ARM HARDWARE HACKING Twesige Richard ARM HARDWARE HACKING













- Slides: 15

ARM & HARDWARE HACKING Twesige Richard

ARM & HARDWARE HACKING � Advanced RISC Machines. � Set of instruction set architectures related to programing registers, CPU’s also I/O devices. � RISC acronym for ‘ Reduced Instruction Set Computing ‘

ARM & HARDWARE HACKING � ARM technology is prevalent in cell phones and micro-controllers. Focusing on Cell Phone technology; - Cell phones have became a big advancement in turn they have become “more trusted” than the Desktop PC/Laptop. - BIGGER the number = BIGGER targets.

ARM & HARDWARE HACKING � How many services are running? � There weaknesses have been hard to exploit. � With more Shell codes, exploitation is simple. � Shell code, is a small piece of code used as a payload in exploitation of software vulnerability.

ARM & HARDWARE HACKING � � � This shell code above can open port 4444 on a local Linux operating machine. It ties a Bourne shell to it with root privileges. It could be Sent through email.

ARM & HARDWARE HACKING � Software vulnerabilities? There has been significant improvement. - Patches. - Updates. - Bug fixes.

ARM & HARDWARE HACKING � How about the hardware? � For we know; - Links are complete when two physical layers of Transfer Control Protocol are connected. More attractive area of attack since; - There is lack of secure hardware development knowledge. - No hardware “patching. ”

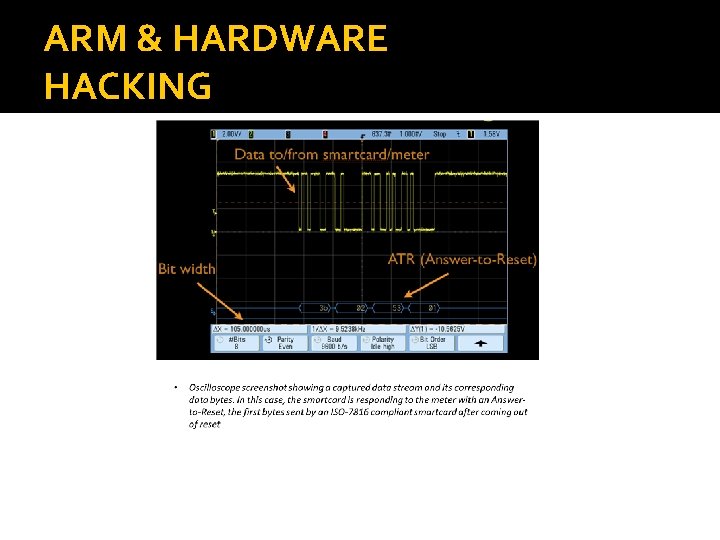
ARM & HARDWARE HACKING � The City of San Francisco contains approximately 23, 000 “smart” electronic parking meters manufactured by Mac. Kay. That boast tamper resistance, payment via smartcard, and usage auditing capabilities. � Evaluated San Francisco’s electronic parking meter implementation, was installed at a cost of $35 million. � Keep in mind these meters are ARM.

ARM & HARDWARE HACKING �Equipped with; - a stored value smartcard. These non- refillable, disposable cards can be purchased online. - A smart-card reader/writer. - Smart-card emulator.

ARM & HARDWARE HACKING

ARM & HARDWARE HACKING

ARM & HARDWARE HACKING � Now with most Cell Phones always roaming and staying connected to WIFi, there is a high chance of an attack happening right now. � With big companies like Lenovo having hardware manufactured in China; - Wouldn’t it be easy to install a 21 Century backdoor?

ARM & HARDWARE HACKING � Sometimes when your phone freezes, its not a glitch. � Caused by; - Trojan Horse in the complex circuitry. - A bug in chip code waiting to be triggered.

Conclusion � There is an easy access to tools, manufactures guide, information about a particular hardware, hobbyist who are interested in electronics. This has made ARM and hardware hacking possible. Attackers are have gained more access to the above. � I will conclude by stating that with the growing concern that an attacker control critical hardware systems such as electrical generation and traffic management systems. Hacking through real-world examples and frequently used electronic devices is a crucial thing to learn in order for us to design better products that will pave a way for even greater technology.

Works Cited � http: //arstechnica. com/gadgets/2008/05/risc-vs-cisc- mobile-era � http: //www. onlamp. com/pub/a/linux/2006/05/18/how- shellcodes-work. html � http: //www. pcworld. com/article/188632/Is_Chinese_PC_H ardware_Safe_and_Secure. html � http: //www. scientificamerican. com/article. cfm? id=the- hacker-in-your-hardware � http: //grandideastudio. com/wp- content/uploads/hacks_and_attacks_paper. pdf