An attempt to simplify security arguments for hashbased

An attempt to simplify security arguments for hash-based signatures Andreas Hülsing Eindhoven University of Technology Oxford Post-Quantum Cryptography Workshop 2019

The quantum threat • Shor’s algorithm breaks RSA, (EC)DSA, (EC)DH, … • Grover’s algorithm asymptotically reduces complexity of brute-force search attacks by a square-root factor. 10. 09. 2020 https: //huelsing. net 2
Why care today • EU launched a one billion Euro project on quantum technologies • Similar range is spent in China • US administration passed a bill on spending $1. 275 billion US dollar on quantum computing research • Google, IBM, Microsoft, Alibaba, and others run their own research programs. 10. 09. 2020 https: //huelsing. net 3

It‘s a question of risk assessment 10. 09. 2020 https: //huelsing. net 4
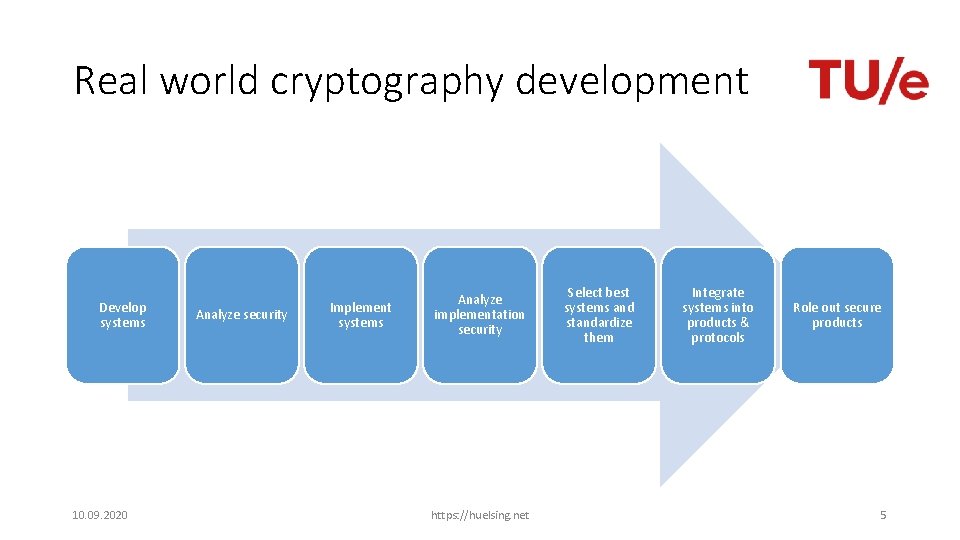
Real world cryptography development Develop systems 10. 09. 2020 Analyze security Implement systems Analyze implementation security https: //huelsing. net Select best systems and standardize them Integrate systems into products & protocols Role out secure products 5

Who would store all encrypted data traffic? That must be expensive! $1. 5 B 10. 09. 2020 https: //huelsing. net 6

Long-lived systems • Development time easily 10+ years • Lifetime easily 10+ years • At least make sure you got a secure update channel! 10. 09. 2020 https: //huelsing. net 7
![Hash-based signatures [Lam 79, Mer 89] No new hardness assumptions Provably (post-quantum) secure if Hash-based signatures [Lam 79, Mer 89] No new hardness assumptions Provably (post-quantum) secure if](http://slidetodoc.com/presentation_image/1083001992eacf58f5e2ad0631317196/image-8.jpg)
Hash-based signatures [Lam 79, Mer 89] No new hardness assumptions Provably (post-quantum) secure if (post-quantum) secure hash function is used Basic concept extremely easy Stateful 10. 09. 2020 https: //huelsing. net 8
Basic construction 10. 09. 2020 https: //huelsing. net 9
![Lamport OTS [Lam 79] * Message M = b 1, …, bm, OWF H Lamport OTS [Lam 79] * Message M = b 1, …, bm, OWF H](http://slidetodoc.com/presentation_image/1083001992eacf58f5e2ad0631317196/image-10.jpg)
Lamport OTS [Lam 79] * Message M = b 1, …, bm, OWF H = n bit SK sk 1, 0 sk 1, 1 H PK Sig 10. 09. 2020 H pk 1, 0 b 1 skm, 0 H H pk 1, 1 Mux skm, 1 H H pkm, 0 b 2 Mux sk 1, b 1 bm pkm, 1 Mux skm, bm https: //huelsing. net 10
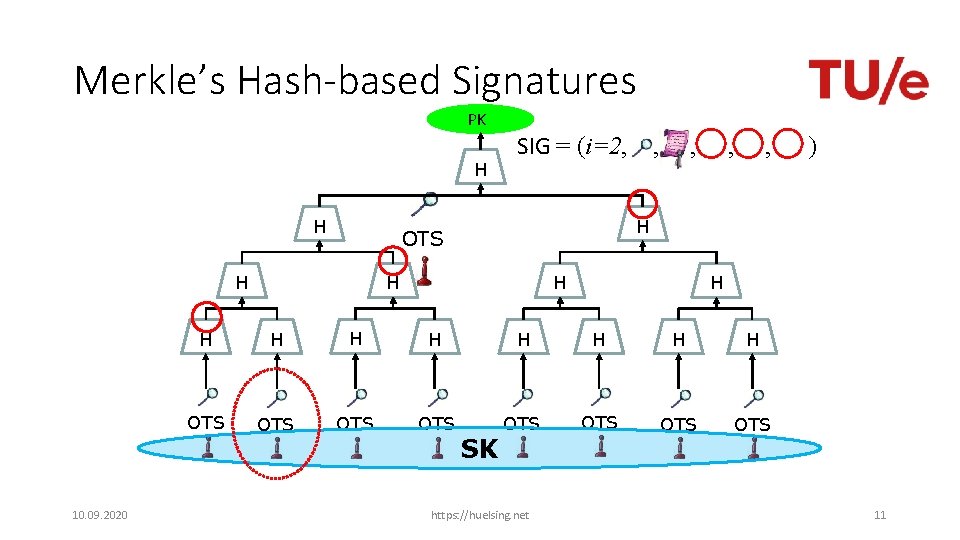
Merkle’s Hash-based Signatures PK H H , , , ) H OTS H 10. 09. 2020 SIG = (i=2, , H H H OTS OTS SK https: //huelsing. net 11

Winternitz-OTS 10. 09. 2020 https: //huelsing. net 12
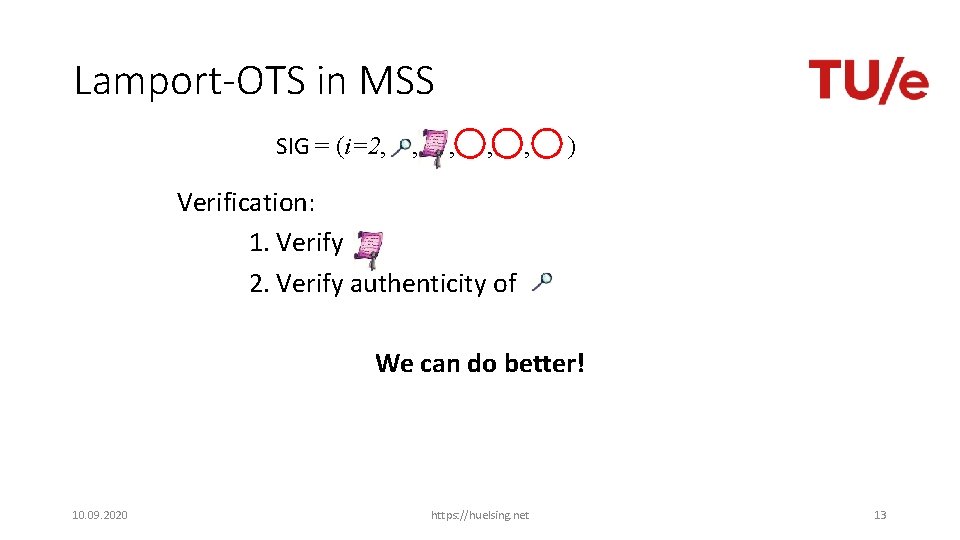
Lamport-OTS in MSS SIG = (i=2, , , ) Verification: 1. Verify 2. Verify authenticity of We can do better! 10. 09. 2020 https: //huelsing. net 13
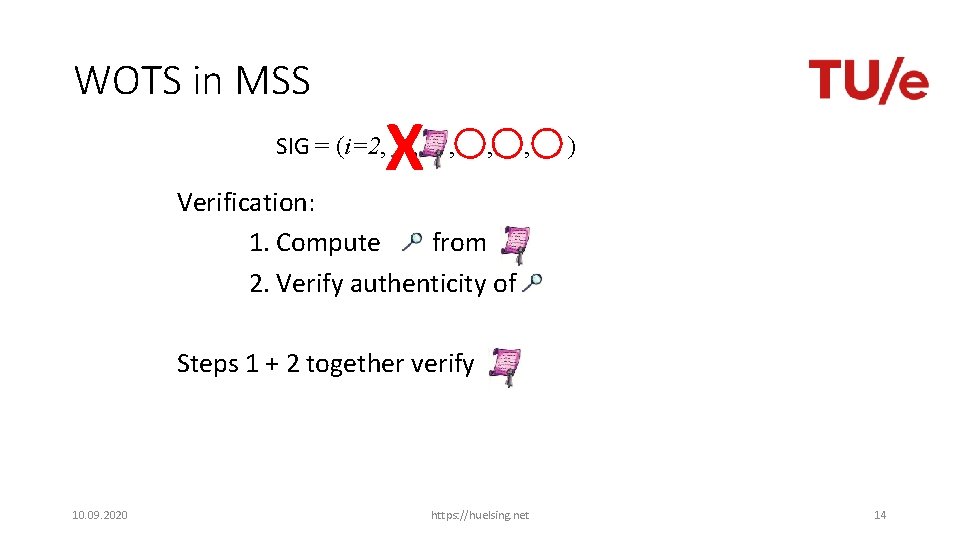
WOTS in MSS X SIG = (i=2, , , ) Verification: 1. Compute from 2. Verify authenticity of Steps 1 + 2 together verify 10. 09. 2020 https: //huelsing. net 14
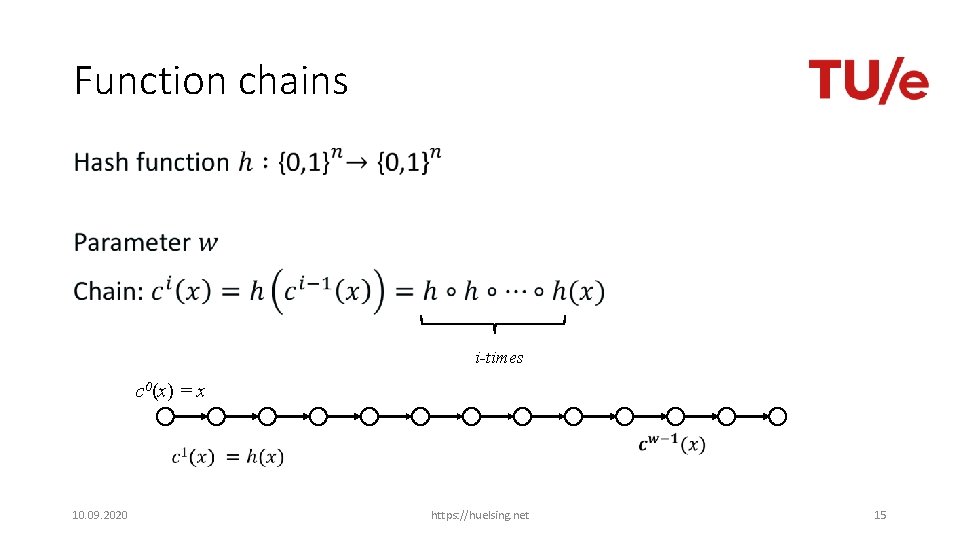
Function chains • i-times c 0(x) = x 10. 09. 2020 https: //huelsing. net 15
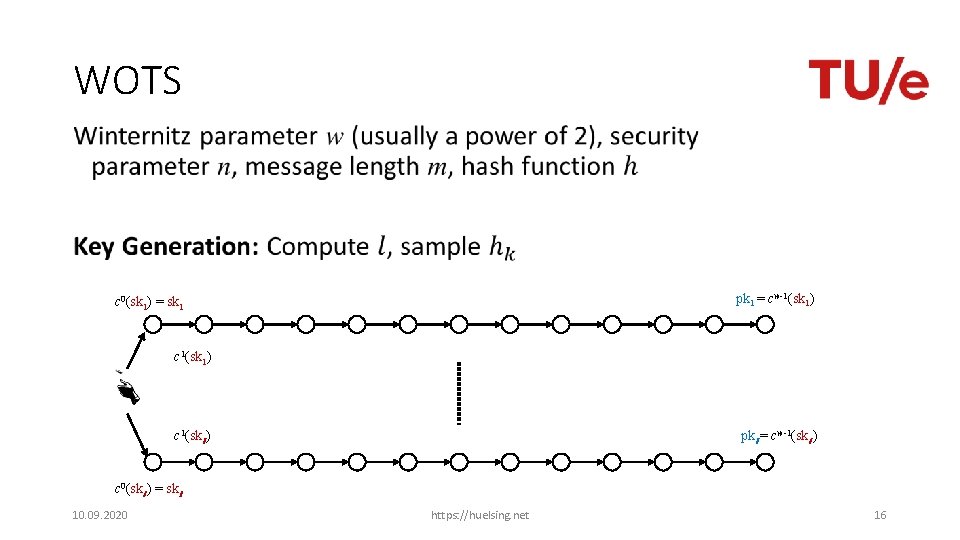
WOTS • pk 1 = cw-1(sk 1) c 0(sk 1) = sk 1 c 1(sk 1) c 1(skl ) pkl = cw-1(skl ) c 0(skl ) = skl 10. 09. 2020 https: //huelsing. net 16
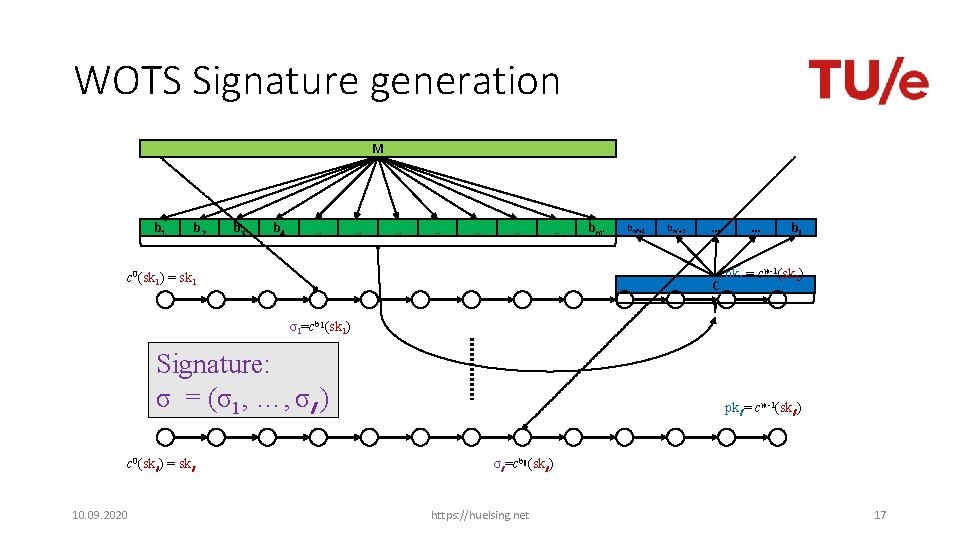
WOTS Signature generation M b 1 b 2 b 3 b 4 … … … … c 0(sk 1) = sk 1 bm‘+1 bm‘+2 … C … bl pk 1 = cw-1(sk 1) σ1=cb 1(sk 1) Signature: σ = (σ1, …, σl ) c 0(skl ) = skl 10. 09. 2020 pkl = cw-1(skl ) σl =cbl (skl ) https: //huelsing. net 17
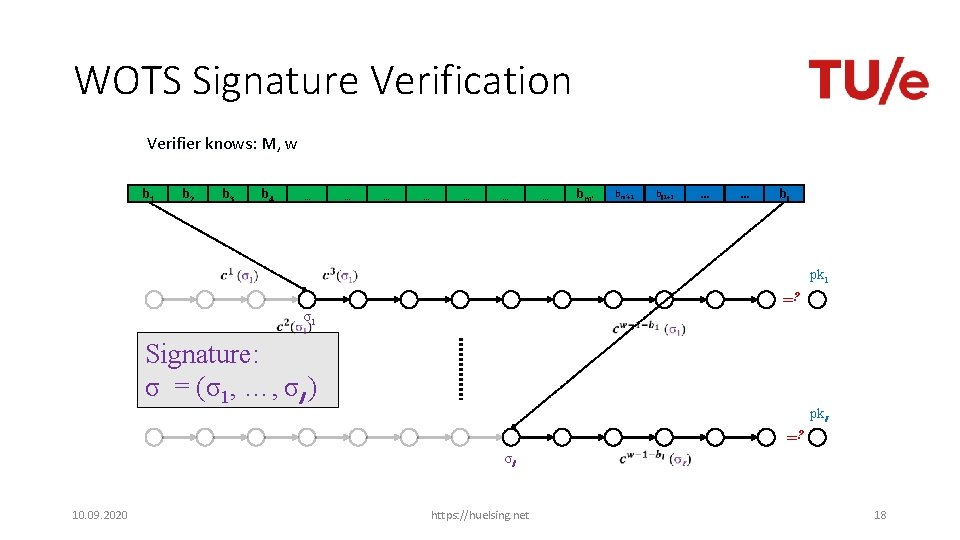
WOTS Signature Verification Verifier knows: M, w b 1 b 2 b 3 b 4 … … … … bm‘+1 bl 1+2 … … bl pk 1 =? σ1 Signature: σ = (σ1, …, σl ) pkl =? σl 10. 09. 2020 https: //huelsing. net 18

Multi-Tree MSS 10. 09. 2020 https: //huelsing. net 19
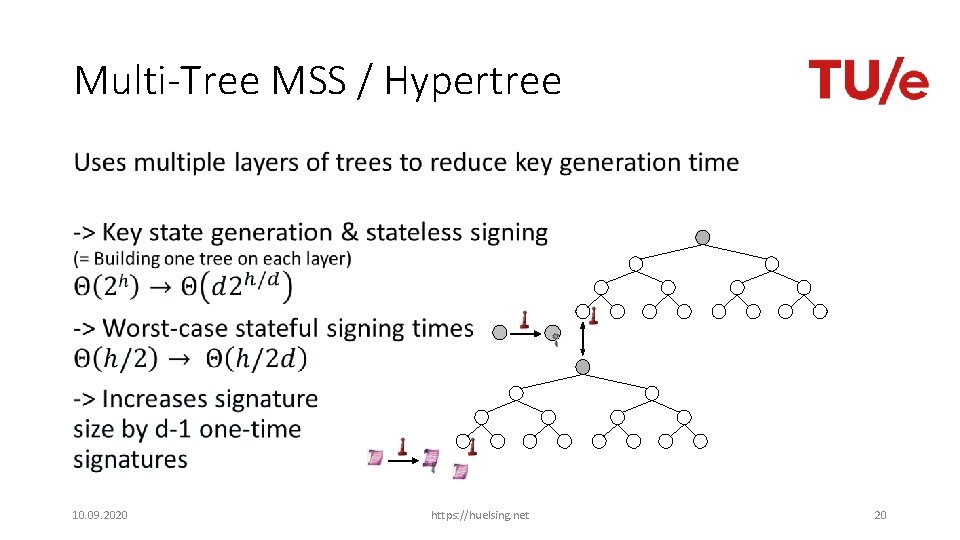
Multi-Tree MSS / Hypertree • 10. 09. 2020 https: //huelsing. net 20

SPHINCS 10. 09. 2020 https: //huelsing. net 21
![Stateless hash-based signatures [NY 89, Gol 87, Gol 04] OTS • OTS OTS OTS Stateless hash-based signatures [NY 89, Gol 87, Gol 04] OTS • OTS OTS OTS](http://slidetodoc.com/presentation_image/1083001992eacf58f5e2ad0631317196/image-22.jpg)
Stateless hash-based signatures [NY 89, Gol 87, Gol 04] OTS • OTS OTS OTS 10 -9 -2020 OTS PAGE 22
![SPHINCS [BHH+15] • Select index pseudo-randomly • Use a few-time signature key-pair on leaves SPHINCS [BHH+15] • Select index pseudo-randomly • Use a few-time signature key-pair on leaves](http://slidetodoc.com/presentation_image/1083001992eacf58f5e2ad0631317196/image-23.jpg)
SPHINCS [BHH+15] • Select index pseudo-randomly • Use a few-time signature key-pair on leaves to sign messages • Few index collisions allowed • Allows to reduce tree height • Use hypertree: Use d << h. 10. 09. 2020 https: //huelsing. net 23

Security arguments 10. 09. 2020 https: //huelsing. net 24

Requirements Reductions should lead to • collision-resilience, • multi-target attack protection, • tight security reductions, and allow for • easy verification, and • maintainability. 10. 09. 2020 https: //huelsing. net 25
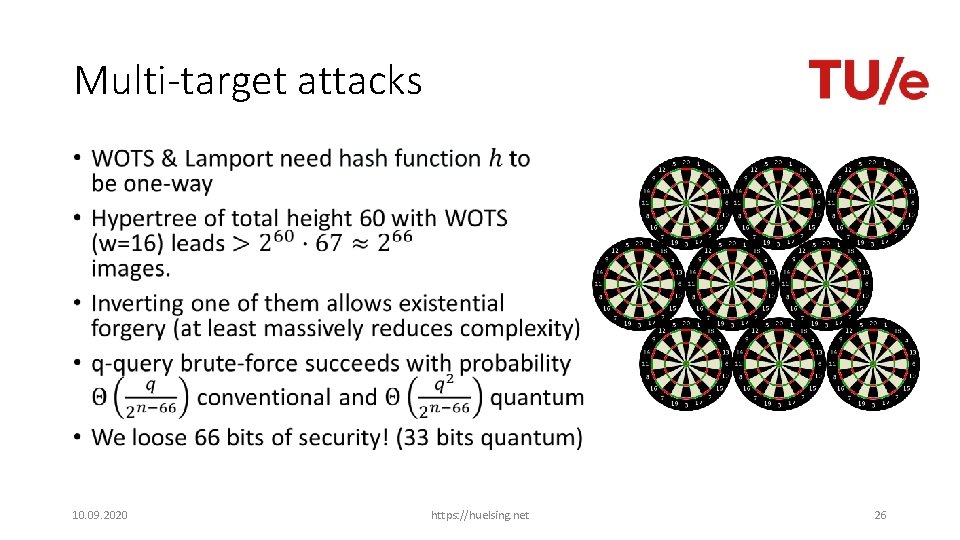
Multi-target attacks • 10. 09. 2020 https: //huelsing. net 26

Multi-target attacks: Mitigation • 10. 09. 2020 https: //huelsing. net 27
![Multi-target attacks: Mitigation • Mitigation: Separate targets [HRS 16] • Common approach: • In Multi-target attacks: Mitigation • Mitigation: Separate targets [HRS 16] • Common approach: • In](http://slidetodoc.com/presentation_image/1083001992eacf58f5e2ad0631317196/image-28.jpg)
Multi-target attacks: Mitigation • Mitigation: Separate targets [HRS 16] • Common approach: • In addition to hash function description and „input“ take • Hash „Address“ (uniqueness in key pair) • Hash „key“ used for all hashes of one key pair (uniqueness among key pairs) 10. 09. 2020 https: //huelsing. net 28
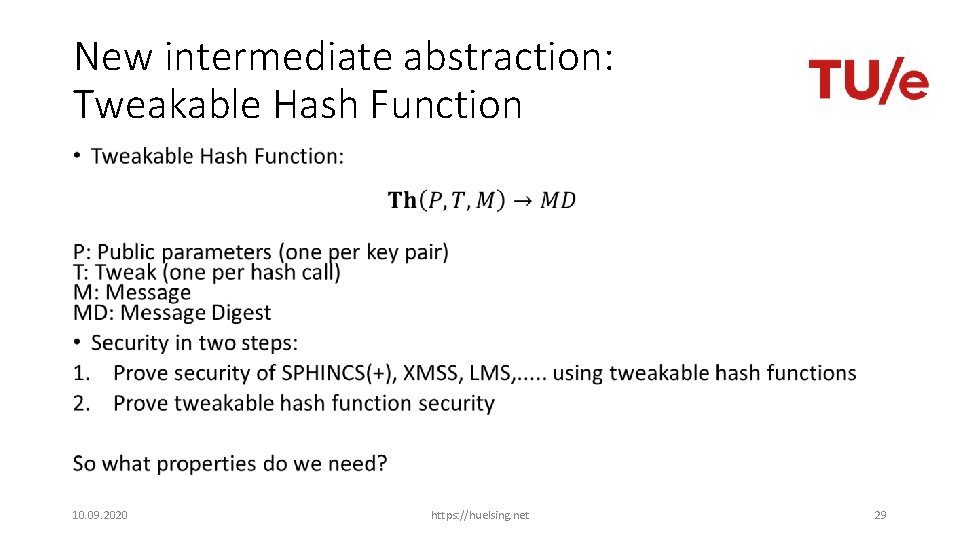
New intermediate abstraction: Tweakable Hash Function • 10. 09. 2020 https: //huelsing. net 29

Single-function multi-target collision resistance for distinct tweaks • 10. 09. 2020 https: //huelsing. net 30
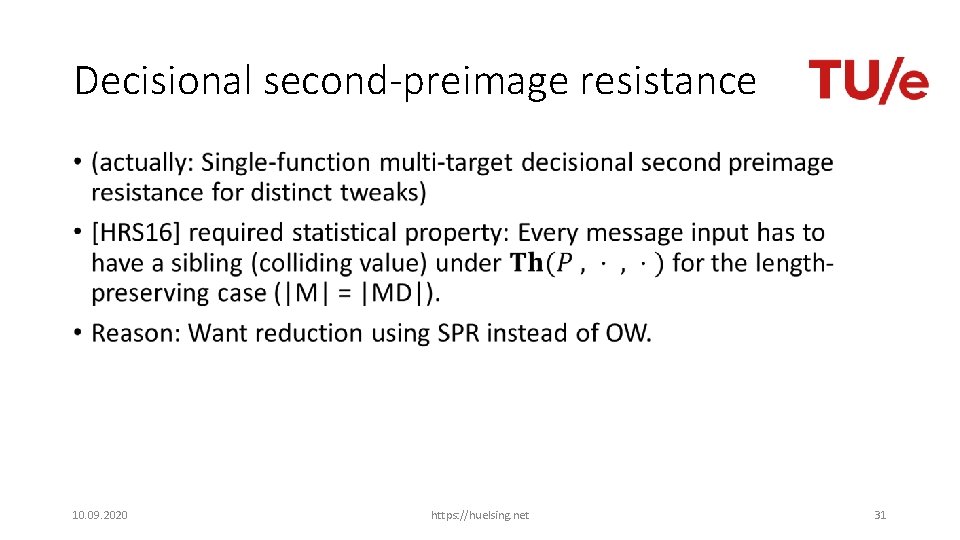
Decisional second-preimage resistance • 10. 09. 2020 https: //huelsing. net 31
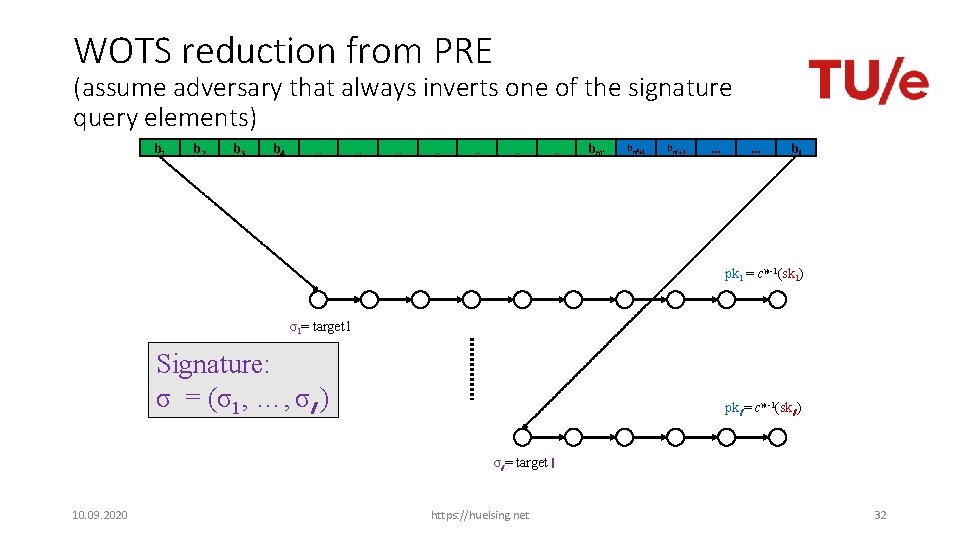
WOTS reduction from PRE (assume adversary that always inverts one of the signature query elements) b 1 b 2 b 3 b 4 … … … … bm‘+1 bm‘+2 … … bl pk 1 = cw-1(sk 1) σ1= target 1 Signature: σ = (σ1, …, σl ) pkl = cw-1(skl ) σl = target l 10. 09. 2020 https: //huelsing. net 32

Decisional second-preimage resistance • 10. 09. 2020 https: //huelsing. net 33

• 10. 09. 2020 https: //huelsing. net 34
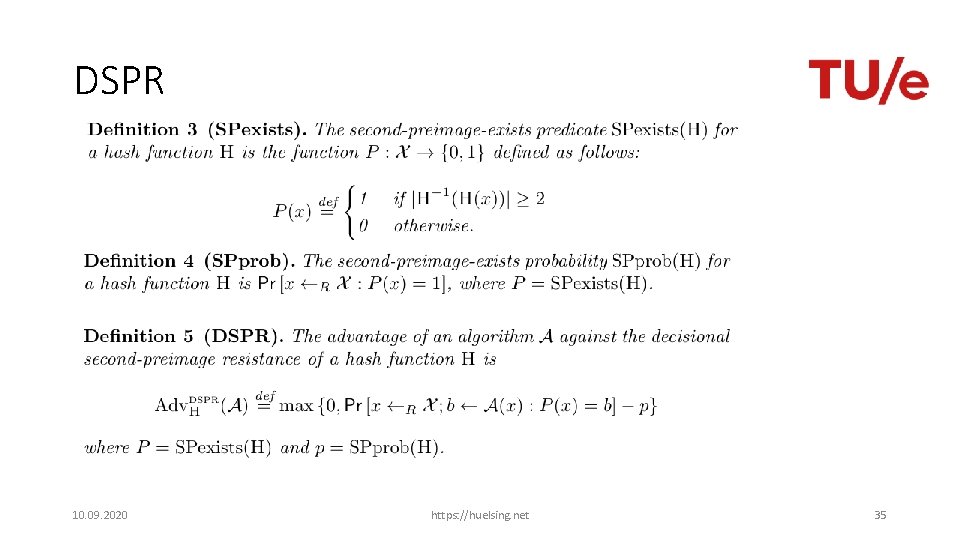
DSPR 10. 09. 2020 https: //huelsing. net 35

DSPR • 10. 09. 2020 https: //huelsing. net 36
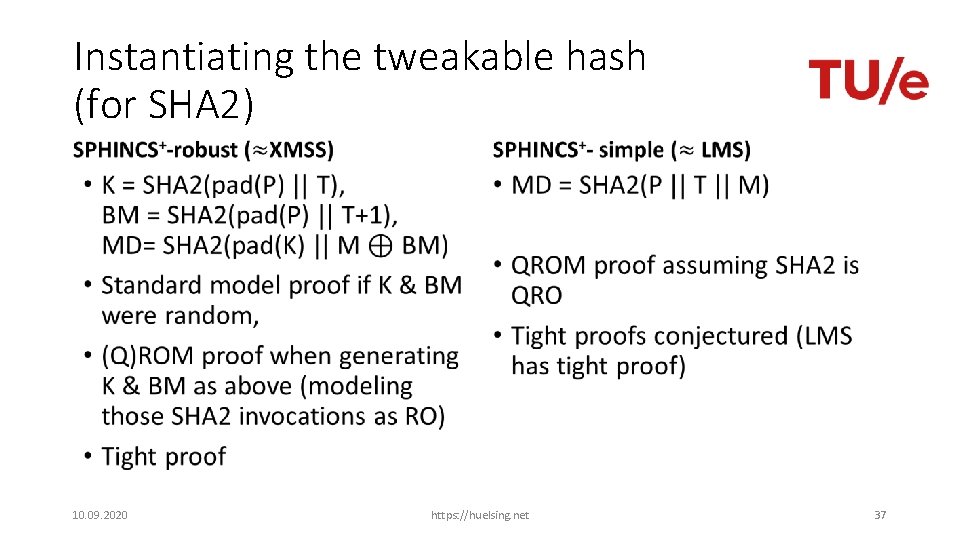
Instantiating the tweakable hash (for SHA 2) • 10. 09. 2020 • https: //huelsing. net 37

Instantiating the tweakable hash • SPHINCS+-simple is factor 3 faster • SPHINCS+-simple makes somewhat stronger assumptions about the security properties of the used hash function • More research on direct constructions needed 10. 09. 2020 https: //huelsing. net 38

Thank you! Questions? For references, literature & longer lectures see https: //huelsing. net 10. 09. 2020 https: //huelsing. net PAGE 39

+ SPHINCS Joint work with Daniel J. Bernstein, Christoph Dobraunig, Maria Eichlseder, Scott Fluhrer, Stefan-Lukas Gazdag, Panos Kampanakis, Stefan Kölbl, Tanja Lange, Martin M. Lauridsen, Florian Mendel, Ruben Niederhagen, Christian Rechberger, Joost Rijneveld, Peter Schwabe 10. 09. 2020 https: //huelsing. net 40

SPHINCS+ (our NIST submission) • Strengthened security gives smaller signatures • Collision- and multi-target attack resilient (XMSS tweakable hash) • Fixed length signatures • Small keys, medium size signatures (lv 3: 17 k. B) • Sizes can be much smaller if q_sign gets reduced • The conservative choice 10. 09. 2020 https: //huelsing. net 41
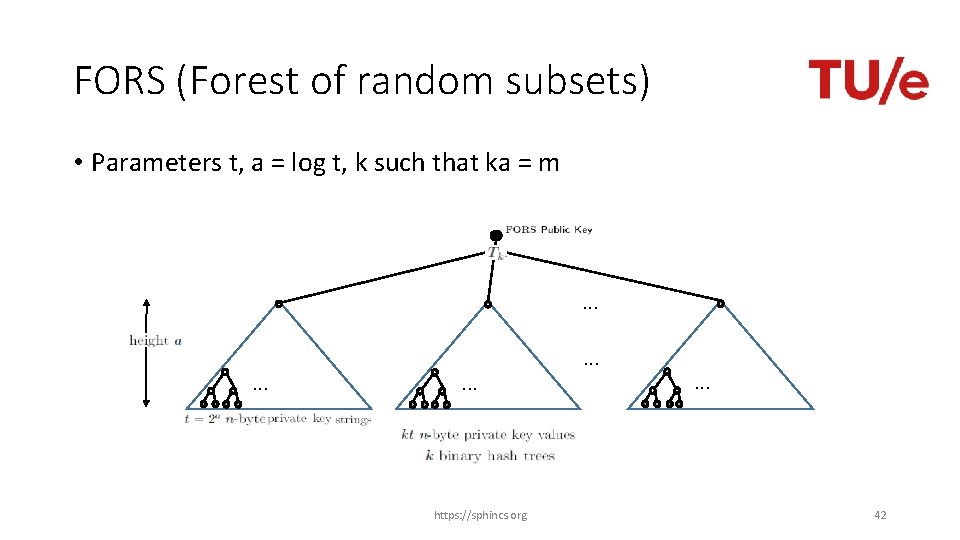
FORS (Forest of random subsets) • Parameters t, a = log t, k such that ka = m . . https: //sphincs. org . . . 42

Verifiable index selection (and optionally non-deterministic randomness) • https: //sphincs. org 43

Verifiable index selection Improves FORS security • SPHINCS: Attacks can target „weakest“ HORST key pair • SPHINCS+: Every hash query also selects FORS key pair • Leads to notion of interleaved target subset resilience https: //sphincs. org 44

Instantiations (after second round tweaks) • SPHINCS+-SHAKE 256 -robust • SPHINCS+-SHAKE 256 -simple NEW! • SPHINCS+-SHA-256 -robust • SPHINCS+-SHA-256 -simple NEW! • SPHINCS+-Haraka-robust • SPHINCS+-Haraka-simple NEW! 10. 09. 2020 https: //huelsing. net 45
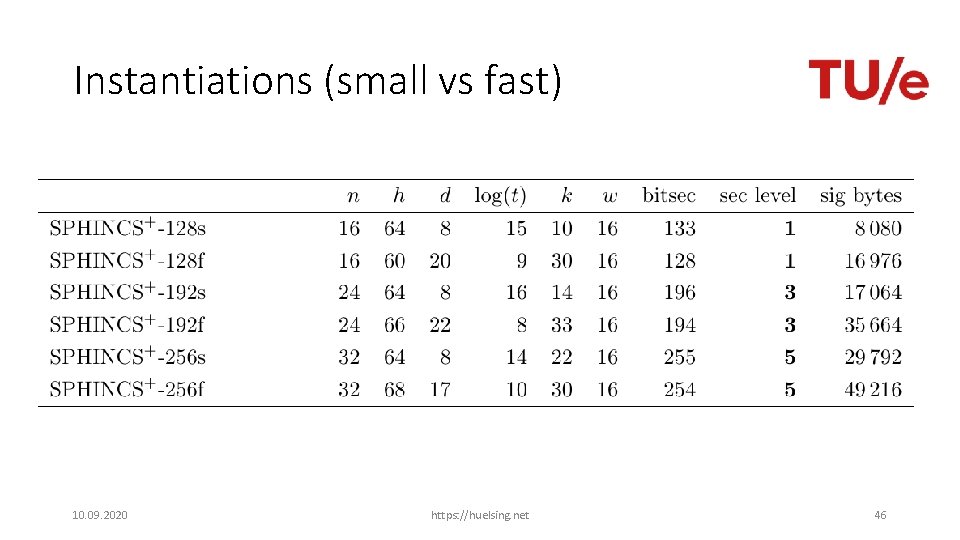
Instantiations (small vs fast) 10. 09. 2020 https: //huelsing. net 46
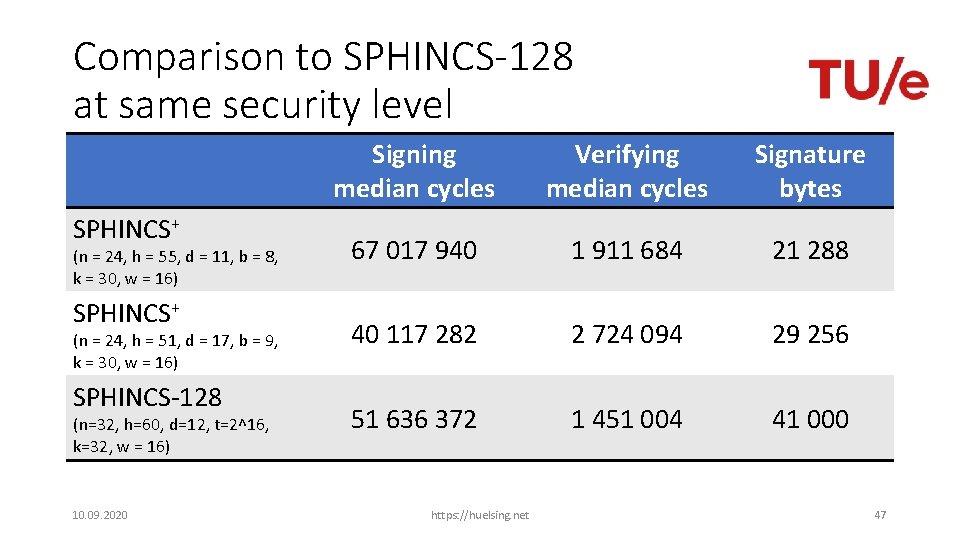
Comparison to SPHINCS-128 at same security level SPHINCS+ (n = 24, h = 55, d = 11, b = 8, k = 30, w = 16) SPHINCS+ (n = 24, h = 51, d = 17, b = 9, k = 30, w = 16) SPHINCS-128 (n=32, h=60, d=12, t=2^16, k=32, w = 16) 10. 09. 2020 Signing median cycles Verifying median cycles Signature bytes 67 017 940 1 911 684 21 288 40 117 282 2 724 094 29 256 51 636 372 1 451 004 41 000 https: //huelsing. net 47
Hash-based Signatures in NIST „Competition“ • SPHINCS+ • FORS as few-time signature • XMSS-T tweakable hash • Gravity-SPHINCS (R. I. P. ) • PORS as few-time signature • Requires collision-resistance -> no tweakable hash • (PICNIC) 10. 09. 2020 https: //huelsing. net 48
- Slides: 48