Gateway Security Devices CSH 6 Chapter 26 Gateway









![What is a Proxy Server? Ø “[An] application that breaks the connection between sender What is a Proxy Server? Ø “[An] application that breaks the connection between sender](https://slidetodoc.com/presentation_image/1210c2da74d5f0912b816f6e148936a0/image-19.jpg)




























- Slides: 64

Gateway Security Devices CSH 6 Chapter 26 “Gateway Security Devices” David Brussin & Justin Opatrny 1 Copyright © 2015 M. E. Kabay. All rights reserved.

Topics ØIntroduction ØHistory & Background ØNetwork Security Mechanisms ØDeployment ØNetwork Security Device Evaluation 2 Copyright © 2015 M. E. Kabay. All rights reserved.

Introduction ØOverview ØChanging Security Landscape ØRise of Gateway Security Device ØApplication Firewall: Beyond the Proxy 3 Copyright © 2015 M. E. Kabay. All rights reserved.

Overview Ø What is a Firewall? Ø Firewall rapidly accepted as perimeter security device q. Even CEOs know about firewalls Ø Original conception q. Allow explicitly allowed communications q. Deny all others Ø Allowed paths became weakest links q. Involve different (and insecure) protocols q. Firewalls evolved to compensate for weak security in allowed protocols Ø Successful use of firewalls depends on proper configuration 4 Copyright © 2015 M. E. Kabay. All rights reserved.

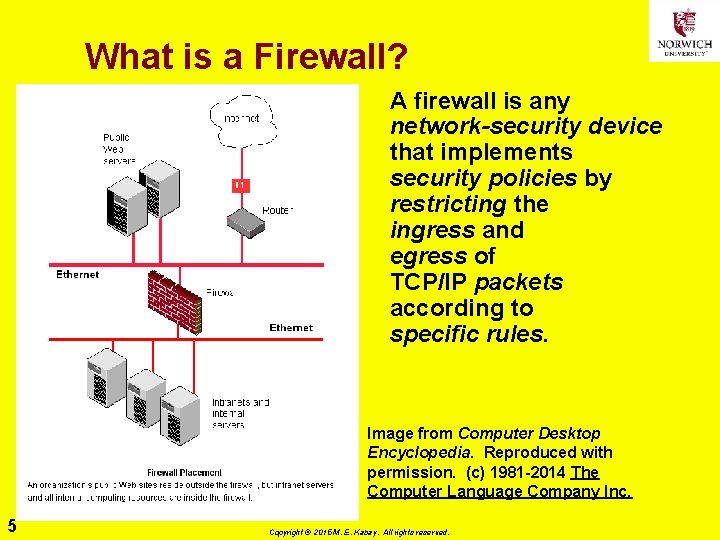
What is a Firewall? A firewall is any network-security device that implements security policies by restricting the ingress and egress of TCP/IP packets according to specific rules. Image from Computer Desktop Encyclopedia. Reproduced with permission. (c) 1981 -2014 The Computer Language Company Inc. 5 Copyright © 2015 M. E. Kabay. All rights reserved.

Changing Security Landscape (1) 6 Ø Pervasive changes in network architectures q. Applications & work patterns require more open interactions q. Perimeter less clearly defined q. Increased centralization (e. g. , servers) q. Increased scrutiny of protocol traffic Ø Borders dissolving q. Outsourcing, hosted applications (e. g. , CRM, e-mail, external storage, Web apps, cloud computing) q. Enterprise applications linked to customer & 3 rd party applications Copyright © 2015 M. E. Kabay. All rights reserved.

Changing Security Landscape (2) 7 Ø Mobility (physical and logical) q. Employees work from home, while traveling q. Use kiosks, home systems, phones q. Opens networks to attacks via compromised client systems Ø Regulatory compliance q. Increased demands for security q. In USA, laws such as Gramm-Leach-Bliley (GLB), Health Information Portability and Accountability Act (HIPAA), and Sarbanes. Oxley (SOX) force protection of personally identifiable information (PII) Copyright © 2015 M. E. Kabay. All rights reserved.

Rise of Gateway Security Devices (GSDs) (1) Ø Firewalls originally defined allowed paths for access (ports) Ø Evolved into GSD to provide many security functions as shown below Ø Gateway security device capabilities: q. Processing power has increased q. Now see multifunction platforms; e. g. , rolebased access controls (RBAC) Ø Enterprise directory integration: q. Lightweight Directory Access Protocol (LDAP) infrastructure for authorization 8 Copyright © 2015 M. E. Kabay. All rights reserved.

Rise of GSDs (2) Ø Unified threat management: q. Perimeter-based antivirus, antimalware, antispyware, antispam q. Intrusion detection & intrusion prevention q. Content control Ø Content control & data leakage prevention: q. Deep inspection of packets in protocols such as HTTP, SMTP, IM q. Dictionary-based and URL-list filters q. Requiring encryption for sensitive data Ø Archive & discovery q. Message security & records for legal compliance 9 Copyright © 2015 M. E. Kabay. All rights reserved.

Application Firewall: Beyond the Proxy Ø Most significant allowed paths for most firewalls: Web access q. HTTP & HTTPS (HTTP with SSL) Ø Increased complexity q. Rich-client applications; e. g. , using AJAX üAsynchronous Java. Script & XML üAKA remote scripting üAllows user to interact a field at a time instead of a page at a time q. Firewall now has to guard against misconfiguration & vulnerability in custom Web applications running over allowed HTTP 10 Copyright © 2015 M. E. Kabay. All rights reserved.

History & Background Ø Changing Network Models q. Mainframe q. Client/Server q. Web Ø Firewall Architectures Ø Firewall Platforms Cross References in CSH 6: • Overview of computing and security history, see Chapter 1. • Introduction to data communication basics, see Chapter 5. • Introduction to local area networks, see Chapter 25. 11 Copyright © 2015 M. E. Kabay. All rights reserved.

Changing Network Models (1) Ø Shift from mainframe-centric to LAN-centric to Internetcentric computing through 1980 s through 1990 s & 2000 s Ø Mainframe architectures q. Glass house approach q. Solitary systems with hardwired dumb or smart terminals (green screens) q. Multiple mainframes linked within single data centers q. WANs used leased lines (telephony) Ø Virtualization began on mainframes q. IBM MVS/VM q. Strict partitions, mandatory access control 12 Copyright © 2015 M. E. Kabay. All rights reserved.

Changing Network Models (2) Ø Client/Server (1980 s, early 1990 s) q. Midrange servers running Unix, Net. Ware, OS/2, Windows NT q. Rapid increase in # & type of connections q. Switch to PCs with local processing Ø Security perimeter expanded q. Out of data center to desktop q. WANs expanded beyond enterprise Ø Application security expanded across systems q. Multiple allowed paths q. Multiple possible attack paths 13 Copyright © 2015 M. E. Kabay. All rights reserved.

Changing Network Models (3) Ø Web q. HTTP/HTML started expanding 1989 q. Commercial Internet exploded starting in 1993 when. com opened in big way q. Web applications replaced fat clients Ø Mobile code complicated security issues q. Asynchronous Java. Script & XML (AJAX) q. Many customized & ad hoc protocols carry data over http q. Firewalls increasingly focused on HTTP traffic 14 Copyright © 2015 M. E. Kabay. All rights reserved.

Firewall Architectures ØAccess Control List ØPacket Filtering ØStateful Inspection ØApplication-Layer Gateway ØMultifunction Hybrid ØHost Environment Context 15 Copyright © 2015 M. E. Kabay. All rights reserved.

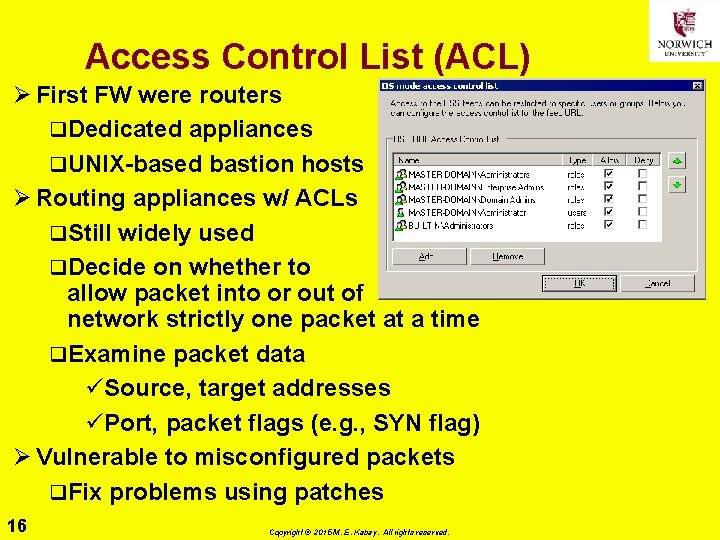
Access Control List (ACL) Ø First FW were routers q. Dedicated appliances q. UNIX-based bastion hosts Ø Routing appliances w/ ACLs q. Still widely used q. Decide on whether to allow packet into or out of network strictly one packet at a time q. Examine packet data üSource, target addresses üPort, packet flags (e. g. , SYN flag) Ø Vulnerable to misconfigured packets q. Fix problems using patches 16 Copyright © 2015 M. E. Kabay. All rights reserved.

Packet Filtering 17 Ø Pure packet-filtering FWs no longer common q Appliance or host-based q Use ACLs to apply policies q Typically provide logging q Support user-based authorization q Include intrusion detection & alerts Ø Strengths q Ideally suited to load-balanced, high-availability environments q Can automatically share load among devices Ø Weaknesses q Lack context information q Underlying operating system vulnerabilities affect security of FW Ø Packet filtering has moved to non-security appliances such as load balancers, Web caches, switches Copyright © 2015 M. E. Kabay. All rights reserved.

Stateful Inspection Ø HTTP is a connectionless protocol q A communications architecture that does not require the establishment of a session between two nodes before transmission can begin. [Computer Desktop Encyclopedia] Ø Stateful-inspection FW maintain connection information locally q Table in memory stores packet header data q Compare current packet info to session q Identify some abnormal packets used in attacks q But attacks that use uninspected portions can succeed Ø Fast mode reduces inspection once connection opened successfully – strongly discouraged Ø Performance can be good q Provide load balancing & failover with out-of-band data synchronization among devices running in parallel 18 Copyright © 2015 M. E. Kabay. All rights reserved.
![What is a Proxy Server Ø An application that breaks the connection between sender What is a Proxy Server? Ø “[An] application that breaks the connection between sender](https://slidetodoc.com/presentation_image/1210c2da74d5f0912b816f6e148936a0/image-19.jpg)
What is a Proxy Server? Ø “[An] application that breaks the connection between sender and receiver. All input is forwarded out a different port, closing a straight path between two networks and preventing a cracker from obtaining internal addresses and details of a private network. ” 19 Image and text from Computer Desktop Encyclopedia. Reproduced with permission. (c) 1981 -2014 The Computer Language Company Inc. Copyright © 2015 M. E. Kabay. All rights reserved.

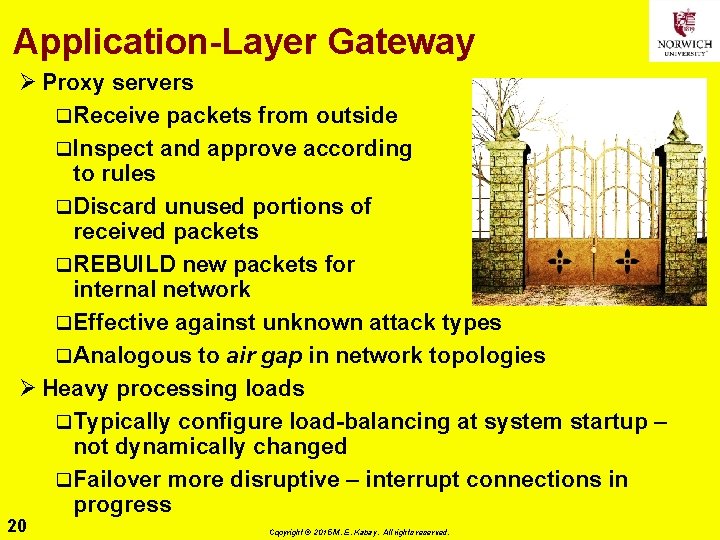
Application-Layer Gateway Ø Proxy servers q. Receive packets from outside q. Inspect and approve according to rules q. Discard unused portions of received packets q. REBUILD new packets for internal network q. Effective against unknown attack types q. Analogous to air gap in network topologies Ø Heavy processing loads q. Typically configure load-balancing at system startup – not dynamically changed q. Failover more disruptive – interrupt connections in progress 20 Copyright © 2015 M. E. Kabay. All rights reserved.

Multifunction Hybrid Ø Most commercial firewalls today are hybrids Ø Apply stateful inspection techniques to most protocols Ø Use application-layer gateway proxies for specific protocols (e. g. , HTTP, SMTP) Ø Can shift to fast mode for stateful inspection once connection established 21 Copyright © 2015 M. E. Kabay. All rights reserved.

Host Environment Context Ø Host-based security more granular than perimeter-based devices q. Define specific applications / services q. Regulate types of data allowed per process q. Use sandbox or virtual machine to test code Ø FWs can run on host or communicate with host q. Use protocols such as Universal Plug and Play (UPn. P) for data exchange q. E. g. , evaluate processes running when packet inspection being performed q. Open and close specific ports as function of need 22 Copyright © 2015 M. E. Kabay. All rights reserved.

Firewall Platforms ØRouting ØHost Based ØAppliance ØPersonal and Desktop Agent ØVirtual ØEmbedded 23 Copyright © 2015 M. E. Kabay. All rights reserved.

FW Platforms: Routing Ø Router q. Heart of TCP/IP networks q. Forwards packets from one network to another q. Internal routing tables allow determination of where to forward each incoming packet q. Destination address determines where outgoing packets are sent q. Current load on different connections determine which line to use for each packet or group of packets Ø ACL allow / deny statements restrict packets Ø Hardware modules (blades) can share processing to increase throughput (bandwidth) 24 Copyright © 2015 M. E. Kabay. All rights reserved.

FW Platforms: Host-Based Ø Dedicated server-based firewalls provide additional functions Sorry, folks: entry forbidden q. Protocol traffic inspection q. Contextual traffic inspection q. Comprehensive logging & alerts q. Air-gap proxy servers Ø Typically run on Unix or Windows q. Often have special hardening (security features) such as modifications of network stack q. Consequences of increased complexity include increased bugs, vulnerabilities 25 Copyright © 2015 M. E. Kabay. All rights reserved.

FW Platforms: Appliance Ø Extension of host-based FW: put FW into its own specialized processor w/ no other functions Ø Total control of operating system q. Control versions, patches specifically for functionality of FW q. Prevent unauthorized, unwanted changes Ø Soft appliances q. Vendor specifies exact characteristics of hardware for user to buy & install q. Provides full software – boot from vendor-supplied disk 26 Copyright © 2015 M. E. Kabay. All rights reserved.

FW Platforms: Personal and Desktop Agent Ø Software FW q. Host-based systems q. Commonplace today q. Running on workstations q. Integrated systems often include antivirus functions Ø Evolve into host intrusionprevention system (H-IPS) Ø Require more maintenance than network-based FW q. Constant signature updates q. Regular patches of client software q. Difficulties for management in wide-area networks 27 Copyright © 2015 M. E. Kabay. All rights reserved.

FW Platforms: Virtual Ø FW running on virtual machines under hypervisor (e. g. , VMware, Xen) Ø Protect virtual & physical networks Ø Complex management issues q. Mapping virtual networks q. Virtual appliances require exact compliance with vendor specifications 28 Copyright © 2015 M. E. Kabay. All rights reserved.

FW Platforms: Embedded Ø Web-server-based plugins q. Create customized application FWs q. Scale to support consumers, small/medium business requirements Ø Integrate tightly with Web server q. Use downloaded signatures q. Develop specific protection for specific applications q. Allows contextual scanning unavailable to application gateways Ø Often become all-in-one security appliances q. Integrate FW, network intrusion-prevention, antivirus…. 29 Copyright © 2015 M. E. Kabay. All rights reserved.

Network Security Mechanisms Ø Recognition of value of network security mechanisms q. IT managers have increased expertise q. Increasingly recognized need q. Often have unrealistic expectations Ø Next slides: q. Basic Roles q. Personal & Desktop Agents q. Additional Roles 30 Copyright © 2015 M. E. Kabay. All rights reserved.

Basic Roles ØAllowed Paths ØIntrusion Detection ØIntrusion Prevention/Response 31 Copyright © 2015 M. E. Kabay. All rights reserved.

Allowed Paths Ø GSDs create physical perimeters Ø Also create logical perimeter extending within protected networks Ø Constitute least-privilege gateway Ø Mechanisms for regulating access q Tunneling: Transmitting data structured in one protocol within the format of another. ” (Computer Desktop Encyclopedia) q Antispoofing: preventing forged network addresses (e. g. , blocking inbound packets with internal addresses and vice versa; blocking packets with originating addresses in reserved address-space) q Network Address Translation (NAT): see following slide 32 Copyright © 2015 M. E. Kabay. All rights reserved.

Network Address Translation (NAT) Ø Masks address of internal nodes q Private address space accessed by internal tables q Limits determination of internal network size & topology q Restricts access to specific endpoints Ø Static NAT q Manual, permanent assignment of IP address to each internal node Ø Dynamic NAT q Pool of addresses assigned as required Ø Port Address Translation (PAT) q AKA Nat overloading q Different TCP port # used for each client session 33 Copyright © 2015 M. E. Kabay. All rights reserved.

Intrusion Detection Ø Alerts may be good or bad q. Appropriate deployment of alarms over new attacks & actual intrusions good q. Torrent of excessive information about routine attempted attacks → shutoff Ø Internet hosts probed & attacked within hours of being put online Ø Observing which GSDs are reporting attacks can signal failure of upstream devices (more external perimeter defenses) q. Can provide early warning of impending security system failure 34 Copyright © 2015 M. E. Kabay. All rights reserved.

Intrusion Prevention & Response (1) Several types of reaction to intrusions: Ø Connection termination: q. Stop traffic using RST (connection reset) q. On User Datagram Protocol (UDP), can use packet dropping to terminate connection q. Good for known attacks on allowed paths q. Can allow denial of service q. Not useful in preventing unknown types Ø Dynamic rule modification q. Target specific originating addresses q. But opens even more to denial of service 35 Copyright © 2015 M. E. Kabay. All rights reserved.

Intrusion Prevention & Response (2) Ø System-level actions q Monitor for compromise q Firewall deactivation q But be sure that shutting down FW STOPS traffic, not leaves it open! Ø Application inspection q Check for known protocol-specific exploits q E. g. , use signatures to spot HTTP-specific attacks such as cross-site scripting (XSS) & SQL query injection attacks Ø Antimalware q Spot malware in transit q Hijack Web session to divert download to quarantine 36 Copyright © 2015 M. E. Kabay. All rights reserved.

Personal & Desktop Agents Ø Individual hosts (workstations) q. Must be protected individually q. Can use sophisticated contextual scanning Ø End Point Protection q. Mobile devices (laptop, phone) become extensions of network protection profile q. Network location: Rules may vary depending on whether device is inside or outside perimeter q. Application access: restrict inbound and outbound access depending on which program is running q. Hybrid protections: spot particular patterns tied to known attack scenarios 37 Copyright © 2015 M. E. Kabay. All rights reserved.

Additional Roles ØEncryption ØAcceleration ØContent Control ØIPv 6 38 Copyright © 2015 M. E. Kabay. All rights reserved.

Encryption (1) 39 Ø Many GSDs support encryption q. Important because encrypted packets could contain dangerous payload Ø Inspection q. Termination: packet decrypted at perimeter üContents inspected üMay be re-encrypted for transmission to internal end-point q. Alternative is passive (simultaneous) decryption using escrowed keys üBut original encrypted packet continues to target while FW decrypts contents üThus there are issues of synchronization Copyright © 2015 M. E. Kabay. All rights reserved.

Encryption (2): VPNs Ø Virtual Private Networks Ø Extend security perimeter to include remote systems Ø Increasingly popular Ø But should consider special rules for VPN clients q. May not be owned by organization q. Need to establish clean operating environment q. Especially important to prevent malware from entering corporate systems See CSH 6 Chapter 32 for more about VPNs 40 Copyright © 2015 M. E. Kabay. All rights reserved.

Acceleration Ø SSL (Secure Sockets Layer) q. Most frequently used encryption protocol q. Defines HTTPS q. Widely used on Web for e-commerce Ø Many high-volume servers equipped with dedicated encryption appliances q. Manage throughput q. Avoid letting encryption/decryption become bottleneck on processing 41 Copyright © 2015 M. E. Kabay. All rights reserved.

Content Control (1) Ø Content filtering q. Policy enforcement q. Address-based filtering can block some sites (sometimes by mistake) q. Keyword scanning has many false positives Ø Antimalware q. Pervasive element of all networks and workstations q. Includes scans for harmful e-mail attachments, spam q. Often uses appliances on network side to speed throughput 42 Copyright © 2015 M. E. Kabay. All rights reserved.

Content Control (2) See CSH 6 Chapter 17 for more about mobile code Ø Active Content q. Flash, Quick. Time, Active. X, VBScript, Java. Script q. Many GSDs scan for and block such code q. Others use signatures and sandboxes to screen hostile code Ø Caching q. Proxy servers keep copies of frequently-used items q. Typically for HTTP, FTP, streaming media Ø Policy Enforcement q. Can scan e-mail for sensitive keywords q. Can require encryption for specific communications 43 Copyright © 2015 M. E. Kabay. All rights reserved.

IPv 6 (1) Ø Successor to IPv 4 (current standard) Ø Support & compatibility q. GSDs must support appropriate protocols üNeighbor discovery (ND) üRouter solicitation/advertisement (RS/RA) üMulticast listener discovery (MLD) q. Stateless autoconfiguration üIPv 6 nodes may assign their own addresses üCan discover their own routers using NS, RS/RA – but may break user/address audit trail (use MAC addresses for hardware nodes) 44 Copyright © 2015 M. E. Kabay. All rights reserved.

IPv 6 (2) Ø Address shortage resolved q. IPv 4 address space = 232 ≈ 109 q. IPv 6 address space = 2128 ≈ 1038 q. Ratio is IPv 6: IPv 4: : solar system: stamp! Ø Be careful about IPv 6 traffic tunneling through IPv 4 infrastructure q. E. g. , antispoofing benefits of IPv 6 lost when using IPv 4 -to-IPv 6 gateways 45 Copyright © 2015 M. E. Kabay. All rights reserved.

IPv 6 (3) Ø NAT not intended to survive transition q. IPv 6 may expose IPv 4 nodes when NAT removed Ø Single IP address associated with specific device (node) q. Can carry address from internal network to external network q. Example: laptop starts session in office but moves to café – same IP address q. Will need new developments to cope with device-specific IPv 6 addresses 46 Copyright © 2015 M. E. Kabay. All rights reserved.

Deployment ØScreened Subnet FW Architectures ØGateway Protection Device Positioning ØManagement & Monitoring Strategies 47 Copyright © 2015 M. E. Kabay. All rights reserved.

Screened Subnet FW Architectures Ø Service Networks q New design strategy: don’t lump Web, DNS, e-mail into single network (NW) q Break functional components into separate, protected NW q Defines service NW with their own security configurations, policies Ø Redirect Back-End Traffic Through FW q Just because FW decrypts packet doesn’t mean it’s necessarily safe q Reroute decrypted packet through FW before allowing it to reach internal destination 48 Copyright © 2015 M. E. Kabay. All rights reserved.

Gateway Protection Device Positioning (1) Ø Encrypting protocols (e. g. , SSL & IPSec) can pose problems q. Bandwidth chokepoints due to processing requirements q. Ideally, deploy GSDs where there is little encrypted traffic Ø Two major approaches (details on following slides): q. Put GSDs inline q. Avoid encrypted traffic 49 Copyright © 2015 M. E. Kabay. All rights reserved.

Gateway Protection Device Positioning (2) Ø Inline q Configure span port to replicate data from one or more switch ports to monitoring port q Problems üCan overload the monitor (too many inputs) üPassive devices don’t offer protection, only alerts (so dangerous packets already gone) q Thus should put GSD inline with traffic üProvides choke point (but device can have wire speed bandwidth) üAllows active prevention (blockage) üBut be sure to configure properly to avoid Do. S 50 Copyright © 2015 M. E. Kabay. All rights reserved.

Gateway Protection Device Positioning (3) Ø Avoid encrypted traffic q. Encrypted packets defeat GSDs q. Therefore GSD must evaluate packets on unencrypted side of encrypted connection üE. g. , on backside of SSL terminator üOn unencrypted side of VPN connection q. Implies likelihood of more than one GSD 51 Copyright © 2015 M. E. Kabay. All rights reserved.

Management & Monitoring Strategies Ø Monitoring Ø Policy Ø Auditing/Testing Ø Maintenance Ø Logging & Alerting Ø Secure Configurations Ø Disaster Recovery 52 Copyright © 2015 M. E. Kabay. All rights reserved.

Monitoring Ø Device Health (may be part of GSD system) q Processor utilization q Available RAM q Number of connections q May have to use SNMP, RMON tools q Restrict access by monitoring tools q Examine trends Ø Availability q Periodically test functionality q ping, traceroute Ø Integrity q Ensure that operating code cannot be / has not been modified without authorization q Checksums, utility scanner…. 53 Copyright © 2015 M. E. Kabay. All rights reserved.

Policy (1) Ø GSDs instantiate policy! q. Look for centralized management consoles Ø Firewall-allowed paths q. Every allowed path must relate to specific required external service q. Start with deny-all basis and add allowed paths q. To degree possible, identify endpoints in rules q. Keep track of direction of connections (inbound vs outbound) 54 Copyright © 2015 M. E. Kabay. All rights reserved.

Policy (2) Ø Complexity of GSD policies q. Standard FW rules are simple Boolean logic q. But GSDs may require multistage rules üOrigination addresses üMessage contents üAttachments virus-free Ø Change management q. Must control & track policy changes & implementation q. Can thus backout mistakes q. Audit trail important for security incident analysis 55 Copyright © 2015 M. E. Kabay. All rights reserved.

Policy (3) Ø Secondary validation q. Making changes can be easy q. But complex systems can result in unexpected errors q. Having second network / system admin check proposed change helpful üAvoid errors üShare knowledge üEnforce security principle of shared responsibility, checks-andbalances 56 Image from http: //www. policynl. ca/policydevelopment/images/policy-development-life -cycle. png Copyright © 2015 M. E. Kabay. All rights reserved.

Auditing/Testing Ø How do we know our GSDs are working? q. Auditing: do the actual rules comply with the rules we claim to want according to policy? q. Assessment: are the rules working as we want / expect? Ø Vulnerability assessment (VA) q. Walkthrough, tools for examining parameters Ø Penetration (“Pen”) testing Actually trying to break through the GSD See CSH 6 Chapter 46 for VA/Pen Testing & Chapter 54 for audits 57 Copyright © 2015 M. E. Kabay. All rights reserved.

Maintenance Ø Patching – see CSH 6 Chapter 40 Ø Pattern updates q. Automatic updates a must to get files promptly q. But production environment cannot automatically trust patches üHave monitor-mode to see if new signatures work properly & safely üThen enable for action as approved by QA team q. Alternative is to install on completely separate non-production systems for testing 58 Copyright © 2015 M. E. Kabay. All rights reserved.

Logging & Alerting Ø Logging essential q Must be able to access data on allowed / denied packets q Record of system changes Ø Alert mechanisms q Configurable q Whom to alert? q How (e-mail? IM? Phone w/ robot voice? ) Ø Log files q Can eat up disk space q Plan for backups to cheaper media q May configure to exclude safe traffic q Need log file utilities to extract & format data 59 Copyright © 2015 M. E. Kabay. All rights reserved.

Secure Configurations Ø Ensure that GSDs are themselves secure against tampering, error Ø Define baseline secure configurations Ø Default configuration may be inadequate Ø Implied rules q. Must be made explicit & examined q. May modify or disable as required Ø Ancillary exposures q. Administrative console can reveal unsuspected functions, services q. Can disable unused functions, services 60 Copyright © 2015 M. E. Kabay. All rights reserved.

Disaster Recovery See CSH 6 Chapters 56 -59 Ø FW or GSD outage can cripple system or leave it wide open to attack Ø Fail-over/high availability q. May need to configure active/standby units üInstant cutover Ø Load-balancing configurations q. Provide better throughput q. Also serves for business continuity Ø Backup/restore q. Be sure all configuration scripts are backed up q. Be able to re-establish known-good configuration ASAP 61 Copyright © 2015 M. E. Kabay. All rights reserved.

Network Security Device Evaluation ØCurrent Infrastructure Limitations ØNew Infrastructure Requirements ØPerformance § 26. 5 provides ØManagement checklists for evaluating GDSs ØUsability ØPrice ØVendor Considerations ØManaged Security Service Providers 62 Copyright © 2015 M. E. Kabay. All rights reserved.

Will Firewalls Ever Be Perfect? 63 Copyright © 2015 M. E. Kabay. All rights reserved.

Now go and study 64 Copyright © 2015 M. E. Kabay. All rights reserved.