Security Aspects SECURITY ASPECTS Three Security Aspects Encryption


















- Slides: 32

Security Aspects

SECURITY ASPECTS • Three Security Aspects…. – Encryption – Digital Signature – Certification Authorities q. Verifying the Person q. Ensuring the Sender & Receiver q. Obtaining Evidence, Date&Time P. J BALALKUMARAN, AP, COMM CA, SNMV

Encryption • In cryptography, encryption is the process of encoding a message or information in such a way that only authorized parties can access it and those who are not authorized cannot. • Encode & Decode P. J BALALKUMARAN, AP, COMM CA, SNMV

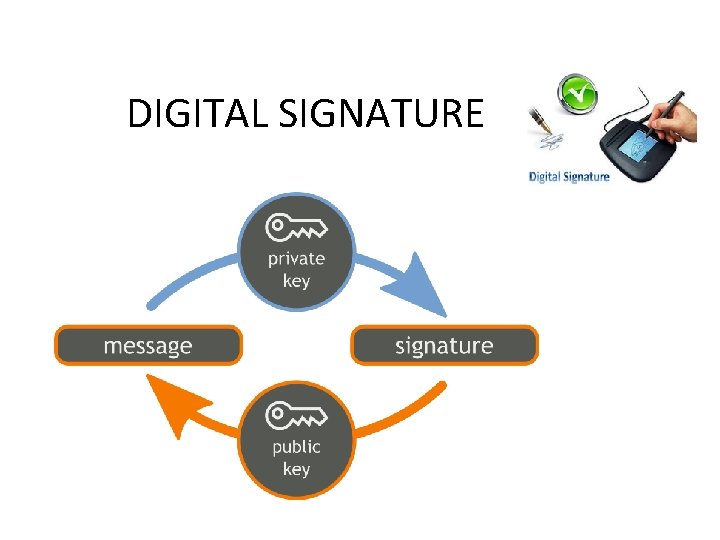
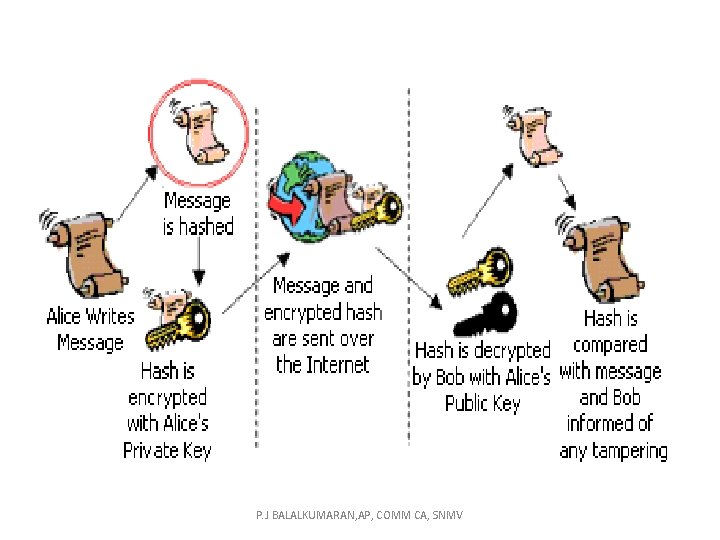
Digital Signature • E- Doc Transaction • Sender & Receiver Authentication • Electronic data that carries the intent of a signature. • Examples include Electronic Mail, Contract P. J BALALKUMARAN, AP, COMM CA, SNMV

P. J BALALKUMARAN, AP, COMM CA, SNMV

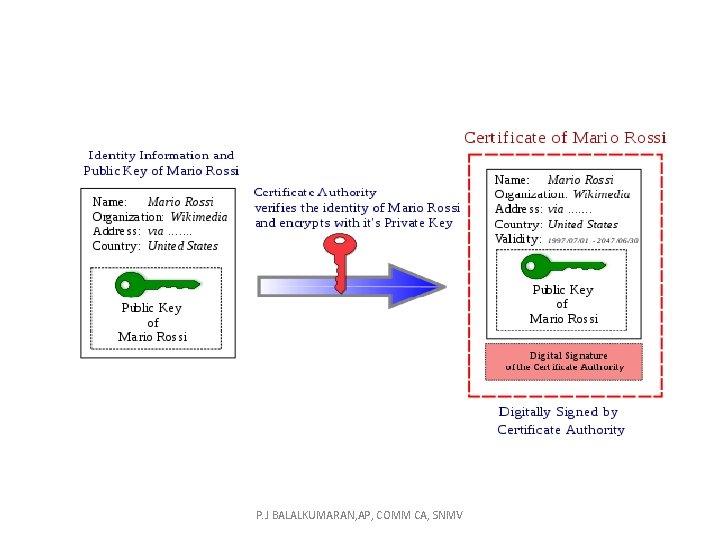
CERTIFICATION AUTHORITIES • Electronic Documents • Public-key cryptography can be used to encrypt data communicated between two parties. • This can typically happen when a user logs on to any site that implements the HTTP Secure protocol. P. J BALALKUMARAN, AP, COMM CA, SNMV

P. J BALALKUMARAN, AP, COMM CA, SNMV

TECHNICAL ASPECTS

Encryption • Encryption- kryptos. Greek Word • Hidden- Secret • Starts from 1900 BC, Egyptian Scribe – Hidden Message • Romans- Caesar Shift Cipher Text P. J BALALKUMARAN, AP, COMM CA, SNMV

Example • Plain: ABCDEFGHIJKLMNOPQRSTUVWXYZ Cipher: XYZABCDEFGHIJKLMNOPQRSTUVW Plain text: THE QUICK BROWN FOX JUMPS OVER THE LAZY DOG Cipher text: QEB NRFZH YOLTK CLU GRJMP LSBO QEB IXWV ALD P. J BALALKUMARAN, AP, COMM CA, SNMV

Middle Stage • Polyalphabetic Technique 1940 s – A polyalphabetic cipher is any cipher based on substitution, using multiple substitution alphabets. • World War II- German P. J BALALKUMARAN, AP, COMM CA, SNMV

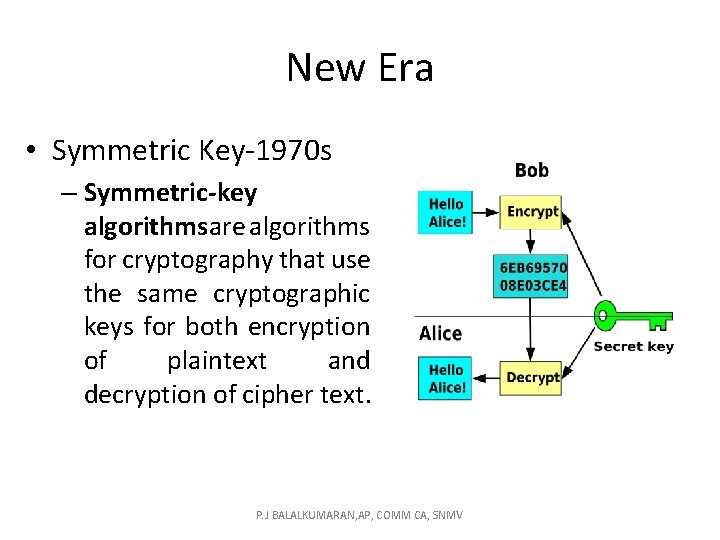
New Era • Symmetric Key-1970 s – Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of cipher text. P. J BALALKUMARAN, AP, COMM CA, SNMV

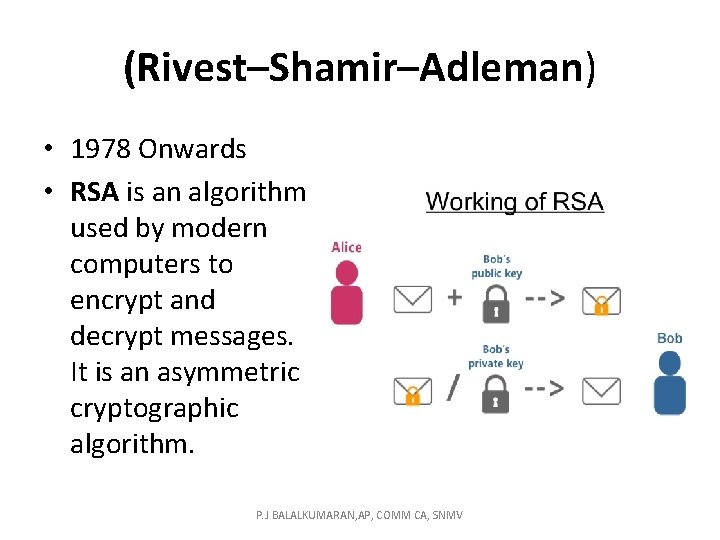
(Rivest–Shamir–Adleman) • 1978 Onwards • RSA is an algorithm used by modern computers to encrypt and decrypt messages. It is an asymmetric cryptographic algorithm. P. J BALALKUMARAN, AP, COMM CA, SNMV

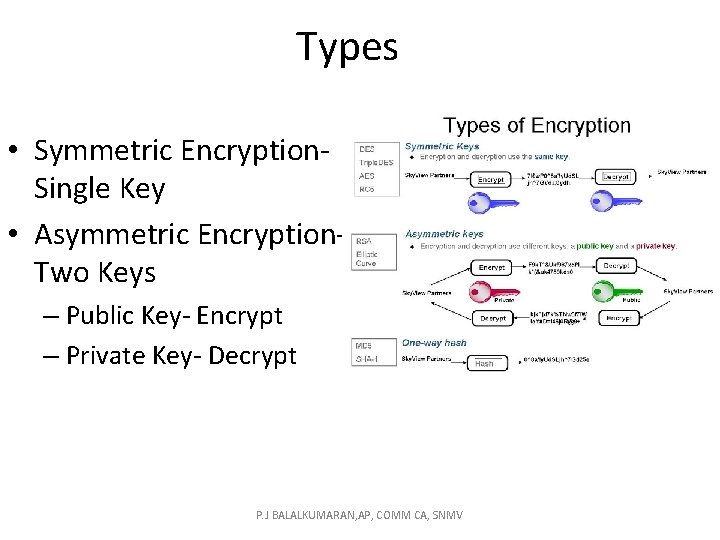
Types • Symmetric Encryption. Single Key • Asymmetric Encryption. Two Keys – Public Key- Encrypt – Private Key- Decrypt P. J BALALKUMARAN, AP, COMM CA, SNMV

Uses • • Authentication Validation • Fingerprint Digital signatures Data protection • Email protection Secure Sockets Layers • Virtual Sockets Networks Encryption Small/Home Office Users Encryption and Viruses Daniel Service Attacks P. J BALALKUMARAN, AP, COMM CA, SNMV

DIGITAL SIGNATURE

P. J BALALKUMARAN, AP, COMM CA, SNMV

P. J BALALKUMARAN, AP, COMM CA, SNMV

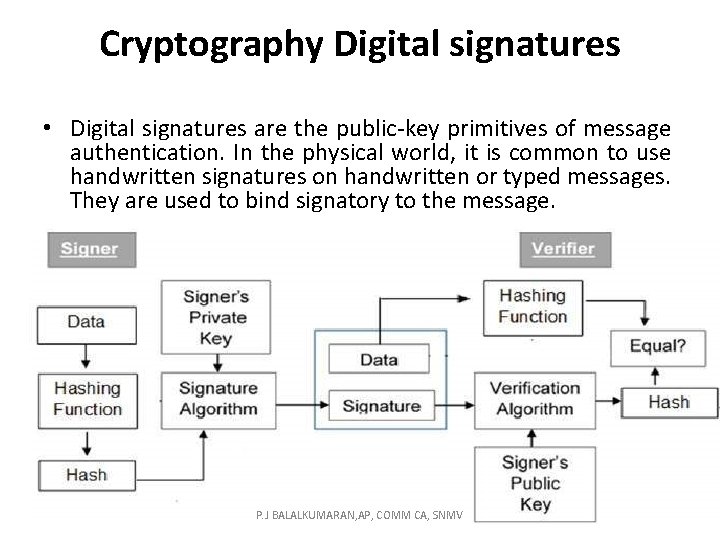
Cryptography Digital signatures • Digital signatures are the public-key primitives of message authentication. In the physical world, it is common to use handwritten signatures on handwritten or typed messages. They are used to bind signatory to the message. P. J BALALKUMARAN, AP, COMM CA, SNMV

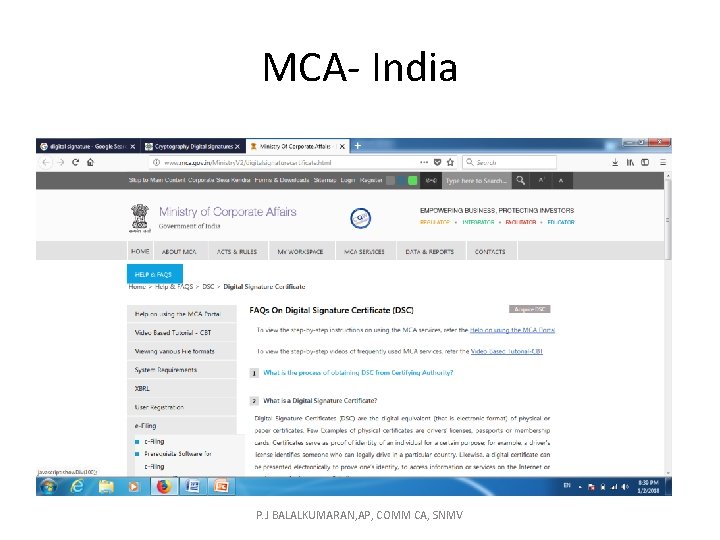
MCA- India P. J BALALKUMARAN, AP, COMM CA, SNMV

Applications • • • Authentication Integrity Non- repudiation Security Precautions Smart Card reader Trusted application P. J BALALKUMARAN, AP, COMM CA, SNMV

DATA SECURITY

• Data security refers to protective digital privacy measures that are applied to prevent unauthorized access to computers, databases and websites. • Data security means protecting digital data, such as those in a database. – cyberattack or a data breach. P. J BALALKUMARAN, AP, COMM CA, SNMV

Indiscriminate attacks • These attacks are wide-ranging, global and do not seem to discriminate among governments and companies. – Operation Shady RAT – World of Hell – Red October, discovered in 2012, diplomatic secrets to personal information, including from mobile devices. – Wanna. Cry ransomware attack on 12 May 2017 affecting hundreds of thousands of computers in more than 150 countries. – 2017 Petya cyberattack P. J BALALKUMARAN, AP, COMM CA, SNMV

Destructive attacks – Great Hacker War, and purported "gang war" in cyberspace – Lulz. Raft, hacker group known for a low impact attack in Canada – Operation Ababil, conducted against American financial institutions – TV 5 Monde April 2015 cyberattack – Vulcanbot – Shamoon, a modular computer virus, was used in 2012 in an attack on 30, 000 Saudi Aramco workstations, causing the company to spend a week restoring their services. – Wiper – in December 2011, the malware successfully erased information on hard disks at the Oil Ministry's headquarters. – Stuxnet - A malicious computer worm believed to be a jointly built American-Israeli cyber weapon. Designed to sabotage Iran's nuclear program with what would seem like a long series of unfortunate accidents. P. J BALALKUMARAN, AP, COMM CA, SNMV

Cyberwarfare • 2007 cyberattacks on Estonia, wide-ranging attack targeting government and commercial institutions • 2010 cyberattacks on Burma, related to the 2010 Burmese general election • 2010 Japan–South Korea cyberwarfare • 2013 Singapore cyberattacks, attack by Anonymous "in response to web censorship regulations in the country, specifically on news outlets" • #Op. Israel, a broad "anti-Israel" attack • Cyberattacks during the Russo-Georgian War • July 2009 cyberattacks, against South Korea and the United States • Operation Olympic Games, against Iranian nuclear facilities, allegedly conducted by the United States P. J BALALKUMARAN, AP, COMM CA, SNMV

Government espionage • • • extract a wealth of sensitive data from 2008 cyberattack on United States, cyber thousands of machines located mostly in the espionage targeting U. S. military computers Middle East. Cyber attack during the Paris G 20 Summit, targeting G 20 -related documents including • Office of Personnel Management data breach—Dec 2014 breach of data on U. S. financial information government employees Ghost. Net • A six-month-long cyberattack on the Moonlight Maze German parliament for which the Sofacy Operation Newscaster, cyber espionage Group is suspected took place in December covert operation allegedly conducted by 2014. Iran is also suspected to be behind a Operation Cleaver, cyberwarfare covert • Vestige spearphishing attack in August 2016 on operation allegedly conducted by Iran members of the Bundestag and multiple Shadow Network, attacks on India by China political parties such as Linken-faction leader Sahra Wagenknecht, Junge Union Titan Rain, targeting defense contractors in and the CDU of Saarland. Authorities fear the United States that sensitive information could be gathered Google – in 2009, the Chinese hackers by hackers to later manipulate the public breached Google's corporate servers gained ahead of elections such as Germany's next access to a database containing classified federal election due in September 2017. information about suspected spies, agents, and terrorists under surveillance by the US government. [7] Gauss trojan, discovered in 2012 is a statesponsored computer espionage operation BALALKUMARAN, AP, COMM CA, SNMV that uses state-of-the-art P. J software to

Corporate espionage • Operation Aurora • Operation Socialist, UK obtaining information from Belgian telecom company on call information • Sony Pictures Entertainment hack P. J BALALKUMARAN, AP, COMM CA, SNMV

Stolen e-mail addresses and login credentials • 2011 Play. Station Network outage, • 2011 attack resulting in stolen credentials and incidentally causing network disruption • Vestige – in 2010, a band of anonymous hackers has rooted the servers of the site and leaked half a gigabyte's worth of its • private data. • IEEE – in September 2012, it exposed user names, plaintext passwords, and website activity • for almost 100, 000 of its members. • Living. Social – in 2014, the company suffered a security breach that has exposed names, e -mail addresses and password data for up to 50 million of its users. Adobe – in 2013, Hackers obtained access to Adobe's networks and stole user information and downloaded the source code for some of Adobe programs. It attacked 150 million customers. Rock. You – in 2009, the company experienced a data breach resulting in the exposure of over 32 million user accounts. Yahoo! – in 2012, hackers posted login credentials for more than 453, 000 user accounts. Again in January 2013 and in January 2014 P. J BALALKUMARAN, AP, COMM CA, SNMV

Stolen credit card and financial data • 2017 Equifax data breach- In Bank, ICICI, YES Bank and Axis 2017, Equifax Inc. announced Bank were among the worst hit. that a cyber-security breach • 2014 JPMorgan Chase data occurred between May to mid breach, allegedly conducted by July of that year. Cyber a group of Russian hackers criminals had accessed • Goodwill Industries – in approximately 145. 5 million September 2014, the company U. S. Equifax consumers' suffered from a credit card personal data, including their data breach that affected the full names, Social Security charitable retailer's stores in at numbers, credit card least 21 states. Another two information, birth dates, retailers were affected. addresses, and, in some cases, driver license numbers. • 2016 Indian Banks data breach - It was estimated 3. 2 million debit cards were compromised. Major Indian banks- SBI, HDFC P. J BALALKUMARAN, AP, COMM CA, SNMV

• Home Depot – in September breach, affecting up to 10 2014, the cybercriminals that million credit cards. compromised Home Depot's • Subway – in 2012, two network and installed malware Romanian men admitted to on the home-supply company's participating in an international point-of-sale systems likely stole conspiracy that hacked into information on 56 million credit-card payment terminals payment cards. at more than 150 Subway • Star. Dust – in 2013, the botnet restaurant franchises and stole compromised 20, 000 cards in data for more than 146, 000 active campaign hitting US accounts. merchants. • Master. Card – in 2005, the • Target – in 2013, approximately company announced that up to 40 million credit and debit card 40 million cardholders may have accounts were impacted in a had account information stolen credit card breach. According to due to one of its payment another estimate, it processors being hacked. compromised as many as 110 million Target customers. • VISA and Master. Card – in 2012, they warned card-issuing banks that a third-party payments processor suffered P. Ja BALALKUMARAN, AP, security COMM CA, SNMV

Stolen medical-related data • By May, three healthcare payer organizations had been attacked in the United States in 2014 and 2015: Anthem, Premera Blue Cross and Care. First. The three attacks together netted information on more than 91 million people. P. J BALALKUMARAN, AP, COMM CA, SNMV