NYU Cryptography Group at Courant Institute Students Faculty

















![Authenticated Encryption • First formal modeling of public-key authenticated encryption (signcryption) [ADR 02] • Authenticated Encryption • First formal modeling of public-key authenticated encryption (signcryption) [ADR 02] •](https://slidetodoc.com/presentation_image_h/ae17fb7eacbfb5d196e30568d2127d1d/image-20.jpg)
![Key Exposure Protection • Exposure-resilient functions and All-ornothing transforms [CDH 00, DSS 01] • Key Exposure Protection • Exposure-resilient functions and All-ornothing transforms [CDH 00, DSS 01] •](https://slidetodoc.com/presentation_image_h/ae17fb7eacbfb5d196e30568d2127d1d/image-21.jpg)
![Distributed Computation • Byzantine Agreement [CKS 00, CKPS 01, KS 01] • Threshold Cryptosystems Distributed Computation • Byzantine Agreement [CKS 00, CKPS 01, KS 01] • Threshold Cryptosystems](https://slidetodoc.com/presentation_image_h/ae17fb7eacbfb5d196e30568d2127d1d/image-22.jpg)
![Some Other Projects • Digital right management [DF 02, DF 03, DFKY 03] • Some Other Projects • Digital right management [DF 02, DF 03, DFKY 03] •](https://slidetodoc.com/presentation_image_h/ae17fb7eacbfb5d196e30568d2127d1d/image-23.jpg)
- Slides: 23

NYU Cryptography Group at Courant Institute • Students: • Faculty: – Yevgeniy Dodis dodis@cs. nyu. edu – Victor Shoup shoup@cs. nyu. edu – Nelly Fazio – Michael Freedman – Anca Ivan – Antonio Nicolosi – Roberto Oliveira – Shabsi Walfish

Cryptography Reading Group • Meet every week – This semester Friday, 1 pm, room 101 • Drop by! – Contact me to be put on the mailing list http: //www. scs. nyu. edu/crypto

Our Main Goals • Improving the security and/or efficiency of cryptographic applications • Designing new, provably secure cryptographic primitives • Formalization and rigorous analysis of common cryptographic practices • Protecting against key exposure • Secure distributed/multiparty computation

Our Style: Provable Security • Formal definition for the cryptographic task at hand • A concrete scheme which provably satisfies the above definition, assuming some commonly believed and well studied mathematical problem is “hard” • Ensures that the only way to break the cryptographic scheme is to break a well studied mathematical problem, which is very unlikely (e. g. , factoring) • Gives much higher guarantee/assurance than commonly utilized “heuristic” approaches

Crypto Skills • Creativity: open mind, love for puzzles • Formalism (proofs!) and elementary math (number theory, probability) • Ability to ask interesting questions • Ability to think as a devil…

Some of Our Projects • • Signature and Encryption Schemes Authenticated Encryption Resilience to Key Exposure Distributed and Multi-party Cryptography – Two-party computation • • • Digital Right Management Cryptography with Imperfect Randomness Ideal Hash Function Methodology Fault-tolerant Authentication Privacy and Anonymity …

Some projects I have been involved in @ NYU… Warnings: • Not meant to… – give formal introduction to cryptography – be crystal clear if you see it for the first time • Instead… – give vague summary of the “kind” of things I like – emphasize joint works with students and faculty • Talk to me if interested in details!

Partial Key Exposure • "Exposure-Resilient Functions and All-Or. Nothing Transforms" , Eurocrypt, 2000. • "On Perfect and Adaptive Security in Exposure-Resilient Cryptography", Eurocrypt, 2001. • "Exposure-Resilience for Free: the Case of Hierarchical ID-based Encryption", IEEE International Security In Storage Workshop (SISW), 2002.

Key Evolving Schemes v Designed new model of key-insulated security, led to intrusion-resilient security • "Key-Insulated Public Key Cryptosystems", Eurocrypt, 2002. • "Strong Key-Insulated Signature Schemes", Workshop on Public Key Cryptography (PKC), 2003. • "Intrusion-Resilient Public-Key Encryption", RSA Conference, Cryptography Track (CTRSA), 2003.

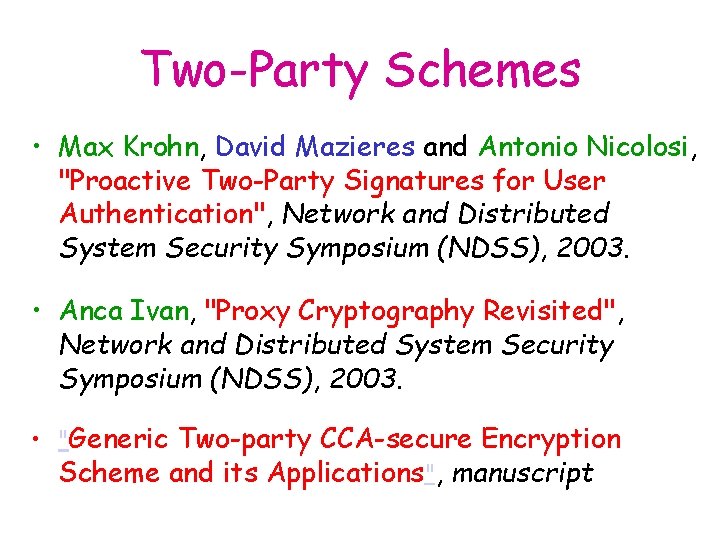
Two-Party Schemes • Max Krohn, David Mazieres and Antonio Nicolosi, "Proactive Two-Party Signatures for User Authentication", Network and Distributed System Security Symposium (NDSS), 2003. • Anca Ivan, "Proxy Cryptography Revisited", Network and Distributed System Security Symposium (NDSS), 2003. • "Generic Two-party CCA-secure Encryption Scheme and its Applications", manuscript

Authenticated Encryption • "On the Security of Joint Signature and Encryption", Eurocrypt, 2002. • "Concealment and Its Applications to Authenticated Encryption", Eurocrypt, 2003. • Michael Freedman and Shabsi Walfish, "Parallel Signcryption with OAEP, PSS-R and other Feistel Paddings", submitted to Crypto 2003. • Michael Freedman and Shabsi Walfish, "Universal Padding Schemes", manuscript. • "Parallel Authenticated Encryption", manuscript.

Digital Right Management • Nelly Fazio, "Public Key Broadcast Encryption for Stateless Receivers", ACM Workshop on Digital Rights Management, 2002. • Nelly Fazio, "Public Key Broadcast Encryption Secure Against Adaptive Chosen Ciphertext Attack", Workshop on Public Key Cryptography (PKC), 2003. • Nelly Fazio, "Fully Scalable Public-Key Traitor Tracing", submitted, 2003. • Nelly Fazio, "Forward-Secure Broadcast Encryption", manuscript.

Imperfect Randomness • "New Imperfect Random Source with Applications to Coin-Flipping", International Colloquium on Automata, Languages and Programming (ICALP), 2001. • Joel Spencer, "On the (non-)Universality of the One-Time Pad", Foundations of Computer Science (FOCS), 2002. • Roberto Oliveira, "On Extracting Private Randomness over a Public Channel", manuscript.

Distributed Cryptography • "Parallel Reducibility for Information. Theoretically Secure Computation", Crypto, 2000. • "Efficient Construction of (Distributed) Verifiable Random Functions", Workshop on Public Key Cryptography (PKC), 2003 • “Distributed Block Ciphers", manuscript

Cryptography: Other… • "Lower Bounds for Oblivious Transfer Reductions", Eurocrypt, 1999. • "A Cryptographic Solution to a Game Theoretic Problem", Crypto, 2000. • "On the Power of Claw-Free Permutations", Conference on Security in Communication Networks (SCN), 2002

Algorithmic Game Theory v Can moderate taxes force selfish users minimize global traffic and congestion? • Richard Cole, "Pricing Network Edges for Heterogeneous Selfish Users", Symposium on Theory of Computing (STOC), 2003. • Richard Cole, "The Cost of Taxes for Selfish Routing", ACM Conference on Electronic Commerce (EC), 2003.

My Other Interests • Algorithms: randomized and approx. algorithms, network design… • Coding Theory: relates to crypto too • Complexity Theory: derandomization… • Combinatorics and Graph Theory • Anything else that has proofs and requires problem solving…

Recap of some recent group activities

Signature & Encryption • First provably secure and yet efficient signature and encryption schemes [CS 98, CS 99, CS 02] – lead to new standards for PKI • Efficient schemes utilizing ideal hash functions [Sho 00, Sho 01, DR 02, DFW 03, DFJW 03] • Signature / encryption schemes with extended functionalities [CS 03, DF 03, NKDM 03]
![Authenticated Encryption First formal modeling of publickey authenticated encryption signcryption ADR 02 Authenticated Encryption • First formal modeling of public-key authenticated encryption (signcryption) [ADR 02] •](https://slidetodoc.com/presentation_image_h/ae17fb7eacbfb5d196e30568d2127d1d/image-20.jpg)
Authenticated Encryption • First formal modeling of public-key authenticated encryption (signcryption) [ADR 02] • Parallel authenticated encryption [ADR 02, DFW 03, DFJW 03, Dod 03 a] • Designing authenticated encryption for long messages [DA 03]
![Key Exposure Protection Exposureresilient functions and Allornothing transforms CDH 00 DSS 01 Key Exposure Protection • Exposure-resilient functions and All-ornothing transforms [CDH 00, DSS 01] •](https://slidetodoc.com/presentation_image_h/ae17fb7eacbfb5d196e30568d2127d1d/image-21.jpg)
Key Exposure Protection • Exposure-resilient functions and All-ornothing transforms [CDH 00, DSS 01] • Key-insulated signature and encryption scheme [DKXY 02, DKXY 03] • Intrusion-Resilient Encryption [DKY 03] • Remotely-Keyed Encryption [DA 03] • Server-Aided/Proxy/Proactive Cryptography [NKDN 03, ID 03, DY 02]
![Distributed Computation Byzantine Agreement CKS 00 CKPS 01 KS 01 Threshold Cryptosystems Distributed Computation • Byzantine Agreement [CKS 00, CKPS 01, KS 01] • Threshold Cryptosystems](https://slidetodoc.com/presentation_image_h/ae17fb7eacbfb5d196e30568d2127d1d/image-22.jpg)
Distributed Computation • Byzantine Agreement [CKS 00, CKPS 01, KS 01] • Threshold Cryptosystems [SG 98, Sho 00] • Distributed verifiable random functions and block ciphers [Dod 03 b, DY 03] • Joint generation of special RSA keys [ACS 02] • Two-party computation [NKDN 03, ID 03] • Concurrent protocols composition [DM 00]
![Some Other Projects Digital right management DF 02 DF 03 DFKY 03 Some Other Projects • Digital right management [DF 02, DF 03, DFKY 03] •](https://slidetodoc.com/presentation_image_h/ae17fb7eacbfb5d196e30568d2127d1d/image-23.jpg)
Some Other Projects • Digital right management [DF 02, DF 03, DFKY 03] • Ideal Hash Function Methodology [Dod 03 b, DS 03] • Basing Cryptography on Imperfect Randomness [DS 02, DO 03] • Cryptography and Game Theory [DHR 00] • …
 Victor shoup
Victor shoup Nyu epilepsy center
Nyu epilepsy center Calcul chute de tension section câble
Calcul chute de tension section câble Convalutes
Convalutes Loi de laplace
Loi de laplace A quel courant artistique appartient claude monet
A quel courant artistique appartient claude monet Freinage d'un moteur asynchrone triphasé
Freinage d'un moteur asynchrone triphasé Fluent user services center
Fluent user services center Courant number
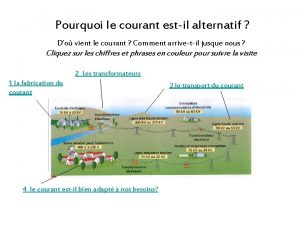
Courant number Un courant alternatif
Un courant alternatif Korhonen courant
Korhonen courant Hacheur reversible en courant
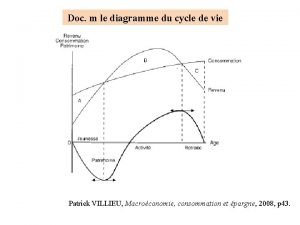
Hacheur reversible en courant Diagramme cycle de vie
Diagramme cycle de vie Source de courant commandée en tension
Source de courant commandée en tension Tension moyenne
Tension moyenne Il nous tient au courant
Il nous tient au courant Courant cognitiviste
Courant cognitiviste Texte courant
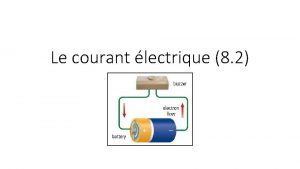
Texte courant Intensité du courant
Intensité du courant Classification des locaux selon nf c 15-100
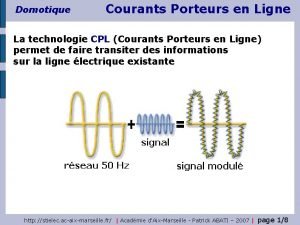
Classification des locaux selon nf c 15-100 Domotique cpl
Domotique cpl Amplitude courant alternatif
Amplitude courant alternatif What image did rizal carved on a piece of batikuling
What image did rizal carved on a piece of batikuling Avery fisher center
Avery fisher center