POWERSHELL SECURITY BEST PRACTICES Lee Holmes LeeHolmes Principal

POWERSHELL SECURITY BEST PRACTICES Lee Holmes | @Lee_Holmes Principal SDE |Windows Power. Shell | Microsoft

ABOUT ME Security geek Developer on the Windows Power. Shell team since V 1 Author of the Windows Power. Shell Cookbook, Power. Shell. Cookbook. com, and Windows Power. Shell Pocket Reference @Lee_Holmes & leeholmes. com/blog

POWERSHELL THE SHELL OPERATIONAL SECURITY What about Execution Policy? Power. Shell Remoting Scripts Executables Dealing with Forensics
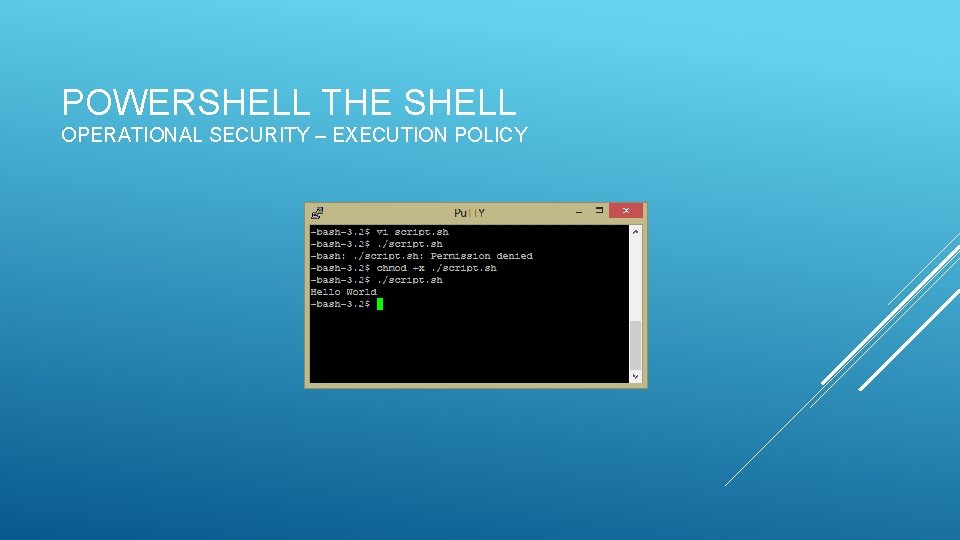
POWERSHELL THE SHELL OPERATIONAL SECURITY – EXECUTION POLICY
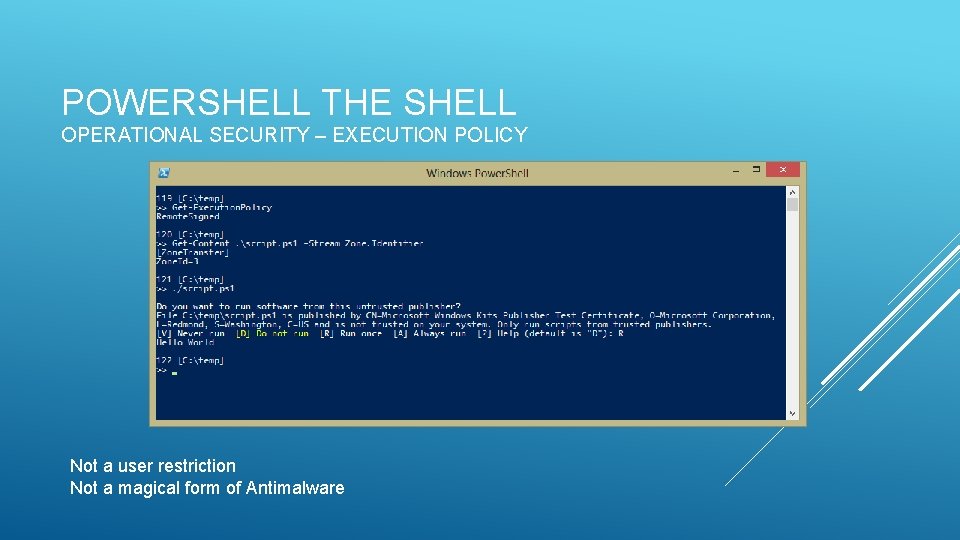
POWERSHELL THE SHELL OPERATIONAL SECURITY – EXECUTION POLICY Not a user restriction Not a magical form of Antimalware
POWERSHELL THE SHELL OPERATIONAL SECURITY – POWERSHELL REMOTING You Remoting Host Understanding the Double-Hop problem Authentication: Kerberos vs. Cred. SSP – Pass the Hash? Accessing Remote Resources Files
POWERSHELL THE SHELL OPERATIONAL SECURITY – SCRIPTS EXECUTABLES Moving to Post-Exploitation defense “I want to secure my system against C++ attacks” Making sense of holistic system lockdown
POWERSHELL THE SHELL OPERATIONAL SECURITY – DEALING WITH FORENSICS @Hacking. Dave @Obscure. Sec / @Mattifestation “Living off the Land” @Joseph. Bialek “Reflective DLL Injection”
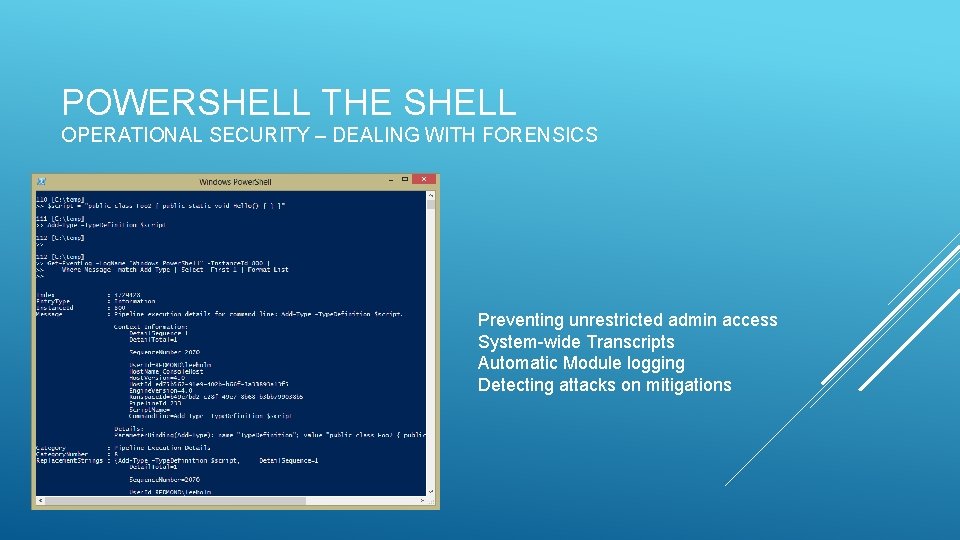
POWERSHELL THE SHELL OPERATIONAL SECURITY – DEALING WITH FORENSICS Preventing unrestricted admin access System-wide Transcripts Automatic Module logging Detecting attacks on mitigations

POWERSHELL THE LANGUAGE SCRIPTING SECURITY Script Encryption / Obfuscation Avoiding Code Injection Avoiding Hard-Coded Secrets
POWERSHELL THE LANGUAGE SCRIPTING SECURITY - SCRIPT ENCRYPTION / OBFUSCATION
POWERSHELL THE LANGUAGE SCRIPTING SECURITY - SCRIPT ENCRYPTION / OBFUSCATION Answer: Don’t.
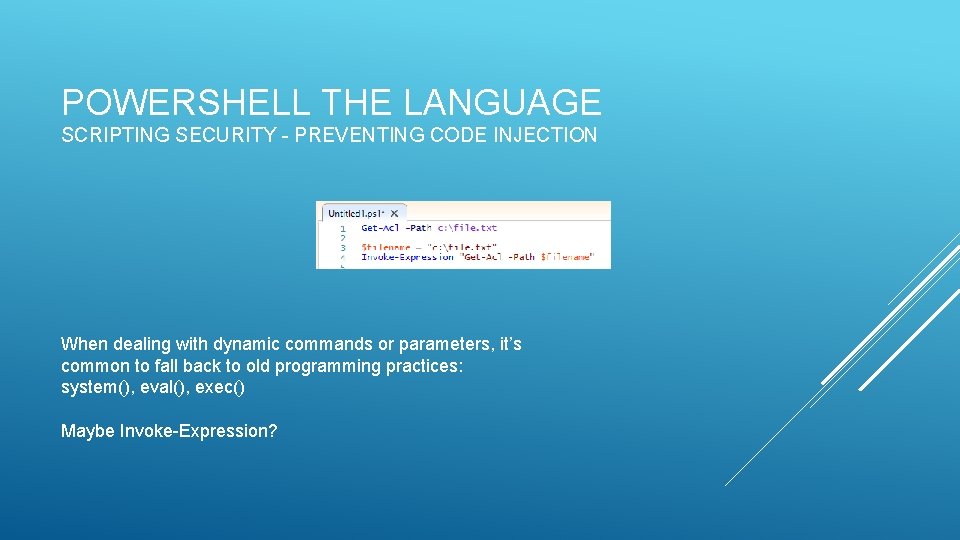
POWERSHELL THE LANGUAGE SCRIPTING SECURITY - PREVENTING CODE INJECTION When dealing with dynamic commands or parameters, it’s common to fall back to old programming practices: system(), eval(), exec() Maybe Invoke-Expression?
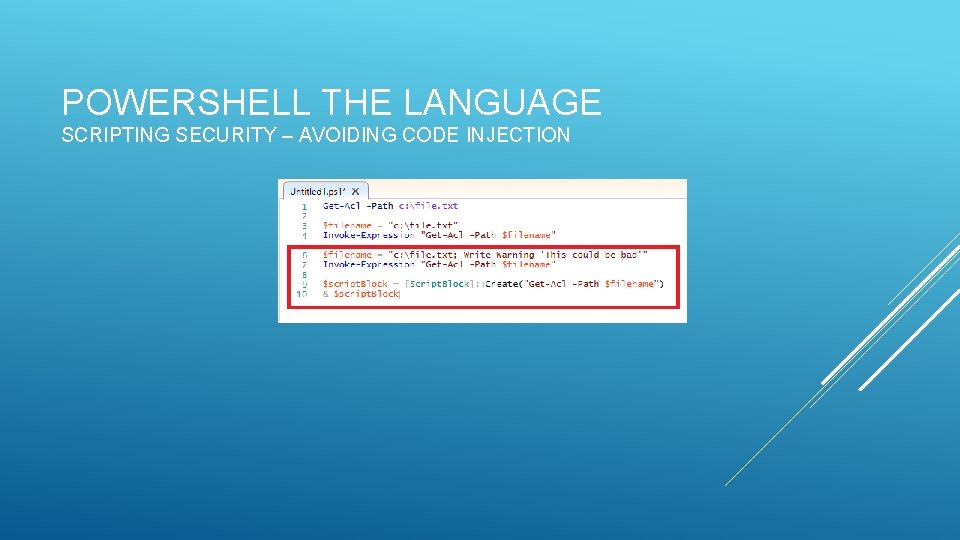
POWERSHELL THE LANGUAGE SCRIPTING SECURITY – AVOIDING CODE INJECTION

POWERSHELL THE LANGUAGE SCRIPTING SECURITY – AVOIDING CODE INJECTION Parameters support variables Commands support splatting Invocation supports indirection
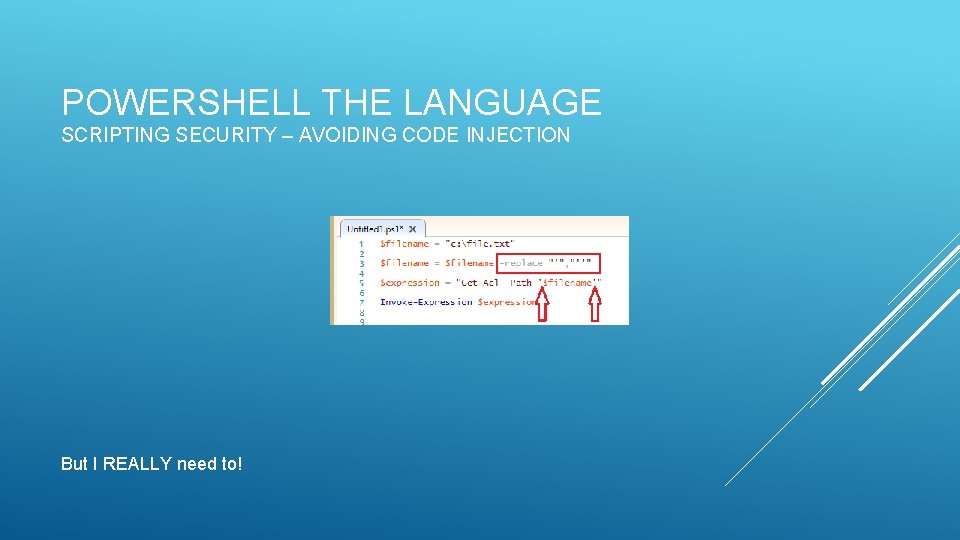
POWERSHELL THE LANGUAGE SCRIPTING SECURITY – AVOIDING CODE INJECTION But I REALLY need to!

POWERSHELL THE LANGUAGE SCRIPTING SECURITY – AVOIDING CODE INJECTION But I REALLY need to!
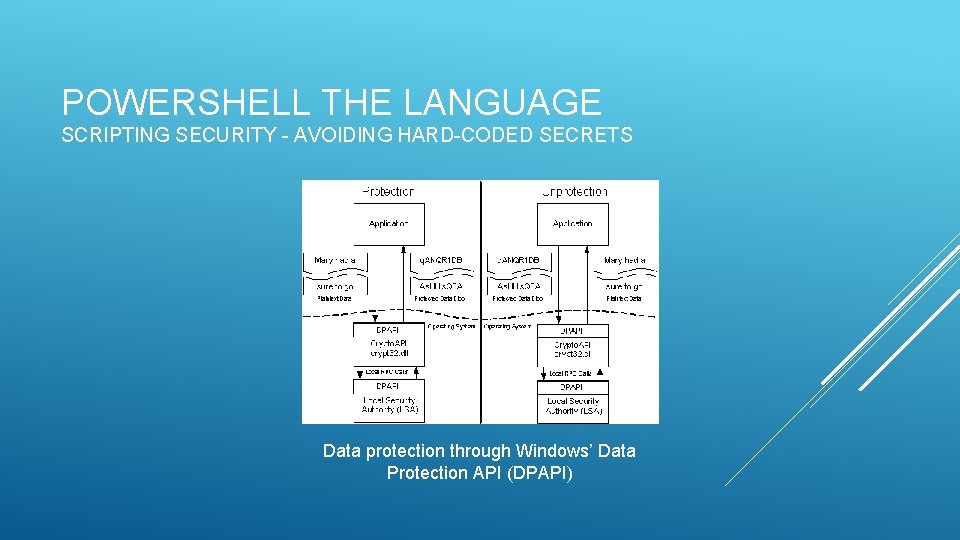
POWERSHELL THE LANGUAGE SCRIPTING SECURITY - AVOIDING HARD-CODED SECRETS Data protection through Windows’ Data Protection API (DPAPI)
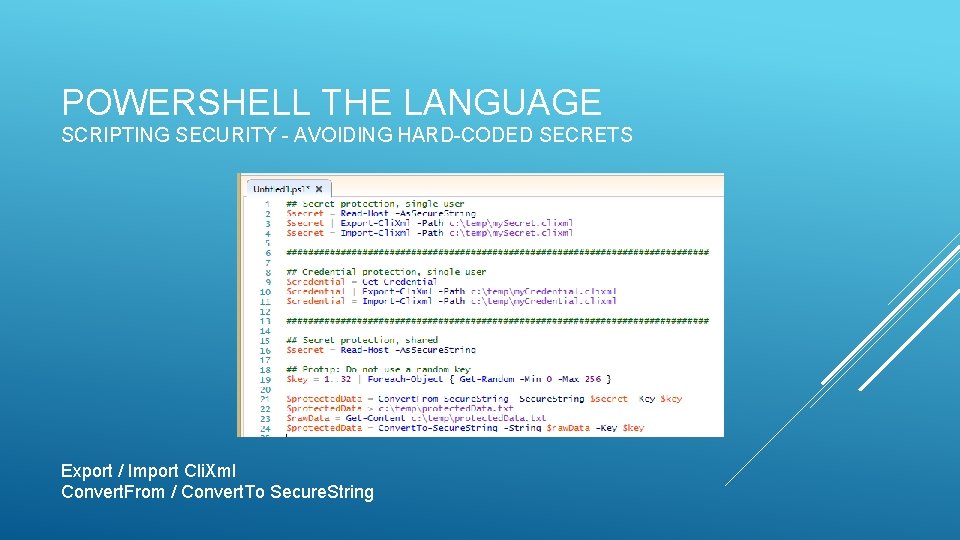
POWERSHELL THE LANGUAGE SCRIPTING SECURITY - AVOIDING HARD-CODED SECRETS Export / Import Cli. Xml Convert. From / Convert. To Secure. String

RESOURCES Reflective DLL Loading with Power. Shell: http: //www. youtube. com/watch? v=OAd 68_SYQc 8 Living off the Land: http: //www. youtube. com/watch? v=j-r 6 Uon. Ek. Uw Get-Help about_Group_Policy_Settings http: //technet. microsoft. com/en-us/library/jj 149004. aspx Constrained Power. Shell Endpoints http: //www. youtube. com/watch? v=kmj. JLKl. L 1 Wg Power. Shell Language Specification: http: //www. microsoft. com/en-us/download/details. aspx? id=36389 Composing Command Arguments: http: //www. powershellcookbook. com/recipe/Xo. Mw/run-programs-scripts-and-existing-tools
- Slides: 20