235034 Security in Computer Systems and Networks Cryptography
















































- Slides: 78

235034 Security in Computer Systems and Networks Cryptography & Steganography Lec. Sanchai Yeewiyom School of Information and Communication Technology University of Phayao


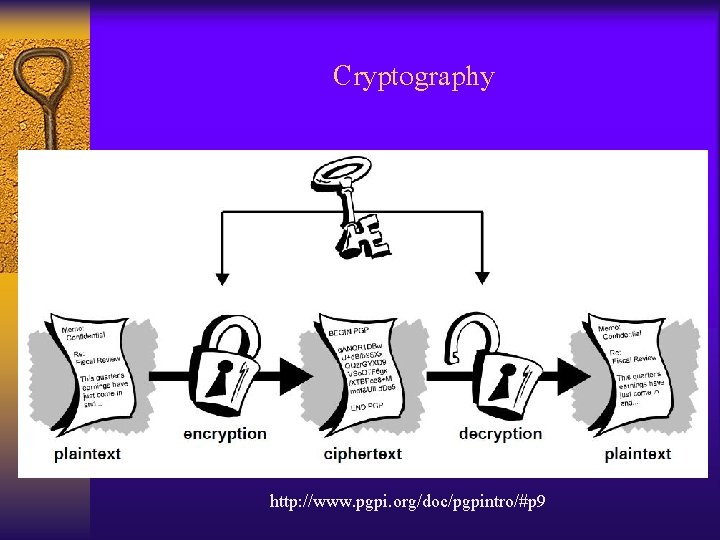
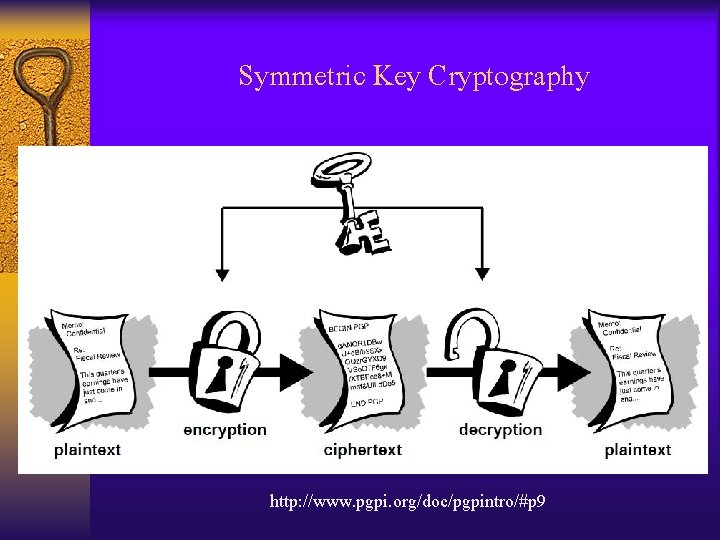
Cryptography http: //www. pgpi. org/doc/pgpintro/#p 9

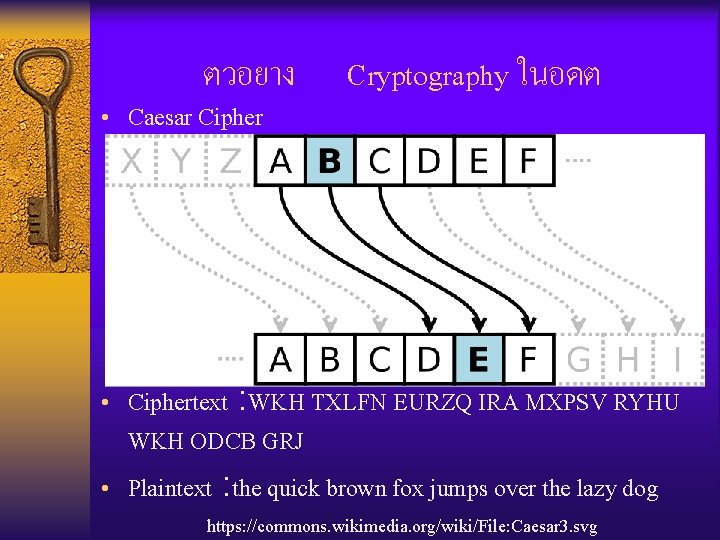
ตวอยาง • Caesar Cipher Cryptography ในอดต • Ciphertext : WKH TXLFN EURZQ IRA MXPSV RYHU WKH ODCB GRJ • Plaintext : the quick brown fox jumps over the lazy dog https: //commons. wikimedia. org/wiki/File: Caesar 3. svg

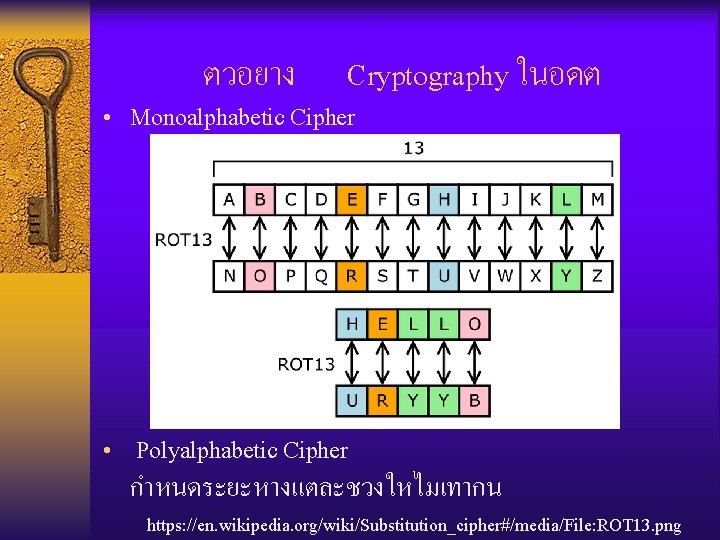
ตวอยาง Cryptography ในอดต • Monoalphabetic Cipher • Polyalphabetic Cipher กำหนดระยะหางแตละชวงใหไมเทากน https: //en. wikipedia. org/wiki/Substitution_cipher#/media/File: ROT 13. png


Pad http: //modes. io/hacktivism-codes/

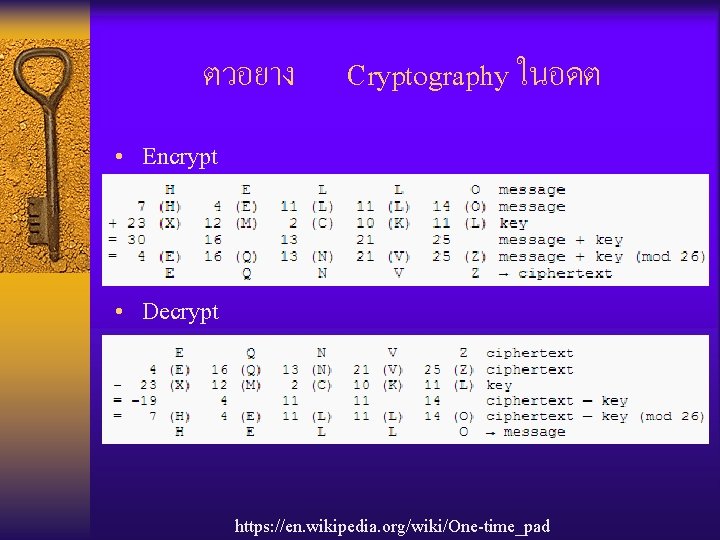
ตวอยาง Cryptography ในอดต • Encrypt • Decrypt https: //en. wikipedia. org/wiki/One-time_pad

ตวอยาง Cryptography

Cryptography ปจจบนสามารถแบงการเขารหสขอมลเปน 3 ประเภท • Symmetric Key Cryptography )Secret Key Cryptography( • Asymmetric Key Cryptography )Public Key Cryptography( • Hash Function


Symmetric Key Cryptography http: //www. pgpi. org/doc/pgpintro/#p 9

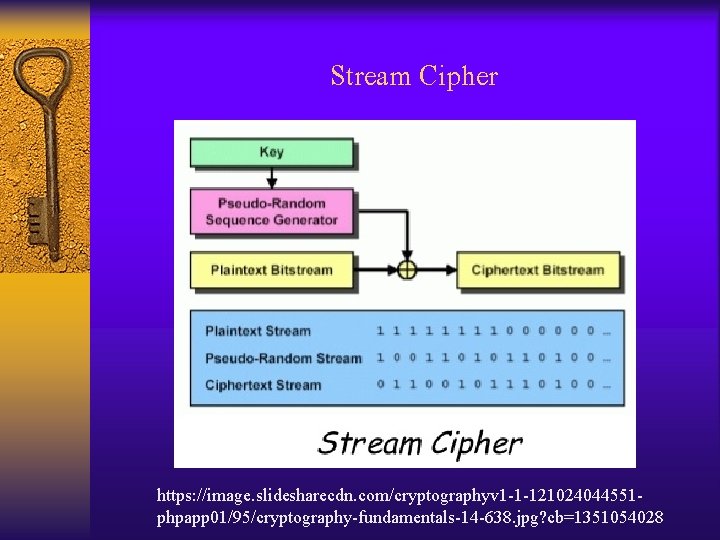
Symmetric Key Cryptography แบงเปน 2 ประเภท คอ • Stream Cipher • Block Cipher


Stream Cipher https: //image. slidesharecdn. com/cryptographyv 1 -1 -121024044551 phpapp 01/95/cryptography-fundamentals-14 -638. jpg? cb=1351054028



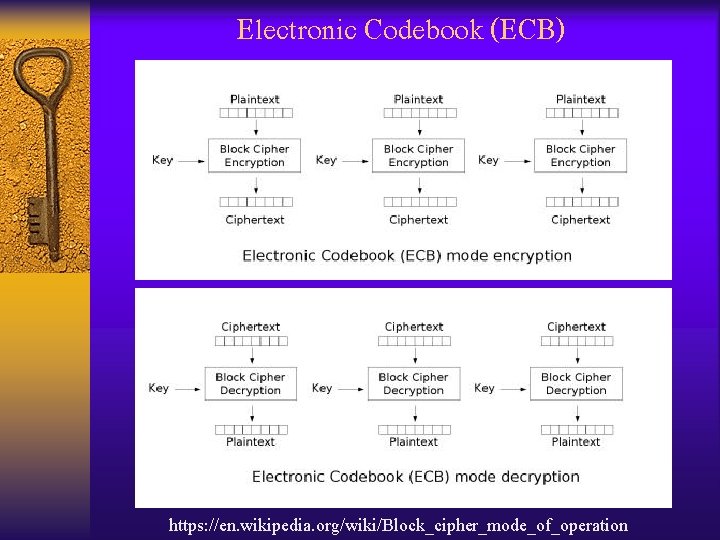
Electronic Codebook (ECB) https: //en. wikipedia. org/wiki/Block_cipher_mode_of_operation


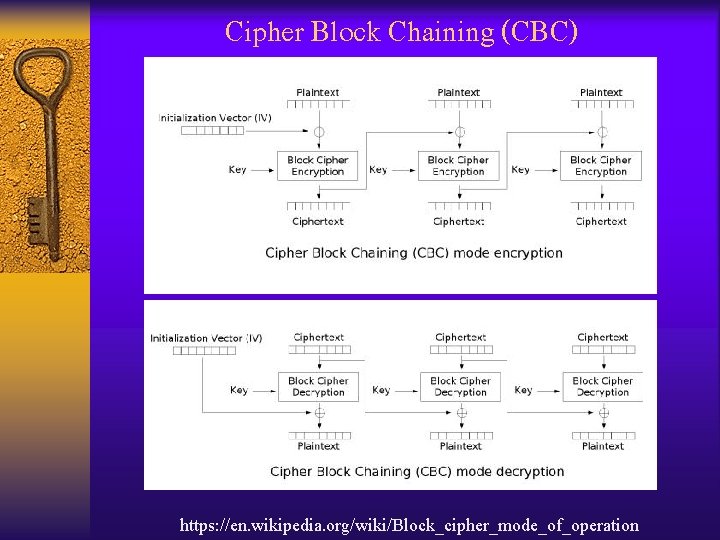
Cipher Block Chaining (CBC) https: //en. wikipedia. org/wiki/Block_cipher_mode_of_operation

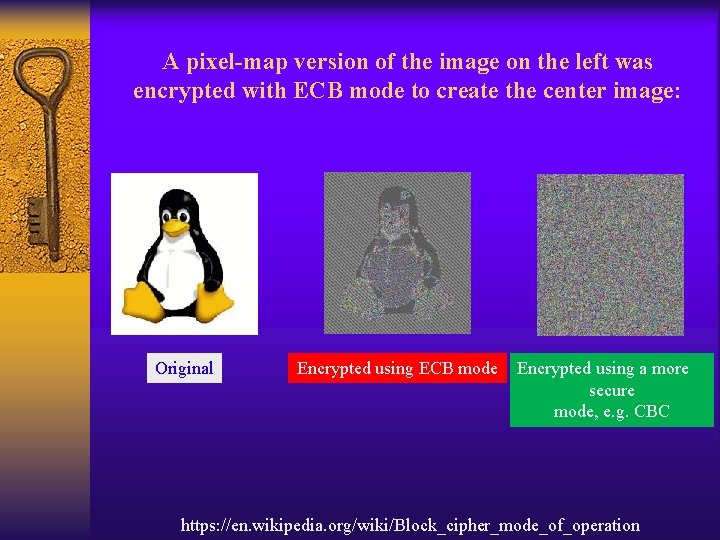
A pixel-map version of the image on the left was encrypted with ECB mode to create the center image: Original Encrypted using ECB mode Encrypted using a more secure mode, e. g. CBC https: //en. wikipedia. org/wiki/Block_cipher_mode_of_operation

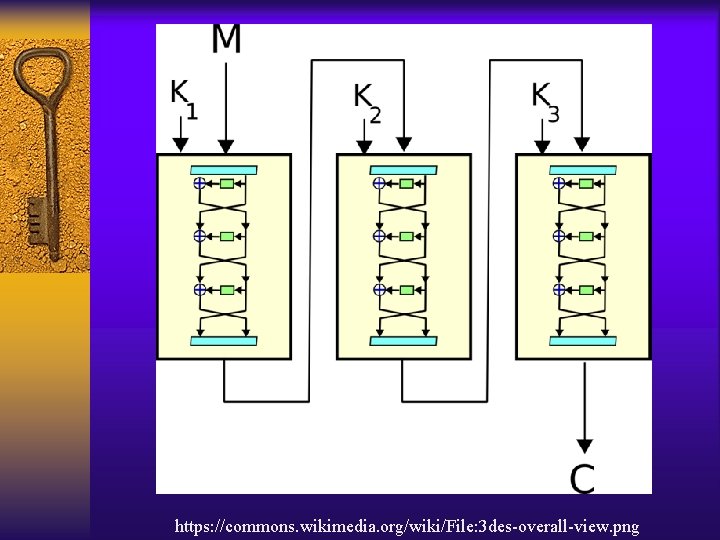
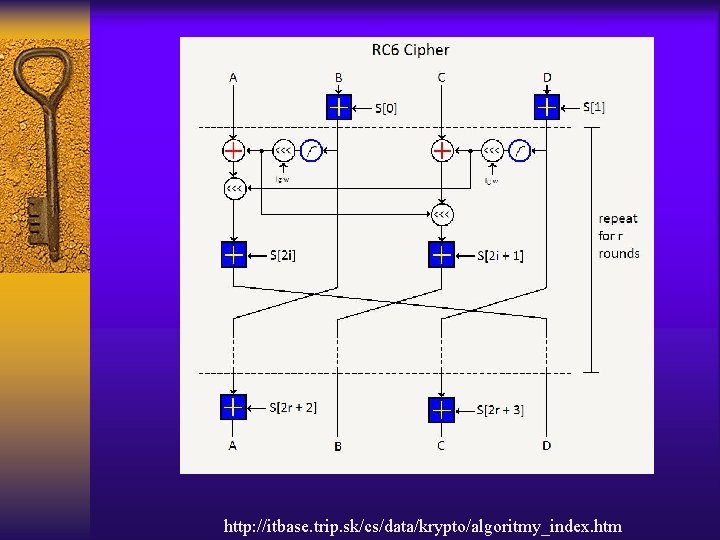
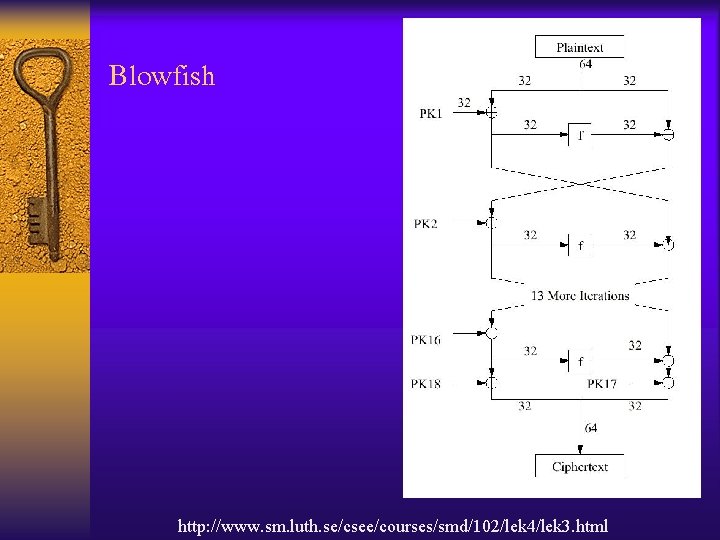
Symmetric Key Cryptography Example • • • Data Encryption Standard (DES) Triple-DES Advanced Encryption Standard (AES) Rivest Ciphers (RC) Blowfish


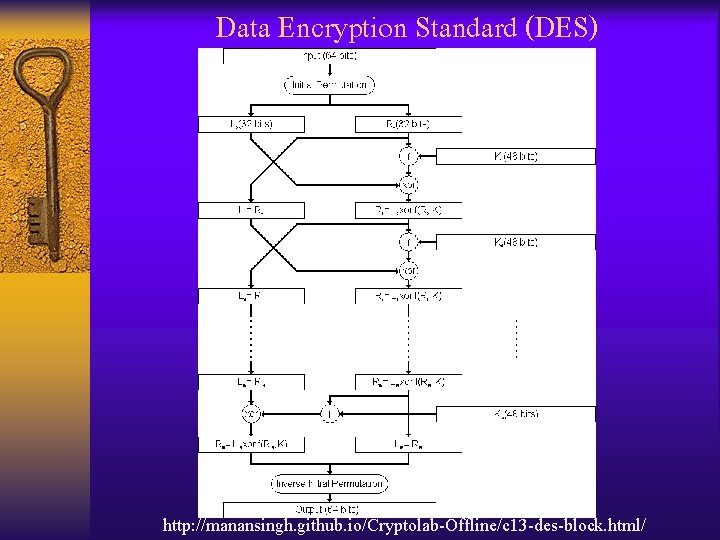
Data Encryption Standard (DES) http: //manansingh. github. io/Cryptolab-Offline/c 13 -des-block. html/




https: //commons. wikimedia. org/wiki/File: 3 des-overall-view. png


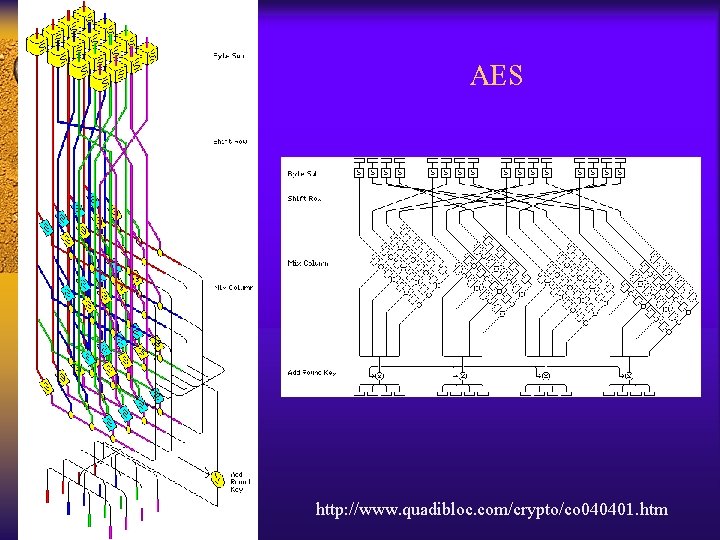
AES http: //www. quadibloc. com/crypto/co 040401. htm


Advanced Encryption Standard (AES) 3. Final Round (No Mix. Columns) • Sub. Bytes • Shift. Rows • Add. Round. Key



http: //itbase. trip. sk/cs/data/krypto/algoritmy_index. htm


Blowfish http: //www. sm. luth. se/csee/courses/smd/102/lek 4/lek 3. html


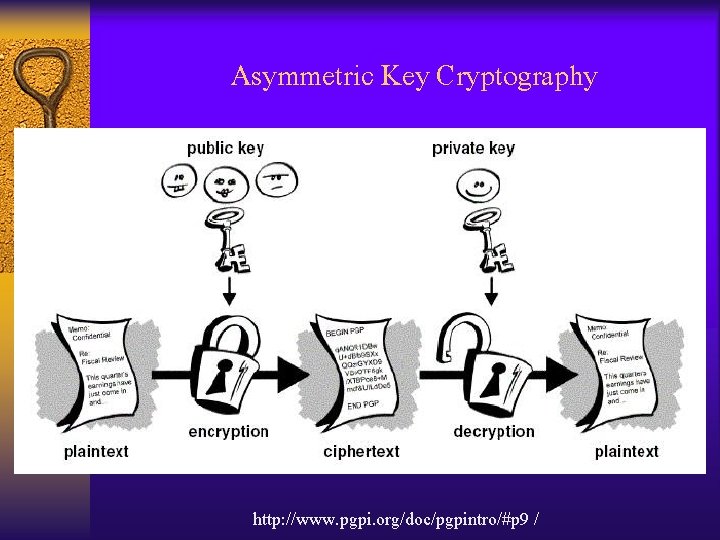
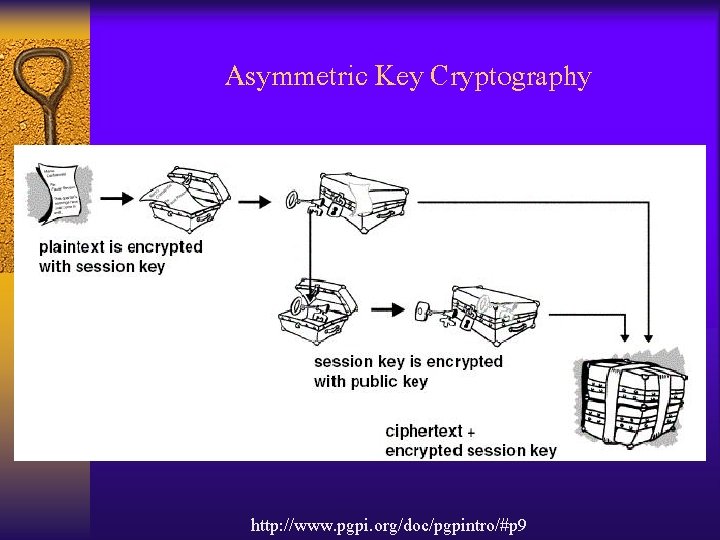
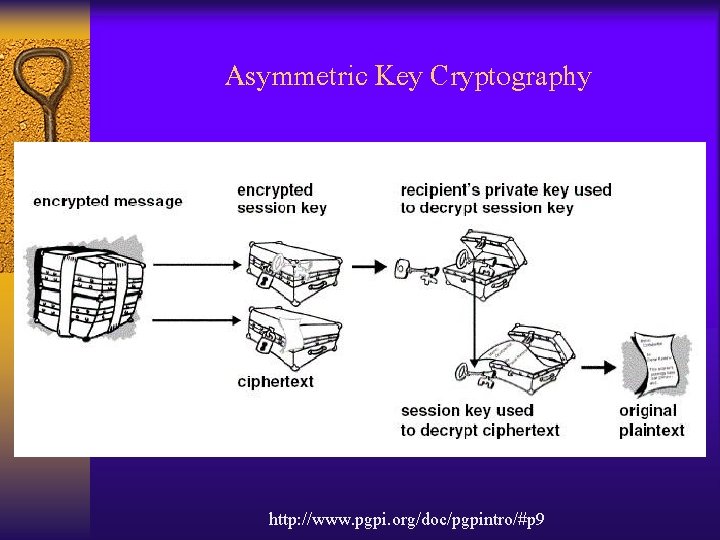
Asymmetric Key Cryptography http: //www. pgpi. org/doc/pgpintro/#p 9 /


Asymmetric Key Cryptography http: //www. pgpi. org/doc/pgpintro/#p 9


Asymmetric Key Cryptography http: //www. pgpi. org/doc/pgpintro/#p 9

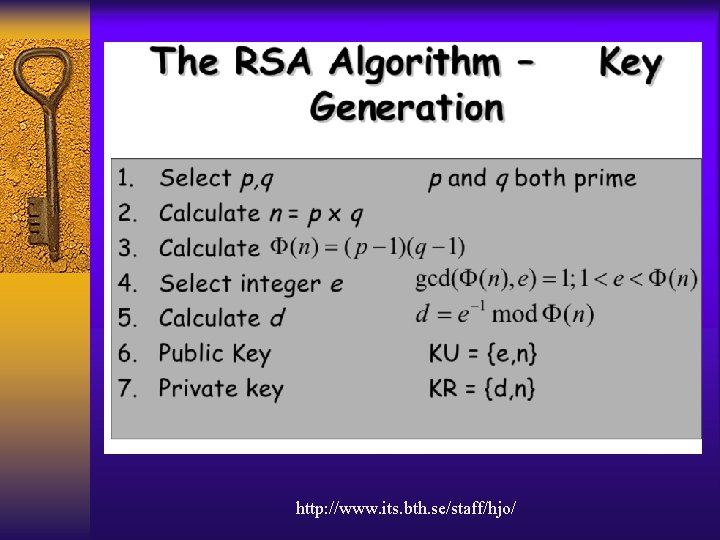
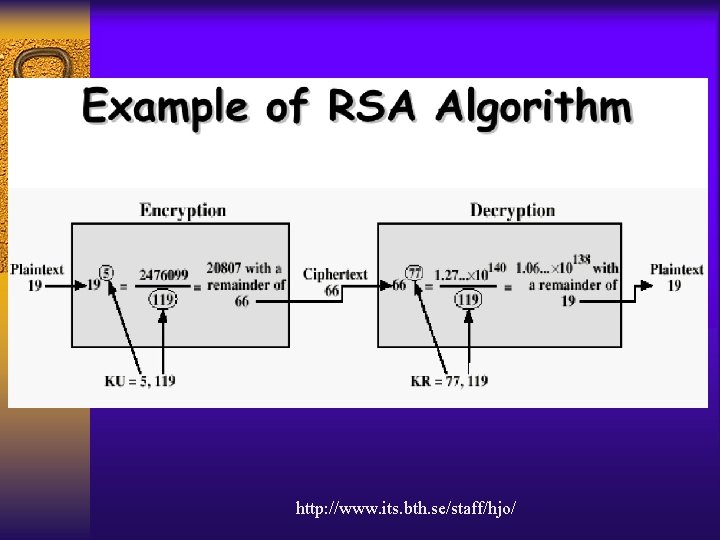
Asymmetric Key Cryptography Example • RSA • Digital Signature • Digital Certificate


http: //www. its. bth. se/staff/hjo/

http: //www. its. bth. se/staff/hjo/


Digital Signature (Authentication) http: //www. infosec. gov. hk/english/itpro/public_main. html

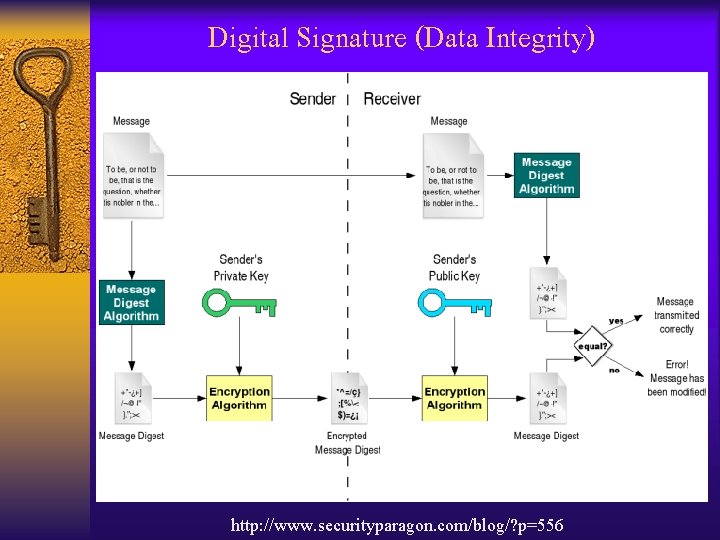
Digital Signature (Data Integrity) http: //www. securityparagon. com/blog/? p=556


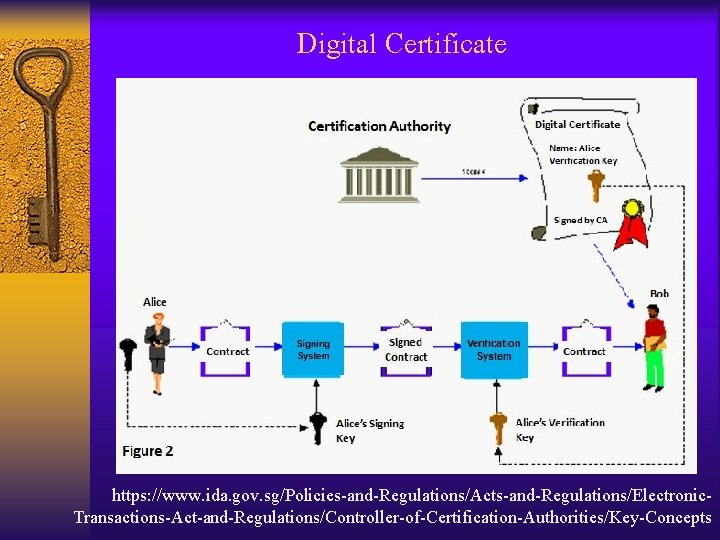
Digital Certificate https: //www. ida. gov. sg/Policies-and-Regulations/Acts-and-Regulations/Electronic. Transactions-Act-and-Regulations/Controller-of-Certification-Authorities/Key-Concepts


Digital Certificate


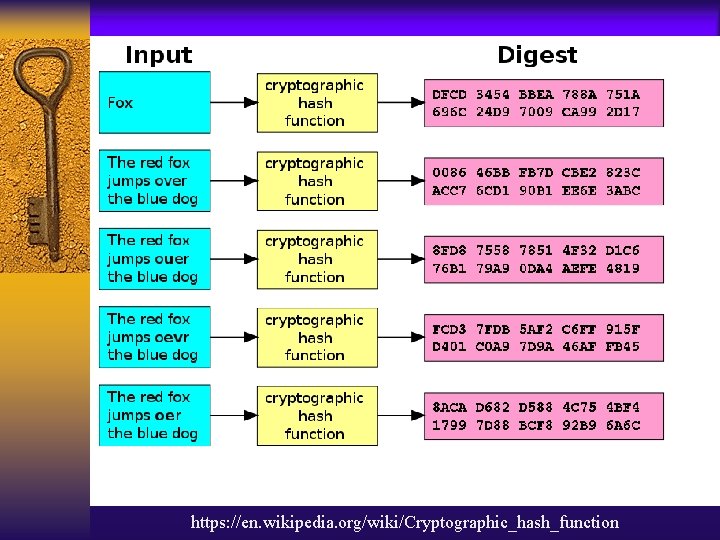
https: //en. wikipedia. org/wiki/Cryptographic_hash_function


Hash Function Example • Message Digest (MD( • Secure Hash Algorithm (SHA(


Message Digest (MD( • MD 2 • MD 4 • MD 5




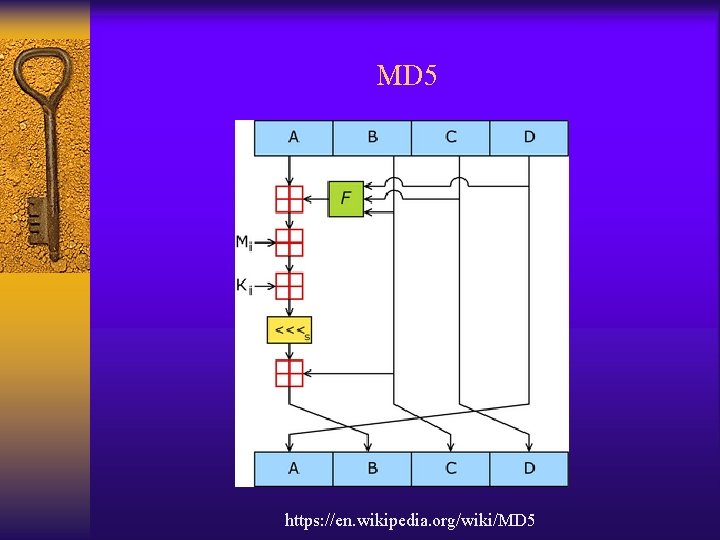
MD 5 https: //en. wikipedia. org/wiki/MD 5


Secure Hash Algorithm (SHA( • SHA-1 • SHA-256, SHA-384 และ SHA-512


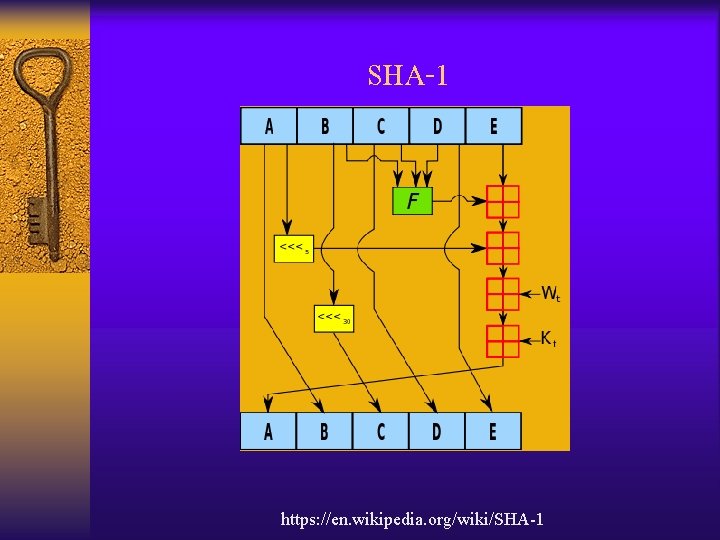
SHA-1 https: //en. wikipedia. org/wiki/SHA-1


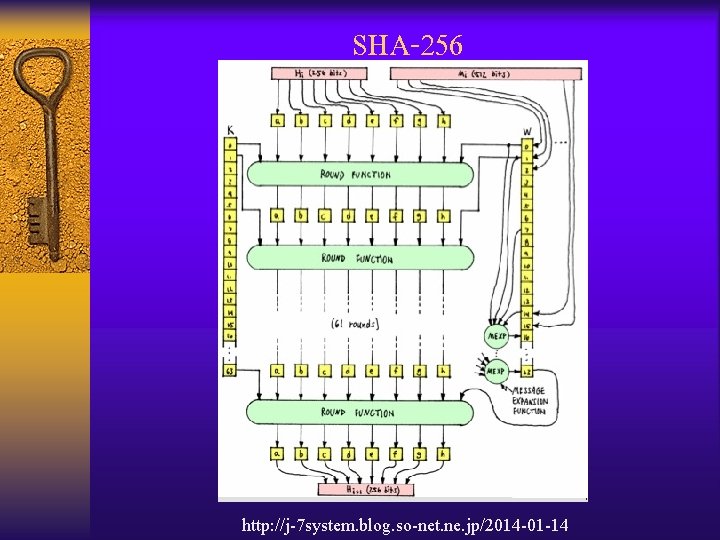
SHA-256 http: //j-7 system. blog. so-net. ne. jp/2014 -01 -14

Encryption Software • Best encryption software tools of 2020: Keep your data secure and private (Tech. Radar) • The Best Encryption Software for 2020 (PC Magazine)


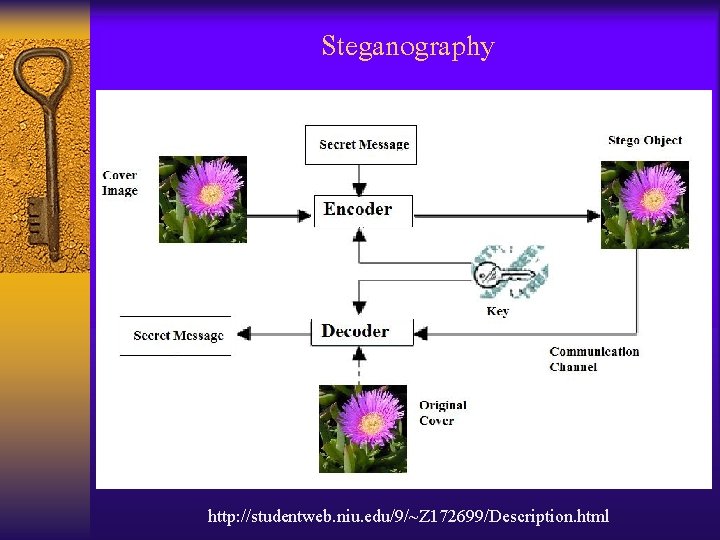
Steganography http: //studentweb. niu. edu/9/~Z 172699/Description. html

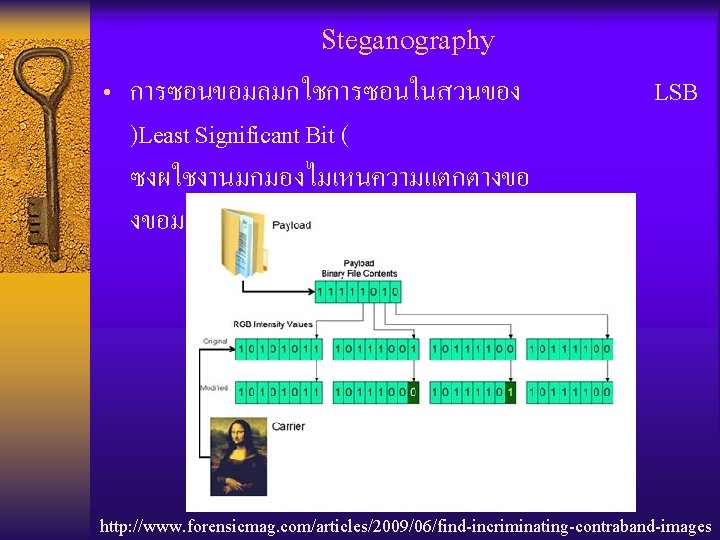
Steganography • การซอนขอมลมกใชการซอนในสวนของ LSB )Least Significant Bit ( ซงผใชงานมกมองไมเหนความแตกตางขอ งขอมลทเปลยนไป (Picture, Sound, etc. ) http: //www. forensicmag. com/articles/2009/06/find-incriminating-contraband-images

Steganography

Steganography • http: //www. mobilefish. com/services/steganography. php

• Exp. Steganography • Open. Puff 4. 00 (http: //embeddedsw. net/Open. Puff_Steganography_Home. html) • Quick. Stego (http: //quickcrypto. com/free-steganographysoftware. html( • MP 3 Stego (http//: www. petitcolas. net/fabien/steganography/mp 3 stego/index html) • Xiao Steganography (https: //download. cnet. com/Xiao. Steganography/3000 -2092_4 -10541494. html)

Steganography • การตรวจจบการซอนขอมล ใชเครองมอ เชน • Steg. Alyzer (https: //stegalyzeras. software. informer. com/3. 9/) • Steg. Detect (https: //stegdetect. apponic. com/) • XSteg. Secret (http: //en. pudn. com/Download/item/id/965028. html)