GS Chapter 4 Symmetric Encryption in Java csci










![Javax. crypto. Cipher. do. Final( ) D. Finish the operation: byte[ ] do. Final( Javax. crypto. Cipher. do. Final( ) D. Finish the operation: byte[ ] do. Final(](https://slidetodoc.com/presentation_image_h/c8e39497eebbf71e1608faf51bffb6b2/image-13.jpg)



![Password-based encryption (PBE) q Random. next. Bytes (byte[ ] bytes) Generates random bytes and Password-based encryption (PBE) q Random. next. Bytes (byte[ ] bytes) Generates random bytes and](https://slidetodoc.com/presentation_image_h/c8e39497eebbf71e1608faf51bffb6b2/image-21.jpg)










- Slides: 36

GS: Chapter 4 Symmetric Encryption in Java csci 5931 Web Security 1

Topics A. Blowfish B. Password-based encryption (PBE) C. Key storage D. Modes E. Cipher streams and IV (initialization vector) F. Sealed objects csci 5931 Web Security 2

Applications of symmetric encryptions q File encryption q Network encryption q Database encryption q Applications that require encryption of large amount of data. csci 5931 Web Security 3

Javax. crypto. Key. Generator http: //java. sun. com/j 2 se/1. 4. 1/docs/api/javax/crypto/Key. Generator. html q § Provides the functionality of a (symmetric) key generator § Key generators are constructed using one of the get. Instance class methods. § Key. Generator objects are reusable, i. e. , after a key has been generated, the same Key. Generator object can be re-used to generate further keys. § There are two ways to generate a key: in an algorithm-independent manner, and in an algorithm-specific manner. The only difference between the two is the initialization of the object. csci 5931 Web Security 4

Javax. crypto. Key. Generator q Using Key. Generator A. Create a new key generator: Key. Generator key. Generator = Key. Generator. get. Instance (“DESede”); Note: DESede is a triple DES variant with three DES keys k 1, k 2, k 3. The message is encrypted with k 1 first, then decrypted with k 2, and finally encrypted again with k 3. This increases the key space and prevents brute force attacks. B. Initialize the key generator with the size of the key: key. Generator. init (168); // initialized to 168 bits C. Generate the key object: Key my. Key = key. Generator. generate. Key ( ); csci 5931 Web Security 5

Java. security. Key http: //java. sun. com/j 2 se/1. 4. 1/docs/api/java/security/Key. html java. security Interface Key q All Superinterfaces: Serializable All Known Subinterfaces: DHPrivate. Key, DHPublic. Key, DSAPrivate. Key, DSAPublic. Key, PBEKey, Private. Key, Public. Key, RSAMulti. Prime. Private. Crt. Key, RSAPrivate. Crt. Key, RSAPrivate. Key, RSAPublic. Key, Secret. Key All Known Implementing Classes: Kerberos. Key, Secret. Key. Spec csci 5931 Web Security 6

Java. security. Key q The Key interface is the top-level interface for all keys. It defines the functionality shared by all key objects. q All keys have three characteristics: 1. 2. 3. q q The key algorithm for that key; An external encoded form for the key used when a standard representation of the key is needed outside the Java Virtual Machine, as when transmitting the key to some other party; The name of the format of the encoded key Keys are generally obtained through key generators, key factory, certificates, or various Identity classes used to manage keys. Examples: javax. crypto. Key. Generator( ); java. security. Key. Factory( ); csci 5931 Web Security 7

Javax. crypto. Cipher q http: //java. sun. com/j 2 se/1. 4. 1/docs/api/ public class Cipher extends Object This class provides the functionality of a cryptographic cipher for encryption and decryption. It forms the core of the Java Cryptographic Extension (JCE) framework. q To use a Cipher: get. Instance( ), init( ), update( ), do. Final( ). csci 5931 Web Security 8

Javax. crypto. Cipher. get. Instance( ) A. In order to create a Cipher object, the application calls the Cipher's get. Instance method, and passes the name of the requested transformation to it. static Cipher get. Instance(String transformation) Generates a Cipher object that implements the specified transformation. static Cipher get. Instance(String transformation, Provider provider) Creates a Cipher object that implements the specified transformation, as supplied by the specified provider. static Cipher get. Instance(String transformation, String provider) Creates a Cipher object that implements the specified transformation, as supplied by the specified provider. csci 5931 Web Security 9

Javax. crypto. Cipher. get. Instance( ) q Examples: Cipher cipher = Cipher. get. Instance("DES/CBC/PKCS 5 Padding"); Cipher cipher = Cipher. get. Instance(“DESede/ECB/PKCS 5 Padding”); csci 5931 Web Security 10

Javax. crypto. Cipher. init( ) B. Initialize an instance of Cipher: 1. Declares the operating mode (ENCRYPT_MODE, DECRYPT_MODE, WRAP_MODE, UNWRAP_MODE) 2. Pass a key (java. security. Key) to the cipher Example: Cipher. init (Cipher. ENCRYPT_MODE, my. Key); Note: When a Cipher object is initialized, it loses all previously-acquired state. In other words, initializing a Cipher is equivalent to creating a new instance of that Cipher and initializing it. csci 5931 Web Security 11

Javax. crypto. Cipher. update( ) C. Pass the information to be encrypted/decrypted to the cipher: 1. The information must be in the form of a byte array. 2. Note: Ciphers typically buffer their output. If the buffer has not been filled, null will be returned. Alternative update( ) methods: byte[ ] update (byte[] input) byte[ ] plaintext = my. String. get. Bytes (“UTF 8”); byte[ ] ciphertext = cipher. update (plaintext); int update (byte[ ] input, int input. Offset, int input. Len, byte[ ] output, int output. Offset) Continues a multiple-part encryption or decryption operation (depending on how this cipher was initialized), processing another data part. csci 5931 Web Security 12
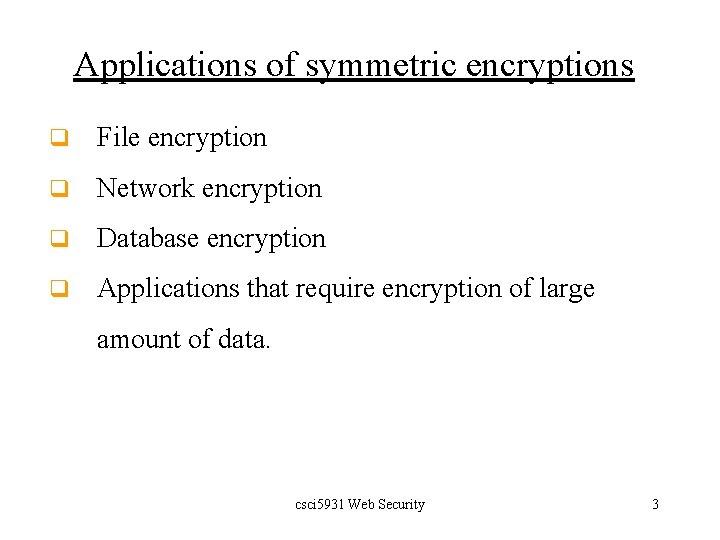
![Javax crypto Cipher do Final D Finish the operation byte do Final Javax. crypto. Cipher. do. Final( ) D. Finish the operation: byte[ ] do. Final(](https://slidetodoc.com/presentation_image_h/c8e39497eebbf71e1608faf51bffb6b2/image-13.jpg)
Javax. crypto. Cipher. do. Final( ) D. Finish the operation: byte[ ] do. Final( ) Finishes a multiple-part encryption or decryption operation, depending on how this cipher was initialized. byte[ ] do. Final(byte[] input) Encrypts or decrypts data in a single-part operation, or finishes a multiple-part operation. Example: Byte[ ] ciphertext = cipher. do. Final ( ); csci 5931 Web Security 13

Simple. Example. java q P. 69: Simple. Example. java (see http: //sce. cl. uh. edu/yang/teaching/pro. Java. Security. Code. html) q Sample output: >java Simple. Example "How are you doing? " Plain Message=How are you doing? Generating a Triple. DES key. . . Done generating the key. Now encrypting the message Message Encrypted Ciphertext=-74 -45759 -44 -115 -19 -8 -56 -99 -47794393 -45 -107 -41 -125 -127 -233271855 Now decrypting the message Message decrypted Decrypted text: How are you doing? csci 5931 Web Security 14

Blowfish. Example. java q Blowfish keys can be any bit size from 8 to 448, as long as the number if divisible by 8. q p. 69: Blowfish. Example. java (see http: //sce. cl. uh. edu/yang/teaching/pro. Java. Security. Code. html) q Sample output: >java Blowfish. Example "It's a wonderful day!" Generating a Blowfish key. . . Done generating the key. Plaintext: 73 116 39 115 32 97 32 119 111 110 101 114 102 117 108 32 100 97 121 33 Ciphertext: -77 56 -88 61 -52 -12 -57 43 -10 66 -54 -98 -86 56 -86 51 -127 -125 30 48 -64 11 2 -37 -125 Decrypted text: It's a wonderful day! csci 5931 Web Security 15

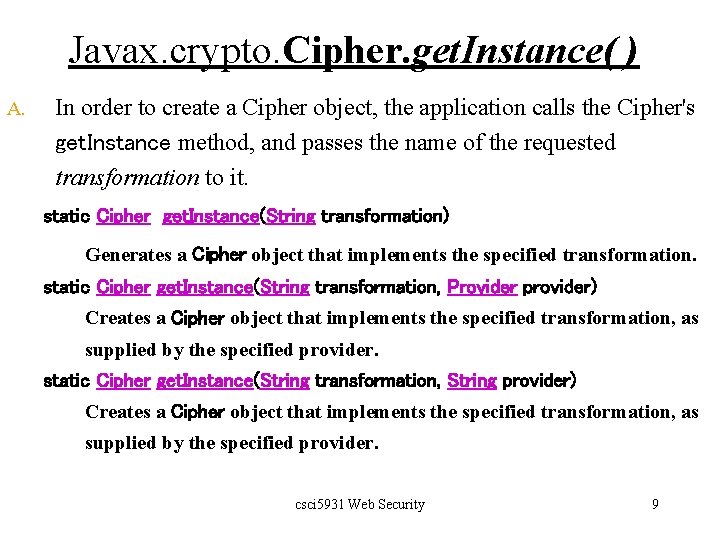
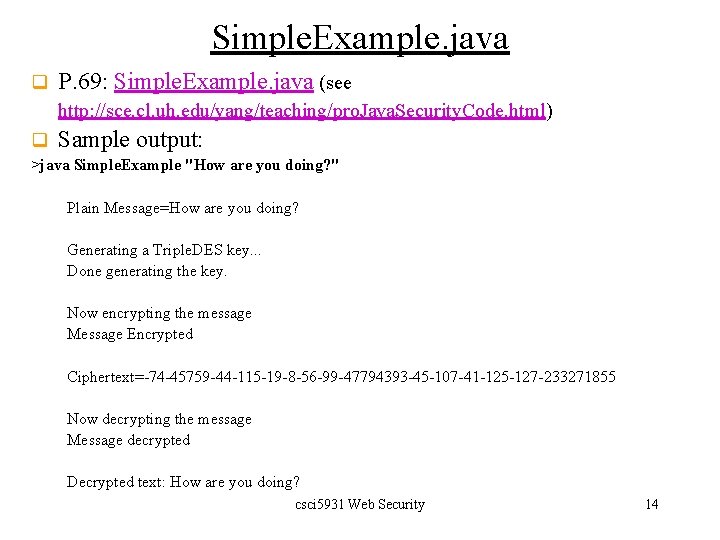
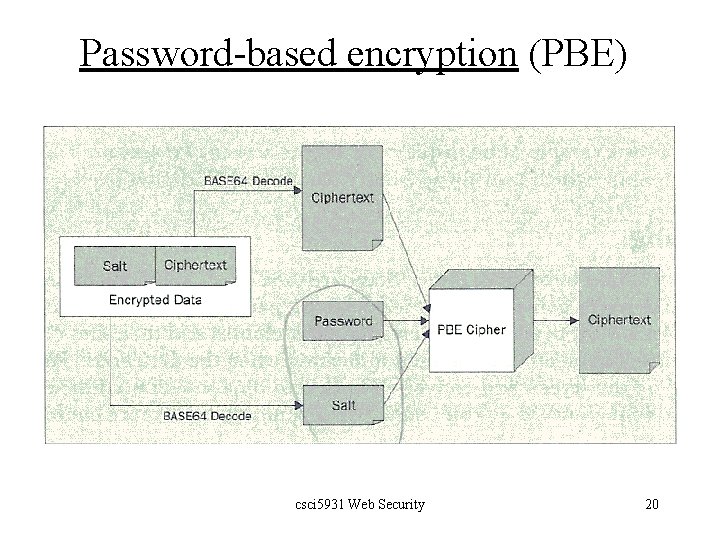
Password-based encryption (PBE) q hashing + symmetric encryption q q The user-provided password is hashed by a message digest algorithm, such as SHA. The hash value is then used to construct a key for a symmetric encryption algorithm, such as Blowfish. The plaintext is then encrypted by the symmetric encryption algorithm. Problems? 1. 2. 3. PBE is usually less secure, due to its smaller key space. Passwords may suffer ‘dictionary attack’. Two people might choose the same password, which would create two identical entries in the password file. csci 5931 Web Security 16

Password-based encryption (PBE) q PBE + salt + iteration count q q q A salt is a randomly generated piece of data, say 64 bits, that is added to each password. The combined salt+password is used to generate the key. The key is then used to generate a symmetric cipher. For the purpose of decryption, the salt must be stored as part of the ciphertext. See figures on page 74. csci 5931 Web Security 17

Password-based encryption (PBE) csci 5931 Web Security 18

Base 64 Encoding q Effective in representing ASCII data as 6 -bit characters (save one bit per character) q Widely used in networking transmissions of data; e. g. , in MIME emails & other Internet-related applications q Input: N bytes q Number of output characters (N * 8 / 24) * 4, if N*8 % 24 is zero; (N * 8 / 24 + 1) * 4, otherwise. Example: N = 8 bytes. (64 / 24 + 1) * 4 12 characters q See http: //nas. cl. uh. edu/yang/teaching/csci 5939 Database. Security/base 64. ppt, RFC 2045, and Appendix C. csci 5931 Web Security 19

Password-based encryption (PBE) csci 5931 Web Security 20
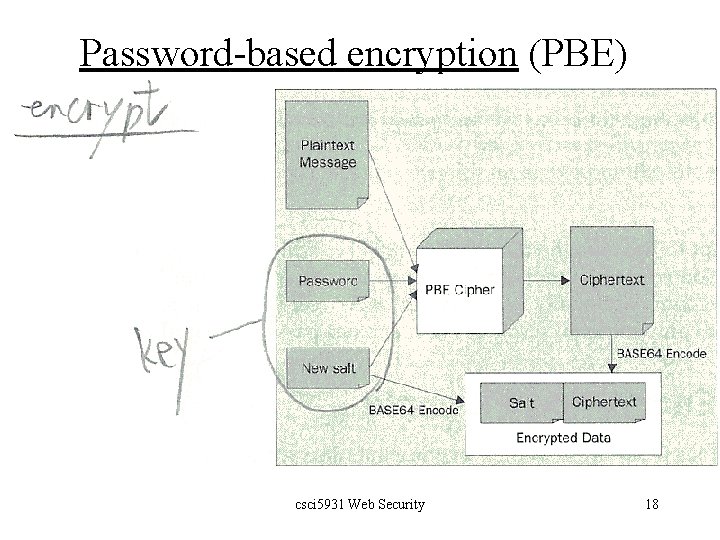
![Passwordbased encryption PBE q Random next Bytes byte bytes Generates random bytes and Password-based encryption (PBE) q Random. next. Bytes (byte[ ] bytes) Generates random bytes and](https://slidetodoc.com/presentation_image_h/c8e39497eebbf71e1608faf51bffb6b2/image-21.jpg)
Password-based encryption (PBE) q Random. next. Bytes (byte[ ] bytes) Generates random bytes and places them into a usersupplied byte array. q public class PBEKey. Spec extends Object implements Key. Spec A user-chosen password that can be used with password-based encryption (PBE). The password can be viewed as some kind of raw key material, from which the encryption mechanism that uses it derives a cryptographic key. csci 5931 Web Security 21

Password-based encryption (PBE) q public class Secret. Key. Factory extends Object This class represents a factory for secret keys. Key factories are used to convert keys (opaque cryptographic keys of type Key) into key specifications (transparent representations of the underlying key material), and vice versa. Secret key factories operate only on secret (symmetric) keys. Key factories are bi-directional, i. e. , they allow to build an opaque key object from a given key specification (key material), or to retrieve the underlying key material of a key object in a suitable format. Application developers should refer to their provider's documentation to find out which key specifications are supported by the generate. Secret and get. Key. Spec methods. csci 5931 Web Security 22

Password-based encryption q Twofish encryption algorithm: A symmetric block cipher that accepts keys of any length, up to 256 bits; Among the new encryption algorithms being considered by the National Institute of Science and Technology (NIST) as a replacement for the DES algorithm; Highly secure and flexible; Works extremely well with large microprocessors, 8 -bit smart card microprocessors, and dedicated hardware. (Source: http: //www. wiley. com/cda/product/0, , 0471353817, 00. html) csci 5931 Web Security 23

Password-based encryption q An example program: PBE. java (see http: //sce. cl. uh. edu/yang/teaching/pro. Java. Security. Code. html) q Sample PBE encryption/decryption: >java PBE -e sasquatch "Hello World!" yr. Vhjq 5 djco=e. SIS 1 Lbe. Atu 5 KIKf 5 nt. Nhg== >java PBE -e sasquatch "Hello World!" l. Q 1 lz. Ml 8 ONM=GBJFXSnpblt. Xowv. JTmck 1 w== >java PBE -d sasquatch "l. Q 1 lz. Ml 8 ONM=GBJFXSnpblt. Xowv. JTmck 1 w==" Hello World! csci 5931 Web Security 24

Key storage Storage of keys in a persistent media (file, q database) for later retrieval or transportation q Objectives: The stored keys must be protected. q Problems? If the key storage is compromised, the data protected by - the keys become unprotected. q Solutions? q Use PBE to encrypt the keys. Problems? csci 5931 Web Security 25

Key storage 1. Key Wrapping The wrap( ) method, defined in javax. crypto. Cipher, takes a key as an argument and returns the encrypted value of the key as a byte array. Example: cipher. init (Cipher. WRAP_MODE, password. Key, param. Spec); byte[ ] encrypted. Key. Bytes = cipher. wrap (secret. Key); q To decrypt the key: cipher. init (Cipher. UNWRAP_MODE, password. Key, param. Spec); Key key = cipher. unwrap(encrypted. Key. Bytes, “Blowfish”, Cipher. SECRET_KEY); csci 5931 Web Security 26

Key storage 1. Key Encryption Use the get. Encoded( ) method, as defined in java. security. Key, to encrypt the key. Example: byte[ ] key. Bytes = my. Key. get. Encoded( ); cipher. init (Cipher. ENCRYPT_MODE, password. Key, param. Spec); byte[ ] encrypted. Key. Bytes = cipher. do. Final (key. Bytes); q To decrypt the key: cipher. init (Cipher. DECRYPT_MODE, password. Key, param. Spec); byte[ ] key. Bytes = cipher. do. Final (encrypted. Key. Bytes); Secret. Key. Spec my. Key = new Secret. Key. Spec (key. Bytes, “Blowfish” ); csci 5931 Web Security 27

Padding q Padding is needed to make the size of the plaintext to be a multiple of the block size. q Most symmetric algorithms use one of two types of padding: q No padding – requires the data end on a block exactly q PKCS#5 padding – (PKCS = Public Key Cryptography Standard) Suppose there are N bytes in a block that need to be padded. Fill each of the N bytes with the value N. If the data end on a multiple of the block size, add an entire block of padding. (See the illustration on p. 81. ) csci 5931 Web Security 28

Modes of DES q ECB, CBC q CFB (Cipher Feed. Back) q Similar to CBC, but may work on smaller chunks of data (8 bits for example). q OFB (Output Feed. Back) q Similar to CFB, but provides better protection against data loss during transmission. q That is, a single-bit error will not cause the whole block to be lost, as in the cases of ECB, CBC and CFB. csci 5931 Web Security 29

Cipher streams and IV q q Javax. crypto. Cipher. Input. Stream javax. crypto. Cipher. Output. Stream q q They provide convenient wrappers around standard input and output streams for them to be automatically encrypted or decrypted. Initialization Vector (IV): q A sequence of random bytes appended to the front of the plaintext before encryption by a block cipher. q Adding the initialization vector to the beginning of the plaintext eliminates the possibility of having the initial ciphertext block the same for any two messages. q How to determine the size of a IV, given a cipher? Example: A 256 -bit Rijndael cipher needs a 16 -byte IV. csci 5931 Web Security 30

IV in Java q public class Iv. Parameter. Spec extends Object implements Algorithm. Parameter. Spec This class specifies an initialization vector (IV). Examples which use IVs are ciphers in feedback mode, e. g. , DES in CBC mode and RSA ciphers with OAEP encoding operation. (NOTE: See page 434 for RSA-OAEP padding. ) csci 5931 Web Security 31

Rijndael q What is Rijndael ? (Dutch, pronounced as ‘Rain Doll’) “Rijndael is a block cipher, designed by Joan Daemen and Vincent Rijmen as a candidate algorithm for the AES. The cipher has a variable block length and key length. We currently specified how to use keys with a length of 128, 192, or 256 bits to encrypt blocks with al length of 128, 192 or 256 bits. ” (Source: http: //www. esat. kuleuven. ac. be/~rijmen/rijndael/) q After nearly four years of evaluation, in October 2000, Rijndael was selected by the NIST as the `AES' (Advanced Encryption Standard). See the press release. csci 5931 Web Security 32

File. Encryptor. java q File. Encryptor. java (see http: //sce. cl. uh. edu/yang/teaching/pro. Java. Security. Code. html) q Four functions: q create. Key( password ) q load. Key ( password ) q encrypt ( password, input. File, output. Encrypted. File ) q decrypt ( password, input. Encrypted. File, outputfile) csci 5931 Web Security 33

Sealed objects q Sealed object: An object that is encrypted. q The object must be serializable. q Sealed objects can be useful for storing or transferring an encrypted version of an object. q The default JDK 1. 2 prevents extensions from using the class loader to create classes that are neither standard objects nor extensions. That is, a custom object such as a Credit. Card object, won’t be able to be decrypted. q See Appendix D “the Encrypted. Object class” for a better sealed object implementation. csci 5931 Web Security 34

Sealed objects q Sealed. Object. Example. java (see http: //sce. cl. uh. edu/yang/teaching/pro. Java. Security. Code. html) q Sample output: >java Sealed. Object. Example Creating a key. Encrypting the object. Unencrypting the object. Credit card number: 1234567890 csci 5931 Web Security 35

Next 1. Asymmetric Encryption (GS: 5) 2. Relevant links: RFC 1829 - The ESP DES-CBC Transform - This document describes the DES-CBC security transform for the IP Encapsulating Security Payload (ESP). 2. The GNU Crypto project – This project aims at providing free, versatile, high-quality, and provably correct implementations of cryptographic primitives and tools in the Java programming language for use by programmers and end-users. It’s also got a comprehensive listing of crypto-related algorithms. 1. csci 5931 Web Security 36