Cryptography SYMMETRIC CRYPTOSYSTEMS Symmetric Cryptosystems 1272020 pag 2


























- Slides: 51

Cryptography

SYMMETRIC CRYPTOSYSTEMS Symmetric Cryptosystems 12/7/2020 | pag. 2

Block Ciphers: Classical examples • Affine Cipher • Affine Linear and Linear Cipher • Vigenère • Hill We needed some linear algebra! Symmetric Cryptosystems 12/7/2020 | pag. 3

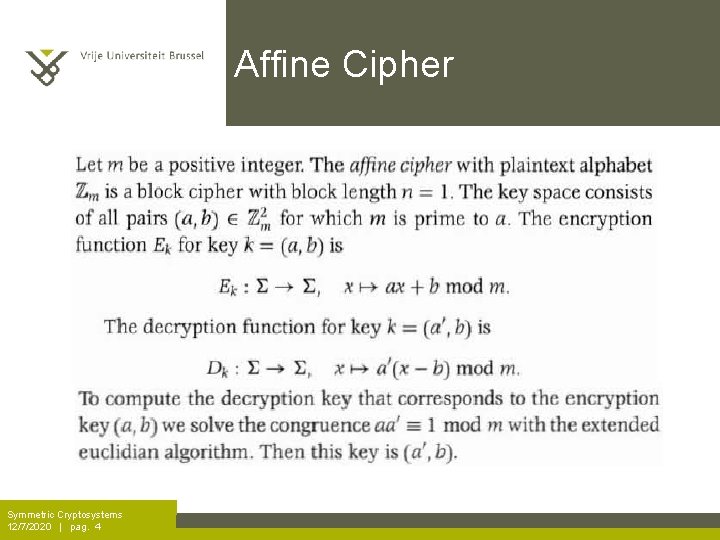
Affine Cipher Symmetric Cryptosystems 12/7/2020 | pag. 4

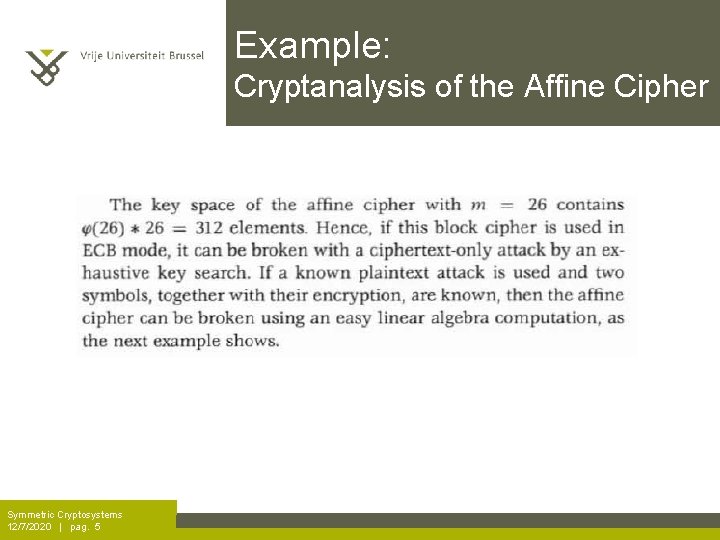
Example: Cryptanalysis of the Affine Cipher Symmetric Cryptosystems 12/7/2020 | pag. 5

Intermezzo: Matrices over Rings Cryptography 12/7/2020 | pag. 6

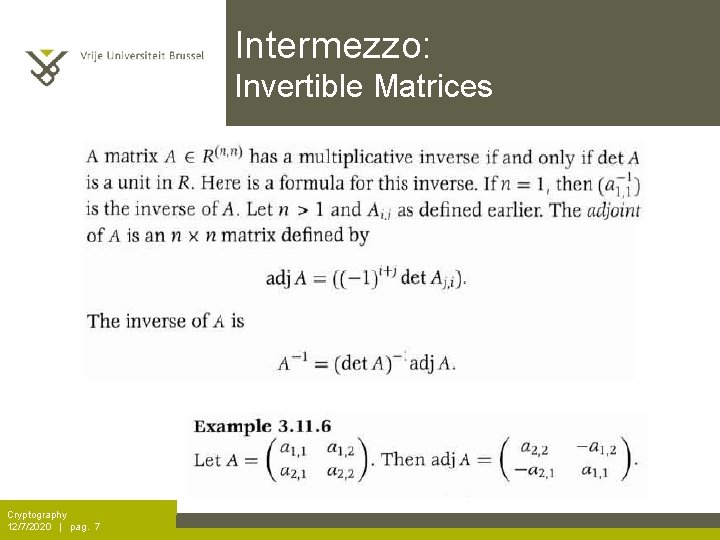
Intermezzo: Invertible Matrices Cryptography 12/7/2020 | pag. 7

Intermezzo: Invertible Matrices Cryptography 12/7/2020 | pag. 8

Intermezzo: Invertible Matrices Cryptography 12/7/2020 | pag. 9

Intermezzo: Invertible Matrices Cryptography 12/7/2020 | pag. 10

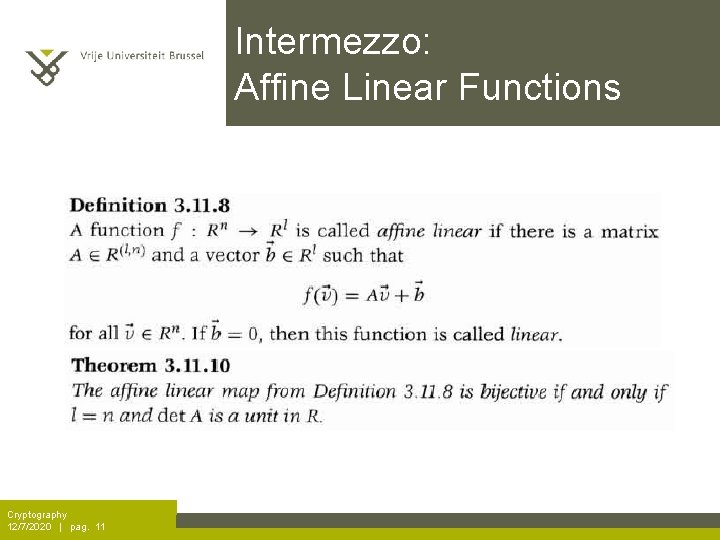
Intermezzo: Affine Linear Functions Cryptography 12/7/2020 | pag. 11

Intermezzo: Affine Linear Functions Cryptography 12/7/2020 | pag. 12

Affine Linear Cipher Cryptography 12/7/2020 | pag. 13

Affine Linear Cipher Cryptography 12/7/2020 | pag. 14

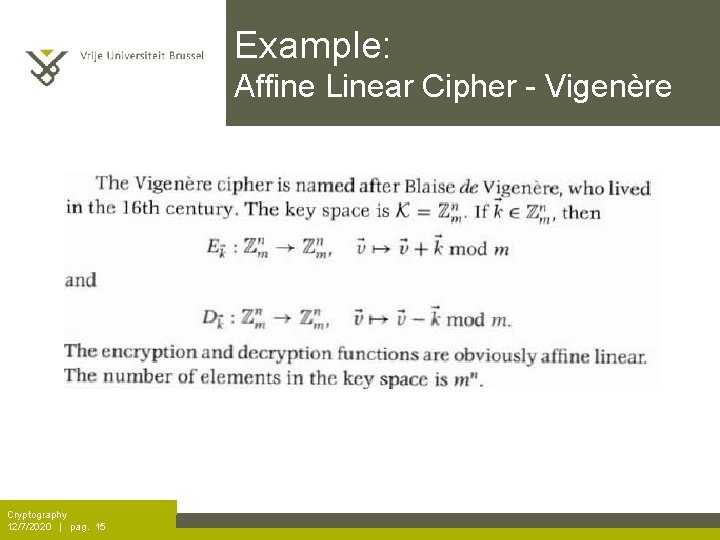
Example: Affine Linear Cipher - Vigenère Cryptography 12/7/2020 | pag. 15

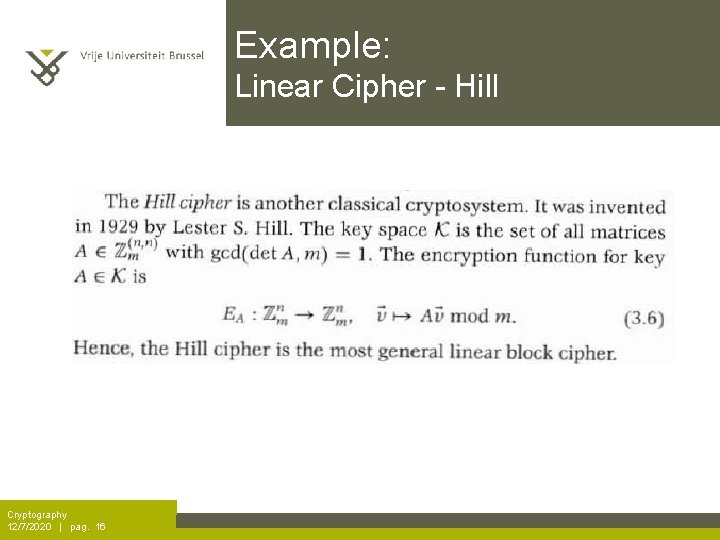
Example: Linear Cipher - Hill Cryptography 12/7/2020 | pag. 16

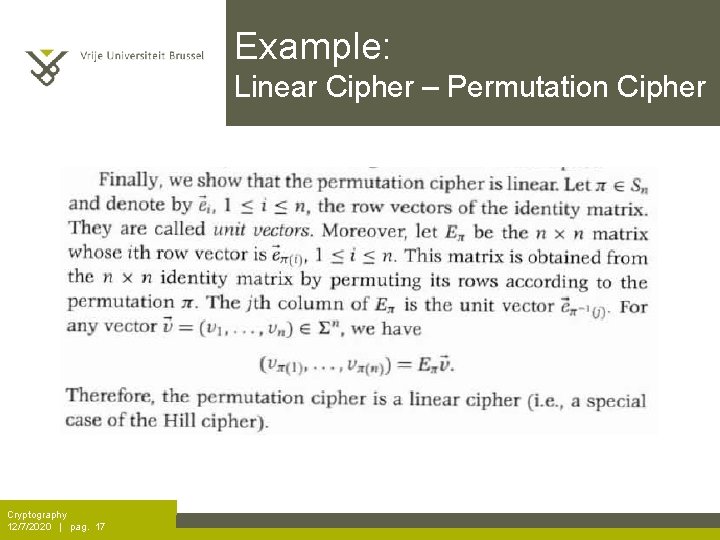
Example: Linear Cipher – Permutation Cipher Cryptography 12/7/2020 | pag. 17

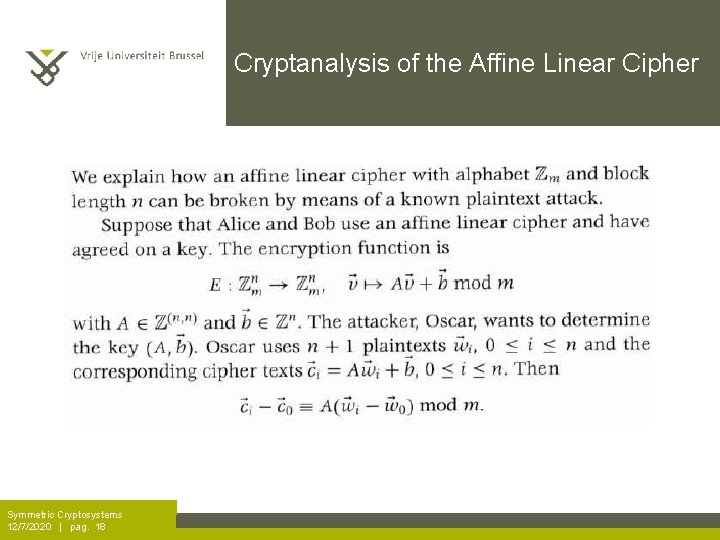
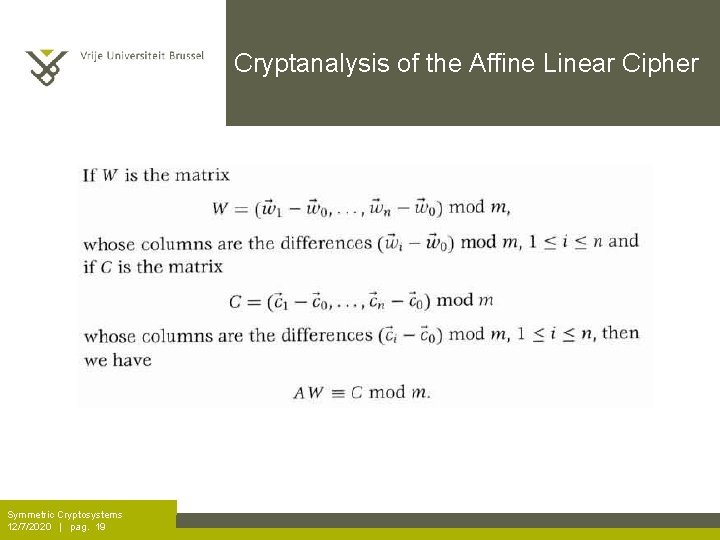
Cryptanalysis of the Affine Linear Cipher Symmetric Cryptosystems 12/7/2020 | pag. 18

Cryptanalysis of the Affine Linear Cipher Symmetric Cryptosystems 12/7/2020 | pag. 19

Cryptanalysis of the Affine Linear Cipher Symmetric Cryptosystems 12/7/2020 | pag. 20

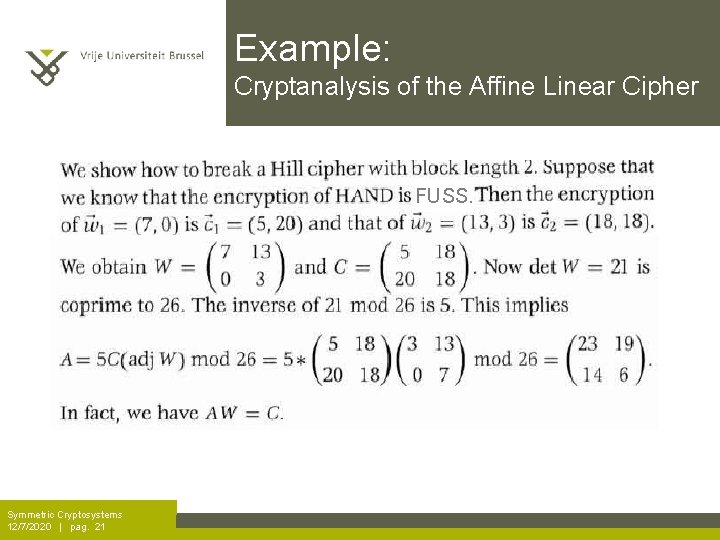
Example: Cryptanalysis of the Affine Linear Cipher FUSS. Symmetric Cryptosystems 12/7/2020 | pag. 21

Block Ciphers: Remark Secure block ciphers must not be (affine) linear or easy to approximate by linear functions!!! Cryptography 12/7/2020 | pag. 22

Block Ciphers: Remark Implementation of a (non-linear!) substitution in a block cipher often occurs through a look-up table, called S-box. Cryptography 12/7/2020 | pag. 23

Block Ciphers: Advanced examples • DES – Feistel Cipher • AES – Rijndael Symmetric Cryptosystems 12/7/2020 | pag. 24

DES Cryptography 12/7/2020 | pag. 25

DES: Feistel Cipher An iterated block cipher is a block cipher involving the sequential repetition of an internal function called rounds. (iterated) Cryptography 12/7/2020 | pag. 26

DES: Feistel Cipher Cryptography 12/7/2020 | pag. 27

DES: Feistel Cipher Cryptography 12/7/2020 | pag. 28

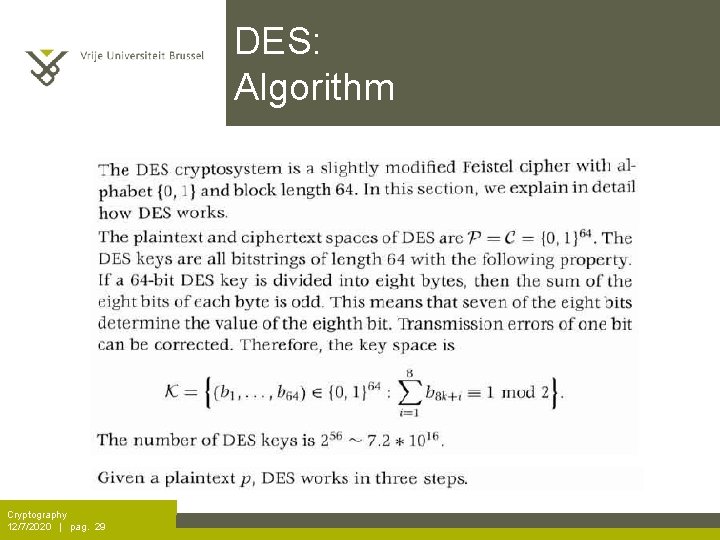
DES: Algorithm Cryptography 12/7/2020 | pag. 29

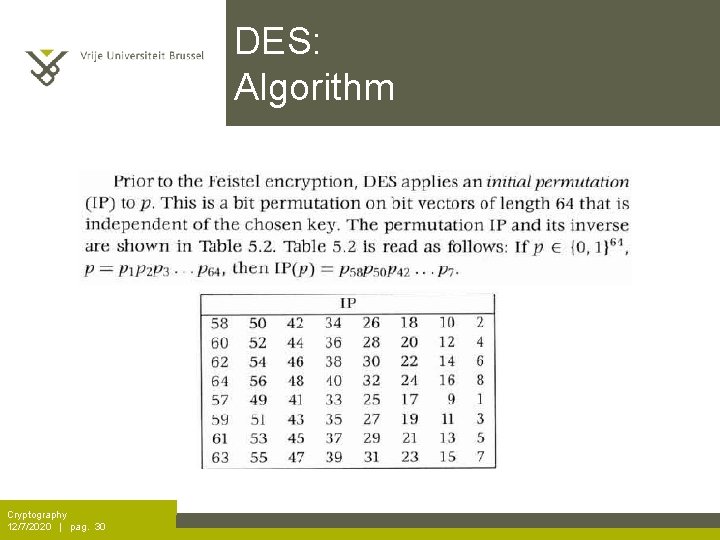
DES: Algorithm Cryptography 12/7/2020 | pag. 30

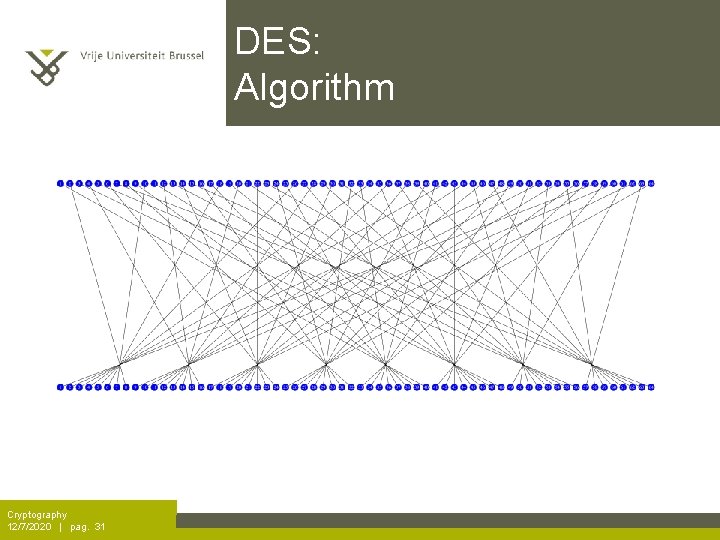
DES: Algorithm Cryptography 12/7/2020 | pag. 31

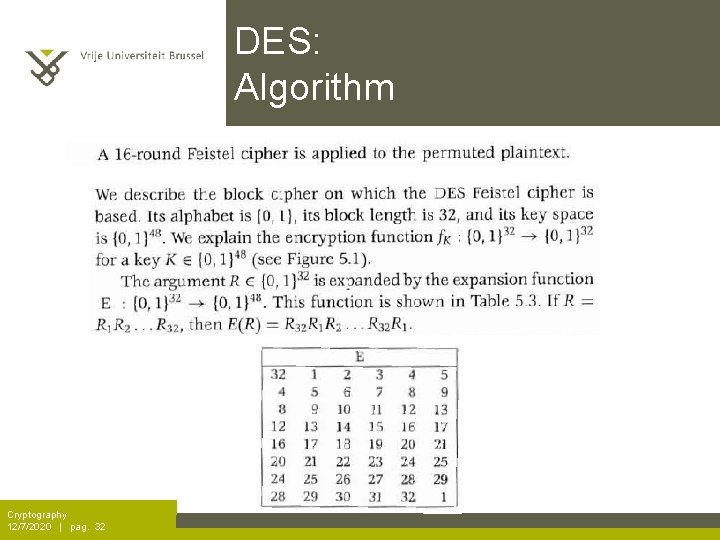
DES: Algorithm Cryptography 12/7/2020 | pag. 32

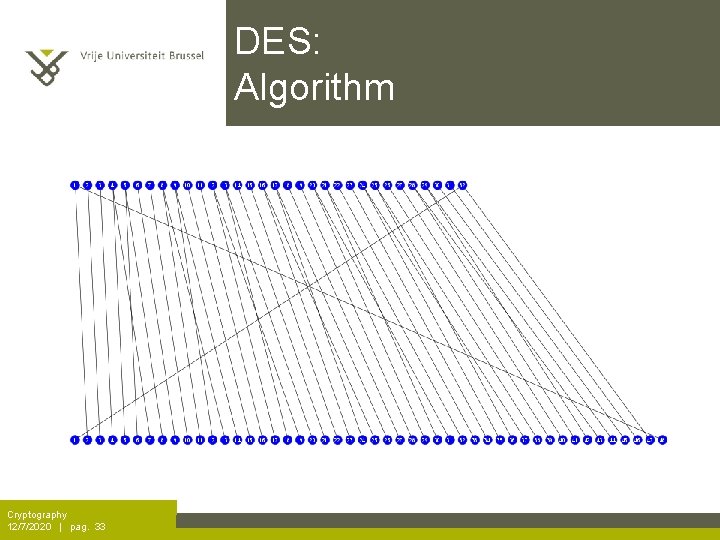
DES: Algorithm Cryptography 12/7/2020 | pag. 33

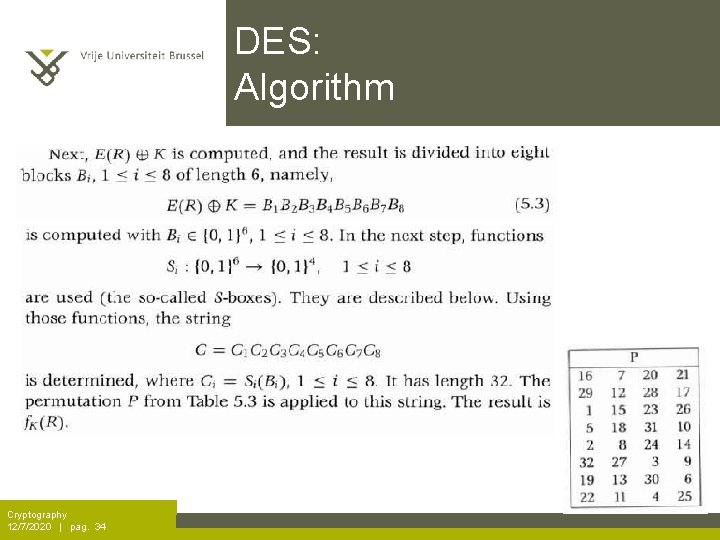
DES: Algorithm Cryptography 12/7/2020 | pag. 34

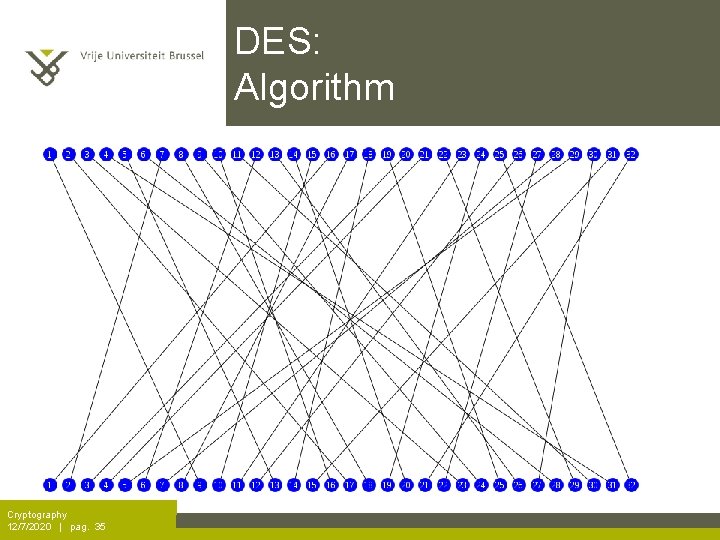
DES: Algorithm Cryptography 12/7/2020 | pag. 35

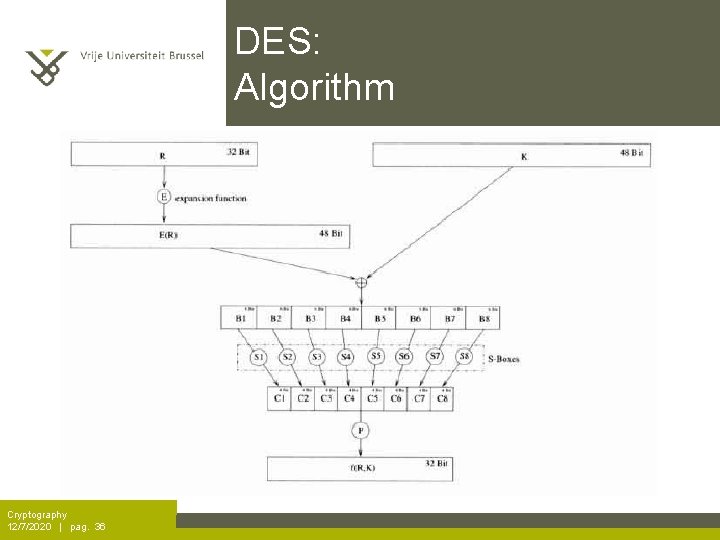
DES: Algorithm Cryptography 12/7/2020 | pag. 36

DES: Algorithm Cryptography 12/7/2020 | pag. 37

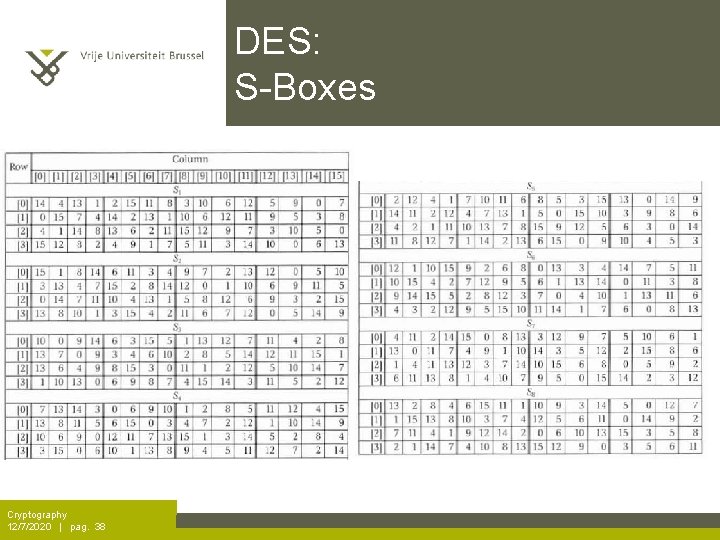
DES: S-Boxes Cryptography 12/7/2020 | pag. 38

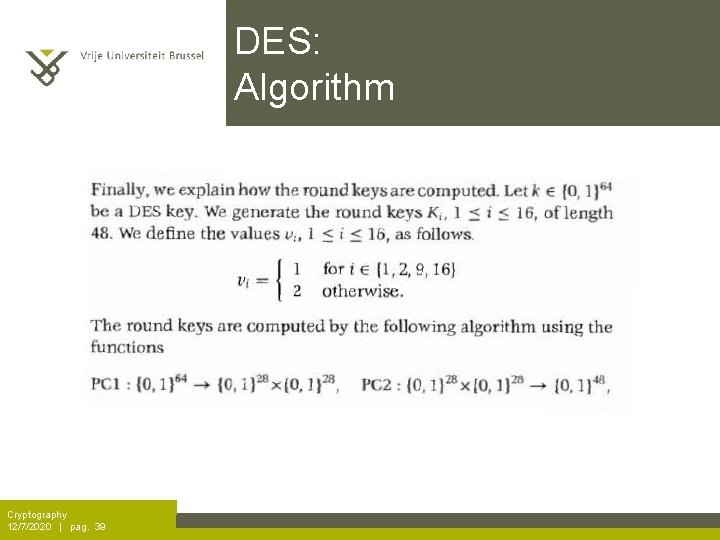
DES: Algorithm Cryptography 12/7/2020 | pag. 39

DES: Algorithm Cryptography 12/7/2020 | pag. 40

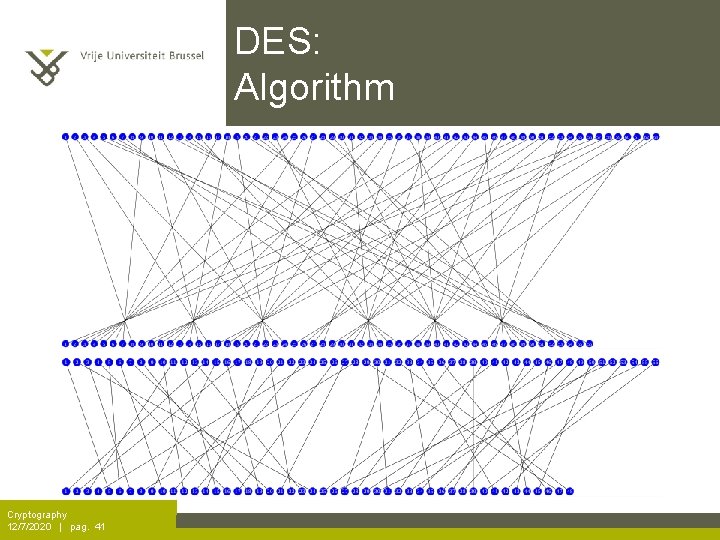
DES: Algorithm Cryptography 12/7/2020 | pag. 41

DES: Algorithm Cryptography 12/7/2020 | pag. 42 Round number Number of left rotations 1 1 2 1 3 2 4 2 5 2 6 2 7 2 8 2 9 1 10 2 11 2 12 2 13 2 14 2 15 2 16 1

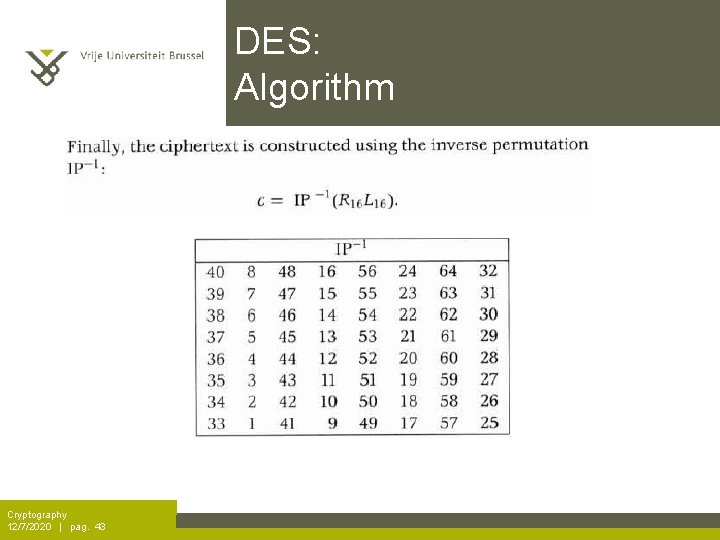
DES: Algorithm Cryptography 12/7/2020 | pag. 43

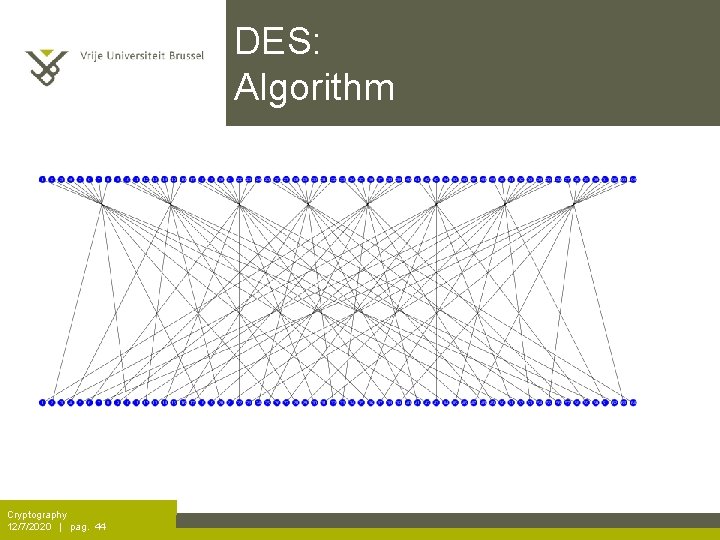
DES: Algorithm Cryptography 12/7/2020 | pag. 44

DES: Algorithm Cryptography 12/7/2020 | pag. 45

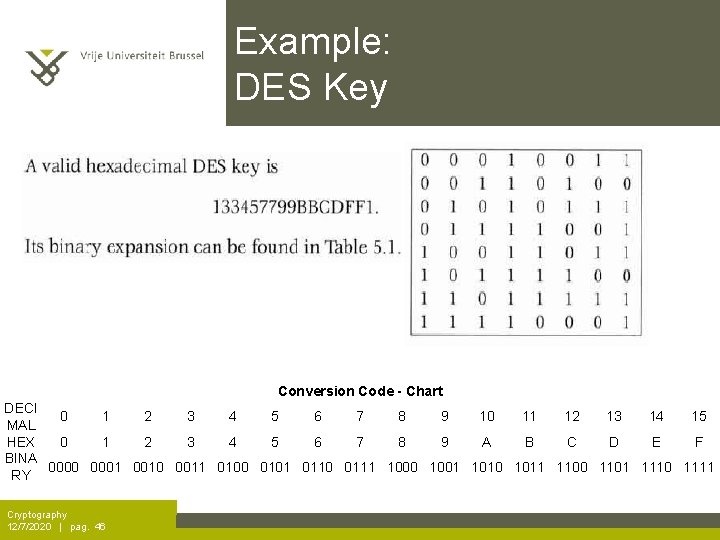
Example: DES Key Conversion Code - Chart DECI 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 MAL HEX 0 1 2 3 4 5 6 7 8 9 A B C D E F BINA 0000 0001 0010 0011 0100 0101 0110 0111 1000 1001 1010 1011 1100 1101 1110 1111 RY Cryptography 12/7/2020 | pag. 46

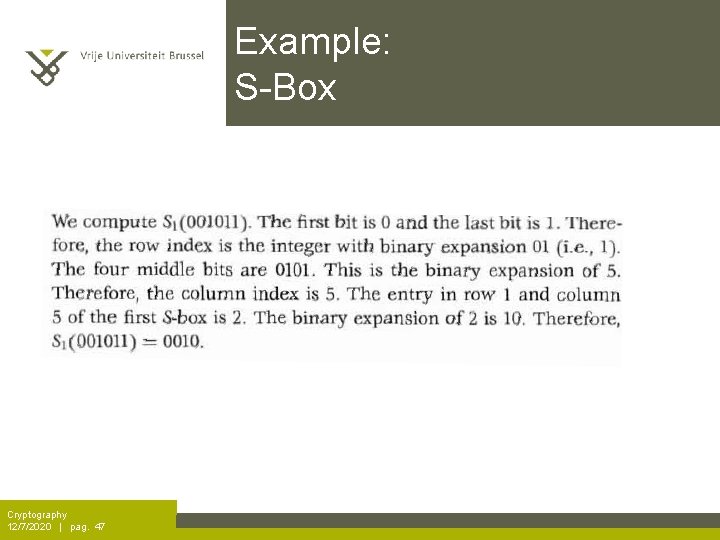
Example: S-Box Cryptography 12/7/2020 | pag. 47

Example: DES Cryptography 12/7/2020 | pag. 48

Example: DES Cryptography 12/7/2020 | pag. 49

Example: DES Cryptography 12/7/2020 | pag. 50

Example: DES Cryptography 12/7/2020 | pag. 51