Chapter 7 Digital Evidence in the Courtroom A






































- Slides: 43

Chapter 7 Digital Evidence in the Courtroom A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in Power. Point form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: q If you use these slides (e. g. , in a class) in substantially unaltered form, that you mention their source (after all, we’d like credit for our effort!) q If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our slides, and note our copyright of this material. Digital Evidence and Computer Crime, 2 nd edition. Eoghan Casey Elsevier Academic Press, July 2004. Thanks and enjoy! IG/DS All material copyright 2004 -2008 Isaac Ghansah, Dick Smith, All Rights Reserved Digital Evidence in Courtroom 7 -1

Chapter 7: Introduction Our goal: q Learn why evidence Overview: q What’s the Role of Digital must be handled Evidence? properly according to q Does digital evidence add to or legal requirements. replace physical evidence? q more depth, detail q Major issues when digital later in course evidence is presented in court. q approach: v use example cases Digital Evidence in Courtroom 7 -2

Chapter 7: Introduction continued q Proof that evidence is authentic and has not been tampered with becomes essential. q To be admitted into court it must be relevant. q Is it hearsay, is the original required or a copy sufficient? q Is there a documented chain of custody? q Best keep the number of people who handled it to a minimum. Digital Evidence in Courtroom 3

Chapter 7: Introduction continued q Set up standard operating procedures, continuing education, and clear policies to maintain consistency and prevent contamination of evidence. q Given the ease with which digital evidence can be altered, important procedures and trained personnel can not be overstated. q Issues of admissibility, uncertainty, and presentation of digital evidence. Digital Evidence in Courtroom 4

Chapter 7: roadmap 7. 1 Admissibility - Warrants 7. 2 Authenticity and Reliability 7. 3 Casey’s Certainty Scale 7. 4 Best Evidence 7. 5 Direct versus Circumstantial Evidence 7. 6 Hearsay 7. 6. 1 Hearsay Exceptions 7. 7 Scientific Evidence 7. 8 Presenting Digital Evidence 7. 9 Summary Digital Evidence in Courtroom 7 -5

7. 1 Admissibility - Warrants q Common mistake is evidence obtained without authorization. q Generally warrant is required to sieze evidence – main exceptions are plain view, consent and exigency. q CASE EXAMPLE (U. S. v. TURNER 1999): law enforcement obtained permission of defendant to search home for evidence of sexual assault of one of his neighbors. During search investigator looked at computer and identified child porn. Turner filled suppress since he did not consent to his computer being searched. Digital Evidence in Courtroom 7 -6

7. 1 Admissibility - Warrants q Four questions investigators must ask themselves when searching and seizing: 1. 2. 3. 4. Does 4 th Amend and/or ECPA apply to situation? Have 4 th Amend and/or ECPA requirements been met? How long can investigators remain at the scene? What do investigators need to re-enter? Digital Evidence in Courtroom 7

7. 1 Admissibility - Warrants q Recall 4 th Amend requires search warrant be secured before search of house, person, papers, and effects. q More specifically have to convince Judge: 1. 2. 3. Crime has been committed; Evidence of crime is in existance; Evidence is likely to exhist at place to be searched. Digital Evidence in Courtroom 8

7. 1 Admissibility - Warrants q CASE EXAMPLE (U. S. v. GRAY 1999): During investigation of Gray’s unauthorized access of National Library of Medicine FBI had warrant and seized 4 computers looking for information he might have downloaded. Examiner discovered pornographic image directories named “teen” and “tiny teen”, halted search and obtained second warrant to search for pornography. Digital Evidence in Courtroom 9

7. 1 Admissibility - Warrants q CASE EXAMPLE (WISCONSIN v. SCHROEDER): While investigating an online harassment complaint made against Schroeder, investigator found evidence relating to the complaint and noticed pornographic pictures of children. A second warrant was obtained giving examiner authority to look for child porn. Defendant charged and convicted for 18 counts of child porn. Also charged and tried on separate proceeding unlawful use of a computer and disorderly conduct. Digital Evidence in Courtroom 10

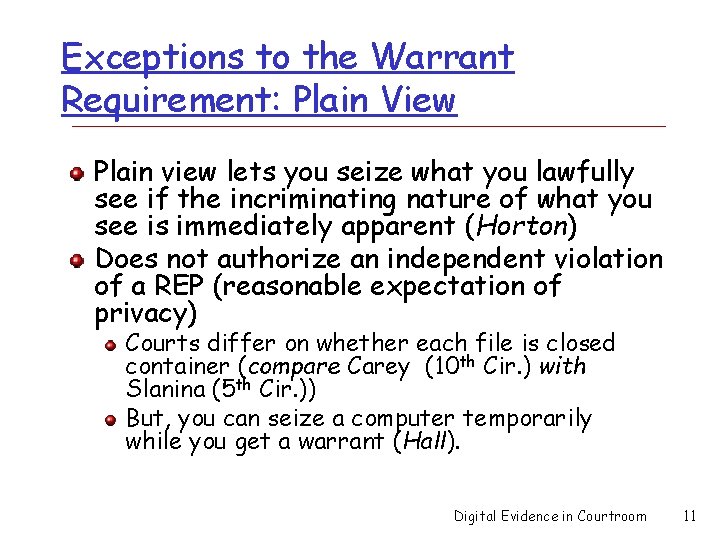
Exceptions to the Warrant Requirement: Plain View Plain view lets you seize what you lawfully see if the incriminating nature of what you see is immediately apparent (Horton) Does not authorize an independent violation of a REP (reasonable expectation of privacy) Courts differ on whether each file is closed container (compare Carey (10 th Cir. ) with Slanina (5 th Cir. )) But, you can seize a computer temporarily while you get a warrant (Hall). Digital Evidence in Courtroom 11

Exceptions to the Warrant Requirement: Consent Target can consent to a search, raising “scope of consent” issues: – Does consent include searching through electronic storage devices? – Test is, what would a reasonable person listening in to the exchange think? – Very fact-specific and unpredictable – Written consent forms should expressly include computers and other electronic storage devices. Digital Evidence in Courtroom 12

Other Exceptions q Exigent Circumstances If necessary to prevent destruction of evidence, can seize computer without a warrant. Pager cases Can’t, however, search the seized computer without a warrant if exigency is gone. A limited exception. Search Incident to Arrest Permits “reasonable” search of the person and electronic storage devices on his person at the time of arrest (e. g. , pagers). Digital Evidence in Courtroom 13

Learning Objectives q At the end of this module you will be able to: Explain the container analogy v Discuss basic issues related to search warrants v Describe warrant and warrantless search criteria v Explain the concept of Reasonable Expectation of Privacy v Compare and contrast the criteria for real-time interceptions and access to stored data v Explain when a warrant, subpoena, or other court order is required to seize electronic evidence v Critically analyze the impact of computer crime search and seizure on 4 th and 5 th amendment rights. v Digital Evidence in Courtroom 14

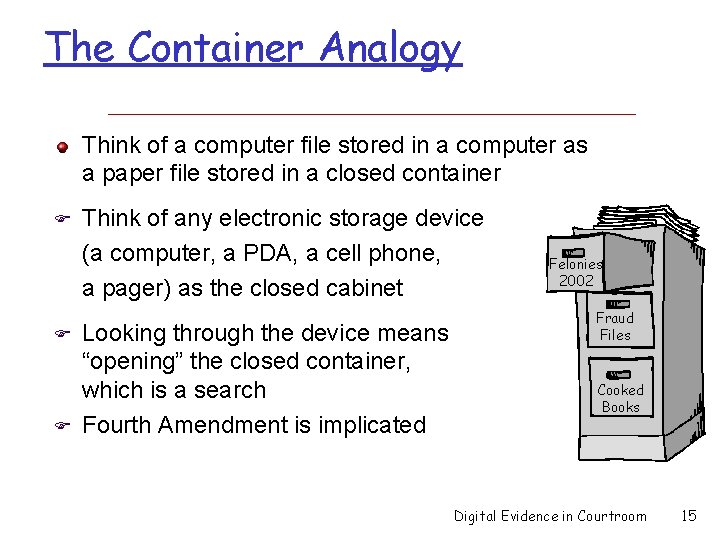
The Container Analogy Think of a computer file stored in a computer as a paper file stored in a closed container Think of any electronic storage device (a computer, a PDA, a cell phone, a pager) as the closed cabinet Looking through the device means “opening” the closed container, which is a search Fourth Amendment is implicated Felonies 2002 Fraud Files Cooked Books Digital Evidence in Courtroom 15

Third Party Consent Any private person who shares common authority or control over the computer can consent to the search (Matlock). Target’s spouse? Usually Target’s Parents? Maybe Target’s co-workers? Maybe Computer repairman? No Government officials? No Password protection probably defeats a claim of common authority. Digital Evidence in Courtroom 16

Private Searches Private third party may search files and show or tell gov’t what she finds. Do you need a warrant to see it? No, it’s a private search (Jacobsen). Under Jacobsen, you can see what private person saw, but no more. Use what private person saw to establish P. C. to get a warrant. Very common in computer cases Digital Evidence in Courtroom 17

Special Case: Workplace Searches Private-sector rules are easy Employee retains Reasonable Expectation of Privacy (REP) at work unless stuff is “open to the world at large” Employer can consent to search of employee’s space Employer searches are usually private searches Digital Evidence in Courtroom 18

Public Employment Searches Unique Reasonable Expectation of Privacy (REP) test for government employees; O’Connor v. Ortega, 480 U. S. 709 (1987). 1) Is workspace to be searched “open to fellow employees or the public”? OR 2) Are there “actual office practices and procedures. . . or legitimate regulation” that permit search? If so, then no REP; very different from private-sector REP test. Digital Evidence in Courtroom 19

Public Employment & Banners This is a government computer network. You have no expectation of privacy in your use of this computer. Your use constitutes consent to monitoring and disclosure of the fruits of the monitoring. The first question: “Is there a banner or written policy that covers this? ” Your next line: “Go find out. ” U. S. v. Simons, 206 F. 3 d 392 (4 th Cir. 2000); US v. Angevine, 281 F. 3 d 1130, 1134 -35 (10 th Cir. 2002) Digital Evidence in Courtroom 20

Public Employment & Work Related Searches What if there is no banner? The search will still be okay if it is “reasonable” in scope and duration. (O’Connor) In effect, another exception to warrant requirement. Search must be work-related (e. g. , workplace misconduct investigation, or getting a file for work purpose); this is for employers, not law enforcement. Search must be justified at its inception, and reasonably related in scope to the circumstances. Mixed Motives Okay. Digital Evidence in Courtroom 21

Examples of Collateral Damage When an employee uses his company’s server to commit a crime, seizing the entire server as an “instrumentality” and shutting down the company. When an ISP has child pornography on its servers, removing the server, effectively shutting down the ISP and denying law abiding users their Internet service. When a kid uses the family PC to hack into NASA, taking the PC even though it has the family’s tax and accounting records on it. Digital Evidence in Courtroom 22

Legal Challenges of Digital Evidence Status as scientific evidence Criteria for admissibility of novel scientific evidence (Daubert v. Merrell) Whether theory or technique has been reliably tested; Whether theory or technique has been subject to peer review and publication; What is the known or potential rate of error of the method used; and Whether theory or method has been generally accepted by the scientific community. Kumho Tire extended the criteria to technical knowledge Digital Evidence in Courtroom 23

5 Rules of Evidence q Admissible v Must be able to be used in court or elsewhere q Authentic v Evidence relates to incident in relevant way q Complete (no tunnel vision) v Exculpatory evidence for alternative suspects q Reliable v No question about authenticity & veracity q Believable v Clear, easy to understand, and believable by a jury Digital Evidence in Courtroom 24

Evidence Life Cycle q Collection & identification q Storage, preservation, and transportation q Presentation q Return to production, owner, or court Digital Evidence in Courtroom 25

Categories of Evidence q Admissibility of evidence based on factual foundation v Varies for different types of evidence q Best evidence v Primary evidence used in trail v Usually documentation falls into this category q Secondary evidence v Not viewed as reliable & strong in proving innocence or guilt v Oral evidence Digital Evidence in Courtroom 26

Categories of Evidence q Direct evidence v Proves a fact all by itself v Eye witness testimony q Conclusive evidence v Irrefutable and cannot be contradicted q Circumstantial evidence v Proves an intermediate fact that can be used to deduce or assume the existence of another fact Digital Evidence in Courtroom 27

Categories of Evidence q Corroborative evidence v Supporting evidence used to help prove an idea or point q Opinion evidence v Pertains to witness testimony v Witness must testify to only the facts of the issue and not their opinion of the facts Digital Evidence in Courtroom 28

Chain of Custody q Protects integrity of the evidence q Effective process of documenting the complete journey of the evidence during the life of the case q Allows you to answer the following questions: v Who collected it? v How & where? v Who took possession of it? v How was it stored & protected in storage? v Who took it out of storage & why? Digital Evidence in Courtroom 29

7. 2 Authenticity and Reliability q Process of determining whether evidence is worthy. q CASE EXAMPLE (MICHIGAN v. MILLER 2002): E- mail and AOL Instant Message provided compelling evidence to convict Sharee Miller of conspiring to kill her husband abetting the suicide of the admitted killer (Jerry Cassady). She controlled the killer’s perception of her husband, going so far as to masquerade as her husband send offensive messages. In this case, the authenticity of the AOL IM was questioned in the light that the online conversation could be staged. Digital Evidence in Courtroom 30

7. 2 Authenticity and Reliability q CASE EXAMPLE (U. S. v. TANK): A case related to the Orchid/Wonderland Club investigation, defendant argued the authenticity and relevance of Internet chat logs was not adequately established. One of the points the defense argued was the logs could be easily modified. The prosecution used a number of witnesses to establish the logs were authentic. The court held that printouts of computer-generated logs of “chat room” discussions maybe established by evidence showing how they were prepared, their accuracy in representing the conversations and their connection to the defendant. Digital Evidence in Courtroom 31

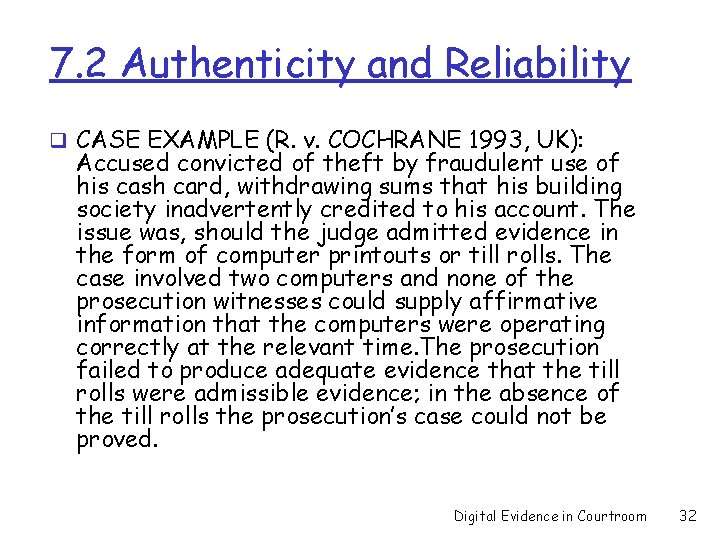
7. 2 Authenticity and Reliability q CASE EXAMPLE (R. v. COCHRANE 1993, UK): Accused convicted of theft by fraudulent use of his cash card, withdrawing sums that his building society inadvertently credited to his account. The issue was, should the judge admitted evidence in the form of computer printouts or till rolls. The case involved two computers and none of the prosecution witnesses could supply affirmative information that the computers were operating correctly at the relevant time. The prosecution failed to produce adequate evidence that the till rolls were admissible evidence; in the absence of the till rolls the prosecution’s case could not be proved. Digital Evidence in Courtroom 32

7. 3 Casey’s Certainty Scale q Our textbook author presents a table that consists of a scale for categorizing levels of certainty in digital evidence. Digital Evidence in Courtroom 7 -33

7. 4 Best Evidence q Courts used to require original evidence, however now they accept exact duplicate. Digital Evidence in Courtroom 7 -34

7. 5 Direct versus Circumstantial Evidence q Direct evidence establishes a fact. q Circumstantial evidence may suggest one. Digital Evidence in Courtroom 7 -35

7. 6 Hearsay Evidence q Hearsay Evidence Oral or written evidence that is secondhand that has no firsthand proof of accuracy or reliability v Statements spoken, written or otherwise uttered by a person outside of court, when the out of court statement is used to try to prove the facts asserted in the statement. v Generally written documents are considered to be hearsay if they are to be admitted into evidence to prove the truth of the facts alleged in the document. v Digital Evidence in Courtroom 36

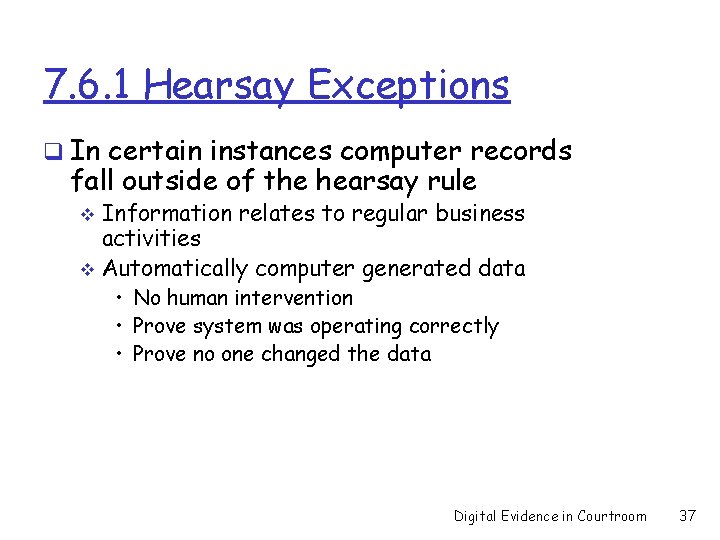
7. 6. 1 Hearsay Exceptions q In certain instances computer records fall outside of the hearsay rule Information relates to regular business activities v Automatically computer generated data v • No human intervention • Prove system was operating correctly • Prove no one changed the data Digital Evidence in Courtroom 37

7. 7 Scientific Evidence q In the US scientific evidence is evaluated using 4 criteria: 1. 2. 3. 4. Whether theory or technique can be (and has been) tested; Whethere is a high known or potential rate of error, and the existence and maintenance of standards controlling the technique’s operation; Whether theory or technique has been subjected to peer review and publication; Whether theory or technique enjoys “general acceptance” within the relevant scientific community. Digital Evidence in Courtroom 7 -38

7. 8 Presenting Digital Evidence q Preparation is one of the most important aspects of testifying in court. q Scripting direct examination and rehearsing it with the attorney ahead of time provides opportunity to identify areas that need further explanation and to anticipate questions that the opposition might raise during cross-examination. q During cross attorneys often attempt to point out flaws and details overlooked. Digital Evidence in Courtroom 7 -39

7. 8 Presenting Digital Evidence q It is necessary to explain how the evidence was handled analyzed to demonstrate chain of custody and thoroughness of methods. q Expect questions such as how files are deleted and recovered and how tools acquire and preserve digital evidence. q Simple diagrams depicting these processes are recommended. Digital Evidence in Courtroom 40

Chapter 7: Summary q A computer system can be thought of as filing cabinet (container) q A computer file can be thought of as a file housed inside the container q What is the importance: Think 4 th amendment q Consent for search can be problematic Digital Evidence in Courtroom 41

Chapter 7 Summary Continued q Reasonable expectation of privacy is very important q Exceptions: Plain view, exigent circumstance, incident to an arrest. q Daubert criteria for admissibility of digital evidence. Digital Evidence in Courtroom 42

Chapter 7: Summary Covered a “ton” of material! q history You now have: q context, overview, “feel” of Investigative Process q more depth, detail to follow! Digital Evidence in Courtroom 7 -43
 Courtroom vocabulary
Courtroom vocabulary Courtroom work group
Courtroom work group What is a courtroom work group
What is a courtroom work group Courtroom roles and responsibilities
Courtroom roles and responsibilities Courtroom roles and responsibilities
Courtroom roles and responsibilities Courtroom
Courtroom Courtroom participants roles
Courtroom participants roles Courtroom work group
Courtroom work group Primary evidence vs secondary evidence
Primary evidence vs secondary evidence Primary evidence vs secondary evidence
Primary evidence vs secondary evidence Secondary sources
Secondary sources Primary evidence vs secondary evidence
Primary evidence vs secondary evidence Primary evidence vs secondary evidence
Primary evidence vs secondary evidence Fiber evidence can have probative value
Fiber evidence can have probative value Class evidence vs individual evidence
Class evidence vs individual evidence Difference between testimonial and physical evidence
Difference between testimonial and physical evidence Class vs individual evidence
Class vs individual evidence Genetic logical fallacy
Genetic logical fallacy Digital evidence as alibi
Digital evidence as alibi Acpo guidelines audit trail
Acpo guidelines audit trail Hình ảnh bộ gõ cơ thể búng tay
Hình ảnh bộ gõ cơ thể búng tay Ng-html
Ng-html Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Chó sói
Chó sói Thang điểm glasgow
Thang điểm glasgow Chúa sống lại
Chúa sống lại Các môn thể thao bắt đầu bằng tiếng chạy
Các môn thể thao bắt đầu bằng tiếng chạy Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Công thức tính độ biến thiên đông lượng
Công thức tính độ biến thiên đông lượng Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ Mật thư anh em như thể tay chân
Mật thư anh em như thể tay chân Phép trừ bù
Phép trừ bù độ dài liên kết
độ dài liên kết Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Thể thơ truyền thống
Thể thơ truyền thống Quá trình desamine hóa có thể tạo ra
Quá trình desamine hóa có thể tạo ra Một số thể thơ truyền thống
Một số thể thơ truyền thống Cái miệng nó xinh thế
Cái miệng nó xinh thế Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Thế nào là sự mỏi cơ
Thế nào là sự mỏi cơ đặc điểm cơ thể của người tối cổ
đặc điểm cơ thể của người tối cổ Thế nào là giọng cùng tên?
Thế nào là giọng cùng tên?