Network Secure Gateway What is the Network Secure






- Slides: 18

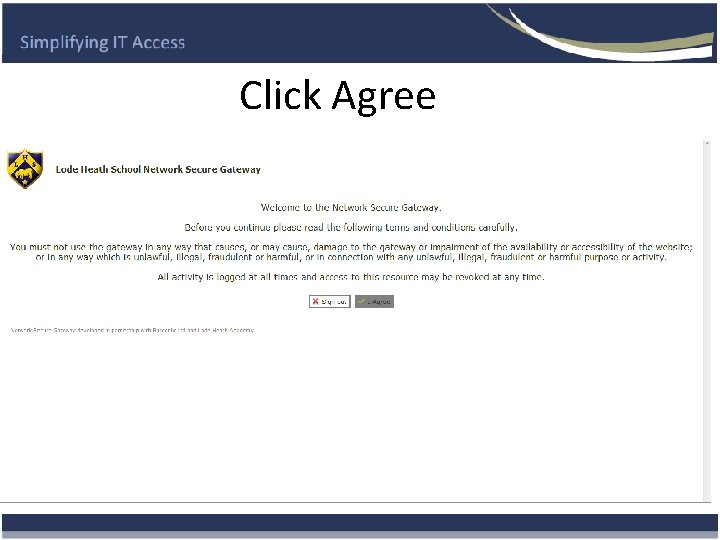
Network Secure Gateway • What is the Network Secure Gateway ? • It is in essence Secure remote access to PC’s and resources on your network. • This includes anything on your Network. • Built on top of Windows Technologies with added security.

Advantages of the Network Secure Gateway • Users can access all resources and systems remotely anytime and from anywhere over the internet. • Use the same systems, applications. • Data doesn’t have to leave the organisation, less data protection issues. • Consistent Environment for users. • Can Save time and money.

Advantages of the Network Secure Gateway continued…… • No issues with different version types with software. • Less chance of Users losing work. • Users can create and test resources on the Network from home. • MIS system can be accessed from home for updating, completing or generating reports.

Advantages of the Network Secure Gateway continued…… • Integrated with AD using your Standard. Network Username and Password. • Using simple encrypted dual factor. Authentication for selected resources. • Built in Threshold of PC’s available feature. • Many other built in features.

Advantages of the Network Secure Gateway continued…… • Users could work from home if this was necessary (extreme weather or Illness etc. ) • Organisation has better control over what resources are available and when.

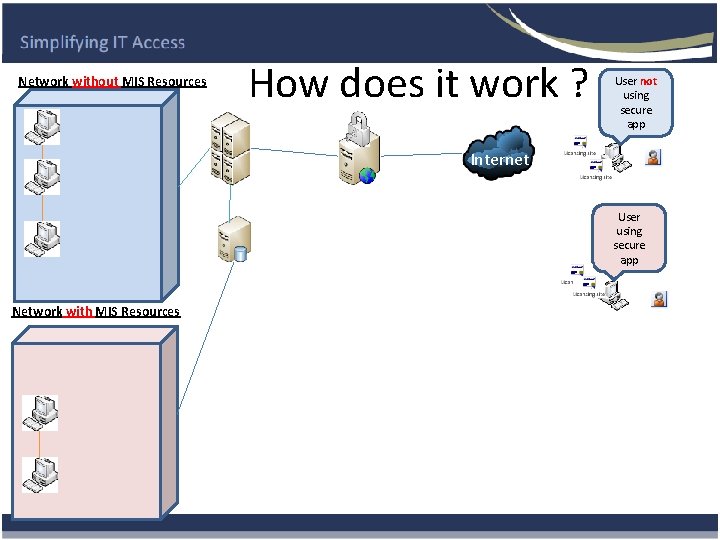
Network without MIS Resources How does it work ? User not using secure app Internet User using secure app Network with MIS Resources

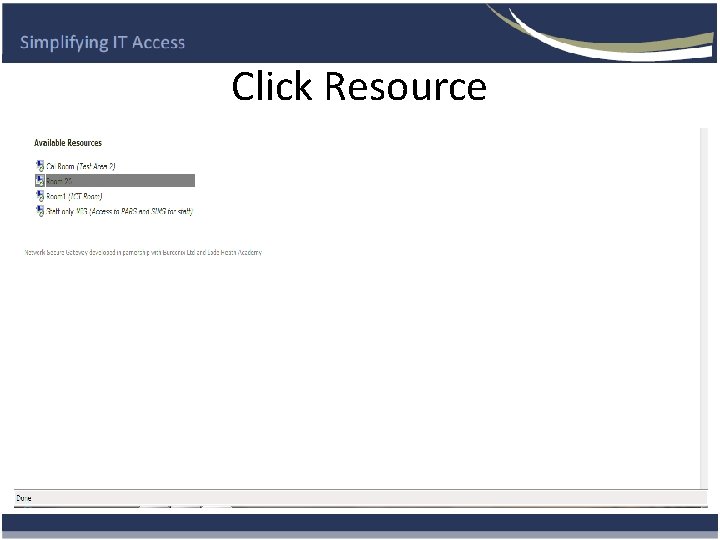
How does it work without Secure App ? • The user goes to the organisations Network Secure Gateway Login Page. • Logs in using there network username password. • Selects resource (PC or Group of PC’S) and Logs in if required. Same username and password.

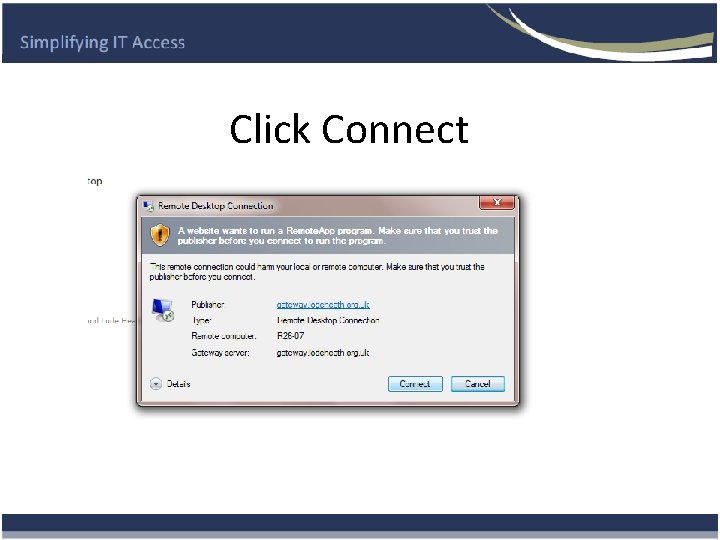
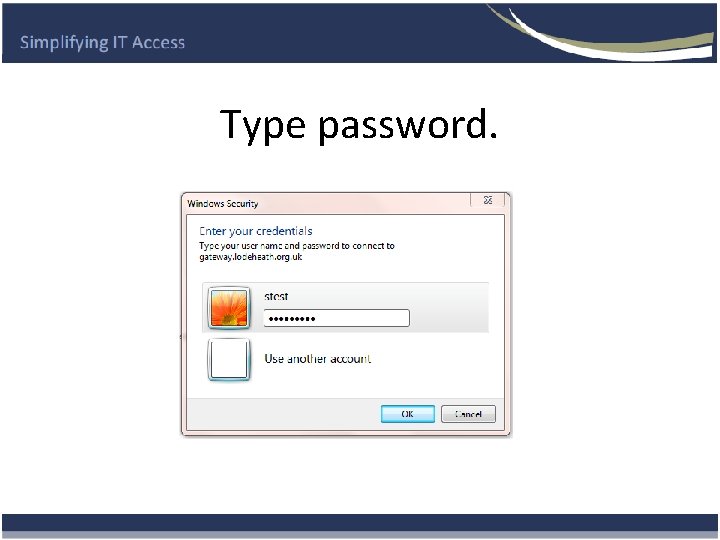
How does it work using the Secure App ? • The user double clicks the Network Secure App and this loads the Gateway Login Page. • The App also does encrypted first factor Authentication. • User logs in using there network username password. (second factor Authentication) • Selects resource (PC or group of PC’S) and Logs in if required. Same username and password.

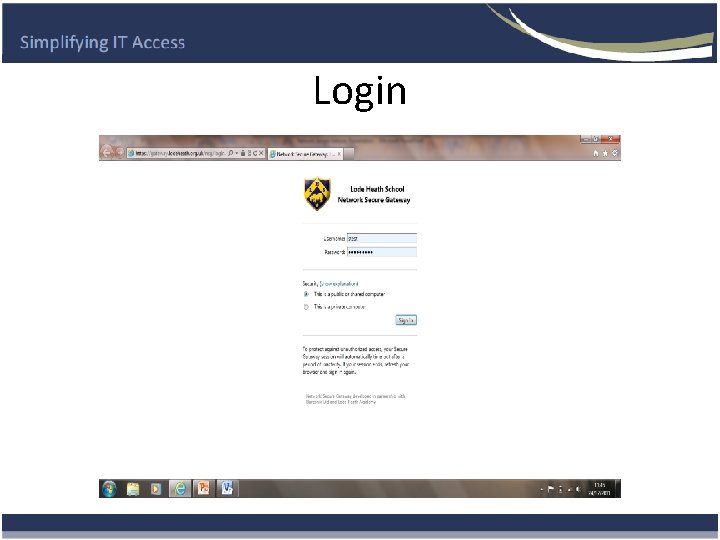
Login

Click Agree

Click Resource

Click Connect

Type password.

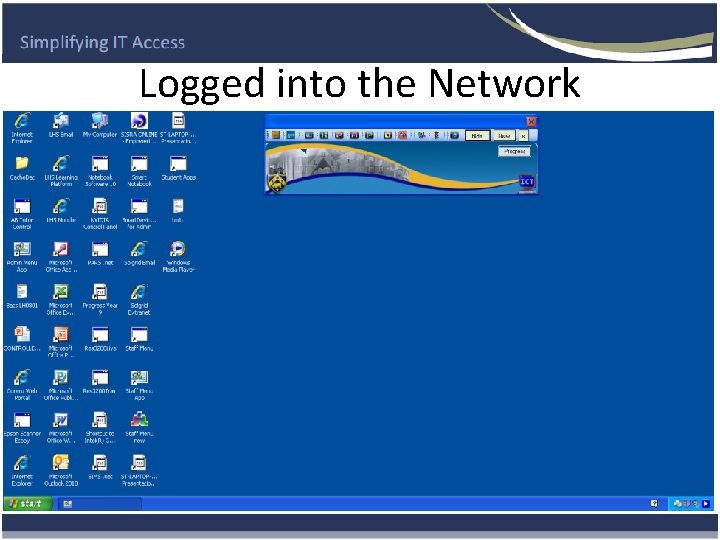
Logged into the Network

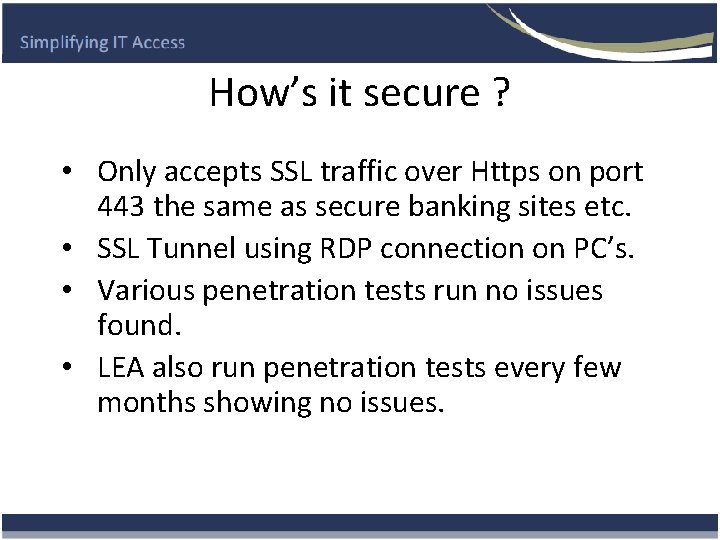
How’s it secure ? • Only accepts SSL traffic over Https on port 443 the same as secure banking sites etc. • SSL Tunnel using RDP connection on PC’s. • Various penetration tests run no issues found. • LEA also run penetration tests every few months showing no issues.

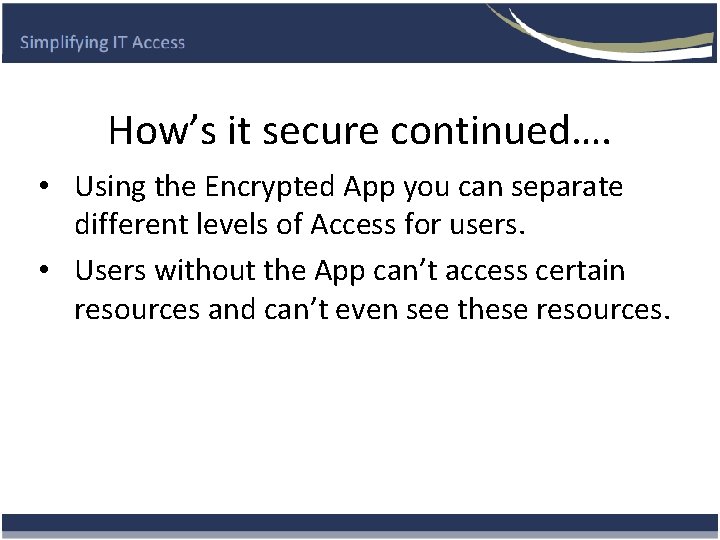
How’s it secure continued…. • Using the Encrypted App you can separate different levels of Access for users. • Users without the App can’t access certain resources and can’t even see these resources.

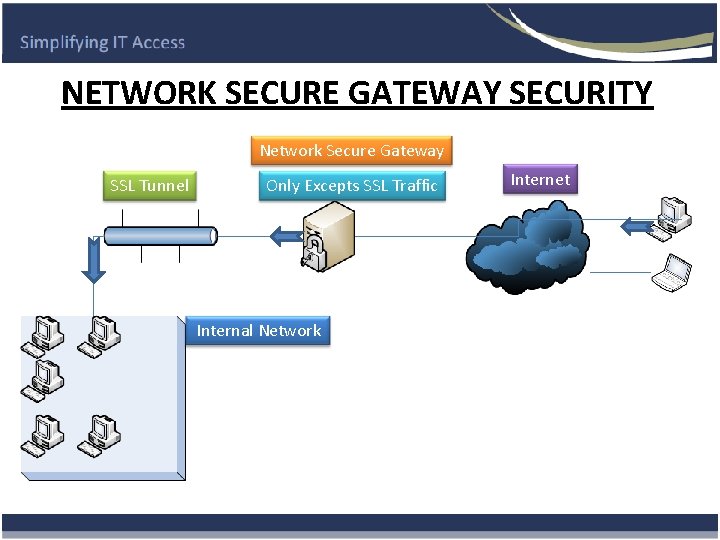
NETWORK SECURE GATEWAY SECURITY Network Secure Gateway SSL Tunnel Only Excepts SSL Traffic Internal Network Internet

Overview • Secure Remote access to everything on your Network. • Dual factor Encrypted Authentication where required. • Simple for users to access. • You control who accesses what and when.