Lect 8 Advanced Encryption Standard http csrc nist




- Slides: 13

Lect. 8 : Advanced Encryption Standard http: //csrc. nist. gov/Crypto. Toolkit/aes/rijndael/ 1

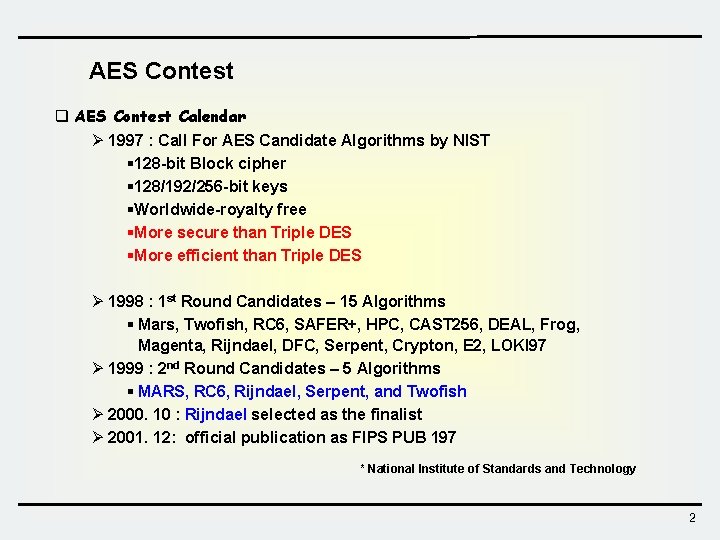
AES Contest q AES Contest Calendar Ø 1997 : Call For AES Candidate Algorithms by NIST § 128 -bit Block cipher § 128/192/256 -bit keys §Worldwide-royalty free §More secure than Triple DES §More efficient than Triple DES Ø 1998 : 1 st Round Candidates – 15 Algorithms § Mars, Twofish, RC 6, SAFER+, HPC, CAST 256, DEAL, Frog, Magenta, Rijndael, DFC, Serpent, Crypton, E 2, LOKI 97 Ø 1999 : 2 nd Round Candidates – 5 Algorithms § MARS, RC 6, Rijndael, Serpent, and Twofish Ø 2000. 10 : Rijndael selected as the finalist Ø 2001. 12: official publication as FIPS PUB 197 * National Institute of Standards and Technology 2

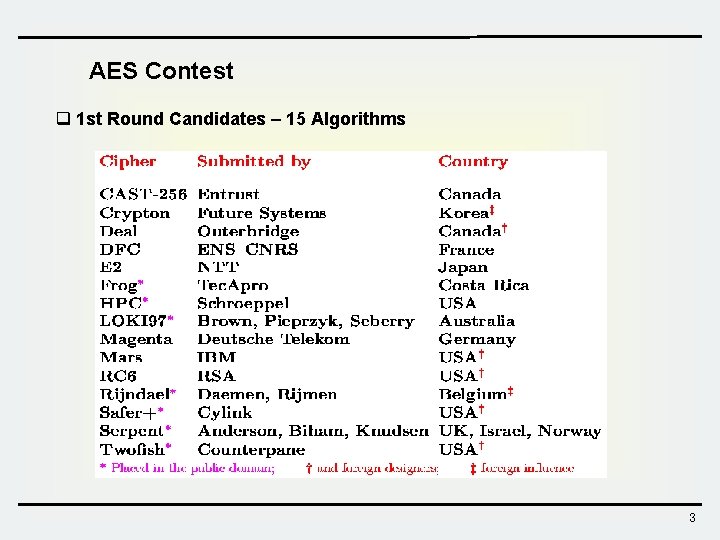
AES Contest q 1 st Round Candidates – 15 Algorithms 3

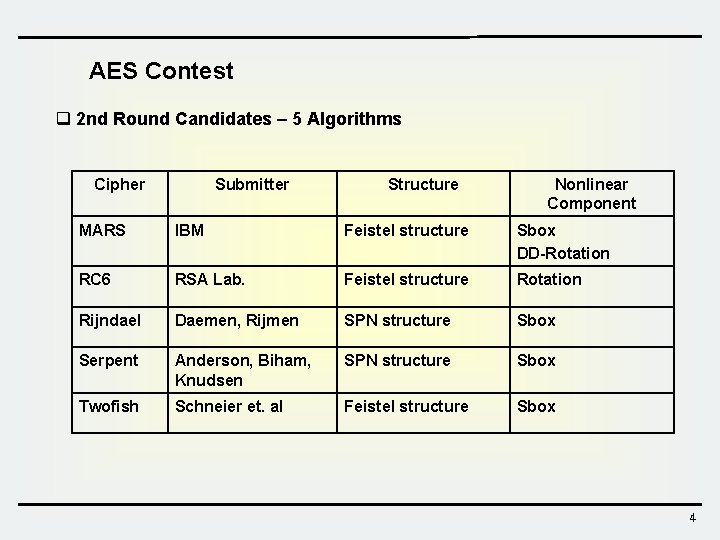
AES Contest q 2 nd Round Candidates – 5 Algorithms Cipher Submitter Structure Nonlinear Component MARS IBM Feistel structure Sbox DD-Rotation RC 6 RSA Lab. Feistel structure Rotation Rijndael Daemen, Rijmen SPN structure Sbox Serpent Anderson, Biham, Knudsen SPN structure Sbox Twofish Schneier et. al Feistel structure Sbox 4

AES Contest q AES Contest Ø 2000. 10 : Rijndael selected as the finalist Ø 2001. 12: official publication as FIPS PUB 197 Joan Daemen and Vincent Rijmen, “The Design of Rijndael, AES – The Advanced Encryption Standard”, Springer, 2002, ISBN 3 -540 -42580 -2 Vincent Rijmen 5

SPN- Structure Block Cipher Ø More constraints on the round function: must be invertible Ø Relatively new architecture than Feistel-structure Ø Faster than Feistelstructure Ø Parallel computation Ø Typically E D 6

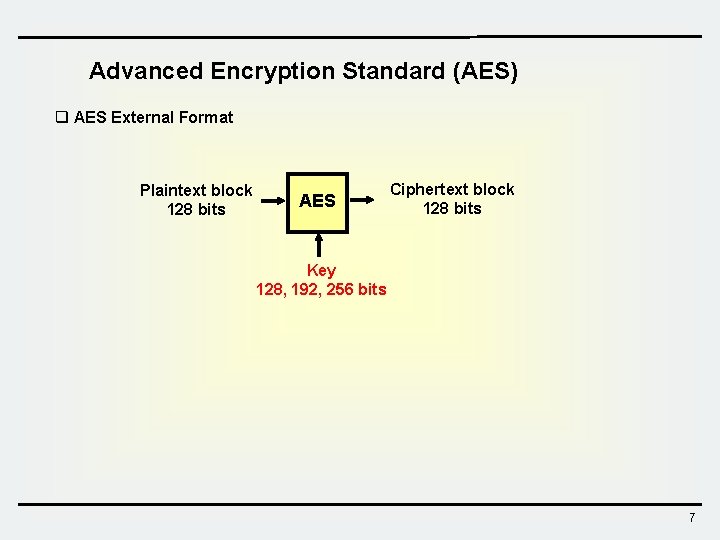
Advanced Encryption Standard (AES) q AES External Format Plaintext block 128 bits AES Ciphertext block 128 bits Key 128, 192, 256 bits 7

AES Architecture • SPN-type block cipher • Block size = 128 bits • Key size / No. round – 128 bits 10 rounds – 192 bits 12 rounds – 256 bits 14 rounds • Round transformation – Sub. Bytes – Shift. Row – Mix. Column – Add. Round. Key Initial Key Plaintext Add. Round. Key Sub. Byte Shift. Row Mix. Column Round key Repeat N-1 rounds Add. Round. Key Sub. Byte Shift. Row Final round key Final round Add. Round. Key Ciphertext 8

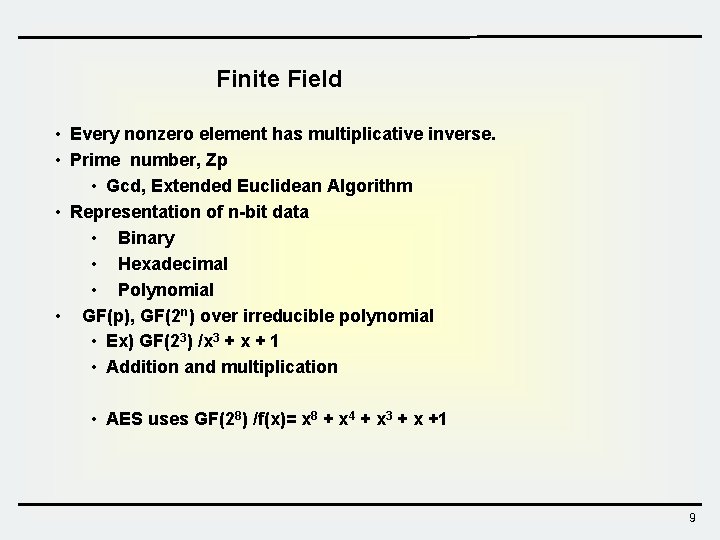
Finite Field • Every nonzero element has multiplicative inverse. • Prime number, Zp • Gcd, Extended Euclidean Algorithm • Representation of n-bit data • Binary • Hexadecimal • Polynomial • GF(p), GF(2 n) over irreducible polynomial • Ex) GF(23) /x 3 + x + 1 • Addition and multiplication • AES uses GF(28) /f(x)= x 8 + x 4 + x 3 + x +1 9

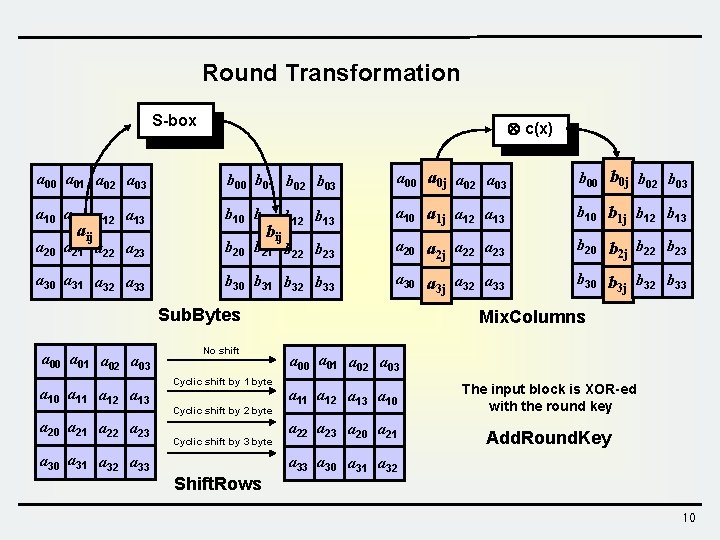
Round Transformation S-box c(x) a 00 a 01 a 02 a 03 b 00 b 01 b 02 b 03 a 00 a 0 j a 02 a 03 b 00 b 0 j b 02 b 03 a 10 a 11 a 12 a 13 b 10 b 11 b 12 b 13 a 10 a 1 j a 12 a 13 b 10 b 1 j b 12 b 13 a 20 a 21 a 22 a 23 b 20 b 21 b 22 b 23 a 20 a a 22 a 23 2 j b 20 b b 22 b 23 2 j a 30 a 31 a 32 a 33 b 30 b 31 b 32 b 33 a 30 a a 32 a 33 3 j b 30 b b 32 b 33 3 j aij bij Sub. Bytes a 00 a 01 a 02 a 03 a 10 a 11 a 12 a 13 a 20 a 21 a 22 a 23 No shift Cyclic shift by 1 byte Cyclic shift by 2 byte Cyclic shift by 3 byte a 30 a 31 a 32 a 33 Shift. Rows Mix. Columns a 00 a 01 a 02 a 03 a 11 a 12 a 13 a 10 a 22 a 23 a 20 a 21 The input block is XOR-ed with the round key Add. Round. Key a 33 a 30 a 31 a 32 10

Add. Round. Key v The input block is XOR-ed with the round key 11

Best Known Attack • related-key attack can break 256 -bit AES with a complexity of 2119, which is faster than brute force but is still infeasible. 192 -bit AES can also be defeated in a similar manner, but at a complexity of 2176. 128 -bit AES is not affected by this attack. • chosen-plaintext attack can break 8 rounds of 192 - and 256 -bit AES, and 7 rounds of 128 -bit AES, although the workload is impractical at 2128 - 2119. (Ferguson et al. , 2000). 12

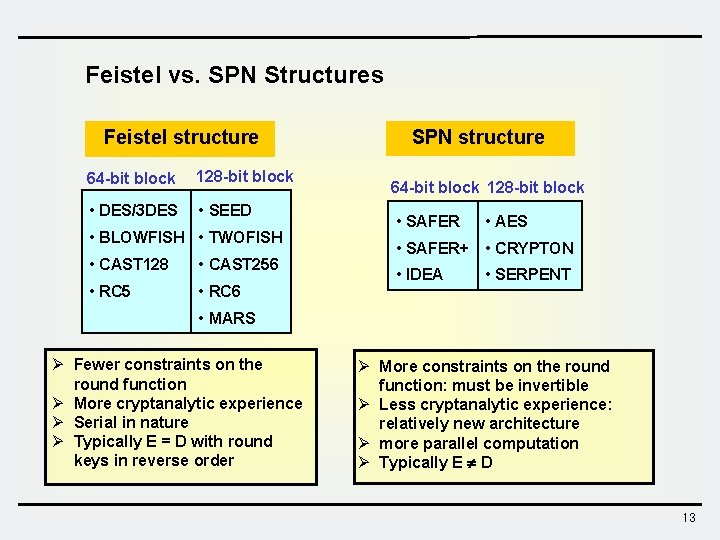
Feistel vs. SPN Structures Feistel structure 64 -bit block 128 -bit block • DES/3 DES • SEED • BLOWFISH • TWOFISH • CAST 128 • CAST 256 • RC 5 • RC 6 SPN structure 64 -bit block 128 -bit block • SAFER • AES • SAFER+ • CRYPTON • IDEA • SERPENT • MARS Ø Fewer constraints on the round function Ø More cryptanalytic experience Ø Serial in nature Ø Typically E = D with round keys in reverse order Ø More constraints on the round function: must be invertible Ø Less cryptanalytic experience: relatively new architecture Ø more parallel computation Ø Typically E D 13