70 293 MCSE Guide to Planning a Microsoft
































- Slides: 51

70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network, Enhanced Chapter 10: Planning and Managing IP Security 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network

Objectives • Describe IP Security issues and how the IPSec protocol addresses them • Choose the appropriate IPSec mode for a given situation • Implement authentication for IPSec • Enable IPSec • Create IPSec policies • Monitor and troubleshoot IPSec 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 2

Why IPSec Is Important • IPSec provides security for IP-based networks • Authenticate both computers engaged in a conversation • Use digital signatures to verify that data has not been tampered with while in transit • Encrypt data while in transit 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 3

How Hackers Work • IPv 4 has no built-in security mechanisms to protect the communication between two hosts • Hackers can corrupt or eavesdrop on communications • • Packet sniffing Data replay Data modification Address spoofing 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 4

Authentication, Encryption, and Digital Signatures • IPSec authenticates the endpoints of any IP-based conversation using IPSec • Each participant must be known and trusted • Encryption can be used by IPSec to hide the contents of data packets • Digital signatures on each packet in a conversation ensure that a packet has not been modified 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 5

Advantages of IPSec • IPSec exists at the network layer of the TCP/IP architecture so most applications are unaware of it • IPSec is a valuable addition to a network when data integrity or confidentiality are required • IPSec is widely used by many vendors • It is a standards protocol 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 6

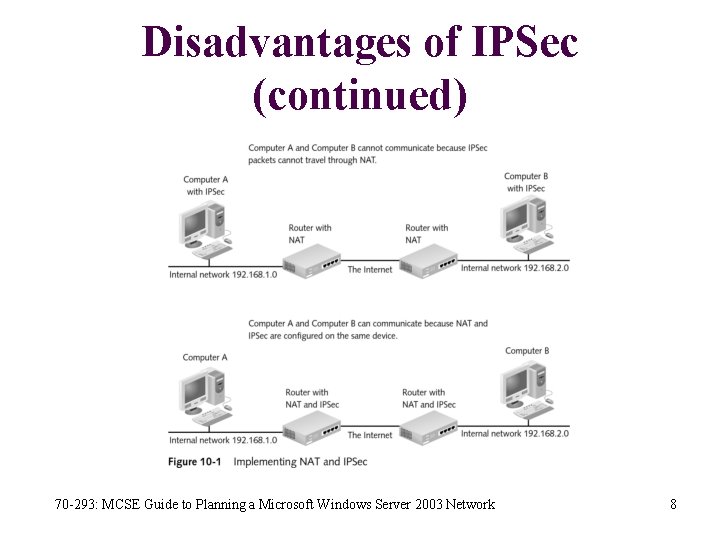
Disadvantages of IPSec • Pre-Windows 2000 operating systems from Microsoft do not support the IPSec • IPSec can significantly slow network communication • Only latest versions of IPSec can be routed through NAT, which is a serious limitation for remote users • IPSec adds complexity to a network 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 7

Disadvantages of IPSec (continued) 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 8

IPSec Modes • The modes of operation define whether communication is secured between two hosts or two networks, and which IPSec services are used • When implementing IPSec, you must choose tunnel mode or transport mode • Must choose AH mode or ESP mode 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 9

AH Mode • Use AH mode when you are concerned about packets being captured with a packet sniffer and replayed • Authentication Headers (AH) mode enforces authentication of the two IPSec clients and includes a digital signature on each packet • Authenticates the two endpoints and adds a checksum • Checksum guarantees that the packet is not modified in transit, including the IP headers • AH mode does not provide data confidentiality, however; the payload of the packet is unencrypted 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 10

ESP Mode • Most implementations of IPSec use ESP mode because data encryption is desired • The ESP mode authenticates the two endpoints, adds a checksum, and encrypts the data in the packet • Authentication performs the same function as in AH mode • Checksum guarantees that the packet was not modified in transit, excluding the IP headers • Encryption ensures that unintended recipients cannot read the data in the packet 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 11

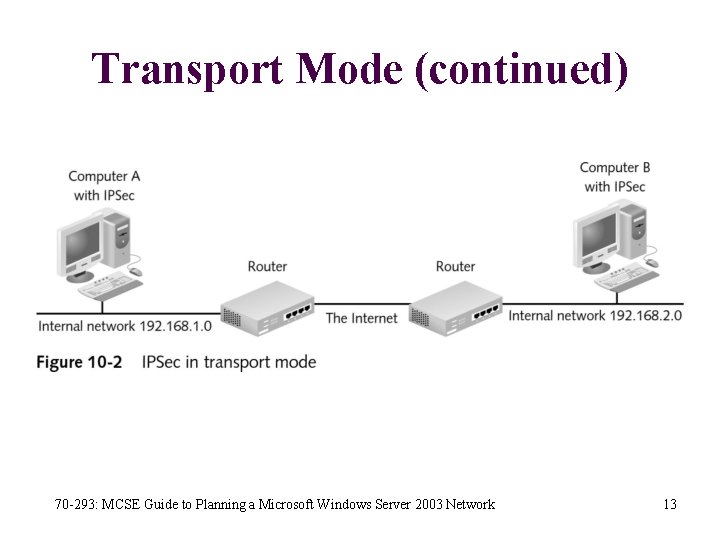
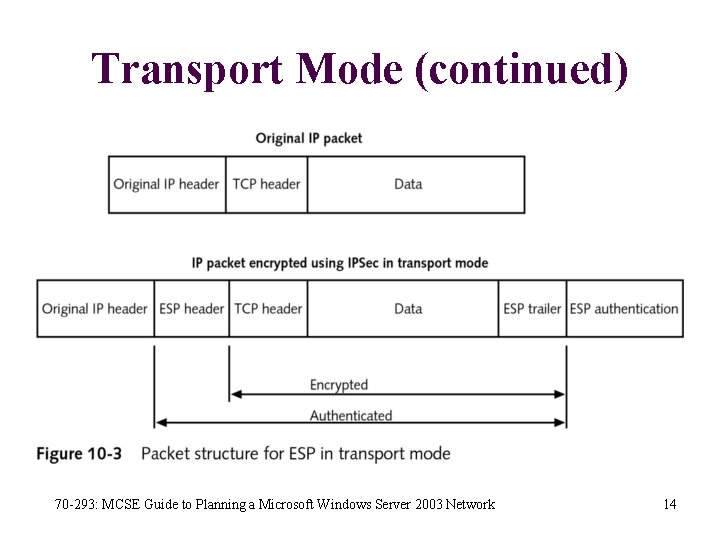
Transport Mode • IPSec in transport mode is used between two hosts • Both endpoints in the communication must support IPSec • This limits the implementation of IPSec because many devices, such as printers, rarely offer IPSec support 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 12

Transport Mode (continued) 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 13

Transport Mode (continued) 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 14

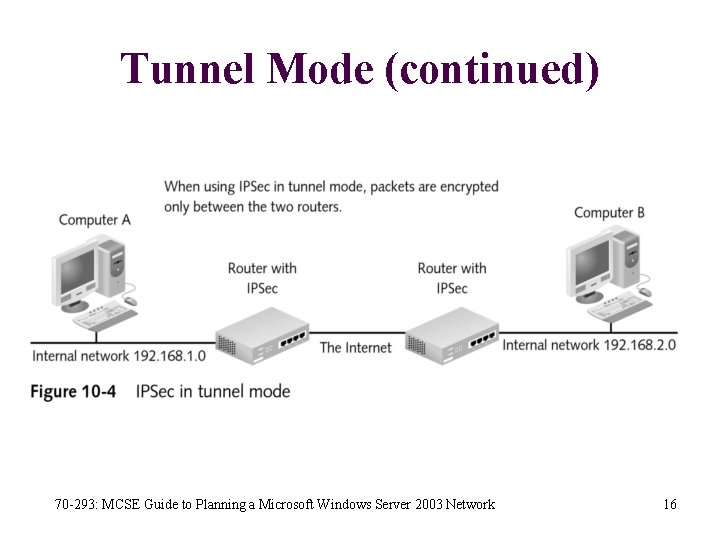
Tunnel Mode • IPSec in tunnel mode is used between two routers • The two hosts communicating through the routers do not need to support IPSec • Authentication takes place between the two routers when using IPSec in tunnel mode • Less secure because a hacker could place an unauthorized computer on a trusted network 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 15

Tunnel Mode (continued) 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 16

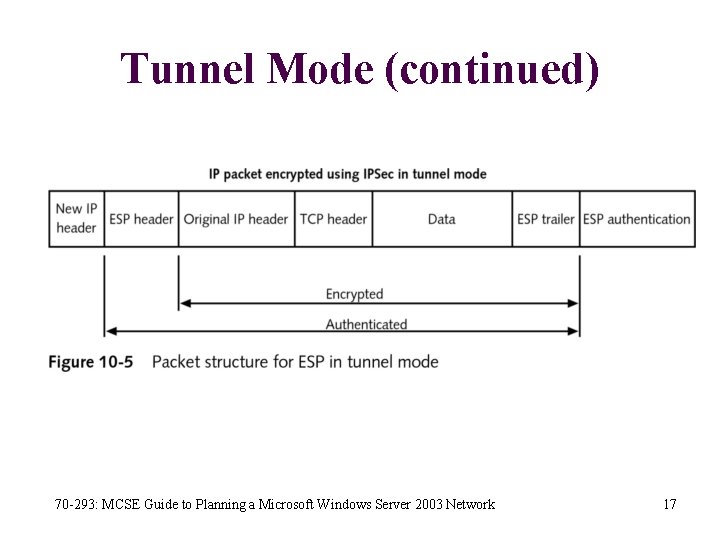
Tunnel Mode (continued) 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 17

IPSec Authentication • Endpoints of an IPSec are authenticated • Internet Key Exchange is the process used by two IPSec computers or routers to negotiate the following security parameters • • • Method of authentication AH or ESP mode Transport or tunnel mode Encryption and hashing algorithms Parameters for key exchange 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 18

IPSec Authentication (continued) • Security association (SA): when security parameters have been agreed upon • Three methods Windows Server 2003 uses to authenticate IPSec connections: • Preshared key • Certificates • Kerberos 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 19

Preshared Key • A preshared key is a combination of characters entered at each endpoint of the IPSec connection • Authentication is based on both endpoints knowing the same secret • The major advantage is simplicity • The major disadvantage is the movement of the preshared key when configuring the two devices 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 20

Certificates • Certificates may be presented for authentication • If the two certificates are part of the same hierarchy, each IPSec device accepts the certificate of the other • The main disadvantage of using third-party certificates is cost 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 21

Kerberos • Kerberos is the authentication system used by Windows 2000/XP/Server 2003 for access to network resources • Seamless integration with domain security • Not a commonly supported authentication system for IPSec on non-Microsoft products such as routers • Not appropriate for Windows computers that are not part of the Active Directory forest 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 22

Enabling IPSec • IPSec is enabled on Windows Server 2003 using IPSec policies • An IPSec policy must be in place to use IPSec • The three policies installed by default • Server (Request Security) • Client (Respond Only) • Secure Server (Require Security) 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 23

Assigning a Default IPSec Policy • • A single server can have many IPSec policies No policy is used until it is assigned One policy can be assigned at a time per machine The Local Security Policy snap-in can assign an IPSec policy on a single computer • Group Policy can assign an IPSec policy to a group of computers 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 24

Activity 10 -1: Assigning an IPSec Policy • The purpose of this activity is to assign an IPSec policy to enable encryption of data packet 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 25

Activity 10 -2: Verifying an IPSec Security Association • The purpose of this activity is to verify that the IPSec policy you have enabled is working 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 26

Creating Your Own IPSec Security Policy • An IPSec rule controls how IPSec is implemented and each rule is composed of: • • • An IP filter list An IPSec filter action Authentication methods A tunnel endpoint A connection type • An IP filter list is a list of protocols that will be affected by the rule 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 27

Creating Your Own IPSec Security Policy (continued) • An IPSec filter action is what will be done to the protocols defined in the filter list • Authentication methods are the protocols that can be used for authentication if IPSec is rule-based • The tunnel endpoint is the remote host IPSec is being performed with when tunnel mode is used • The connection type defines the type of connections to which this rule applies 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 28

Activity 10 -3: Creating an IPSec Policy • The purpose of this activity is to create a new IPSec policy that is more flexible than the default policies 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 29

Adding and Creating Rules • After creating an IPSec policy, edit it to add rules that define how different types of IP traffic are handled • After selecting an IP filter list, select an action to be performed on the packets that match the IP filter list • The three filter actions that exist by default are • Permit • Request security • Require security 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 30

Activity 10 -4: Creating a New IPSec Filter Rule • The purpose of this activity is to add a new IPSec filter rule that allows ICMP traffic to pass through unmodified 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 31

IPSec Filter Lists • When a new IP filter list is created • Give it a name • Have the option of giving it a description • Add IP filters that make up the list and specify the traffic to which this list applies 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 32

Activity 10 -5: Creating an IPSec Filter List • The purpose of this activity is to create a new IPSec filter list for all FTP traffic 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 33

Filter Actions • Filter actions define what is done to traffic that matches an IP filter list: • Permit • Request Security (Optional) • Require Security • Filter actions define a number of security parameters, including the type of encryption • In highly secure situations, you may want to modify these or create your own 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 34

Cryptography Algorithms • Two algorithms for AH and ESP data integrity • Secure Hash Algorithm (SHA 1) • Message Digest 5 (MD 5) • Two algorithms for ESP data encryption • Data encryption standard (DES) • Triple data encryption standard (3 DES) 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 35

Activity 10 -6: Creating a Filter Action • The purpose of this activity is to create a new filter action that enforces encryption 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 36

Activity 10 -7: Adding a Customized Filter List and Filter Action • The purpose of this activity is to edit your FTP filter and add a rule using the customized filter list and filter action you have created 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 37

Troubleshooting IPSec • IPSec troubleshooting deals with • General network issues • IPSec-specific configuration settings • Group policy settings 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 38

Troubleshooting IPSec (continued) • Most common IPSec troubleshooting tools/utilities • • Ping IPSec Security Monitor Event Viewer Resultant Set of Policy Netsh Oakley logs Network Monitor 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 39

Ping • Tests network connectivity between two hosts • The default IPSec policies permit ICMP packets and do not interfere with ping • Does not test IPSec specifically, but can confirm that two hosts can communicate • If they cannot communicate, they are not able to create an IPSec SA 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 40

IPSec Security Monitor • MMC snap-in that allows you to view the status of IPSec SAs • Can confirm that an SA was negotiated between two hosts • Can be used to view the configuration of the IPSec policy that is applied 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 41

Event Viewer • Event Viewer can be used to view the events that the IPSec Policy Agent writes to the event log • Events show the configuration settings that IPSec is using and events generated during the creation of SAs • Events are only written to the log if the Audit logon events option is enabled in the local security policy or Group Policy 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 42

Resultant Set of Policy Snap-in • If you try to distribute and apply IPSec policies through Group Policy, and they are not functioning as you expect, you can use the Resultant Set of Policy (RSo. P) snap-in • Allows you to • View which policies apply • Simulate the application of new policies to test their results 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 43

Netsh • The Netsh utility allows you to configure networkrelated settings: • • Bridging DHCP Diagnostics IP configuration remote access Routing WINS Remote procedure calls 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 44

Netsh (continued) • IPSec configuration can also be modified using Netsh • Some IPSec management tasks that can be performed with Netsh: • Viewing policies • Adding policies • Deleting policies 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 45

Oakley Logs • Oakley logs track the establishment of SAs • This logging is not enabled by default 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 46

Network Monitor • Network Monitor can be used to view packets that are traveling on the network and to identify IPSec traffic • Cannot view encrypted information inside an IPSec packet • Useful for determining whether packets are being properly transmitted between computers • Not useful for troubleshooting application level problems if the traffic is encrypted 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 47

Activity 10 -8: Disabling IPSec • The purpose of this activity is to disable IPSec policies that have been applied 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 48

Summary • IPv 4 has no built-in security mechanisms and uses IPSec to make communication secure • IPSec AH mode does not perform data encryption, but can authenticate and guarantee data integrity • IPSec ESP mode can perform data encryption, authentication, and guarantees data integrity for the data portion of the packet, but not the IP headers 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 49

Summary (continued) • Transport mode is used between two hosts • Tunnel mode is used between two routers • The Windows Server 2003 implementation can perform authentication using a preshared key, certificates, or Kerberos • IPSec policies contain rules that control • Authentication • Which traffic is affected and what is done to the affected traffic • Type of connections affected • Whether this computer is a tunnel endpoint 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 50

Summary (continued) • Filter actions define what is done to traffic that matches an IP filter list • SHA 1 and MD 5 are used for AH and ESP data integrity • DES and 3 DES are used for ESP data encryption • IPSec troubleshooting covers general network issues, IPSec-specific configuration settings, and group policy settings 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 51