Taiwan Advanced Research and Education Network TWAREN Current















- Slides: 58

Taiwan Advanced Research and Education Network (TWAREN) Current status & Future Plan Dr. Te-Lung Liu Researcher National Center for High-Performance Computing tlliu@nchc. narl. org. tw

Outline TWAREN Network Overview Development and Research Technologies 2

TWAREN Network Overview Development and Research Technologies 3

N E R A TW n a d W i e a c T d n a n v a Ad search Re ucation Ed twork Ne 4

What is TWAREN A physical network serves multiple purposes and logical networks TANet, connects to commodity Internet TWAREN research network experiment, testbed, special research Provisioning services on multiple layers L 1 lightpaths L 2 VLAN L 3 IP has been successfully migrated from old backbone in Oct 2006 5

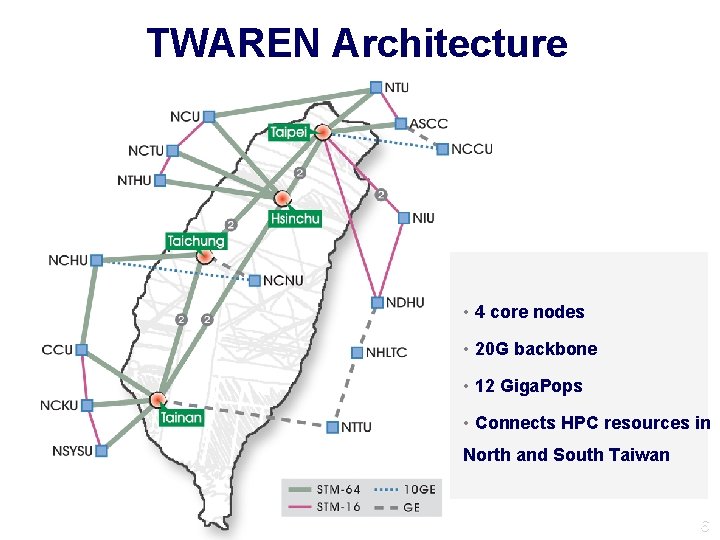
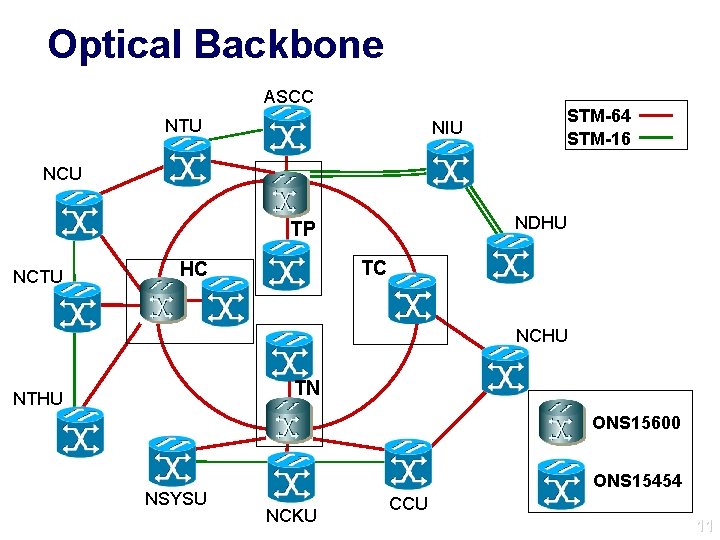
TWAREN Architecture • 4 core nodes • 20 G backbone • 12 Giga. Pops • Connects HPC resources in North and South Taiwan 6

Goals of TWAREN is part of “Challenge 2008”, a comprehensive sixyear national development plan formulated by the government Build a highly reliable, stable and flexible R&E network for academic and research community in TW Provide advanced network services to satisfy the needs of academia field in TW. Increase the International and domestic collaboration Future infrastructure drives today’s research agenda 7

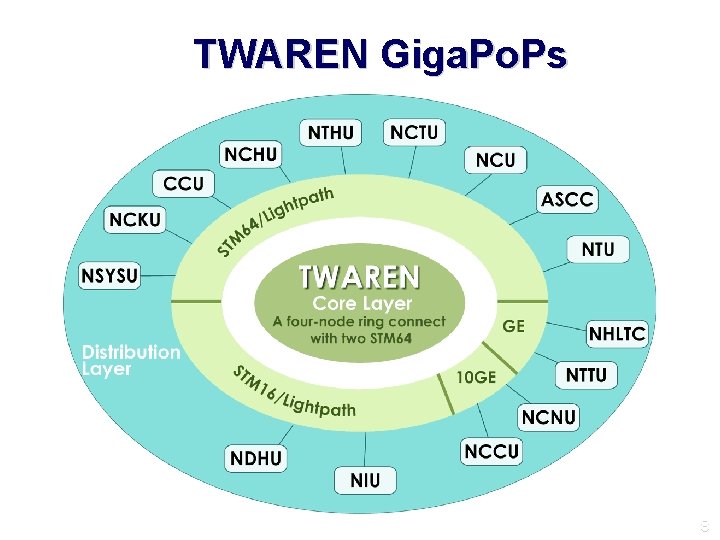
TWAREN Giga. Po. Ps 8

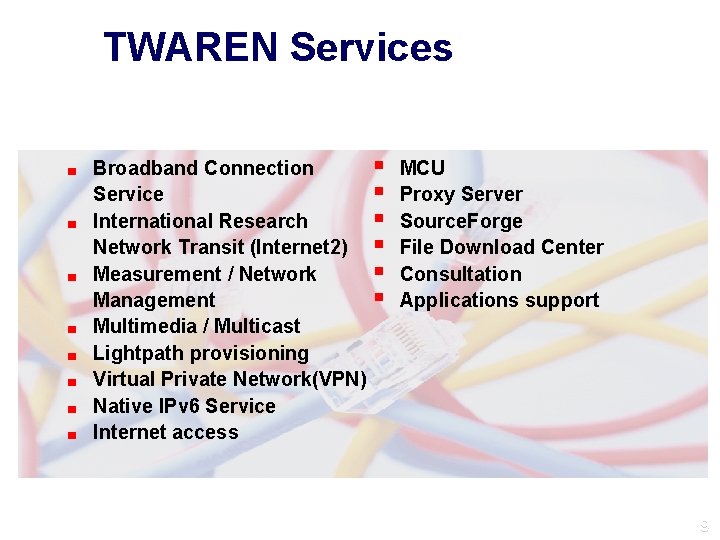
TWAREN Services ■ ■ ■ ■ Broadband Connection Service International Research Network Transit (Internet 2) Measurement / Network Management Multimedia / Multicast Lightpath provisioning Virtual Private Network(VPN) Native IPv 6 Service Internet access MCU Proxy Server Source. Forge File Download Center Consultation Applications support 9

TWAREN Achivements High reliability & availability (99. 9% 99. 99%) l fault tolerance l automatic protection if possible l automatic failure detection and locating Better performance: minimum number of routers between Giga. Po. Ps Flexible: can be easily and quickly to set up a logical network per user’s request People skills: Optical network OAM 10

Optical Backbone ASCC NTU STM-64 STM-16 NIU NCU NDHU TP NCTU TC HC NCHU TN NTHU ONS 15600 NSYSU ONS 15454 NCKU CCU 11

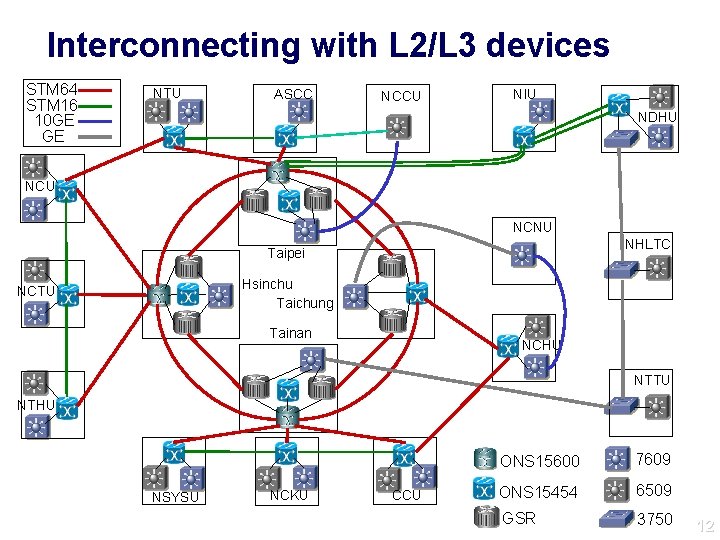
Interconnecting with L 2/L 3 devices STM 64 STM 16 10 GE GE NTU ASCC NCCU NIU NDHU NCNU NHLTC Taipei Hsinchu Taichung NCTU Tainan NCHU NTTU NTHU NSYSU NCKU CCU ONS 15600 7609 ONS 15454 6509 GSR 3750 12

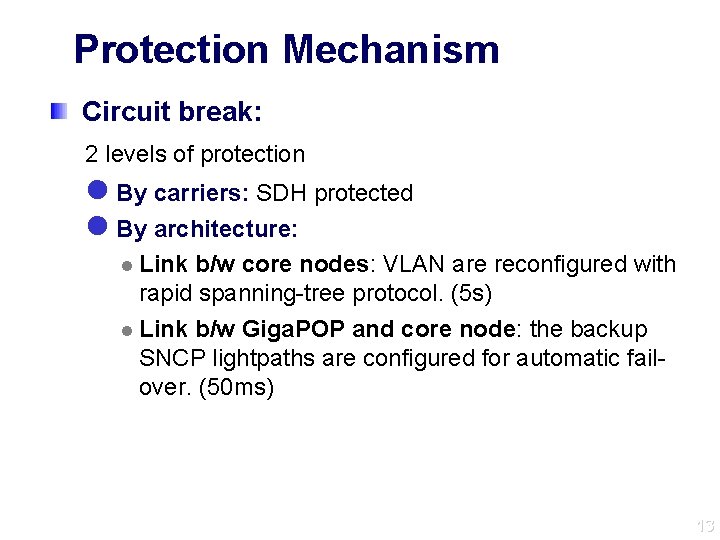
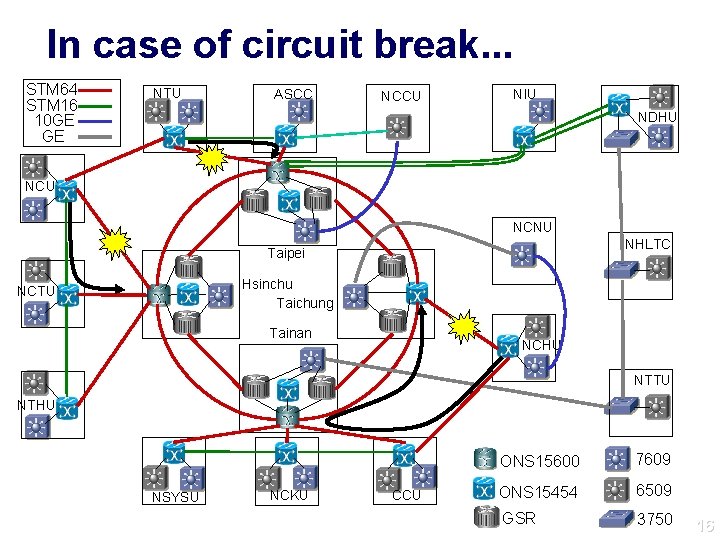
Protection Mechanism Circuit break: 2 levels of protection l By carriers: SDH protected l By architecture: l Link b/w core nodes: VLAN are reconfigured with rapid spanning-tree protocol. (5 s) l Link b/w Giga. POP and core node: the backup SNCP lightpaths are configured for automatic failover. (50 ms) 13

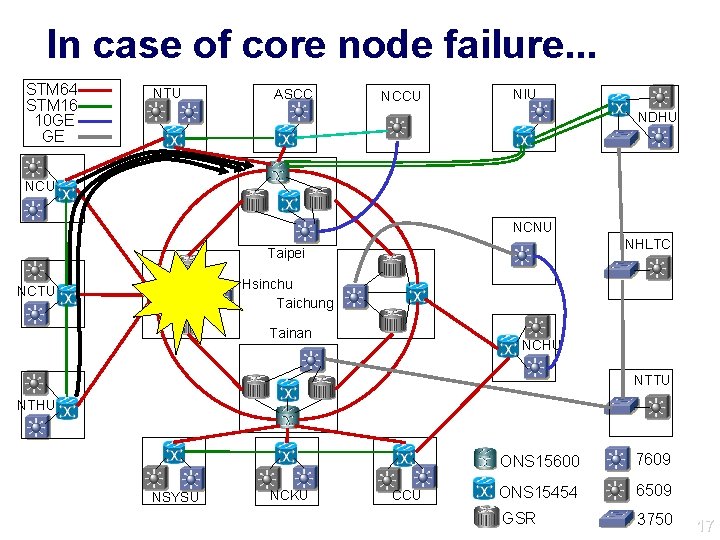
Protection Mechanism Equipment protection l Core node failure: Manually configure emergency lightpaths to re-route traffic from affected Giga. Po. Ps to another core node. Emergency lightpaths need to be designed and documented. l Giga. Po. P failure: Spare line cards 14

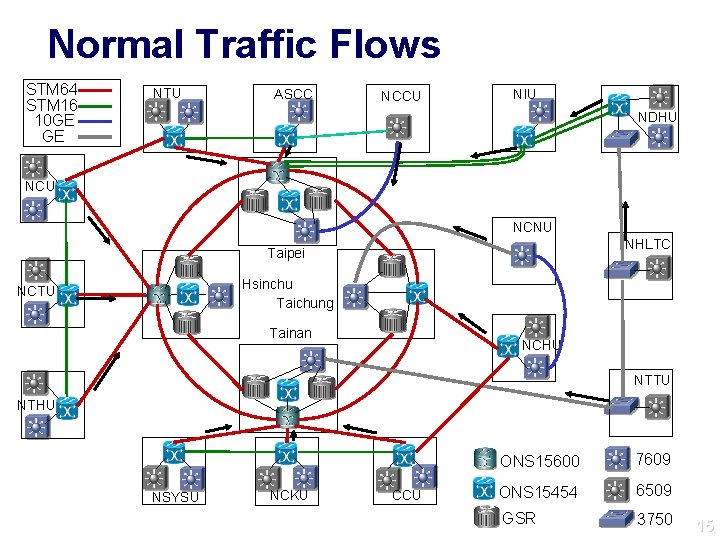
Normal Traffic Flows STM 64 STM 16 10 GE GE NTU ASCC NCCU NIU NDHU NCNU NHLTC Taipei Hsinchu Taichung NCTU Tainan NCHU NTTU NTHU NSYSU NCKU CCU ONS 15600 7609 ONS 15454 6509 GSR 3750 15

In case of circuit break. . . STM 64 STM 16 10 GE GE NTU ASCC NCCU NIU NDHU NCNU NHLTC Taipei Hsinchu Taichung NCTU Tainan NCHU NTTU NTHU NSYSU NCKU CCU ONS 15600 7609 ONS 15454 6509 GSR 3750 16

In case of core node failure. . . STM 64 STM 16 10 GE GE NTU ASCC NCCU NIU NDHU NCNU NHLTC Taipei Hsinchu Taichung NCTU Tainan NCHU NTTU NTHU NSYSU NCKU CCU ONS 15600 7609 ONS 15454 6509 GSR 3750 17

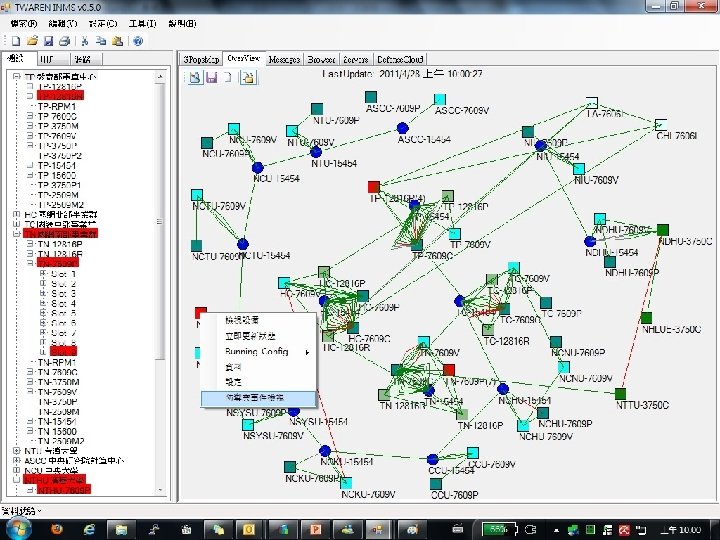
TWAREN NOC (Network Operation Center) Located at NCHC southern business unit in Tainan Science Park Goals: To ensure the 7 x 24 network operation Major works: l l l Providing 7 x 24 network maintenance and operation Enhance the security capacity Provide network service l l l Peering Light path provision Network architecture design TWAREN NOC 18

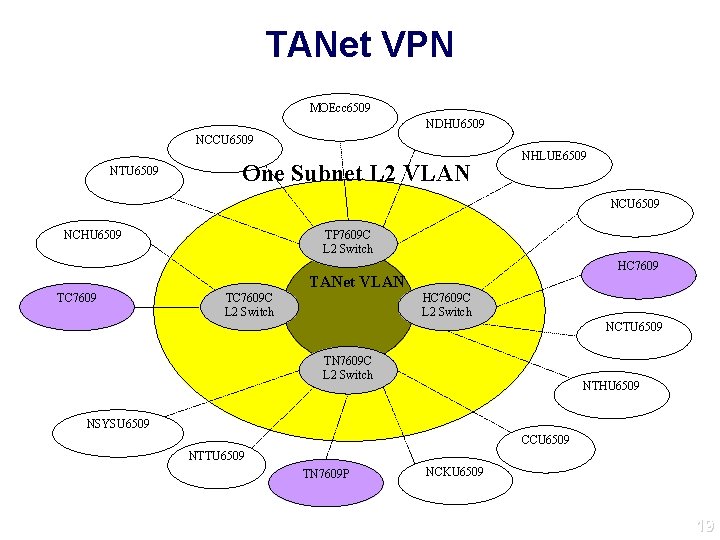
TANet VPN MOEcc 6509 NDHU 6509 NCCU 6509 NTU 6509 One Subnet L 2 VLAN NHLUE 6509 NCU 6509 NCHU 6509 TP 7609 C L 2 Switch HC 7609 TANet VLAN TC 7609 C L 2 Switch HC 7609 C L 2 Switch NCTU 6509 TN 7609 C L 2 Switch NTHU 6509 NSYSU 6509 CCU 6509 NTTU 6509 TN 7609 P NCKU 6509 19

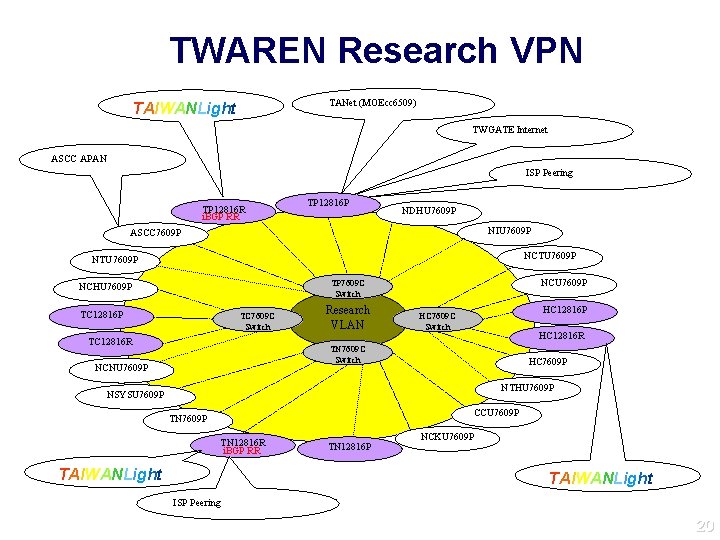
TWAREN Research VPN TANet (MOEcc 6509) TAIWANLight TWGATE Internet ASCC APAN ISP Peering TP 12816 R i. BGP RR TP 12816 P NDHU 7609 P NIU 7609 P ASCC 7609 P NCTU 7609 P NCU 7609 P TP 7609 C Switch NCHU 7609 P TC 12816 P TC 7609 C Switch TC 12816 R Research VLAN HC 12816 P HC 7609 C Switch HC 12816 R TN 7609 C Switch NCNU 7609 P HC 7609 P NTHU 7609 P NSYSU 7609 P CCU 7609 P TN 12816 R i. BGP RR TAIWANLight TN 12816 P NCKU 7609 P TAIWANLight ISP Peering 20

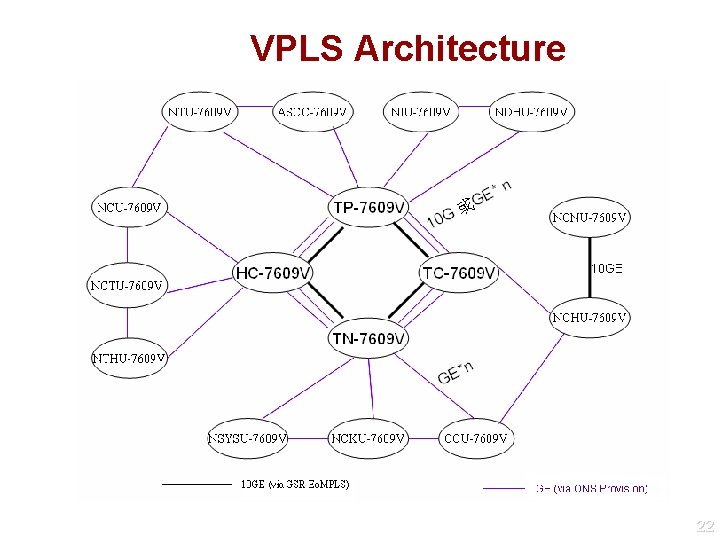
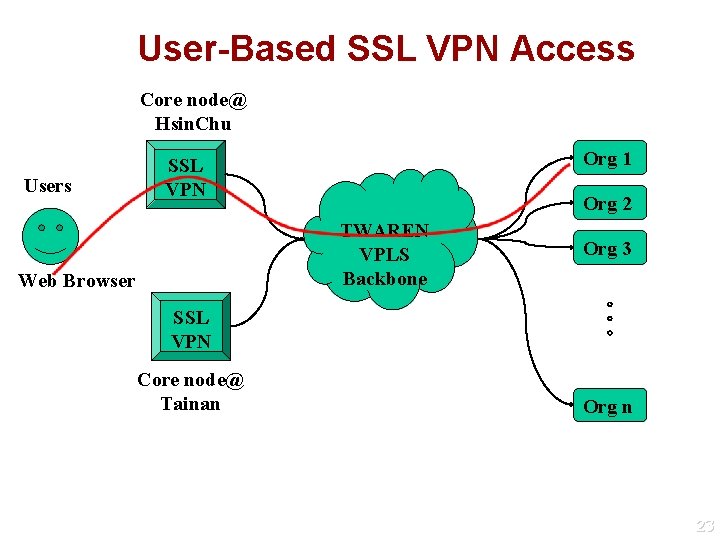
VPN Services l l Multipoint-to-Multipoint Layer 2 VPN (VPLS) Multiple VPNs over single architecture Cross-area campuses and offices can be connected within single administrative domain l Provide dynamic creation of VPNs for Nationalwide integrated projects l l User-based SSL VPN Access to different VPN according to login name and password authentication Researchers and Professors could access their own research resources from home or outside 21

VPLS Architecture 22

User-Based SSL VPN Access Core node@ Hsin. Chu Users Org 1 SSL VPN Org 2 TWAREN VPLS Backbone Web Browser Org 3 SSL VPN 。 。 。 Core node@ Tainan Org n 23

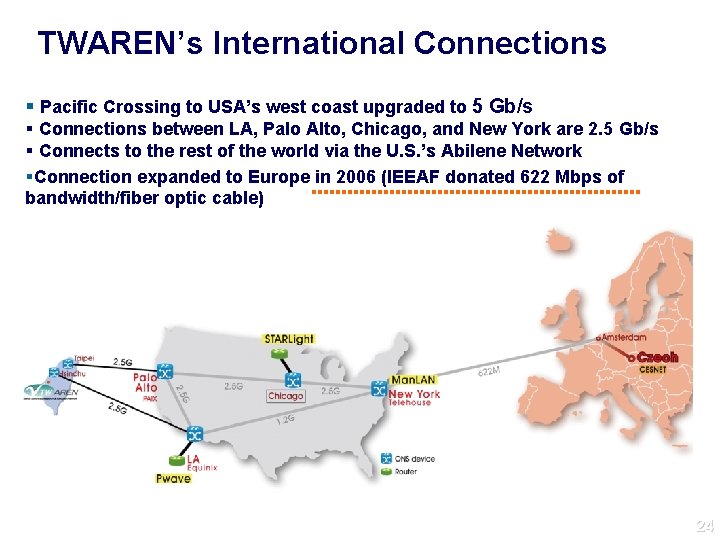
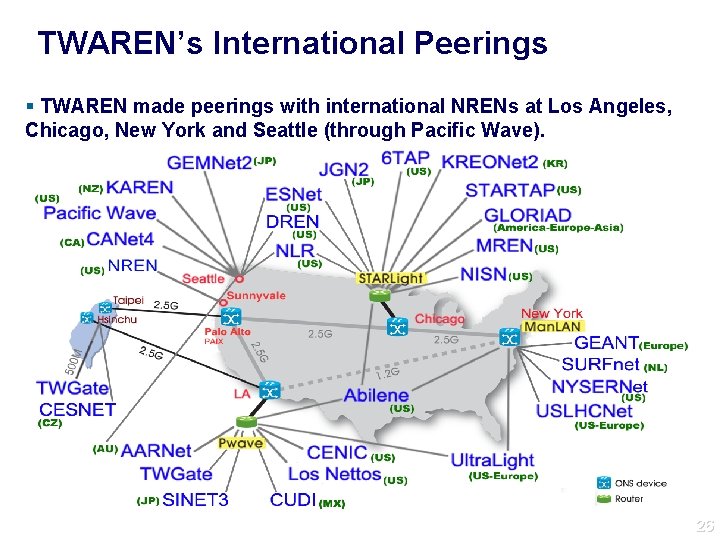
TWAREN’s International Connections Pacific Crossing to USA’s west coast upgraded to 5 Gb/s Connections between LA, Palo Alto, Chicago, and New York are 2. 5 Gb/s Connects to the rest of the world via the U. S. ’s Abilene Network Connection expanded to Europe in 2006 (IEEAF donated 622 Mbps of bandwidth/fiber optic cable) 24

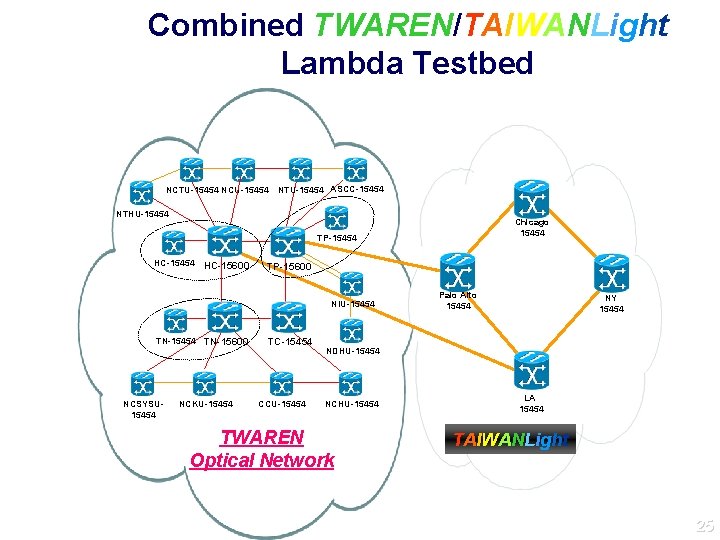
Combined TWAREN/TAIWANLight Lambda Testbed NCTU-15454 NCU-15454 NTU-15454 ASCC-15454 NTHU-15454 Chicago 15454 TP-15454 HC-15600 TP-15600 NIU-15454 TN-15600 NCSYSU 15454 NCKU-15454 TC-15454 CCU-15454 Palo Alto 15454 NY 15454 NDHU-15454 NCHU-15454 TWAREN Optical Network LA 15454 TAIWANLight 25

TWAREN’s International Peerings TWAREN made peerings with international NRENs at Los Angeles, Chicago, New York and Seattle (through Pacific Wave). 26

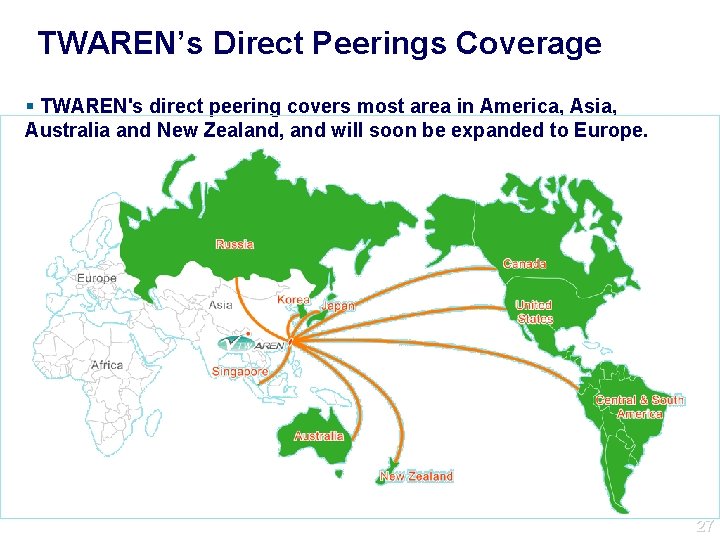
TWAREN’s Direct Peerings Coverage TWAREN's direct peering covers most area in America, Asia, Australia and New Zealand, and will soon be expanded to Europe. 27

TWAREN/TAIWANLight and GLIF TWAREN is a member of GLIF (Global Lambda Integrated Facility) TAIWANLight is an official optical exchange GOLE (GLIF Open Lightpath Exchange) 28

TWAREN Network Overview Development and Research Technologies 29

Future Internet Testbed @ Taiwan 30

Future Internet There are many serious limitations in current Internet. l l Scalability Security Qo. S Virtualization Future Internet is a summarizing term for worldwide research activities dedicated to the further development of the original Internet. (From Wiki) 31

Future Internet Testbed For innovations and researches in Future Internet, the testbed requires some advanced concepts: l l l Programmability Virtualization End-to-end slice 32

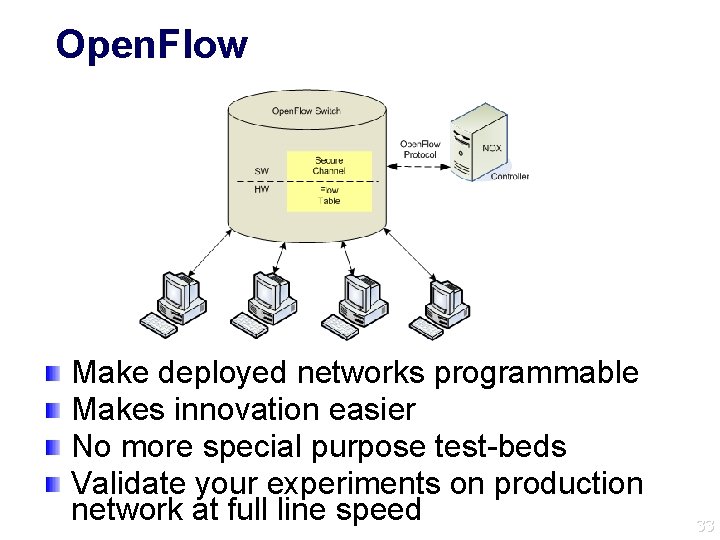
Open. Flow Make deployed networks programmable Makes innovation easier No more special purpose test-beds Validate your experiments on production network at full line speed 33

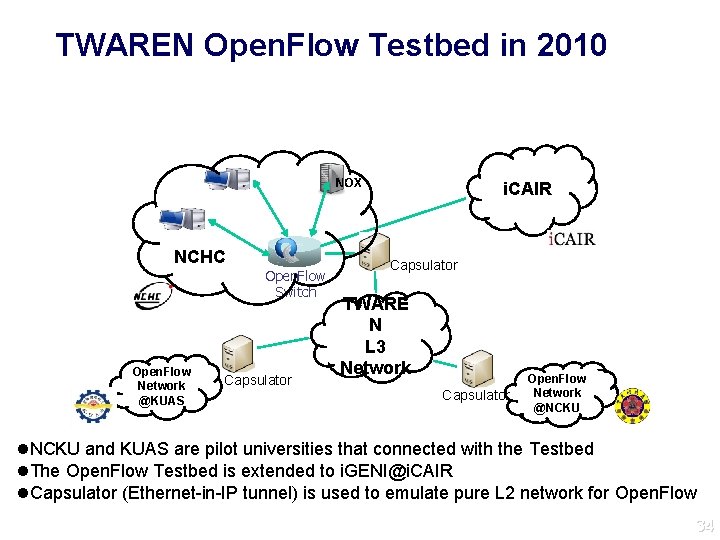
TWAREN Open. Flow Testbed in 2010 NOX NCHC Open. Flow Switch Open. Flow Network @KUAS Capsulator i. CAIR Capsulator TWARE N L 3 Network Capsulator Open. Flow Network @NCKU l. NCKU and KUAS are pilot universities that connected with the Testbed l. The Open. Flow Testbed is extended to i. GENI@i. CAIR l. Capsulator (Ethernet-in-IP tunnel) is used to emulate pure L 2 network for Open. Flow 34 34

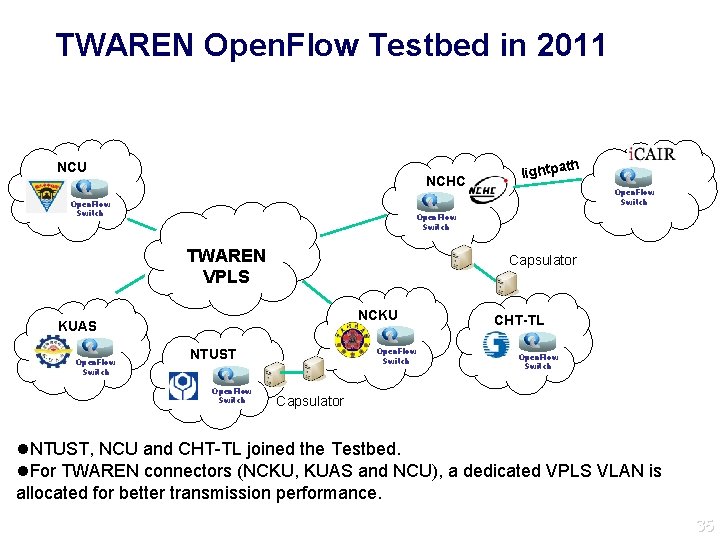
TWAREN Open. Flow Testbed in 2011 NCU NCHC Open. Flow Switch TWAREN VPLS Capsulator NCKU KUAS Open. Flow Switch th lightpa Open. Flow Switch NTUST Open. Flow Switch CHT-TL Open. Flow Switch Capsulator l. NTUST, NCU and CHT-TL joined the Testbed. l. For TWAREN connectors (NCKU, KUAS and NCU), a dedicated VPLS VLAN is allocated for better transmission performance. 35 35

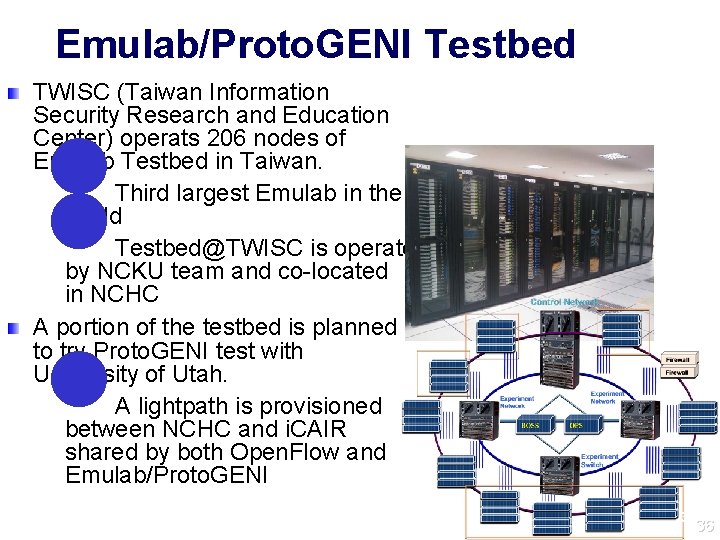
Emulab/Proto. GENI Testbed TWISC (Taiwan Information Security Research and Education Center) operats 206 nodes of Emulab Testbed in Taiwan. Third largest Emulab in the world Testbed@TWISC is operated by NCKU team and co-located in NCHC A portion of the testbed is planned to try Proto. GENI test with University of Utah. A lightpath is provisioned between NCHC and i. CAIR shared by both Open. Flow and Emulab/Proto. GENI l l l 36 36

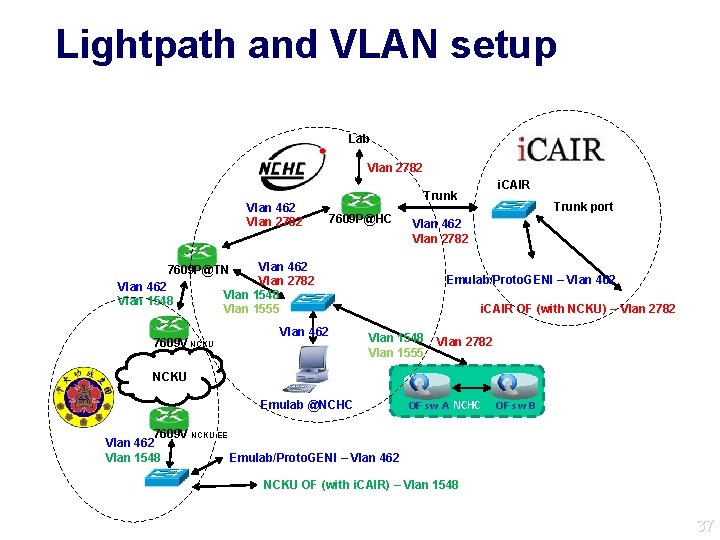
Lightpath and VLAN setup Lab Vlan 2782 Vlan 462 Vlan 2782 7609 P@HC 7609 V NCKU Vlan 462 Vlan 2782 Vlan 1548 Vlan 1555 Vlan 462 Trunk port Vlan 462 Vlan 2782 7609 P@TN Vlan 462 Vlan 1548 i. CAIR Trunk Emulab/Proto. GENI – Vlan 462 i. CAIR OF (with NCKU) – Vlan 2782 Vlan 1548 Vlan 1555 Vlan 2782 NCKU Emulab @NCHC OF sw A NCHC OF sw B 7609 V NCKU EE Vlan 462 Vlan 1548 Emulab/Proto. GENI – Vlan 462 NCKU OF (with i. CAIR) – Vlan 1548 37 37

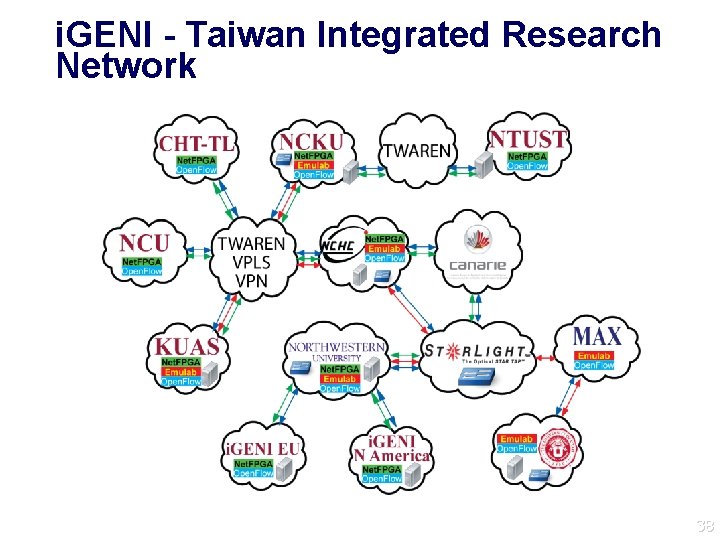
i. GENI - Taiwan Integrated Research Network 38 38

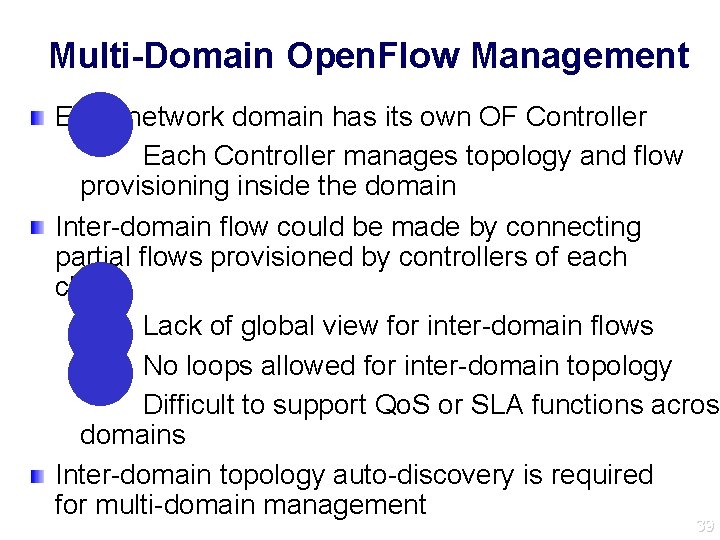
Multi-Domain Open. Flow Management l Each network domain has its own OF Controller Each Controller manages topology and flow provisioning inside the domain Inter-domain flow could be made by connecting partial flows provisioned by controllers of each cloud Lack of global view for inter-domain flows No loops allowed for inter-domain topology Difficult to support Qo. S or SLA functions across domains Inter-domain topology auto-discovery is required for multi-domain management 39 l l l 39

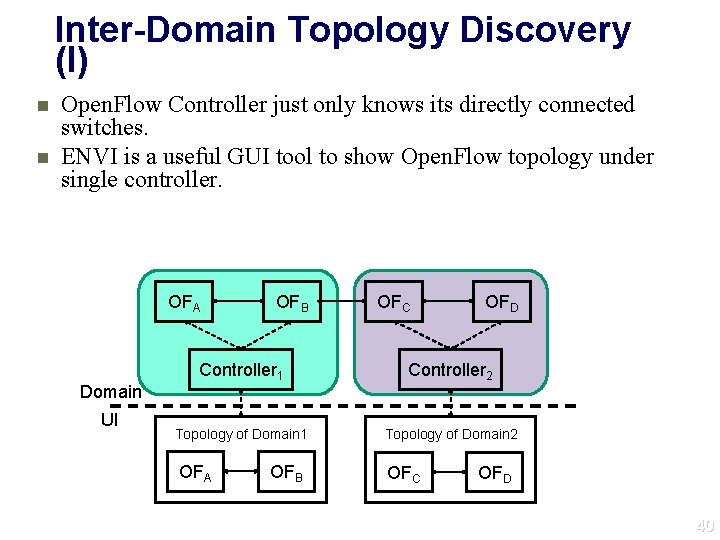
Inter-Domain Topology Discovery (I) n n Open. Flow Controller just only knows its directly connected switches. ENVI is a useful GUI tool to show Open. Flow topology under single controller. OFA Domain UI OFB OFC OFD Controller 1 Controller 2 Topology of Domain 1 Topology of Domain 2 OFA OFC OFB OFD 40 40

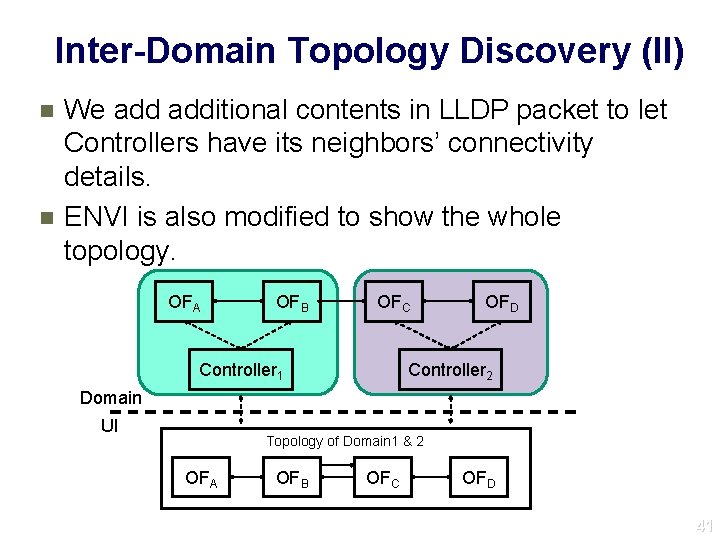
Inter-Domain Topology Discovery (II) n n We additional contents in LLDP packet to let Controllers have its neighbors’ connectivity details. ENVI is also modified to show the whole topology. OFA OFB OFC Controller 1 OFD Controller 2 Domain UI Topology of Domain 1 & 2 OFA OFB OFC OFD 41 41

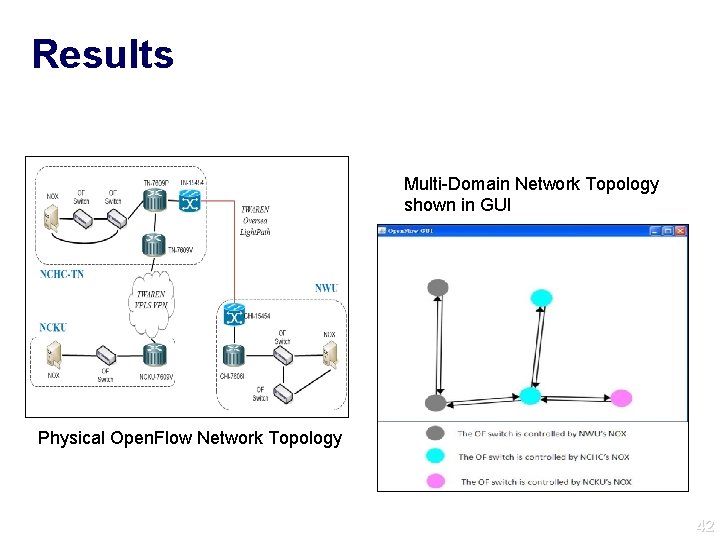
Results Multi-Domain Network Topology shown in GUI Physical Open. Flow Network Topology 42 42

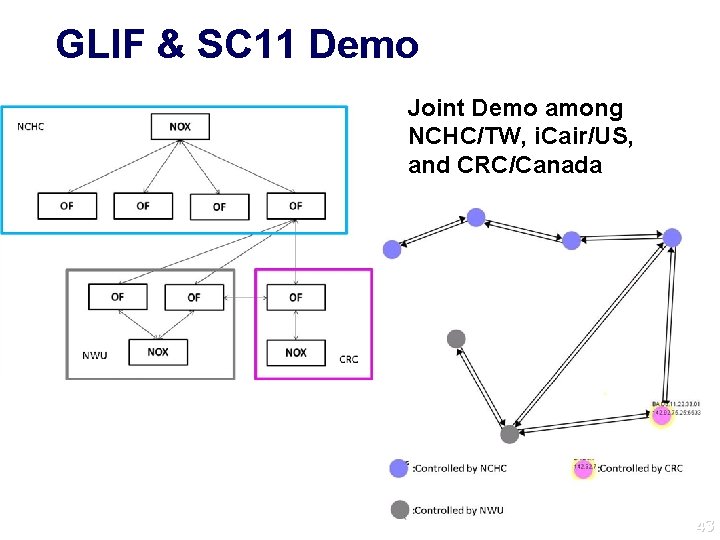
GLIF & SC 11 Demo Joint Demo among NCHC/TW, i. Cair/US, and CRC/Canada 43

Information Security Activity Detection over High-Speed Backbone 44

Security Detection over High. Speed Backbone Normally, we don’t install IDS/IDP in backbone for performance issue. l l IDS/IDP are placed at user’s local sites Backbone traffic is hard to mirroring due to its large amount and high-speed It’s impossible to do packet analysis Packet header analysis is available with Netflow/s. Flow Information Security Activity Detection over High-Speed Backbone Integrate fast packet header analysis with attack information from user’s local site 45

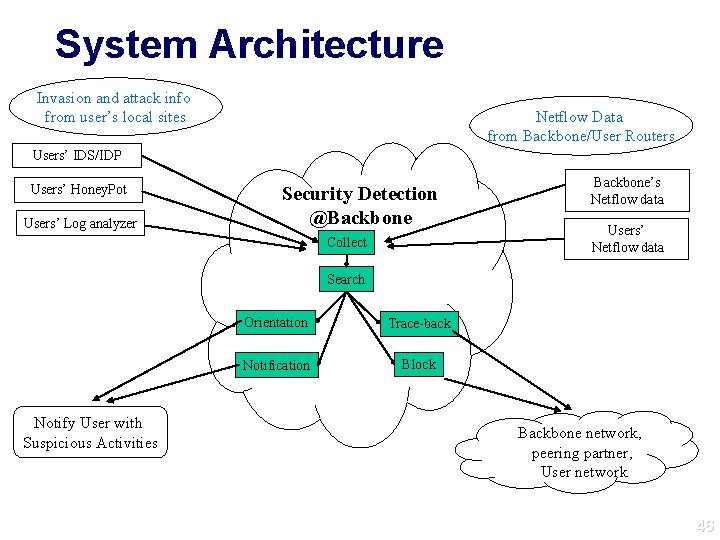
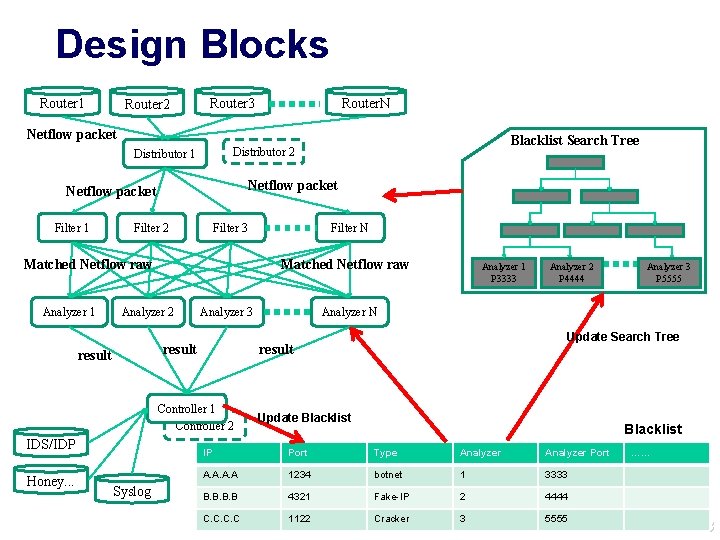
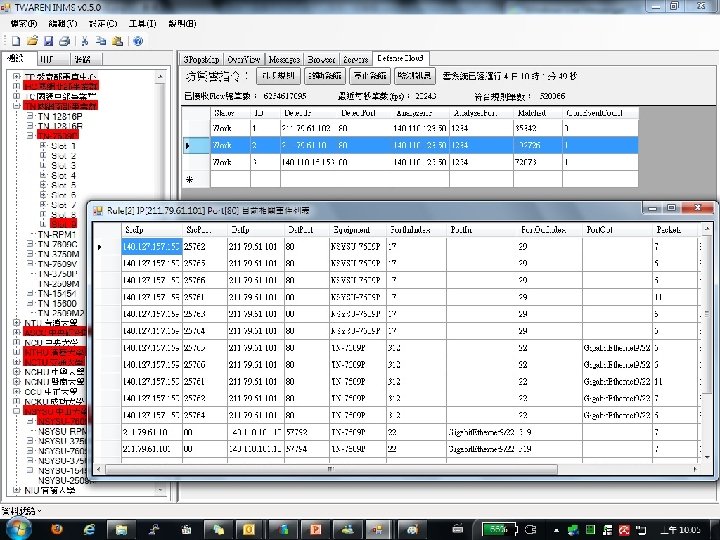
System Architecture Invasion and attack info from user’s local sites Netflow Data from Backbone/User Routers Users’ IDS/IDP Users’ Honey. Pot Users’ Log analyzer Security Detection @Backbone Collect Backbone’s Netflow data Users’ Netflow data Search Notify User with Suspicious Activities Orientation Trace-back Notification Block Backbone network, peering partner, User network 46

Design Concepts l l l Distributed Computing For monitoring netflow data in real-time Fast Search Effective Tree-Searching algorithm Expandable Simply add more machines when larger data analysis is required Remote Backup Separate different computing nodes in order to provide robust analysis service Single Portal All input can be submit to single portal with Global Server Load. Balancing technology Cooperate with Researchers/Developers Will design an open API for developers to contribute their own ideas 47

Design Blocks Router 1 Router 2 Router 3 Router. N Netflow packet Filter 1 Filter 2 Filter 3 Matched Netflow raw Analyzer 1 Analyzer 3 result Honey. . . Syslog Analyzer 1 P 3333 Analyzer 2 P 4444 Analyzer 3 P 5555 Analyzer N Update Search Tree result Controller 1 Controller 2 IDS/IDP Filter N Matched Netflow raw Analyzer 2 result Blacklist Search Tree Distributor 2 Distributor 1 Update Blacklist IP Port Type Analyzer Port A. A 1234 botnet 1 3333 B. B 4321 Fake-IP 2 4444 C. C 1122 Cracker 3 5555 …… 48

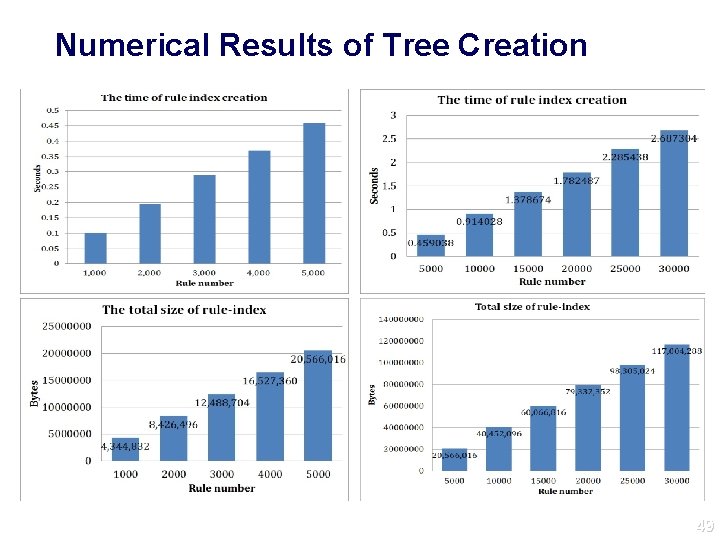
Numerical Results of Tree Creation 49

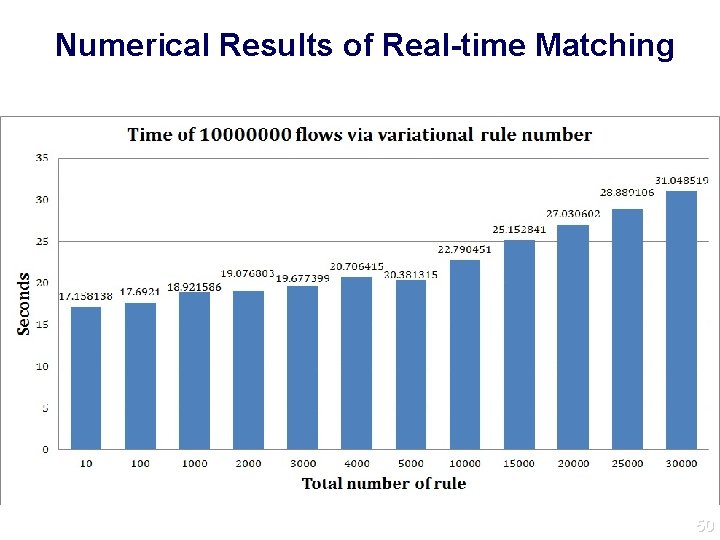
Numerical Results of Real-time Matching 50

51

52

53

54

55

56

57

Thank You ! For more information, please see : www. twaren. net - 2011 - 58