CONFIDENTIALY USING CONVENTIONAL ENCRYPTION Chapter 7 Historically Conventional

















- Slides: 26

CONFIDENTIALY USING CONVENTIONAL ENCRYPTION – Chapter 7 • Historically – Conventional Encryption • Recently – Authentication, Integrity, Signature, Public-key • Link • End-to-End • Traffic-Analysis • Key Distribution • Random Number Generation

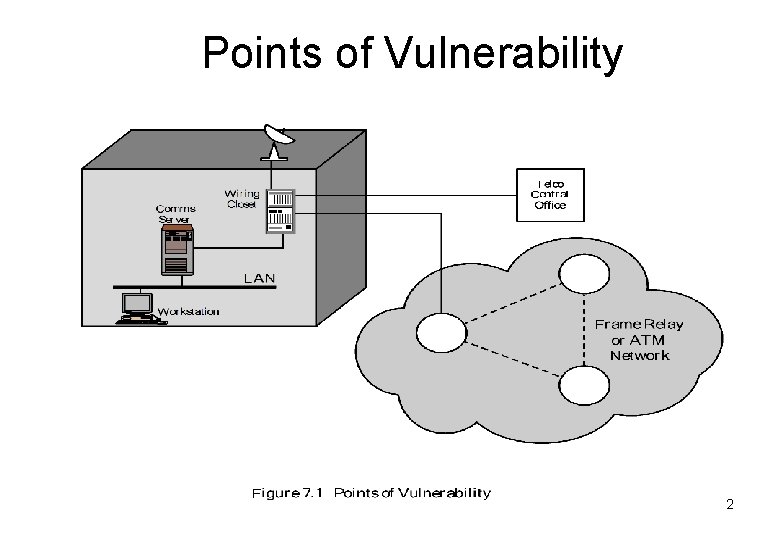
Points of Vulnerability 2

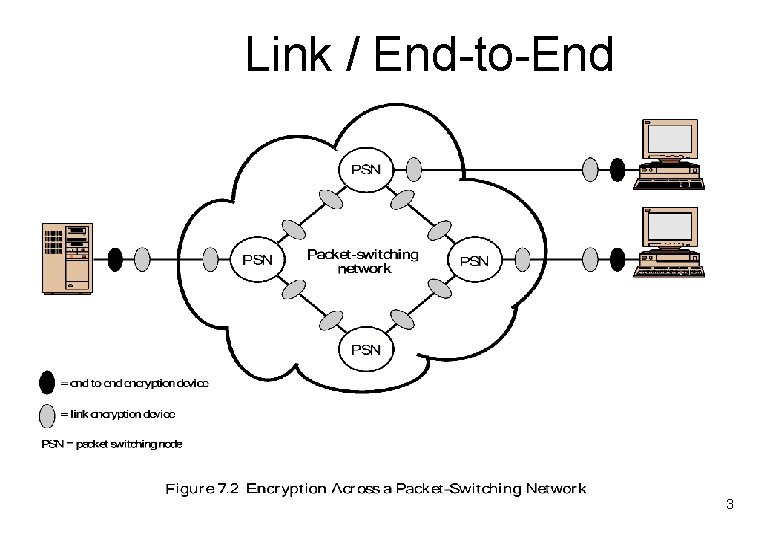
Link / End-to-End 3

• Link Confidentiality - both ends of link - many encryps / decryps - all links use it - decrypt at packet switch (read addr. ) - unique key / node pair • End- to-End - only at ends - data encrypted, not address (header) - one key pair - traffic pattern insecure - authentication from sender

Characteristics of Link and End-to-End Table 7. 1

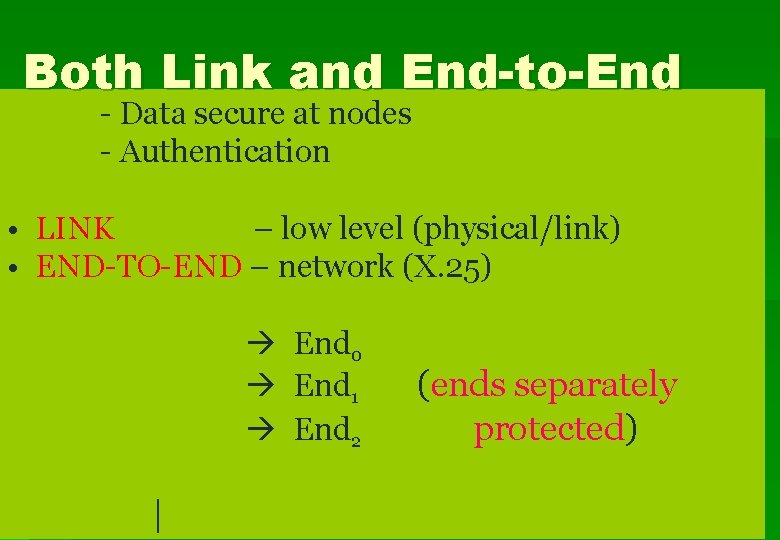
Both Link and End-to-End - Data secure at nodes - Authentication • LINK – low level (physical/link) • END-TO-END – network (X. 25) End 0 End 1 End 2 | (ends separately protected)

Front-End Processor Function 7

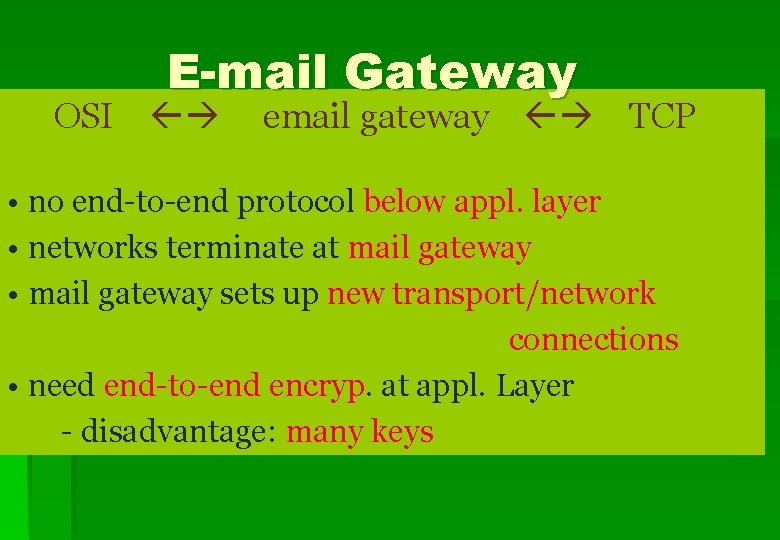
E-mail Gateway 8

E-mail Gateway OSI email gateway TCP • no end-to-end protocol below appl. layer • networks terminate at mail gateway • mail gateway sets up new transport/network connections • need end-to-end encryp. at appl. Layer - disadvantage: many keys

Various Encryption Strategies 10

Traffic Confidentiality • Identities • Message Frequency • Message Pattern • Event Correlation • Covert Channel Link • Headers encrypted • Traffic padding (Fig 7. 6) End-to-End • Pad data • Null messages

Traffic Padding 12

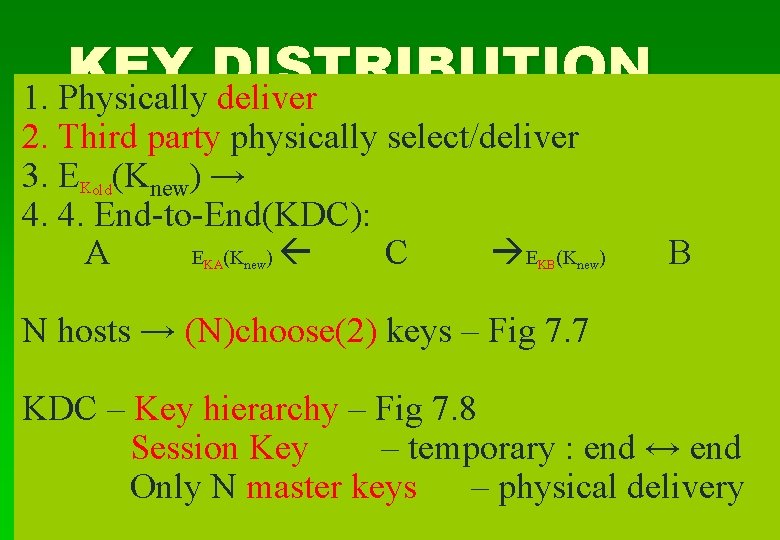
KEY DISTRIBUTION 1. Physically deliver 2. Third party physically select/deliver 3. EKold(Knew) → 4. 4. End-to-End(KDC): A E (K ) C E (K KA new KB new) B N hosts → (N)choose(2) keys – Fig 7. 7 KDC – Key hierarchy – Fig 7. 8 Session Key – temporary : end ↔ end Only N master keys – physical delivery

#End-to-End Keys 14

Key Hierarchy 15

KEY DISTRIBUTION SCENARIO 16

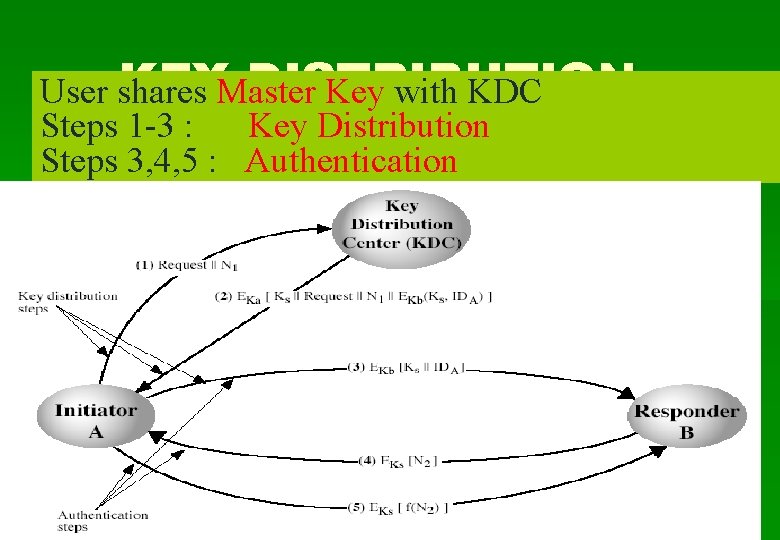
KEYMaster DISTRIBUTION User shares Key with KDC Steps 1 -3 : Key Distribution Steps 3, 4, 5 : Authentication

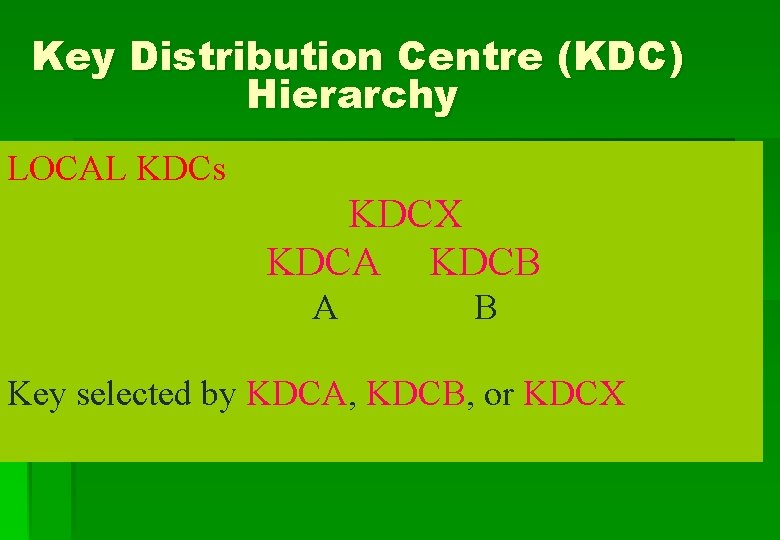
Key Distribution Centre (KDC) Hierarchy LOCAL KDCs KDCX KDCA KDCB A B Key selected by KDCA, KDCB, or KDCX

LIFETIME Shorter Lifetime → Highter Security → Reduced Capacity Connection-oriented: - change session key periodically Connectionless: - new key every exchange or #transactions or after time period

Key Distribution (connection-oriented) End-to-End (X. 25, TCP), FEP obtains session keys 20

Decentralised Key Control Not practical for large networks - avoids trusted third party 21

KEY USAGE key types : Data, PIN, File key tags : Session/Master/Encryp/Decryp Control Vector: associate session key with control vector (Fig 7. 12)

Control Vector Encryp. and Decryp. 23

PRNG From Counter 24

ANSI X 9. 17 PRNG 25

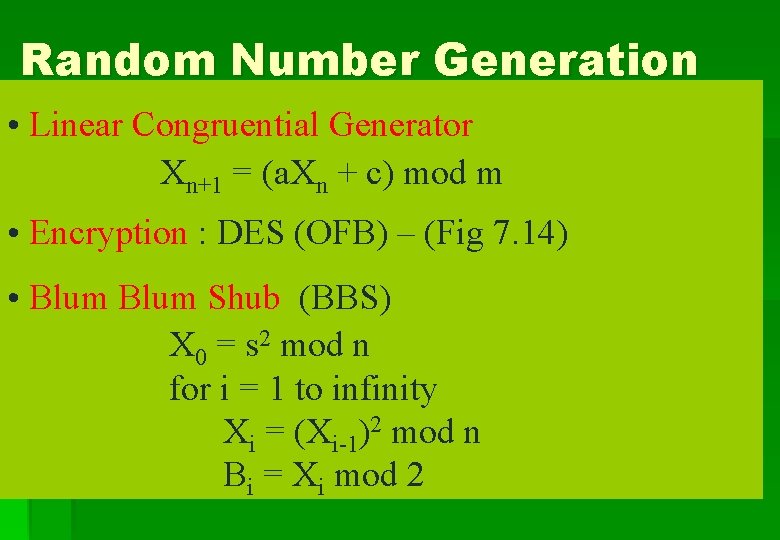
Random Number Generation • Linear Congruential Generator Xn+1 = (a. Xn + c) mod m • Encryption : DES (OFB) – (Fig 7. 14) • Blum Shub (BBS) X 0 = s 2 mod n for i = 1 to infinity Xi = (Xi-1)2 mod n Bi = Xi mod 2