Security Management Practices General overview of good security
























- Slides: 32

Security Management Practices General overview of good security management processes. Introduces topics used in several other sections

Overview o o o Basic Security Concepts Policies, Standards, Guidelines, & Procedures Roles played in security management Security Awareness Risk Management Data & Information Classification

Concepts o o o C. I. A. - Confidentiality, Integrity, & Availability Identification, Authentication, Accountability, Authorization, Privacy Objective of Security Controls: reduce likelihood & impact of threats

Systems Security Lifecycle 1. 2. 3. 4. 5. Initiation Development/Acquisition Implementation Operation/maintenance Disposal

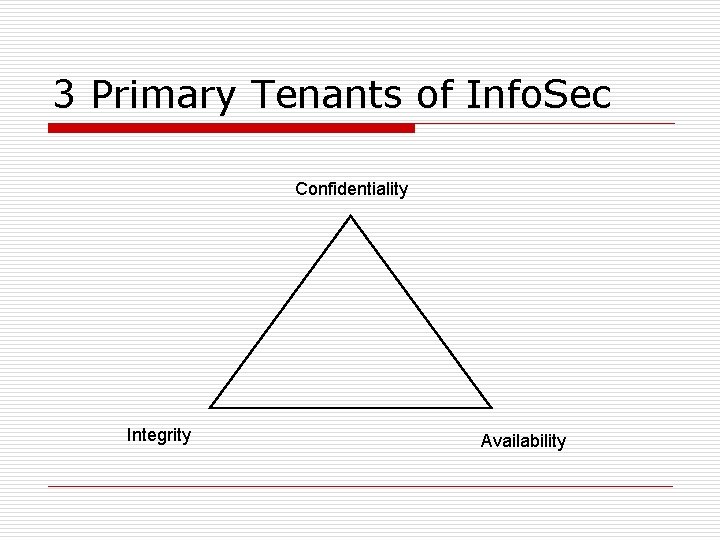
3 Primary Tenants of Info. Sec Confidentiality Integrity Availability

Personnel Concepts o Identification o Authentication o Accountability o Authorization o Privacy

System Concepts o o o o Assume external systems are insecure Examine the trade-offs (nothing is free) Use Layered Security (greater work factor) Minimize the system elements that are “trusted” Isolate public accessed systems Authenticate both users & processes Use Unique Identities to ensure accountability Implement least privilege

TOA: Trade-off Analysis o Define the objective (in writing) o Identify alternatives (courses of action) o Compare alternatives o Realize that there are no perfectly secure systems in opperation

Security Controls o Objective: reduce vulnerabilities & minimize the effect of an attack n n n o o o Attack likelihood Attack cost Attack countermeasures Deterrent controls Corrective Controls Detective Controls

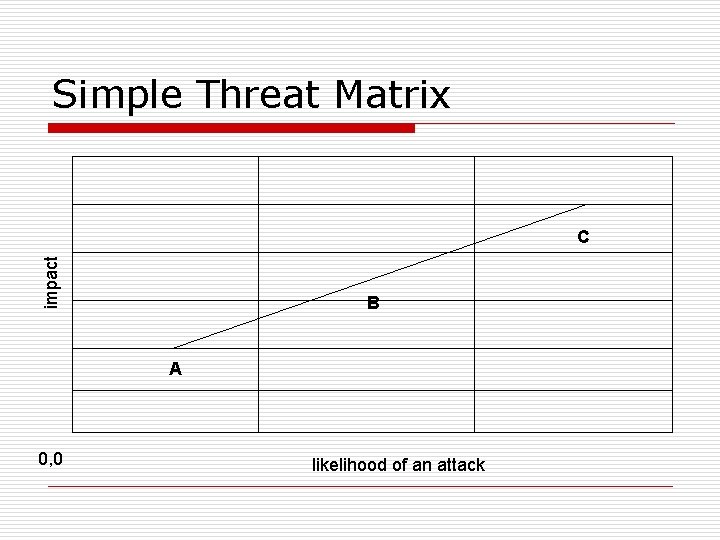
Simple Threat Matrix impact C B A 0, 0 likelihood of an attack

Information Classification o o o Why classify data & information Concepts Classification Terms n n o o Governmental Private Sector Criteria Roles used in the classification process

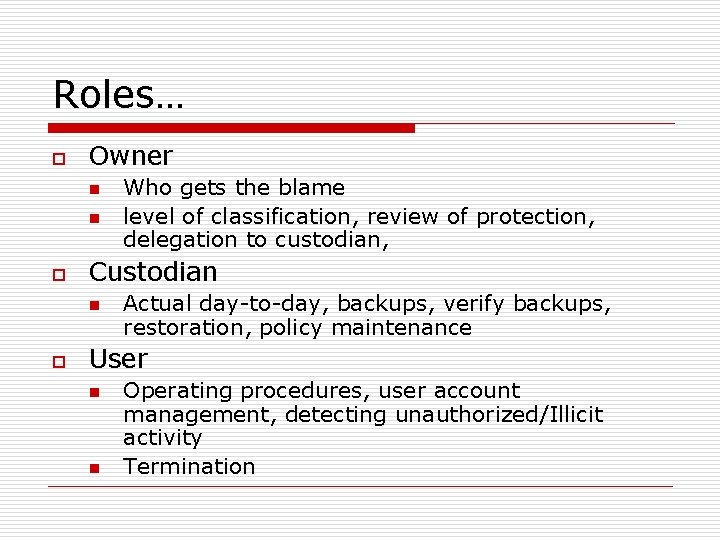
Roles… o Owner n n o Custodian n o Who gets the blame level of classification, review of protection, delegation to custodian, Actual day-to-day, backups, verify backups, restoration, policy maintenance User n n Operating procedures, user account management, detecting unauthorized/Illicit activity Termination

Implementation 1. Policy: 1. 2. 3. 2. senior management (demonstration of commitment general organizational Policy: Functional Implementation 1. 2. 3. Standards -Guidelines Procedures Baselines

Risk management o o Risk can never be totally eliminated Primary purpose 1. 2. o Identification of risks Cost / benefit analysis Benefits 1. 2. 3. Creates clear cost-to-value Helps analysis process Helps design and creation

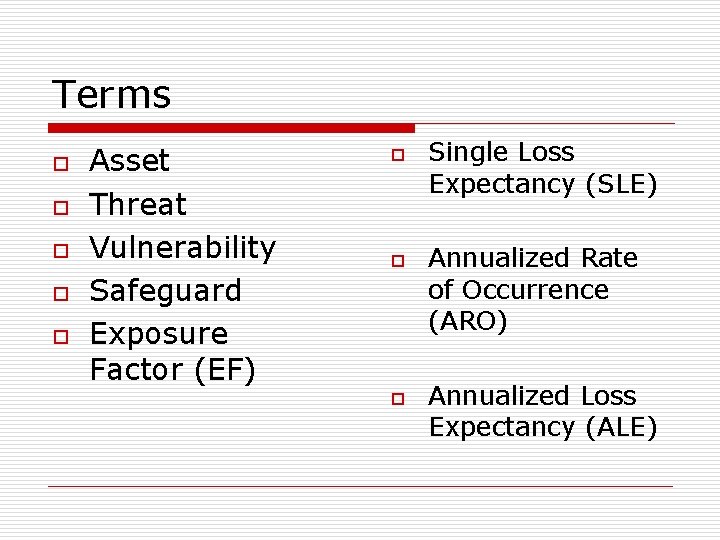
Terms o o o Asset Threat Vulnerability Safeguard Exposure Factor (EF) o o o Single Loss Expectancy (SLE) Annualized Rate of Occurrence (ARO) Annualized Loss Expectancy (ALE)

Attacks o Criminal n n n o Privacy: less and less available n n n o o Fraud-prolific on the Internet Destructive, Intellectual Property Identity Theft, Brand Theft people do not own their own data Surveillance, Databases, Traffic Analysis Echelon, Carnivore Publicity & Denial of Service Legal

Brief Risk Analysis Overview o o Quantitative vs Qualitative Steps n n o o o Potential losses Potential threats Asset valuation Safeguard selection Remedies

Risk Analysis “The identification and evaluation of the most likely permutation of assets, known and anticipated vulnerabilities, and known and anticipated types of attackers. ”

Assets o o What are you trying to Protect Why is it being protected Risk for other systems on network Data n n Tampering vs. Stealing Liability

Attackers o Categorize by n o Hackers: n o Objective, Access, Resources, Expertise, and Risk Galileo, Marie Curie Lone Criminals, Insiders, Espionage, Press, Organized Crime, Terrorists

Motives Business competitors o Same motives as “real-life” criminals o Financial motives n n o o Credit cards The Cuckcoo’s Egg Political motives Personal / psychological motives

Motives o Honeypot o Script Kiddies community” n n o o “to learn tools tactics and motives of blackhat Canned Exploits of Perl or Shell scripts Still major threat Knowing motives helps predict attack Degrees of motivation n n Automated tools Hardened systems vs Easy Kills

Steps in an Attack 1. 2. 3. 4. 5. Identify Target & collect Information Find vulnerability in target Gain appropriate access to target Perform the attack Complete attack, remove evidence, ensure future access

After you get root 1. 2. 3. 4. Remove traces of root compromise Gather information about system Make sure you can get back in Disable or patch vulnerability

Vulnerability Landscape o Physical World n Laptops o Virtual World o Trust Model o System Life cycled

Vulnerabilities o o Only potential until someone figures out how to exploit Need to identify and address n n n Those applicable & which must mitigated now Are likely to apply & must be planned against Seem unlikely and/or are easy to mitagate

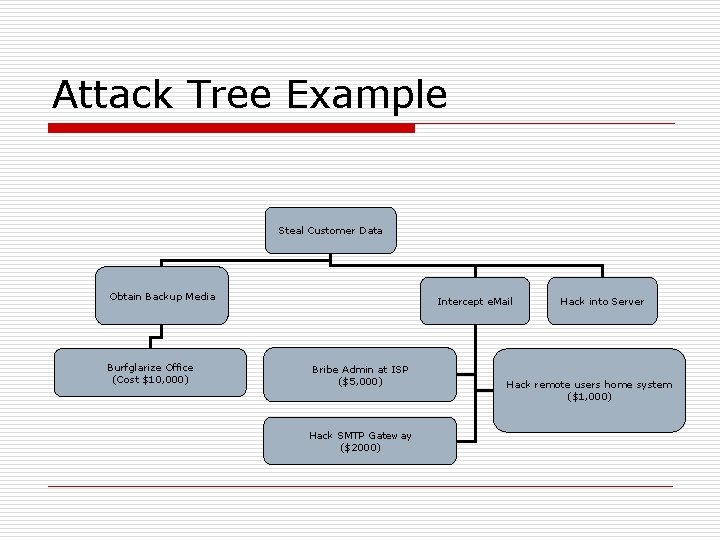
Attack Trees o o o (Bruce Schneier) Visual Representation of attacks against any given target Attack goal is root Attack subgoals are leaf nodes n n For each leaf determine subgoals necessary to achieve And cost to achieve penetration using different types of attackers

Attack Tree Example Steal Customer Data Obtain Backup Media Burfglarize Office (Cost $10, 000) Intercept e. Mail Bribe Admin at ISP ($5, 000) Hack SMTP Gateway ($2000) Hack into Server Hack remote users home system ($1, 000)

Defenses o Three general means of mitigating attack risk n n Reducing asset value to attacker Mitigating specific vulnerabilities o o n Software patches Defensive Coding Neutralizing or preventing attacks o o Access control mechanisms Distinguish between trusted & untrusted users

Security o Security is a process not a Product o Weakest link in the process o Examples of Threat Modeling in Secrets & Lies chapter 19

Security Awareness o o People are often the weakest link Benefits: n n n o Awareness of need to protect the system Skill & knowledge improvement More in-depth knowledge Be careful of over training n n Constant barrage == ignored Too much knowledge of how the system works

References o o Cohen, Fred “A Preliminary Classification Scheme for Information Security Threats, Attacks, and Defenses; A Cause and Effect Model; and Some Analysis Based on that Model. ” Sandia National Laboratories, Sept 1998 (www. all. net/journal/ntb/cause-andeffect. html) Bauer, Michael E. “Building Secure Servers with Linux. ” O’Reilly, 2003