ARC 303 Aspectos essenciais no desenvolvimento de aplicaes














- Slides: 52

ARC 303 Aspectos essenciais no desenvolvimento de aplicações com o Windows Identity Foundation Pedro Félix CCISEL sel. ipl. pt pedrofelix@cc. i

try { • Motivation • The claims based model • Windows Identity Foundation • • Identity and claims representation Consumption pipeline ASP. NET and WCF Integration Issuance pipeline 4

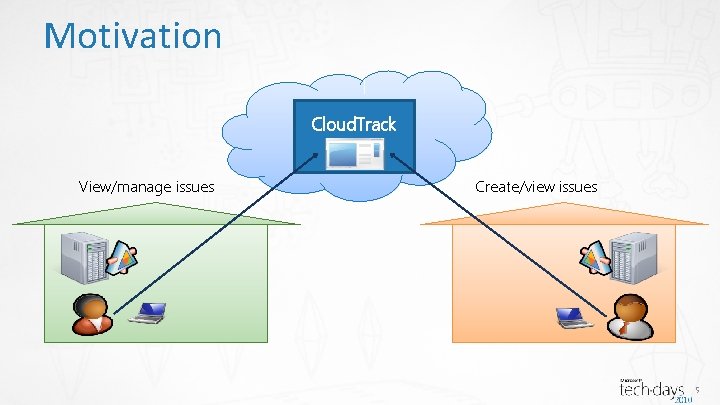
Motivation Cloud. Track. View/manage issues Create/view issues 5

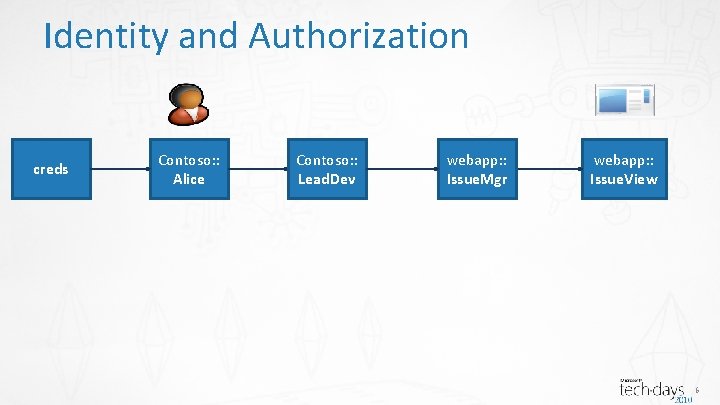
Identity and Authorization creds Contoso: : Alice Contoso: : Lead. Dev webapp: : Issue. Mgr webapp: : Issue. View 6

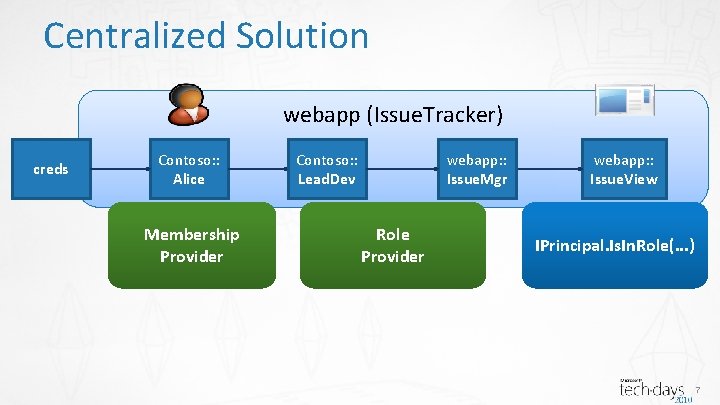
Centralized Solution webapp (Issue. Tracker) creds Contoso: : Alice Membership Provider Contoso: : Lead. Dev webapp: : Issue. Mgr Role Provider webapp: : Issue. View IPrincipal. Is. In. Role(. . . ) 7

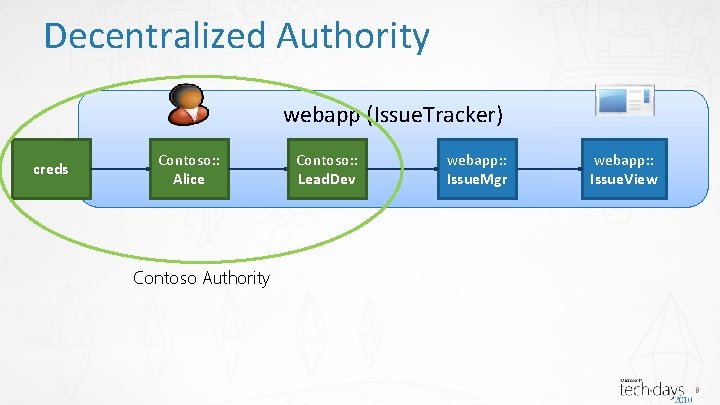
Decentralized Authority webapp (Issue. Tracker) creds Contoso: : Alice Contoso: : Lead. Dev webapp: : Issue. Mgr webapp: : Issue. View Contoso Authority 8

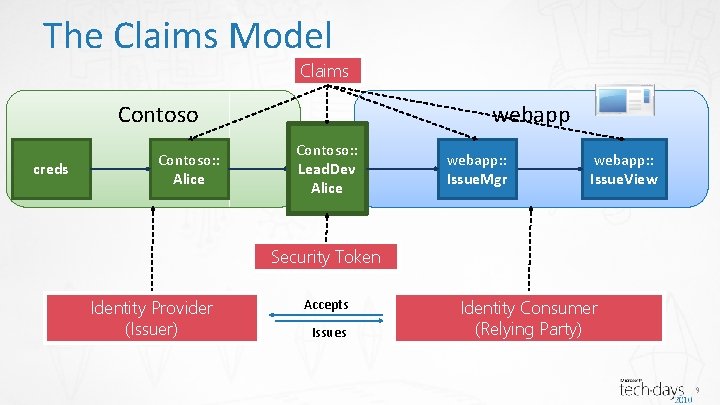
The Claims Model Claims Contoso creds Contoso: : Alice webapp Contoso: : Lead. Dev Alice webapp: : Issue. Mgr webapp: : Issue. View Security Token Identity Provider (Issuer) Accepts Issues Identity Consumer (Relying Party) 9

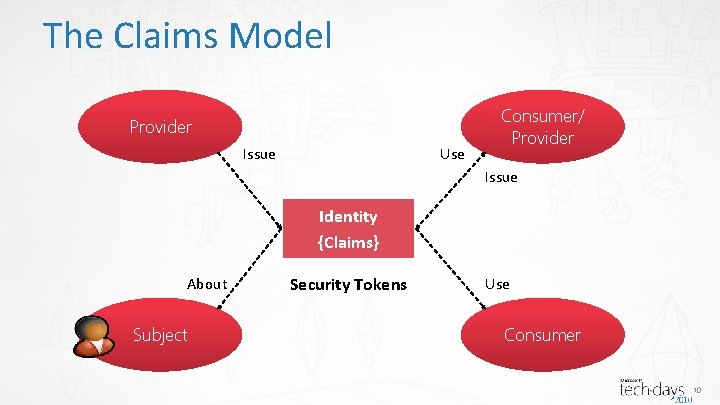
The Claims Model Provider Issue Use Consumer/ Provider Issue Identity {Claims} About Subject Security Tokens Use Consumer 10

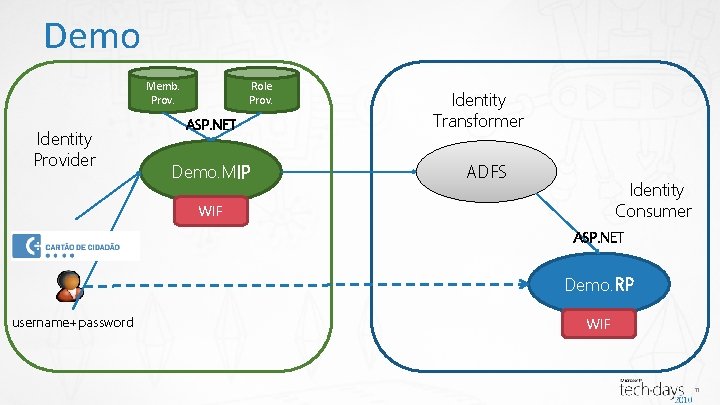
Demo Memb. Prov. Identity Provider Role Prov. ASP. NET Demo. MIP Identity Transformer ADFS Identity Consumer WIF ASP. NET Demo. RP username+password WIF 11

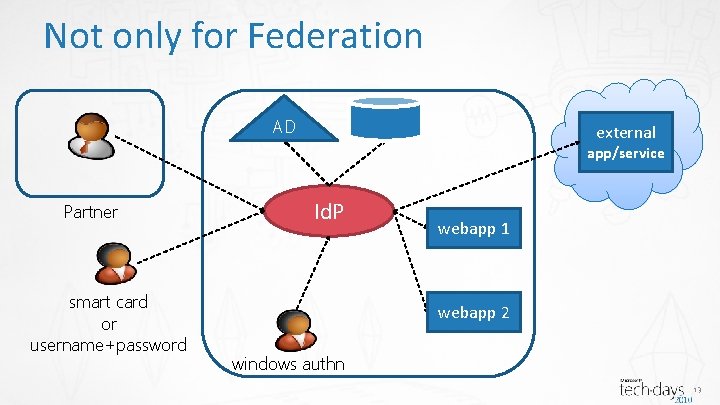
Not only for Federation AD webapp 1 smart card or username+password webapp 2 windows authn 12

Not only for Federation AD external app/service Partner smart card or username+password Id. P webapp 1 webapp 2 windows authn 13

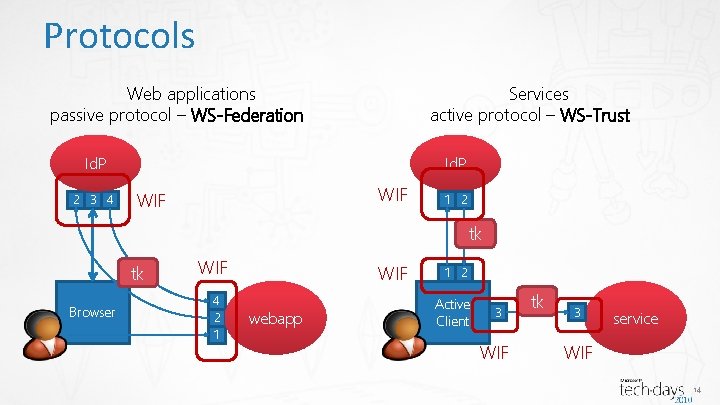
Protocols Web applications passive protocol – WS-Federation Services active protocol – WS-Trust Id. P 2 3 4 Id. P WIF 1 2 tk tk Browser WIF 4 2 1 WIF webapp 1 2 Active Client 3 WIF tk 3 service WIF 14

SAML Tokens • Secure Assertion Markup Language • Signed by provider (issuer) • (Optionally) Encrypted to consumer • Subject confirmation • • Certificate configuration Bearer (passive protocols) Holder-of-Key (active protocols) • Audience restrictions (avoid reusage) • Statements (claims) • Authentication, Authorization and Attributes 15

Federation Metadata • Purpose: automatic configuration • Published by both consumers and providers • Signed XML documents containing • • Endpoint addresses Claims and token types required and offered Certificates … 16

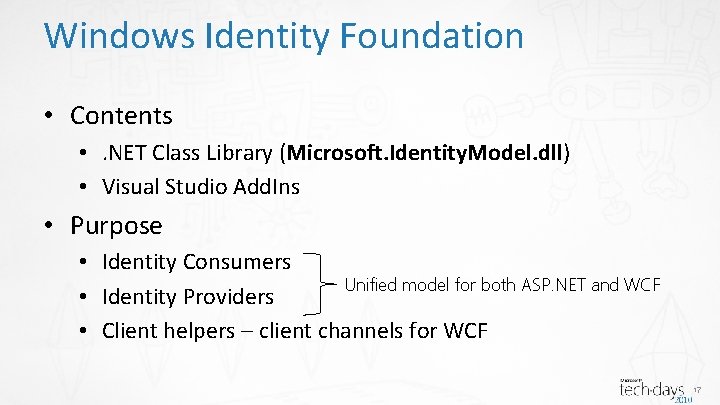
Windows Identity Foundation • Contents • . NET Class Library (Microsoft. Identity. Model. dll) • Visual Studio Add. Ins • Purpose • Identity Consumers Unified model for both ASP. NET and WCF • Identity Providers • Client helpers – client channels for WCF 17

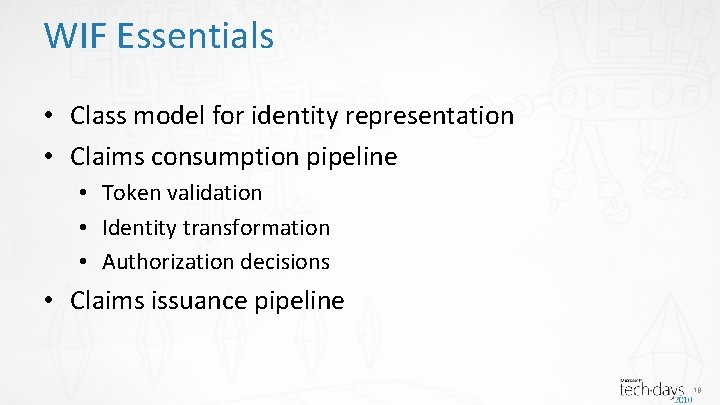
WIF Essentials • Class model for identity representation • Claims consumption pipeline • Token validation • Identity transformation • Authorization decisions • Claims issuance pipeline 18

Claims Class Model 19

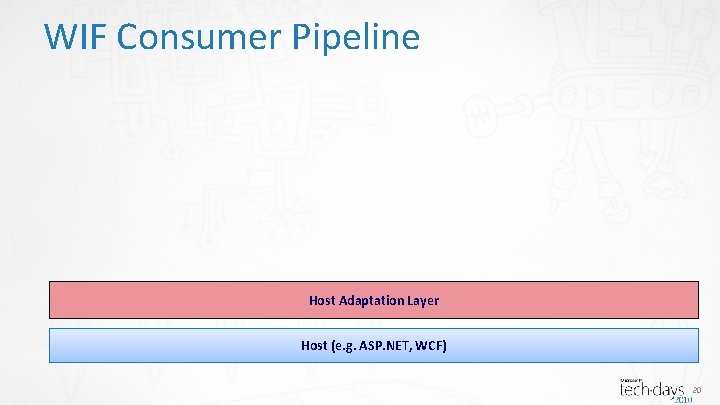
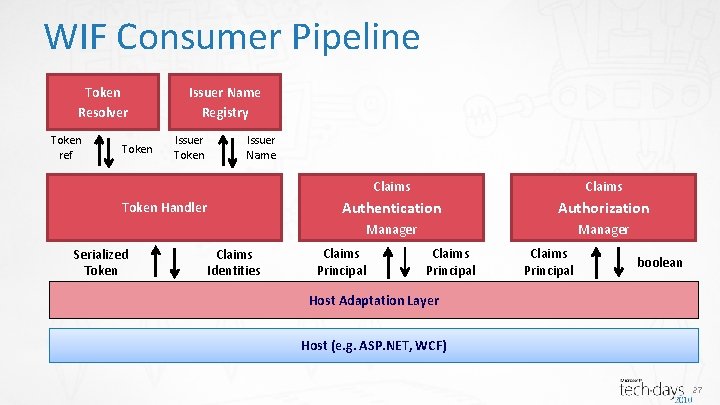
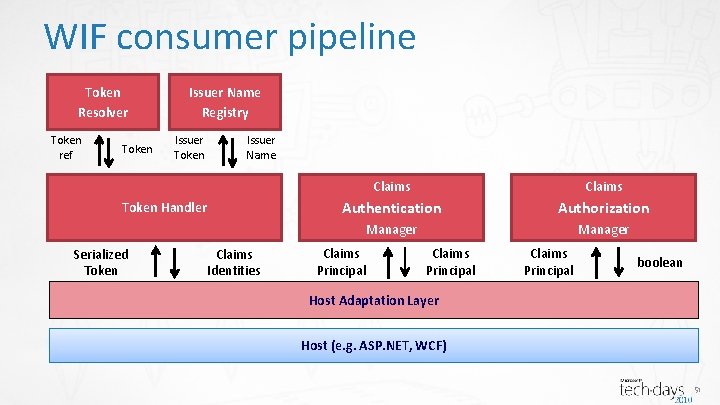
WIF Consumer Pipeline Host Adaptation Layer Host (e. g. ASP. NET, WCF) 20

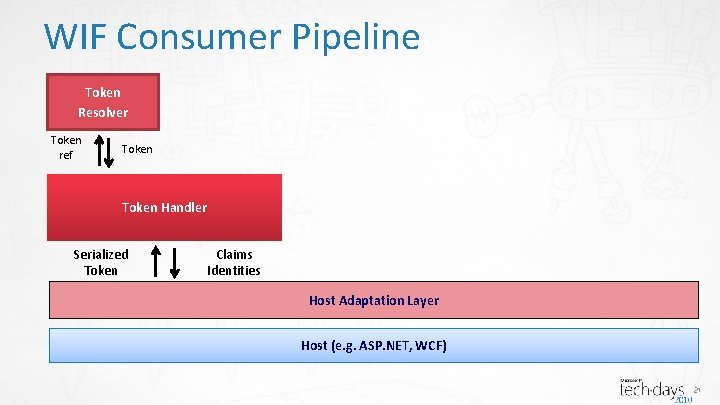
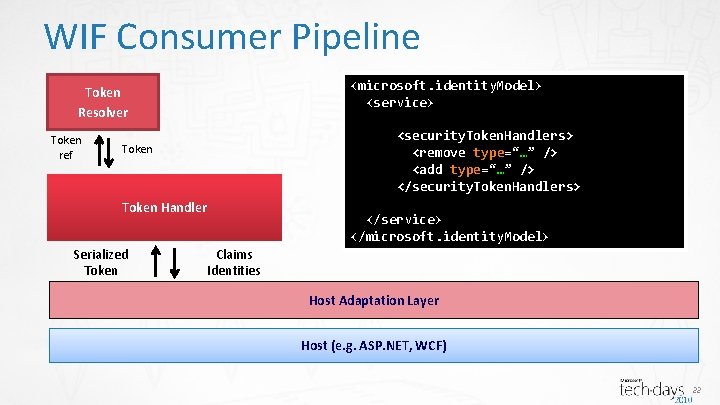
WIF Consumer Pipeline Token Resolver Token ref Token Handler Serialized Token Claims Identities Host Adaptation Layer Host (e. g. ASP. NET, WCF) 21

WIF Consumer Pipeline <microsoft. identity. Model> <service> Token Resolver Token ref <security. Token. Handlers> <remove type=“…” /> <add type=“…” /> </security. Token. Handlers> Token Handler Serialized Token </service> </microsoft. identity. Model> Claims Identities Host Adaptation Layer Host (e. g. ASP. NET, WCF) 22

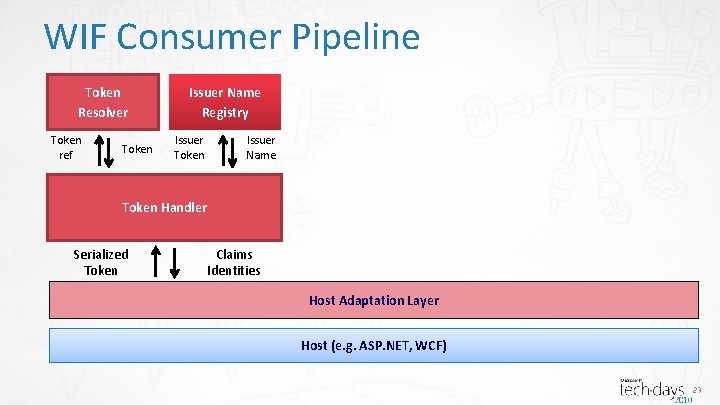
WIF Consumer Pipeline Token Resolver Token ref Token Issuer Name Registry Issuer Token Issuer Name Token Handler Serialized Token Claims Identities Host Adaptation Layer Host (e. g. ASP. NET, WCF) 23

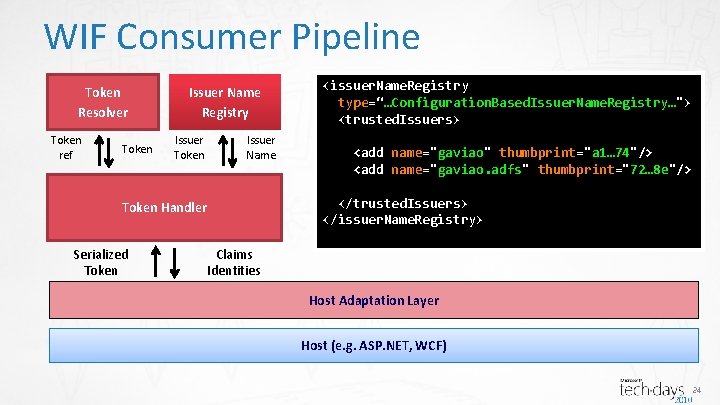
WIF Consumer Pipeline Token Resolver Token ref Token Issuer Name Registry Issuer Token Issuer Name <add name="gaviao" thumbprint="a 1… 74"/> <add name="gaviao. adfs" thumbprint="72… 8 e"/> </trusted. Issuers> </issuer. Name. Registry> Token Handler Serialized Token <issuer. Name. Registry type=“…Configuration. Based. Issuer. Name. Registry…"> <trusted. Issuers> Claims Identities Host Adaptation Layer Host (e. g. ASP. NET, WCF) 24

WIF Consumer Pipeline Token Issuer Name public override IClaims. Principal Authenticate( Resolver string endpoint. Uri, Registry IClaims. Principal incoming. Principal) { Token Issuer ref } Token Name if (incoming. Principal. Identities[0]. Claims. Any(c => Claims c. Claim. Type. Equals(Claim. Types. Role) && c. Value. Equals("Lead. Developer@http: //gaviao/demo. mip/issue. aspx"))) Token Handler Authentication { Manager incoming. Principal. Identities[0]. Claims. Add( Claims new Claim(Claim. Types. Role, "Issue. Mgr)); Serialized Claims Principal } Token Identities return incoming. Principal; Host Adaptation Layer Host (e. g. ASP. NET, WCF) 25

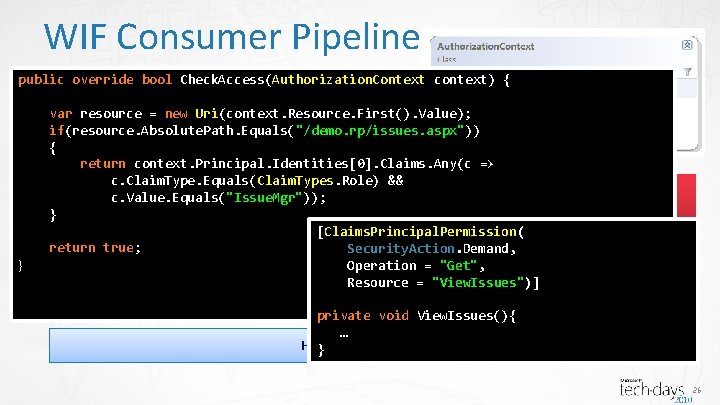
WIF Consumer Pipeline public override bool Check. Access(Authorization. Context context) { Token Issuer Name Registry var Resolver resource = new Uri(context. Resource. First(). Value); if(resource. Absolute. Path. Equals("/demo. rp/issues. aspx")) Token Issuer { Token ref Token Name return context. Principal. Identities[0]. Claims. Any(c => c. Claim. Type. Equals(Claim. Types. Role) && Claims c. Value. Equals("Issue. Mgr")); Token Handler Authentication Authorization } Manager [Claims. Principal. Permission( return true; Security. Action. Demand, Claims Authorization Serialized Claims boolean } Operation = "Get", Principal Context Token Identities Resource = "View. Issues")] Host Adaptation Layer private void View. Issues(){ … Host (e. g. ASP. NET, WCF) } 26

WIF Consumer Pipeline Token Resolver Token ref Token Issuer Name Registry Issuer Token Issuer Name Token Handler Serialized Token Claims Identities Claims Authentication Authorization Manager Claims Principal boolean Host Adaptation Layer Host (e. g. ASP. NET, WCF) 27

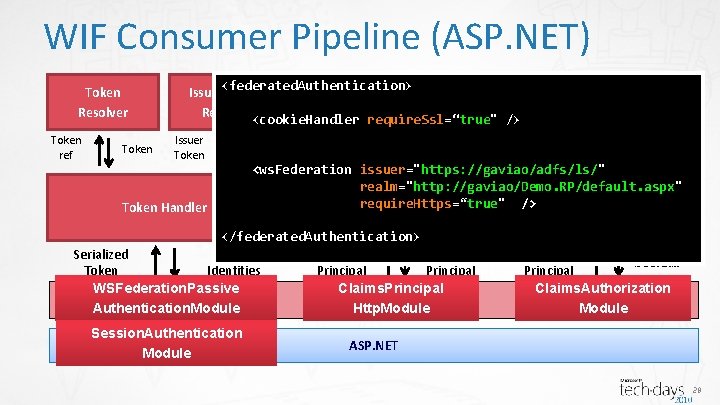
WIF Consumer Pipeline (ASP. NET) Token Resolver Token ref Token Issuer<federated. Authentication> Name Registry <cookie. Handler require. Ssl=“true" /> Issuer Token Handler Issuer Name <ws. Federation issuer="https: //gaviao/adfs/ls/" Claims realm="http: //gaviao/Demo. RP/default. aspx" require. Https=“true" /> Authentication Authorization Manager </federated. Authentication> Claims Serialized Claims Principal Token Identities WSFederation. Passive Claims. Principal Host Adaptation Layer Authentication. Module Http. Module Session. Authentication Module Manager Claims boolean Principal Claims. Authorization Module ASP. NET 28

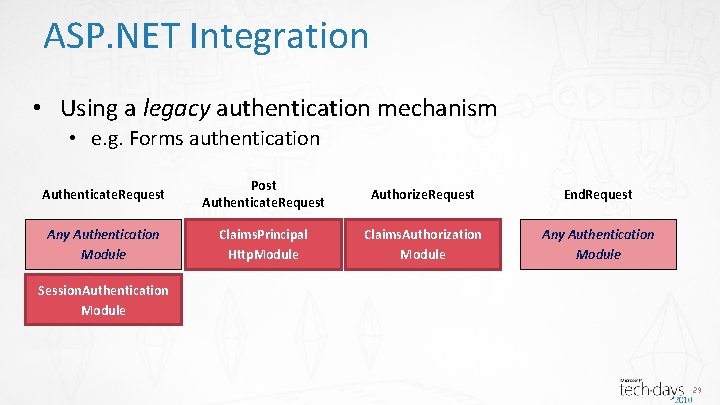
ASP. NET Integration • Using a legacy authentication mechanism • e. g. Forms authentication Authenticate. Request Post Authenticate. Request Authorize. Request End. Request Any Authentication Module Claims. Principal Http. Module Claims. Authorization Module Any Authentication Module Session. Authentication Module 29

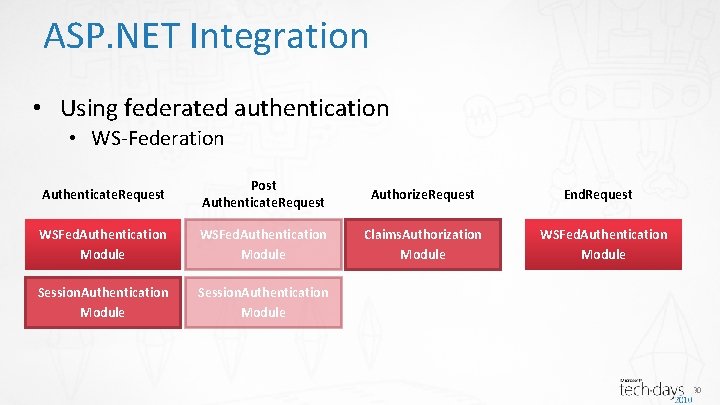
ASP. NET Integration • Using federated authentication • WS-Federation Authenticate. Request Post Authenticate. Request Authorize. Request WSFed. Authentication Module Claims. Authorization Module Session. Authentication Module End. Request WSFed. Authentication Module 30

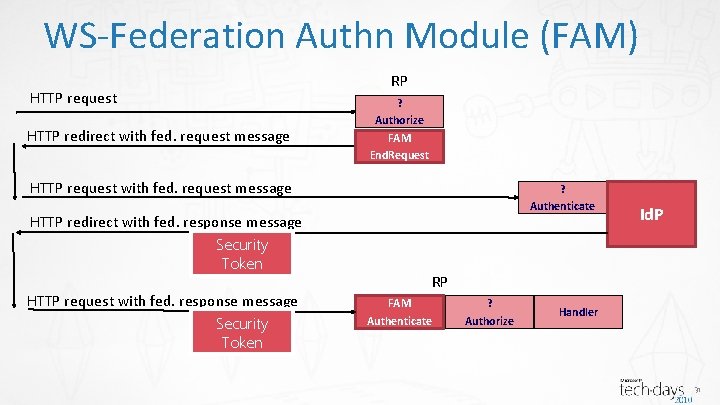
WS-Federation Authn Module (FAM) HTTP request HTTP redirect with fed. request message RP ? Authorize FAM End. Request HTTP request with fed. request message HTTP redirect with fed. response message Security Token HTTP request with fed. response message Security Token ? Authenticate Id. P RP FAM Authenticate ? Authorize Handler 31

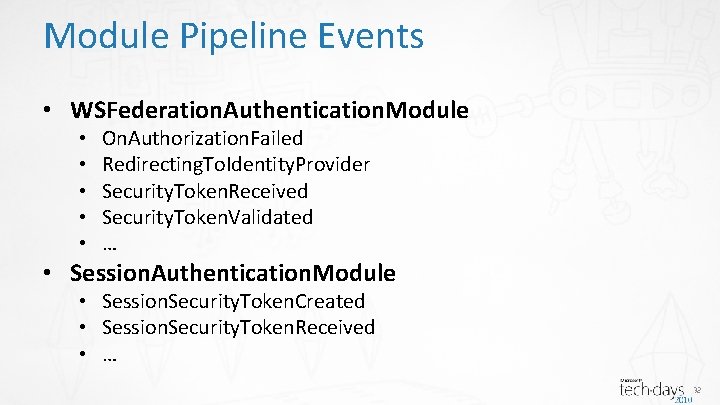
Module Pipeline Events • WSFederation. Authentication. Module • • • On. Authorization. Failed Redirecting. To. Identity. Provider Security. Token. Received Security. Token. Validated … • Session. Authentication. Module • Session. Security. Token. Created • Session. Security. Token. Received • … 32

Controls • Federated. Passive. Sign. In. Status 33

WCF Integration • WCF already supported federation and claims • System. Identity. Model. dll • e. g. WS 2007 Federation. Http. Binding binding, Claims class • WIF • Builds upon this previous support • Changes the token processing model • WCF and ASP. NET uniform model • Adds client-side features (e. g. explicit token requests) 34

WCF Integration • Federated. Service. Credentials • Derives from Service. Credentials • Static <extensions> method Configure. Service. Host(Service. Host. Base) <behavior. Extensions> “installs” WIF (the Host Adaptation Layer) <add name="federated. Service. Host. Configuration" type=“…Configure. Service. Host. Behavior. Extension. Element, …"/> </behavior. Extensions> </extensions> • Overrides WCF behavior, namely • Configuration (e. g. username validation) <behavior name="Demo. RP. status. Behavior"> • Authorization policies <federated. Service. Host. Configuration/> </behavior> • Authentication manager 35

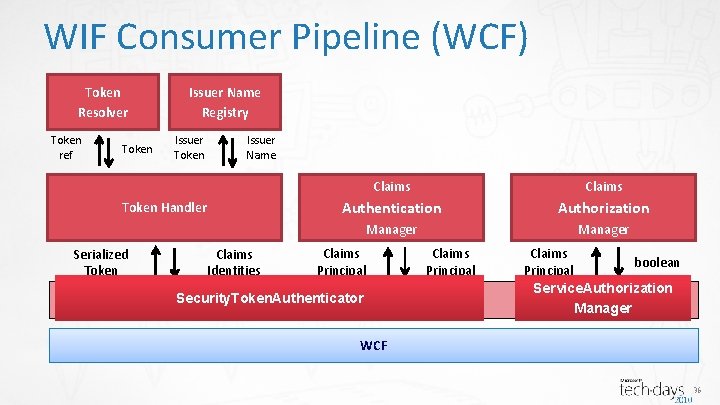
WIF Consumer Pipeline (WCF) Token Resolver Token ref Token Issuer Name Registry Issuer Token Issuer Name Token Handler Serialized Token Claims Identities Claims Authentication Authorization Manager Claims Principal Security. Token. Authenticator Host Adaptation Layer Claims boolean Principal Service. Authorization Manager WCF 36

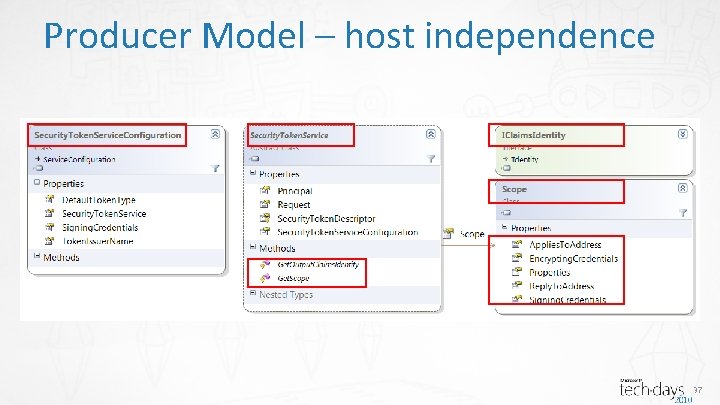
Producer Model – host independence 37

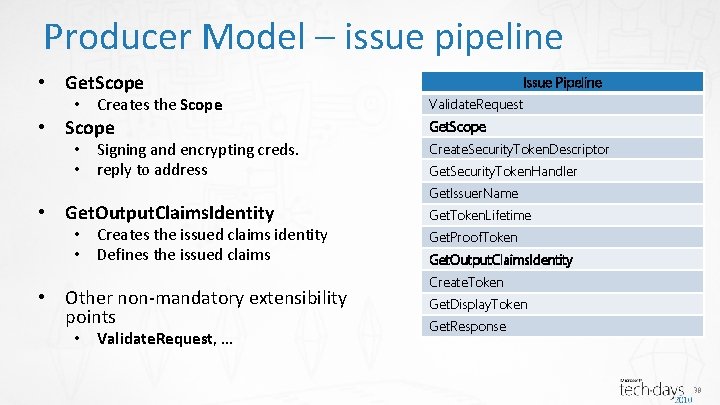
Producer Model – issue pipeline • Get. Scope • Creates the Scope • Signing and encrypting creds. • reply to address • Get. Output. Claims. Identity • Creates the issued claims identity • Defines the issued claims • Other non-mandatory extensibility points • Validate. Request, … Issue Pipeline Validate. Request Get. Scope Create. Security. Token. Descriptor Get. Security. Token. Handler Get. Issuer. Name Get. Token. Lifetime Get. Proof. Token Get. Output. Claims. Identity Create. Token Get. Display. Token Get. Response 38

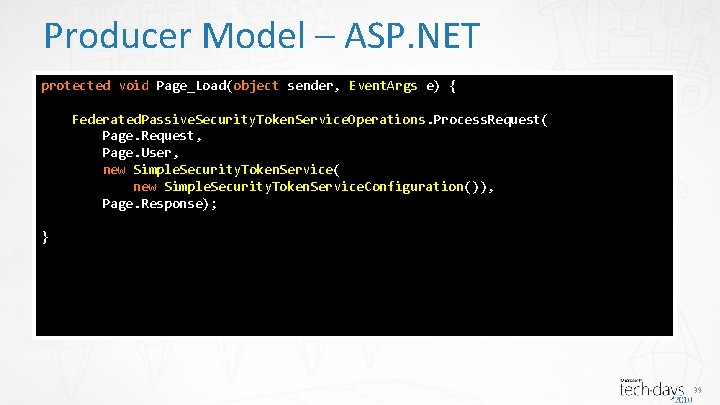
Producer Model – ASP. NET protected void Page_Load(object sender, Event. Args e) { Federated. Passive. Security. Token. Service. Operations. Process. Request( Page. Request, Page. User, new Simple. Security. Token. Service( new Simple. Security. Token. Service. Configuration()), Page. Response); } 39

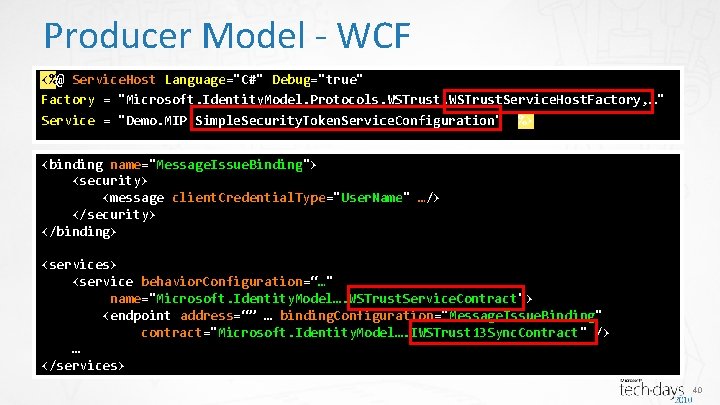
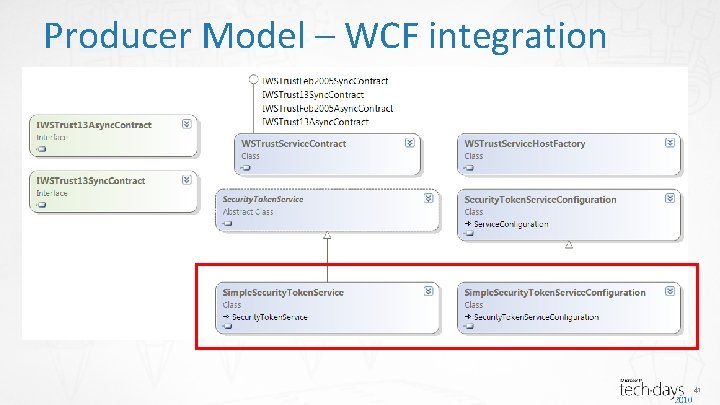
Producer Model - WCF <%@ Service. Host Language="C#" Debug="true" Factory = "Microsoft. Identity. Model. Protocols. WSTrust. Service. Host. Factory, …" Service = "Demo. MIP. Simple. Security. Token. Service. Configuration" %> <binding name="Message. Issue. Binding"> <security> <message client. Credential. Type="User. Name" …/> </security> </binding> <services> <service behavior. Configuration=“…" name="Microsoft. Identity. Model…. WSTrust. Service. Contract"> <endpoint address=“” … binding. Configuration="Message. Issue. Binding" contract="Microsoft. Identity. Model…. IWSTrust 13 Sync. Contract" /> … </services> 40

Producer Model – WCF integration 41

} finally { • Identity and Access Control Management • Claims Model Relevance • WIF • Class library for both identity providers and consumers • Multiple hosts: ASP. NET and WCF 42

Q&A 43

A sua opinião é importante! Complete o questionário de avaliação e devolva-o à saida.

45

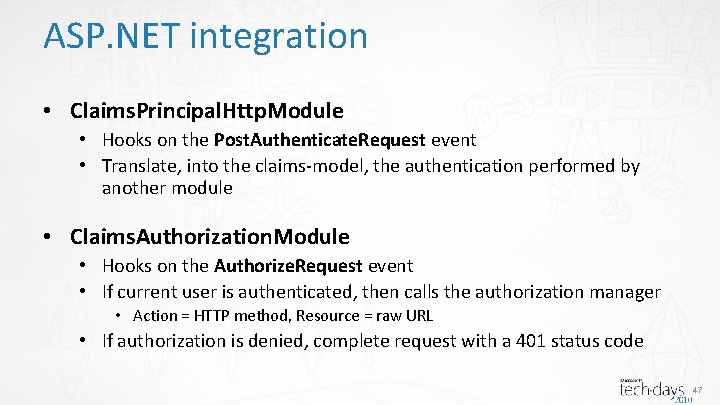
46

ASP. NET integration • Claims. Principal. Http. Module • Hooks on the Post. Authenticate. Request event • Translate, into the claims-model, the authentication performed by another module • Claims. Authorization. Module • Hooks on the Authorize. Request event • If current user is authenticated, then calls the authorization manager • Action = HTTP method, Resource = raw URL • If authorization is denied, complete request with a 401 status code 47

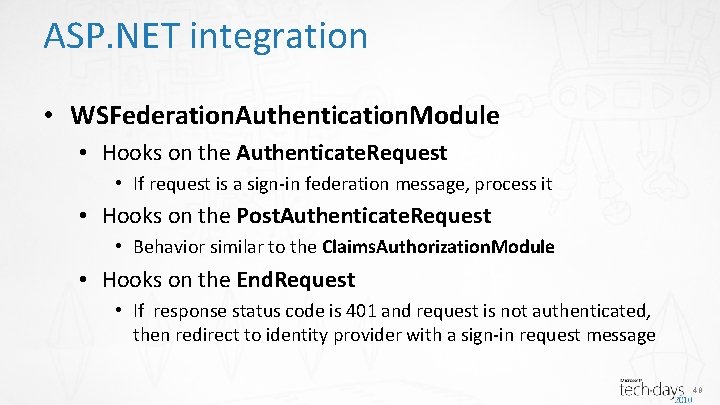
ASP. NET integration • WSFederation. Authentication. Module • Hooks on the Authenticate. Request • If request is a sign-in federation message, process it • Hooks on the Post. Authenticate. Request • Behavior similar to the Claims. Authorization. Module • Hooks on the End. Request • If response status code is 401 and request is not authenticated, then redirect to identity provider with a sign-in request message 48

ASP. NET integration • Session. Authentication. Module • Hooks on the Authenticate. Request event • Try to read and validate session token from a cookie • If successful, then sets the current principal with the session token info • Uses a Cookie. Handler to read and write from cookies 49

Authorization Model - Enforcement • Called automatically in the pipeline • ASP. NET – In a HTTP Module (Claims. Authorization. Module) • WCF – In the service dispatcher • Called explicitly via permission demand • Similar to Principal. Permission and Principal. Permission. Attribute • Claims. Principal. Permission and Claims. Principal. Permission. Attribute 50

WIF consumer pipeline Token Resolver Token ref Token Issuer Name Registry Issuer Token Issuer Name Token Handler Serialized Token Claims Identities Claims Authentication Authorization Manager Claims Principal boolean Host Adaptation Layer Host (e. g. ASP. NET, WCF) 51

A taxonomy of claims • Primordial vs. Substantive claims • • • Primordial – proof (e. g. shared secret) presentable by only one subject Substantive – produced by claims providers Claim types • Static – properties of the subject • • Derived – derived from other claims • • Can-emit-purchase-order; Can-admin-CI-server Contextual – information about the context • 52 Administrator; Lead Developer; Purchase Officer Capability – authorization to something • • Portuguese Citizen; Over-18 Membership – role or group membership, relation with other subject • • National Identifier Number; Date-of-Birth Authentication method, location and time

Security Token Analogies • National Identity Card • • Claims: Name, Do. B, Po. B, Address Subject binding: picture and signature Issuer binding: physical anti-tampering measures Consumer binding: omni-directional identity • Train Ticket • • 53 Claims: authorization to travel in a specific train/place Subject binding: holder, claim Issuer binding: physical anti-tampering measures, signature Consumer binding: authorization details

Authorization Model • “Old” model (Principal. Permission) • Principal. Permission constructed with the required identity names and/or roles • Association between the permission and the users is hard-coded • “New” model (Claims. Principal. Permission) • Claims. Principal. Permission constructed with the resource and action characterization • Association between the permission and the required identity is external 54
 Aplicaes
Aplicaes Aplicaes
Aplicaes Habilidades essenciais dos negociadores
Habilidades essenciais dos negociadores Elizabete nunes
Elizabete nunes Termos da oração
Termos da oração Quais são os substantivos
Quais são os substantivos Pessoas essenciais
Pessoas essenciais Conjunções coordenativas
Conjunções coordenativas Mino arc
Mino arc Arc emu88 com arc info 47 100047 html
Arc emu88 com arc info 47 100047 html Arc promoteur vs arc investigateur
Arc promoteur vs arc investigateur Parts of a circle
Parts of a circle Kin 303
Kin 303 Zool 303
Zool 303 Vir 303
Vir 303 Bilişi yönetme
Bilişi yönetme Eco 303
Eco 303 Uib290
Uib290 Sis-303
Sis-303 Comp 303
Comp 303 Software development problems
Software development problems Dywizjon 303 klp
Dywizjon 303 klp 303-318-9014
303-318-9014 Vicentiu covrig
Vicentiu covrig 3 6 9 12 15 18 21 24 27 30
3 6 9 12 15 18 21 24 27 30 38cfr3.303
38cfr3.303 Lili ruger
Lili ruger Mktg 303
Mktg 303 Kravis and linder theory of trade
Kravis and linder theory of trade Desenvolvimento da ciência
Desenvolvimento da ciência Desenvolvimento da linguagem humana
Desenvolvimento da linguagem humana Desenvolvimento combinado e desigual
Desenvolvimento combinado e desigual Desenvolvimento
Desenvolvimento Desenvolvimento adulto
Desenvolvimento adulto Somitos
Somitos Estagios de desenvolvimento piaget
Estagios de desenvolvimento piaget Jocelyne giasson
Jocelyne giasson Desenvolvimento intrauterino
Desenvolvimento intrauterino Pixabay
Pixabay Biografia de david ausubel
Biografia de david ausubel Autoavaliação jornada de desenvolvimento socioemocional
Autoavaliação jornada de desenvolvimento socioemocional L
L Como começar o desenvolvimento
Como começar o desenvolvimento Ministério do desenvolvimento social e combate à fome
Ministério do desenvolvimento social e combate à fome Aspecto do desenvolvimento humano
Aspecto do desenvolvimento humano Processo unificado de software
Processo unificado de software Desenvolvimento da ciência
Desenvolvimento da ciência Controle do desenvolvimento microbiano nos alimentos
Controle do desenvolvimento microbiano nos alimentos Teoria do desenvolvimento organizacional
Teoria do desenvolvimento organizacional Desenvolvimento vocacional donald super
Desenvolvimento vocacional donald super Desenvolvimento
Desenvolvimento Partenogênese
Partenogênese Com o desenvolvimento
Com o desenvolvimento