Lect 7 Data Encryption Standard 1 Data Encryption



- Slides: 17

Lect. 7 : Data Encryption Standard 1

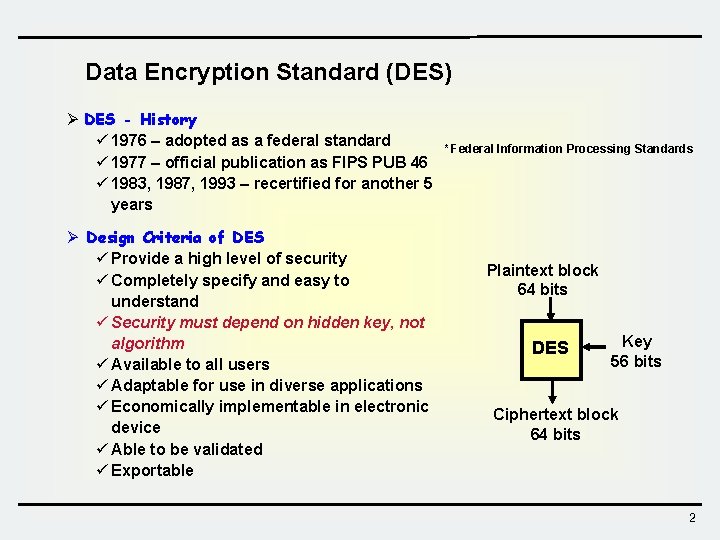
Data Encryption Standard (DES) Ø DES - History ü 1976 – adopted as a federal standard ü 1977 – official publication as FIPS PUB 46 ü 1983, 1987, 1993 – recertified for another 5 years Ø Design Criteria of DES ü Provide a high level of security ü Completely specify and easy to understand ü Security must depend on hidden key, not algorithm ü Available to all users ü Adaptable for use in diverse applications ü Economically implementable in electronic device ü Able to be validated ü Exportable * Federal Information Processing Standards Plaintext block 64 bits DES Key 56 bits Ciphertext block 64 bits 2

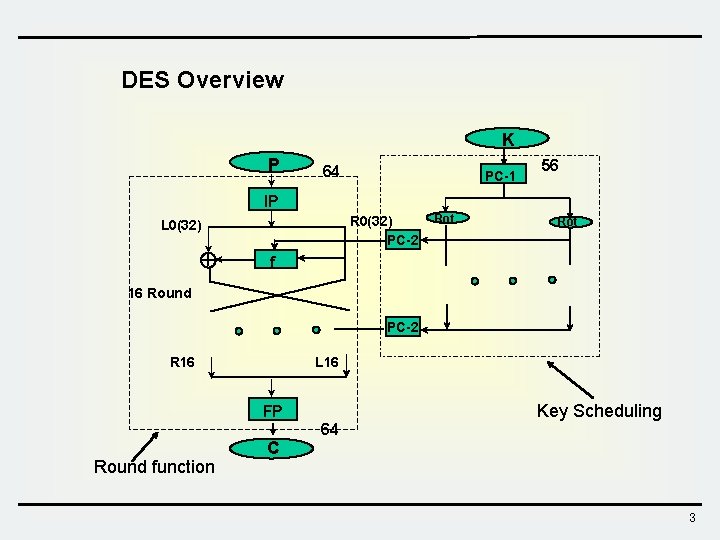
DES Overview K P 64 PC-1 56 IP R 0(32) PC-2 L 0(32) Rot f 16 Round PC-2 R 16 L 16 FP 64 Round function Key Scheduling C 3

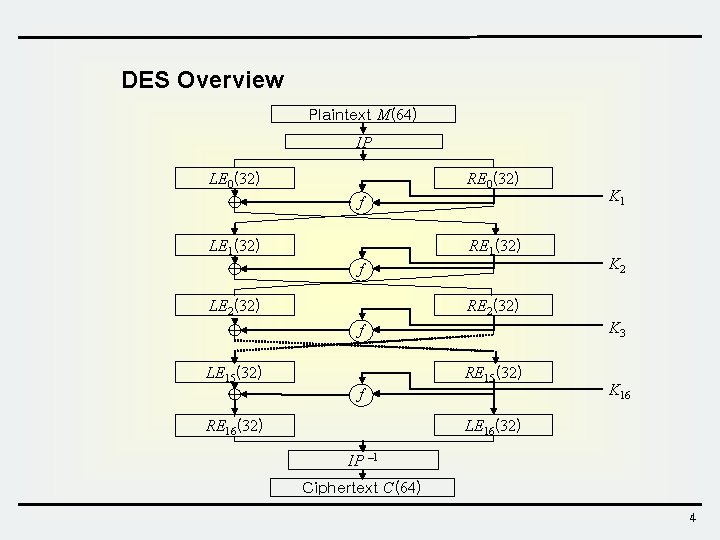
DES Overview Plaintext M(64) IP LE 0(32) RE 0(32) f LE 1(32) RE 1(32) f LE 2(32) K 1 K 2 RE 2(32) K 3 f LE 15(32) RE 15(32) f K 16 LE 16(32) RE 16(32) IP – 1 Ciphertext C(64) 4

Initial Permutation and Final Permutation IP – 1 (Final permutation) IP (Initial permutation) 58 50 42 34 26 18 10 2 40 8 48 16 56 24 64 32 60 52 44 36 28 20 12 4 39 7 47 15 55 23 63 31 62 54 46 38 30 22 14 6 38 6 46 14 54 22 62 30 64 56 48 40 32 24 16 8 37 5 45 13 53 21 61 29 57 49 41 33 25 17 9 1 36 4 44 12 52 20 60 28 59 51 43 35 27 19 11 3 35 3 43 11 51 19 59 27 61 53 45 37 29 21 13 5 34 2 42 10 50 18 58 26 63 55 47 39 31 23 15 7 33 1 41 9 49 17 57 25 cf. ) The 58 th bit of x is the first bit of IP(x) 5

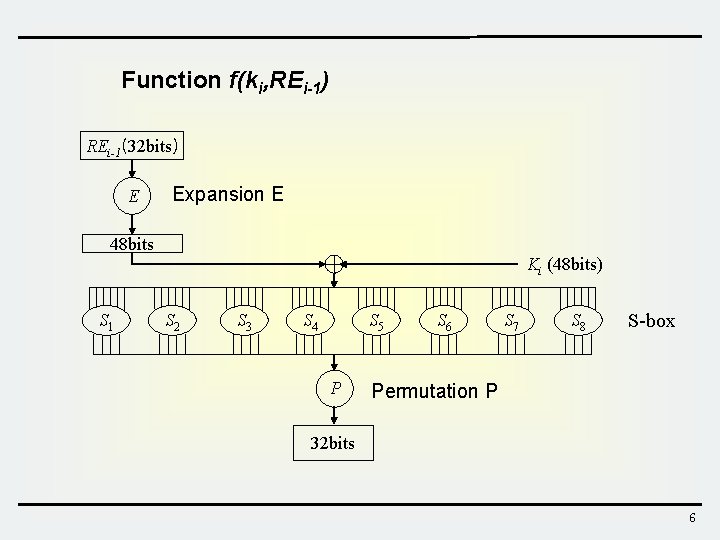
Function f(ki, REi-1) REi-1(32 bits) E Expansion E 48 bits Ki (48 bits) S 1 S 2 S 3 S 4 S 5 P S 6 S 7 S 8 S-box Permutation P 32 bits 6

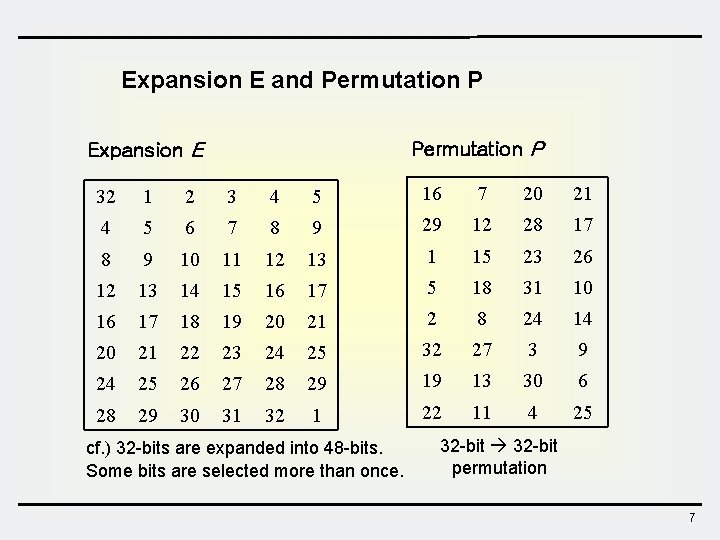
Expansion E and Permutation P Expansion E 32 1 2 3 4 5 16 7 20 21 4 5 6 7 8 9 29 12 28 17 8 9 10 11 12 13 1 15 23 26 12 13 14 15 16 17 5 18 31 10 16 17 18 19 20 21 2 8 24 14 20 21 22 23 24 25 32 27 3 9 24 25 26 27 28 29 19 13 30 6 28 29 30 31 32 1 22 11 4 25 cf. ) 32 -bits are expanded into 48 -bits. Some bits are selected more than once. 32 -bit permutation 7

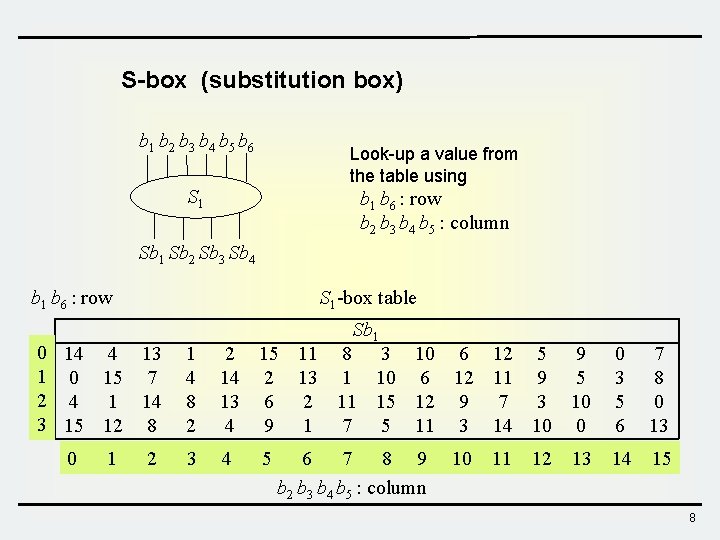
S-box (substitution box) b 1 b 2 b 3 b 4 b 5 b 6 Look-up a value from the table using S 1 b 6 : row b 2 b 3 b 4 b 5 : column Sb 1 Sb 2 Sb 3 Sb 4 S 1 -box table b 1 b 6 : row 0 14 4 13 1 0 15 7 2 4 1 14 3 15 12 8 0 1 2 Sb 1 1 4 8 2 2 15 11 8 3 10 6 12 5 9 14 2 13 1 10 6 12 11 9 5 13 6 2 11 15 12 9 7 3 10 4 9 1 7 5 11 3 14 10 0 0 3 5 6 7 8 0 13 3 4 14 15 5 6 7 8 9 b 2 b 3 b 4 b 5 : column 10 11 12 13 8

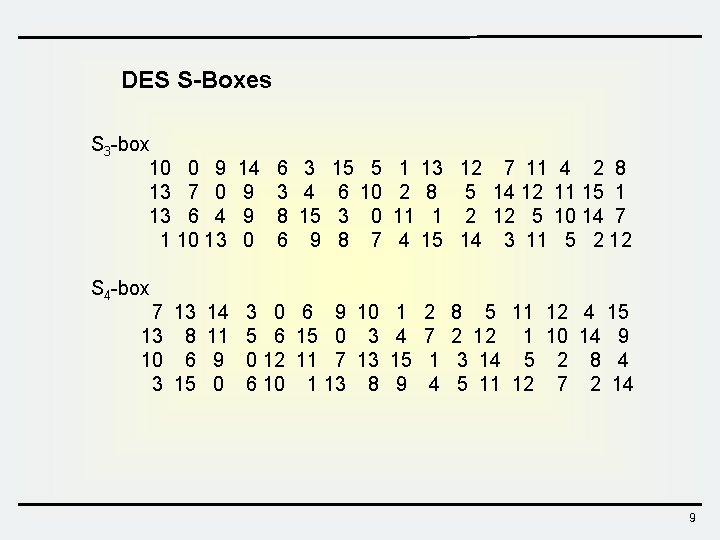
DES S-Boxes S 3 -box 10 0 9 13 7 0 13 6 4 1 10 13 S 4 -box 14 9 9 0 6 3 3 4 8 15 6 9 15 5 6 10 3 0 8 7 1 13 12 7 11 4 2 8 5 14 12 11 15 1 11 1 2 12 5 10 14 7 4 15 14 3 11 5 2 12 7 13 14 3 0 6 9 10 1 13 8 11 5 6 15 0 3 4 10 6 9 0 12 11 7 13 15 0 6 10 1 13 8 9 2 7 1 4 8 5 11 12 4 15 2 12 1 10 14 9 3 14 5 2 8 4 5 11 12 7 2 14 9

DES S-boxes Ø 8 S-boxes (6 4 bits) Øsome known design criteria ünot linear üAny one bit of the inputs changes at least two output bits üS(x) and S(x 001100) differs at least 2 bits üS(x) S(x 11 ef 00) for any ef üResistance against DC etc. üThe actual design principles have never been revealed (US classified information) HW : For the S 4 -box, check whether the following property holds üS 4 (x) and S 4 (x 001100) differs at least 2 bits 10

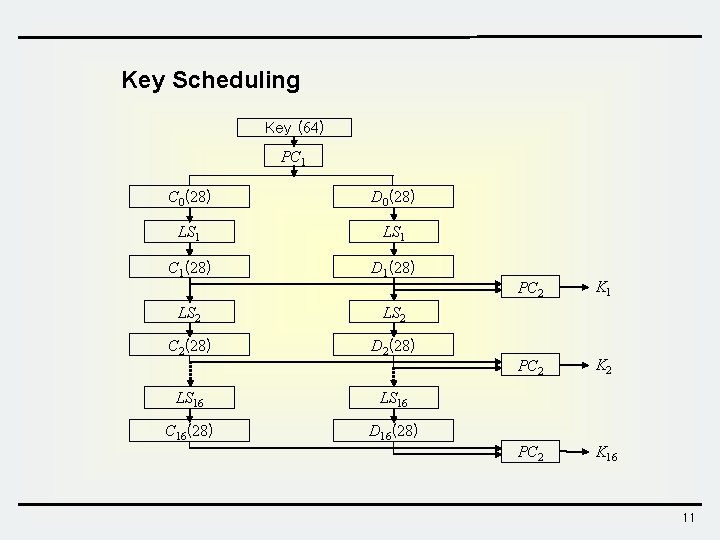
Key Scheduling Key (64) PC 1 C 0(28) D 0(28) LS 1 C 1(28) D 1(28) LS 2 C 2(28) D 2(28) LS 16 C 16(28) D 16(28) PC 2 K 1 PC 2 K 2 PC 2 K 16 11

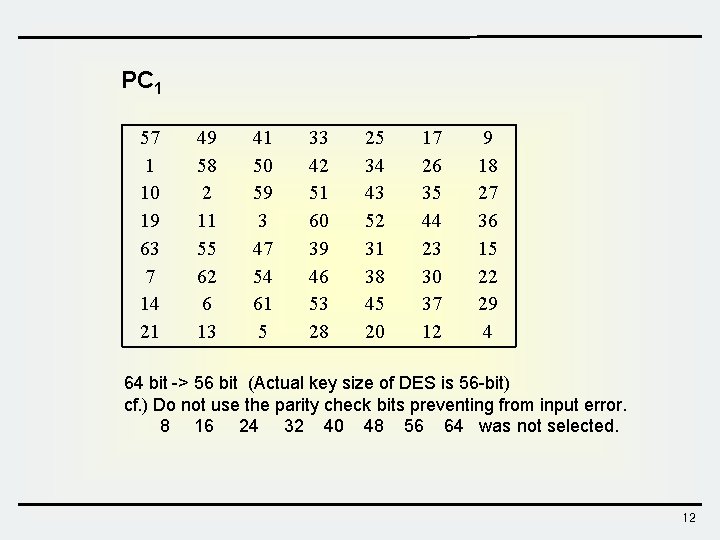
PC 1 57 1 10 19 63 7 14 21 49 58 2 11 55 62 6 13 41 50 59 3 47 54 61 5 33 42 51 60 39 46 53 28 25 34 43 52 31 38 45 20 17 26 35 44 23 30 37 12 9 18 27 36 15 22 29 4 64 bit -> 56 bit (Actual key size of DES is 56 -bit) cf. ) Do not use the parity check bits preventing from input error. 8 16 24 32 40 48 56 64 was not selected. 12

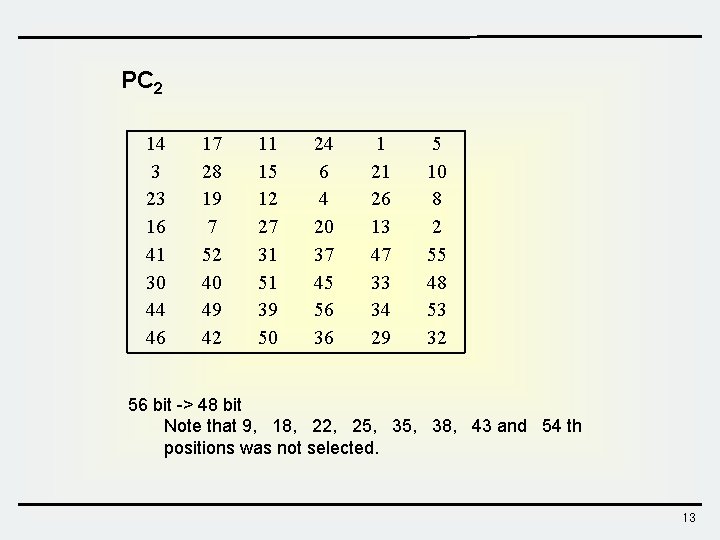
PC 2 14 3 23 16 41 30 44 46 17 28 19 7 52 40 49 42 11 15 12 27 31 51 39 50 24 6 4 20 37 45 56 36 1 21 26 13 47 33 34 29 5 10 8 2 55 48 53 32 56 bit -> 48 bit Note that 9, 18, 22, 25, 38, 43 and 54 th positions was not selected. 13

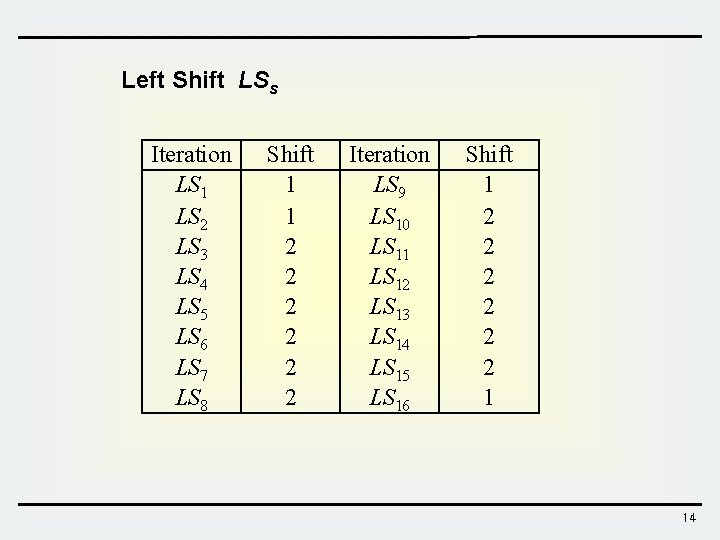
Left Shift LSs Iteration LS 1 LS 2 LS 3 LS 4 LS 5 LS 6 LS 7 LS 8 Shift 1 1 2 2 2 Iteration LS 9 LS 10 LS 11 LS 12 LS 13 LS 14 LS 15 LS 16 Shift 1 2 2 2 1 14

Breaking DES(1/2) Ø DES - Controversies ü Unknown design criteria ü Slow in software ü Too short key size – 56 bits Ø DES Crack Machine ü Can test over 90 billion keys per second ü EFF's "Deep Crack" and the Distributed. Net computers were testing 245 billion keys per second ü On Jan. 19, 1999, RSA DES-III Challenge was deciphered after searching 22 h. and 15 m. Identifier: DES-Challenge-III http: //www. rsa. com/rsalabs/node. asp? id=2108 Cipher: DES Start: January 18, 1999 9: 00 AM PST Prize: $10, 000 IV: da 4 b be f 1 6 b 6 e 98 3 d Plaintext: See you in Rome (second AES Conference, March 22 -23, 1999) 15

Breaking DES(2/2) 250, 000$@1998 10, 000$@2008

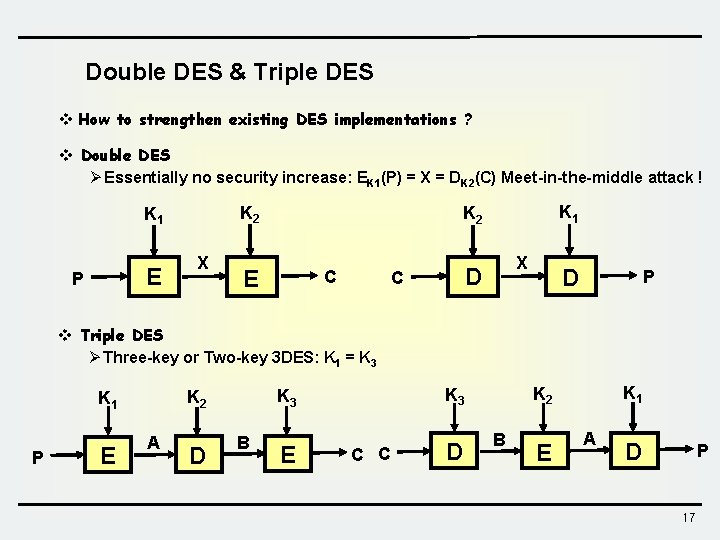
Double DES & Triple DES v How to strengthen existing DES implementations ? v Double DES Ø Essentially no security increase: EK 1(P) = X = DK 2(C) Meet-in-the-middle attack ! K 2 K 1 E P X K 1 K 2 E C X D C D P v Triple DES Ø Three-key or Two-key 3 DES: K 1 = K 3 P E A D B E C C D K 1 K 2 K 3 K 2 K 1 B E A D P 17