SYMMETRIC KEY ENCRYPTION PERFORMANCE ANALYSIS Tony Nguyen Symmetric
![Symmetric vs. Asymmetric [2] Key bits Algorithm RSA 112 3 DES k = 2048 Symmetric vs. Asymmetric [2] Key bits Algorithm RSA 112 3 DES k = 2048](https://slidetodoc.com/presentation_image/13279f9c461fa6138490ecc4a12730a7/image-3.jpg)
- Slides: 16

SYMMETRIC KEY ENCRYPTION PERFORMANCE ANALYSIS Tony Nguyen

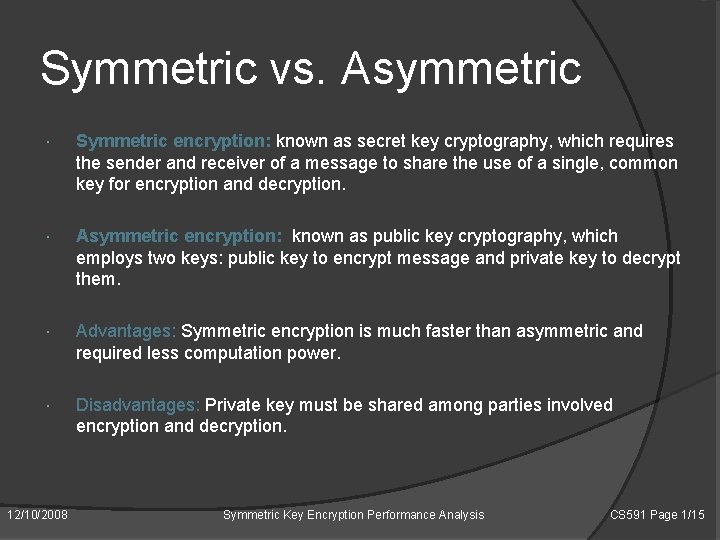
Symmetric vs. Asymmetric Symmetric encryption: known as secret key cryptography, which requires the sender and receiver of a message to share the use of a single, common key for encryption and decryption. Asymmetric encryption: known as public key cryptography, which employs two keys: public key to encrypt message and private key to decrypt them. Advantages: Symmetric encryption is much faster than asymmetric and required less computation power. Disadvantages: Private key must be shared among parties involved encryption and decryption. 12/10/2008 Symmetric Key Encryption Performance Analysis CS 591 Page 1/15
![Symmetric vs Asymmetric 2 Key bits Algorithm RSA 112 3 DES k 2048 Symmetric vs. Asymmetric [2] Key bits Algorithm RSA 112 3 DES k = 2048](https://slidetodoc.com/presentation_image/13279f9c461fa6138490ecc4a12730a7/image-3.jpg)
Symmetric vs. Asymmetric [2] Key bits Algorithm RSA 112 3 DES k = 2048 128 AES-128 k = 3072 192 AES-192 k = 7680 256 AES-256 k = 15360 [Ketu. File White Papers] 12/10/2008 Symmetric Key Encryption Performance Analysis CS 591 Page 2/15

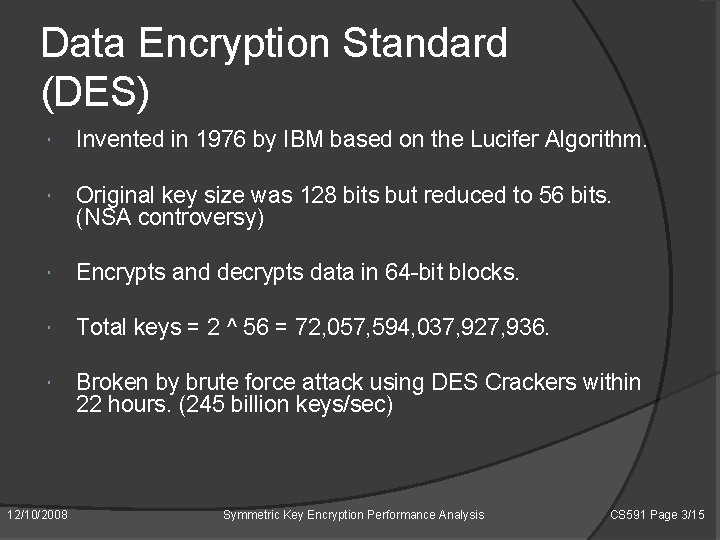
Data Encryption Standard (DES) Invented in 1976 by IBM based on the Lucifer Algorithm. Original key size was 128 bits but reduced to 56 bits. (NSA controversy) Encrypts and decrypts data in 64 -bit blocks. Total keys = 2 ^ 56 = 72, 057, 594, 037, 927, 936. Broken by brute force attack using DES Crackers within 22 hours. (245 billion keys/sec) 12/10/2008 Symmetric Key Encryption Performance Analysis CS 591 Page 3/15

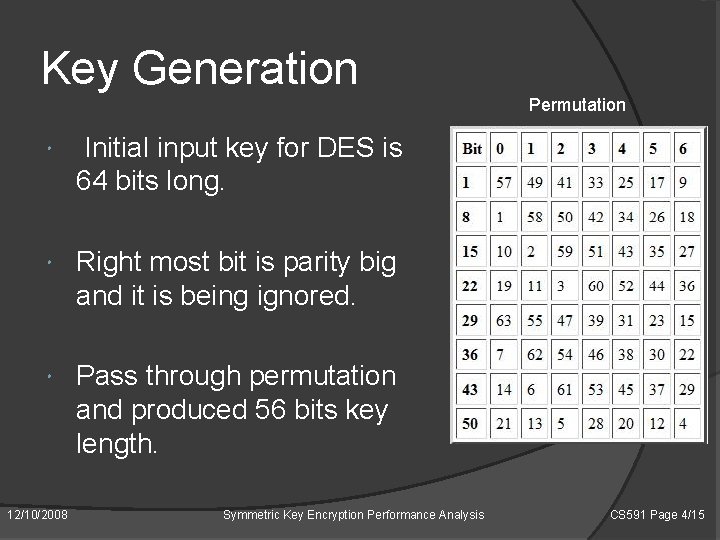
Key Generation Permutation Initial input key for DES is 64 bits long. Right most bit is parity big and it is being ignored. Pass through permutation and produced 56 bits key length. 12/10/2008 Symmetric Key Encryption Performance Analysis CS 591 Page 4/15

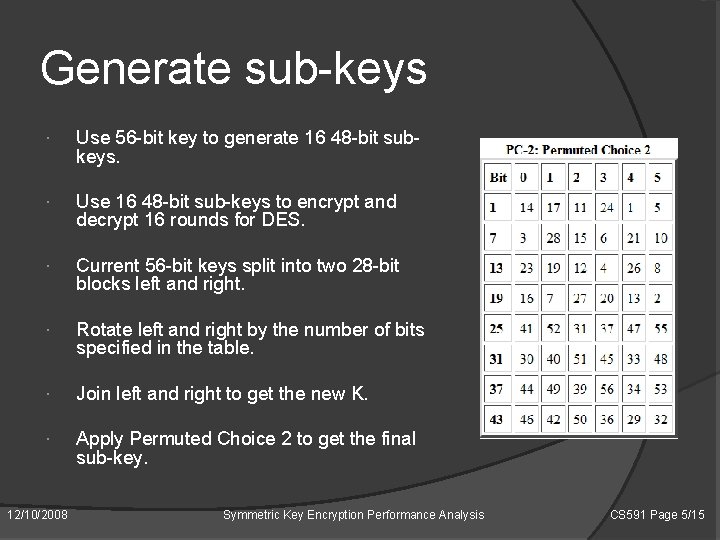
Generate sub-keys Use 56 -bit key to generate 16 48 -bit subkeys. Use 16 48 -bit sub-keys to encrypt and decrypt 16 rounds for DES. Current 56 -bit keys split into two 28 -bit blocks left and right. Rotate left and right by the number of bits specified in the table. Join left and right to get the new K. Apply Permuted Choice 2 to get the final sub-key. 12/10/2008 Symmetric Key Encryption Performance Analysis CS 591 Page 5/15

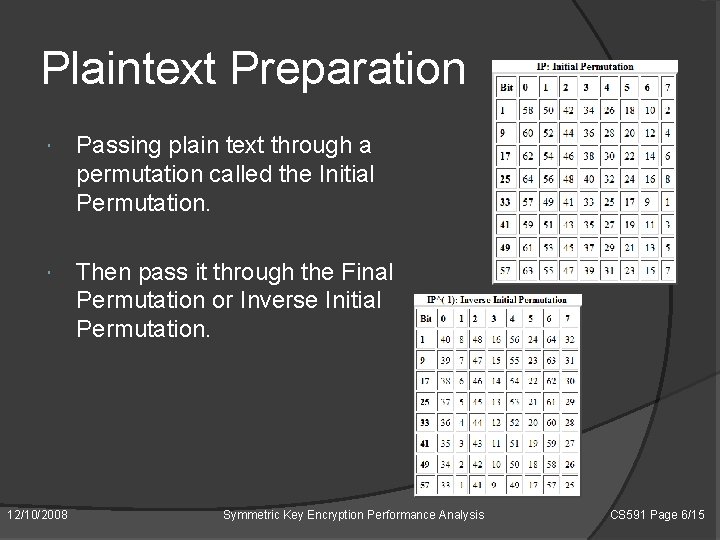
Plaintext Preparation Passing plain text through a permutation called the Initial Permutation. Then pass it through the Final Permutation or Inverse Initial Permutation. 12/10/2008 Symmetric Key Encryption Performance Analysis CS 591 Page 6/15

DES Core Function 64 -bit block of input data split into two halves, L and R. Data from R[I-1] is XOR with K[I] (16 sub-keys) and stored in the buffer. Data is split into 8 segments of 6 bits each and submit to S-boxes. Results passed into the Permutation. Data is now XOR with L[I-1] and moved into R[I]. R[I-1] is moved into L[I]. Repeat the core function until we have completed 16 rounds. When L[16] and R[16] obtained, they join back in the same fashion as they were split apart. Apply the Inverse Permutation to the pre-output which results in encrypted text. 12/10/2008 Symmetric Key Encryption Performance Analysis CS 591 Page 7/15

Modes of Operation Electronic Code Book (ECB): Data is divided into 64 -bit blocks and encrypted one at a time. It is fastest and easy to implement but cannot detect re-order contents. Cipher Block Chaining (CBC): Each block of encrypted cipher text is XOR with the next plaintext block. All blocks dependent on previous blocks. More secure than ECB because the extra XOR step. 12/10/2008 Symmetric Key Encryption Performance Analysis CS 591 Page 8/15

Triple DES Similar to DES. Invented by IBM in 1978. Encrypts and decrypts data in 64 -bit blocks. Key size: 192 bits. Modes of Operation: ECB and CBC. Very secure if implemented correctly. Safe to use until 2035. 12/10/2008 Symmetric Key Encryption Performance Analysis CS 591 Page 9/15

Blowfish Invented in 1993 by Bruce Schneier. 64 -bit block cipher. Key length: 32 to 448 bits. No effective cryptanalysis on the full-round version of Blowfish as of 2008. 12/10/2008 Symmetric Key Encryption Performance Analysis CS 591 Page 10/15

Advanced Encryption Standard (AES) Invented by Vincent Rijmen and Joan Daemen in 1998. Encrypts and decrypts data in 128 -bit blocks. Key size: 128, 192 or 256 bits. Structure: substitution-permutation network. Most popular and secure for symmetric key cryptography. No effective cryptanalysis of it has been found to date. 12/10/2008 Symmetric Key Encryption Performance Analysis CS 591 Page 11/15

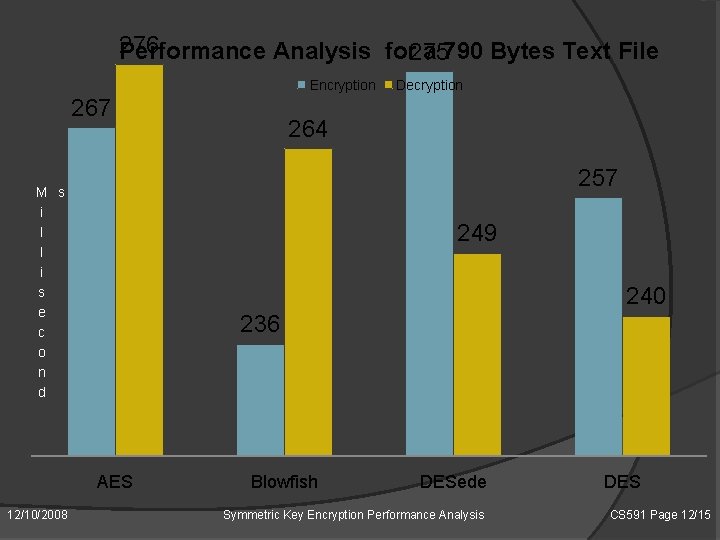
276 Performance Analysis for 275 a 790 Bytes Text File Encryption 267 264 257 M s i l l i s e c o n d 249 240 236 AES 12/10/2008 Decryption Blowfish DESede Symmetric Key Encryption Performance Analysis DES CS 591 Page 12/15

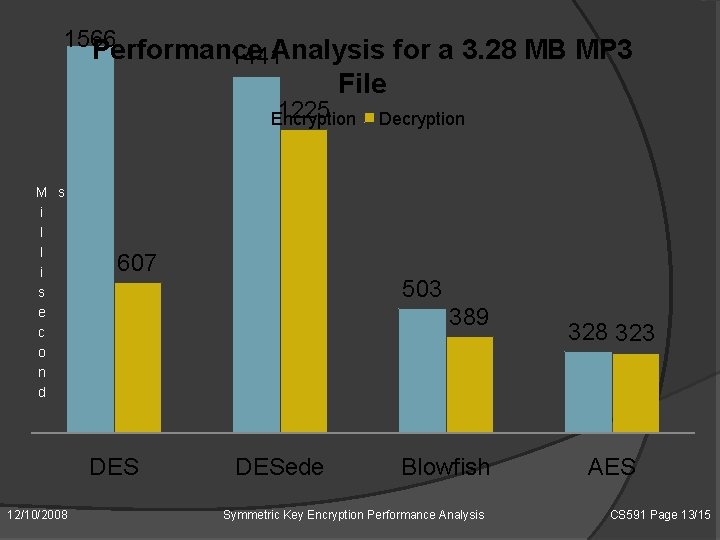
1566 Performance Analysis for a 3. 28 MB MP 3 1441 File 1225 Encryption M s i l l i s e c o n d 607 503 389 DES 12/10/2008 Decryption DESede Blowfish Symmetric Key Encryption Performance Analysis 328 323 AES CS 591 Page 13/15

Demo Java GUI application. Java Security Library. Maximum file size: 50 MB File restriction: Jar file Algorithms: DES, 3 DES, Blowfish, AES 12/10/2008 Symmetric Key Encryption Performance Analysis CS 591 Page 14/15

References DES Encryption, http: //www. tropsoft. com/strongenc/des. htm Triple Data Encryption Standard (TDES), http: //www. vocal. com/tdes. html The Blowfish Encryption Algorithm, http: //www. schneier. com/blowfish. html The Advanced Encryption Standard (Rijndael), http: //www. quadibloc. com/crypto/co 040401. htm The Enduring Value of Symmetric Encryption, http: //etoken. mikrobeta. com. tr/PDF/WP-Symmetric. Encryption. pdf Ketu. File White Papers, http: //www. ketufile. com/Symmetric_vs_Asymmetric_Encryption. pdf 12/10/2008 Symmetric Key Encryption Performance Analysis CS 591 Page 15/15