Crytography Chapter 8 Cryptology Cryptography Comes from Greek

















- Slides: 36

Crytography Chapter 8

Cryptology Cryptography Comes from Greek Kryptos meaning “hidden” Grahein meaning “to write” Process of making and using codes to secure the transmission of information Cryptanalysis Process of obtaining the original message form encrypted message

Cryptology Encryption Process of converting an original message into a form that is unreadable to unauthorized individuals Decryption Process of converting the encrypted message (cipertext) into an easily read message (plain text)

Basic Definitions Algorithm Programmatic steps to encrypt message Cipher Encryption method or process Ciphertext or cryptogram Encrypted message Code Process of converting unencrypted components into encrypted components

Basic Definitions Decipher Convert to plaintext Encipher To encrypt Key or crypto-variable Information used with the algorithm to encrypt Key-space Entire range of values that can possibly be used to construct an individual key

Basic Definitions Link encryption Series of encryptions /decryptions between a number of systems Plaintext or clear text The original message Steganography Process of hiding messages Work factor Amount - effort required to perform cryptanalysis

Cipher methods Bit stream method Each bit in the plaintext is transformed bit by bit Most common use XOR Block cipher method Messaged divided into blocks Each block is encoded Substitution, transposition, XOR or combination

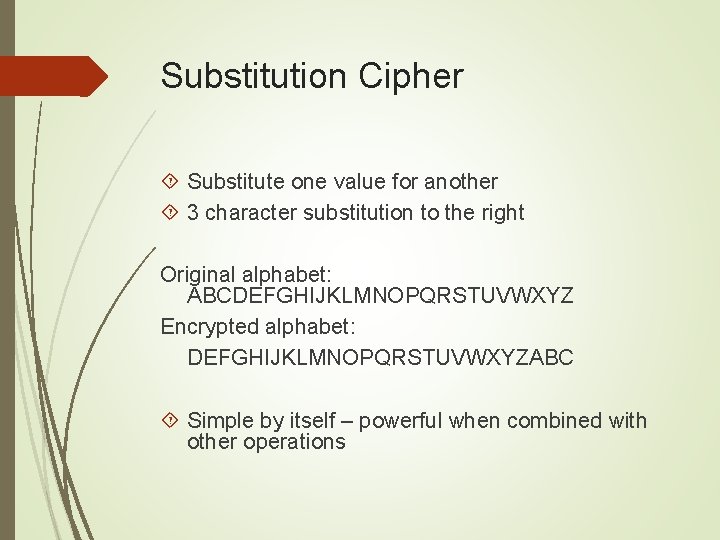
Substitution Cipher Substitute one value for another 3 character substitution to the right Original alphabet: ABCDEFGHIJKLMNOPQRSTUVWXYZ Encrypted alphabet: DEFGHIJKLMNOPQRSTUVWXYZABC Simple by itself – powerful when combined with other operations

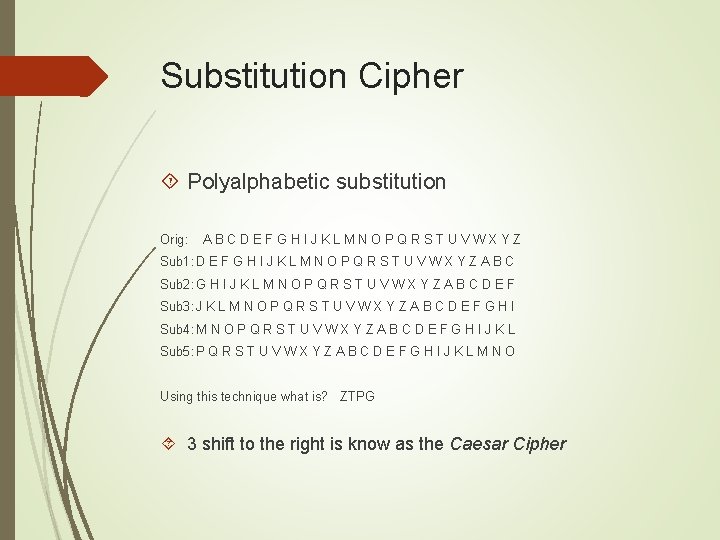
Substitution Cipher Polyalphabetic substitution Orig: ABCDEFGHIJKLMNOPQRSTUVWXYZ Sub 1: D E F G H I J K L M N O P Q R S T U V W X Y Z A B C Sub 2: G H I J K L M N O P Q R S T U V W X Y Z A B C D E F Sub 3: J K L M N O P Q R S T U V W X Y Z A B C D E F G H I Sub 4: M N O P Q R S T U V W X Y Z A B C D E F G H I J K L Sub 5: P Q R S T U V W X Y Z A B C D E F G H I J K L M N O Using this technique what is? ZTPG 3 shift to the right is know as the Caesar Cipher

Vigenere Cipher Implemented using the Vigenere Square 26 distinct cipher alphabets Header row – normal order Each additional row – shift right Start in first row and find a substitution for one letter Move down the rows for each subsequent letter of plaintext


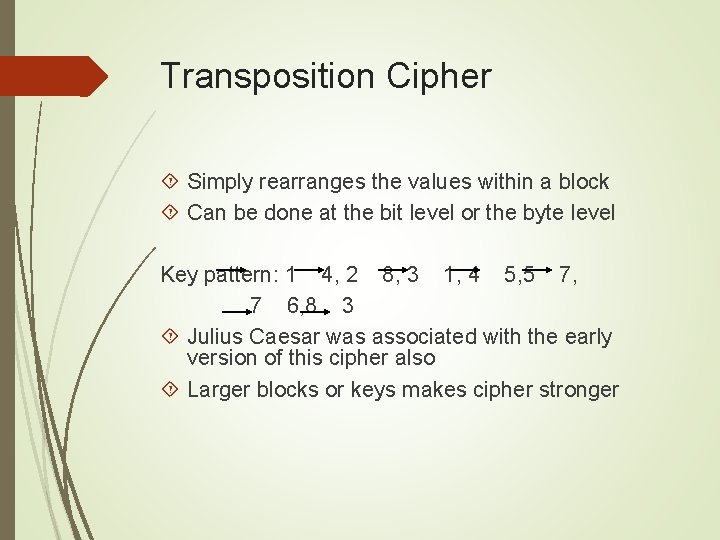
Transposition Cipher Simply rearranges the values within a block Can be done at the bit level or the byte level Key pattern: 1 4, 2 8, 3 1, 4 5, 5 7, 7 6, 8 3 Julius Caesar was associated with the early version of this cipher also Larger blocks or keys makes cipher stronger

Exclusive OR (XOR) Function of Boolean algebra Two bits are compared If identical, result is binary 0 If not identical, result is binary 1 Very simple encryption Not very secure

Vernam Cipher One-time pad Uses a set of characters only one time for each encryption process Each character of the plaintext is turned into a number and a pad value for that position is added Sum is then converted back to a cipher text Decryption requires knowledge of pad values or difficult cryptanalysis.

Book or Running Key Cipher text List of codes representing a page number, line number, and word number of the plaintext word. Must know which book was used

Hash functions Not an encryption methodology Mathematical algorithm -generates a message summary or digest Fingerprinting Used to determine if it is the same message Not used to decypher Message always provide same hash value if unaltered

Hash functions Do not require keys Uses Message Authentication Code (MAC) Key-dependent Used in password verification systems

Secure Hash Standard (SHS) Secure algorithm Standard issued by National Institute of Standards and Technology (NIST) SHA-1 Produces a 160 bit digest Family of SHA-256 A 256 -bit cipher algorithm Creates a key - encrypting the intermediate hash value with the message block functioning as the key

Cryptographic Algorithms Symmetric and asymmetric and hybrid Distinguished by the types of keys they use Symmetric Encryption Requires the same secret key Encryption methods use mathematical operations Both the sender and receiver must have the secret key Primary challenge – getting key to receiver

Symmetric Encryption Cryptosystems Data Encryption Standard (DES) Key length of 128 bits 64 -bit block size 56 -bit key Too weak Triple DES (3 DES) Advanced Encryption Standards Used by federal agencies other than national defense Declassified, publicly disclosed, royalty-free Uses block cipher, variable length block, key length of 128, 192, or 256

Asymmetric Encryption Uses two different but related keys Either key can encrypt or decrypt Must use other to perform other function One key private One key public Also know as public key encryption Based on one-way functions One is simple to compute , the opposite is complex

Asymmetric Encryption Based on hash value Uses mathematical trapdoor Secret mechanism that enable you to easily accomplish the reverse function in a one-way function. Public key becomes the true key Private is derived form public key using trapdoor

Public Key RSA (Rivest-Shamir-Adlemann) First public key encryption algorithm Published for commercial use E-commerce browsers Has become the de facto standard

Encryption Key Size Cryptovariable or key size must be decided Length of key increase the number of random selections to be guessed Length of key influences strength The security of encrypted data is NOT dependent on keeping the algorithm secret Depends on keeping some or all of the elements of the keys secret See table on page 367

Public Key Infrastructure (PKI) Integrated system of software, encryption methodologies, protocols, legal agreements, and 3 rd part services Based on public key Include digital certificates and certificate authorities

Digital Certificates Public key container files that allow computer program to validate the key and identify to whom it belongs. Allows integration of key characteristics to be integrated into business practices Authentication Integrity Privacy Authorization Non-repudiation

Digital Certificate Used by third party Certifies the authenticity of the Digital signature is attached Certify that file is from the entity that it claims to be Has not been modified Certificate authority Software agent Manages the issuance of certificates Serves as the electronic notary pubic Verify the certificates worth and integrity

PKI Common implementation Systems to issue digital certificates to users and servers Directory enrollment Key issuing systems Tools for managing the key issuance Verification and return cetificates

Digital Signatures Created to verify information transferred using electronic systems Currently asymmetric encryption processes are used to create digital signatures Encrypted messages that can be mathematically authentic Used when using DSS (digital Signature Standard)

Digital Signatures Process Create a message digest using the hash Input into the digital signature algorithm along with a random number to be used for generating the digital signature Depends upon the sender’s private key and other info provided by the CA Verified by the recipient through use of the sender’s public key

Hybrid Cryptography Systems Pure asymmetric keys encryption is not widely used except in digital certificates More widely used as part of hybrid system Diffie-Hellman Key Exchange method Exchanging private keys using public key encryption Asymmetric encryption is used to exchange session keys Limited use keys Temporary communications

Steganography Process of hiding information Not technically a form of cryptography Most popular version Hiding information within files that appear to contain digital picture or other images Use one bit per color or 3 bits per pixel to store information. Compute files that don’t use all available bits

Protocols for Secure Communication Secure Socket Layer (SSL) Used public key encryption to secure channel Support by most internet browsers Client and server establish HTTP session Client requests access part of web site - requires secure communications Server sends message to client Client respond - sending its public key & security parameters Server finds a public key match Sends a digital certificate to the client Client must verify - digital certificate –received, valid & trustworthy Lasts for duration of session

Protocols for Secure Communication SSL Two layers of protocol SSL Record Protocol Compression, encryption and attachment of SSL header Received encrypted messages are decrypted and reassembled Basic security at top level of SSL protocol stack Standard HTTP Internet communication services

Protocols for Secure Communication S-HTTP (Secure Hypertext Transfer Protocol) Extended version of hypertext transfer protocol Provides for encryption of individual messages between client and server No session Designed for sending individual messages

Securing E-mail Secure Multipurpose Internet mail Extensions (S/MIME) Adds encryption of MIME (Multipurpose Internet Mail Extensions) PEM Uses 3 DES symmetric key encryption and RSA for key exchanges and digital signature PGP Pretty Good Privacy Used IDEA Cipher