Chapter 20 Symmetric Encryption and Message Confidentiality Symmetric













- Slides: 39

Chapter 20 Symmetric Encryption and Message Confidentiality

Symmetric Encryption • Also referred to as: o o • Only alternative before public-key encryption in 1970’s o • Conventional encryption Secret-key or single-key encryption Still most widely used alternative Has five ingredients: o Plaintext - Encryption algorithm - Secret key – Ciphertext - Decryption algorithm • Encryption is computationally secure if: o Cost of breaking cipher exceeds value of information o Time required to break cipher exceeds the useful lifetime of the information • Usually very difficult to estimate the amount of effort required to break • Can estimate time/cost of a brute-force attack

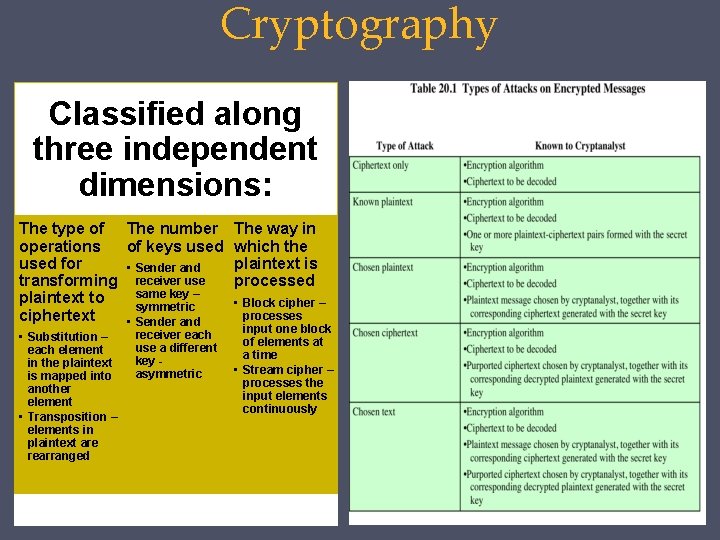
Cryptography Classified along three independent dimensions: The type of The number operations of keys used for • Sender and transforming receiver use same key – plaintext to symmetric ciphertext • Sender and • Substitution – each element in the plaintext is mapped into another element • Transposition – elements in plaintext are rearranged receiver each use a different key asymmetric The way in which the plaintext is processed • Block cipher – processes input one block of elements at a time • Stream cipher – processes the input elements continuously

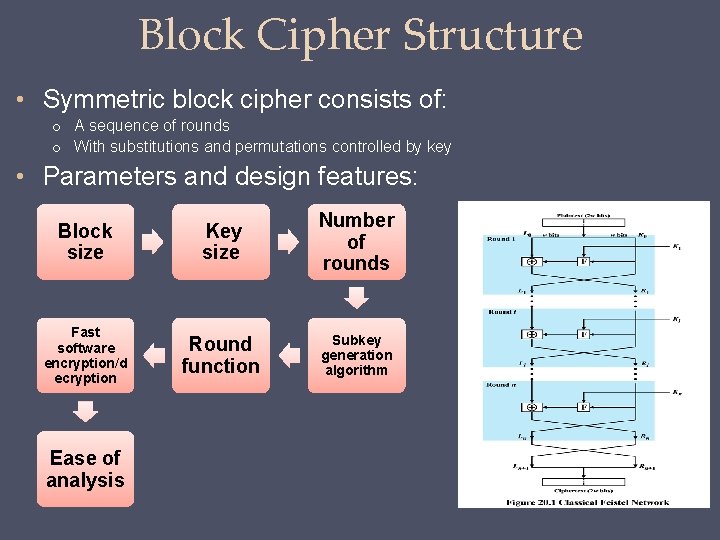
Block Cipher Structure • Symmetric block cipher consists of: o A sequence of rounds o With substitutions and permutations controlled by key • Parameters and design features: Block size Key size Number of rounds Fast software encryption/d ecryption Round function Subkey generation algorithm Ease of analysis

DES • Most Widely used Encryption • Minor variation on Feistel Network • Modern symmetric-key cryptosystems o Data Encryption Standard (DES) • Adopted in 1976 - Block size = 64 bits - Key length = 56 bits o Advanced Encryption Standard (AES) • Adopted in 2000 - Block sizes = 128, 192, or 256 bits • Key lengths = 128, 192, or 256 bits • 1973: NBS (now NIST) solicits proposals for crypto algorithm which: o Provides a high level of security - Completely specified and easy to understand - Is available royalty-free and Is efficient • • Any 56 -bit string can be a DES key There are 256 keys o 72, 057, 594, 037, 927, 936 DES keys • Test one trillion keys per second o • 2 hours to find the key A very small number of “weak keys”

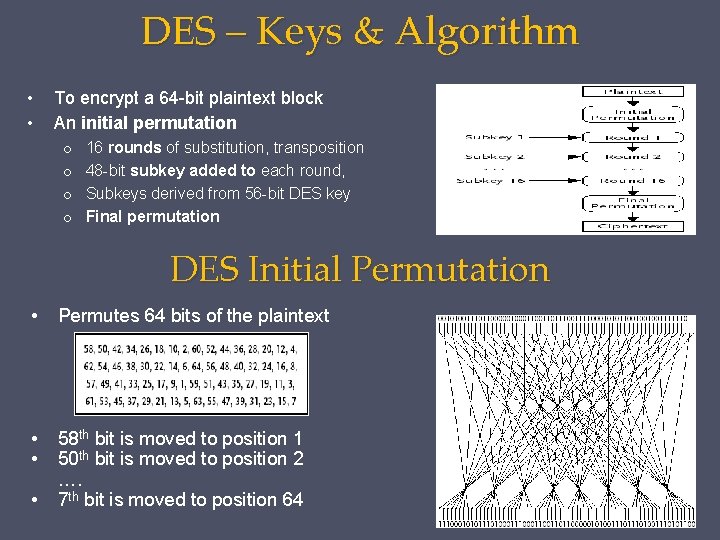
DES – Keys & Algorithm • • To encrypt a 64 -bit plaintext block An initial permutation o o 16 rounds of substitution, transposition 48 -bit subkey added to each round, Subkeys derived from 56 -bit DES key Final permutation DES Initial Permutation • Permutes 64 bits of the plaintext • • 58 th bit is moved to position 1 50 th bit is moved to position 2 …. 7 th bit is moved to position 64 •

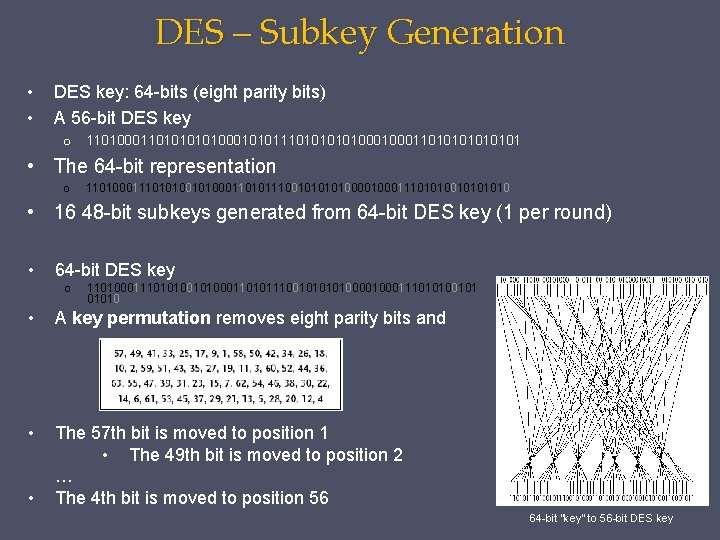
DES – Subkey Generation • • DES key: 64 -bits (eight parity bits) A 56 -bit DES key o 11010001101010001010111010100011010101 • The 64 -bit representation o 1101000111010100011010111001010000111010101010 • 16 48 -bit subkeys generated from 64 -bit DES key (1 per round) • 64 -bit DES key o 11010001110101000110101110010100001110101001010 • A key permutation removes eight parity bits and • The 57 th bit is moved to position 1 • The 49 th bit is moved to position 2 … The 4 th bit is moved to position 56 • 64 -bit “key” to 56 -bit DES key

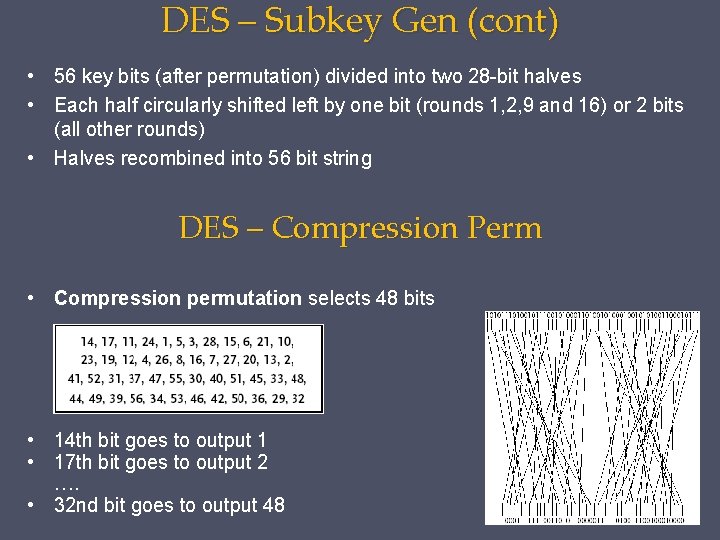
DES – Subkey Gen (cont) • 56 key bits (after permutation) divided into two 28 -bit halves • Each half circularly shifted left by one bit (rounds 1, 2, 9 and 16) or 2 bits (all other rounds) • Halves recombined into 56 bit string DES – Compression Perm • Compression permutation selects 48 bits • 14 th bit goes to output 1 • 17 th bit goes to output 2 …. • 32 nd bit goes to output 48

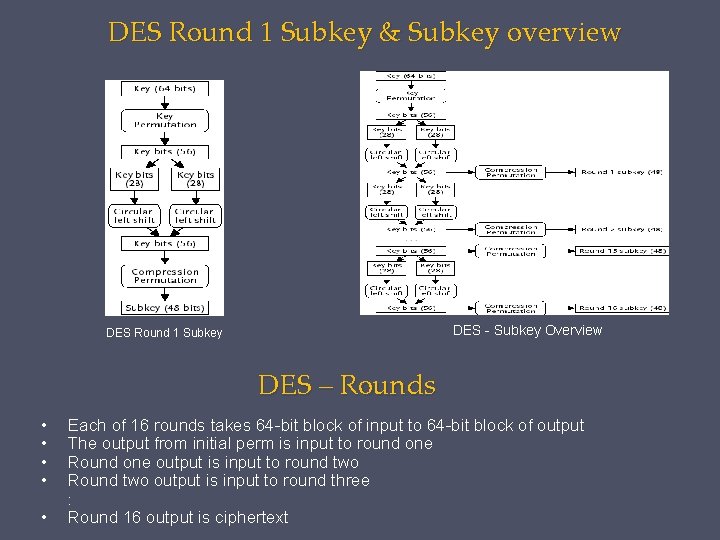
DES Round 1 Subkey & Subkey overview DES - Subkey Overview DES Round 1 Subkey DES – Rounds • • • Each of 16 rounds takes 64 -bit block of input to 64 -bit block of output The output from initial perm is input to round one Round one output is input to round two Round two output is input to round three Round 16 output is ciphertext

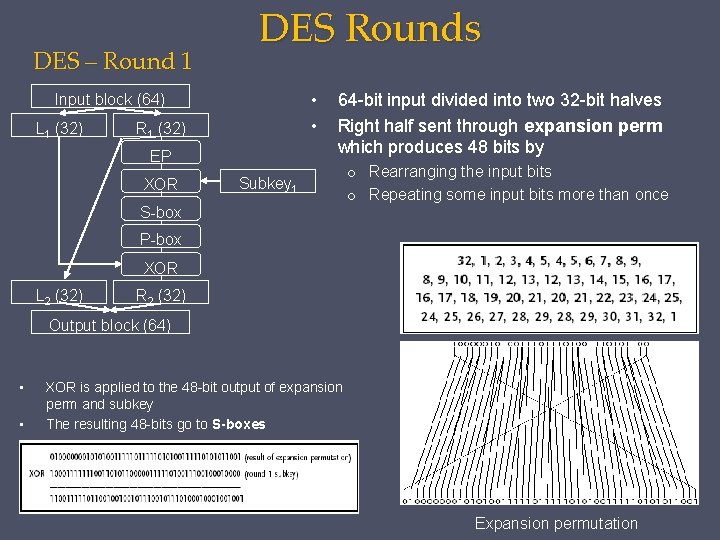
DES – Round 1 DES Rounds • • Input block (64) L 1 (32) R 1 (32) EP XOR 64 -bit input divided into two 32 -bit halves Right half sent through expansion perm which produces 48 bits by Subkey 1 S-box o Rearranging the input bits o Repeating some input bits more than once P-box XOR L 2 (32) R 2 (32) Output block (64) • • XOR is applied to the 48 -bit output of expansion perm and subkey The resulting 48 -bits go to S-boxes Expansion permutation

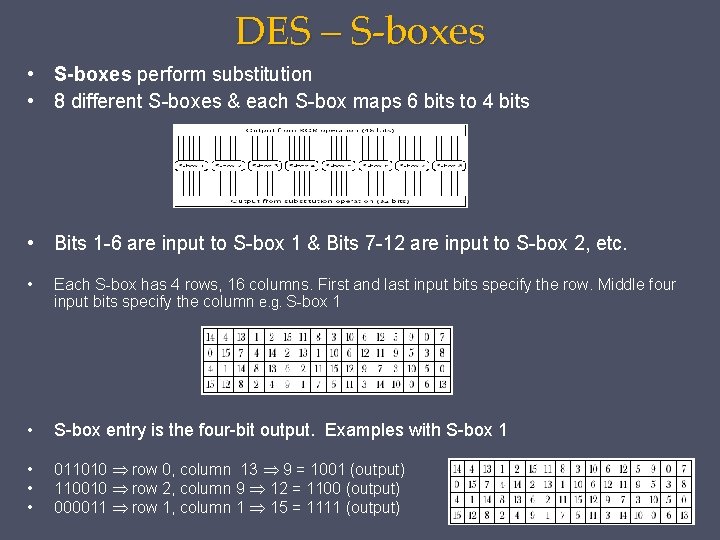
DES – S-boxes • S-boxes perform substitution • 8 different S-boxes & each S-box maps 6 bits to 4 bits • Bits 1 -6 are input to S-box 1 & Bits 7 -12 are input to S-box 2, etc. • Each S-box has 4 rows, 16 columns. First and last input bits specify the row. Middle four input bits specify the column e. g. S-box 1 • S-box entry is the four-bit output. Examples with S-box 1 • • • 011010 row 0, column 13 9 = 1001 (output) 110010 row 2, column 9 12 = 1100 (output) 000011 row 1, column 1 15 = 1111 (output)

DES – P-box • 32 -bit output of S-boxes goes to P-box • P-box permutes the bits o The first bit is moved to position 16 o The second bit is moved to position 7 : o The thirty-second bit is moved into position 25 DES – Second XOR Operation • Output of P-box is XORed with the left half of 64 -bit input block • 32 -bit output of the XOR operation: o 01101101100011010010010

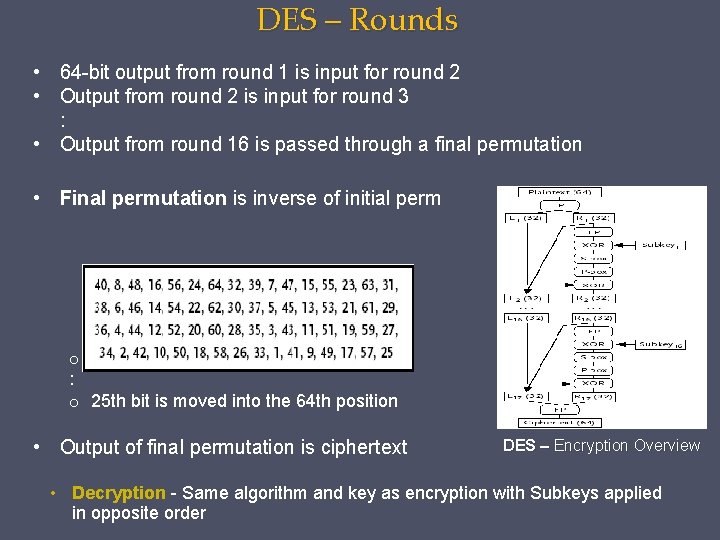
DES – Rounds • 64 -bit output from round 1 is input for round 2 • Output from round 2 is input for round 3 : • Output from round 16 is passed through a final permutation • Final permutation is inverse of initial perm o 40 th bit is moved into the 1 st position : o 25 th bit is moved into the 64 th position • Output of final permutation is ciphertext DES – Encryption Overview • Decryption - Same algorithm and key as encryption with Subkeys applied in opposite order

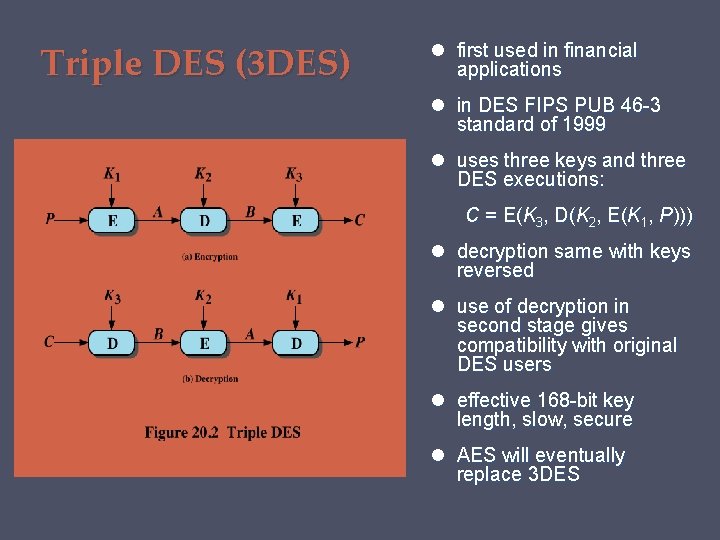
Triple DES (3 DES) first used in financial applications in DES FIPS PUB 46 -3 standard of 1999 uses three keys and three DES executions: C = E(K 3, D(K 2, E(K 1, P))) decryption same with keys reversed use of decryption in second stage gives compatibility with original DES users effective 168 -bit key length, slow, secure AES will eventually replace 3 DES

AES • 1997: NIST requests proposals for a new Advanced Encryption Standard (AES) to replace DES • NIST required that the algorithm be: o o o A symmetric-key cryptosystem A block cipher Capable of supporting a block size of 128 bits Capable of supporting key lengths of 128, 192, and 256 bits Available on a worldwide, non-exclusive, royalty-free basis • Evaluation criteria: o Security - soundness of the mathematical basis and the results of analysis by the research community o Computational efficiency, memory requirements, flexibility, and simplicity

AES – Round 1 Results • After eight months of analysis and public comment, NIST: o Eliminated DEAL, Frog, HPC, Loki 97, and Magenta • Had what NIST considered major security flaws • Were among the slowest algorithms submitted o Eliminated Crypton, DFC, E 2, and SAFER+ • Had what NIST considered minor security flaws • Had unimpressive characteristics on the other evaluation criteria o Eliminated CAST-256 • Had mediocre speed and large ROM requirements • Five candidates, MARS, RC 6, Rijndael, Serpent, and Twofish, advanced to the second round • Analysis and public comment on the five finalists circa 2000 o Selects Rijndael • Adequate security margin, fast encryption, decryption, and key setup speeds, low RAM and ROM requirements

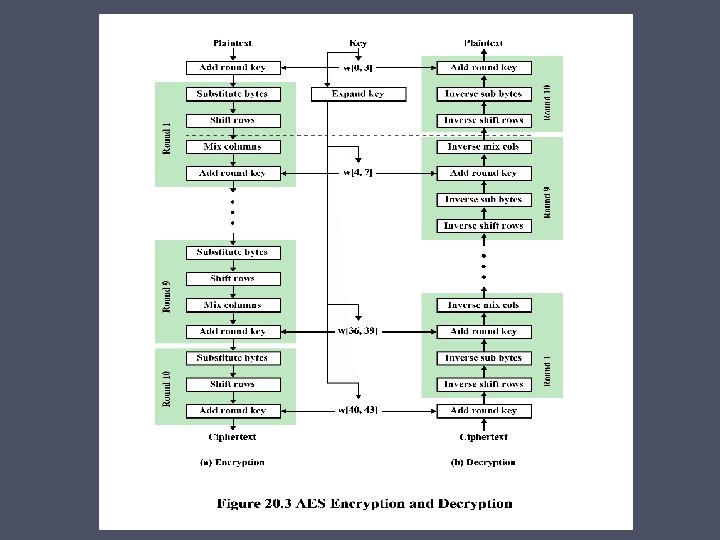
AES – Rijndael Algorithm • Symmetric-key block cipher o Block sizes are 128, 192, or 256 bits o Key lengths are 128, 192, or 256 bits • Performs several rounds of operations to transform each block of plaintext into a block of ciphertext o The number of rounds depends on the block size and the length of the key: • Nine regular rounds if both the block and key are 128 bits • Eleven regular rounds if either the block or key are 192 bits • Thirteen regular rounds if either the block or key is 256 bits o One, slightly different, final round is performed after the regular rounds

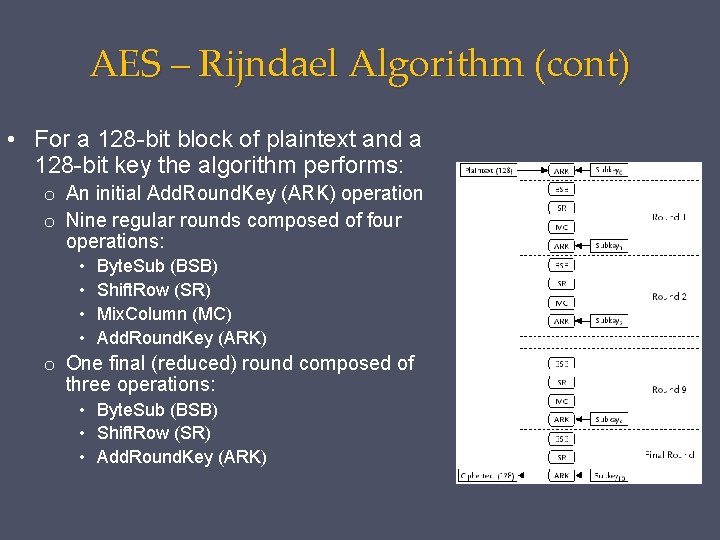
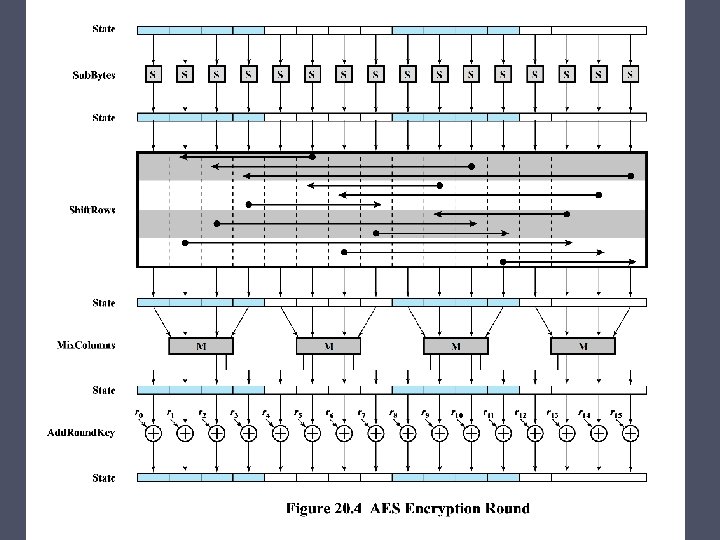
AES – Rijndael Algorithm (cont) • For a 128 -bit block of plaintext and a 128 -bit key the algorithm performs: o An initial Add. Round. Key (ARK) operation o Nine regular rounds composed of four operations: • • Byte. Sub (BSB) Shift. Row (SR) Mix. Column (MC) Add. Round. Key (ARK) o One final (reduced) round composed of three operations: • Byte. Sub (BSB) • Shift. Row (SR) • Add. Round. Key (ARK)

AES – Rijndael Keys • Keys are expressed as 128 -bit (or bigger) quantities • Keyspace contains at least 2128 elements: o 340, 282, 366, 920, 938, 463, 374, 607, 431, 768, 211, 456 • Exhaustive search at one trillion keys per second takes: o 1 x 1019 years (the universe is about 1 x 1010 years old) • Blocks &keys are represented as a two-dimensional array of bytes with four rows and four columns: o Block = 128 bits = 16 bytes = b 0 , b 1, . , b 15 o Key = 128 bits = 16 bytes = k 0 , k 1, . k 15


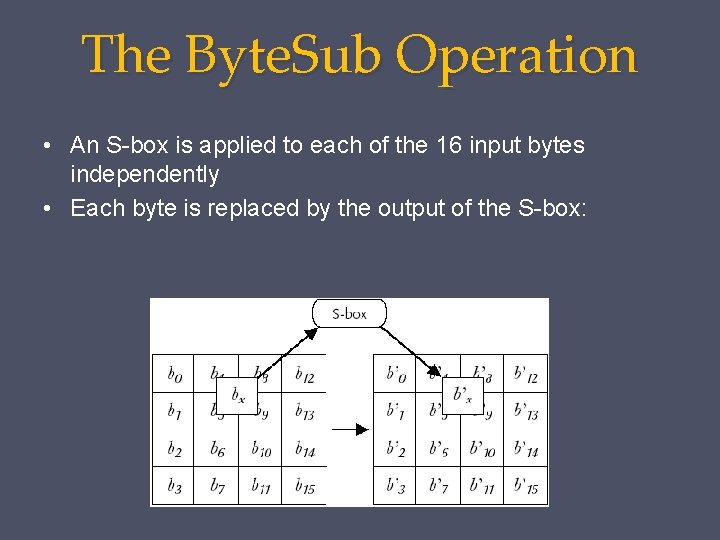
The Byte. Sub Operation • An S-box is applied to each of the 16 input bytes independently • Each byte is replaced by the output of the S-box:

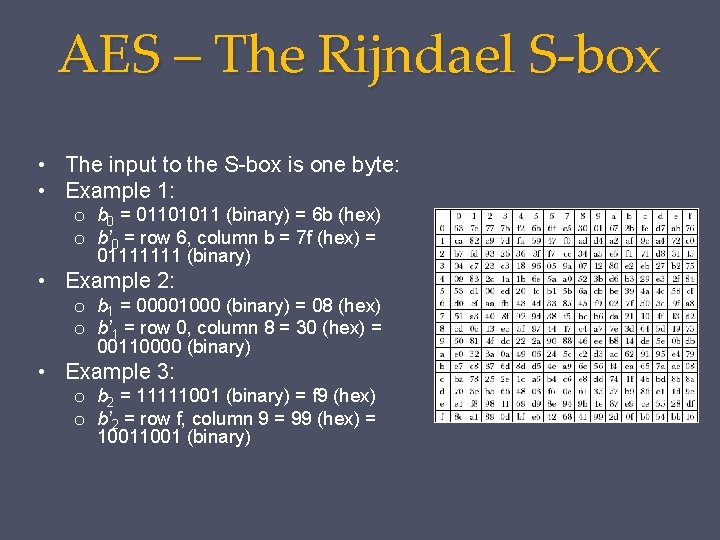
AES – The Rijndael S-box • The input to the S-box is one byte: • Example 1: o b 0 = 01101011 (binary) = 6 b (hex) o b’ 0 = row 6, column b = 7 f (hex) = 01111111 (binary) • Example 2: o b 1 = 00001000 (binary) = 08 (hex) o b’ 1 = row 0, column 8 = 30 (hex) = 00110000 (binary) • Example 3: o b 2 = 11111001 (binary) = f 9 (hex) o b’ 2 = row f, column 9 = 99 (hex) = 1001 (binary)

AES - Shift. Row Operation • Each row of the input is circularly left shifted: o o First row by zero places Second row by one place Third row by two places Fourth row by three places

Mix Columns and Add Key • Mix columns o Operates on each column individually o Mapping each byte to a new value that is a function of all four bytes in the column o Use of equations over finite fields o To provide good mixing of bytes in column • Add round key o Simply XOR State with bits of expanded key o Security from complexity of round key expansion and other stages of AES

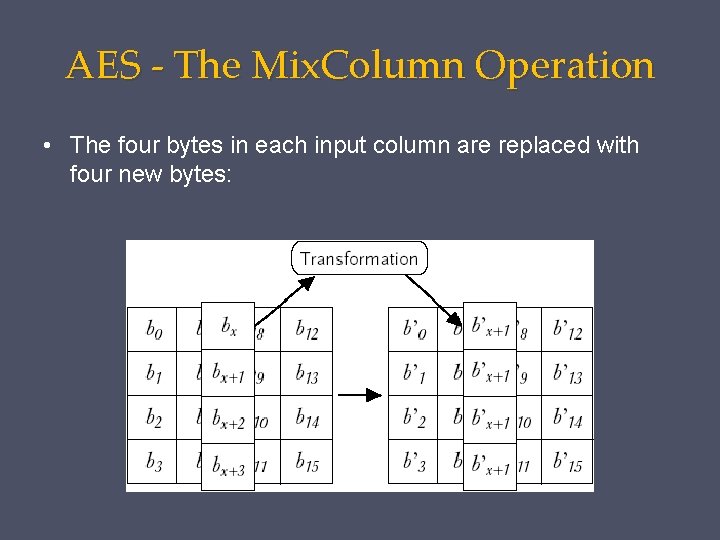
AES - The Mix. Column Operation • The four bytes in each input column are replaced with four new bytes:

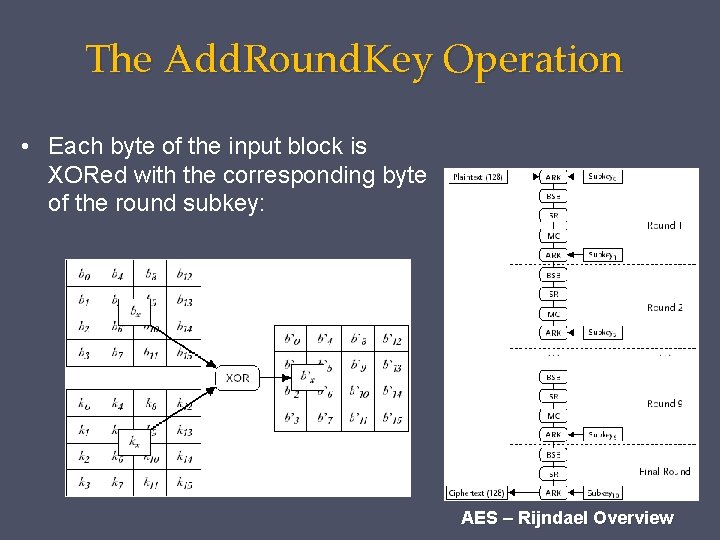
The Add. Round. Key Operation • Each byte of the input block is XORed with the corresponding byte of the round subkey: AES – Rijndael Overview


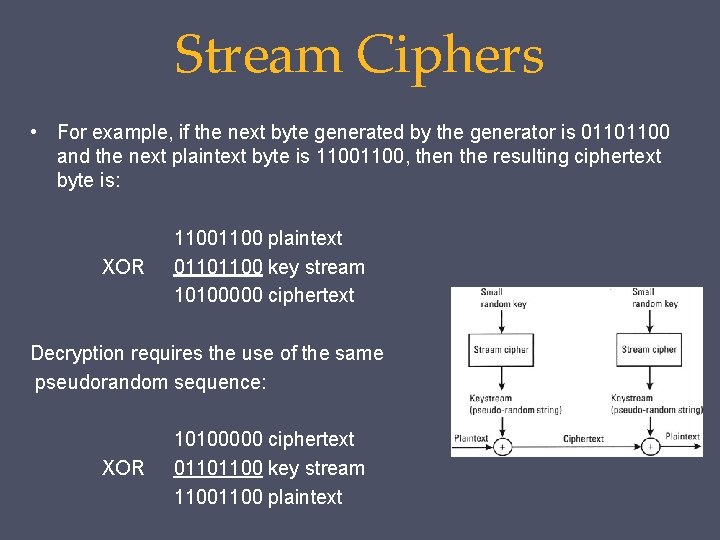
Stream Ciphers • A typical stream cipher encrypts plaintext one byte at a time, although a stream cipher may be designed to operate on one bit at a time or on units larger than a byte at a time. • A key is input to a pseudorandom bit generator that produces a stream of 8 -bit numbers that are apparently random - unpredictable without knowledge of the input key. • The output of the generator, called a keystream, is combined one byte at a time with the plaintext stream using the bitwise exclusive-OR (XOR) operation. • For applications that require encryption/decryption of a stream of data, such as over a data communications channel or a browser/Web link, a stream cipher might be the better alternative. For applications that deal with blocks of data, such as file transfer, e-mail, and database, block -4 ciphers may be more appropriate. However, either type of cipher can be used in any application.

Stream Ciphers • For example, if the next byte generated by the generator is 01101100 and the next plaintext byte is 1100, then the resulting ciphertext byte is: XOR 1100 plaintext 01101100 key stream 10100000 ciphertext Decryption requires the use of the same pseudorandom sequence: XOR 10100000 ciphertext 01101100 key stream 1100 plaintext

design considerations for a stream cipher • 1. The encryption sequence should have a large period. A pseudorandom number generator uses a function that produces a deterministic stream of bits that eventually repeats. The longer the period of repeat the more difficult it will be to do cryptanalysis. • 2. The keystream should approximate the properties of a true random number stream as close as possible. For example, there should be an approximately equal number of 1 s and 0 s. If the keystream is treated as a stream of bytes, then all of the 256 possible byte values should appear approximately equally often i. e. Confusion/Diffusion - Shannon • 3. With a properly designed pseudorandom number generator, a stream cipher can be as secure as block cipher of comparable key length. The primary advantage of a stream cipher is that stream ciphers are almost always faster and use far less code than do block ciphers. • 4. The advantage of a block cipher is that you can reuse keys. However, if two plaintexts are encrypted with the same key using a stream cipher, then cryptanalysis is often quite simple. If the two ciphertext streams are XORed together, the result is the XOR of the original plaintexts. If the plaintexts are text strings, credit card numbers, or other byte streams with known properties, then cryptanalysis may be successful.

Stream Ciphers • Remember only showing encoding of 1 st byte below. . . plain test 1 "h"ello key cipher 1 01101101 10110011 1 1 0 "h" encoded after XOR plain text 2 "B"ye key cipher 2 10011100 10110011 0 0 1 1 1 1 "B" encoded after XOR Both ciphers captured cipher 1 cipher 2 XOR operation 1 1 0 "h" 0 0 1 1 1 1 "B" 11110001 Crib Dragging is then used to crack the cipher: https: //crypto. stackexchange. com/questions/59/takingadvantage-of-one-time-pad-key-reuse

The danger of Key Re-use Reusing the same key multiple times is called giving the encryption 'depth' - and it is intuitive that the more depth given, the more likely it is that information about the plaintext is contained within the encrypted text.

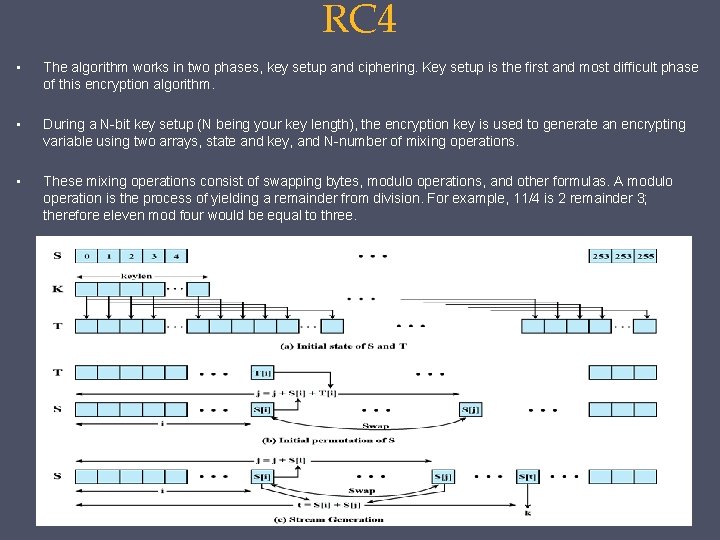
RC 4 • The RC 4 Encryption Algorithm, developed by Ronald Rivest of RSA, is a shared key stream cipher algorithm requiring a secure exchange of a shared key. • The symmetric key algorithm is used identically for encryption and decryption such that the data stream is simply XORed with the generated key sequence. • The algorithm is serial as it requires successive exchanges of state entries based on the key sequence. Hence implementations can be very computationally intensive. • The RC 4 encryption algorithm is used by standards such as IEEE 802. 11 within WEP (Wireless Encryption Protocol) using 40 and 128 -bit keys. Published procedures exist for cracking the security measures as implemented in WEP. • In the RC 4 encryption algorithm, the key stream is completely independent of the plaintext used. An 8 * 8 S-Box (S 0 S 255), where each of the entries is a permutation of the numbers 0 to 255, and the permutation is a function of the variable length key. There are two counters i, and j, both initialized to 0 used in the algorithm. • The algorithm uses a variable length key from 1 to 256 bytes to initialize a 256 -byte state table. The state table is used for subsequent generation of pseudo-random bytes and then to generate a pseudo-random stream which is XORed with the plaintext to give the ciphertext. Each element in the state table is swapped at least once. • The key is often limited to 40 bits, because of export restrictions but it is sometimes used as a 128 bit key. It has the capability of using keys between 1 and 2048 bits. RC 4 is used in many commercial software packages such as Lotus Notes and Oracle Secure SQL.

RC 4 • The algorithm works in two phases, key setup and ciphering. Key setup is the first and most difficult phase of this encryption algorithm. • During a N-bit key setup (N being your key length), the encryption key is used to generate an encrypting variable using two arrays, state and key, and N-number of mixing operations. • These mixing operations consist of swapping bytes, modulo operations, and other formulas. A modulo operation is the process of yielding a remainder from division. For example, 11/4 is 2 remainder 3; therefore eleven mod four would be equal to three.

RC 4 Strengths of RC 4 • The difficulty of knowing where any value is in the table. • The difficulty of knowing which location in the table is used to select each value in the sequence. • A particular RC 4 Algorithm key can be used only once. • Encryption is about 10 times faster than DES. Limitations of RC 4 • One in every 256 keys can be a weak key. These keys are identified by cryptanalysis that is able to find circumstances under which one of more generated bytes are strongly correlated with a few bytes of the key.

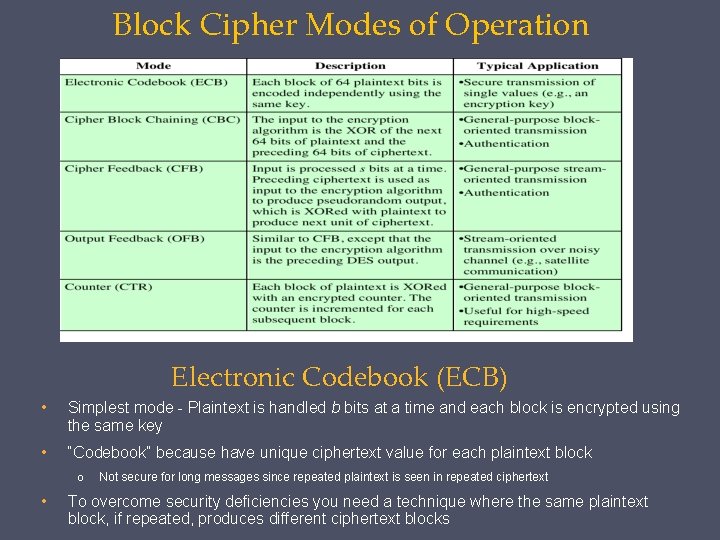
Block Cipher Modes of Operation Electronic Codebook (ECB) • Simplest mode - Plaintext is handled b bits at a time and each block is encrypted using the same key • “Codebook” because have unique ciphertext value for each plaintext block o • Not secure for long messages since repeated plaintext is seen in repeated ciphertext To overcome security deficiencies you need a technique where the same plaintext block, if repeated, produces different ciphertext blocks

Block Cipher Modes of Operation

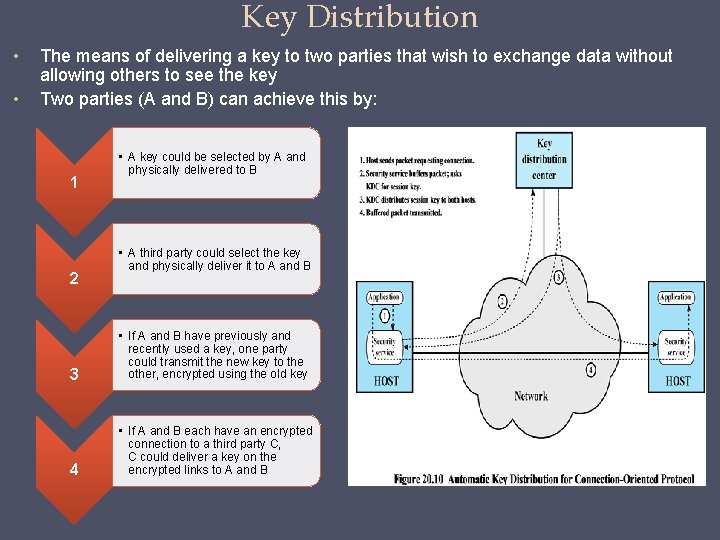
Key Distribution • • The means of delivering a key to two parties that wish to exchange data without allowing others to see the key Two parties (A and B) can achieve this by: 1 2 • A key could be selected by A and physically delivered to B • A third party could select the key and physically deliver it to A and B 3 • If A and B have previously and recently used a key, one party could transmit the new key to the other, encrypted using the old key 4 • If A and B each have an encrypted connection to a third party C, C could deliver a key on the encrypted links to A and B

Summary • Symmetric encryption principles o Cryptography o Cryptanalysis o Feistel cipher structure • Data encryption standard o Triple DES • Advanced encryption standard o Overview of the algorithm o Algorithm details • Stream ciphers and RC 4 o Stream cipher structure o The RC 4 algorithm • Cipher block modes of operation o Electronic codebook mode o Cipher block chaining mode o Cipher feedback mode o Counter mode • Location of symmetric encryption devices • Key distribution