Conventional Cryptography Classical Encryption Techniques Topics Introduction to






























- Slides: 72

Conventional Cryptography Classical Encryption Techniques

Topics • • • Introduction to Cryptography Encryption / Decryption Basic Terminologies Cryptography Types Classical Cryptographic Techniques Stenography Mono-alphabetic & Poly-alphabetic Caesar Cipher Transposition Cipher OTPs Rotor Machines

Encryption / Decryption • The process of disguising a message (plaintext) into an unintelligible form (ciphertext) by an encryption algorithm and a secret variable, called a key • The process of transforming ciphertext back into plaintext using the encryption algorithm and a key

Cryptography • Cryptography is the study of secret (crypto-) writing (-graphy) concerned with developing algorithms which may be used to: – Conceal the context of some message from all except the sender and recipient (privacy or secrecy), and/or – Verify the correctness of a message to the recipient (authentication or integrity) • Basis of many technological solutions to computer and communications security problems. • Cryptography may be part of a security solution, but it is never the whole solution. At best, it transforms a more general security problem into a key management problem.

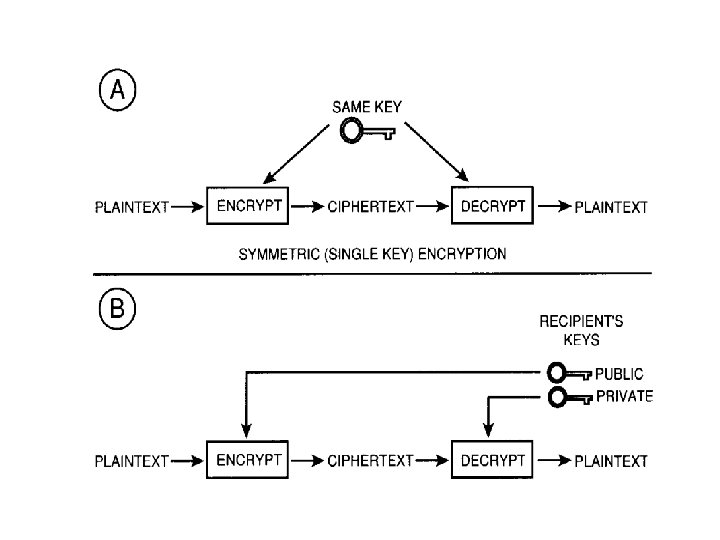
Crypto Systems Classification • Two requirements for secure use of symmetric encryption: – a strong encryption algorithm – a secret key known only to sender / receiver Y = EK(X) X = DK(Y) • Assume encryption algorithm is known • Implies a secure channel to distribute key • The way in which the plaintext is processed – Block cipher – Stream cipher

History of Cryptography • Ancient Cipher – Have a history of some 4000 years – Ancient Egyptians encoded some hieroglyphic writings on monuments – Ancient Hebrews enciphered certain words in the scriptures using the ATBASH cipher – Greek writings show the first discussions of the use of secret writings.

Hieroglyphic Writings

Basic Terminologies • cryptology – the field encompassing both cryptography and cryptanalysis • cryptography – the art or science encompassing the principles and methods of transforming an intelligible message into one that is unintelligible, and then retransforming that message back to its original form. • cryptanalysis (codebreaking) – the study of principles and methods of transforming an unintelligible message back into an intelligible message without knowledge of the key. • plaintext – the original intelligible message • ciphertext – the transformed message

Basic Terminologies (Contd. ) • cipher – Mathematical algorithm for transforming an intelligible message into unintelligible by transposition and/or substitution methods • key – Critical information used by the cipher, known only to the sender & receiver • encipher (encrypt) – the process of converting plaintext to ciphertext using a cipher and a key • decipher (decrypt) – the process of converting ciphertext back into plaintext using a cipher and a key • code – an algorithm for transforming an intelligible message into an unintelligible one using a code-book

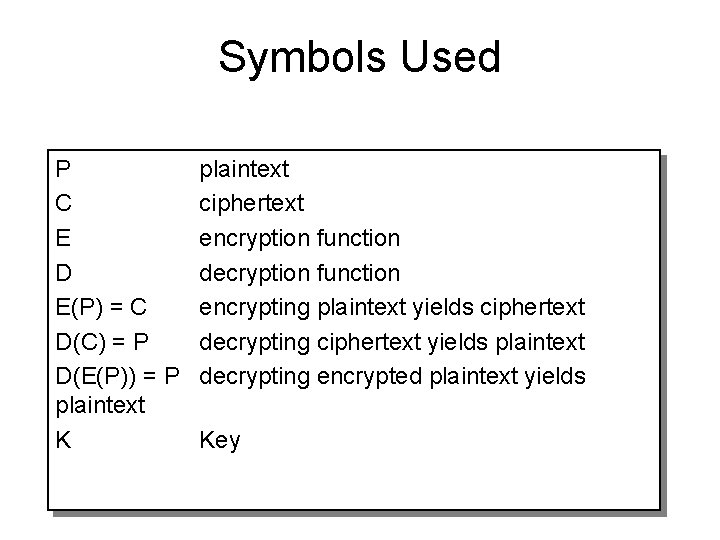
Symbols Used P C E D E(P) = C D(C) = P D(E(P)) = P plaintext K plaintext ciphertext encryption function decryption function encrypting plaintext yields ciphertext decrypting ciphertext yields plaintext decrypting encrypted plaintext yields Key

Cryptographic Concept • Encryption C = EK(P) • Decryption P = EK-1(C) • EK is chosen from a family of transformations known as a cryptographic system. • The parameter that selects the individual transformation is called the key K, selected from a keyspace K.

The Key ! • All modern algorithms use a key to control encryption and decryption • The key used for decryption can be different from the encryption key, but for most algorithms they are the same.

Key Management Problems • Key management is the hardest part of cryptography • Two classes of keys – Short-term session keys (sometimes called ephemeral keys) • Generated automatically and invisibly • Used for one message or session and discarded – Long-term keys • Generated explicitly by the user • Long-term keys are used for two purposes – Authentication (including access control, integrity, and non-repudiation) – Confidentiality (encryption) • Establish session keys • Protect stored data

Key Lifetimes and Key Compromise • Authentication keys – Public keys may have an long lifetime (decades) – Conventional keys have shorter lifetimes (a year or two) • If the key is compromised – Revoke the key • Effects of compromise – Authentication: Signed documents are rendered invalid unless time-stamped. – Confidentiality: All data encrypted with it is compromised.

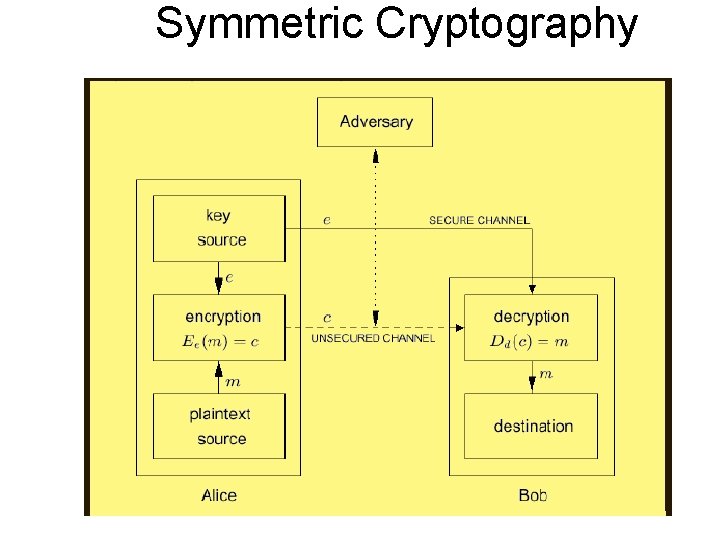
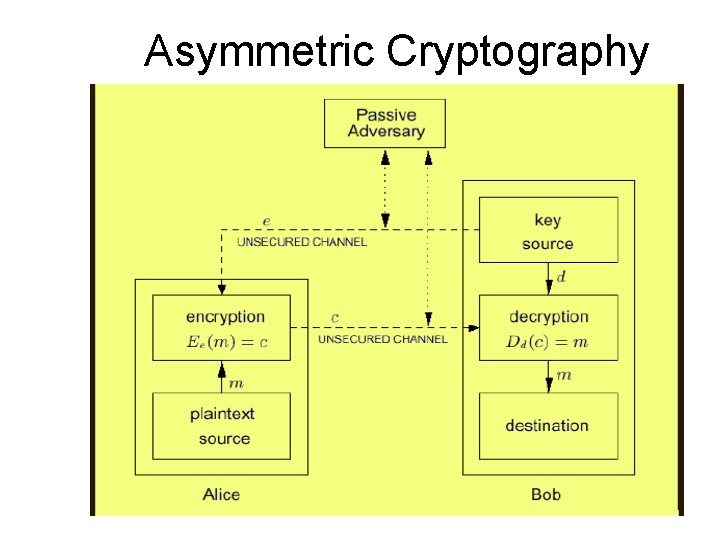
Cryptography Types • Symmetric cryptography – Use the same key for encryption and decryption • Asymmetric cryptography – More popularly known as Public Key Cryptography – Use different keys for encryption and decryption


Symmetric Cryptography

Asymmetric Cryptography

Comparison of SK and PK Cryptography

Cryptanalysis • Cryptanalysis is the process of breaking an encrypted message without knowledge of key • Several different types of attacks can be identified: – Ciphertext only • • only known: algorithm and some ciphertext use statistical attacks only Purpose is to recover plaintext and/or key must be able to identify when have plaintext – Known plaintext • know (or strongly suspect) some plaintext-ciphertext pairs • use this knowledge in attacking cipher and recover key

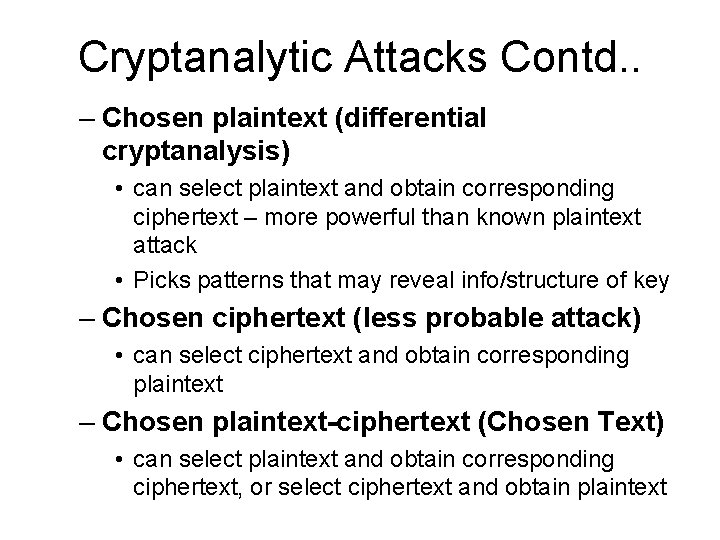
Cryptanalytic Attacks Contd. . – Chosen plaintext (differential cryptanalysis) • can select plaintext and obtain corresponding ciphertext – more powerful than known plaintext attack • Picks patterns that may reveal info/structure of key – Chosen ciphertext (less probable attack) • can select ciphertext and obtain corresponding plaintext – Chosen plaintext-ciphertext (Chosen Text) • can select plaintext and obtain corresponding ciphertext, or select ciphertext and obtain plaintext

Cryptology • Cryptology is the branch of mathematics that studies the mathematical foundations of cryptographic methods. • Cryptology comes from the Greek words Kryptos, meaning hidden, and Graphen, meaning to write. Cryptology is actually the study of codes and ciphers. • Cryptology = both cryptography and cryptanalysis

Algorithm Secrecy • Some cryptographic methods rely on the secrecy of the algorithms; such algorithms are only of historical interest and are not adequate for real-world needs. • Kerchoff’s Principle: If the strength of your new cryptosystems relies on the fact that the attacker does not know the algorithm's inner workings, you are sunk. Security through Obscurity Does Not Work !!!

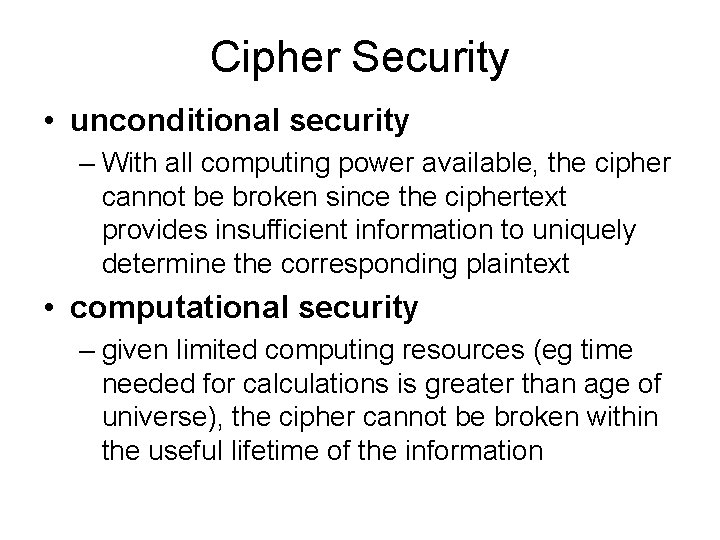
Cipher Security • unconditional security – With all computing power available, the cipher cannot be broken since the ciphertext provides insufficient information to uniquely determine the corresponding plaintext • computational security – given limited computing resources (eg time needed for calculations is greater than age of universe), the cipher cannot be broken within the useful lifetime of the information

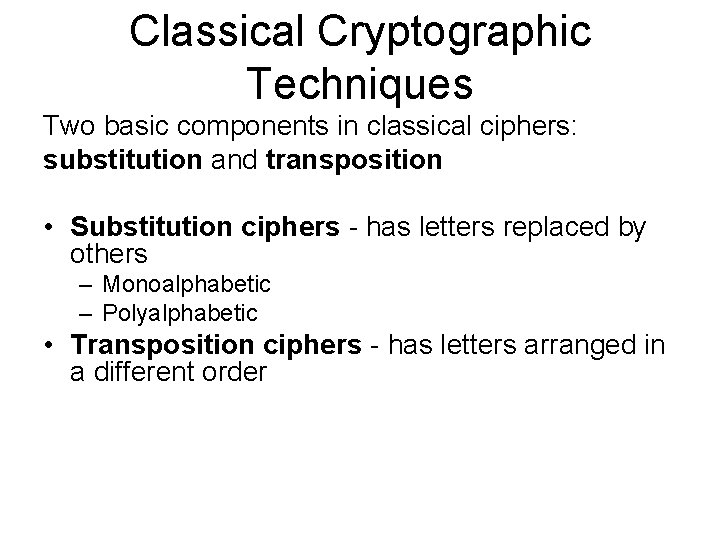
Key Strengths Key Size Number of (bits) Alternative Keys Time required at 106 Decryption/µs 32 232 = 4. 3 x 109 2. 15 milliseconds 56 256 = 7. 2 x 1016 10 hours 128 2128 = 3. 4 x 1038 5. 4 x 1018 years 168 2168 = 3. 7 x 1050 5. 9 x 1030 years

Steganography • Simply takes one piece of information and hides it within another. • Stenography can also be used to place a hidden "trademark" in images, audio, and software, a technique referred to as watermarking. • More – http: //members. tripod. com/steganography/ste go/info. htm – http: //www. belmont. cc. oh. us/Majors/Steno. ht ml

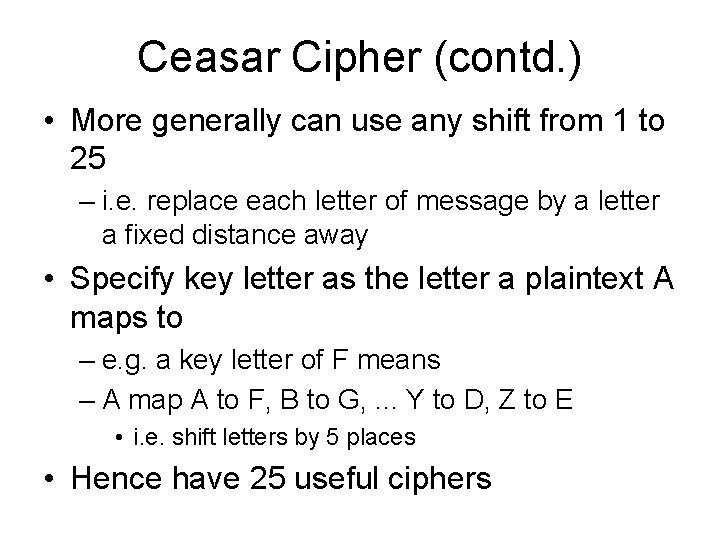
Classical Cryptographic Techniques Two basic components in classical ciphers: substitution and transposition • Substitution ciphers - has letters replaced by others – Monoalphabetic – Polyalphabetic • Transposition ciphers - has letters arranged in a different order

Caesar Cipher – History • A Monoalphabetic Substitution Cipher • 2000 years ago Julius Ceasar used a simple substitution cipher, now known as the Caesar cipher • First attested use in military affairs (Gallic Wars) • General Caeser Algorithm – C = E(p) = (p + k) mod (26) – p = D(C) = (C – k) mod (26) • Replace each letter by 3 rd letter on, eg. – e. g. SSUET is cipher as V V X H W

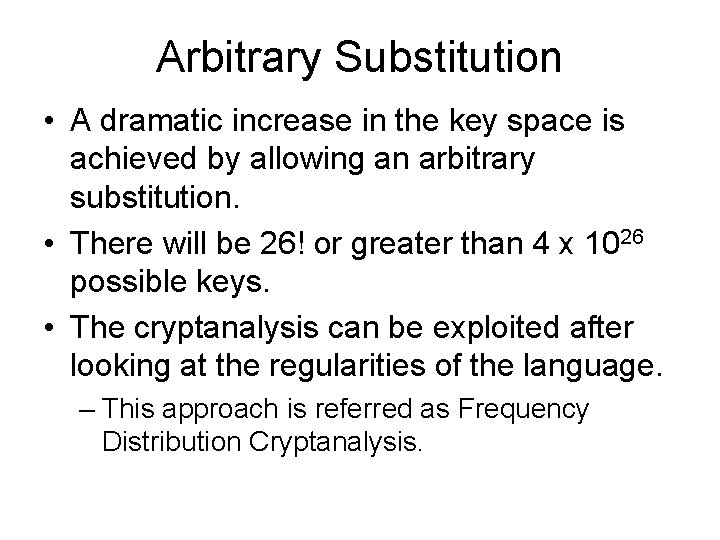
Ceasar Cipher (contd. ) • More generally can use any shift from 1 to 25 – i. e. replace each letter of message by a letter a fixed distance away • Specify key letter as the letter a plaintext A maps to – e. g. a key letter of F means – A map A to F, B to G, . . . Y to D, Z to E • i. e. shift letters by 5 places • Hence have 25 useful ciphers

Example: Caesar Cipher • Replace each letter of message by a letter a fixed distance away • e. g. use the 3 rd letter on – L FDPH L VDZ L FRQTXHUHG (Cipher) – i came i saw i conquered (Plain) • i. e. Mapping in above case is as – ABCDEFGHIJKLMNOPQRSTUVWXYZ – DEFGHIJKLMNOPQRSTUVWXYZABC • Caesar Cipher as: – Encryption Ek : i -> i + k mod 26 – Decryption Dk : i -> i - k mod 26

Cryptanalysis: Caesar Cipher • Exhaustive key search • Given some ciphertext, just try every shift of letters: – LIZHZLVKWRUHSODFHOHWWHUV KHYGYKUJVQTGRNCEGNGVVGTU JGXFXJTIUPSFQMBDFMFUUFST IFWEWISHTOREPLACELETTERS HEVDVHRGSNQDOKZBDKDSSDQR GDUCUGQFRMPCNJYACJCRRCPQ MJAIAMWLXSVITPEGIPIXXIVW Original Ciphertext Shift 1 Shift 2 Shift 3 Plaintext Shift 4 Shift 5 Shift 25 • Class Room Task – Break ciphertext "GCUA VQ DTGCM"

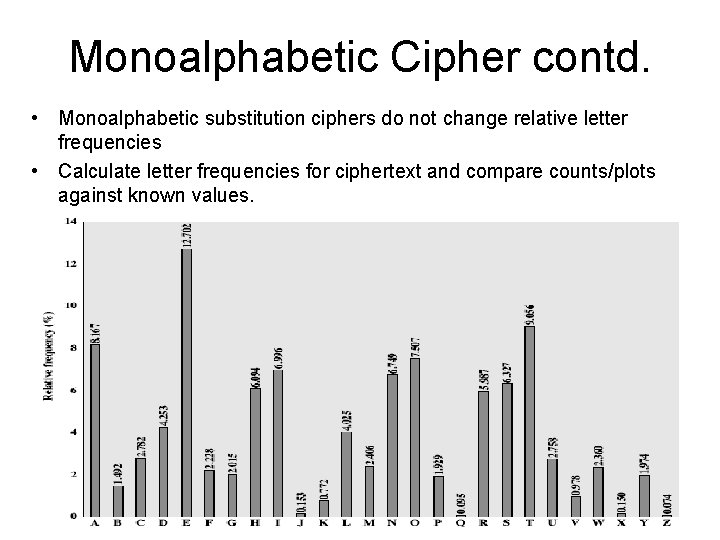
Arbitrary Substitution • A dramatic increase in the key space is achieved by allowing an arbitrary substitution. • There will be 26! or greater than 4 x 1026 possible keys. • The cryptanalysis can be exploited after looking at the regularities of the language. – This approach is referred as Frequency Distribution Cryptanalysis.

Monoalphabetic Cipher contd. • Monoalphabetic substitution ciphers do not change relative letter frequencies • Calculate letter frequencies for ciphertext and compare counts/plots against known values.

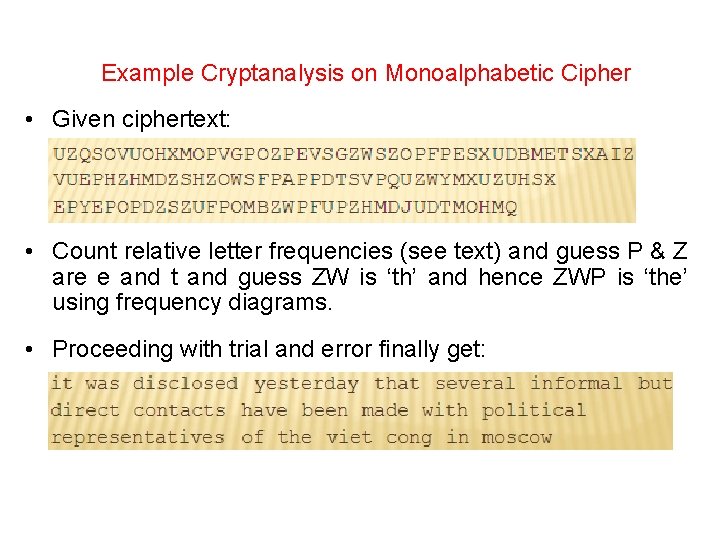
Example Cryptanalysis on Monoalphabetic Cipher • Given ciphertext: • Count relative letter frequencies (see text) and guess P & Z are e and t and guess ZW is ‘th’ and hence ZWP is ‘the’ using frequency diagrams. • Proceeding with trial and error finally get:

Playfair Cipher • Not even the large number of keys in a monoalphabetic cipher provides security • One approach to improving security was to encrypt multiple letters instead of single letter at a time. • This approach will destroy to some extent the frequency structure of the letters. • The Playfair Cipher is one such example • Invented by Charles Wheatstone in 1854, but named after his friend Baron Playfair

Playfair Cipher • Invented by Sir Charles Wheatstone, in 1854. • Developed for Telegraph Secrecy • Based on the 5*5 matrix of letters constructed using a keyword. • The matrix is constructed by filling in the letters of the keyword (minus duplicates). • Then filling in the remainder of the matrix with the remaining letters in alphabetic order. • More… – – http: //raphael. math. uic. edu/~jeremy/crypt/contrib/hong. html http: //members. magnet. at/wilhelm. m. plotz/Doc/Playfair. html http: //www. math. temple. edu/~renault/cryptology/playfair. html http: //www. mactech. com/progchallenge/9909 Challenge. html

Playfair: Rules of Enciphering • Repeating plaintext letters are separated by a filler letter, such as x. – BALOON as BA LX LO ON • Plaintext letters that fall in same row of the matrix are each replaced by the letter to the right. – AR in arch as RM • Plaintext letters that fall in same column are each replaced by the letter beneath. – MU in mute as CM • Otherwise, each plaintext letter is replaced by the letter that lies in its corresponding row and column. – SH in shell as PB Refer to the matrix given in Text book on page 34.

Using "playfair example" as the key, (assuming I and J are interchangeable) the table becomes:

Encrypting the message "Hide the gold in the tree stump": HI DE TH EG OL DI NT HE TR EX ES TU MP

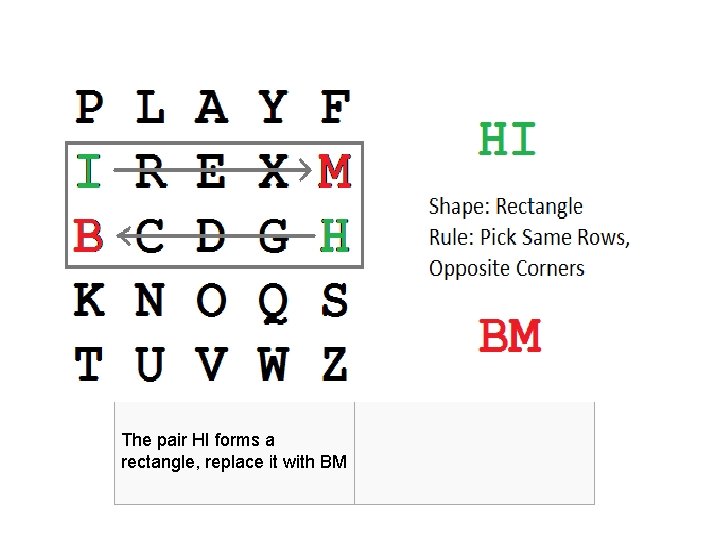
The pair HI forms a rectangle, replace it with BM

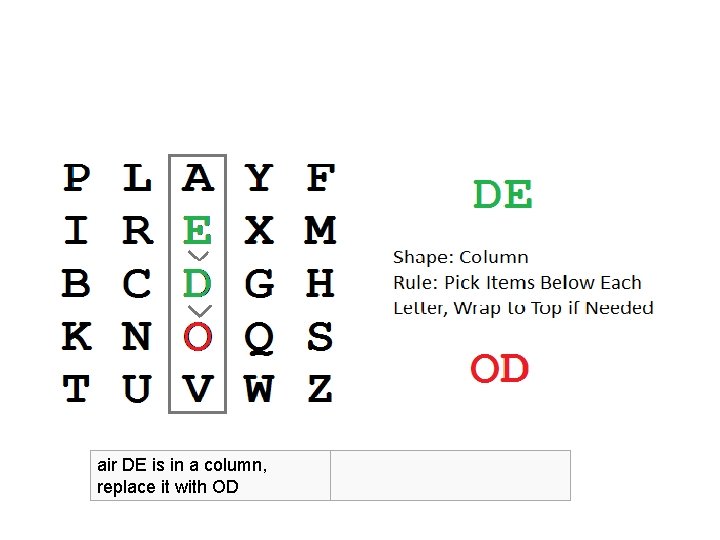
air DE is in a column, replace it with OD

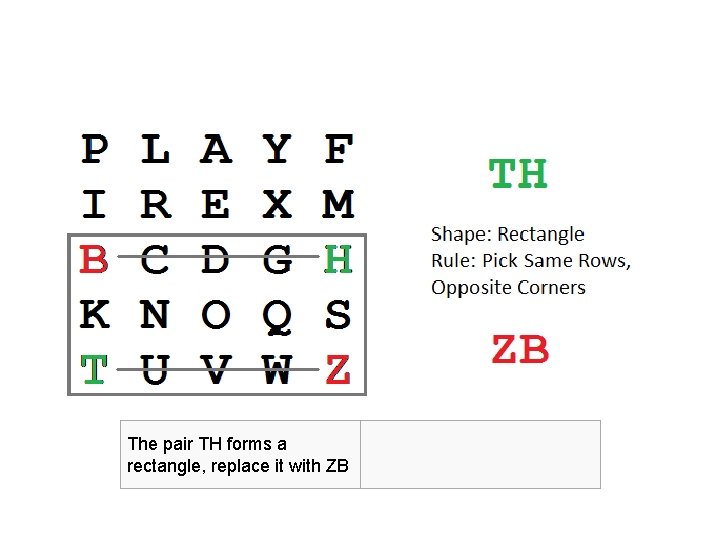
The pair TH forms a rectangle, replace it with ZB

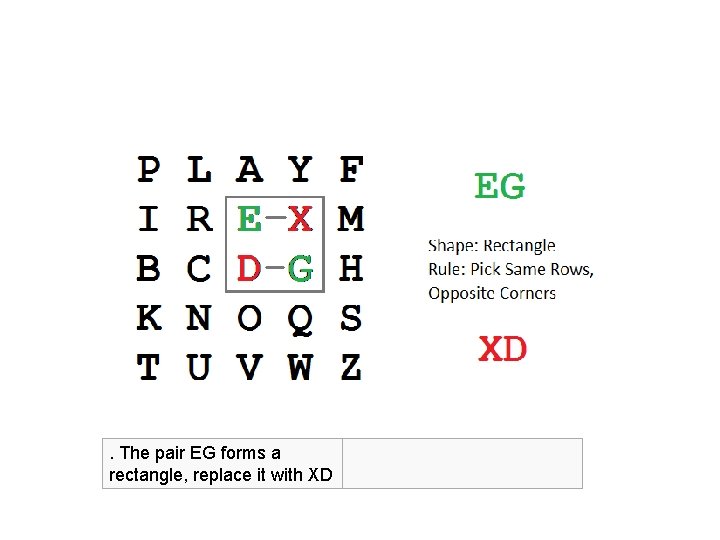
. The pair EG forms a rectangle, replace it with XD

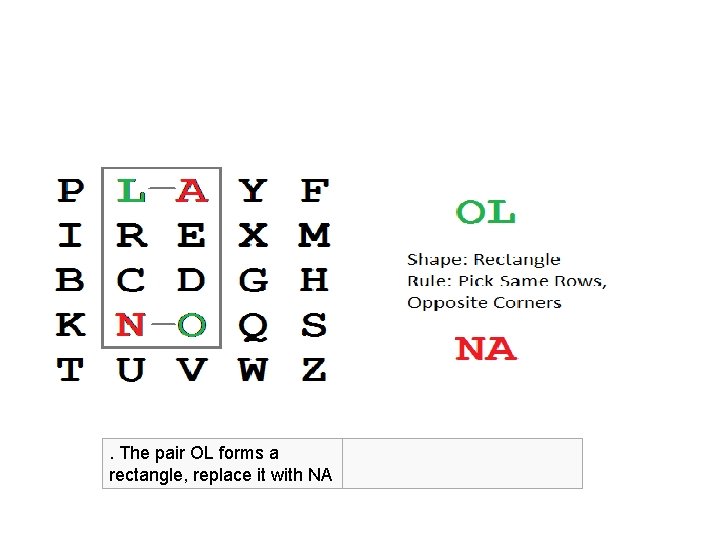
. The pair OL forms a rectangle, replace it with NA

The pair EX (X inserted to split EE) is in a row, replace it with XM

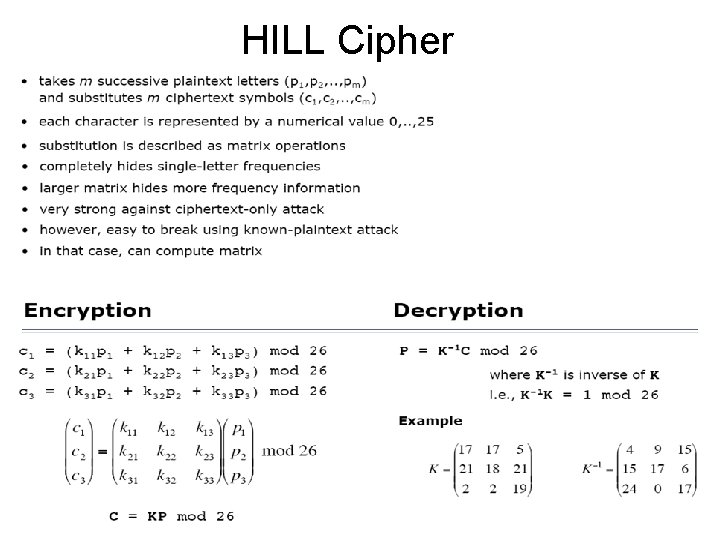
Hill Cipher • Developed by the mathematician Lester Hill in 1929. • Implemented in the form of a machine using gears and chains like those used with bicycles. • The fact that it is impractical for hand use, while it predates the computer age. • More – http: //math. vassar. edu/Classes/280/matrixcode. html – http: //home. ecn. ab. ca/~jsavard/crypto/ro 020103. htm

HILL Cipher

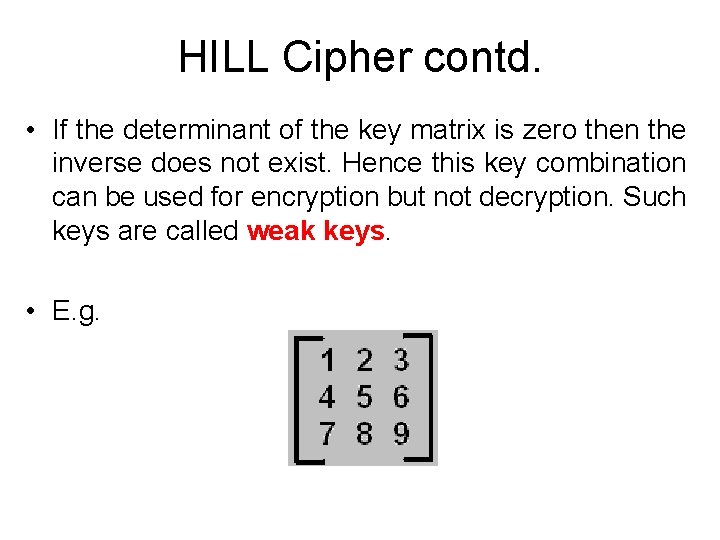
HILL Cipher contd. • If the determinant of the key matrix is zero then the inverse does not exist. Hence this key combination can be used for encryption but not decryption. Such keys are called weak keys. • E. g.

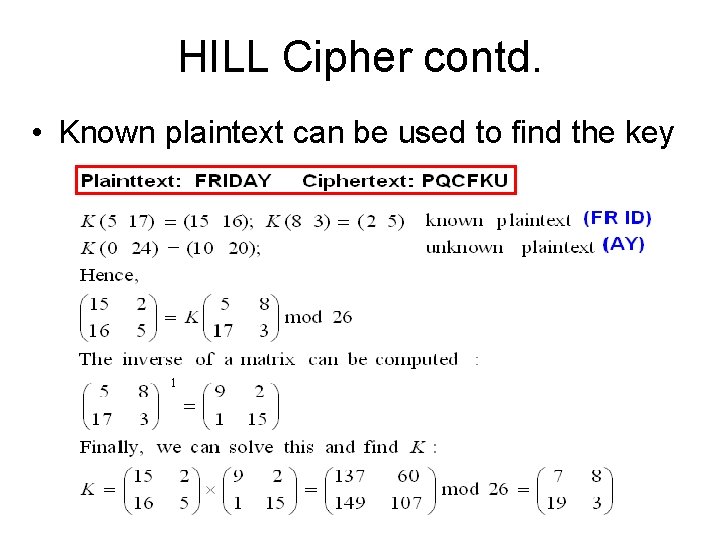
HILL Cipher contd. • Known plaintext can be used to find the key

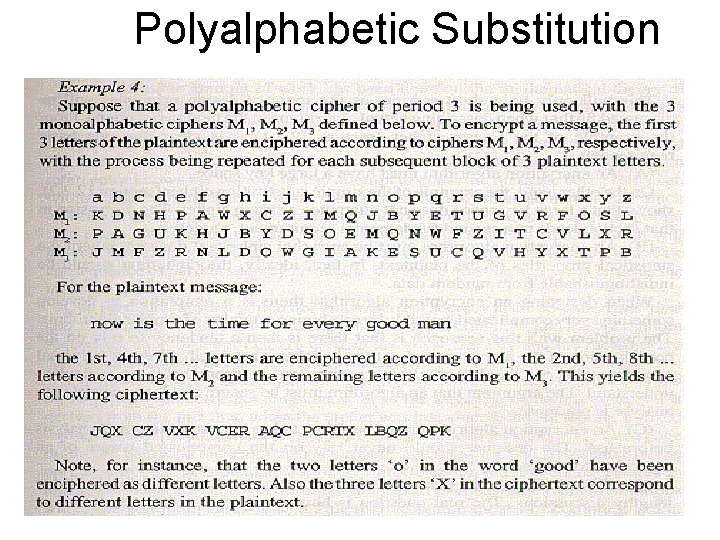
Polyalphabetic Cipher • An approach to improving security is to use multiple cipher alphabets, hence the name Polyalphabetic ciphers • Makes cryptanalysis harder since have more alphabets to guess and because flattens frequency distribution • Use a key to select which alphabet is used for each letter of the message • ith letter of key specifies ith alphabet to use • Use each alphabet in turn • Repeat from start after end of key is reached

Polyalphabetic Substitution

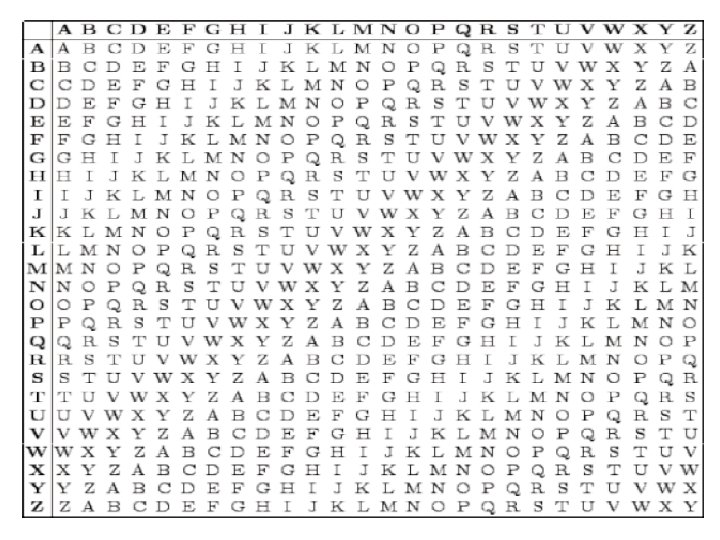
Vigenère Cipher • Simplest Polyalphabetic substitution cipher is the Vigenère Cipher • Key is multiple letters long K = k 1 k 2. . . kd • ith letter specifies ith alphabet to use • Use each alphabet in turn • Repeat from start after ‘d’ letters in message • Describe this mathematically as the function: • Encryption is done using – Eki(a): a -> a + ki (mod 26) • Decryption is done using – Dki(a): a -> a - ki (mod 26)

Vigenère Cipher Contd. . • Write the plaintext out • Under it write the keyword in repetition • Use each key letter in turn as a Caesar cipher key • Encrypt the corresponding plaintext letter • Example – Plaintext THISPROCESSCANALSOBEEXPRESSED – Keyword CIPHERCIPHERCIPHE – Plaintext VPXZTIQKTZWTCVPSWFDMTETIGAHLH


Vernam Cipher • Introduced by an AT&T engineer named Gilbert Vernam. • Uses a keyword that is as long as the plaintext. • The key has no statistical relationship to the plain text. • This system works on binary data rather than letters. • Mathematical representation – Pi = Ci XOR ki

Transposition Ciphers • Referred as classical Transposition or Permutation ciphers • These hide the message by rearranging the letter order without altering the actual letters used. • Scheme uses writing message in a rectangle, row by row, and reading the message off, column by column, but permute the order of the columns. • The order of the columns then becomes the key to the algorithm. • The transposition cipher can be made significantly more secure by performing more than one stage of transposition.

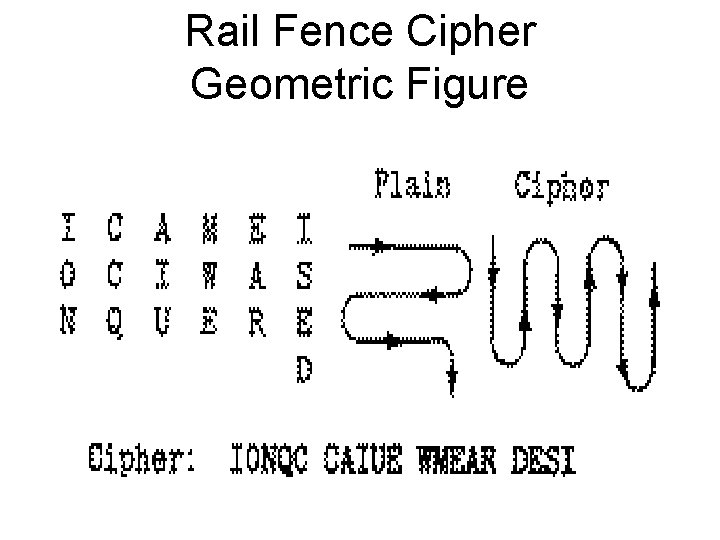
Rail Fence Cipher • Write message with letters on alternate rows (of depth ‘n’). • Read off cipher row by row – Plain: I A E S W C N U R D CMIAIOQEE – Cipher: IAESW CNURD CMIAI OQEE

Rail Fence Cipher Geometric Figure

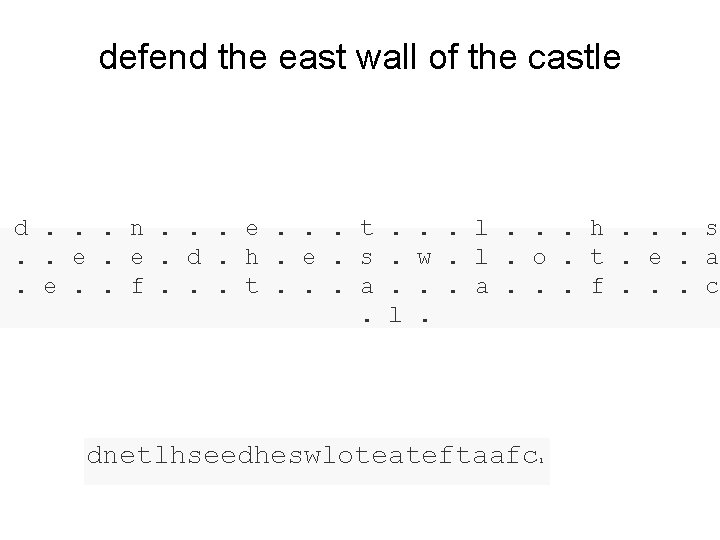
defend the east wall of the castle d. . . n. . . e. . . t. . e. e. d. h. e. s. e. . f. . . t. . . a. . l. . . h. . . s w. l. o. t. e. a. . . f. . . c. dnetlhseedheswloteateftaafc l

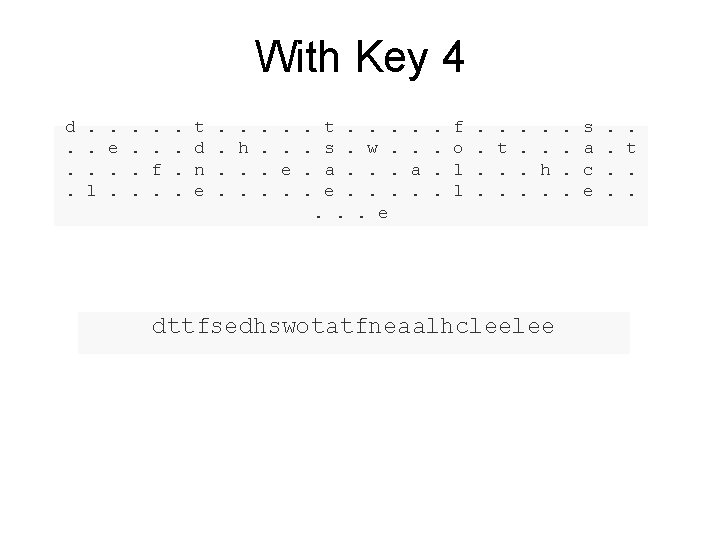
With Key 4 d. . . l . e. . . . f. . . t d n e . . . h. . . . e. . . t. . . s. w. a. . . e . . a. . . f o l l . . . t. . . . h. dttfsedhswotatfneaalhcleelee . . s a c e . . . t. .

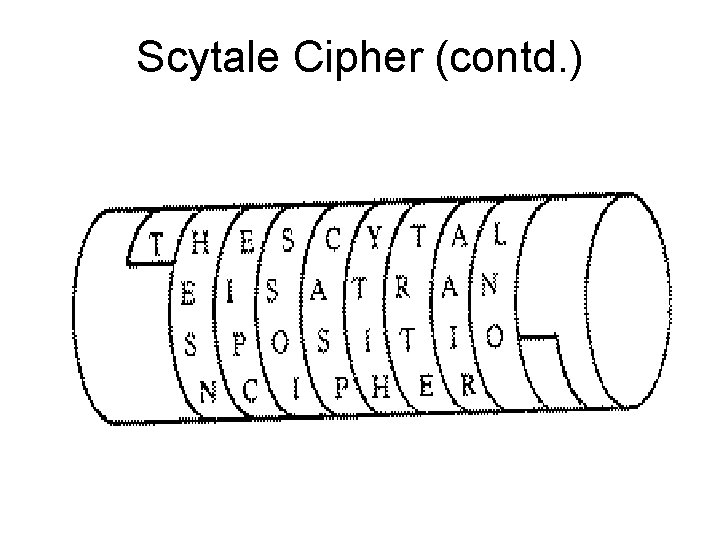
Scytale Cipher • An early Greek transposition cipher. • A strip of paper was wound round a staff. • Message written along staff in rows, then paper removed. • Leaving a strip of seemingly random letters. • Not very secure as key was width of paper & staff.

Scytale Cipher (contd. )

Reverse (Mirror) Cipher • Write the message backwards – Plain: I CAME I SAW I CONQUERED – Cipher: DEREU QNOCI WASIE MACI

Key Concepts for Transposition • In a transposition cipher the key idea is, – Write the message out in columns according to some rule – Read the letters off to form the ciphertext according to another rule – Key used to find order to: • Read off the cipher • Write in the plaintext, or • Both

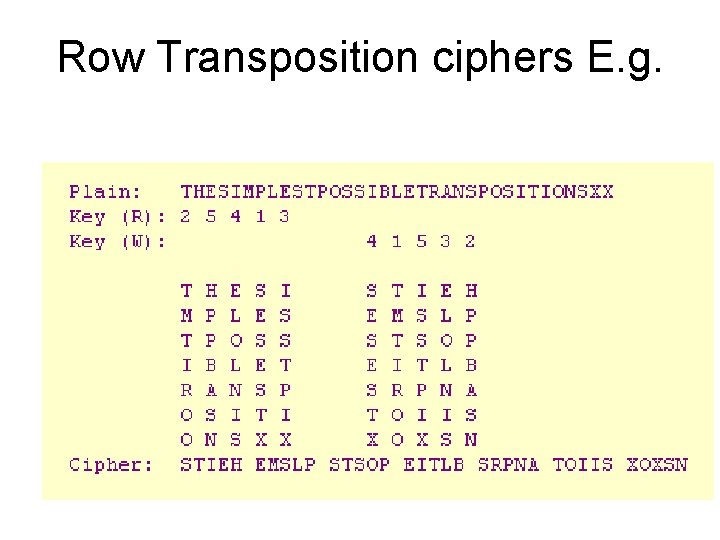
Row Transposition ciphers • Group the message and shuffle letters within each group. • More formally write letters across rows. • Then re-order the columns before reading off the rows. • Always have an equivalent pair of keys (Read off vs. Write In)

Row Transposition ciphers E. g.

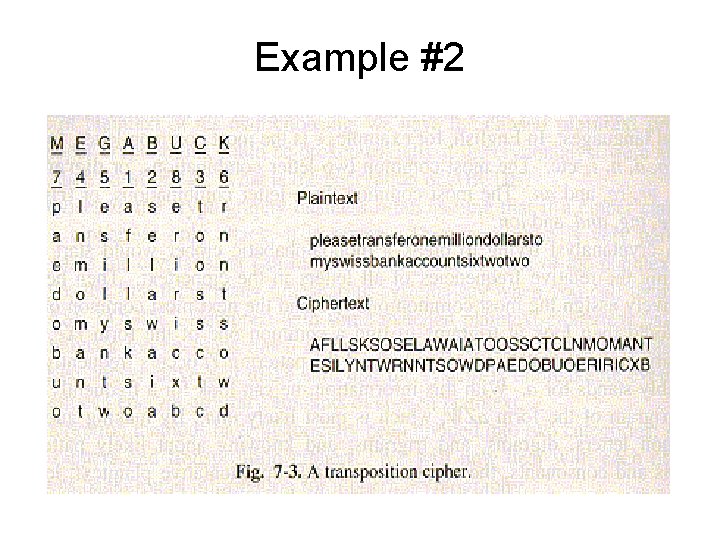
Example #2

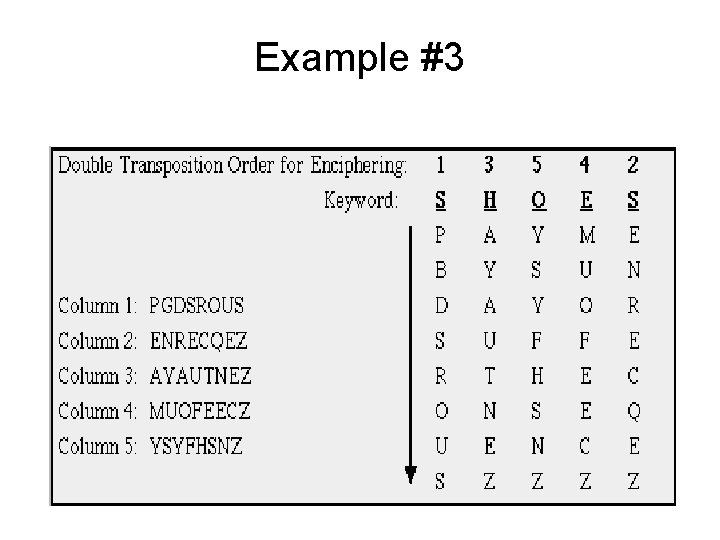
Example #3

What is a One Time Pad? OTPs • An improvement to the Vernam Cipher. • It is the only currently known unconditionally secure encryption system. • Other are cryptographically secure which means that they have a cost associated with breaking, this cost will be very high, but it would theoretically be possible to break if enough compute time could be gathered. • OTPs are provably unconditionally secure. • Example: Statement in C-language main(i, c)int*c; {for(c=fopen(c[1], "r"); ~(i=getchar()); putchar(getc(c)^i)); }

How Does It Work? • Basically you have your random OTP, which both you and your intended recipient have. You have a message M, and you compute the ciphertext C by XORing the message with the OTP: C = M XOR OTP • You send the ciphertext to your recipient, the recipient knowing the OTP also can recover the message by computing the reverse, XORing the ciphertext C with the OTP: M = C XOR OTP • You must never re-use the OTP, other wise it wouldn't be a "One-Time" pad anymore, and it would loose it's unbreakable properties as information would start to be leaked.

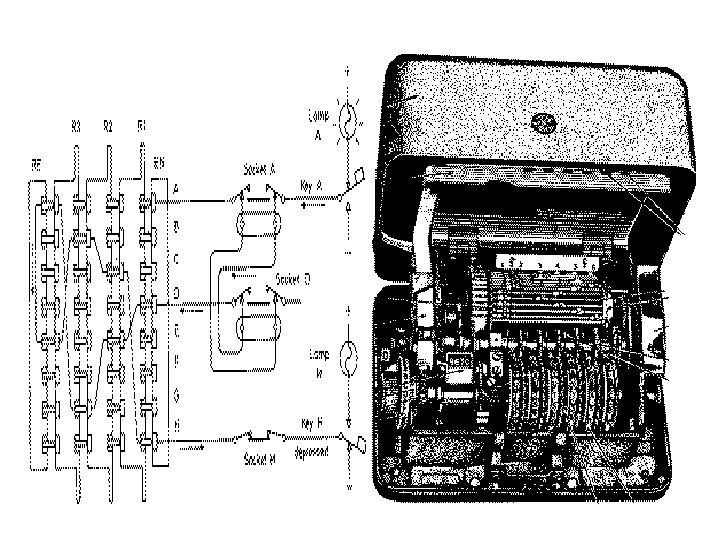
Rotor Machines • A rotor is a small disk of insulating material. • Consist of 26 equally-spaced electrical contacts in a circle on each side. • The contacts on one side are connected to the contacts on the other side in a scrambled order. • Enigma: A Unique Rotor Machine – Enigma Rotor Machine, one of a very important class of cipher machines, heavily used during 2 nd world war, – Comprised a series of rotor wheels with internal crossconnections, providing a substitution using a continuously changing alphabet.
