GS Chapter 5 Asymmetric Encryption in Java csci











- Slides: 19

GS: Chapter 5 Asymmetric Encryption in Java csci 5233 Computer Security 1

Topics A. Ciphers, modes and padding B. Asymmetric encryption in Java C. Session key encryption D. File encryption/decryption using RSA E. Key agreement csci 5233 Computer Security 2

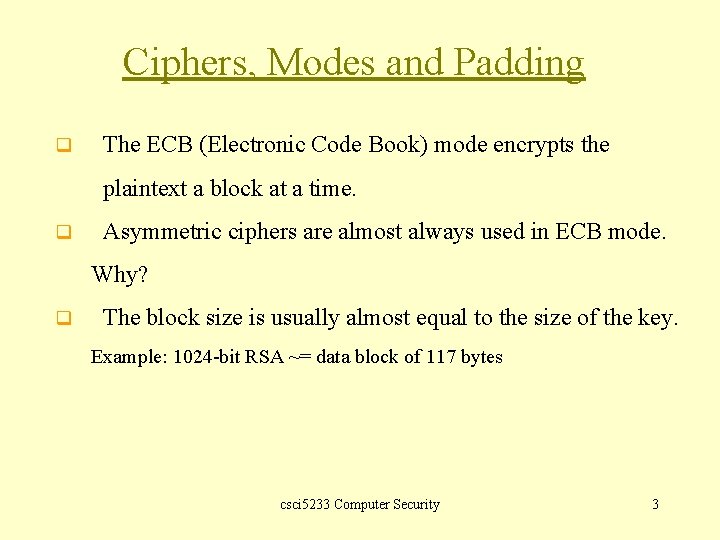
Ciphers, Modes and Padding q The ECB (Electronic Code Book) mode encrypts the plaintext a block at a time. q Asymmetric ciphers are almost always used in ECB mode. Why? q The block size is usually almost equal to the size of the key. Example: 1024 -bit RSA ~= data block of 117 bytes csci 5233 Computer Security 3

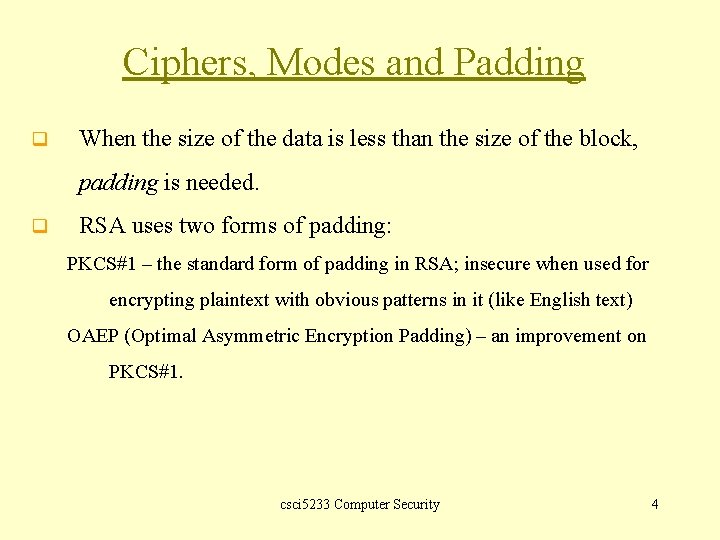
Ciphers, Modes and Padding q When the size of the data is less than the size of the block, padding is needed. q RSA uses two forms of padding: PKCS#1 – the standard form of padding in RSA; insecure when used for encrypting plaintext with obvious patterns in it (like English text) OAEP (Optimal Asymmetric Encryption Padding) – an improvement on PKCS#1. csci 5233 Computer Security 4

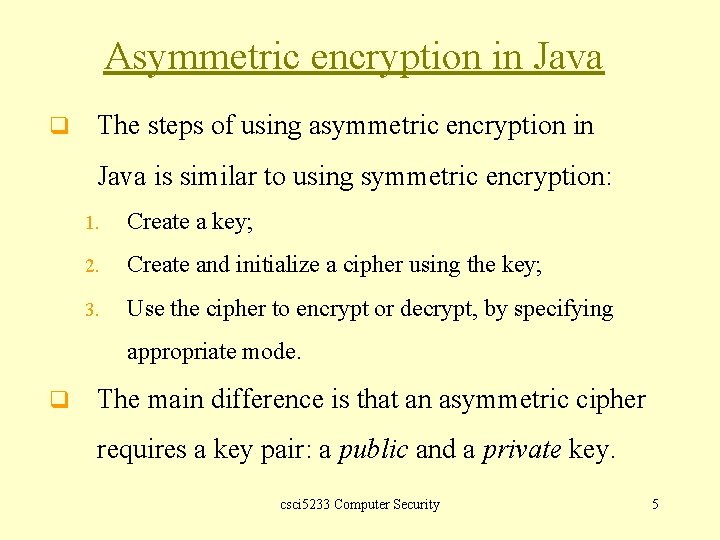
Asymmetric encryption in Java q The steps of using asymmetric encryption in Java is similar to using symmetric encryption: 1. Create a key; 2. Create and initialize a cipher using the key; 3. Use the cipher to encrypt or decrypt, by specifying appropriate mode. q The main difference is that an asymmetric cipher requires a key pair: a public and a private key. csci 5233 Computer Security 5

Major Java Classes for Key Pairs 1. java. security. Key. Pair public final class Key. Pair extends Object implements Serializable 2. java. security. Public. Key public interface Public. Key extends Key This interface contains no methods or constants. It merely serves to group (and provide type safety for) all public key interfaces. Note: The specialized public key interfaces extend this interface. See, for example, the DSAPublic. Key interface in java. security. interfaces. csci 5233 Computer Security 6

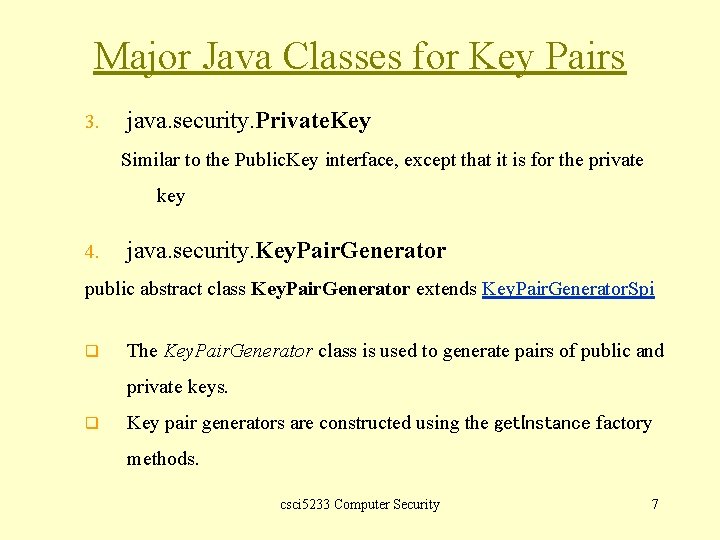
Major Java Classes for Key Pairs 3. java. security. Private. Key Similar to the Public. Key interface, except that it is for the private key 4. java. security. Key. Pair. Generator public abstract class Key. Pair. Generator extends Key. Pair. Generator. Spi q The Key. Pair. Generator class is used to generate pairs of public and private keys. q Key pair generators are constructed using the get. Instance factory methods. csci 5233 Computer Security 7

Session key encryption q Oddly enough, the greatest value in using asymmetric encryption is in encrypting symmetric keys. Why? (discussed earlier in Chapter 2) q Exercise: Explain how session key encryption works. q Simple. RSAExample. java (or find it at http: //sce. cl. uh. edu/yang/teaching/pro. Java. Security. Code. html) csci 5233 Computer Security 8

File encrypt/decrypt using RSA q Steps: 1) Use an AES session key to encrypt the file. (Note: Each file is encrypted by a different session key. ) q 2) Use RSA to encrypt the session key. 3) Store the encrypted session key inside the file. Source code: File. Encryptor. RSA. java csci 5233 Computer Security 9

File encrypt/decrypt using RSA q File. Encryptor is started with one of three options: -c: create key pair and write it to 2 files -e: encrypt a file, given as an argument -d: decrypt a file, given as an argument csci 5233 Computer Security 10

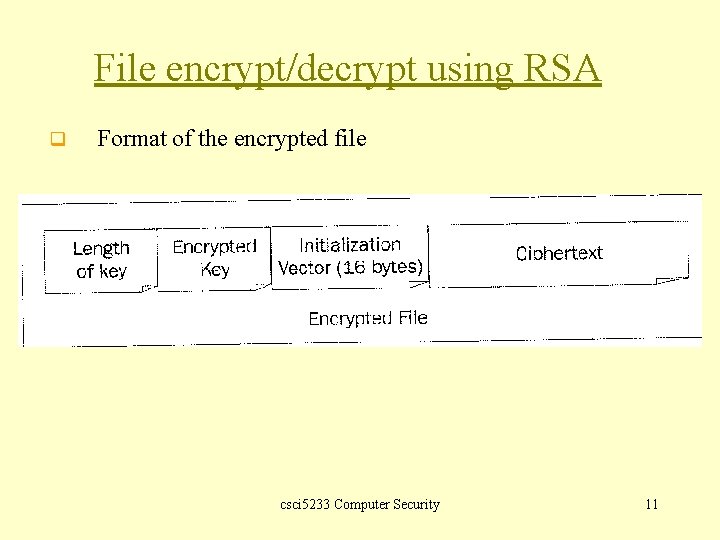
File encrypt/decrypt using RSA q Format of the encrypted file csci 5233 Computer Security 11

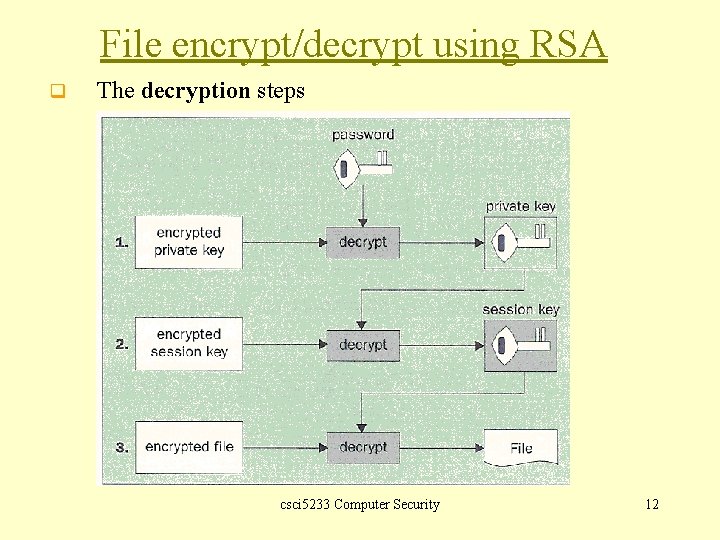
File encrypt/decrypt using RSA q The decryption steps csci 5233 Computer Security 12

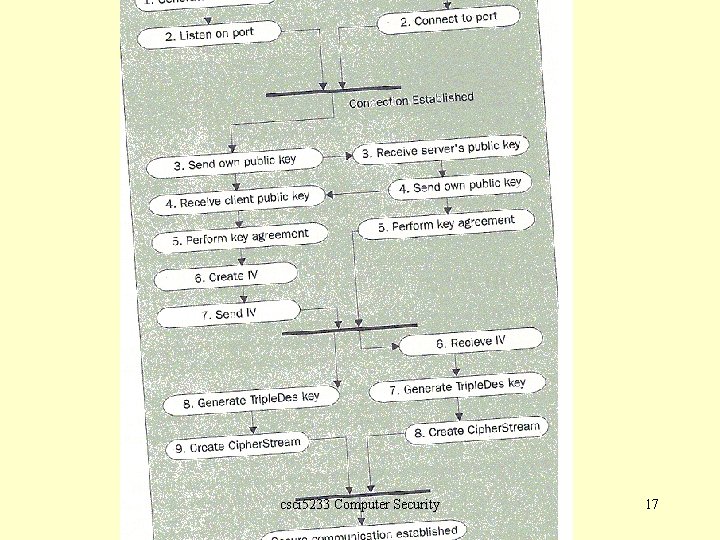
Key agreement q javax. crypto Class Key. Agreement This class provides the functionality of a key agreement (or key exchange) protocol. For each of the correspondents in the key exchange, do. Phase needs to be called. For example, if this key exchange is with one other party, do. Phase needs to be called once, with the last. Phase flag set to true. csci 5233 Computer Security 13

Key agreement Key do. Phase (Key key, boolean last. Phase) Executes the next phase of this key agreement with the given key that was received from one of the other parties involved in this key agreement. csci 5233 Computer Security 14

Key agreement q If this key exchange is with two other parties, do. Phase needs to be called twice, the first time setting the last. Phase flag to false, and the second time setting it to true. There may be any number of parties involved in a key exchange. q With the do. Phase method, Diffie-Hellman allows any number of public keys to be added to perform a key agreement. csci 5233 Computer Security 15

Key agreement q Once all the keys have been passed in with do. Phase( ), a call to generate. Secret( ) will perform the actual key agreement and return a byte array that is the shared secret. byte[] generate. Secret() Generates the shared secret and returns it in a new buffer. int generate. Secret (byte[] shared. Secret, int offset) Generates the shared secret, and places it into the buffer shared. Secret, beginning at offset inclusive. Secret. Key generate. Secret (String algorithm) Creates the shared secret and returns it as a Secret. Key object of the specified algorithm. csci 5233 Computer Security 16

csci 5233 Computer Security 17

Key agreement for a Chat Application q The sample application q Key. Agreement. Client. java q Key. Agreement. Server. java csci 5233 Computer Security 18

Next q Message digest, Digital signatures & Certificates (GS: 6) csci 5233 Computer Security 19