its own faulty parts and send alarms Copyright 2005 John Wiley & Sons, Inc 51

Trouble Tickets • Reports that indicate network faults – Automatically produced by software packages • Main reasons for trouble tickets – Problem tracking • To determine status for correcting problems – Responsible people, schedule, status, resolution, etc – Problem statistics • Used to generate various statistical reports (number of failures per card, circuit, hardware, etc. , ) – Problem solving methodology • To ensure critical problems get higher priority – Management reports • To determine availability, product and vendor reliability, vendor responsiveness Copyright 2005 John Wiley & Sons, Inc 52

Trouble Log • Purpose – To record problems that must be corrected and keep track of associated statistics • Helpful for reviewing problem patterns on the network • Can be used to identify which network components are the most problematic • Example of a trouble log: – 37 calls for software problems, 26 calls for modems, 49 calls for client computers, 2 calls for common carriers Copyright 2005 John Wiley & Sons, Inc 53

Performance and Failure Statistics • Main performance statistics – Number of packets moved on a circuit and – Response time • Failure statistics – Availability: • Percent of time the network available to users – Number of hours per month the network is available divided by the total of hours in a month (I. e. , 720 hours) – Most networks: 99% to 99. 5% – Downtime: • Percent of time network is not available Copyright 2005 John Wiley & Sons, Inc 54

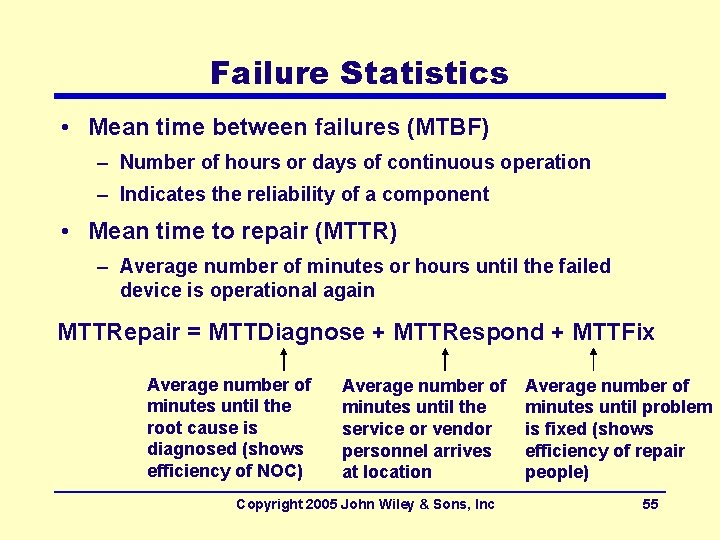
Failure Statistics • Mean time between failures (MTBF) – Number of hours or days of continuous operation – Indicates the reliability of a component • Mean time to repair (MTTR) – Average number of minutes or hours until the failed device is operational again MTTRepair = MTTDiagnose + MTTRespond + MTTFix Average number of minutes until the root cause is diagnosed (shows efficiency of NOC) Average number of minutes until the service or vendor personnel arrives at location Copyright 2005 John Wiley & Sons, Inc Average number of minutes until problem is fixed (shows efficiency of repair people) 55

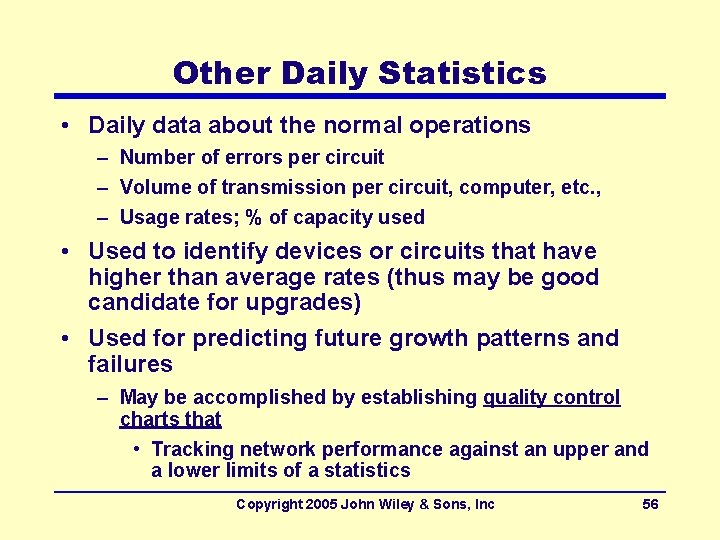
Other Daily Statistics • Daily data about the normal operations – Number of errors per circuit – Volume of transmission per circuit, computer, etc. , – Usage rates; % of capacity used • Used to identify devices or circuits that have higher than average rates (thus may be good candidate for upgrades) • Used for predicting future growth patterns and failures – May be accomplished by establishing quality control charts that • Tracking network performance against an upper and a lower limits of a statistics Copyright 2005 John Wiley & Sons, Inc 56

Quality Control Chart Copyright 2005 John Wiley & Sons, Inc 57

End User Support • Solving the problems users encounter while using the network • Main functions within end user support: – Resolving network faults (discussed already) – Resolving user problems – End user Training Copyright 2005 John Wiley & Sons, Inc 58

Resolving Problems • Major sources of problems (with user equipment) – Hardware device failures (easiest to fix) – Lack of user knowledge on properation (easier to fix) • Solved by discussing the problem with user and taking the person through the process step by step – Problems with software, software settings or software incompatibility (hardest to fix) • Could be result of a bug or software not functioning properly • May requires expertise with that specific software • May require software upgrades Copyright 2005 John Wiley & Sons, Inc 59

Process of Resolving Problems • • • Assistance requested (by user) form the help desk Trouble ticket created and maintained by the trouble log Problem resolved by the receiving staff members – If not resolved, problem is escalated • Levels of problem resolution process – Help desk: Resolve about 85% of problems – Staff members with specialized skills specific to the problem at hand: Brought in when help desk can’t solve – Technical specialists with a higher level of training: Contacted by level 2 to look into harder problems Copyright 2005 John Wiley & Sons, Inc 60

Cost Management • One of the most challenging areas lately – Traffic growing more rapidly than the budget – Forcing managers to provide greater capacity at an ever lower cost per megabyte Copyright 2005 John Wiley & Sons, Inc 61

Sources of Cost • Total Cost of Ownership (TCO) – A measure of how much it costs per year to keep one computer operating – Includes cost of • Repairs and software/hardware upgrades • Support staff (maintain, install, administer, etc) • Training and technical support • Time “wasted” by the user when problems occur – TCO of a Windows computer • TOO HIGH - $8 -12, 000 per computer per year • Main culprit: inclusion of “wasted” time – Not commonly accepted Copyright 2005 John Wiley & Sons, Inc 62

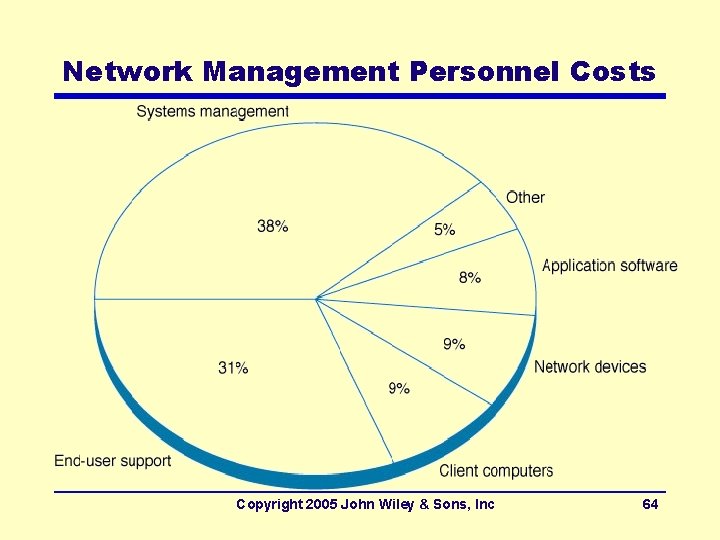
Sources of Cost (Cont. ) • Net Cost of Ownership (NCO) – An alternative to TCO; also called as “real TCO” – Measures only direct costs • Leaving out so-called “wasted” time – NCO costs per computer: between $1500 -$3500 • Net management for a 100 -user network require an annual budget of between $150, 000 - $350, 000 – Largest network budget items (with NCO): • Personnel cost, accounting for 50 -70% of costs • WAN circuits • Hardware upgrades and replacement parts – Important message: Focus should be on ways to reduce personnel time, not hardware costs Copyright 2005 John Wiley & Sons, Inc 63

Network Management Personnel Costs Copyright 2005 John Wiley & Sons, Inc 64

Managing Network Budgets • Difficult to manage – Networks growing rapidly requiring more staff and more equipment • Use charge-back policies to counter increasing cost – Allocate costs associated with the network to specific users • Users must pay for their usage (by moving part of their budget) to the network group – Applicable to WAN and mainframe users as a cost accounting mechanism – Difficult to implement on LANs Copyright 2005 John Wiley & Sons, Inc 65

Reducing Costs • Develop standard hardware/software configurations for client computers, servers, and network devices – Easier to diagnose and fix problems; Easier to learn • Automate as much of the network management process as possible – Use of ESD, DHCP and a other network management tools • Reduce the cost of installing new hardware/software – Reduce the staff time spent in installing; Work with vendors • Centralize help desks – More specialists in one location faster problem resolution • Move to thin client architectures – Reduces software and support costs Copyright 2005 John Wiley & Sons, Inc 66

Implications for Management • Network management requires – A good understanding of networking technologies – An ability to work with end users and management – An understanding of key elements driving network costs • Requires special skill to explain the business value of the networks to senior management – Needed to justify increased cost of management • Network management increasing its complexity – New, more intelligent technologies in managing networks – More reliable, but more expensive and requires new skills in designing, installing and managing • Difficulty in keeping the staff Copyright 2005 John Wiley & Sons, Inc 67