Advanced Encryption Standard Network Security 1 Advanced Encryption











- Slides: 23

Advanced Encryption Standard Network Security 1

Advanced Encryption Standard Objectives of the Topic • After completing this topic, a student will be able to – describe Advanced Encryption Standard. 2

Advanced Encryption Standard Figures and material in this topic have been • adapted from “Network Security Essentials: Applications and Standards”, 2014, by William Stallings. 3

Advanced Encryption Standard • The principal drawbacks of 3 DES: • 1. It has three times as many rounds as DEA and is correspondingly slower. • 2. Both DEA and 3 DES use a 64 -bit block size. • Its not a reasonable candidate for long term use. 4

Advanced Encryption Standard • In 1997 NIST issued a call for proposals for a new AES: • 1. Should have a security strength equal to or better than 3 DES and significantly improved efficiency. 5

Advanced Encryption Standard • 2. Must be a symmetric block cipher with a block length of 128 bits and support for key lengths of 128, 192, and 256 bits. 6

Advanced Encryption Standard • 3. Evaluation criteria included security, computational efficiency, memory requirements, hardware and software suitability, and flexibility 7

Advanced Encryption Standard • NIST selected Rijndael as the proposed AES algorithm • Developers were two cryptographers from Belgium: Dr. Joan Daemen and Dr. Vincent Rijmen • published as a final standard (FIPS PUB 197) in 2001. 8

Advanced Encryption Standard • AES uses a block length of 128 bits and a key length that can be 128, 192, or 256 bits. • For our discussion, we assume 128 bits in this topic. 9

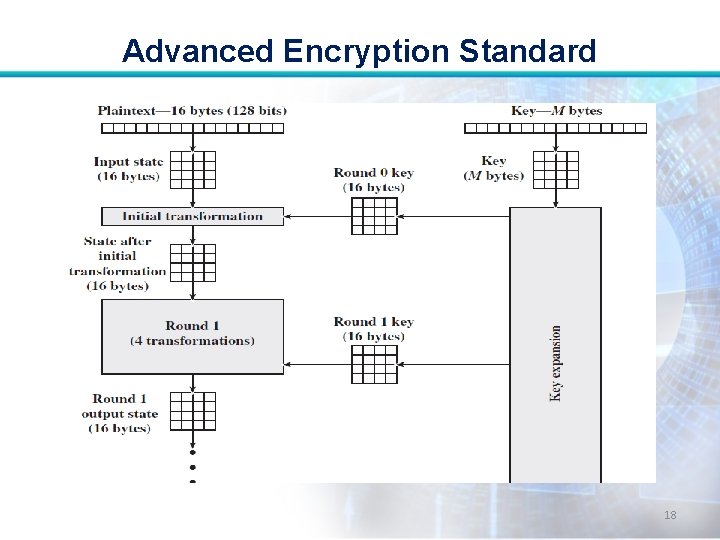
Advanced Encryption Standard • The input to the encryption and decryption algorithms is a single 128 -bit block. • In FIPS PUB 197, this block is depicted as a square matrix of bytes. 10

Advanced Encryption Standard • The block is copied into the State array, which is modified at each stage of encryption or decryption. • After the final stage, State is copied to an output matrix. 11

Advanced Encryption Standard • Similarly, the 128 -bit key is depicted as a square matrix of bytes. • This key is then expanded into an array of key schedule words: Each word is four bytes and total key schedule is 44 words for 128 -bit key. 12

Advanced Encryption Standard • Ordering of bytes in a matrix is by column. • First four bytes of a 128 -bit plaintext input to the encryption cipher occupy the first column of the in matrix, the second four bytes occupy the second column, and so on. 13

Advanced Encryption Standard • Similarly, the first four bytes of the expanded key, which form a word, occupy the first column of the w matrix. 14

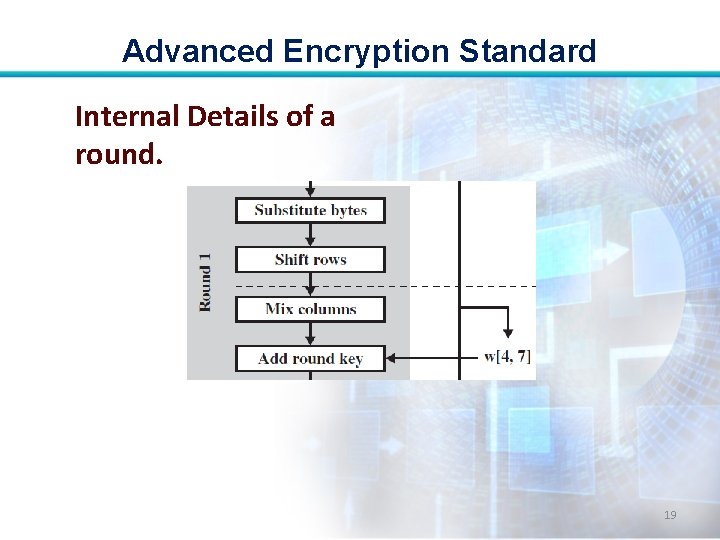
Advanced Encryption Standard AES’s Working: • Four different stages are used, one of permutation and three of substitution 15

Advanced Encryption Standard • Substitute bytes: Uses a table, referred to as an S-box, to perform a byte-bybyte substitution of the block. • Shift rows: A simple permutation that is performed row by row. 16

Advanced Encryption Standard • Mix columns: A substitution that alters each byte in a column as a function of all of the bytes in the column. • Add round key: A simple bitwise XOR of the current block with a portion of the expanded key. 17

Advanced Encryption Standard 18

Advanced Encryption Standard Internal Details of a round. 19

Advanced Encryption Standard 20

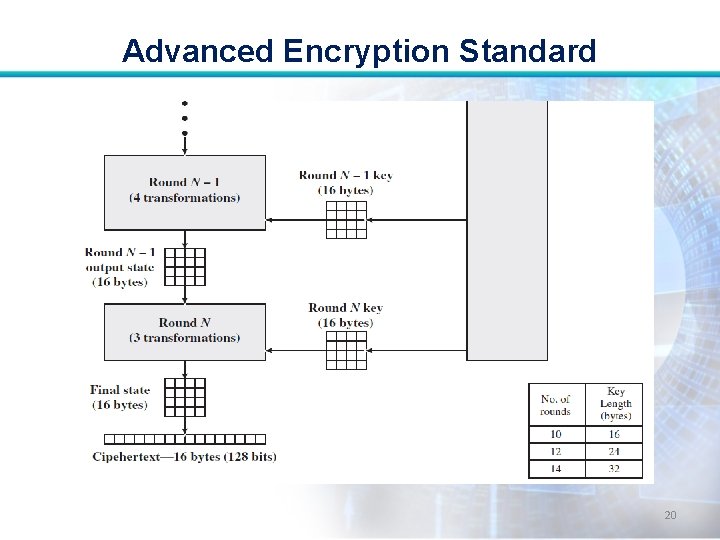
Advanced Encryption Standard Some comments: • AES structure is not a Feistel structure. • For both encryption and decryption, the cipher begins with an Add Round Key stage, followed by nine rounds that each includes all four stages 21

Advanced Encryption Standard • Each stage is easily reversible. • The final round of both encryption and decryption consists of only three stages. • The decryption algorithm is not identical to the encryption algorithm. 22

Advanced Encryption Standard • The decryption algorithm makes use of the expanded key in reverse order. End 23