Cloud Computing Cloud computing refers to applications and















































- Slides: 101

Cloud Computing • Cloud computing refers to applications and services that run on a distributed network using virtualized resources and accessed by common Internet protocols and networking standards. • It is distinguished by the notion that resources are virtual and limitless and that details of the physical systems on which software runs are abstracted from the user.

• Abstraction: – Cloud computing abstracts the details of system implementation from users and developers. – Applications run on physical systems that aren't specified, – data is stored in locations that are unknown, – administration of systems is outsourced to others, and access by users is ubiquitous.

• Virtualization: – Cloud computing virtualizes systems by pooling and sharing resources. – Systems and storage can be provisioned as needed from a centralized infrastructure, – costs are assessed on a metered basis, – multi-tenancy is enabled, – and resources are scalable with agility.

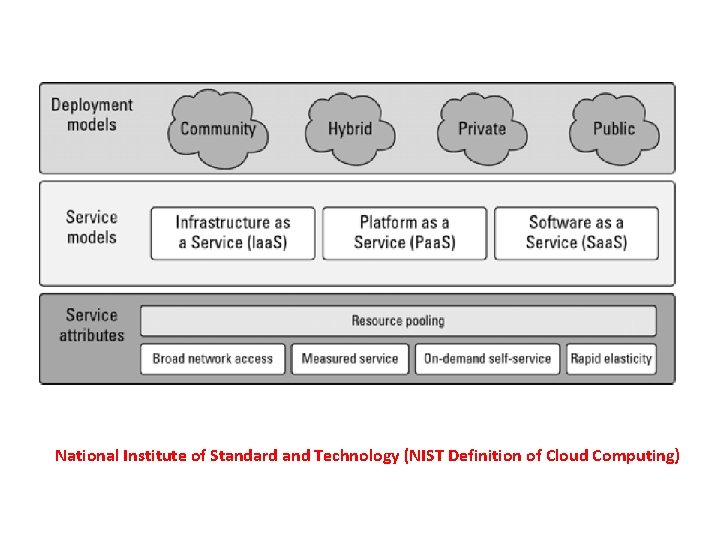
Cloud Types • Deployment Model: • Refers to location and management of the cloud’s infrastructure • Service Model • Consists of particular types of services that can be accessed on cloud computing platform • Some widely used model • NIST Model • The Cloud Cube Model

National Institute of Standard and Technology (NIST Definition of Cloud Computing)

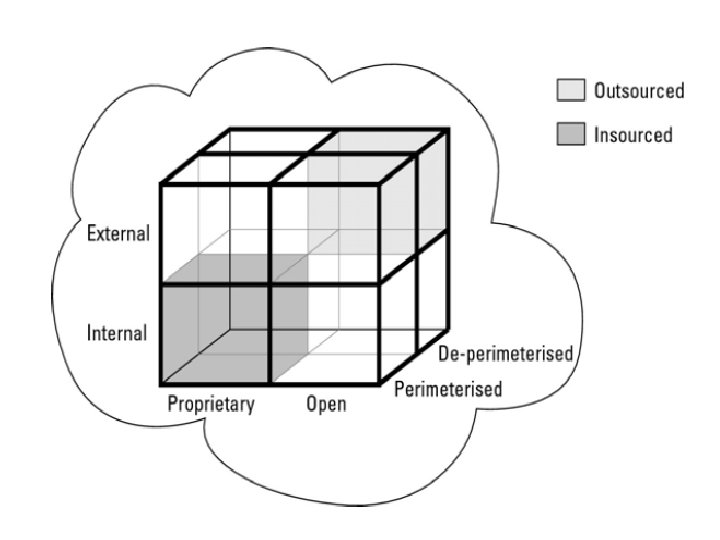
The Cloud Cube Model • Physical location of the data: Internal (I) / External (E) determines your organization's boundaries. • Ownership: Proprietary (P) / Open (O) is a measure of not only the technology ownership, but of interoperability, ease of data transfer, and degree of vendor application lock-in. • Security boundary: Perimeterised (Per) / De-perimiterised (D-p) is a measure of whether the operation is inside or outside the security boundary or network firewall. • Sourcing: Insourced or Outsourced means whether the service is provided by the customer or the service provider.


Deployment Models

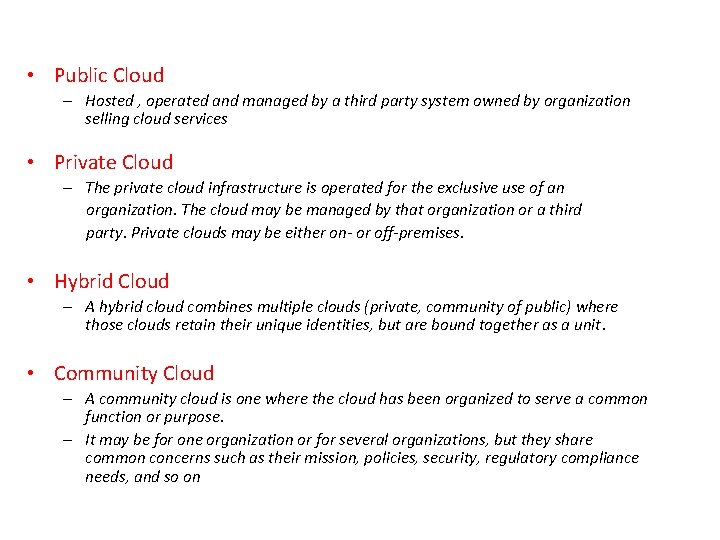
• Public Cloud – Hosted , operated and managed by a third party system owned by organization selling cloud services • Private Cloud – The private cloud infrastructure is operated for the exclusive use of an organization. The cloud may be managed by that organization or a third party. Private clouds may be either on- or off-premises. • Hybrid Cloud – A hybrid cloud combines multiple clouds (private, community of public) where those clouds retain their unique identities, but are bound together as a unit. • Community Cloud – A community cloud is one where the cloud has been organized to serve a common function or purpose. – It may be for one organization or for several organizations, but they share common concerns such as their mission, policies, security, regulatory compliance needs, and so on

Service Models

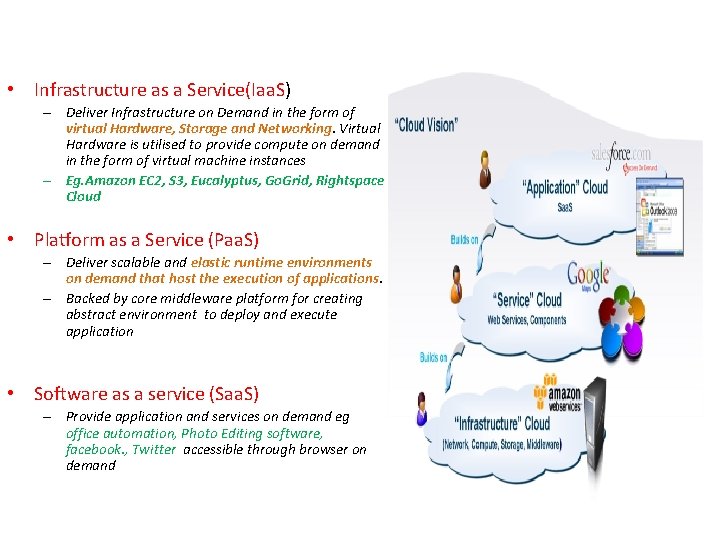
• Infrastructure as a Service(Iaa. S) – Deliver Infrastructure on Demand in the form of virtual Hardware, Storage and Networking. Virtual Hardware is utilised to provide compute on demand in the form of virtual machine instances – Eg. Amazon EC 2, S 3, Eucalyptus, Go. Grid, Rightspace Cloud • Platform as a Service (Paa. S) – Deliver scalable and elastic runtime environments on demand that host the execution of applications. – Backed by core middleware platform for creating abstract environment to deploy and execute application • Software as a service (Saa. S) – Provide application and services on demand eg office automation, Photo Editing software, facebook. , Twitter accessible through browser on demand

Cloud Companies/Service Providers

Benefits of Cloud Computing • • • Lower Computational Costs Improved Performance Reduced Software Costs Instant Software updates Unlimited storage capacity Increased Data Reliability Universal Document Access Latest version availability Easier Group Collaboration/ Sharing Device Independence

Disadvantages of Cloud Computing • • • Requires constant Internet Connection Does not work well with low speed connection Stored data might not be Secured Stored data can be lost Features might be limited

VIRTUALIZATION & CLOUD COMPUTING Lecture # 16 -17 CSE 423 Introduction to Cloud Computing

Cloud Computing in a nutshell • Analogy to electricity use • Technologies such as cluster, grid, and now cloud computing, have all aimed at allowing access to large amounts of computing power in a fully virtualized manner, by aggregating resources and offering a single system view • Utility computing describes a business model for on-demand delivery of computing power; consumers pay providers based on usage. • It denotes a model on which a computing infrastructure is viewed as a “cloud, ” from which businesses and individuals access applications from anywhere in the world on demand

Cloud Computing in a nutshell • BUYYA • “Cloud is a parallel and distributed computing system consisting of a collection of inter-connected and virtualized computers that are dynamically provisioned and presented as one or more unified computing resources based on service-level agreements (SLA) established through negotiation between the service provider and consumers. ” • NIST • a pay-per-use model for enabling available, convenient, on-demand network access to a shared pool of configurable computing resources (e. g. networks, servers, storage, applications, services) that can be rapidly provisioned and released with minimal management effort or service provider interaction. ”

Cloud Computing in a nutshell • While there are countless other definitions, there seems to be common characteristics between the most notable ones listed above, which a cloud should have: ( (i) pay-per-use (no ongoing commitment, utility prices); (ii) elastic capacity and the illusion of infinite resources; (iii) self-service interface (iv) resources that are abstracted or virtualised.

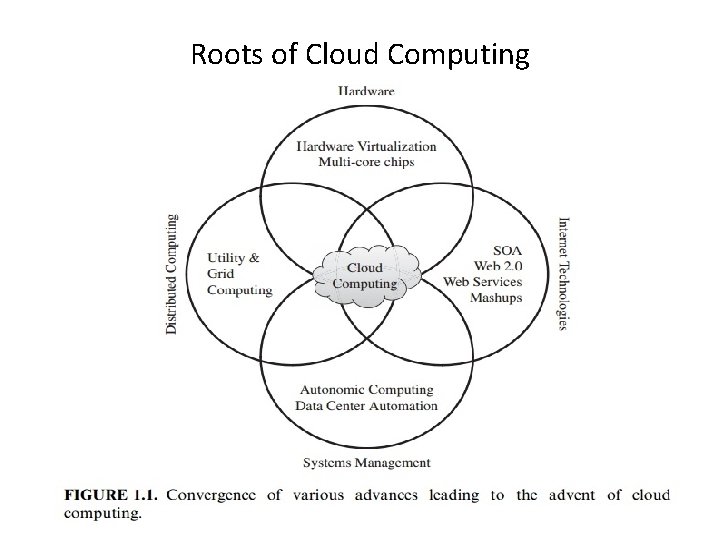
Roots of Cloud Computing

Roots of Cloud Computing (i) Mainframe to cloud (ii) SOA, Web Services, Web 2. 0 and Mashups (iii) Grid Computing (iv) Utility Computing (v)Hardware Virtualization (vi)Virtual Appliance and OVF (vii) Autonomic Computing

From Mainframe to cloud • Currently experiencing a switch in the IT world, from in-house generated computing power into utility-supplied computing resources delivered over the Internet as Web services • Computing delivered as a utility can be defined as “on demand delivery of infrastructure, applications, and business processes in a security-rich, shared, scalability based computer environment over the Internet for a fee” • Advantage to both consumer and providers • Earlier provided timeshared mainframes , declined due to advent of fast and inexpensive microprocessors

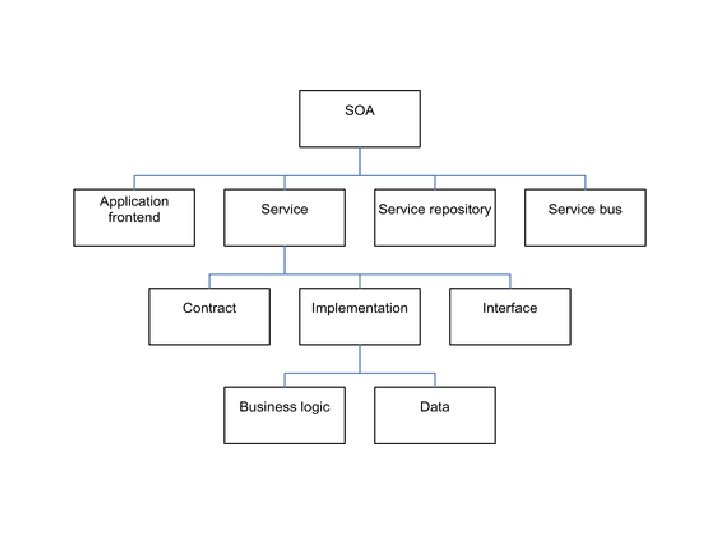
SOA, Web Services, Web 2. 0 and Mashups • Web services can glue together applications running on different messaging product platforms, enabling information from one application to be made available to others, and enabling internal applications to be made available over the Internet. • The purpose of a SOA is to address requirements of loosely coupled, standards-based, and protocol-independent distributed computing • Services such user authentication, e-mail, payroll management, and calendars are examples of building blocks that can be reused and combined in a business solution in case a single, ready-made system does not provide all those features


Grid Computing • Grid computing is the collection of computer resources from multiple locations to reach a common goal. The grid can be thought of as a distributed system with non-interactive workloads that involve a large number of files. • A key aspect of the grid vision realization has been building standard Web services-based protocols that allow distributed resources to be “discovered, accessed, allocated, monitored, accounted for, and billed for. . • Issues: • QOS, Avaibility of resource with diverse software configuration • Soln: virtualisation

Utility Computing • Utility computing is a service provisioning model in which a service provider makes computing resources and infrastructure management available to the customer as needed, and charges them for specific usage rather than a flat rate. • In utility computing environments, users assign a “utility” value to their jobs, where utility is a fixed or time-varying valuation that captures various Qo. S constraints (deadline, importance, satisfaction). • The service providers then attempt to maximize their own utility, where said utility may directly correlate with their profit.

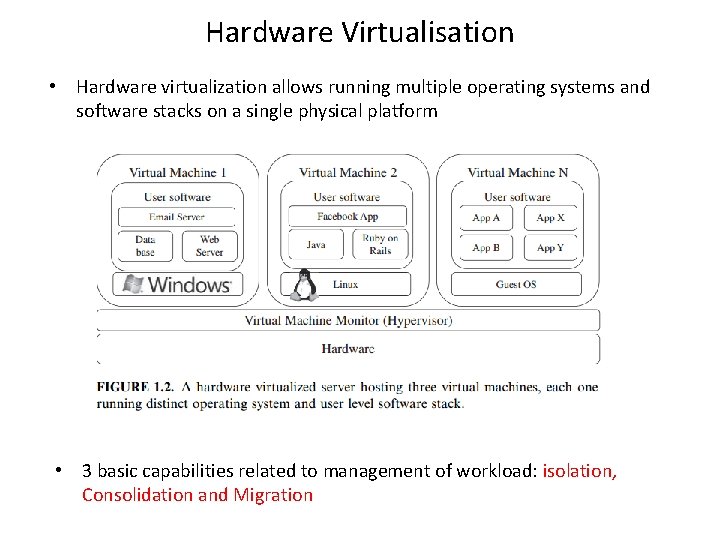
Hardware Virtualisation • Hardware virtualization allows running multiple operating systems and software stacks on a single physical platform • 3 basic capabilities related to management of workload: isolation, Consolidation and Migration

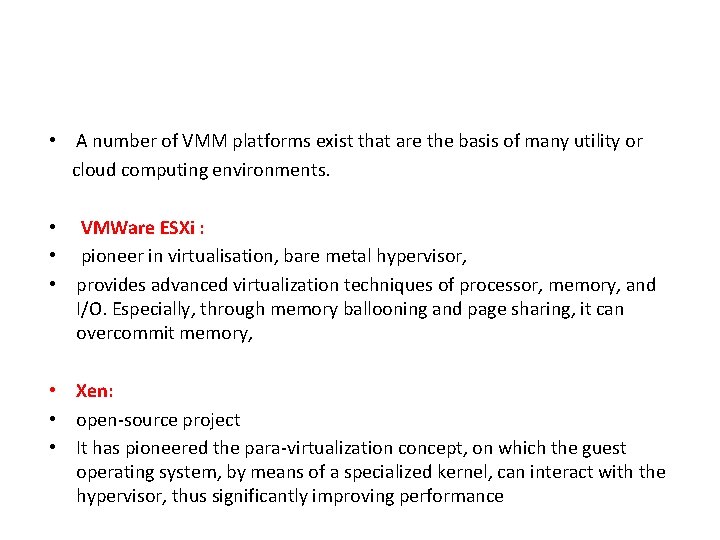
• A number of VMM platforms exist that are the basis of many utility or cloud computing environments. • VMWare ESXi : • pioneer in virtualisation, bare metal hypervisor, • provides advanced virtualization techniques of processor, memory, and I/O. Especially, through memory ballooning and page sharing, it can overcommit memory, • Xen: • open-source project • It has pioneered the para-virtualization concept, on which the guest operating system, by means of a specialized kernel, can interact with the hypervisor, thus significantly improving performance

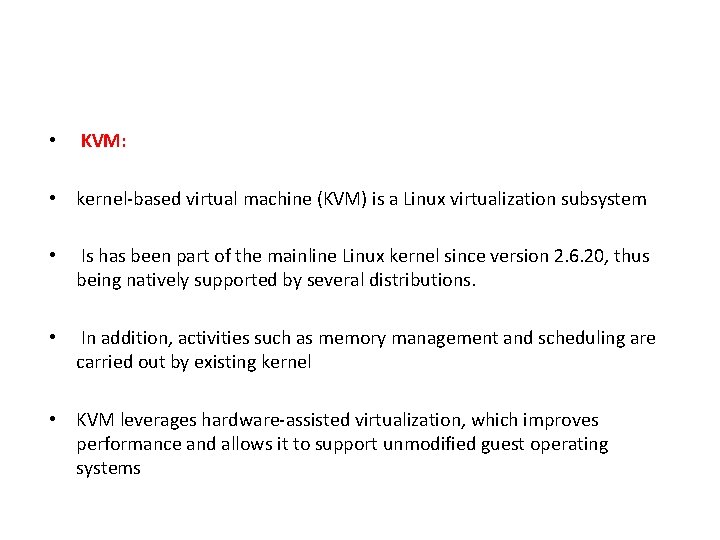
• KVM: • kernel-based virtual machine (KVM) is a Linux virtualization subsystem • Is has been part of the mainline Linux kernel since version 2. 6. 20, thus being natively supported by several distributions. • In addition, activities such as memory management and scheduling are carried out by existing kernel • KVM leverages hardware-assisted virtualization, which improves performance and allows it to support unmodified guest operating systems

Virtual Appliance and OVF(open virtual format) • An application combined with the environment needed to run it (operating system, libraries, compilers, databases, application containers, and so forth) is referred to as a “virtual appliance. ” • A virtual appliance is a pre-integrated, self contained system that is made by combining a software application (e. g. , server software) with just enough operating system for it to run optimally on industry standard hardware or a virtual machine e. g. , VMWare, Virtual. Box • In a multitude of hypervisors, where each one supports a different VM image format and the formats are incompatible with one another, a great deal of interoperability issues arises. • For instance, Amazon has its Amazon machine image (AMI) format, made popular on the Amazon EC 2 public cloud. Other formats are used by Citrix Xen. Server, several Linux distributions that ship with KVM, Microsoft Hyper-V, and VMware ESX

Autonomic Computing • The increasing complexity of computing systems has motivated research on autonomic computing, which seeks to improve systems by decreasing human involvement in their operation • Autonomic, or self-managing, systems rely on monitoring probes and gauges (sensors), on an adaptation engine (autonomic manager) for computing optimizations based on monitoring data, and on effectors to carry out changes on the system.

Migration • When and how to migrate one’s application into a cloud ? • What part or component of the IT application to migrate into a cloud and what not to migrate into a cloud ? • What kind of customers really benefit from migrating their IT into the cloud ?

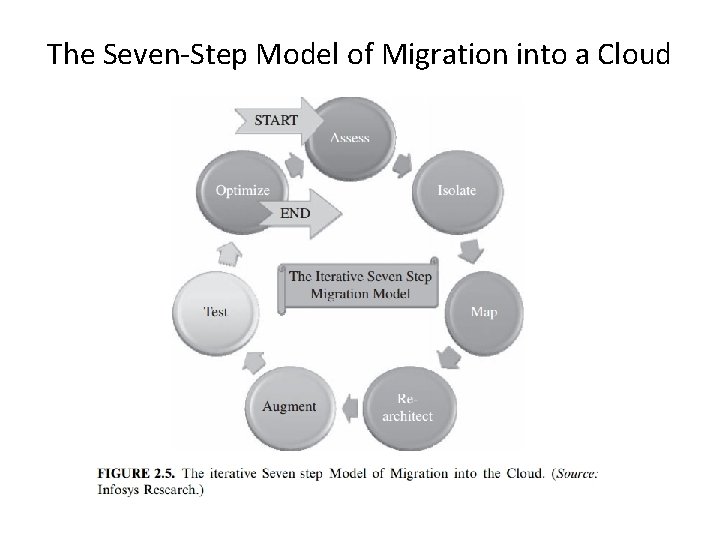
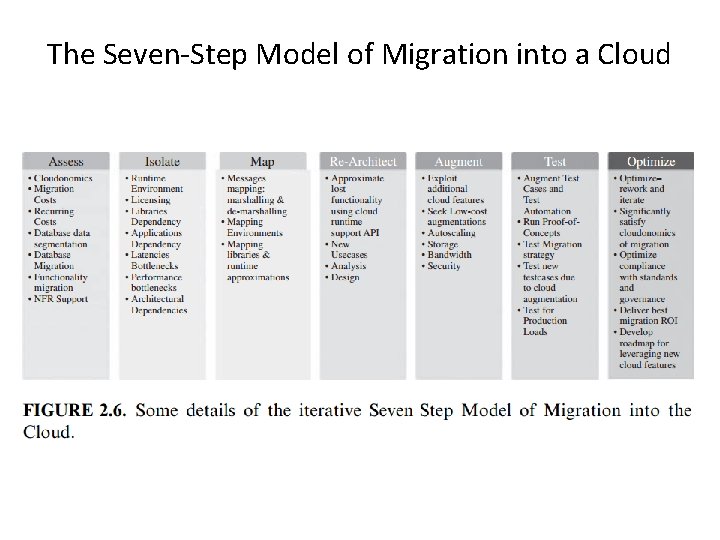
The Seven-Step Model of Migration into a Cloud

The Seven-Step Model of Migration into a Cloud

The Seven-Step Model of Migration into a Cloud Step 1 • Cloud migration assessments comprise assessments to understand the issues involved in the specific case of migration at the application level or the code, the design, the architecture, or usage levels. • These assessments are about the cost of migration as well as about the ROI that can be achieved in the case of production version. Step 2 • isolating all systemic and environmental dependencies of the enterprise application components within the captive data center Step 3 • generating the mapping constructs between what shall possibly remain in the local captive data center and what goes onto the cloud.

The Seven-Step Model of Migration into a Cloud Step 4 • substantial part of the enterprise application needs to be rearchitected, redesigned, and reimplemented on the cloud Step 5 • We leverage the intrinsic features of the cloud computing service to augment our enterprise application in its own small ways. Step 6 • we validate and test the new form of the enterprise application with an extensive test suite that comprises testing the components of the enterprise application on the cloud as well Step 7 • Test results could be positive or mixed. • In the latter case, we iterate and optimize as appropriate. After several such optimizing iterations, the migration is deemed successful

The Seven-Step Model of Migration into a Cloud

VIRTUALIZATION & CLOUD COMPUTING Lecture # 22 CSE 423 The Law of Cloudonomics Specifying SLA, Defining Licensing Models

Cloud Computing • Cloud computing is particularly valuable because it shifts capital expenditures into operating expenditures. • It also shifts risk away from an organization and onto the cloud provider. • Cloud computing presents new opportunities to users and developers because it is based on the paradigm of a shared multitenant utility. • A cloud is an infrastructure that can be partitioned and provisioned, and resources are pooled and virtualized. If the cloud is available to the public on a pay-as-you-go basis, then the cloud is a public cloud, and the service is described as a utility

These are the unique characteristics of an ideal cloud computing model: • Scalability: You have access to unlimited computer resources as needed. • Elasticity: You have the ability to right-size resources as required. • Low barrier to entry: You can gain access to systems for a small investment. • Utility: A pay-as-you-go model matches resources to need on an ongoing basis. .

Companies become cloud computing providers for several reasons: • Profit: The economies of scale can make this a profitable business. • Optimization: The infrastructure already exists and isn't fully utilized. - This is the case for Amazon Web Services. • Strategic: A cloud computing platform extends the company's products and defends their franchise. - This is the case for Microsoft's Windows Azure Platform. • Extension: A branded cloud computing platform can extend customer relationships by offering additional service options. This is the case with various IBM cloud services.

• Presence: Establish a presence in a market before a large competitor can emerge. - Google App Engine allows a developer to scale an application immediately. For Google, its office applications can be rolled out quickly and to large audiences. • Platform: A cloud computing provider can become a hub master at the center of many ISV's (Independent Software Vendor) offerings. - The customer relationship management provider Sales. Force. com has a development platform called Force. com that is a Paa. S offering.

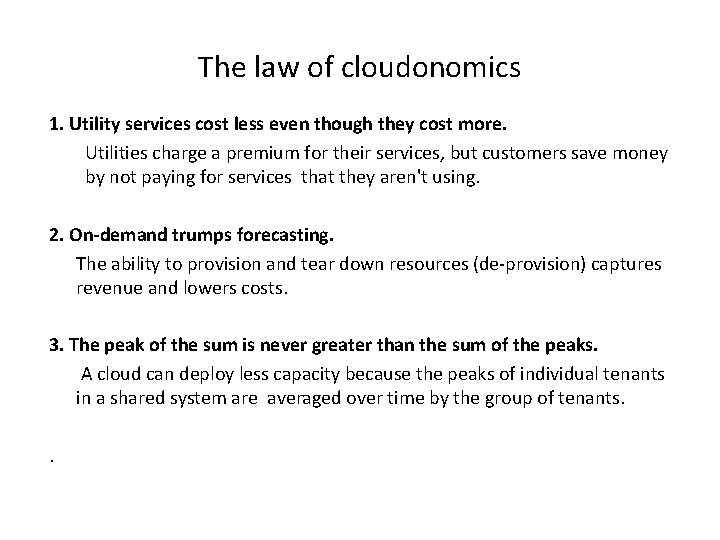
The law of cloudonomics 1. Utility services cost less even though they cost more. Utilities charge a premium for their services, but customers save money by not paying for services that they aren't using. 2. On-demand trumps forecasting. The ability to provision and tear down resources (de-provision) captures revenue and lowers costs. 3. The peak of the sum is never greater than the sum of the peaks. A cloud can deploy less capacity because the peaks of individual tenants in a shared system are averaged over time by the group of tenants. .

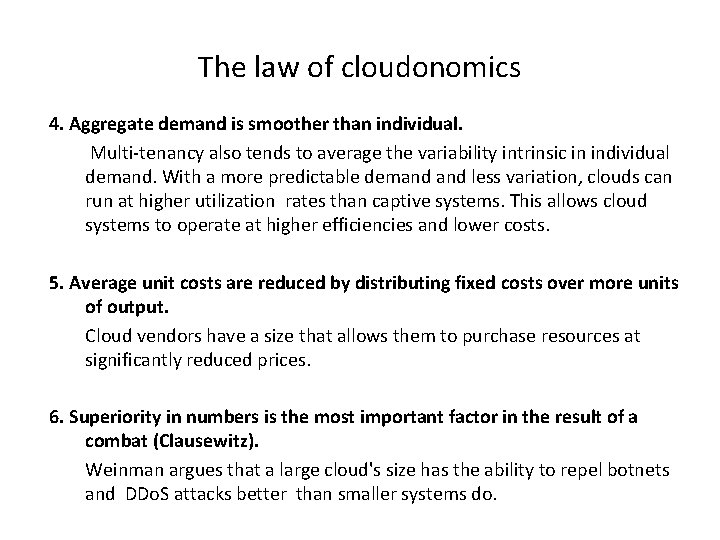
The law of cloudonomics 4. Aggregate demand is smoother than individual. Multi-tenancy also tends to average the variability intrinsic in individual demand. With a more predictable demand less variation, clouds can run at higher utilization rates than captive systems. This allows cloud systems to operate at higher efficiencies and lower costs. 5. Average unit costs are reduced by distributing fixed costs over more units of output. Cloud vendors have a size that allows them to purchase resources at significantly reduced prices. 6. Superiority in numbers is the most important factor in the result of a combat (Clausewitz). Weinman argues that a large cloud's size has the ability to repel botnets and DDo. S attacks better than smaller systems do.

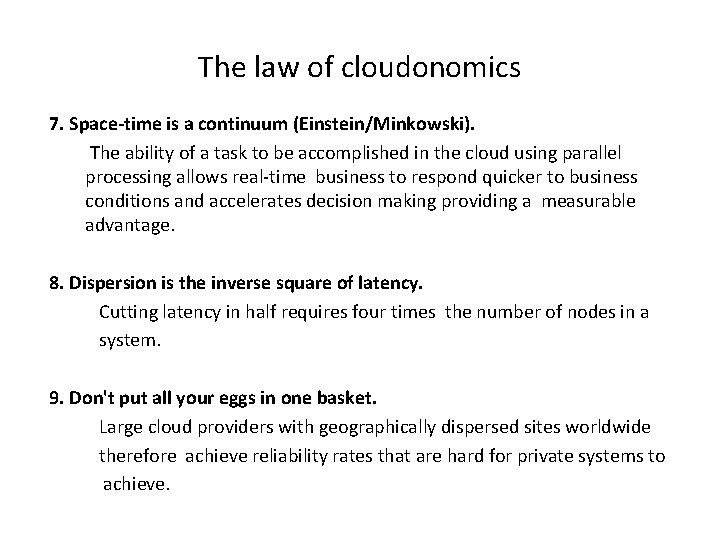
The law of cloudonomics 7. Space-time is a continuum (Einstein/Minkowski). The ability of a task to be accomplished in the cloud using parallel processing allows real-time business to respond quicker to business conditions and accelerates decision making providing a measurable advantage. 8. Dispersion is the inverse square of latency. Cutting latency in half requires four times the number of nodes in a system. 9. Don't put all your eggs in one basket. Large cloud providers with geographically dispersed sites worldwide therefore achieve reliability rates that are hard for private systems to achieve.

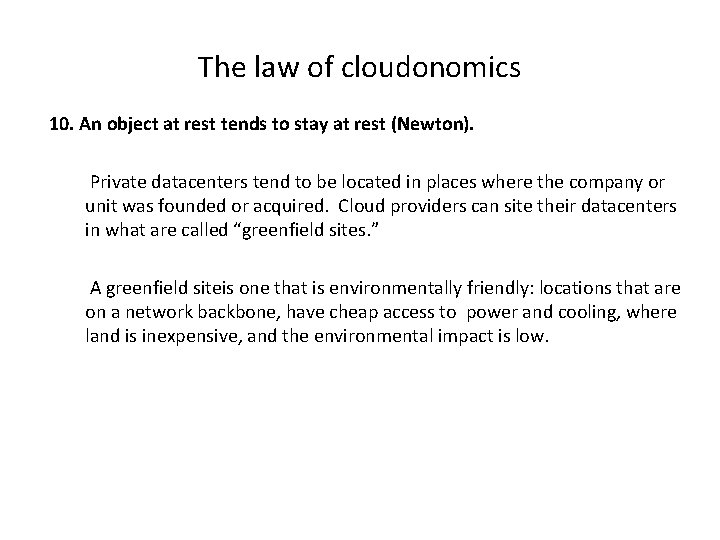
The law of cloudonomics 10. An object at rest tends to stay at rest (Newton). Private datacenters tend to be located in places where the company or unit was founded or acquired. Cloud providers can site their datacenters in what are called “greenfield sites. ” A greenfield siteis one that is environmentally friendly: locations that are on a network backbone, have cheap access to power and cooling, where land is inexpensive, and the environmental impact is low.

Laws of Behavioral Cloudonomics • 1. People are risk averse and loss averse. • 2. People have a flat-rate bias. • 3. People have the need to control their environment and remain autonomous. • 4. People fear change. • 5. People value what they own more than what they are given. • 6. People favor the status quo and invest accordingly.

• 7. People discount future risk and favor instant gratification. • 8. People favor things that are free. • 9. People have the need for status. • 10. People are incapacitated by choice.

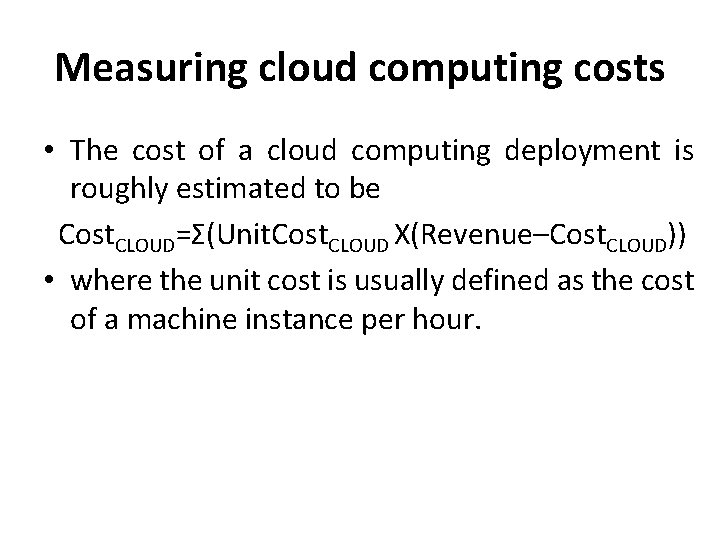
Measuring cloud computing costs • The cost of a cloud computing deployment is roughly estimated to be Cost. CLOUD=Σ(Unit. Cost. CLOUD X(Revenue–Cost. CLOUD)) • where the unit cost is usually defined as the cost of a machine instance per hour.

• To compare your cost benefit with a private cloud, you will have to compare the value that you determined in the previous equation with the same calculation: • Cost. DATACENTER = Σ(Unit Cost. DATACENTER x (Revenue –(Cost. DATACENTER /Utilization))

• The Cost. DATACENTER consists of the summation of the cost of each of the individual systems with all the associated resources, as follows: • Cost. DATACENTER = 1 nΣ(Unit. Cost. DATACENTER x (Revenue – (Cost. DATACENTER/Utilization))SYSTEMn where the sum includes terms for System 1, System 2, System 3, and so on.

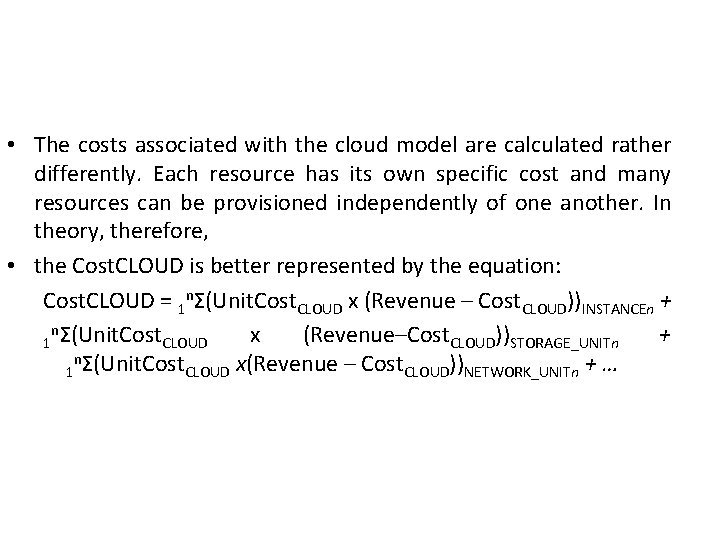
• The costs associated with the cloud model are calculated rather differently. Each resource has its own specific cost and many resources can be provisioned independently of one another. In theory, therefore, • the Cost. CLOUD is better represented by the equation: Cost. CLOUD = 1 nΣ(Unit. Cost. CLOUD x (Revenue – Cost. CLOUD))INSTANCEn + nΣ(Unit. Cost x (Revenue–Cost. CLOUD))STORAGE_UNITn + 1 CLOUD nΣ(Unit. Cost 1 CLOUD x(Revenue – Cost. CLOUD))NETWORK_UNITn + …

Defining Licensing Models When you purchase shrink-wrapped software, you are using that software based on a licensing agreement called a EULA or End User License Agreement. The EULA may specify that the software meets the following criteria: • It is yours to own. • It can be installed on a single or multiple machines. • It allows for one or more connections. • It has whatever limit the ISV(independent software vendor) has placed on its software. In most instances, the purchase price of the software is directly tied to the EULA.

Chapter 3: Understanding Cloud Architecture • IN THIS CHAPTER • Using the cloud computing stack to describe different models • Understanding how platforms and virtual appliances are used • Learning how cloud communications work • Discovering the new world of the cloud client

• One property that differentiates cloud computing is referred to as composability, which is the ability to build applications from component parts. A platform is a cloud computing service that is both hardware and software. Platforms are used to create more complex software. Virtual appliances are an important example of a platform, and they are becoming a very important standard cloud computing deployment object.

Cloud computing requires some standard protocols with which different layers of hardware, software, and clients can communicate with one another. Many of these protocols are standard Internet protocols. Cloud computing relies on a set of protocols needed to manage interprocess communications that have been developed over the years. The most commonly used set of protocols uses XML as the messaging format, the Simple Object Access Protocol (SOAP) protocol as the object model, and a set of discovery and description protocols based on the Web Services Description Language (WSDL) to manage transactions. Some completely new clients are under development that are specifically meant to connect to the cloud. These clients have as their focus cloud applications and services, and are often hardened and more securely connected. Two examples presented are Jolicloud and Google Chrome OS. They represent a new client model that is likely to have considerable impact.


Exploring the Cloud Computing Stack • • • Composability Infrastructure Platforms Virtual Appliances Communication Protocols Applications

Composability • A composable component must be: • Modular: It is a self-contained and independent unit that is cooperative, reusable, and replaceable. • Stateless: A transaction is executed without regard to other transactions or requests.

• The essence of a service oriented design is that services are constructed from a set of modules using standard communications and service interfaces. • An example of a set of widely used standards describes the services themselves in terms of the Web Services Description Language (WSDL), data exchange between services using some form of XML, and the communications between the services using the SOAP protocol.

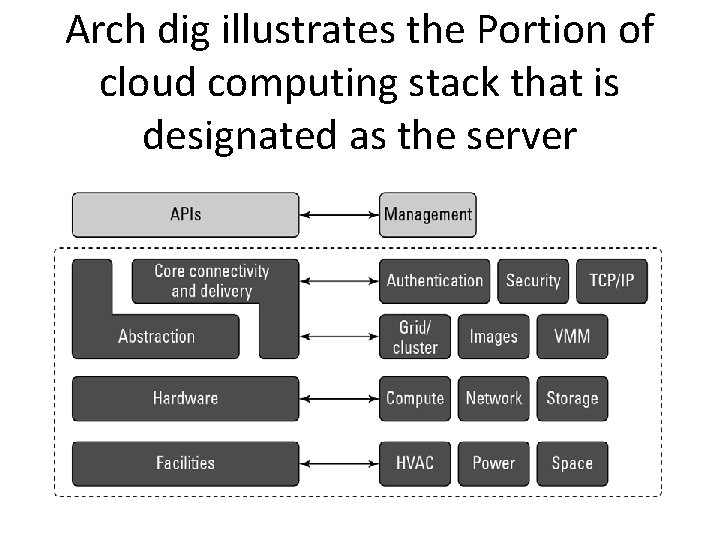
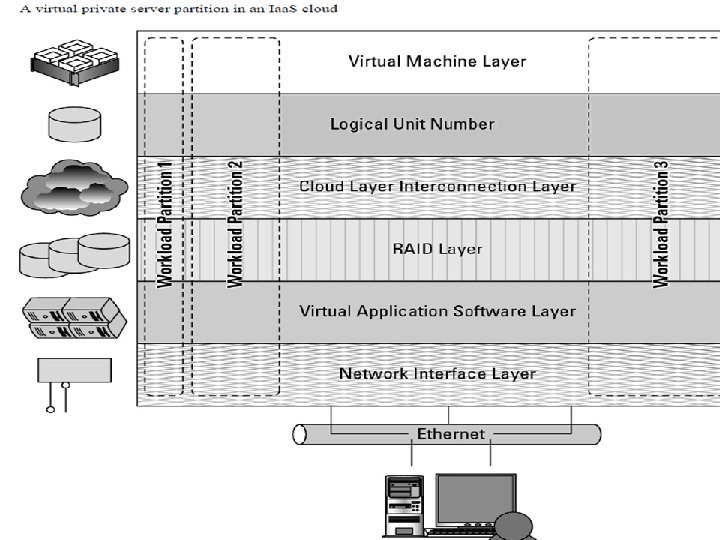
Infrastructure Most large Infrastructure as a Service (Iaa. S) providers rely on virtual machine technology to deliver servers that can run applications. Virtual servers described in terms of a machine image or instance have characteristics that often can be described in terms of real servers delivering a certain number of microprocessor (CPU) cycles, memory access, and network bandwidth to customers. Virtual machines are containers that are assigned specific resources. The software that runs in the virtual machines is what defines the utility of the cloud computing system.

Arch dig illustrates the Portion of cloud computing stack that is designated as the server

Platforms • Platform in the cloud is a software layer that is used to create higher levels of service. • Salesforce. com's Force. com Platform • Windows Azure Platform • Google Apps and the Google App. Engine

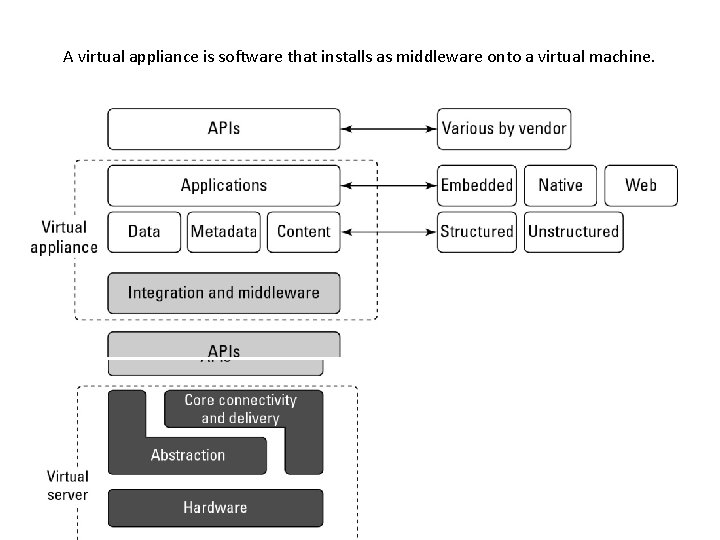
A virtual appliance is software that installs as middleware onto a virtual machine.

Virtual Appliances • Virtual appliances are software installed on virtual servers—application modules that are meant to run a particular machine instance or image type. • A virtual appliance is a platform instance. Therefore, virtual appliances occupy the middle of the cloud computing stack

Understanding Services and Applications by Type

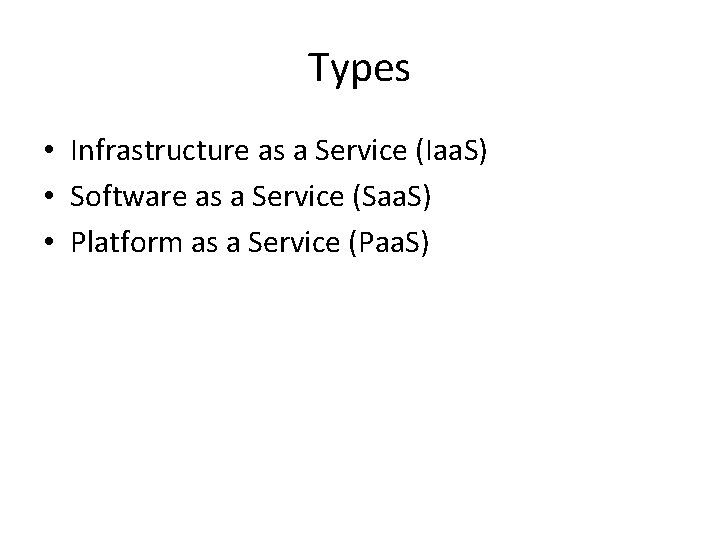
Types • Infrastructure as a Service (Iaa. S) • Software as a Service (Saa. S) • Platform as a Service (Paa. S)

• Infrastructure as a Service allows for the creation of virtual computing systems or networks. • Software as a Service represents a hosted application that is universally available over the Internet, usually through a browser. • Software as a Service, the user interacts directly with the hosted software. • Saa. S may be seen to be an alternative model to that of shrink-wrapped software and may replace much of the boxed software that we buy today.

• Platform as a Service is a cloud computing infrastructure that creates a development environment upon which applications may be build. • Paa. S provides a model that can be used to create or augment complex applications such as Customer Relation Management (CRM) or Enterprise Resource Planning (ERP) systems. • Paa. S offers the benefits of cloud computing and is often componentized and based on a serviceoriented architecture model.

• Identity as a Service (IDaa. S) • Identity as a Service provides authentication and authorization services on distributed networks. • Infrastructure and supporting protocols for IDaa. S. • Other service types such as Compliance as a Service (Caa. S), provisioning, monitoring, communications.

Infrastructure as a Service (Iaa. S) • Infrastructure as a Service (Iaa. S) is a cloud computing service model in which hardware is virtualized in the cloud. • In this particular model, the service vendor owns the equipment: servers, storage, network infrastructure. • The developer creates virtual hardware on which to develop applications and services. • Essentially, an Iaa. S vendor has created a hardware utility service where the user provisions virtual resources as required.


• The fundamental unit of virtualized client in an Iaa. S deployment is called a workload. • A workload simulates the ability of a certain type of real or physical server to do an amount of work. • The work done can be measured by the number of Transactions Per Minute (TPM) or a similar metric against a certain type of system.


• For example, “run this blog for 1 year, for up to 100 visitors a day” is a what (workload), while “run this blog on m 1. small EC 2 instance in us-east-1 for 1 year” or “run this blog on Terremark instance with 1 VPU and 1 GB of RAM for 1 year” are a how (for lack of a better word, I am going to call them deployments).

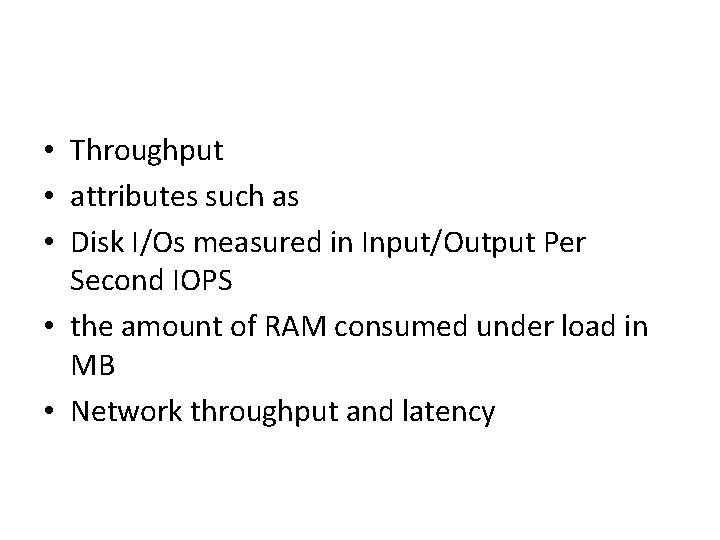
• Throughput • attributes such as • Disk I/Os measured in Input/Output Per Second IOPS • the amount of RAM consumed under load in MB • Network throughput and latency

• In a hosted application environment, a client's application runs on a dedicated server inside a server rack or perhaps as a standalone server in a room full of servers. • In cloud computing, a provisioned server called an instance is reserved by a customer, and the necessary amount of computing resources needed to achieve that type of physical server is allocated to the client's needs.


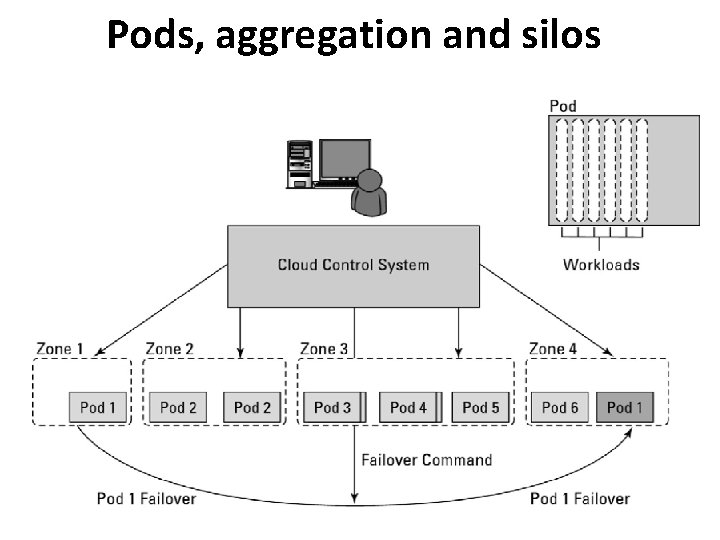
Pods, aggregation and silos

Platform as a Service (Paa. S) • Platform as a Service model describes a software environment in which a developer can create customized solutions within the context of the development tools that the platform provides. • Platforms can be based on specific types of development languages, application frameworks or other constructs.

• Paa. S offering provides the tools and development environment to deploy applications on another vendor's application. • Often a Paa. S tool is a fully integrated development environment i. e all the tools and services are part of the Paa. S service. • In a Paa. S model, customers may interact with the software to enter and retrieve data, perform actions, get results, and to the degree that the vendor allows it, customize the platform involved. • The customer takes no responsibility for maintaining the hardware, the software or the development of the applications and is responsible only for his interaction with the platform. • The one example that is most quoted as a Paa. S offering is

Software as a Service (Saa. S) • Saa. S provides the complete infrastructure, software, and solution stack as the service offering. • A good way to think about Saa. S is that it is the cloud-based equivalent of shrink-wrapped software.

• Software as a Service (Saa. S) may be described as software that is deployed on a hosted service and can be accessed globally over the Internet, most often in a browser. • With the exception of the user interaction with the software, all other aspects of the service are abstracted away.

• Saa. S software for end-users are Google Gmail and Calendar, Quick. Books online, Zoho Office Suite, and others that are equally well known. • Saa. S applications come in all shapes and sizes, and include custom software such as • billing and invoicing systems • Customer Relationship Management (CRM) applications • Help Desk applications • Human Resource (HR) solutions

Saa. S characteristics The software is available over the Internet globally through a browser on demand. • • The typical license is subscription-based or usage-based and is billed on a recurring basis. • The software and the service are monitored and maintained by the vendor, regardless of where all the different software components are running. • There may be executable client-side code, but the user isn't responsible for maintaining that code or its interaction with the service. • Reduced distribution and maintenance costs and minimal end-user system costs generally make Saa. S applications cheaper to use than their shrink-wrapped versions. • Such applications feature automated upgrades, updates, and patch management and much faster rollout of changes. • Saa. S applications often have a much lower barrier to entry than their locally installed competitors, a known recurring cost, and they scale on demand (a property of cloud computing in general). • All users have the same version of the software so each user's software is compatible with another's. • Saa. S supports multiple users and provides a shared data model through a singleinstance, multi-tenancy model.


Identity as a Service (IDaa. S) • An identity service is one that stores the information associated with a digital entity in a form that can be queried and managed for use in electronic transactions. • Identity services have as their core functions: a data store, a query engine, and a policy engine that maintains data integrity.

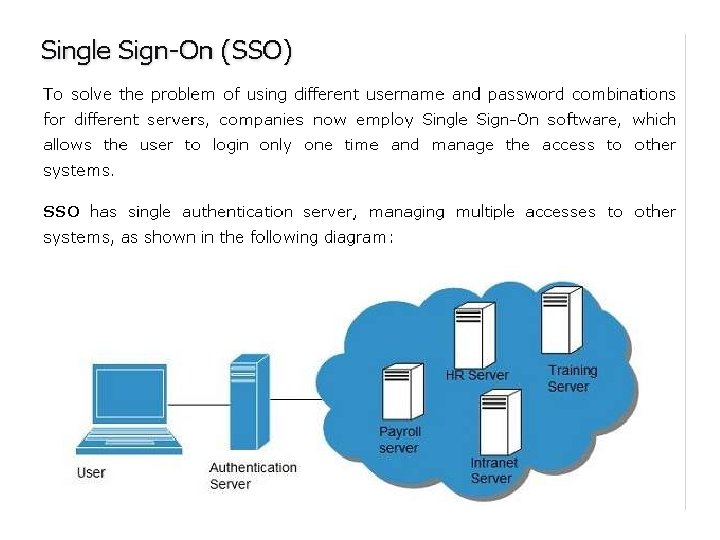
• Employees in a company require to login to system to perform various tasks. These systems may be based on local server or cloud based. Following are the problems that an employee might face: • Remembering different username and password combinations for accessing multiple servers. • If an employee leaves the company, it is required to ensure that each account of that user is disabled. This increases workload on IT staff. • To solve above problems, a new technique emerged which is known as Identity-as–a-Service (IDaa. S). • IDaa. S offers management of identity information as a digital entity. This identity can be used during electronic transactions.

• The Domain Name Service can run on a private network, but is at the heart of the Internet as a service that provides identity authorization and lookup. • The name servers that run the various Internet domains (. COM, . ORG, . EDU, . MIL, and so on) are IDaa. S servers. • DNS establishes the identity of a domain as belonging to a set of assigned addresses, associated with an owner and that owner's information, and so forth. If the identification is the assigned IP number, the other properties are its metadata. • IDaa. S offers management of identity information as a digital entity. This identity can be used during electronic transactions.

What is an identity? • An identity is a set of characteristics or traits that make something recognizable or known. • In computer network systems, it is one's digital identity that most concerns us. • A digital identity is those attributes and metadata of an object along with a set of relationships with other objects that makes an object identifiable.






An identity can belong to a person and may include the following: • Things you are: Biological characteristics such as age, gender, appearance, and so forth • Things you know: Biography, personal data such as social security numbers, PINs, where you went to school, and so on • Things you have: A pattern of blood vessels in your eye, your fingerprints, a bank account you can access, a security key you were given, objects and possessions, and more • Things you relate to: Your family and friends, a software license, beliefs and values, activities and endeavors, personal selections and choices, habits and practices, an i. Google account, and more

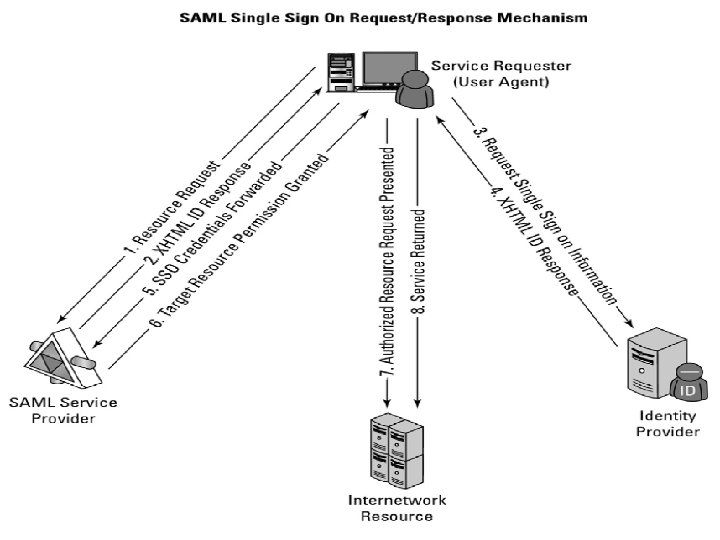
Networked Identity Service Classes • To validate Web sites, transaction participants, clients, and network services—various forms of identity services— have been deployed on networks. • Ticket or token providing services, certificate servers, and other trust mechanisms all provide identity services that can be pushed out of private networks and into the cloud.

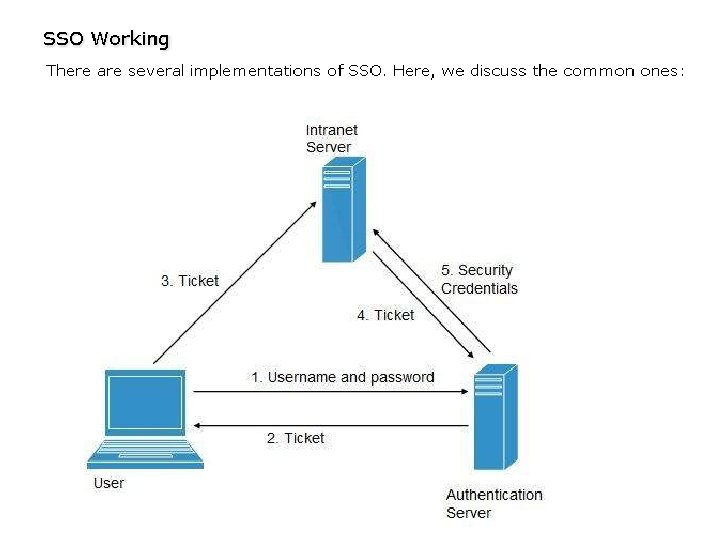
Identity as a Service (IDaa. S) may include any of the following: • • • Authentication services (identity verification) Directory services Federated identity Identity governance Identity and profile management Policies, roles, and enforcement Provisioning (external policy administration) Registration Risk and event monitoring, including audits Single sign-on services (pass-through authentication)

Identity System Codes of Conduct • User control for consent: Users control their identity and must consent to the use of their information. • Minimal Disclosure: The minimal amount of information should be disclosed for an intended use. • Justifiable access: Only parties who have a justified use of the information contained in a digital identity and have a trusted identity relationship with the owner of the information may be given access to that information. • Directional Exposure: An ID system must support bidirectional identification for a public entity so that it is discoverable and a unidirectional identifier for private entities, thus protecting the private ID. • Interoperability: A cloud computing ID system must interoperate with other identity services from other identity providers. • Unambiguous human identification: An IDaa. S application must provide an unambiguous mechanism for allowing a human to interact with a system while protecting that user against an identity attack. • Consistency of Service: An IDaa. S service must be simple to use, consistent across all its uses, and able to operate in different contexts using different technologies.


Compliance as a Service (Caa. S) • The laws of the country of a request's origin may not match the laws of the country where the request is processed, and it's possible that neither location's laws match the laws of the country where the service is provided.

• A Compliance as a Service application would need to serve as a trusted third party, because this is a man-in-the-middle type of service. • Caa. S may need to be architected as its own layer of a SOA architecture in order to be trusted. • A Caa. S would need to be able to manage cloud relationships, understand security policies and procedures, know how to handle information and administer privacy, be aware of geography, provide an incidence response, archive, and allow for the system to be queried, all to a level that can be captured in a Service Level Agreement.