An Interface and Algorithms for Authenticated Encryption RFC





- Slides: 16

An Interface and Algorithms for Authenticated Encryption (RFC 5116) David Mc. Grew mcgrew@cisco. com

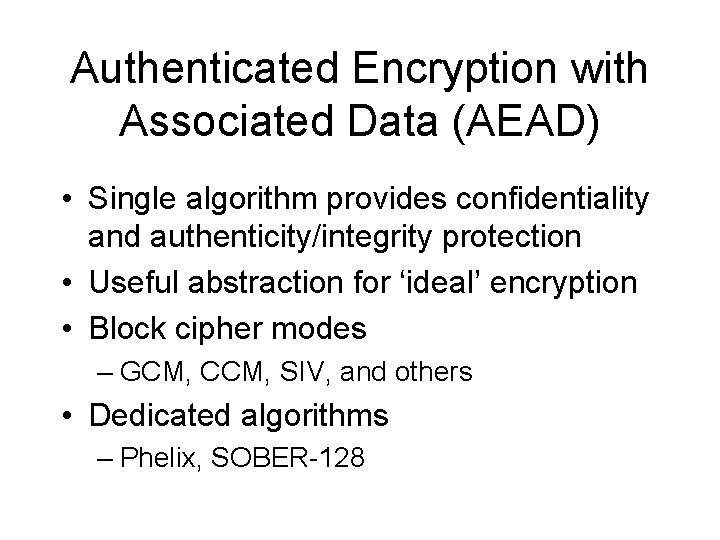
Authenticated Encryption with Associated Data (AEAD) • Single algorithm provides confidentiality and authenticity/integrity protection • Useful abstraction for ‘ideal’ encryption • Block cipher modes – GCM, CCM, SIV, and others • Dedicated algorithms – Phelix, SOBER-128

RFC 5116 • Defines interface to AEAD algorithms • Defines four algorithms – AES GCM, AES CCM • Defines IANA registry for algorithms

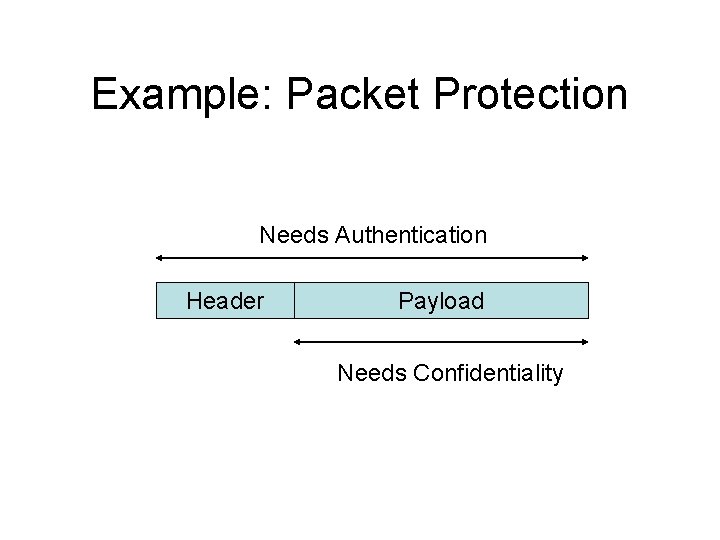
Example: Packet Protection Needs Authentication Header Payload Needs Confidentiality

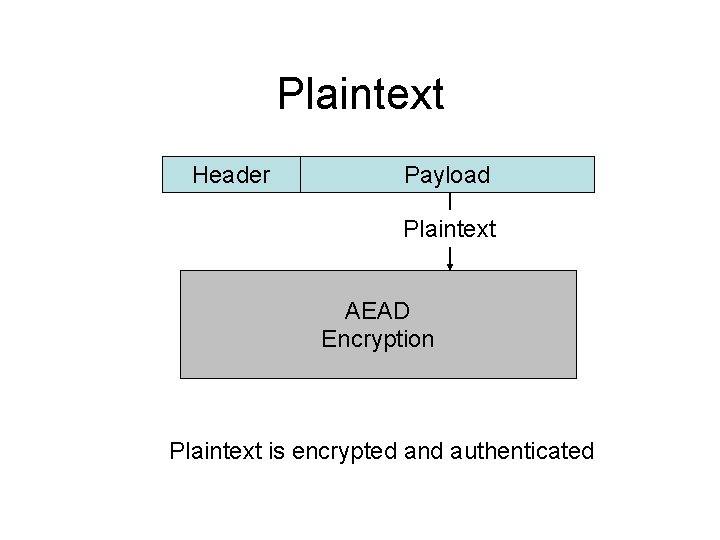
Plaintext Header Payload Plaintext AEAD Encryption Plaintext is encrypted and authenticated

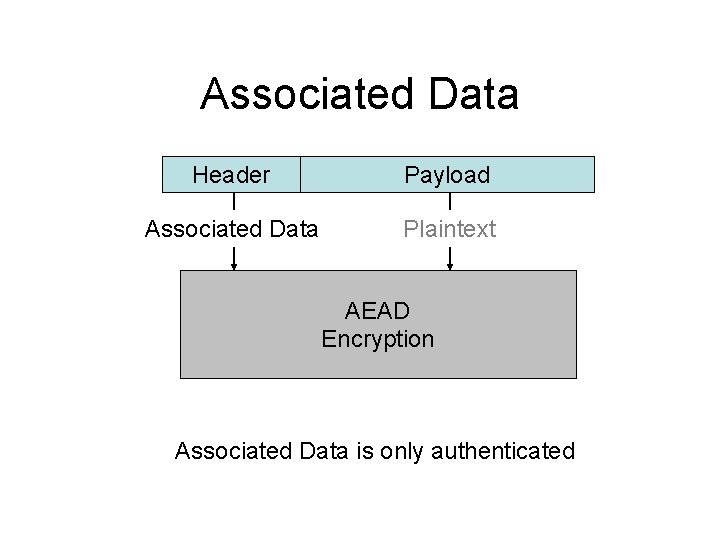
Associated Data Header Payload Associated Data Plaintext AEAD Encryption Associated Data is only authenticated

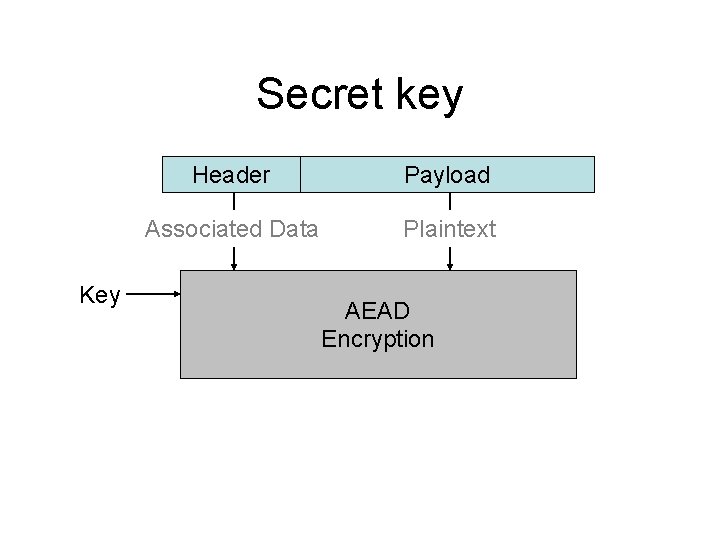
Secret key Key Header Payload Associated Data Plaintext AEAD Encryption

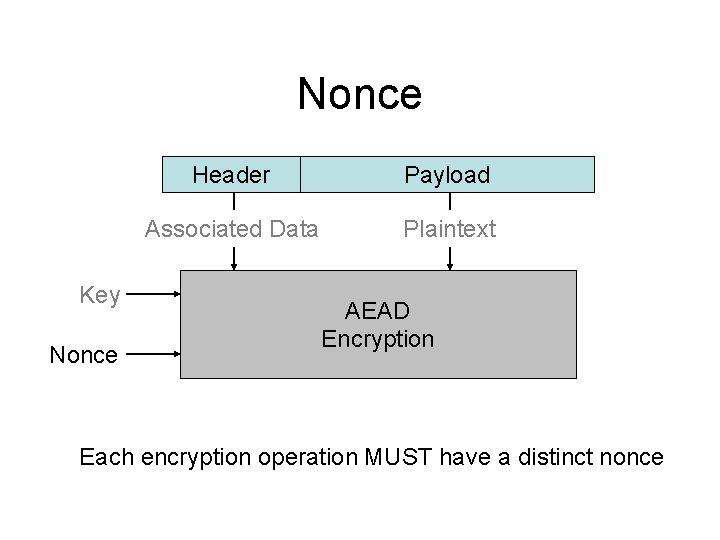
Nonce Key Nonce Header Payload Associated Data Plaintext AEAD Encryption Each encryption operation MUST have a distinct nonce

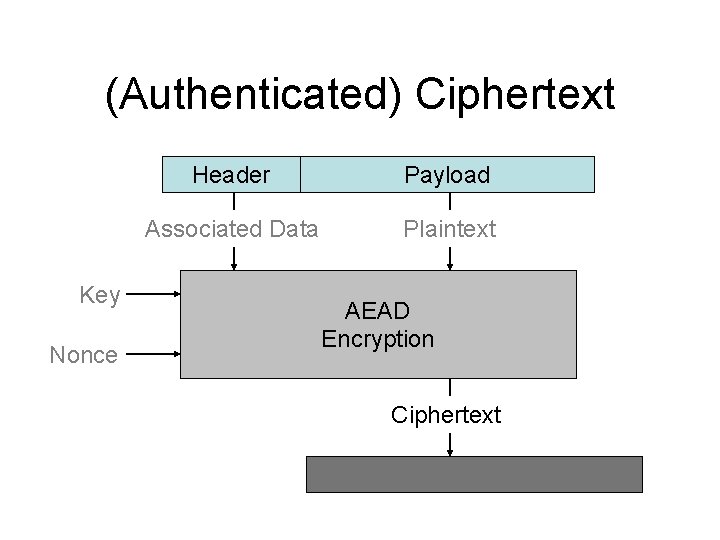
(Authenticated) Ciphertext Key Nonce Header Payload Associated Data Plaintext AEAD Encryption Ciphertext

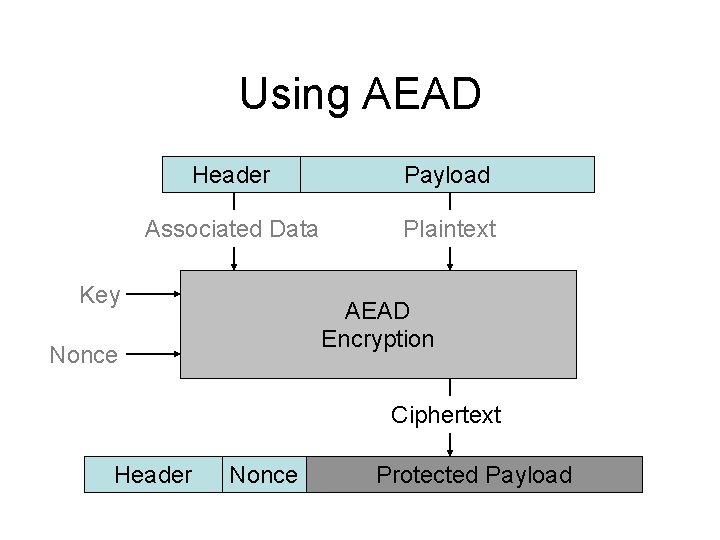
Using AEAD Header Payload Associated Data Plaintext Key AEAD Encryption Nonce Ciphertext Header Nonce Protected Payload

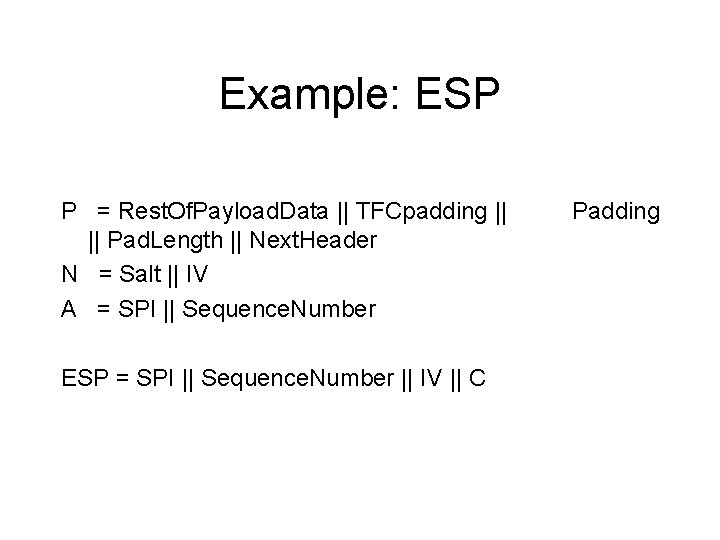
Example: ESP P = Rest. Of. Payload. Data || TFCpadding || || Pad. Length || Next. Header N = Salt || IV A = SPI || Sequence. Number ESP = SPI || Sequence. Number || IV || C Padding

AEAD Benefits • Interface hides algorithm details from application • Application designer relieved of crypto issues • Promotes algorithm agility • Admits crypto optimizations • Simplifies analysis and testing

RFC 5116 Uses • ESP – Backwards compatible with RFC 4106 • TLS – ecc-new-mac, rsa-aes-gcm • IKE – draft-black-ikev 2 -aead-modes • SRTP, SSH work underway • 802. 1 AE

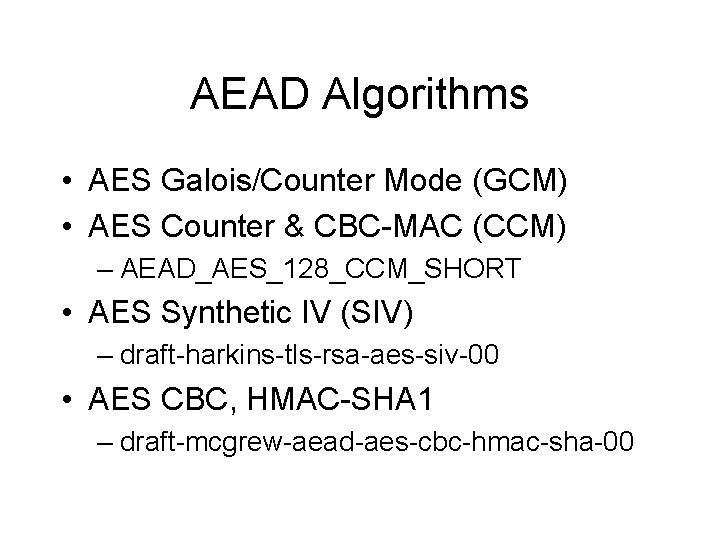
AEAD Algorithms • AES Galois/Counter Mode (GCM) • AES Counter & CBC-MAC (CCM) – AEAD_AES_128_CCM_SHORT • AES Synthetic IV (SIV) – draft-harkins-tls-rsa-aes-siv-00 • AES CBC, HMAC-SHA 1 – draft-mcgrew-aead-aes-cbc-hmac-sha-00

Issues & Future Work • Nonces aren’t user friendly – Security and usability • No nonceless algorithms in registry yet

Acknowledgements • Thanks are due to: Hal Finney, Greg Rose, Russ Housley, Alfred Hines, John Wilkinson, Jack Lloyd, Scott Fluhrer, David Wagner, Ken Raeburn, Wei Dai, Aaron Christensen, Phil Rogaway, and Dan Harkins • IRTF CFRG participants