Encryption and Security Outline Overview of encryption Terminology




















- Slides: 33

Encryption and Security

Outline Overview of encryption � Terminology � History � Common issues � Secret-key encryption � Block and stream ciphers � DES � RC 5 �

Overview Intro, history and terminology � Symmetric-key encryption � Techniques � DES, RC 5 � Public-key encryption � RSA, hash functions, digital signatures � Key exchange, certificates, PKI �

Overview Types of attacks and countermeasures � Application layers � S-HTTP, SSL � Steganography and digital watermarking � Security and trust �

Terminology Code � Replacement based on words or semantic structures � Cipher � Replacement based on symbols �

Terminology Cryptography � The science of encrypting or hiding secrets. � Cryptanalysis � The science of decrypting messages or breaking codes � and ciphers. Cryptology � The combination of the two. �

Terminology Plaintext – an unencrypted message � Cyphertext – an encrypted message � Security: a combination of � Authentication � Access control �

Three eras of cryptology Pre-WWII � Cryptography as a craft � Widely used, but few provable techniques � 1940 s-1970 � Secret key encryption introduced � Information theory used to characterize security � 1970 -present � Public key systems introduced �

Early cryptography Caesar cipher � Replace each letter l with l +3 mod 26 � “Attack at dawn” becomes � Dwwdfn dw gdzq � Two components: � Algorithm: Shift characters by a fixed amount � Key: the fixed amount. � Note: Knowing the algorithm (but not the key) � makes this cipher much easier to crack 26 possibilities vs 26! �

Weaknesses of the Caesar Cipher Word structure is preserved. � Break message into equal-length blocks. � dww dfn dwg dzq � Letter frequency is a big clue � e, t, a, o most common English letters. � Using a single key preserves frequency. � Solution: use multiple keys � E. g. shift by (3, 5, 7) � “Attack at dawn” becomes dya dhr dyk dbu Better, but frequency information still present. An attacker that knows the block size can separate out characters encoded with different keys. � � �

Caesar Cipher The Caesar cipher is still useful as a way to prevent � people from unintentionally reading something. ROT-13 � By decrypting, the user agrees that they want to view � the content. Fundamental problem: key length is shorter than the � message.

Vernam Cipher 1920’s: introduction of the one-time pad. � Randomly generated key � Same length as message � XORed with message � Theoretically unbreakable � Attacker can do no better than guessing � Ciphertext gives no information about plaintext. �

Vernam Cipher Example: winning lottery number is 117 � 1110101 (7 bits) � Randomly generated key: 0110101 � XOR: 1000000 � No two bits are encoded with the same � mapping – an attacker has no frequency information to help guess the key. Problem: keys are very large. � How to distribute this key? � Shared source of randomness? �

Symmetric Key Encryption The Caesar Cipher and the one-time pad are examples of symmetric-key (secret-key) encryption. Single key shared by all users. Fast How to distribute keys? � �

Keyspace The keyspace is the set of all possible keys. � Caesar cipher: keyspace = {0, 1, 2, …, 25} � Vernam cipher: |keyspace| = 2 n – 1 � Size of the keyspace helps us estimate security. � Assumption: exhaustive search is the only way to find a � key.

Substitution Ciphers Symbols are replaced by other symbols according � to a key. Caesar cipher is a substitution cipher. � To escape frequency analysis, we can use a � homophonic substitution cipher Map symbols to multiple symbols. e. g 0 -> {01, 10}, 1 ->{00, 11} 011010010 becomes: 0111001011110 Advantage: frequencies hidden Disadvantage: message and key are longer Substitution is said to add confusion Measure of the relationship between plaintext and ciphertext � � � �

Transposition Ciphers A transposition cipher is one that permutes the � symbols of the message according to a preset pattern. “Attack at dawn” becomes “cda tka wan tat” � Helps avoid detection of symbols based on � correspondence. ‘q’ followed by ‘u’. � Said to increase diffusion � Reduce redundancies in plaintext. �

Product ciphers By themselves, substitution and transposition � ciphers are relatively insecure. By combining these operations, we can produce a � secure cipher. This is how DES works. � M -> Sub(M) -> Trans(Sub(M)). � Might go through multiple rounds. �

Block Ciphers The ciphers we have seen so far are known as block ciphers. Plaintext is broken into blocks of size k. Each block is encrypted separately. Advantages: random access, potentially high security Disadvantages: larger block size needed, patterns retained throughout messages. � � �

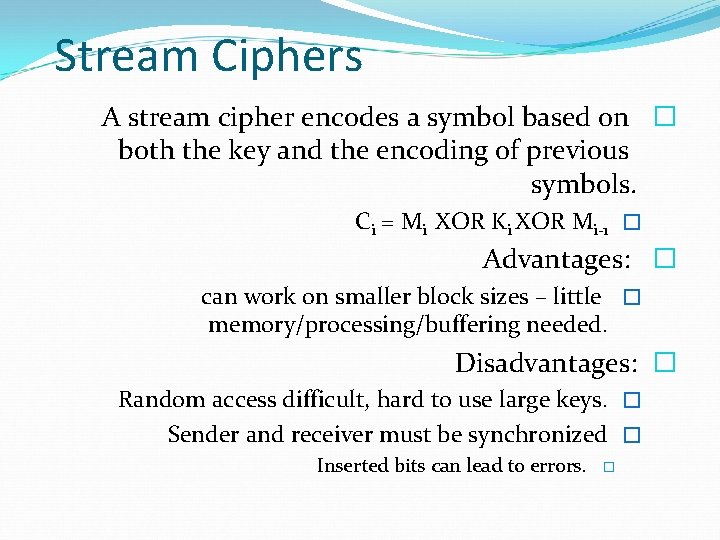
Stream Ciphers A stream cipher encodes a symbol based on � both the key and the encoding of previous symbols. Ci = Mi XOR Ki XOR Mi-1 � Advantages: � can work on smaller block sizes – little � memory/processing/buffering needed. Disadvantages: � Random access difficult, hard to use large keys. � Sender and receiver must be synchronized � Inserted bits can lead to errors. �

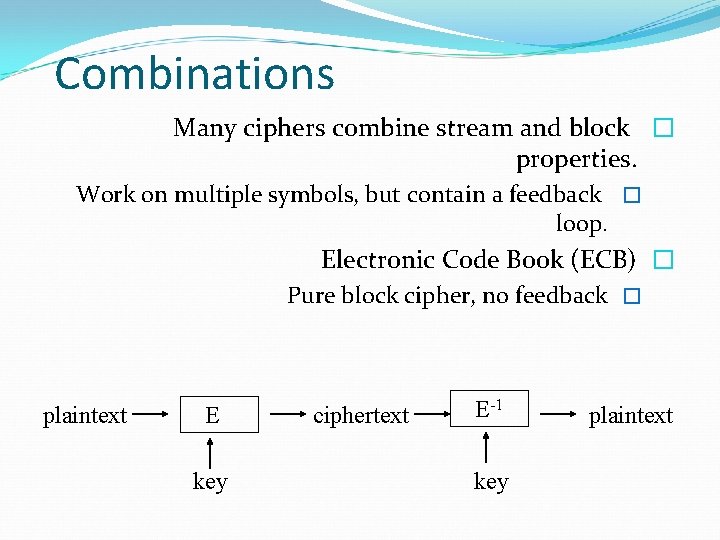
Combinations Many ciphers combine stream and block � properties. Work on multiple symbols, but contain a feedback � loop. Electronic Code Book (ECB) � Pure block cipher, no feedback � plaintext E key ciphertext E-1 key plaintext

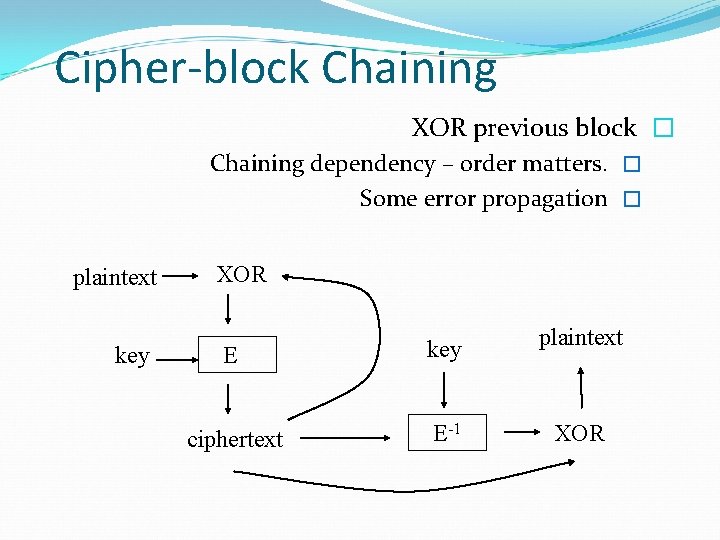
Cipher-block Chaining XOR previous block � Chaining dependency – order matters. � Some error propagation � plaintext key XOR E key plaintext ciphertext E-1 XOR

Cipher-Block Chaining Also incorporated into block ciphers. � Makes tampering easier to detect. � Helps prevent substitution and impersonation � attacks. Secret key can also be used to construct a running- � key generator. Longer sequence of pseudo-random numbers. � Can be used to build a one-time pad. �

Modifications to CBC Cipher feedback � Shift register is used to store data. � r-bit are shifted into mask of size m. � Allows a small number of bits to be immediately � sent. Output feedback � Like cipher feedback, but uses output of encryption � function. Eliminates error propagation. �

DES Data Encryption Standard � DEA is actually the algorithm. � First commercial-grade algorithm with open � implementation details. Uses a 64 -bit key with 8 parity bits, for an effective � key of 56 bits. Keyspace = 256 = 1017 �

DES Is a combination of a product cipher and a Feistel � cipher. Product cipher: transposition and substitution. � Feistel cipher: Iterates through a number of rounds � of a product cipher mapping (L, R) to (R’, L’) 16 rounds � Block size=48 � In each round, a different 48 -bit subkey is selected � from the 56 -bit key.

Security of DES Keyspace is approximately 1017 � Thought to be secure in 70’s. � Recently, 56 -bit DES broken in under 1 day. � Combination of distributed. net & EFF’s Deep. Crack. � Able to search several billion keys per second. �

Extensions to DES 3 DES � Message is run through DES 3 times C = k 3 (k 2 (k 1(M))) Backwards-compatible with DES if all three keys are the same. Keyspace is 1042 Drawback: bit-oriented operations are slow to implement in software � � �

RC 5 Symmetric encryption algorithm Word-oriented block cipher. Can vary word length, number of rounds, and key length. Goals: fast, easy to understand implement, flexible, low memory requirements, secure. Uses stream techniques to modify data � � �

RC 5 Uses three mathematical operations: � Two’s complement addition � XOR � Left cyclic rotation by variable amounts. � These are all fast operations that are directly � supported by most modern processors.

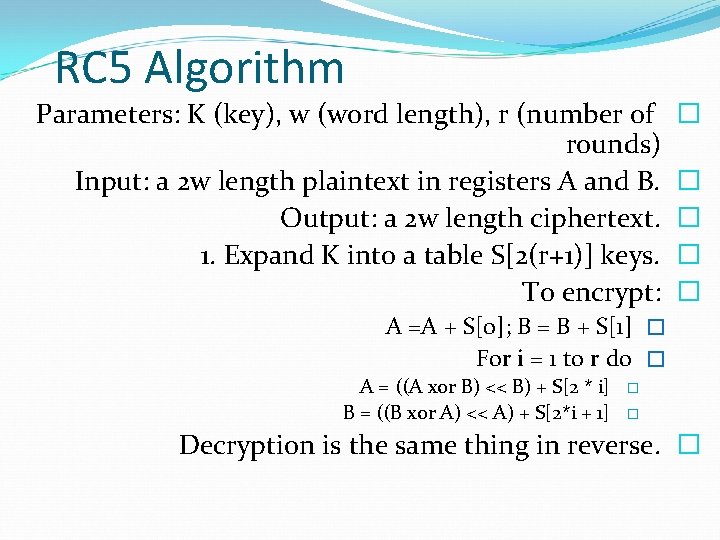
RC 5 Algorithm Parameters: K (key), w (word length), r (number of rounds) Input: a 2 w length plaintext in registers A and B. Output: a 2 w length ciphertext. 1. Expand K into a table S[2(r+1)] keys. To encrypt: � � � A =A + S[0]; B = B + S[1] � For i = 1 to r do � A = ((A xor B) << B) + S[2 * i] B = ((B xor A) << A) + S[2*i + 1] � � Decryption is the same thing in reverse. �

RC 5 Simple algorithm – key is the data-dependent � rotations. Keys are accessed sequentially, allowing for � small caches. Security still unclear, but looks good. � 56 -bit key: 250 days by distributed. net � 64 -bit key: 1747 days by distributed. net � 1. 02 x 10^11 keys/sec, 1. 5 x 10^19 keyspace � 72 -bit key in progress. � 4. 8 x 10^10 keys/sec, 4 x 10^21 keyspace 100% in 788, 747 days = 2160 years � �

Summary Secret-key algorithms (DES, RC 5) have been � widely studied. Fast Potentially highly secure Well-understood. Excellent for repeated communication. Hard to use in open environments, one-shot communications Works for hiding secrets; what about signing things? � � � Public-key encryption evolved as an answer to � this problem.