70 293 MCSE Guide to Planning a Microsoft





























- Slides: 46

70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network, Enhanced Chapter 13: Planning Server and Network Security 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network

Objectives • • • Describe three types of security Plan security configurations for server roles Plan network protocol security Plan wireless network security Define the default security settings used by Windows Server 2003 • Plan a secure baseline for client computers and servers • Create a plan for software updates • Ensure secure administrative access 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 2

Types of Security • Three commonly used categories are: • Physical security • Network security • Data security 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 3

Physical Security • Physical security is controlling physical access to the computing devices on your network • Who has a key to the server room? • Prevents users and hackers from physically accessing network resources that they have no legitimate need to touch • After physical security is in place, software-based security is more effective 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 4

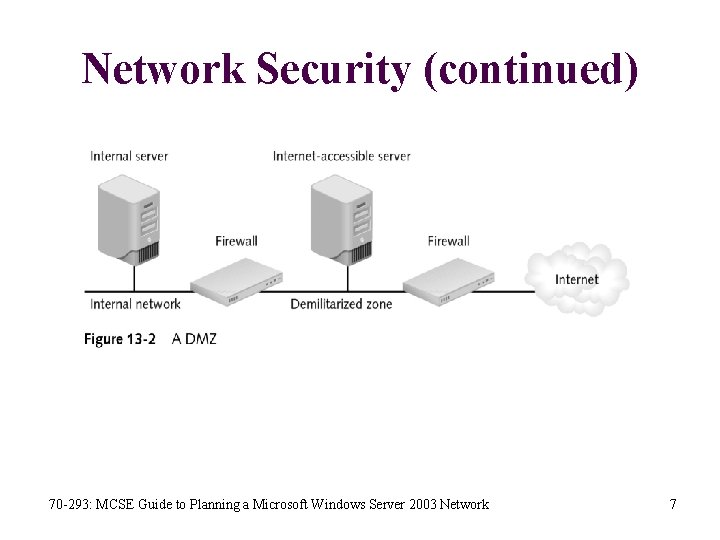
Network Security • Network security refers to accessing network-based resources through a computer network • Tools available for enforcing network security are: Authentication, IPSec and Firewalls • Authentication verifies the identity of users before giving them access to resources • IPSec encrypts data packets in transit on the network • Firewalls control data movement based on IP addresses and port numbers • For enhanced security, most organizations use a demilitarized zone (DMZ) 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 5

Network Security (continued) 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 6

Network Security (continued) 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 7

Data Security • Data security: mechanisms to ensure only authorized users access sensitive data • Tools for enforcing data security include: • NTFS permissions: used to control access to files and folders stored on network servers • Share permissions: used to control access to a particular network share • Auditing: allows you to track which users have performed, or attempted to perform, certain actions • EFS: encrypts files that are stored on NTFS partitions 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 8

Encrypting File System • EFS (encrypting file system) encrypts files that are stored on NTFS partitions • When files are stored encrypted, only the user who encrypted them, other designated users, or a designated recovery agent can decrypt and read them • Certificates used by EFS can be created automatically, through an internal CA or a third party CA 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 9

Activity 13 -1: Using EFS to Protect Files • The purpose of this activity is to use EFS to protect files 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 10

Planning Security Configuration for Server Roles • General rules for server security are: • Disable unnecessary services • Limit access to the minimum required for users to perform their jobs • Use separate administrator accounts for different staff • Allow packets to necessary TCP and UDP ports only 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 11

Securing Domain Controllers • Some ways to secure domain controllers are: • • • Place domain controller behind firewall If VPN is being used, place the VPN in a DMZ Use RADIUS Net. BIOS ports should be blocked by a firewall Net. BIOS can be disabled on the network connection that is connected to the Internet 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 12

Securing Web Servers • Some ways to secure web servers are: • Web servers should be in a DMZ • Web sites that authenticate users or collect sensitive information should run on TCP port 443 using SSL • install the operating system, IIS, and the Web site data on separate hard drive partitions • remove any demonstration scripts that installed by default on the Web server • disable the ability to run scripts by disabling ASP processing and the processing of all other script types 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 13

Activity 13 -2: Disabling Script Processing in IIS • The purpose of this activity is to disable processing of scripts in IIS 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 14

Securing Database Servers • When securing database servers: • If concerned with protecting the data while it is in transit on the network between the client and the server, use IPSec • If database is used as part of a Web-based application, it is quite common to place the Web server in the DMZ and the SQL server on the internal, private network • A database that holds sensitive information should never be on the same server as the Web site • If the database runs on a separate server, then the hacker must still find the database 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 15

Securing Mail Servers • The only protection you can give a mail server is a firewall • Mail servers that communicate with the Internet should be placed in the DMZ • The best way for clients to access e-mail is from a server on the internal network • Configure a second e-mail server on the internal network that forwards all mail to the mail server in the DMZ 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 16

Securing Mail Servers (continued) 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 17

Planning Network Protocol Security • A VPN connection can be used to secure IPX, Apple. Talk, and TCP/IP network traffic • If TCP/IP is used, traffic can also be secured with IPSec or with SSL 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 18

Using VPNs to Secure Network Traffic • A VPN is used to secure network traffic for remote users • All network traffic between the client computer and the VPN server is encrypted • A VPN can ensure that user access to confidential company information is not monitored by an ISP or hackers • VPNs can also be used internally on the network to protect network traffic to certain areas of the network 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 19

Using IPSec to Secure Network Traffic • IPSec is ideal for securing network traffic because: • It is very flexible to configure because rules can be configured to protect only certain traffic • In addition to performing encryption, IPSec authenticates both computers in the conversation to prevent imposters • Applications do not have to be aware of IPSec to use it any IP-based application can use it • The major drawback to IPSec is that it does not move through NAT very well 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 20

Securing Web-based Applications • Key points concerning SSL (Secure Sockets Layer): • It is often used to secure Web-based applications • Requires that a certificate be installed on the server to which it is being connected • It is a well-recognized, standard protocol • It is not platform specific in any way 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 21

Planning Wireless Network Security • Concepts regarding wireless security include: • • • Wired Equivalent Protocol Authorized MAC addresses Using VPNs to secure wireless access 802. 1 X Microsoft-specific mechanisms for configuring wireless networks 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 22

Wired Equivalent Protocol • Wired Equivalent Privacy (WEP) is a protocol built into the 802. 11 standards for wireless connectivity • WEP governs how data can be encrypted while in transit on the wireless network • WEP is seriously flawed when dealing with motivated hackers • Wi. Fi Protected Access (WPA), is replacing WEP and fixes most of its flaws • WPA will be a standard in all newly certified wireless equipment as of January 2004 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 23

Authorized MAC Addresses • If you try to communicate with the AP using a wireless card with a MAC address that is not on the list, the AP ignores you • This prevents access to resources on your network, but is very awkward to implement • Each AP must be configured with the MAC address of each wireless network card • Packet sniffers can view MAC addresses and exploit them 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 24

Using VPNs to Secure Wireless Access • One easy way to secure a wireless network is to require VPN authentication before allowing access to the main network • All packets that can be viewed by hackers with wireless connections are encrypted by the VPN 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 25

The 802. 1 X Protocol • The protocol 802. 1 X is an authentication protocol defined by the IEEE to authenticate wireless users 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 26

The 802. 1 X Protocol (continued) 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 27

Configuring Wireless Networks • Many wireless configuration settings are managed by the OS, and can be managed using Group Policy • In a group policy, you can define Wireless Network (802. 11) policies where you can configure: • The type of wireless networks to access • Whether Windows should be used to configure the wireless networks for a client • Whether to connect to non preferred networks 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 28

Activity 13 -3: Creating a Policy for Wireless Workstations • The purpose of this activity is to create a policy to configure wireless workstations 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 29

Default Security Settings • Windows Server 2003 features: • It is more secure than Windows Server 2000 • Only the Administrators group is given Full Control to the file system • A minimum of services is installed 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 30

Default Security Settings (continued) • Windows Server 2003 features (continued): • IIS is not installed by default • If IIS is installed after the server installation is complete, script processing must be enabled • Default security settings for Windows 2003 are configured during installation by applying a security template • A security template is a group of security settings that can be applied to server or client computers 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 31

Activity 13 -4: Viewing Default Security Settings • The purpose of this activity is to view the default security settings in Setup security. inf 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 32

Configuring Client Computers • Client computers should be divided into categories where specific configuration options and a security template can be developed • When defining a security template, start by copying one of the predefined templates • The Security Configuration and Analysis snap-in can analyze and configure client computers from a GUI 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 33

Configuring Servers • Servers should be categorized and grouped to assist in applying security settings • Servers are more likely to hold sensitive data than workstations, their settings are likely to be more restrictive for: • • • Password policies Account lockout policy Users performing local logons Auditing, limiting services Restricting file Registry permissions 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 34

Activity 13 -5: Analyzing Security • The purpose of this activity is to compare the default security level of your server to the hisecws. inf template 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 35

Software Updates • Systems must be fully patched because viruses take advantage of known flaws in operating systems and applications for which there are patches available • To help administrators keep systems patched, Microsoft has released a number of tools: • • • Windows Update Automatic Updates Software Update Services Microsoft Baseline Security Analyzer Hfnetchk 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 36

Windows Update • Windows Update is a Web site that administrators and users can visit to find out which updates are available for their systems • Windows Update • Automatically checks for the files that are needed • Downloads them • Installs them 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 37

Automatic Updates • Automatic Updates is a service that runs on Windows clients and servers that makes the process of downloading and installing hotfixes automatic • Automatic Updates is a significant improvement over Windows Update because it is automatic and configurable • This takes a significant load off of administrator • It is not very efficient because all downloads are from the Internet 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 38

Activity 13 -6: Configuring Automatic Updates • The purpose of this activity is to configure Automatic Updates to download and install patches automatically 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 39

Software Update Services (SUS) • SUS is a service available for Windows 2000 and Windows Server 2003 • Automatically downloads the latest hotfixes and service packs from the Windows Update Web site • Client computers on your network then can download the hotfixes and service packs from a local server on the network instead of the Internet • Internet traffic is reduced 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 40

Microsoft Baseline Security Analyzer • The Microsoft Baseline Security Analyzer (MBSA) is a tool that verifies security updates on a wide variety of Microsoft operating systems and applications • MBSA can scan a single machine or an entire group of computers on the network 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 41

Hfnetchk • Hfnetchk is an older command-line utility for verifying patch levels on Windows clients and servers • It is no longer offered by Microsoft as a stand-alone utility • The functionality of Hfnetchk is now only available in MBSA 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 42

Securing Administrative Access • Administrators should maintain two accounts: • One for day-to-day work with limited permission (like an average user) • One with elevated privileges and permissions that are required for administration of the network • Most network administrators find it cumbersome to log on and off of the network as they switch between tasks; Windows Server 2003 allows administrators to run individual applications as a different user 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 43

Summary • Three types of security are: physical security, network security and data security • EFS (encrypting file system) encrypts files that are stored on NTFS partitions • Securing all servers includes the following: • Disabling unnecessary services • Limiting access to the minimum required for users to perform their jobs • Using separate administrator accounts for different staff, and allow packets to necessary TCP and UDP ports only 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 44

Summary (continued) • Domain controllers should not be exposed to traffic from the Internet and should not be located in a DMZ • Web servers that are accessible from the Internet should be located in a DMZ • Database servers should be on the internal network • Mail servers must be accessible from the Internet and should be located in a DMZ • A VPN can be used to secure network traffic for IP, IPX, and Apple. Talk packets 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 45

Summary (continued) • Common standards for wireless networks are 802. 11 b and 802. 11 g • Default security settings for Windows Server 2003 are much more secure than Windows 2000 Server • Software updates can be managed using: • • Windows Update Automatic Updates SUS MBSA 70 -293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network 46