CLOUD REFERENCE ARCHITECTURE PART 4 Virtual Data Center















- Slides: 49

CLOUD REFERENCE ARCHITECTURE PART 4 – Virtual Data Center Presented by: Ammar Hasayen | MS MVP CISSP | Cybersecurity http: //ahasayen. com Available on Slide. Share & You. Tub @ammarhasay e| en Date: 9 Th May 2020

AMMAR HASAYEN Microsoft MVP | Pluralsight Author | Blogger Book Author About Me: http: //ahasayen. com Blog: http: //blog. ahasayen. com Social Media: @ammarhasayen CISSP | CISM | AWS Architect | Azure Security Engineer | M 365 Security Engineer

Quick Overview of Previous Talk CHECK THE VIDEO DESCRIPTION BELOW FOR LINKS TO PREVIOUS TALK

CRA Cloud reference architecture (CRA) helps organizations address the need for detailed, modular and current architecture guidance for building solutions in the cloud

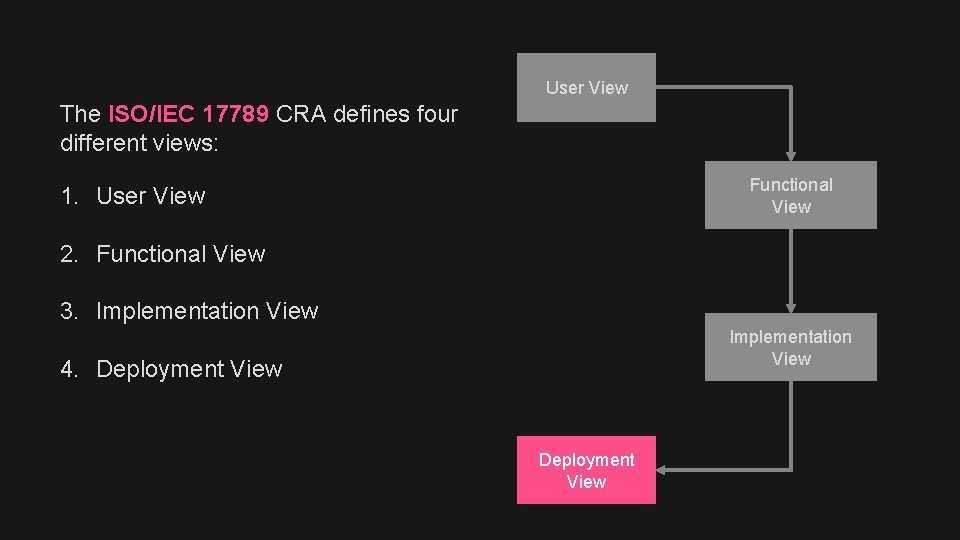
User View The ISO/IEC 17789 CRA defines four different views: Functional View 1. User View 2. Functional View 3. Implementation View 4. Deployment View

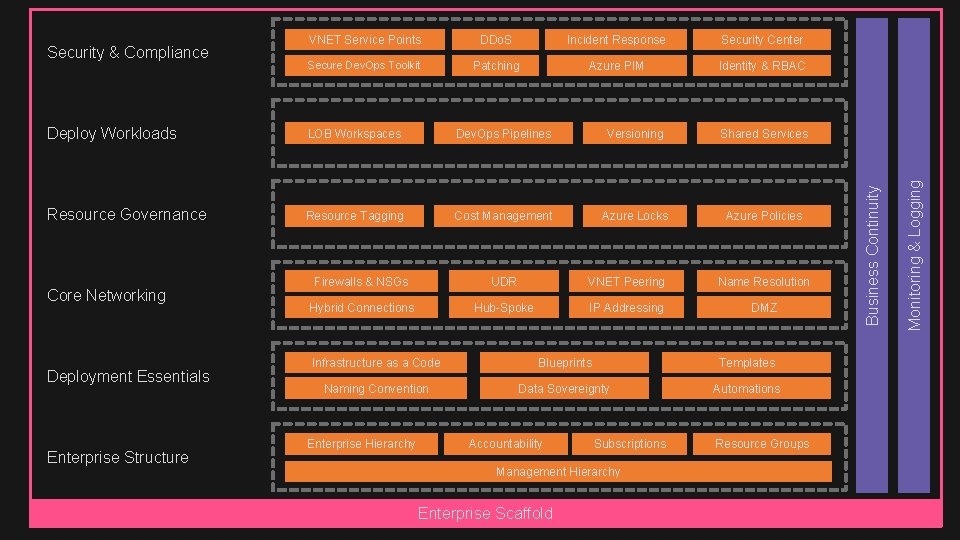
Incident Response Security Center Secure Dev. Ops Toolkit Patching Azure PIM Identity & RBAC Deploy Workloads LOB Workspaces Dev. Ops Pipelines Versioning Shared Services Resource Governance Resource Tagging Cost Management Azure Locks Azure Policies Core Networking Deployment Essentials Enterprise Structure Firewalls & NSGs UDR VNET Peering Name Resolution Hybrid Connections Hub-Spoke IP Addressing DMZ Infrastructure as a Code Blueprints Templates Naming Convention Data Sovereignty Automations Enterprise Hierarchy Accountability Subscriptions Management Hierarchy Enterprise Scaffold Resource Groups Monitoring & Logging DDo. S Business Continuity Security & Compliance VNET Service Points

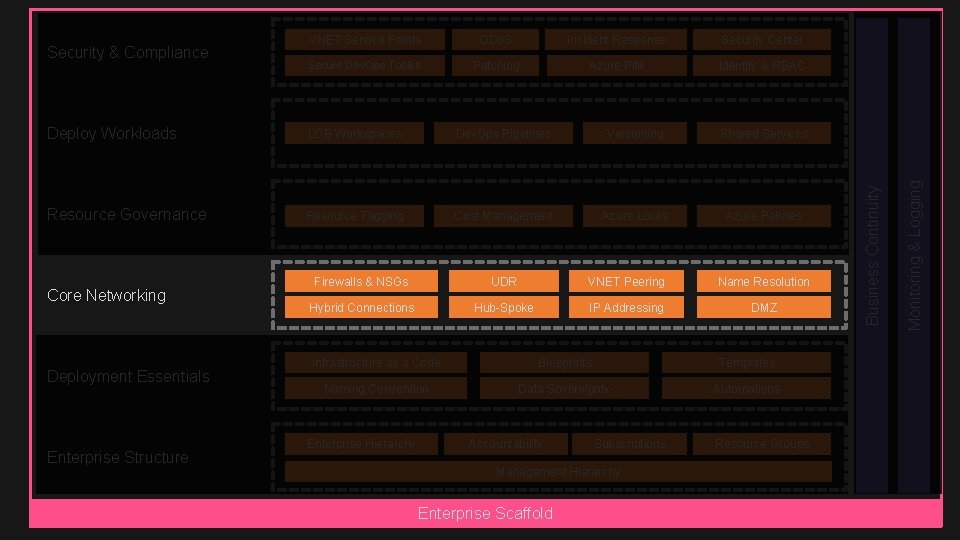
Incident Response Security Center Secure Dev. Ops Toolkit Patching Azure PIM Identity & RBAC Deploy Workloads LOB Workspaces Dev. Ops Pipelines Versioning Shared Services Resource Governance Resource Tagging Cost Management Azure Locks Azure Policies Core Networking Deployment Essentials Enterprise Structure Firewalls & NSGs UDR VNET Peering Name Resolution Hybrid Connections Hub-Spoke IP Addressing DMZ Infrastructure as a Code Blueprints Templates Naming Convention Data Sovereignty Automations Enterprise Hierarchy Accountability Subscriptions Management Hierarchy Enterprise Scaffold Resource Groups Monitoring & Logging DDo. S Business Continuity Security & Compliance VNET Service Points

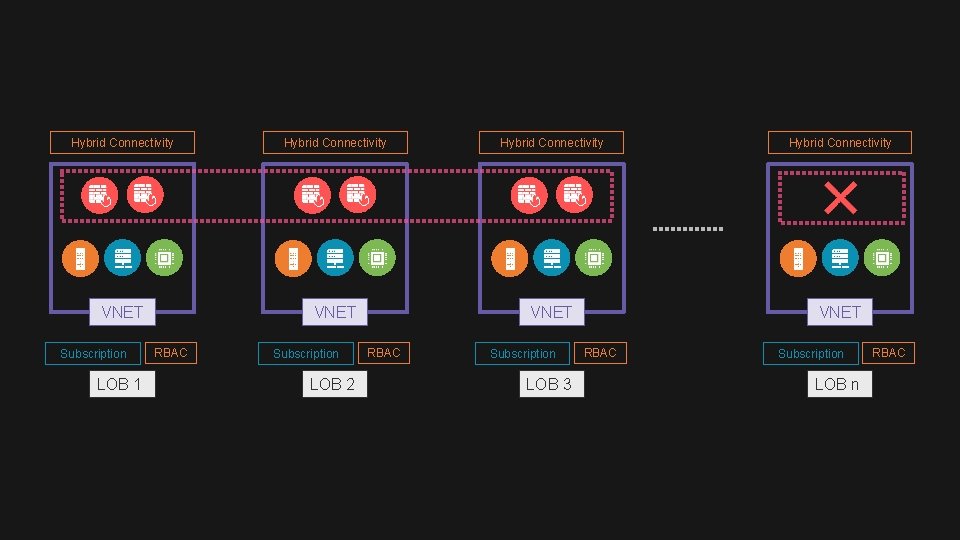
The Need For The Virtual Data Center An approach to isolation, security, and trust in the cloud

Hybrid Connectivity VNET Subscription LOB 1 RBAC Subscription LOB 2 RBAC Subscription LOB 3 RBAC Subscription LOB n RBAC

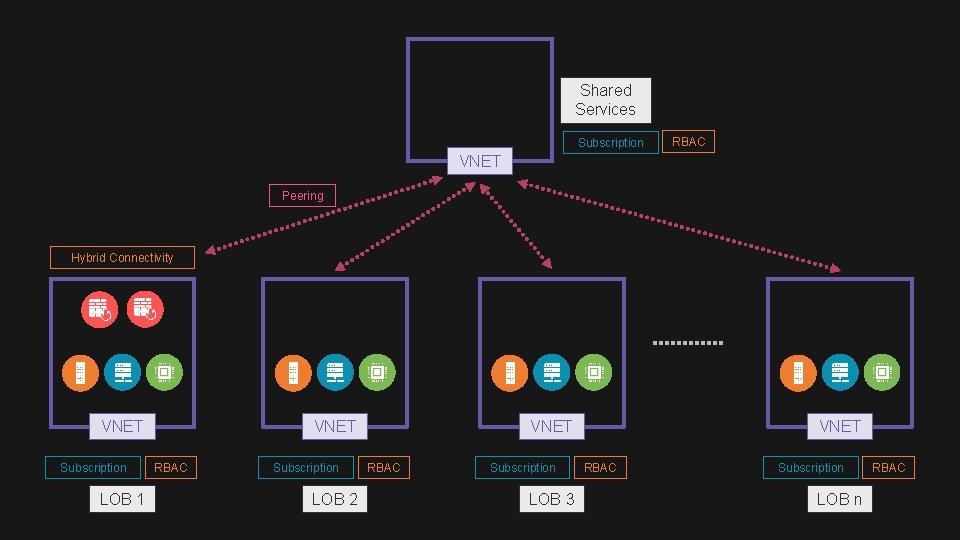
Shared Services Subscription RBAC VNET Peering Hybrid Connectivity VNET Subscription LOB 1 VNET RBAC Subscription LOB 2 VNET RBAC Subscription LOB 3 VNET RBAC Subscription LOB n RBAC

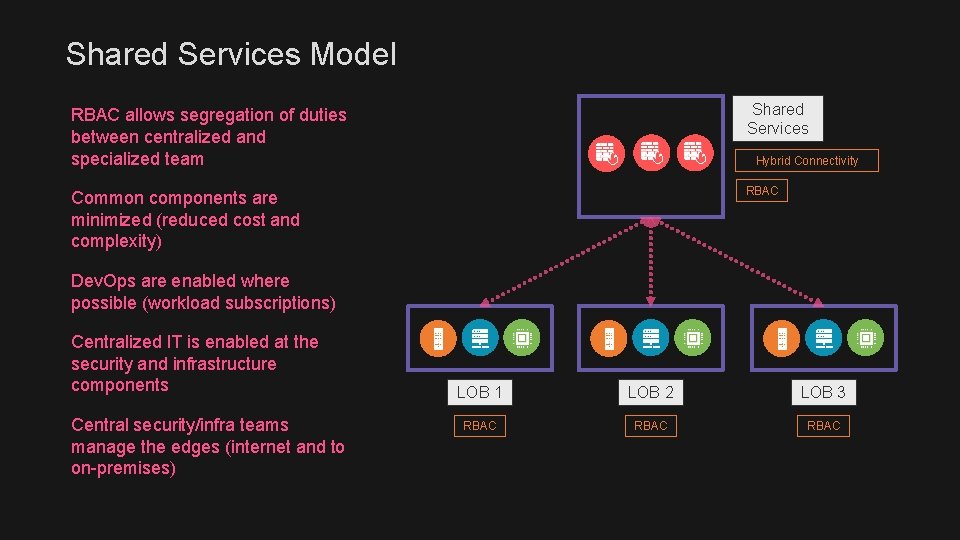
Shared Services Model RBAC allows segregation of duties between centralized and specialized team Shared Services Common components are minimized (reduced cost and complexity) RBAC Hybrid Connectivity Dev. Ops are enabled where possible (workload subscriptions) Centralized IT is enabled at the security and infrastructure components Central security/infra teams manage the edges (internet and to on-premises) LOB 1 LOB 2 LOB 3 RBAC

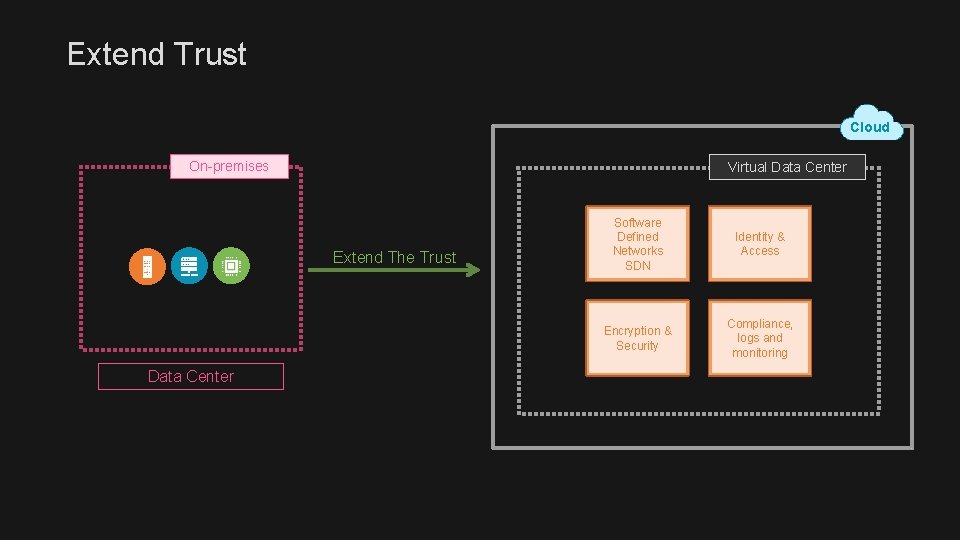
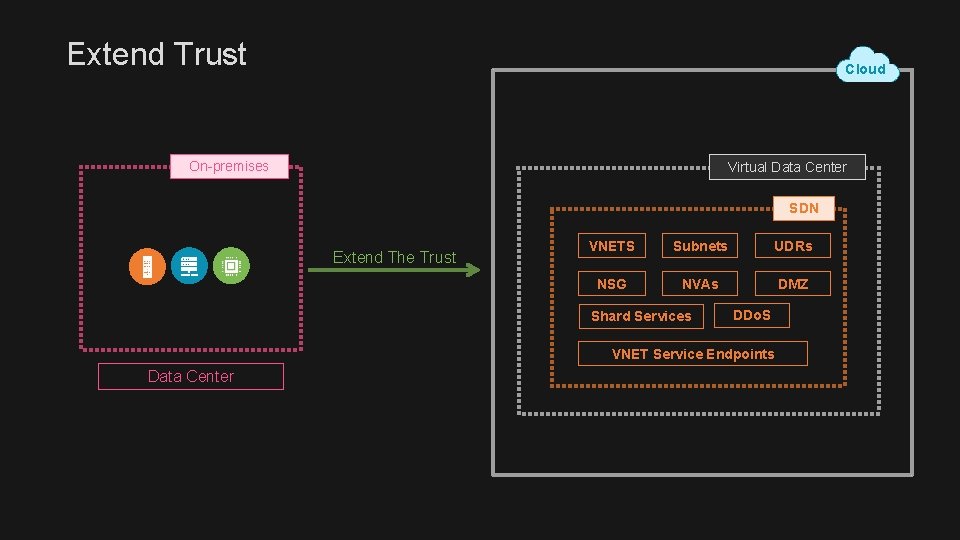
Extend Trust Cloud On-premises Virtual Data Center Extend The Trust Data Center Software Defined Networks SDN Identity & Access Encryption & Security Compliance, logs and monitoring

Extend Trust Cloud On-premises Virtual Data Center SDN Extend The Trust VNETS Subnets UDRs NSG NVAs DMZ Shard Services DDo. S VNET Service Endpoints Data Center

Virtual Data Center An approach to isolation, security, and trust in the cloud

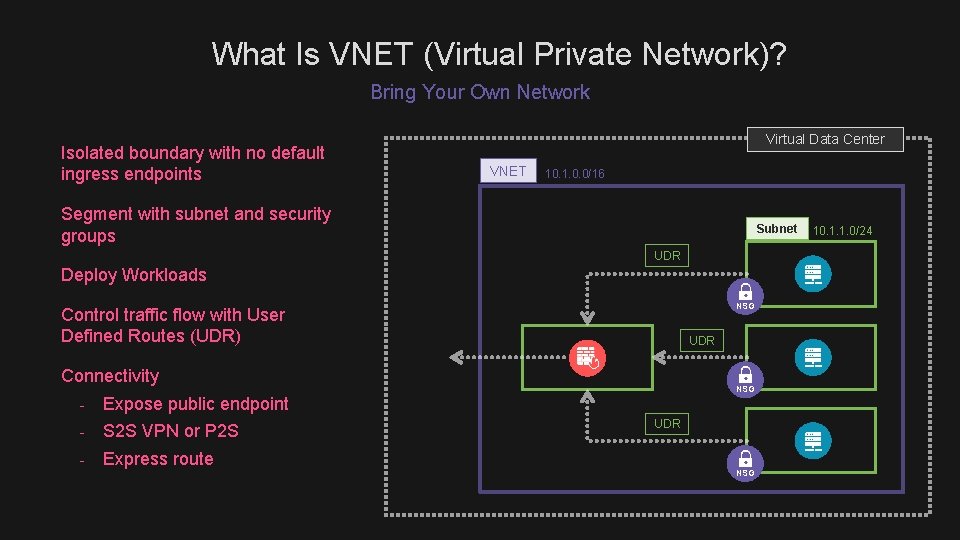
What Is VNET (Virtual Private Network)? Bring Your Own Network Isolated boundary with no default ingress endpoints Virtual Data Center VNET 10. 1. 0. 0/16 Segment with subnet and security groups Subnet UDR Deploy Workloads NSG Control traffic flow with User Defined Routes (UDR) UDR Connectivity - Expose public endpoint - S 2 S VPN or P 2 S - Express route NSG UDR NSG 10. 1. 1. 0/24

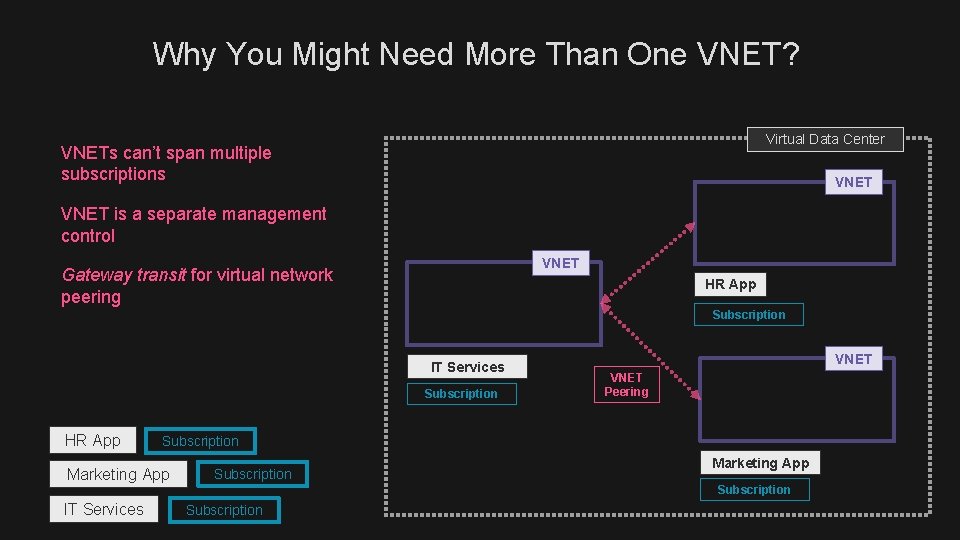
Why You Might Need More Than One VNET? Virtual Data Center VNETs can’t span multiple subscriptions VNET is a separate management control VNET Gateway transit for virtual network peering HR App Subscription IT Services Subscription HR App VNET Peering Subscription Marketing App Subscription IT Services Subscription

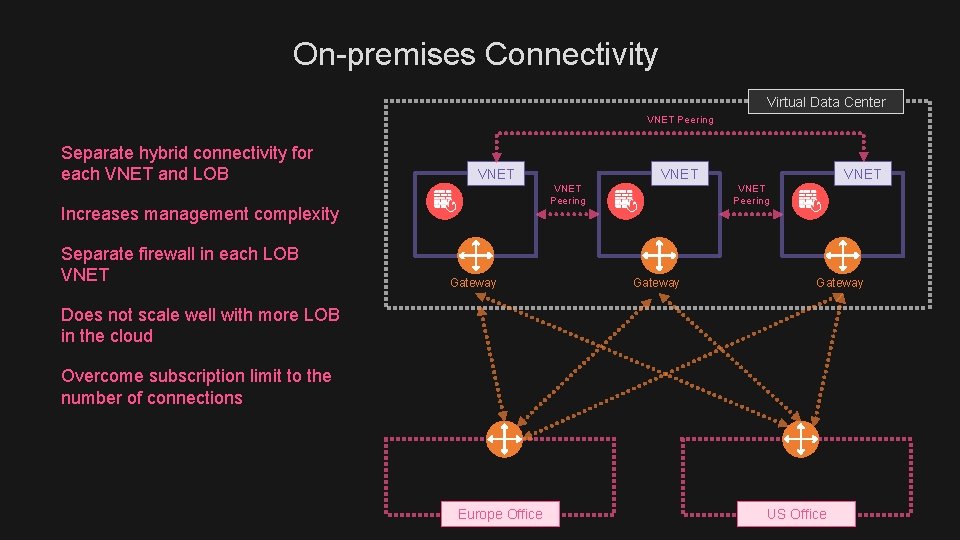
On-premises Connectivity Virtual Data Center VNET Peering Separate hybrid connectivity for each VNET and LOB VNET Increases management complexity Separate firewall in each LOB VNET Peering Gateway VNET Peering Gateway Does not scale well with more LOB in the cloud Overcome subscription limit to the number of connections Europe Office US Office

Cloud Security Alliance (CSA) promotes the use a bastion network

Cloud Security Alliance It is a non-profit organization with a mission to “promote the use of best practices for providing security assurance within cloud computing. The cloud security alliance recommend implementing a preferred and flexible architecture for hybrid cloud connectivity using a “bastion virtual network”. In this architecture, it is possible to connect multiple cloud networks to your on-premises datacenter via one hybrid cloud connection. You build a dedicated virtual network for the hybrid connection and then peers any other networks through the designated bastion network. You can also deploy firewall rule sets to protect traffic flowing in and out of the hybrid connection.

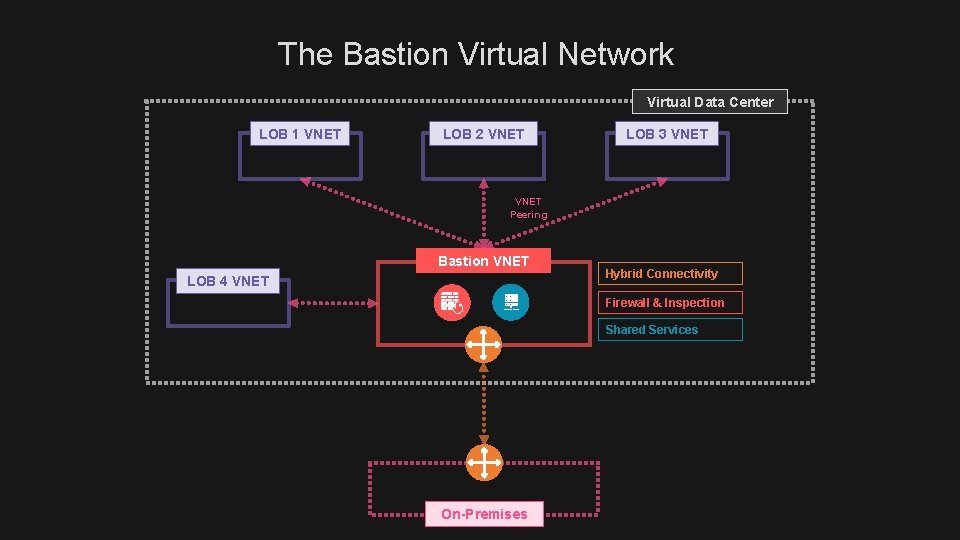
The Bastion Virtual Network Virtual Data Center LOB 1 VNET LOB 2 VNET LOB 3 VNET Peering Bastion VNET LOB 4 VNET Hybrid Connectivity Firewall & Inspection Shared Services On-Premises

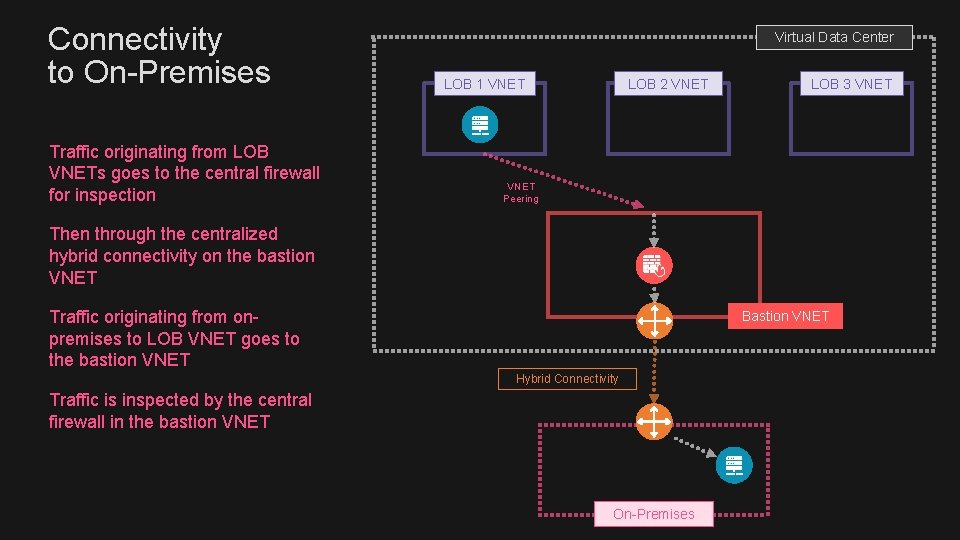
Connectivity to On-Premises Traffic originating from LOB VNETs goes to the central firewall for inspection Virtual Data Center LOB 1 VNET LOB 2 VNET LOB 3 VNET Peering Then through the centralized hybrid connectivity on the bastion VNET Traffic originating from onpremises to LOB VNET goes to the bastion VNET Bastion VNET Hybrid Connectivity Traffic is inspected by the central firewall in the bastion VNET On-Premises

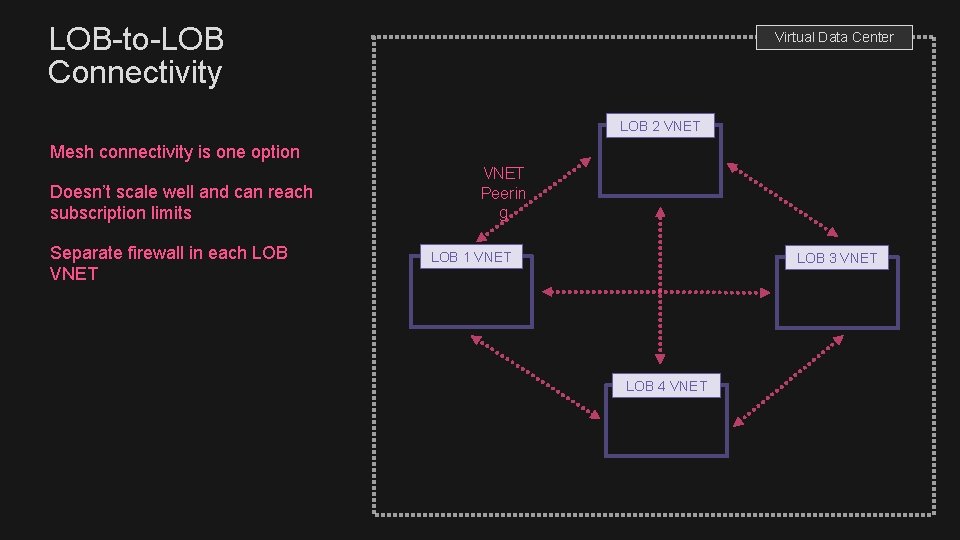
LOB-to-LOB Connectivity Virtual Data Center LOB 2 VNET Mesh connectivity is one option Doesn’t scale well and can reach subscription limits Separate firewall in each LOB VNET Peerin g LOB 1 VNET LOB 3 VNET LOB 4 VNET

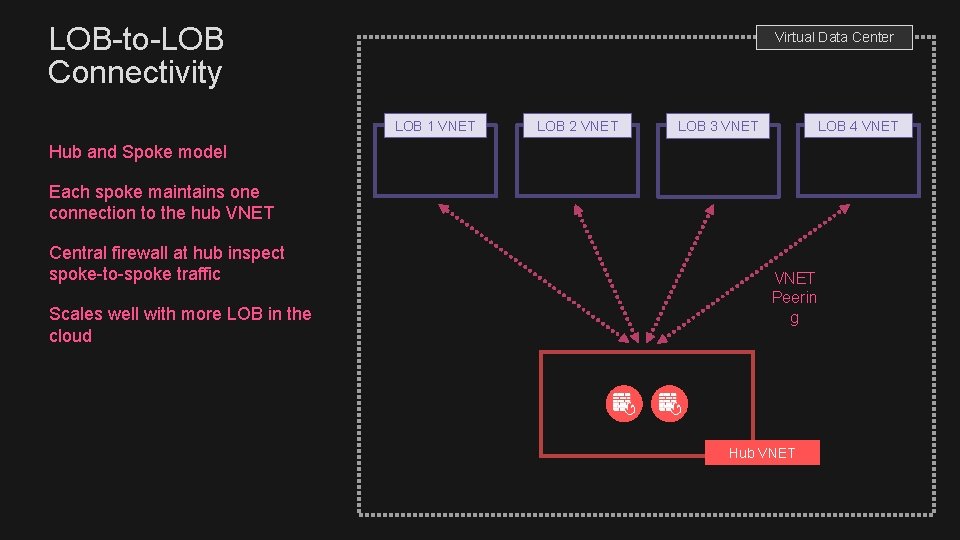
LOB-to-LOB Connectivity Virtual Data Center LOB 1 VNET LOB 2 VNET LOB 4 VNET LOB 3 VNET Hub and Spoke model Each spoke maintains one connection to the hub VNET Central firewall at hub inspect spoke-to-spoke traffic Scales well with more LOB in the cloud VNET Peerin g Hub VNET

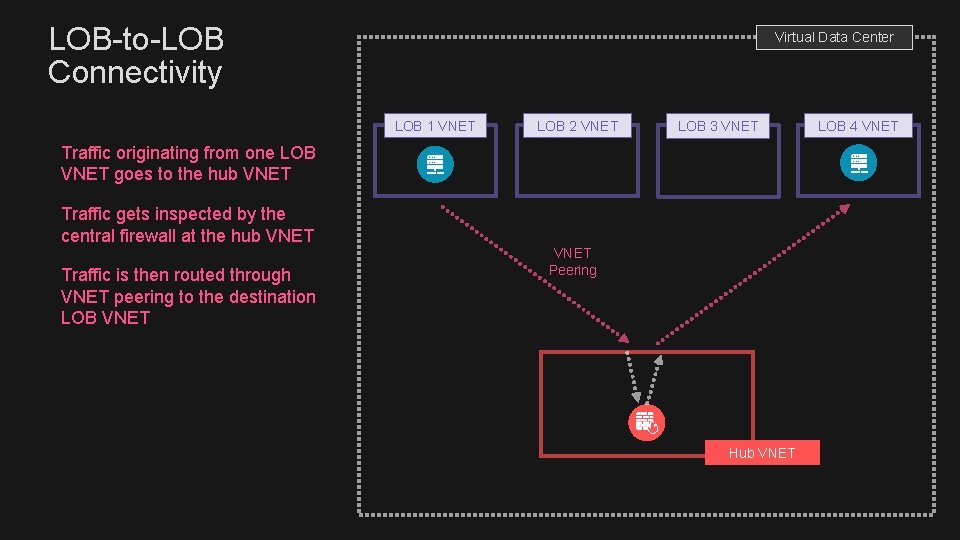
LOB-to-LOB Connectivity Virtual Data Center LOB 1 VNET LOB 2 VNET LOB 3 VNET Traffic originating from one LOB VNET goes to the hub VNET Traffic gets inspected by the central firewall at the hub VNET Traffic is then routed through VNET peering to the destination LOB VNET Peering Hub VNET LOB 4 VNET

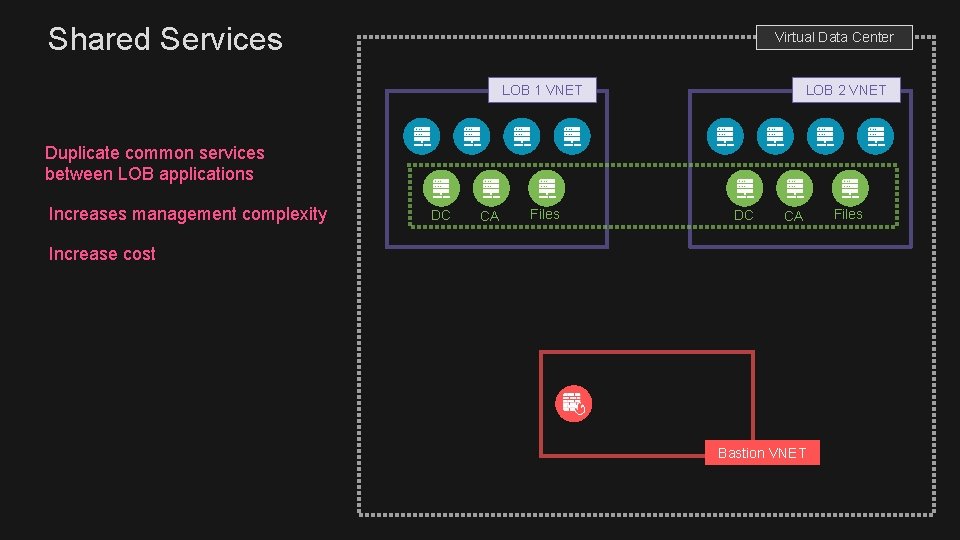
Shared Services Virtual Data Center LOB 1 VNET LOB 2 VNET Duplicate common services between LOB applications Increases management complexity DC CA Files DC CA Increase cost Bastion VNET Files

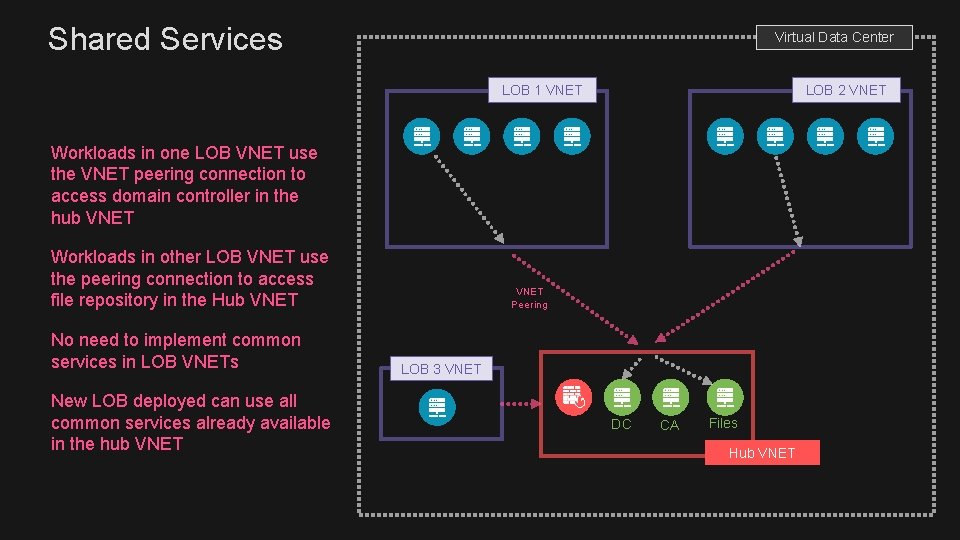
Shared Services Virtual Data Center LOB 1 VNET LOB 2 VNET Workloads in one LOB VNET use the VNET peering connection to access domain controller in the hub VNET Workloads in other LOB VNET use the peering connection to access file repository in the Hub VNET No need to implement common services in LOB VNETs New LOB deployed can use all common services already available in the hub VNET Peering LOB 3 VNET DC CA Files Hub VNET

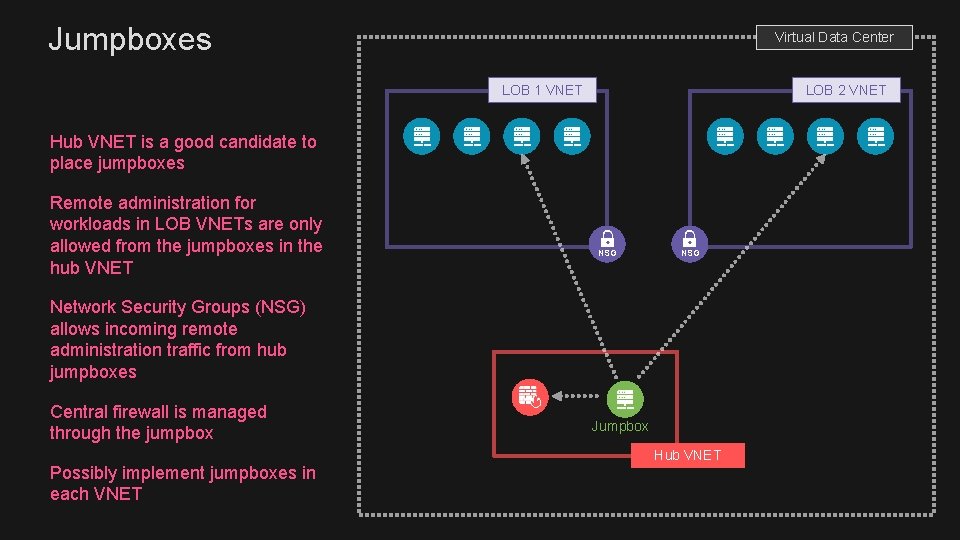
Jumpboxes Virtual Data Center LOB 1 VNET LOB 2 VNET Hub VNET is a good candidate to place jumpboxes Remote administration for workloads in LOB VNETs are only allowed from the jumpboxes in the hub VNET NSG Network Security Groups (NSG) allows incoming remote administration traffic from hub jumpboxes Central firewall is managed through the jumpbox Possibly implement jumpboxes in each VNET Jumpbox Hub VNET

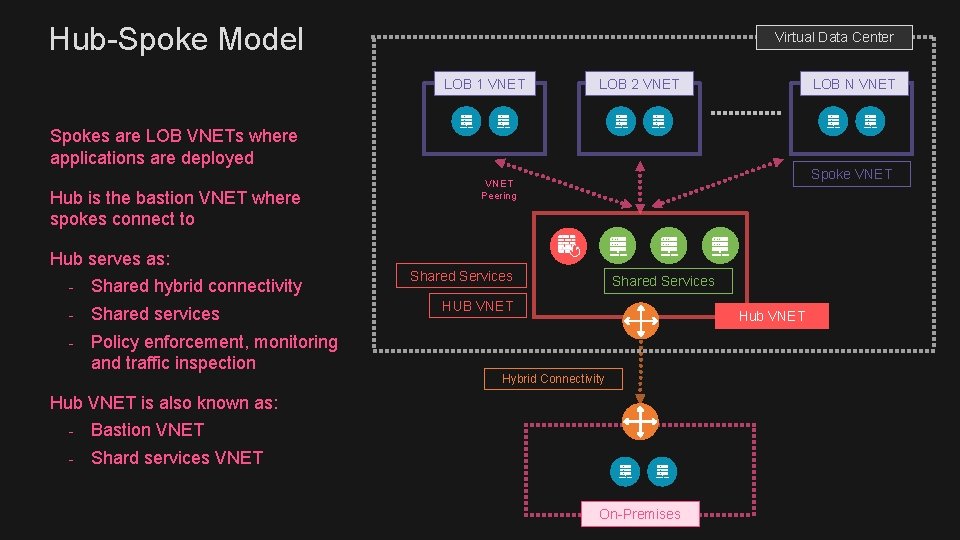
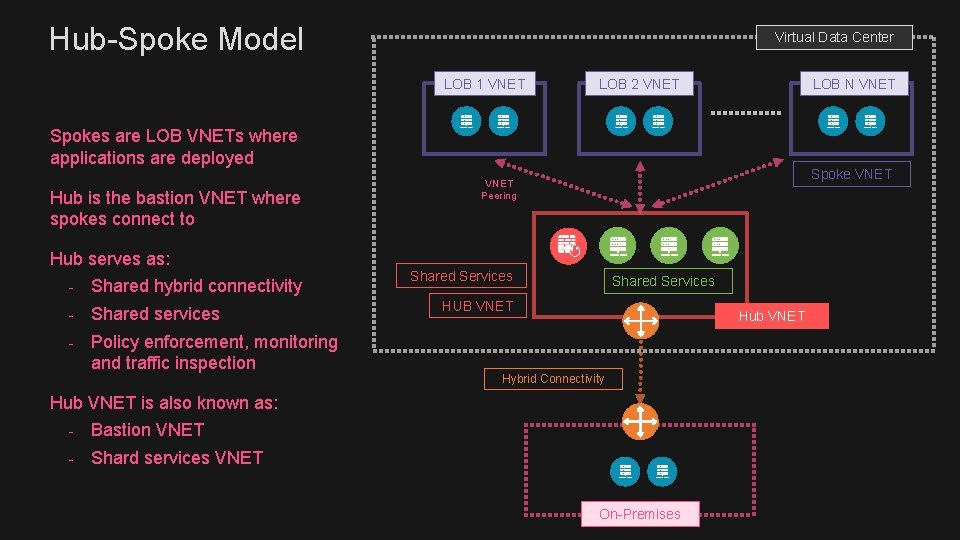
Hub-Spoke Model Virtual Data Center LOB 1 VNET LOB 2 VNET LOB N VNET Spokes are LOB VNETs where applications are deployed Hub is the bastion VNET where spokes connect to Hub serves as: - Shared hybrid connectivity - Shared services - Policy enforcement, monitoring and traffic inspection Spoke VNET Peering Shared Services HUB VNET Hub VNET Hybrid Connectivity Hub VNET is also known as: - Bastion VNET - Shard services VNET On-Premises

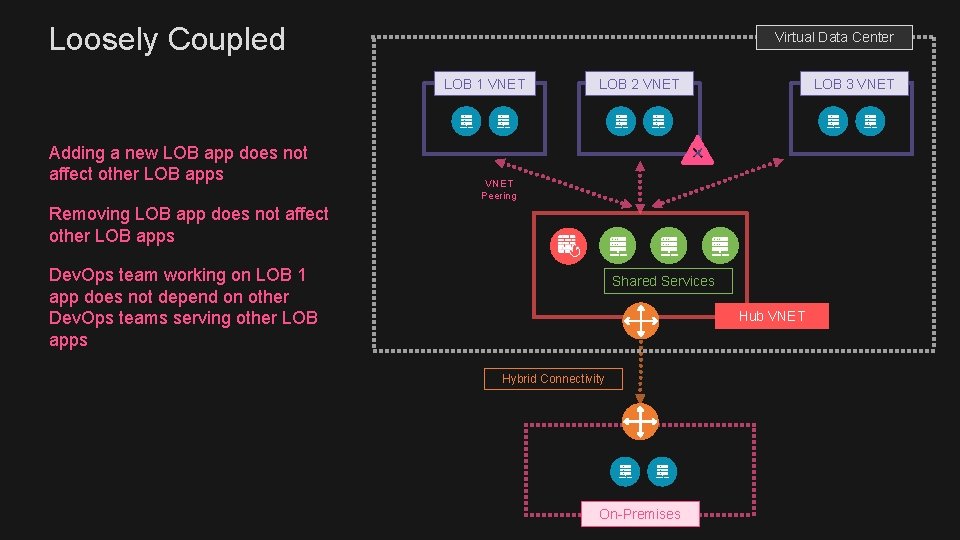
Loosely Coupled Virtual Data Center LOB 1 VNET Adding a new LOB app does not affect other LOB apps LOB 2 VNET LOB 3 VNET Peering Removing LOB app does not affect other LOB apps Dev. Ops team working on LOB 1 app does not depend on other Dev. Ops teams serving other LOB apps Shared Services Hub VNET Hybrid Connectivity On-Premises

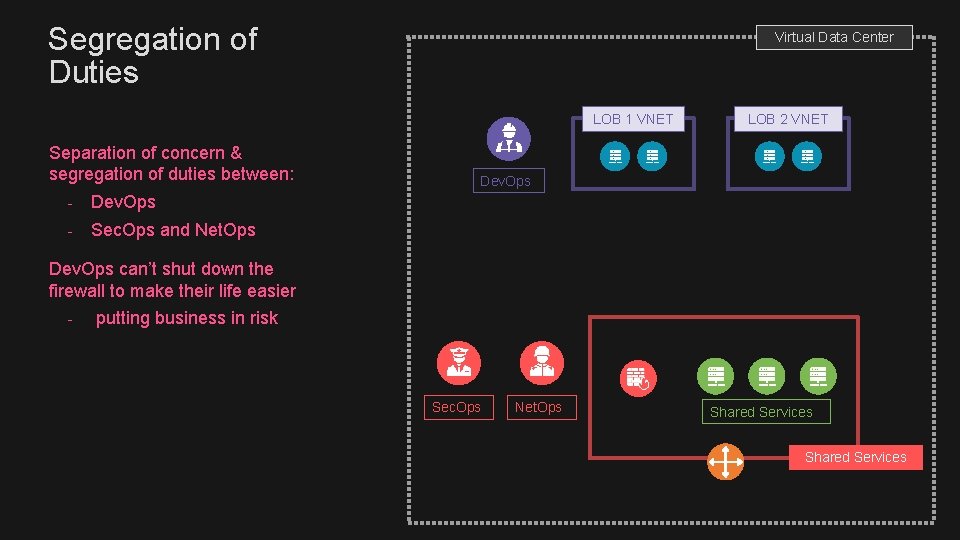
Segregation of Duties Virtual Data Center LOB 1 VNET Separation of concern & segregation of duties between: - Dev. Ops - Sec. Ops and Net. Ops LOB 2 VNET Dev. Ops can’t shut down the firewall to make their life easier - putting business in risk Sec. Ops Net. Ops Shared Services

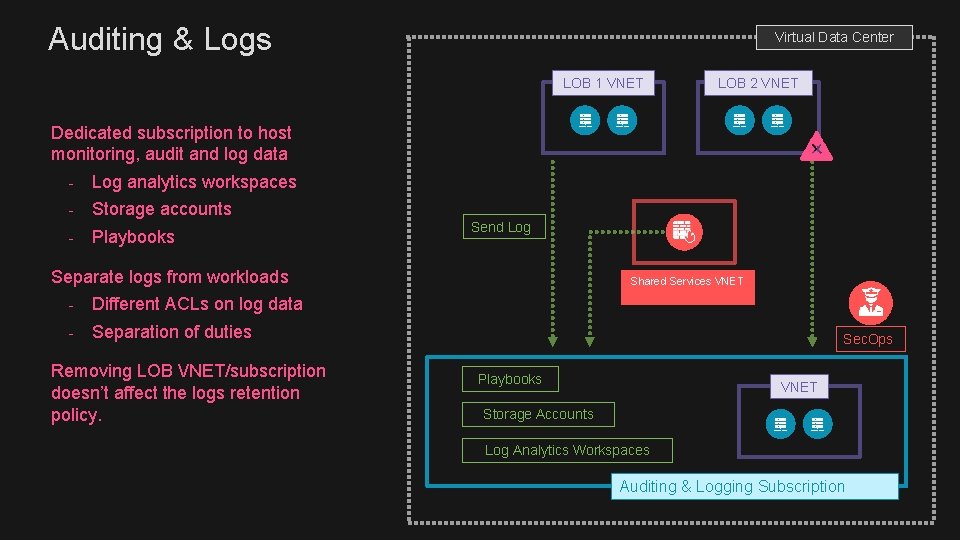
Auditing & Logs Virtual Data Center LOB 1 VNET LOB 2 VNET Dedicated subscription to host monitoring, audit and log data - Log analytics workspaces - Storage accounts - Playbooks Send Log Separate logs from workloads - Different ACLs on log data - Separation of duties Removing LOB VNET/subscription doesn’t affect the logs retention policy. Shared Services VNET Sec. Ops Playbooks VNET Storage Accounts Log Analytics Workspaces Auditing & Logging Subscription

Hub VNET Deep Dive The need for “Financial Governance”

Hub-Spoke Model Virtual Data Center LOB 1 VNET LOB 2 VNET LOB N VNET Spokes are LOB VNETs where applications are deployed Hub is the bastion VNET where spokes connect to Hub serves as: - Shared hybrid connectivity - Shared services - Policy enforcement, monitoring and traffic inspection Spoke VNET Peering Shared Services HUB VNET Hub VNET Hybrid Connectivity Hub VNET is also known as: - Bastion VNET - Shard services VNET On-Premises

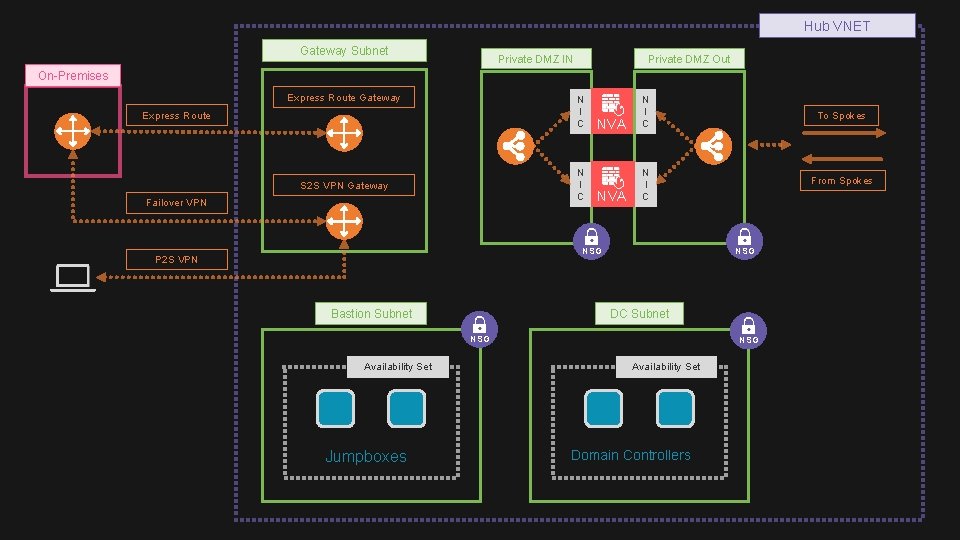
Hub VNET Gateway Subnet Private DMZ IN Private DMZ Out On-Premises Express Route Gateway N I C Express Route N I C S 2 S VPN Gateway Failover VPN NVA N I C To Spokes From Spokes NVA N I C NSG P 2 S VPN Bastion Subnet NSG DC Subnet NSG Availability Set Jumpboxes NSG Availability Set Domain Controllers

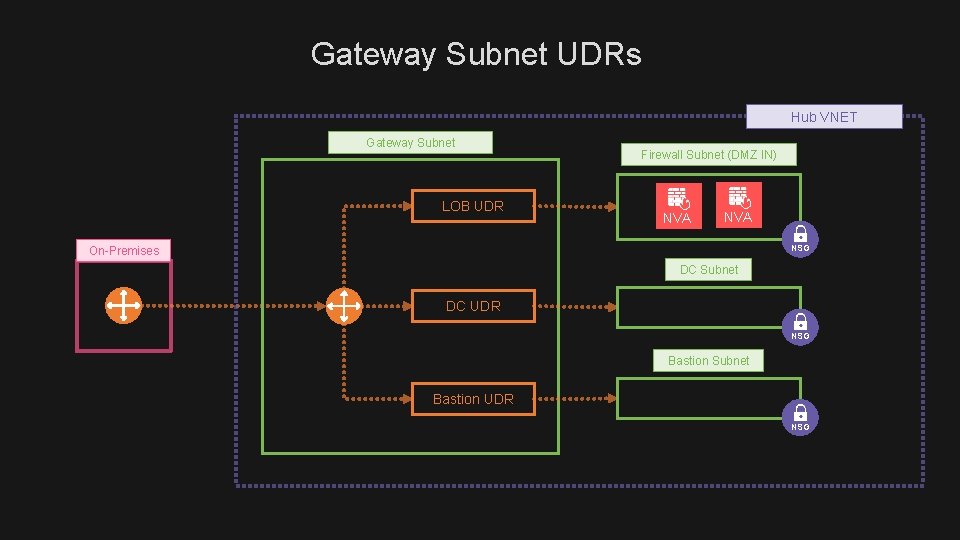
Gateway Subnet UDRs Hub VNET Gateway Subnet LOB UDR Firewall Subnet (DMZ IN) NVA NSG On-Premises DC Subnet DC UDR NSG Bastion Subnet Bastion UDR NSG

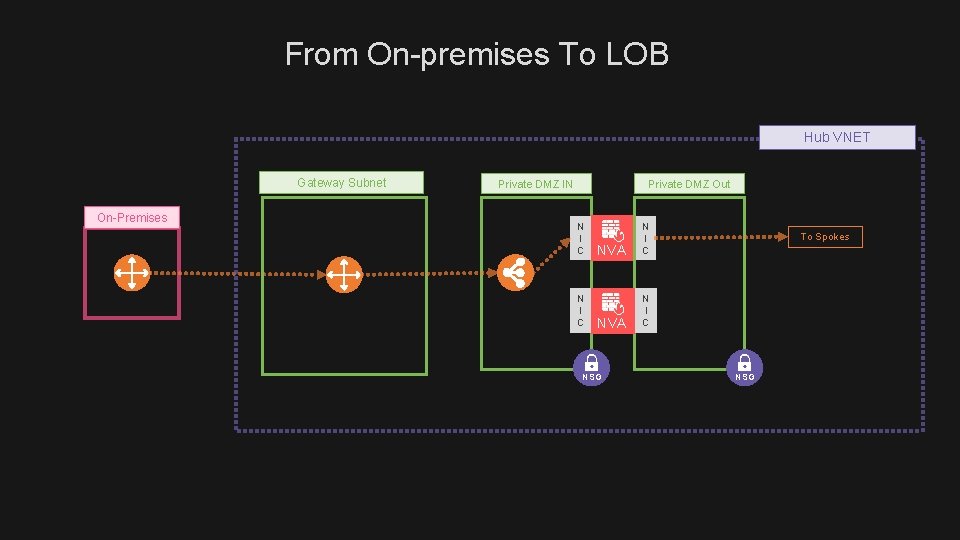
From On-premises To LOB Hub VNET Gateway Subnet On-Premises Private DMZ IN Private DMZ Out N I C NVA N I C NSG To Spokes NSG

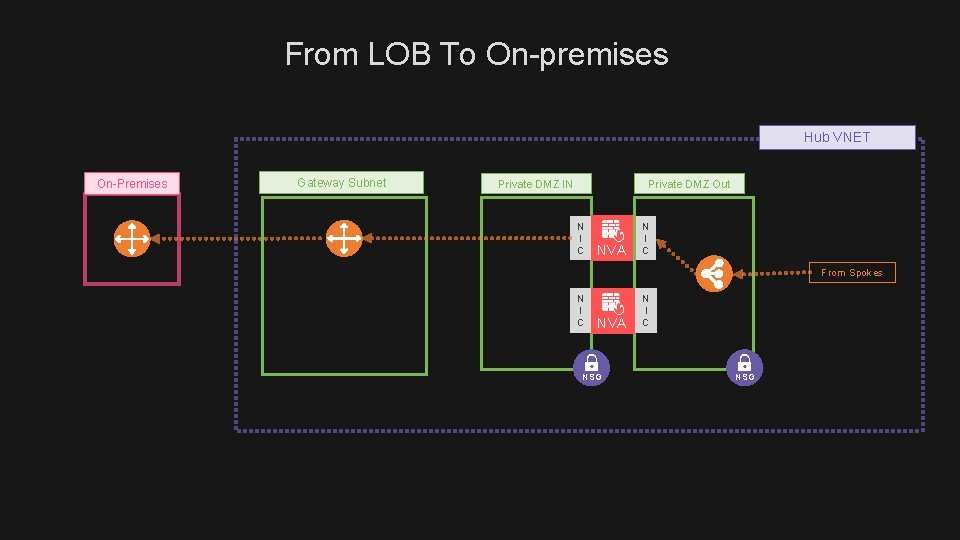
From LOB To On-premises Hub VNET On-Premises Gateway Subnet Private DMZ IN Private DMZ Out N I C NVA N I C From Spokes N I C NVA NSG N I C NSG

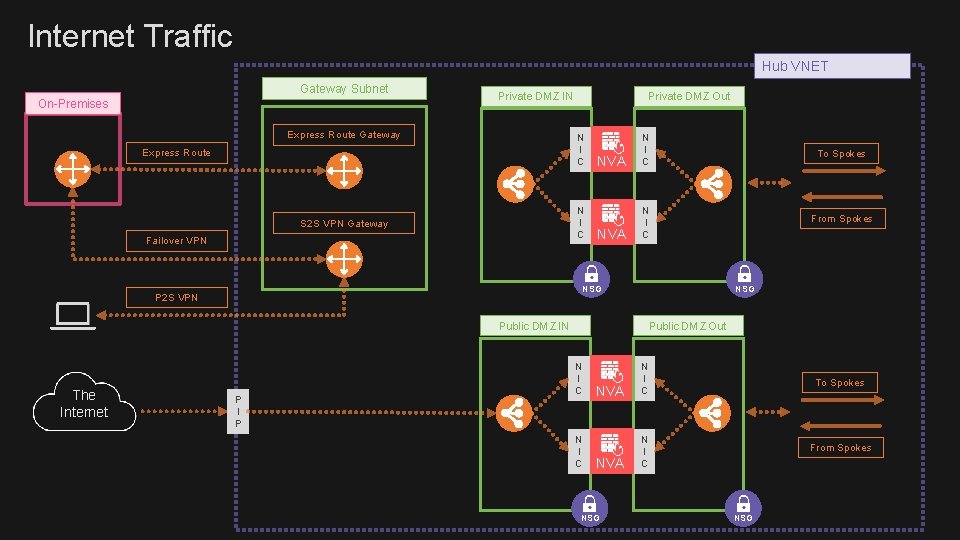
Internet Traffic Hub VNET Gateway Subnet On-Premises Private DMZ IN Express Route Gateway Private DMZ Out N I C Express Route N I C S 2 S VPN Gateway Failover VPN NVA N I C To Spokes From Spokes NVA N I C NSG P 2 S VPN NSG Public DMZ IN The Internet P I P Public DMZ Out N I C NVA N I C To Spokes From Spokes NVA N I C NSG

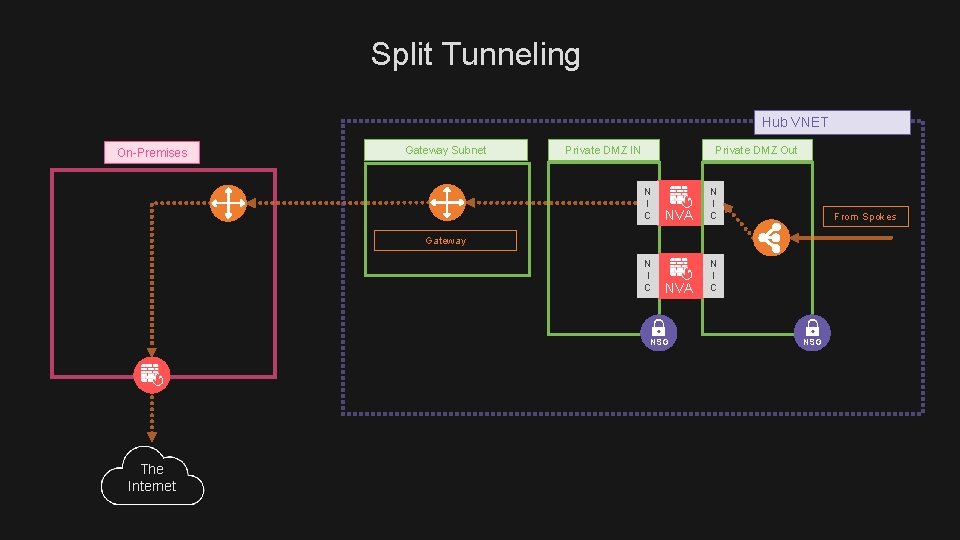
Split Tunneling Hub VNET On-Premises Gateway Subnet Private DMZ IN Private DMZ Out N I C NVA N I C From Spokes Gateway N I C NSG The Internet NSG

Multiple Regions Europe Virtual Data Center Spoke 2 Spoke n Hub VNET Spoke 1 Hub VNET US Virtual Data Center US Office Europe Office Spoke 1 Spoke 2 Spoke n

Let Me Know Your Feedback PLEASE SHARE YOUR FEEDBACK ON ONE OF MY SOCIAL CHANNELS @ammarhasayen

Thank You For Your Time YOU CAN ACCESS THE SLIDES FROM Slide. Share @ammarhasayen

Watch It Online YOU CAN WATCH THIS PRESENTATION ON YOUTUBE http: //You. Tube. com/ammarhasayen

CONNECT ON SOCIAL MEDIA @ammarhasayen

CHECK OUT MY BLOG http: //blog. ahasayen. com

CHECK OUT COURSES IN MY PLURALSIGH T https: //www. pluralsight. com/authors/ammar-hasayen

IMPLEMENTIN G AZURE AD PRIVILEGED IDENTITY MANAGEMENT https: //www. pluralsight. com/courses/microsoft-azure-privileged-identity-management-implementing

COPYRIGHT STATEMENT I want to help you share knowledge and creativity, to build a more equitable, accessible, and innovative world, by unlocking the potential of the internet to drive new era of development, growth and productivity. This is why I provide you with my copyright license, to make it easy for you to share and use creative work on simple terms and conditions. This license lets you remix, tweak, and build upon my work non-commercially, as long as you credit me and license your new creations under the identical terms. Attribution-Non. Commercial-Share. Alike https: //creativecommons. org/licenses/by-nc-sa/4. 0/legalcode

AMMAR HASAYEN @ammarhasayen