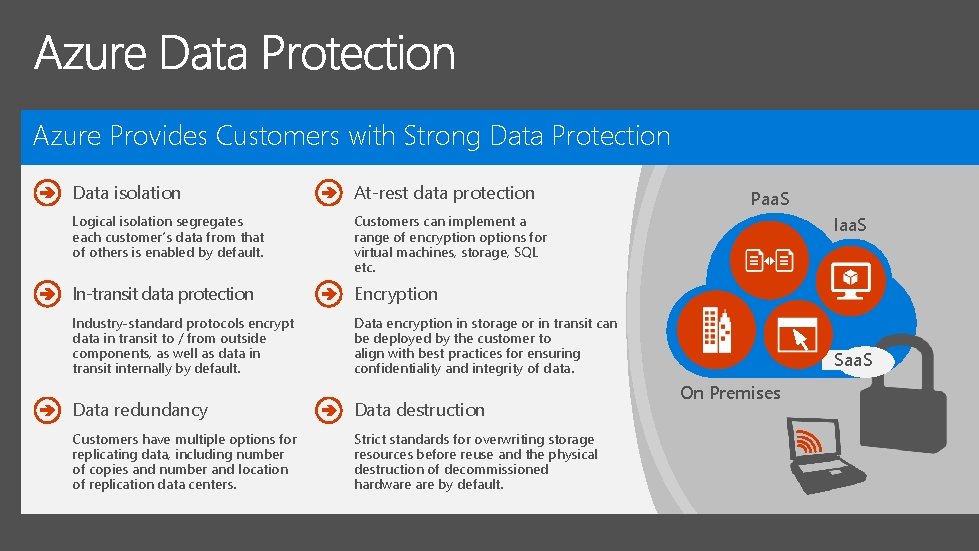
Azure Provides Customers with Strong Data Protection Data



![• Secrets like Bit. Locker Encryption Keys [BEK] or Linux Pass. Phrase are • Secrets like Bit. Locker Encryption Keys [BEK] or Linux Pass. Phrase are](https://slidetodoc.com/presentation_image_h/9a75649ee5714ce9535e091a79a70896/image-16.jpg)




- Slides: 24



Azure Provides Customers with Strong Data Protection Data isolation At-rest data protection Logical isolation segregates each customer’s data from that of others is enabled by default. Customers can implement a range of encryption options for virtual machines, storage, SQL etc. In-transit data protection Encryption Industry-standard protocols encrypt data in transit to / from outside components, as well as data in transit internally by default. Data encryption in storage or in transit can be deployed by the customer to align with best practices for ensuring confidentiality and integrity of data. Data redundancy Data destruction Customers have multiple options for replicating data, including number of copies and number and location of replication data centers. Strict standards for overwriting storage resources before reuse and the physical destruction of decommissioned hardware by default. Paa. S Iaa. S Saa. S On Premises

SECURING THE PLATFORM EMPOWERING YOU Security Privacy and Control Transparency Compliance Identity & Access Controls Encryption and Key Management Secure Networking Partner Solutions Azure Security Center

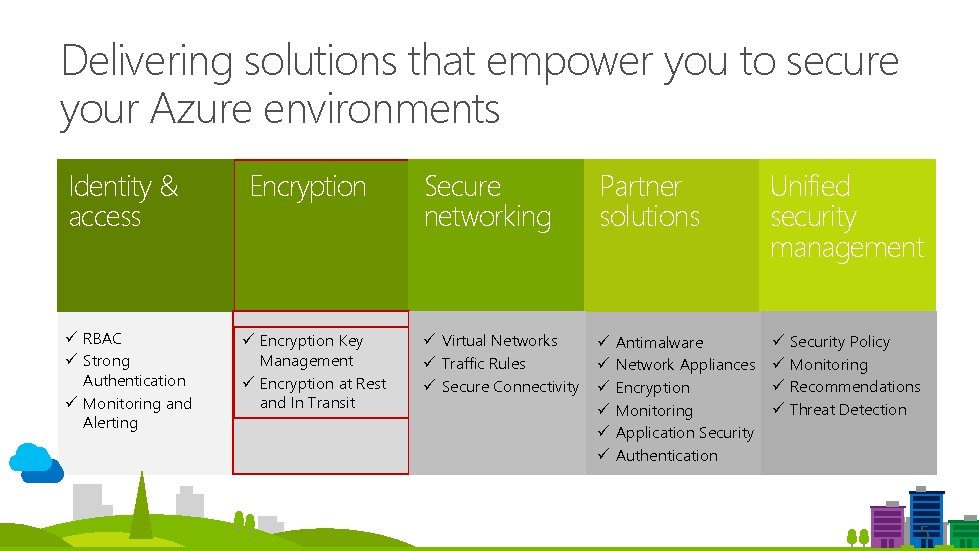
Delivering solutions that empower you to secure your Azure environments Identity & access ü RBAC ü Strong Authentication ü Monitoring and Alerting Encryption ü Encryption Key Management ü Encryption at Rest and In Transit Secure networking Partner solutions ü Virtual Networks ü Traffic Rules ü Secure Connectivity ü ü ü Antimalware Network Appliances Encryption Monitoring Application Security Authentication Unified security management ü ü Security Policy Monitoring Recommendations Threat Detection 5

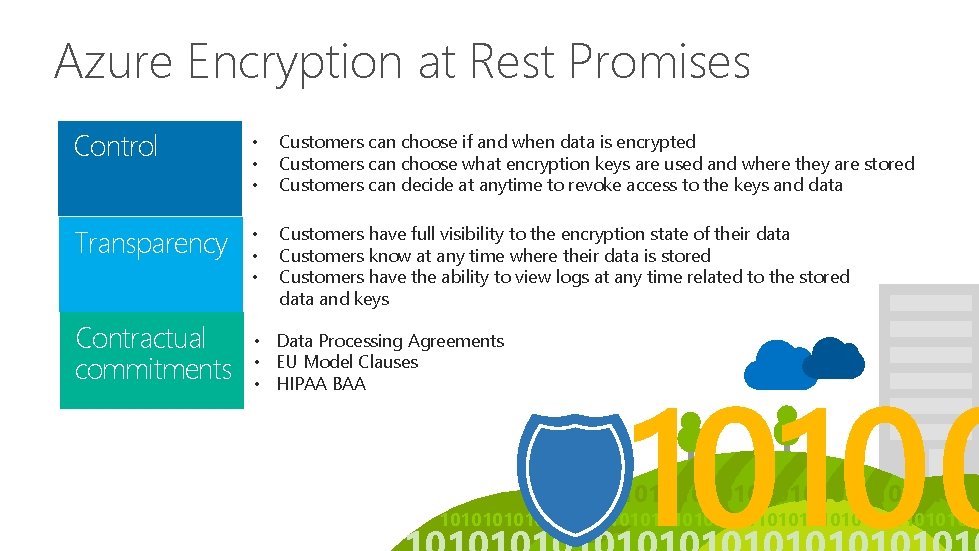
Azure Encryption at Rest Promises Control • • • Customers can choose if and when data is encrypted Customers can choose what encryption keys are used and where they are stored Customers can decide at anytime to revoke access to the keys and data Transparency • • • Customers have full visibility to the encryption state of their data Customers know at any time where their data is stored Customers have the ability to view logs at any time related to the stored data and keys Contractual commitments • Data Processing Agreements • EU Model Clauses • HIPAA BAA 101010101010101010101010101010101010101010

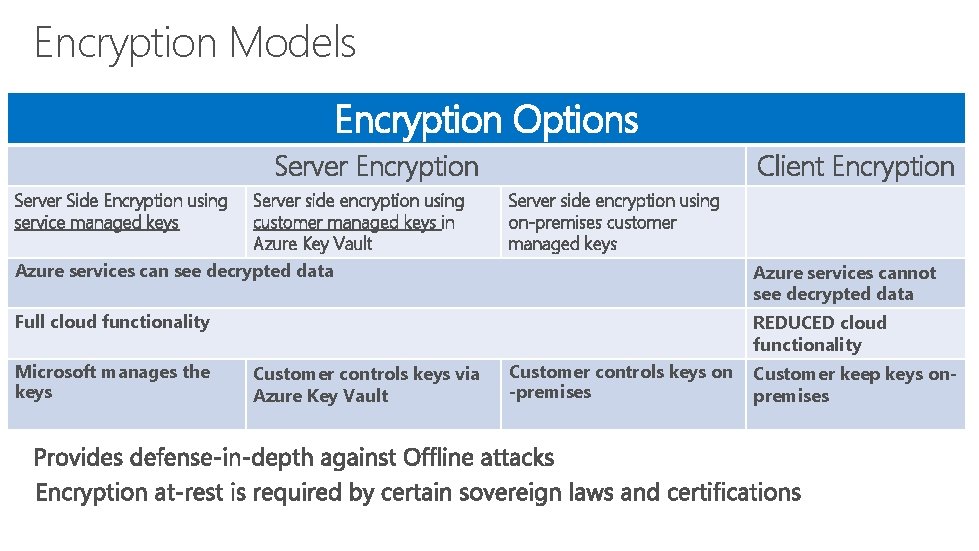
Encryption Models Encryption Options Server Encryption Server Side Encryption using service managed keys Server side encryption using customer managed keys in Azure Key Vault Client Encryption Server side encryption using on-premises customer managed keys Azure services can see decrypted data Azure services cannot see decrypted data Full cloud functionality REDUCED cloud functionality Microsoft manages the keys Customer controls keys via Azure Key Vault Customer controls keys on -premises Customer keep keys onpremises

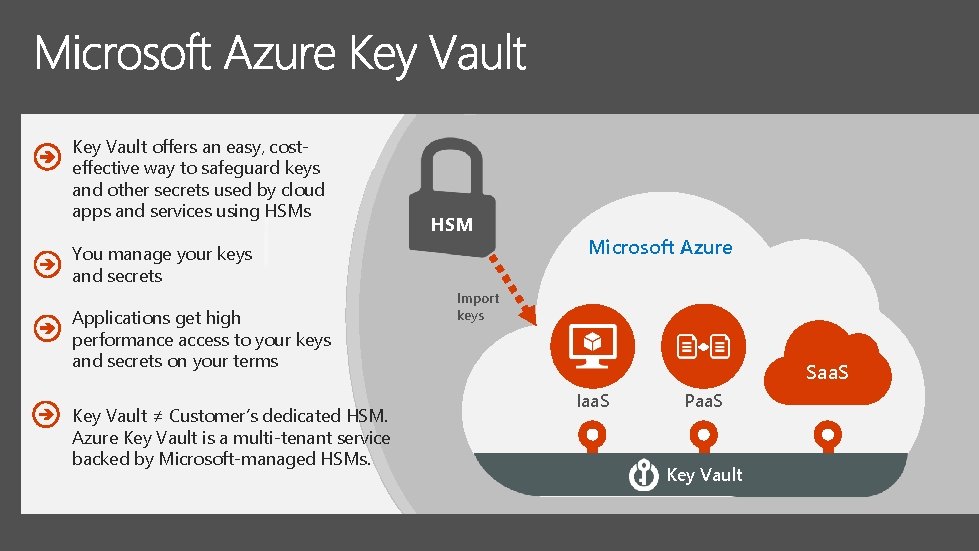
Key Vault offers an easy, costeffective way to safeguard keys and other secrets used by cloud apps and services using HSMs HSM You manage your keys and secrets Applications get high performance access to your keys and secrets on your terms Key Vault ≠ Customer’s dedicated HSM. Azure Key Vault is a multi-tenant service backed by Microsoft-managed HSMs. Microsoft Azure Import keys Saa. S Iaa. S Paa. S Key Vault

Virtual Machines Power. BI SQL Databases Storage blobs Media Services Data Lake Resource Providers HDInsight Machine Learning Workspaces Stream Analytics

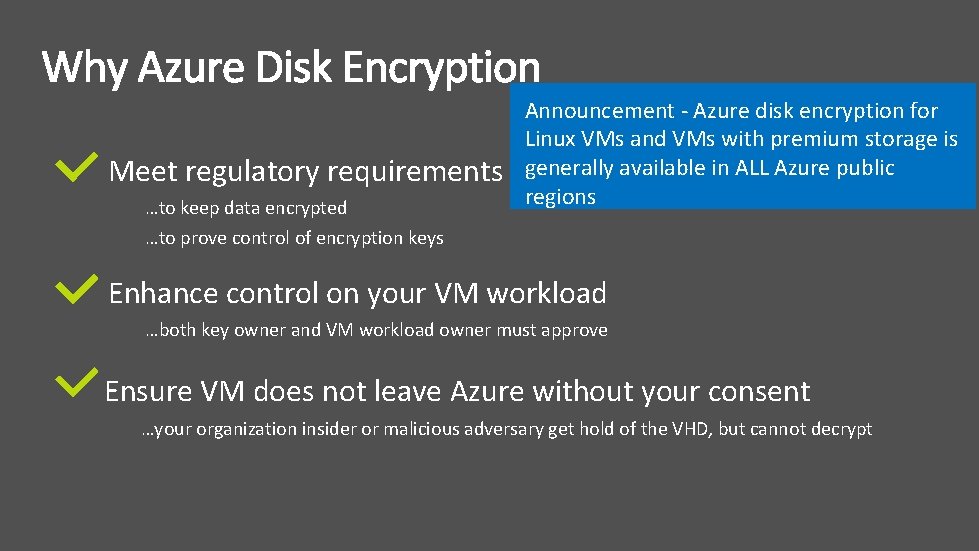
Meet regulatory requirements …to keep data encrypted …to prove control of encryption keys Announcement - Azure disk encryption for Linux VMs and VMs with premium storage is generally available in ALL Azure public regions Enhance control on your VM workload …both key owner and VM workload owner must approve Ensure VM does not leave Azure without your consent …your organization insider or malicious adversary get hold of the VHD, but cannot decrypt

• Key management integrated in customer Azure key vault using HSM Value Proposition: • VM’s are secured at rest using industry standard encryption technology to address organizational security and compliance requirements • VM’s boot under customer controlled keys and policies, and customers can audit the usage in Key Vault Threats Addressed: • Data breach Loss of Disks, Loss of storage account keys, Offline disk attacks

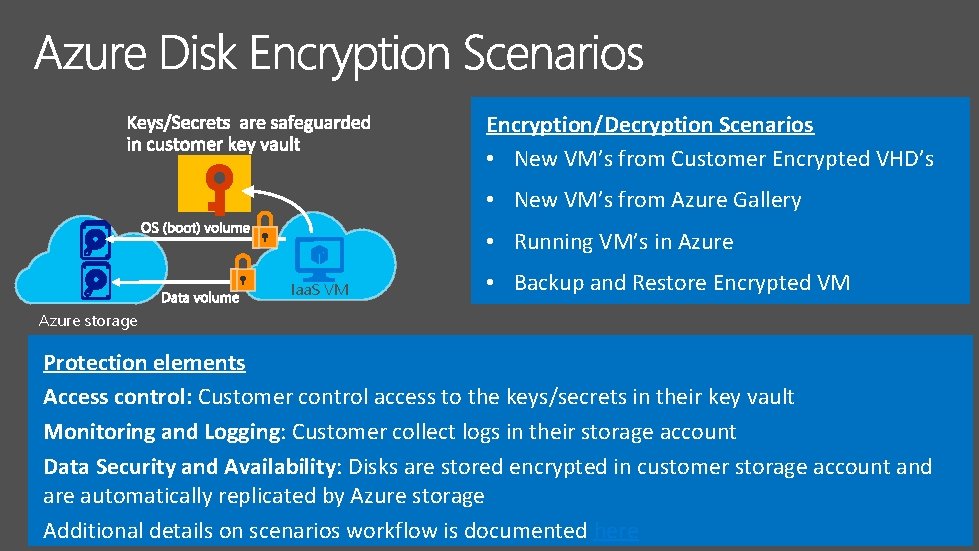
Encryption/Decryption Scenarios • New VM’s from Customer Encrypted VHD’s • New VM’s from Azure Gallery • Running VM’s in Azure Iaa. S VM • Backup and Restore Encrypted VM Azure storage Protection elements Access control: Customer control access to the keys/secrets in their key vault Monitoring and Logging: Customer collect logs in their storage account Data Security and Availability: Disks are stored encrypted in customer storage account and are automatically replicated by Azure storage Additional details on scenarios workflow is documented here

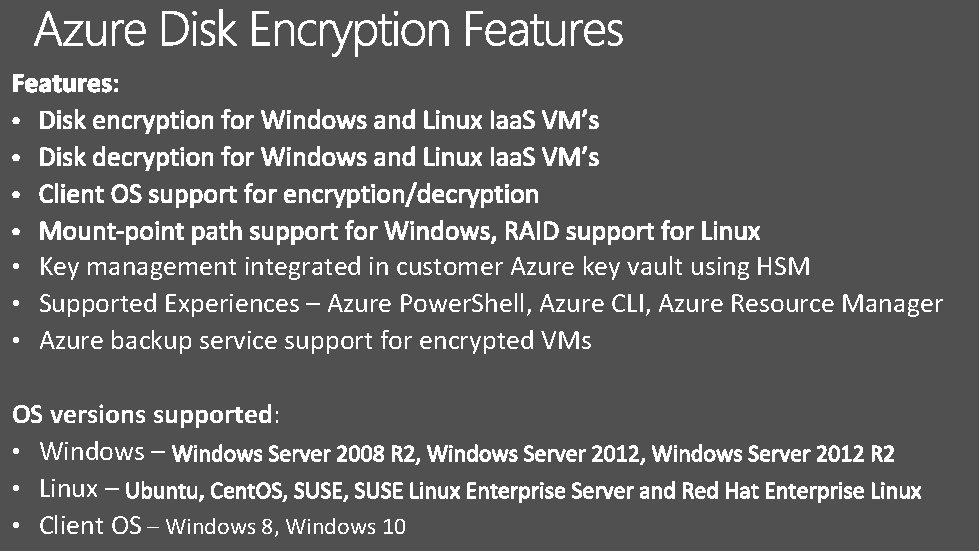
• Key management integrated in customer Azure key vault using HSM • Supported Experiences – Azure Power. Shell, Azure CLI, Azure Resource Manager • Azure backup service support for encrypted VMs OS versions supported: • Windows – • Linux – • Client OS – Windows 8, Windows 10

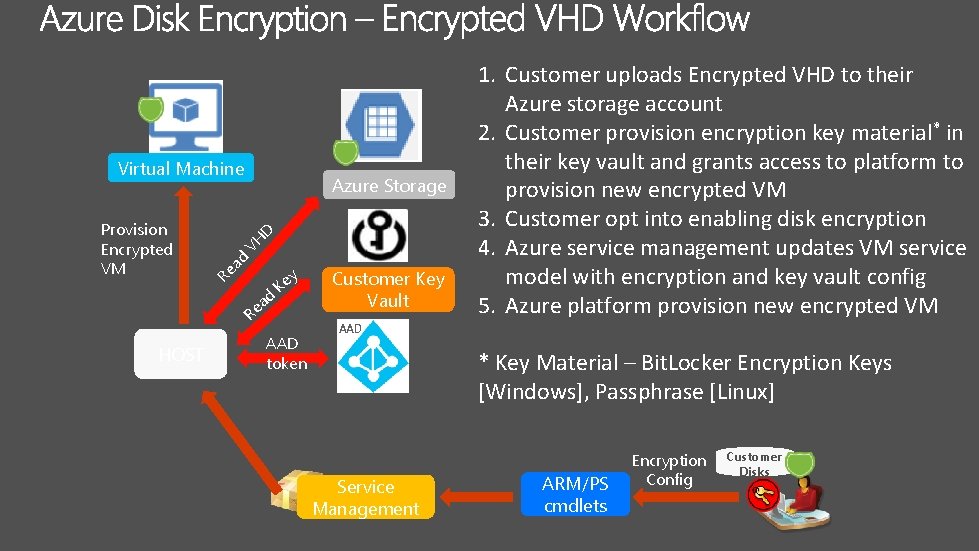
Virtual Machine D VH ad y Re Provision Encrypted VM Azure Storage d a Re HOST Ke AAD token Customer Key Vault 1. Customer uploads Encrypted VHD to their Azure storage account 2. Customer provision encryption key material* in their key vault and grants access to platform to provision new encrypted VM 3. Customer opt into enabling disk encryption 4. Azure service management updates VM service model with encryption and key vault config 5. Azure platform provision new encrypted VM AAD * Key Material – Bit. Locker Encryption Keys [Windows], Passphrase [Linux] Service Management ARM/PS cmdlets Encryption Config Customer Disks

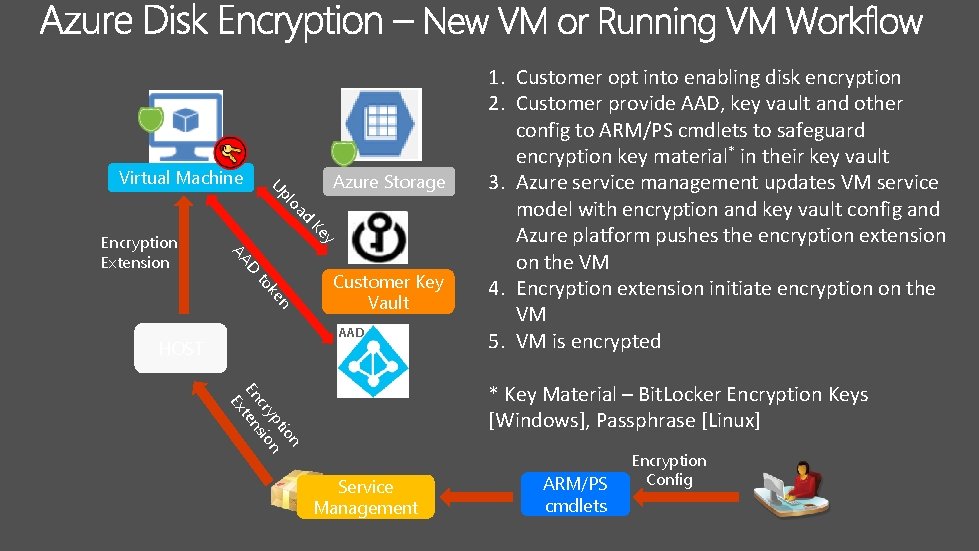
Azure Storage ad lo Up Virtual Machine Ke y D AA Encryption Extension n ke to Customer Key Vault AAD HOST 1. Customer opt into enabling disk encryption 2. Customer provide AAD, key vault and other config to ARM/PS cmdlets to safeguard encryption key material* in their key vault 3. Azure service management updates VM service model with encryption and key vault config and Azure platform pushes the encryption extension on the VM 4. Encryption extension initiate encryption on the VM 5. VM is encrypted n tio yp n cr sio En ten Ex * Key Material – Bit. Locker Encryption Keys [Windows], Passphrase [Linux] Service Management ARM/PS cmdlets Encryption Config
![Secrets like Bit Locker Encryption Keys BEK or Linux Pass Phrase are • Secrets like Bit. Locker Encryption Keys [BEK] or Linux Pass. Phrase are](https://slidetodoc.com/presentation_image_h/9a75649ee5714ce9535e091a79a70896/image-16.jpg)
• Secrets like Bit. Locker Encryption Keys [BEK] or Linux Pass. Phrase are safeguarded in customer Azure key vault • Secrets can be encrypted by customer controlled Key Encryption Key [KEK – RSA 2048] when KEK is specified • Azure do not have ANY default access to customer key vault • Customer grant explicit read access to their key vault to Azure platform to enable disk encryption • Customer provide AAD credentials to write the BEK or Linux Pass. Phrase secret to their key vault to enable disk encryption Secret Keys Contoso. BEK [encrypted by Contoso. KEK] – Bit. Locker Windows Contoso. KEK Contoso. Pass. Phrase [encrypted by Contoso. KEK] – Linux


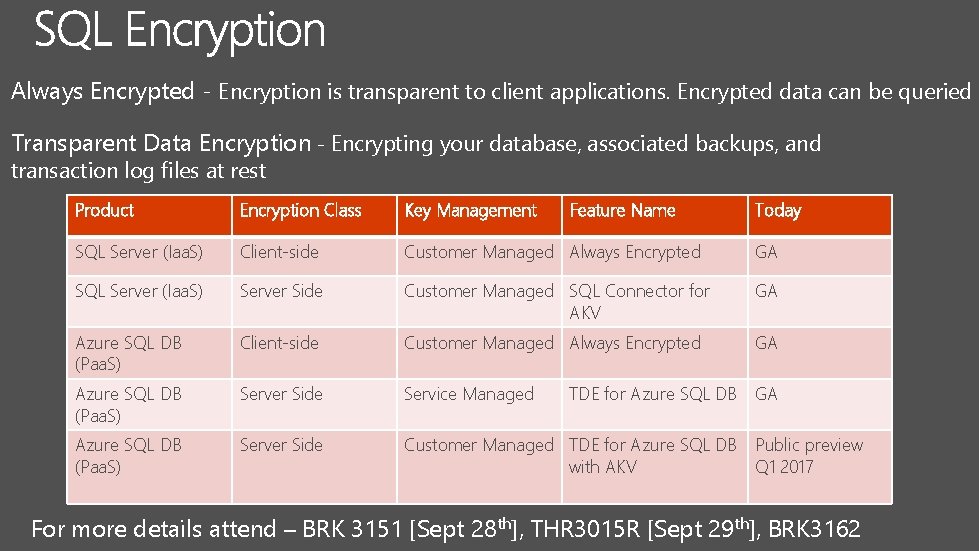
Always Encrypted - Encryption is transparent to client applications. Encrypted data can be queried Transparent Data Encryption - Encrypting your database, associated backups, and transaction log files at rest Product Encryption Class Key Management Feature Name Today SQL Server (Iaa. S) Client-side Customer Managed Always Encrypted GA SQL Server (Iaa. S) Server Side Customer Managed SQL Connector for AKV GA Azure SQL DB (Paa. S) Client-side Customer Managed Always Encrypted GA Azure SQL DB (Paa. S) Server Side Service Managed Azure SQL DB (Paa. S) Server Side Customer Managed TDE for Azure SQL DB Public preview with AKV Q 1 2017 TDE for Azure SQL DB GA For more details attend – BRK 3151 [Sept 28 th], THR 3015 R [Sept 29 th], BRK 3162


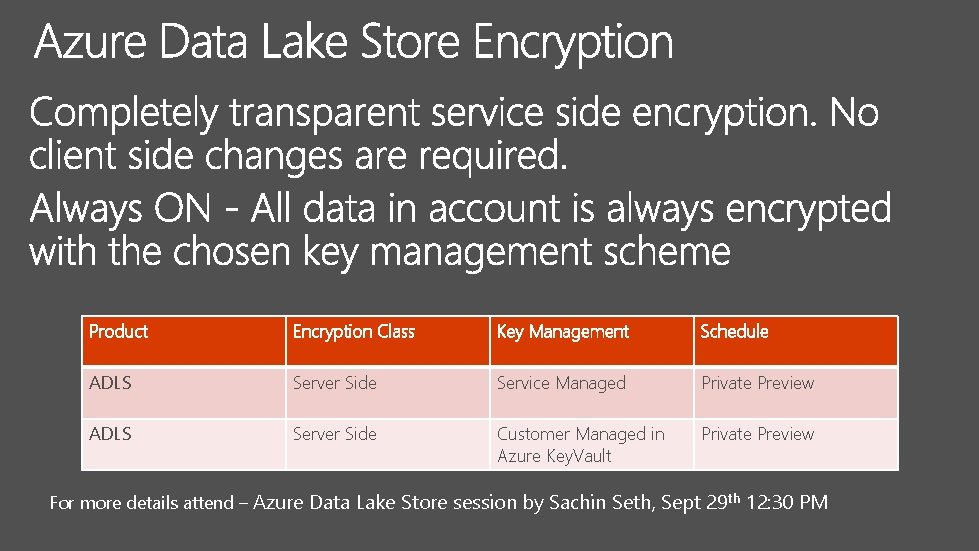
Product Encryption Class Key Management Schedule ADLS Server Side Service Managed Private Preview ADLS Server Side Customer Managed in Azure Key. Vault Private Preview For more details attend – Azure Data Lake Store session by Sachin Seth, Sept 29 th 12: 30 PM

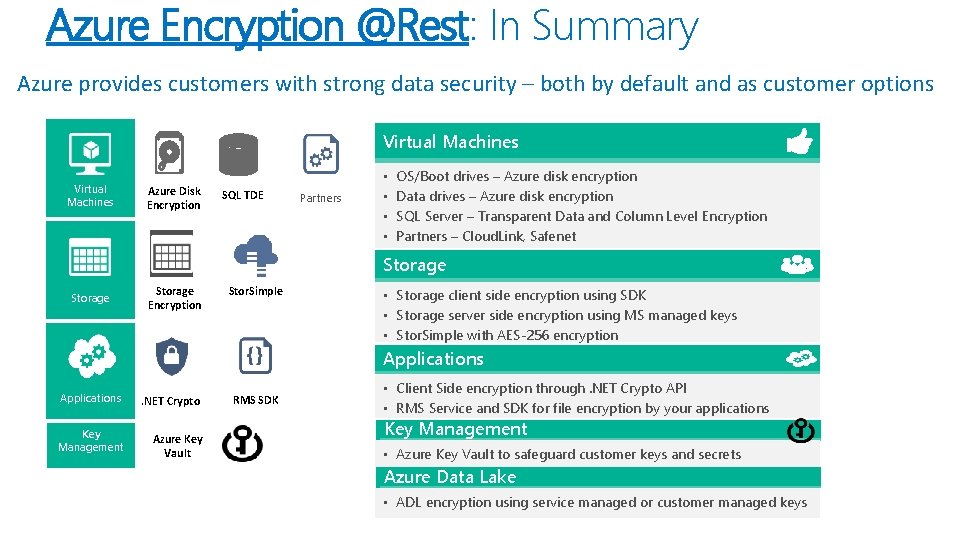
Azure Encryption @Rest: In Summary Azure provides customers with strong data security – both by default and as customer options Virtual Machines Azure Disk Encryption SQL TDE Partners • • OS/Boot drives – Azure disk encryption Data drives – Azure disk encryption SQL Server – Transparent Data and Column Level Encryption Partners – Cloud. Link, Safenet Storage Encryption Stor. Simple • Storage client side encryption using SDK • Storage server side encryption using MS managed keys • Stor. Simple with AES-256 encryption Applications . NET Crypto Key Management Azure Key Vault RMS SDK • Client Side encryption through. NET Crypto API • RMS Service and SDK for file encryption by your applications Key Management • Azure Key Vault to safeguard customer keys and secrets Azure Data Lake • ADL encryption using service managed or customer managed keys

www. microsoft. com/itprocareercenter www. microsoft. com/itprocloudessentials www. microsoft. com/mechanics https: //techcommunity. microsoft. com

http: //myignite. microsoft. com https: //aka. ms/ignite. mobileapp
