Network Management Accounting and Performance Strategies Graphically Rich






- Slides: 26

Network Management: Accounting and Performance Strategies - Graphically Rich Book Network Management: Accounting and Performance Strategies by Benoit Claise - CCIE No. 2686; Ralf Wolter Publisher: Cisco Press Pub Date: June 20, 2007 Print ISBN-10: 1 -58705 -198 -2 Print ISBN-13: 978 -1 -58705 -198 -2 Pages: 672 ACCOUNTING MANAGEMENT

Understanding the need for Accounting Management What is accounting management? Why do networks require accounting management? Why is accounting almost a stealth area within network management? Which problems do accounting management solutions solve? How can the business use this information for network planning, redesign, and billing? What aspects make up accounting (data collection, data analysis, reporting, billing, and so on)?

Defining accounting management

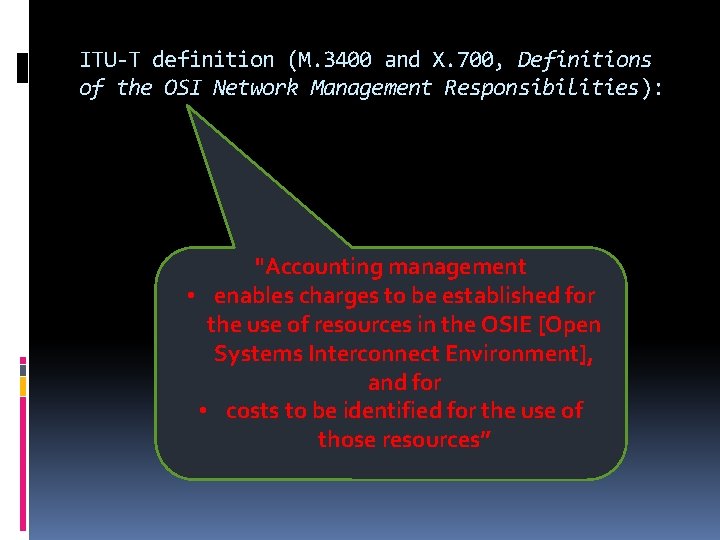
ITU-T definition (M. 3400 and X. 700, Definitions of the OSI Network Management Responsibilities): "Accounting management • enables charges to be established for the use of resources in the OSIE [Open Systems Interconnect Environment], and for • costs to be identified for the use of those resources”

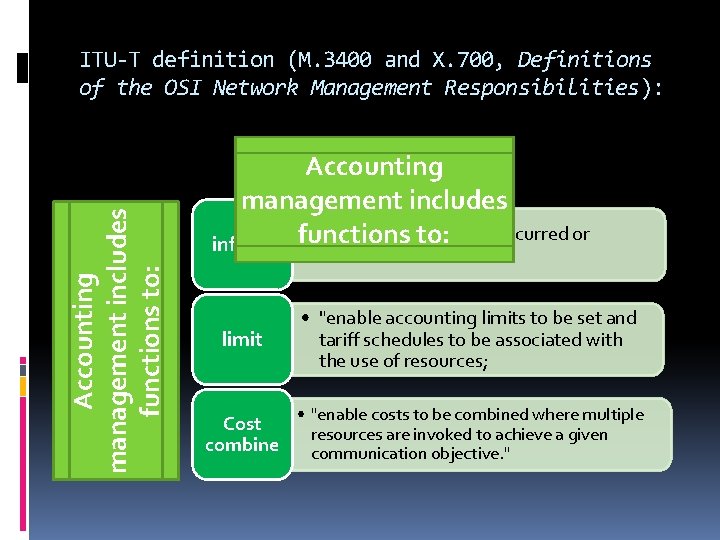
Accounting management includes functions to: ITU-T definition (M. 3400 and X. 700, Definitions of the OSI Network Management Responsibilities): Accounting management includes • "inform users of costs incurred or inform functions to: resources consumed” limit • "enable accounting limits to be set and tariff schedules to be associated with the use of resources; • "enable costs to be combined where multiple Cost resources are invoked to achieve a given combine communication objective. "

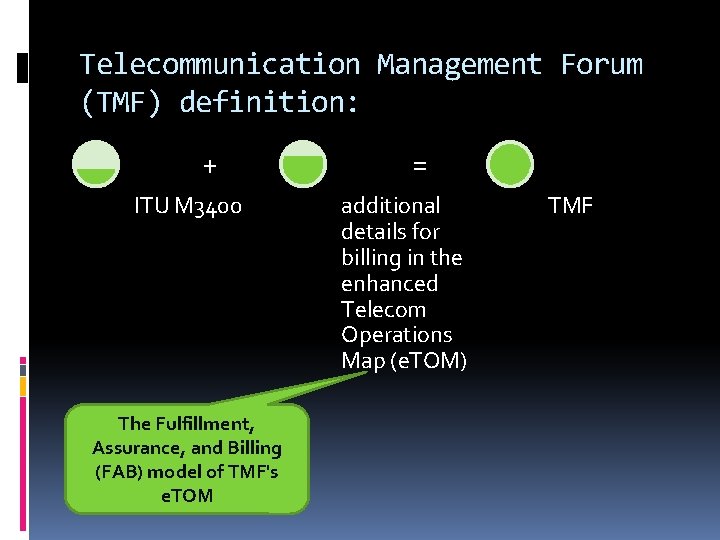
Telecommunication Management Forum (TMF) definition: + ITU M 3400 The Fulfillment, Assurance, and Billing (FAB) model of TMF's e. TOM = additional details for billing in the enhanced Telecom Operations Map (e. TOM) TMF

Telecommunication Management Forum (TMF) definition: The TMF refers to the ITU-T accounting definition (M. 3400) and provides additional details for billing in the enhanced Telecom Operations Map (e. TOM), The Business Process Framework, Document GB 921. The Fulfillment, Assurance, and Billing (FAB) model of TMF's e. TOM positions the "Network Data Management" building block between assurance and billing. "Network Data Management: this process encompasses the collection of usage data and network and information technology events and data for the purpose of network performance and traffic analysis. This data may also be an input to Billing (Rating and Discounting) processes at the Service Management Layer, depending on the service and its architecture. " Chapter 3 explains the FAB model in more detail.

IETF definition: Request For Comment (RFC) 2975, Introduction to Accounting Management the collection of resource consumption data for the purposes of capacity and trend analysis, cost allocation, auditing, and billing. Accounting management requires that resource consumption be measured, rated, assigned, and communicated between appropriate parties. "

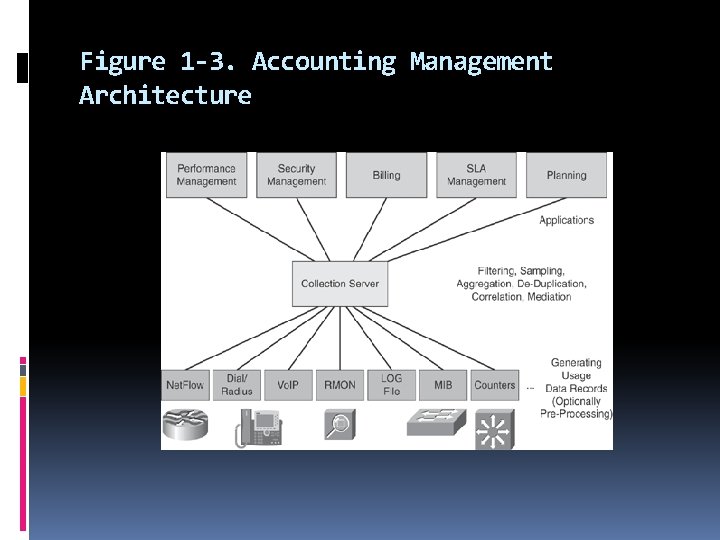
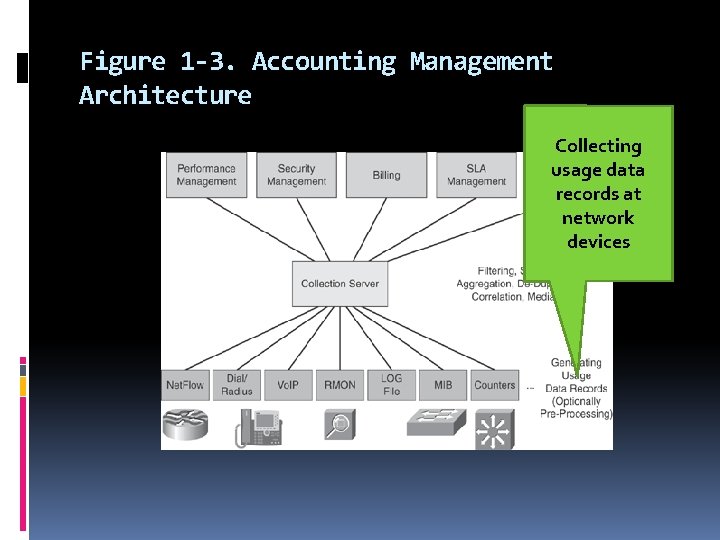
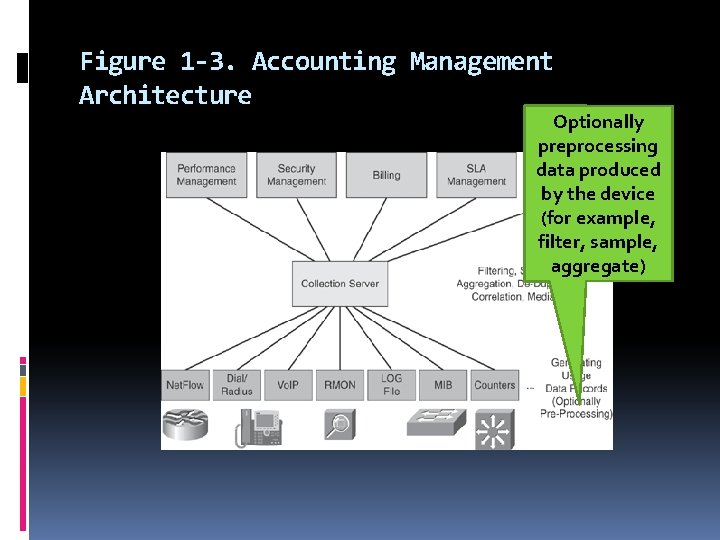
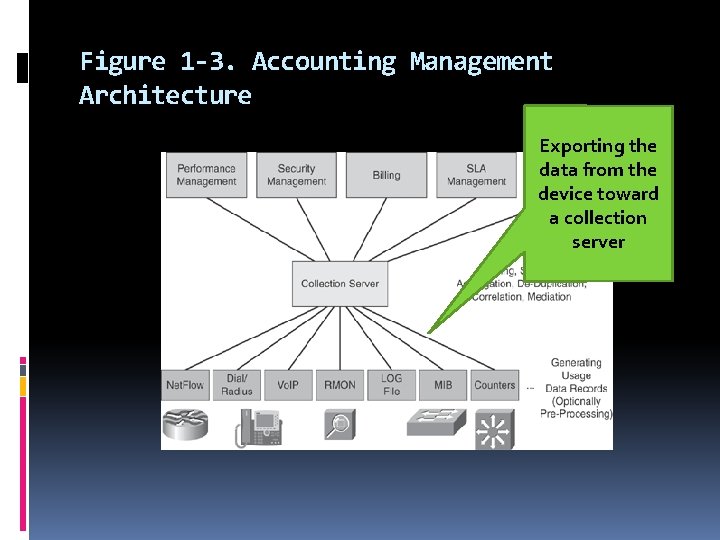
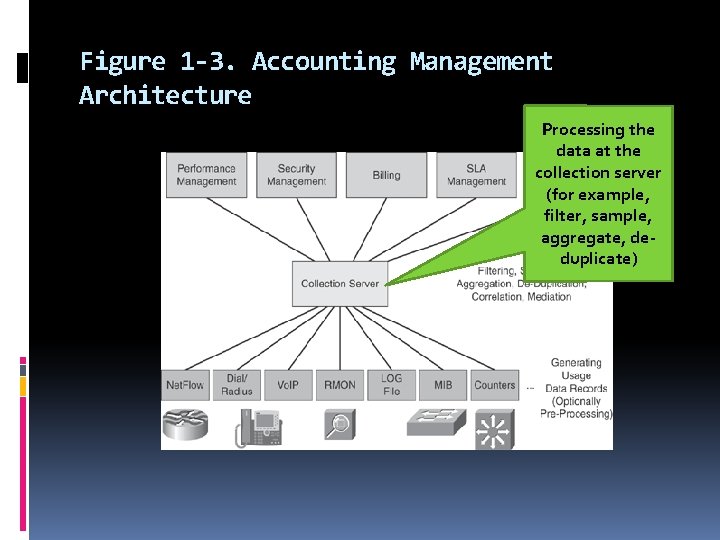
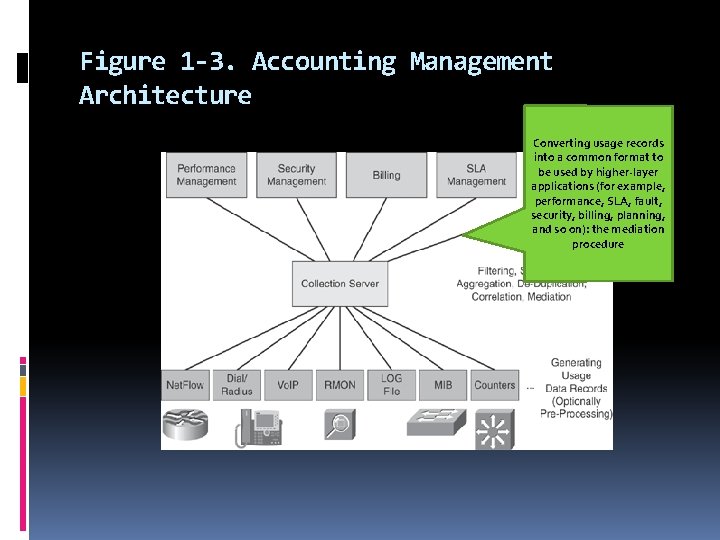
In this book, we use the term accounting management to describe the following processes: Collecting usage data records at network devices Optionally preprocessing data produced by the device (for example, filter, sample, aggregate) Exporting the data from the device toward a collection server Processing the data at the collection server (for example, filter, sample, performance, aggregate, de-duplicate) SLA, fault, security, Converting usage records into a common format to be used by higherlayer applications : the mediation procedure billing, planning, and so on

Figure 1 -3. Accounting Management Architecture

Figure 1 -3. Accounting Management Architecture Collecting usage data records at network devices

Figure 1 -3. Accounting Management Architecture Optionally preprocessing data produced by the device (for example, filter, sample, aggregate)

Figure 1 -3. Accounting Management Architecture Exporting the data from the device toward a collection server

Figure 1 -3. Accounting Management Architecture Processing the data at the collection server (for example, filter, sample, aggregate, deduplicate)

Figure 1 -3. Accounting Management Architecture Converting usage records into a common format to be used by higher-layer applications (for example, performance, SLA, fault, security, billing, planning, and so on): the mediation procedure

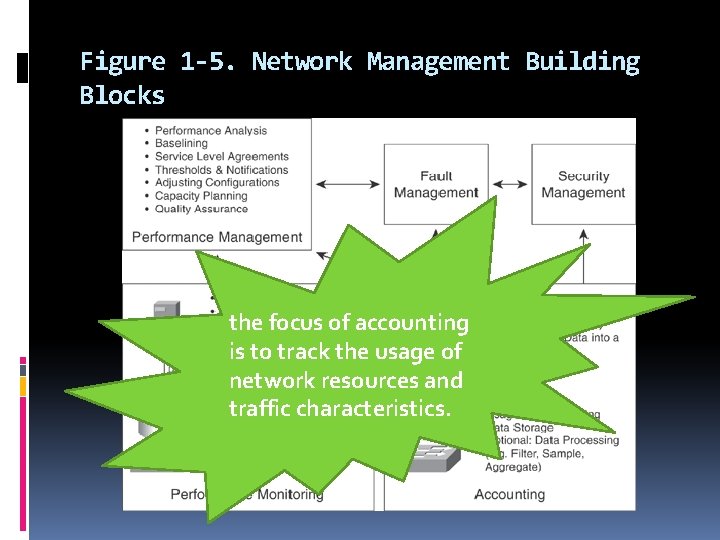
Figure 1 -5. Network Management Building Blocks the focus of accounting is to track the usage of network resources and traffic characteristics.

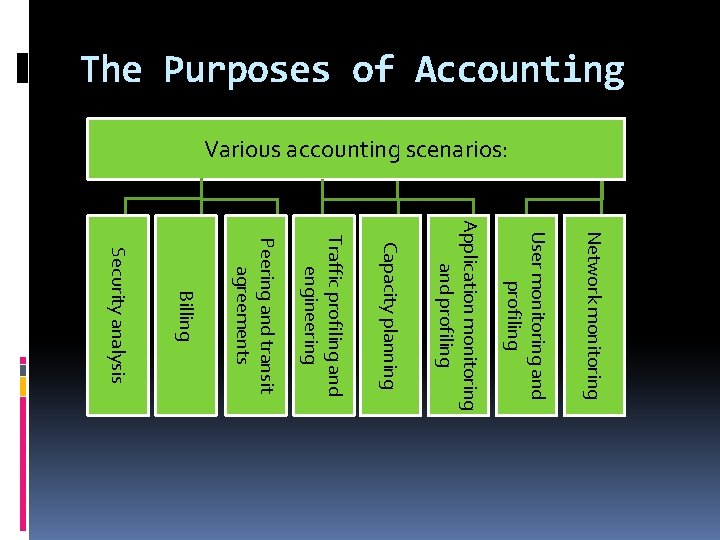
The Purposes of Accounting Various accounting scenarios: Network monitoring User monitoring and profiling Application monitoring and profiling Capacity planning Traffic profiling and engineering Peering and transit agreements Billing Security analysis

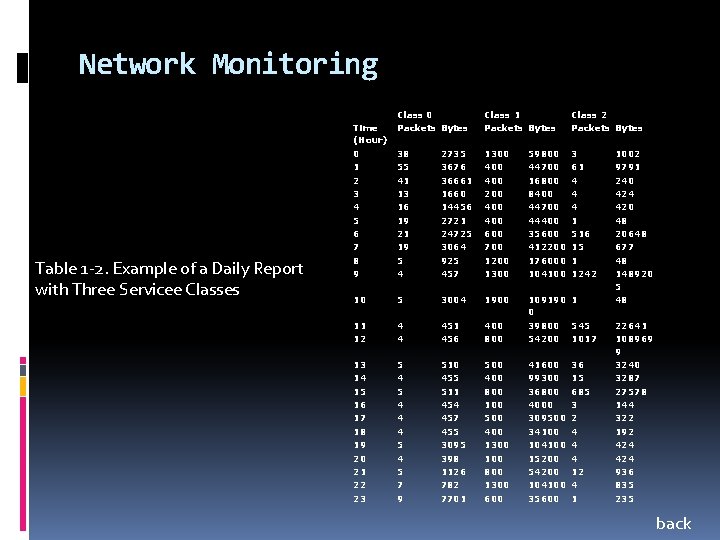
Network Monitoring Table 1 -2. Example of a Daily Report with Three Servicee Classes Time (Hour) 0 1 2 3 4 5 6 7 8 9 Class 0 Packets Bytes Class 1 Packets Bytes Class 2 Packets Bytes 38 55 41 13 16 19 21 19 5 4 2735 3676 36661 1660 14456 2721 24725 3064 925 457 1300 400 200 400 600 700 1200 1300 59800 44700 16800 8400 44700 44400 35600 412200 176000 104100 3 61 4 4 4 1 516 15 1 1242 10 5 3004 1900 11 12 4 4 451 456 400 800 109190 1 0 39800 545 54200 1017 13 14 15 16 17 18 19 20 21 22 23 5 4 4 4 5 7 9 510 455 511 454 457 455 3095 398 1126 782 7701 500 400 800 100 500 400 1300 100 800 1300 600 41600 99300 36800 4000 309500 34100 104100 15200 54200 104100 35600 36 15 685 3 2 4 4 4 12 4 1 1002 9791 240 424 420 48 20648 677 48 148920 5 48 22641 108969 9 3240 3287 27578 144 322 192 424 936 835 235 back

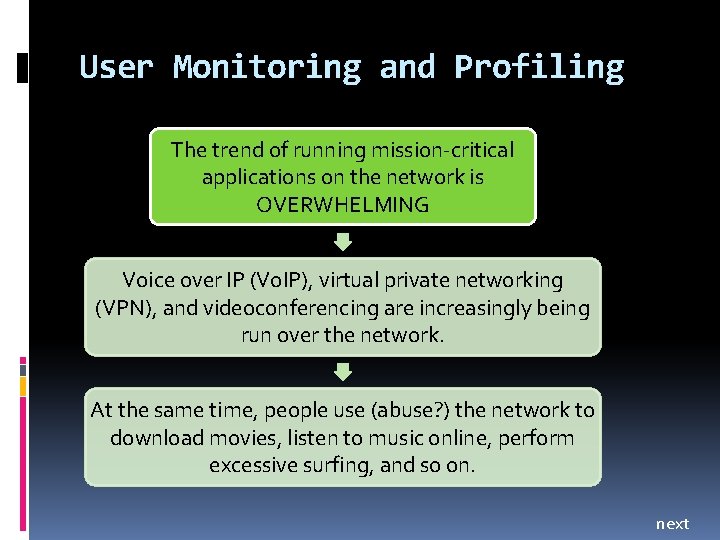
User Monitoring and Profiling The trend of running mission-critical applications on the network is OVERWHELMING Voice over IP (Vo. IP), virtual private networking (VPN), and videoconferencing are increasingly being run over the network. At the same time, people use (abuse? ) the network to download movies, listen to music online, perform excessive surfing, and so on. next

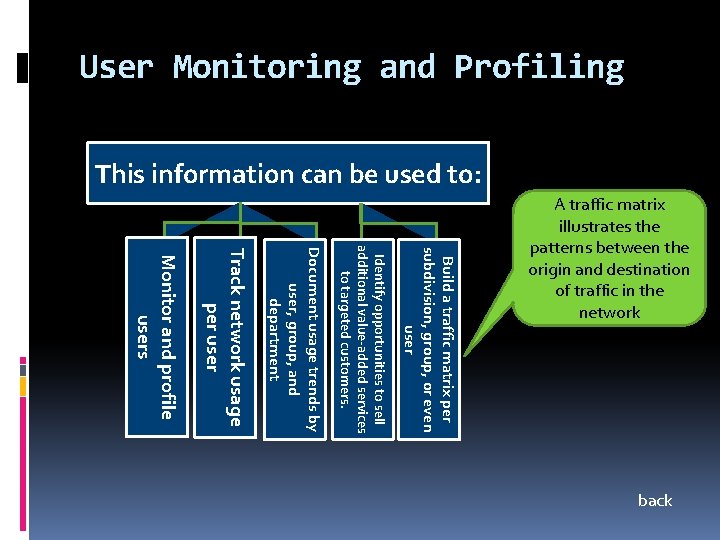
User Monitoring and Profiling This information can be used to: Monitor and profile users Track network usage per user Document usage trends by user, group, and department Identify opportunities to sell additional value-added services to targeted customers. Build a traffic matrix per subdivision, group, or even user A traffic matrix illustrates the patterns between the origin and destination of traffic in the network back

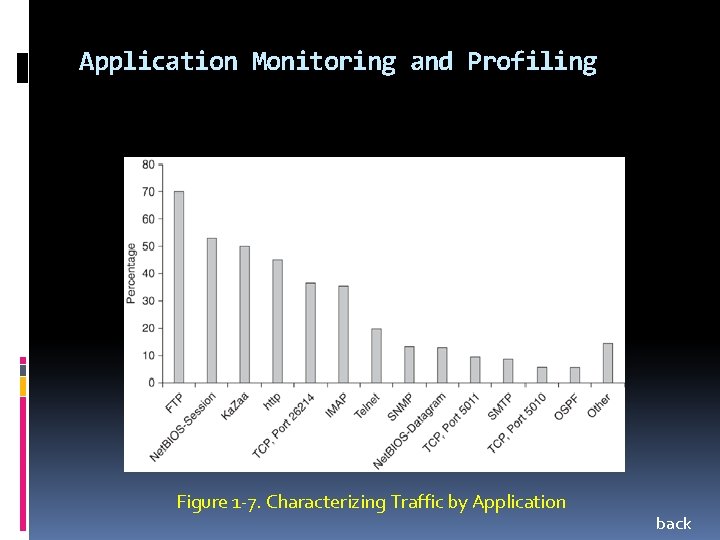
Application Monitoring and Profiling Figure 1 -7. Characterizing Traffic by Application back

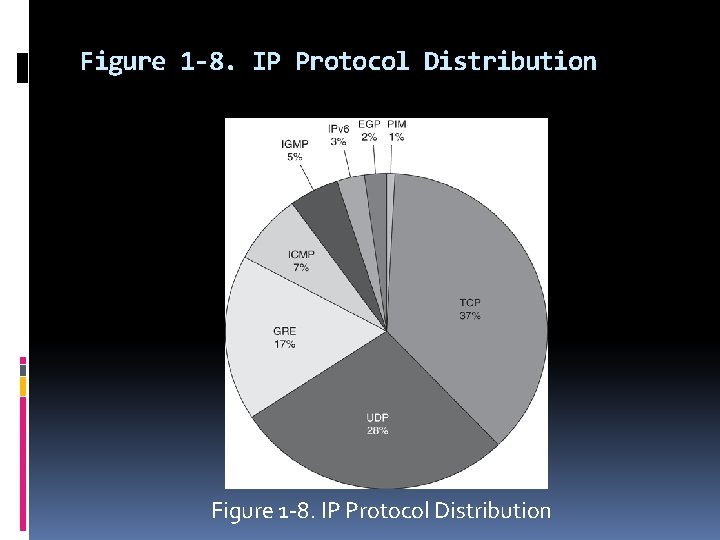
Figure 1 -8. IP Protocol Distribution

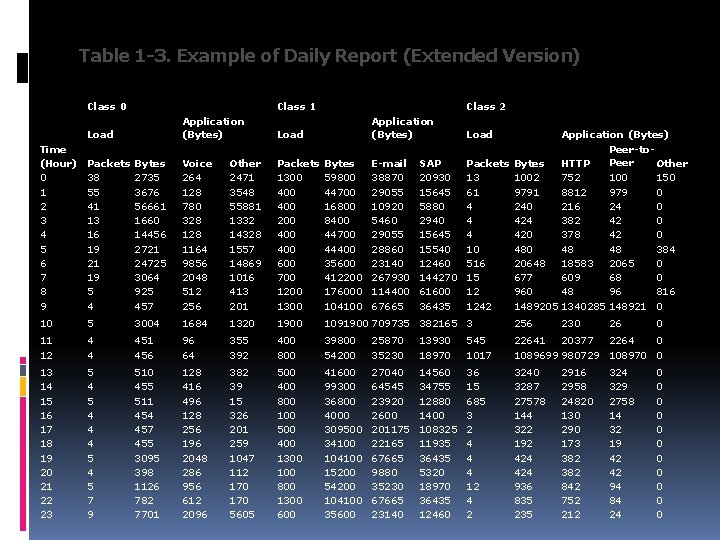
Table 1 -3. Example of Daily Report (Extended Version) Class 0 Class 1 Application (Bytes) Load Class 2 Application (Bytes) Load Time (Hour) 0 1 2 3 4 5 6 7 8 9 Packets 38 55 41 13 16 19 21 19 5 4 Bytes 2735 3676 56661 1660 14456 2721 24725 3064 925 457 Voice 264 128 780 328 1164 9856 2048 512 256 Other 2471 3548 55881 1332 14328 1557 14869 1016 413 201 Application (Bytes) Peer-to. Peer Packets Bytes E-mail SAP Packets Bytes HTTP Other 1300 59800 38870 20930 13 1002 752 100 150 400 44700 29055 15645 61 9791 8812 979 0 400 16800 10920 5880 4 240 216 24 0 200 8400 5460 2940 4 424 382 42 0 400 44700 29055 15645 4 420 378 42 0 400 44400 28860 15540 10 48 48 384 600 35600 23140 12460 516 20648 18583 2065 0 700 412200 267930 144270 15 677 609 68 0 1200 176000 114400 61600 12 960 48 96 816 1300 104100 67665 36435 1242 1489205 1340285 148921 0 10 5 3004 1684 1320 1900 1091900 709735 382165 3 256 11 12 4 4 451 456 96 64 355 392 400 800 39800 54200 25870 35230 13930 18970 545 1017 22641 20377 2264 0 1089699 980729 108970 0 13 14 15 16 17 18 19 20 21 22 23 5 4 4 4 5 7 9 510 455 511 454 457 455 3095 398 1126 782 7701 128 416 496 128 256 196 2048 286 956 612 2096 382 39 15 326 201 259 1047 112 170 5605 500 400 800 100 500 400 1300 100 800 1300 600 41600 99300 36800 4000 309500 34100 104100 15200 54200 104100 35600 27040 64545 23920 2600 201175 22165 67665 9880 35230 67665 23140 14560 34755 12880 1400 108325 11935 36435 5320 18970 36435 12460 36 15 685 3 2 4 4 4 12 4 2 3240 3287 27578 144 322 192 424 936 835 230 2916 2958 24820 130 290 173 382 842 752 212 26 324 329 2758 14 32 19 42 42 94 84 24 0 0 0

Capacity Planning A service provider might consider the following: next

ACCESS Which point of presence (Po. P) generates the most revenue? Which access points are not profitable and should be consolidated? SPARE CAPACITY POP Should there be spare capacity for premium users? SEGMENT A service provider might consider the following: Capacity Planning In which segment is the traffic decreasing? Did we lose customers to the competition? What might be the reason? next

Capacity Planning An enterprise IT department might consider the following HIGH AVAILABILITY GROW Which departments are growing the fastest? Which links will require an upgrade soon? For which department is network connectivity business-critical and therefore should have a high-availability design? back