Classical Encryption Techniques Lecture slides adapted from Lawrie









































- Slides: 60

Classical Encryption Techniques Lecture slides adapted from Lawrie Brown 1

Chapter 2 – Classical Encryption Techniques Many savages at the present day regard their names as vital parts of themselves, and therefore take great pains to conceal their real names, lest these should give to evil-disposed persons a handle by which to injure their owners. —The Golden Bough, Sir James George Frazer 2

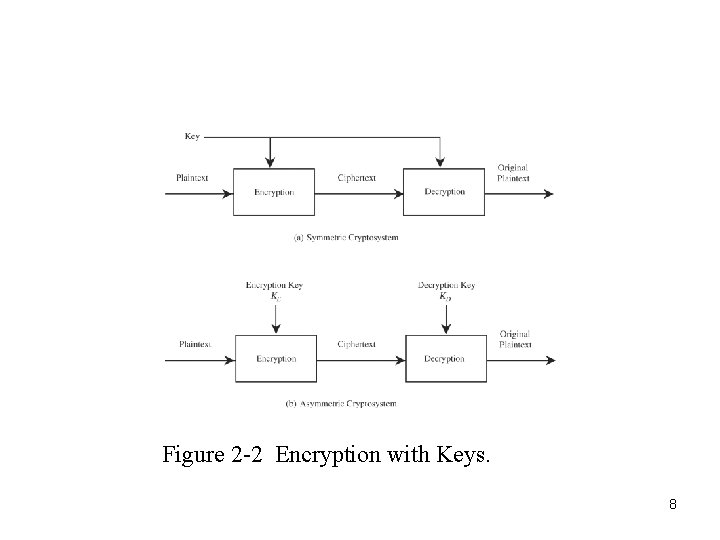
Symmetric Encryption • or conventional / private-key / single-key • sender and recipient share a common key • all classical encryption algorithms are private-key • was only type prior to invention of publickey in 1970’s 3

Basic Terminology • • plaintext - the original message ciphertext - the coded message cipher - algorithm for transforming plaintext to ciphertext key - info used in cipher known only to sender/receiver encipher (encrypt) - converting plaintext to ciphertext decipher (decrypt) - recovering ciphertext from plaintext cryptography - study of encryption principles/methods cryptanalysis (codebreaking) - the study of principles/ methods of deciphering ciphertext without knowing key • cryptology - the field of both cryptography and cryptanalysis 4

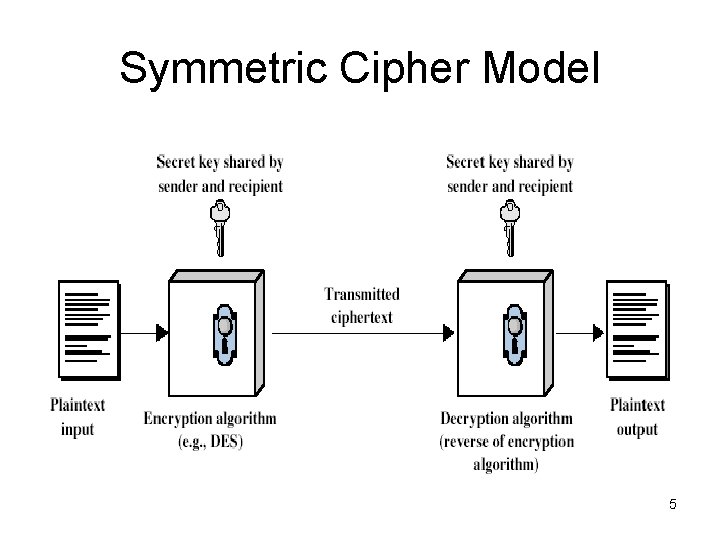
Symmetric Cipher Model 5

Requirements • two requirements for secure use of symmetric encryption: – a strong encryption algorithm – a secret key known only to sender / receiver Y = EK(X) X = DK(Y) • assume encryption algorithm is known • implies a secure channel to distribute key 6

Figure 2 -1 Encryption. 7

Figure 2 -2 Encryption with Keys. 8

Cryptography • can characterize by: – type of encryption operations used • substitution / transposition / product – number of keys used • single-key or private / two-key or public – way in which plaintext is processed • block / stream 9

Types of Cryptanalytic Attacks • ciphertext only – only know algorithm / ciphertext, statistical, can identify plaintext • known plaintext – know/suspect plaintext & ciphertext to attack cipher • chosen plaintext – select plaintext and obtain ciphertext to attack cipher • chosen ciphertext – select ciphertext and obtain plaintext to attack cipher • chosen text – select either plaintext or ciphertext to en/decrypt to attack cipher 10

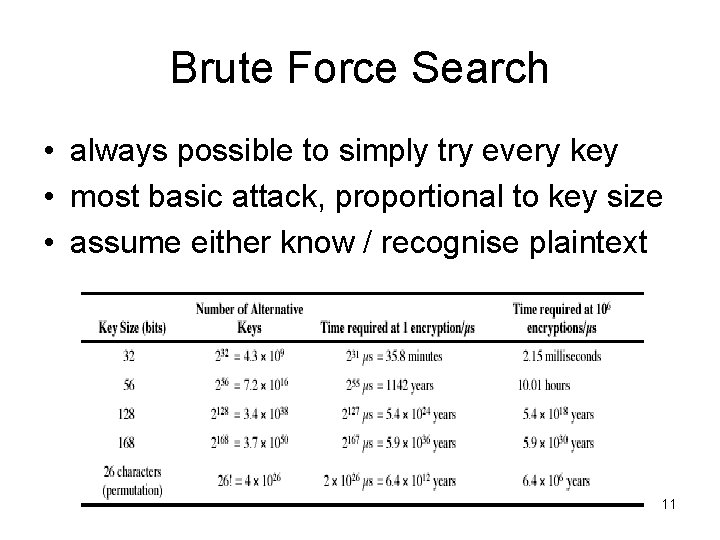
Brute Force Search • always possible to simply try every key • most basic attack, proportional to key size • assume either know / recognise plaintext 11

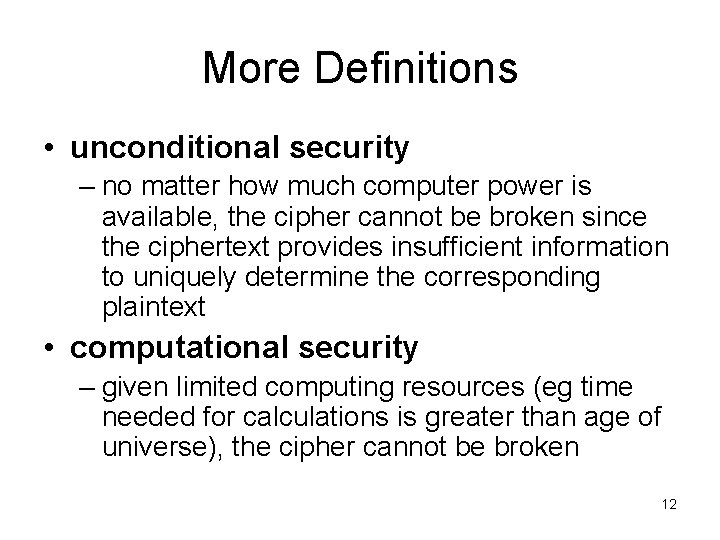
More Definitions • unconditional security – no matter how much computer power is available, the cipher cannot be broken since the ciphertext provides insufficient information to uniquely determine the corresponding plaintext • computational security – given limited computing resources (eg time needed for calculations is greater than age of universe), the cipher cannot be broken 12

Classical Substitution Ciphers • where letters of plaintext are replaced by other letters or by numbers or symbols • or if plaintext is viewed as a sequence of bits, then substitution involves replacing plaintext bit patterns with ciphertext bit patterns 13

Caesar Cipher • • • earliest known substitution cipher by Julius Caesar first attested use in military affairs replaces each letter by 3 rd letter on example: meet me after the toga party PHHW PH DIWHU WKH WRJD SDUWB 14

Caesar Cipher • can define transformation as: a b c d e f g h i j k l m n o p q r s t u v w x y z D E F G H I J K L M N O P Q R S T U V W X Y Z A B C • mathematically give each letter a number a b c 0 1 2 n o 13 14 d e f 3 4 5 p q 15 16 g h i 6 7 8 r s 17 18 j k l m 9 10 11 12 t u v w x y Z 19 20 21 22 23 24 25 • then have Caesar cipher as: C = E(p) = (p + k) mod (26) p = D(C) = (C – k) mod (26) 15

Cryptanalysis of Caesar Cipher • only have 26 possible ciphers – A maps to A, B, . . Z • • • could simply try each in turn a brute force search given ciphertext, just try all shifts of letters do need to recognize when have plaintext eg. break ciphertext "GCUA VQ DTGCM" 16

Monoalphabetic Cipher • rather than just shifting the alphabet • could shuffle (jumble) the letters arbitrarily • each plaintext letter maps to a different random ciphertext letter • hence key is 26 letters long Plain: abcdefghijklmnopqrstuvwxyz Cipher: DKVQFIBJWPESCXHTMYAUOLRGZN Plaintext: ifwewishtoreplaceletters Ciphertext: WIRFRWAJUHYFTSDVFSFUUFYA 17


Monoalphabetic Cipher Security • • now have a total of 26! = 4 x 1026 keys with so many keys, might think is secure but would be !!!WRONG!!! problem is language characteristics 19

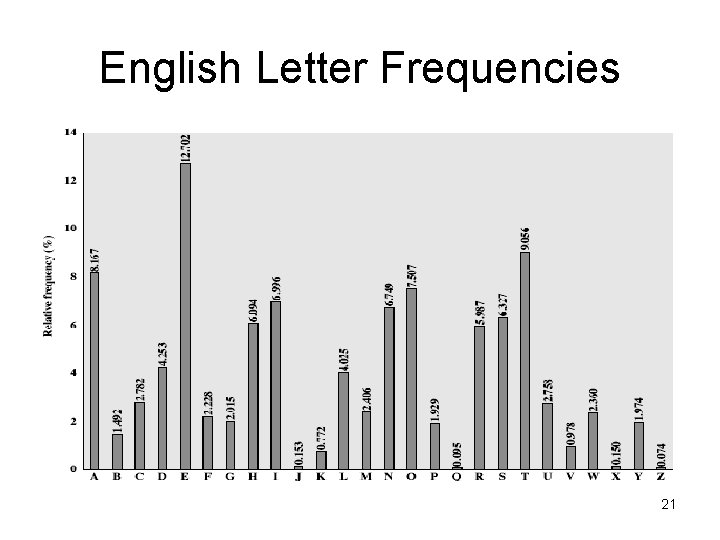
Language Redundancy and Cryptanalysis • • human languages are redundant eg "th lrd s m shphrd shll nt wnt" letters are not equally commonly used in English e is by far the most common letter then T, R, N, I, O, A, S other letters are fairly rare cf. Z, J, K, Q, X have tables of single, double & triple letter frequencies 20

English Letter Frequencies 21

Use in Cryptanalysis • key concept - monoalphabetic substitution ciphers do not change relative letter frequencies • discovered by Arabian scientists in 9 th century • calculate letter frequencies for ciphertext • compare counts/plots against known values • if Caesar cipher look for common peaks/troughs – peaks at: A-E-I triple, NO pair, RST triple – troughs at: JK, X-Z • for monoalphabetic must identify each letter – tables of common double/triple letters help 22

Example Cryptanalysis • given ciphertext: UZQSOVUOHXMOPVGPOZPEVSGZWSZOPFPESXUDBMETSXAIZ VUEPHZHMDZSHZOWSFPAPPDTSVPQUZWYMXUZUHSX EPYEPOPDZSZUFPOMBZWPFUPZHMDJUDTMOHMQ • • count relative letter frequencies (see text) guess P & Z are e and t guess ZW is th and hence ZWP is the proceeding with trial and error fially get: it was disclosed yesterday that several informal but direct contacts have been made with political representatives of the viet cong in moscow 23

Playfair Cipher • not even the large number of keys in a monoalphabetic cipher provides security • one approach to improving security was to encrypt multiple letters • the Playfair Cipher is an example • invented by Charles Wheatstone in 1854, but named after his friend Baron Playfair 24

Playfair Key Matrix • • a 5 X 5 matrix of letters based on a keyword fill in letters of keyword (sans duplicates) fill rest of matrix with other letters eg. using the keyword MONARCHY MONAR CHYBD EFGIK LPQST UVWXZ 25

Encrypting and Decrypting • plaintext encrypted two letters at a time: 1. if a pair is a repeated letter, insert a filler like 'X', eg. "balloon" encrypts as "ba lx lo on" 2. if both letters fall in the same row, replace each with letter to right (wrapping back to start from end), eg. “ar" encrypts as "RM" 3. if both letters fall in the same column, replace each with the letter below it (again wrapping to top from bottom), eg. “mu" encrypts to "CM" 4. otherwise each letter is replaced by the one in its row in the column of the other letter of the pair, eg. “hs" encrypts to "BP", and “ea" to "IM" or "JM" (as desired) 26

Security of the Playfair Cipher • security much improved over monoalphabetic • since have 26 x 26 = 676 digrams • would need a 676 entry frequency table to analyse (verses 26 for a monoalphabetic) • and correspondingly more ciphertext • was widely used for many years (eg. US & British military in WW 1) • it can be broken, given a few hundred letters • since still has much of plaintext structure 27

Polyalphabetic Ciphers • another approach to improving security is to use multiple cipher alphabets • called polyalphabetic substitution ciphers • makes cryptanalysis harder with more alphabets to guess and flatter frequency distribution • use a key to select which alphabet is used for each letter of the message • use each alphabet in turn • repeat from start after end of key is reached 28

Vigenère Cipher • simplest polyalphabetic substitution cipher is the Vigenère Cipher • effectively multiple caesar ciphers • key is multiple letters long K = k 1 k 2. . . kd • ith letter specifies ith alphabet to use • use each alphabet in turn • repeat from start after d letters in message • decryption simply works in reverse 29

Example • • • write the plaintext out write the keyword repeated above it use each key letter as a caesar cipher key encrypt the corresponding plaintext letter eg using keyword deceptive key: deceptivedeceptive plaintext: wearediscoveredsaveyourself ciphertext: ZICVTWQNGRZGVTWAVZHCQYGLMGJ 30

Aids • simple aids can assist with en/decryption • a Saint-Cyr Slide is a simple manual aid – a slide with repeated alphabet – line up plaintext 'A' with key letter, eg 'C' – then read off any mapping for key letter • can bend round into a cipher disk • or expand into a Vigenère Tableau (see text Table 2. 3) 31

Security of Vigenère Ciphers • have multiple ciphertext letters for each plaintext letter • hence letter frequencies are obscured • but not totally lost • start with letter frequencies – see if look monoalphabetic or not • if not, then need to determine number of alphabets, since then can attach each 32

Overview of the DES • A block cipher: – encrypts blocks of 64 bits using a 64 bit key – outputs 64 bits of ciphertext • A product cipher – basic unit is the bit – performs both substitution and transposition (permutation) on the bits • Cipher consists of 16 rounds (iterations) each with a round key generated from the usersupplied key 33

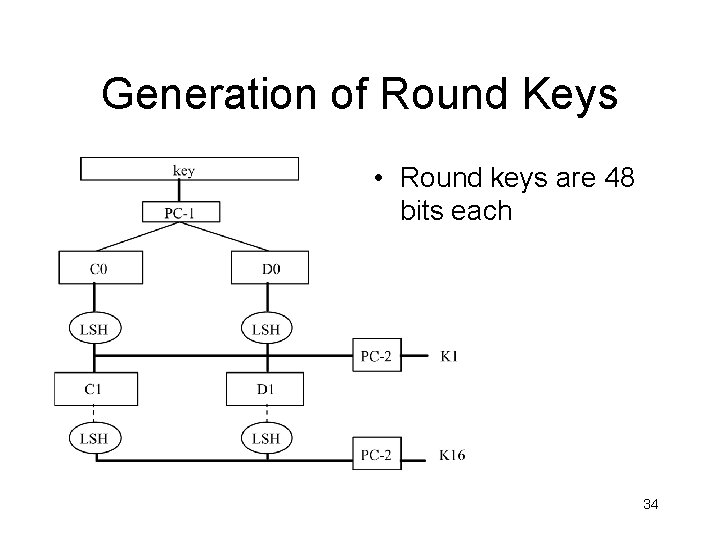
Generation of Round Keys • Round keys are 48 bits each 34

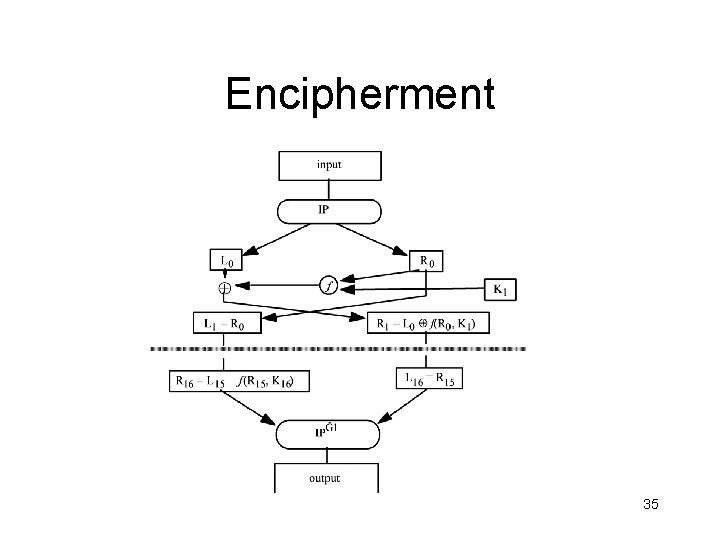
Encipherment 35

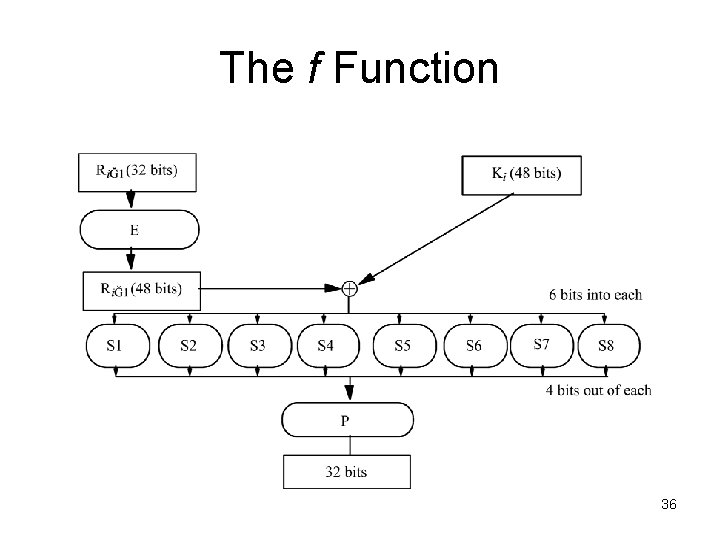
The f Function 36

DES Computations • The cipher consists of 16 rounds or iterations • Each round uses a separate key of 48 bits – These round keys are generated by dropping the parity bits (reducing the effective key size to 56 bits) – Permuting the bits and extracting 48 bits (out of the 56 bits) • A different set of 48 bits is extracted for each round of the 16 rounds • The rounds are extracted sequentially – The input of one round is the output of the previous round 37

DES Computations • The right half of the input, and the round key, are run through a function f that produces 32 bits of output • The 32 bits output are XORed into the left half, and the resulting left and right halves are swapped • The function f provides the strength of the DES. • The right half of the input (32 bits) is expanded to 48 bits • These 48 bits are XORed with the round key (48 bits) 38

DES Computations • The resulting 48 bits are split into eight sets of six bits each • Each set is put through a substitution table called S-box. • Each S-box produces four bits output. • They are catenated into a single 32 -bit quantity, which is permuted. • The resulting 32 bits constitute the output of function f. 39

Public Key Cryptography • Two keys – Private key known only to individual – Public key available to anyone • Public key, private key inverses • Idea – Confidentiality: encipher using public key, decipher using private key – Integrity/authentication: encipher using private key, decipher using public one 40

Requirements 1. It must be computationally easy to encipher or decipher a message given the appropriate key 2. It must be computationally infeasible to derive the private key from the public key 3. It must be computationally infeasible to determine the private key from a chosen plaintext attack 41

RSA • Exponentiation cipher • Relies on the difficulty of determining the number of numbers relatively prime to a large integer n 42

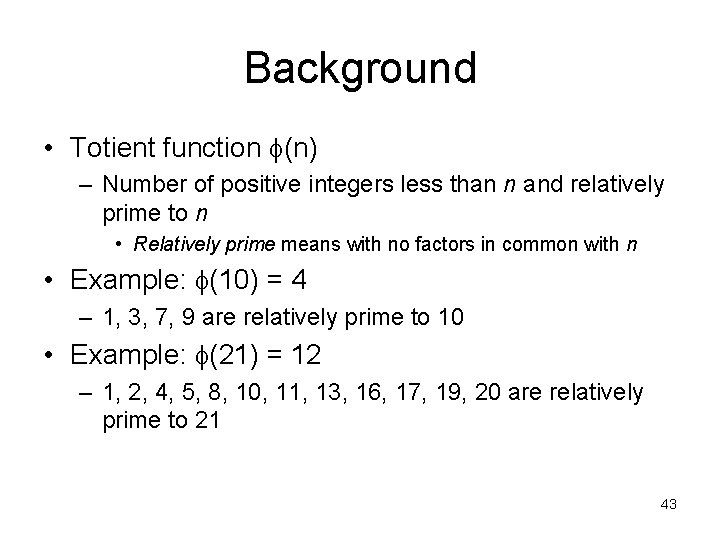
Background • Totient function (n) – Number of positive integers less than n and relatively prime to n • Relatively prime means with no factors in common with n • Example: (10) = 4 – 1, 3, 7, 9 are relatively prime to 10 • Example: (21) = 12 – 1, 2, 4, 5, 8, 10, 11, 13, 16, 17, 19, 20 are relatively prime to 21 43

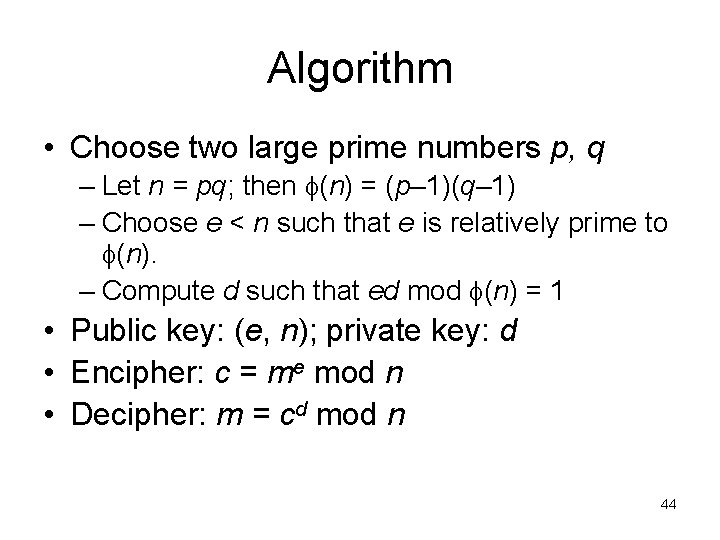
Algorithm • Choose two large prime numbers p, q – Let n = pq; then (n) = (p– 1)(q– 1) – Choose e < n such that e is relatively prime to (n). – Compute d such that ed mod (n) = 1 • Public key: (e, n); private key: d • Encipher: c = me mod n • Decipher: m = cd mod n 44

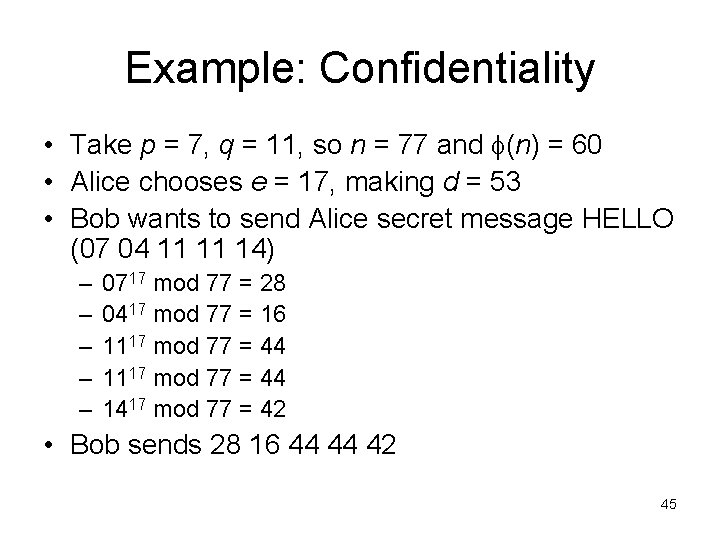
Example: Confidentiality • Take p = 7, q = 11, so n = 77 and (n) = 60 • Alice chooses e = 17, making d = 53 • Bob wants to send Alice secret message HELLO (07 04 11 11 14) – – – 0717 mod 77 = 28 0417 mod 77 = 16 1117 mod 77 = 44 1417 mod 77 = 42 • Bob sends 28 16 44 44 42 45

Example • Alice receives 28 16 44 44 42 • Alice uses private key, d = 53, to decrypt message: – – – 2853 mod 77 = 07 1653 mod 77 = 04 4453 mod 77 = 11 4253 mod 77 = 14 • Alice translates message to letters to read HELLO – No one else could read it, as only Alice knows her private key and that is needed for decryption 46

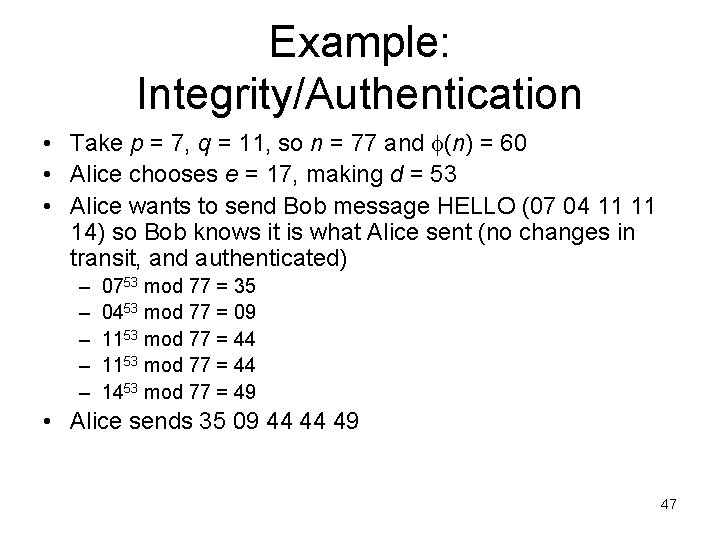
Example: Integrity/Authentication • Take p = 7, q = 11, so n = 77 and (n) = 60 • Alice chooses e = 17, making d = 53 • Alice wants to send Bob message HELLO (07 04 11 11 14) so Bob knows it is what Alice sent (no changes in transit, and authenticated) – – – 0753 mod 77 = 35 0453 mod 77 = 09 1153 mod 77 = 44 1453 mod 77 = 49 • Alice sends 35 09 44 44 49 47

Example • Bob receives 35 09 44 44 49 • Bob uses Alice’s public key, e = 17, n = 77, to decrypt message: – – – 3517 mod 77 = 07 0917 mod 77 = 04 4417 mod 77 = 11 4917 mod 77 = 14 • Bob translates message to letters to read HELLO – Alice sent it as only she knows her private key, so no one else could have enciphered it – If (enciphered) message’s blocks (letters) altered in transit, would not decrypt properly 48

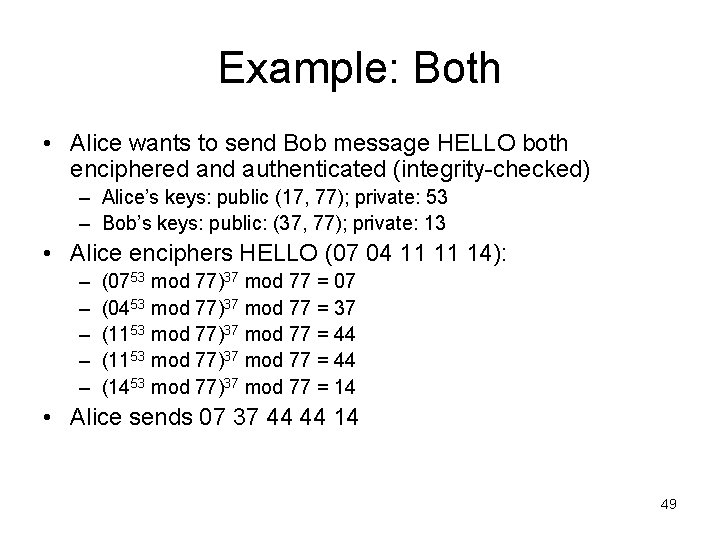
Example: Both • Alice wants to send Bob message HELLO both enciphered and authenticated (integrity-checked) – Alice’s keys: public (17, 77); private: 53 – Bob’s keys: public: (37, 77); private: 13 • Alice enciphers HELLO (07 04 11 11 14): – – – (0753 mod 77)37 mod 77 = 07 (0453 mod 77)37 mod 77 = 37 (1153 mod 77)37 mod 77 = 44 (1453 mod 77)37 mod 77 = 14 • Alice sends 07 37 44 44 14 49

Security Services • Confidentiality – Only the owner of the private key knows it, so text enciphered with public key cannot be read by anyone except the owner of the private key • Authentication – Only the owner of the private key knows it, so text enciphered with private key must have been generated by the owner 50

More Security Services • Integrity – Enciphered letters cannot be changed undetectably without knowing private key • Non-Repudiation – Message enciphered with private key came from someone who knew it 51

Warnings • Encipher message in blocks considerably larger than the examples here – If 1 character per block, RSA can be broken using statistical attacks (just like classical cryptosystems) – Attacker cannot alter letters, but can rearrange them and alter message meaning • Example: reverse enciphered message of text ON to get NO 52

Encryption Applications 1. Cryptographic Hash Functions (Checksums) 2. Key Exchange 3. Digital Signatures 4. Certificates 53

Cryptographic Hash Functions • Also called checksums or message digests • Encryption is most commonly used for secrecy – The message content –and sometimes its existence- is not known • Sometimes other things are more important – Integrity: In a document retrieval system containing legal records, it may be important to know that the copy retrieved is exactly what was stored. 54

Cryptographic Checksums • Elements or components of the file are not bound together. – This means changing one value affects the integrity of the file, but that one change can easily go undetected. • We need to put a seal or a shield around the file do that we can detect when the seal has been broken and thus know that something has been changed. • One way for providing the seal is to compute a cryptographic function – One-way functions (Have no inverse functions) 55

Cryptographic Checksums • Mathematical function to generate a set of k bits from a set of n bits (where k ≤ n). – k is smaller then n except in unusual circumstances • Example: ASCII parity bit – ASCII has 7 bits; 8 th bit is “parity” – Even parity: even number of 1 bits – Odd parity: odd number of 1 bits 56

Example Use • Bob receives “ 10111101” as bits. – Sender is using even parity; 6 1 bits, so character was received correctly – Sender is using odd parity; even number of 1 bits, so character was not received correctly 57

Cryptographic Checksums • The function must depend on all bits of the file being sealed – Any change to even a single bit will alter the checksum result • The checksum value is stored with the file • Each time the file is accessed or used, the checksum is recomputed • If the computed checksum matches the stored value, it is likely that the file has not been changed 58

Cryptographic Checksums • In block encryption: – Chaining: means linking each block to the previous block’s value (and therefore to all previous blocks) • For example, by using an XOR to combine the encrypted previous block with the encryption of the current one • A file’s cryptographic checksum could be the last block of the chained encryption of a file since that block will depend on all other blocks 59

Cryptographic Checksums • Most widely used cryptographic hash functions: – MD 4 – MD 5 (MD stands for Message Digest) – SHA/SHS (Secure Hash Algorithm or Standard) – SHA-1 60