Secure Network Design Designing a Secure Local Area









- Slides: 27

Secure Network Design: Designing a Secure Local Area Network Case Study http: //www. sans. org/reading_room/whitepapers/bes tprac/designing-secure-local-area-network_853 1 IT 352 | Network Security |Najwa Al. Ghamdi

Introduction • In order to design and build a well-secured network many factors must be taken into consideration 1. Network topology and placement of hosts within the network 2. The selection of hardware and software technologies 3. The careful configuration of each component. 4. the issues in designing a secure Local Area Network (LAN) and some of the best

Introduction • Securing a LAN network should take care of 1. Securing the network topology which comprises the physical and logical design of the network; 2. securing the routers and switches which connect segments and hosts to form the network

Secure LAN Design Challenges 1. Securing the network from Internet launched attacks 2. Securing Internet facing web, DNS and mail servers 3. Containing damage from compromised systems, and preventing internally launched attacks 4. Securing sensitive and mission critical internal resources such financial records, customer databases, trade secrets, etc. 5. Building a framework for administrators to securely manage the network 6. Providing systems for logging and intrusion detection

Case study • we wish to secure a small to medium sized (under 500 hosts) TCP/IP based LAN which is connected to the Internet via broadband or other high speed connection. • We need for a reasonable amount of security because of mission critical records or proprietary information. 5 IT 352 | Network Security |Najwa Al. Ghamdi

Topology and Architecture • Topology is the physical and logical layout of the network. • On the physical side, we will need to 1. provide distribution to the offices or buildings where the users are located. 2. We will need to provide connectivity to the servers which comprise our intranet, to the Internet, and possibly to other company locations or business partners, remote users connecting via telephone lines, etc. 6 IT 352 | Network Security |Najwa Al. Ghamdi

Topology and Architecture • The logical topology : technologies in how data is transferred in physical topology such (VLANs) and (VPNs). In laying out the logical topology we will need to 1. Decide what parts of the network are less trusted, and which are more? 2. Which groups of devices and users should be logically grouped together, and which should be separated? 7 IT 352 | Network Security |Najwa Al. Ghamdi

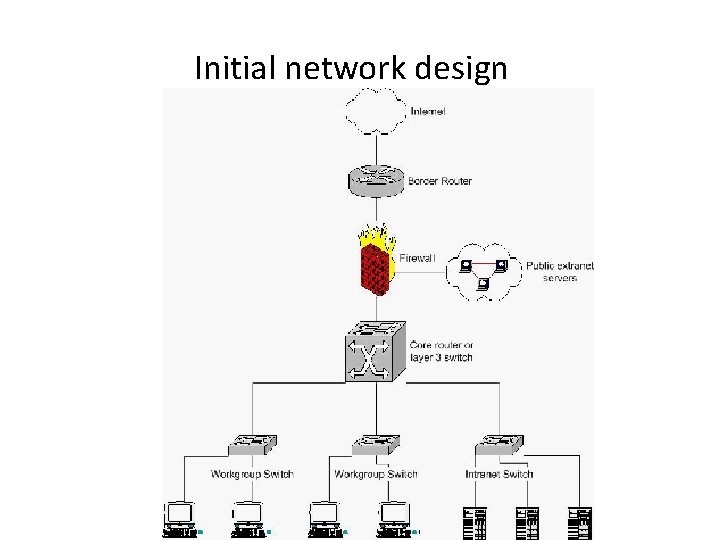
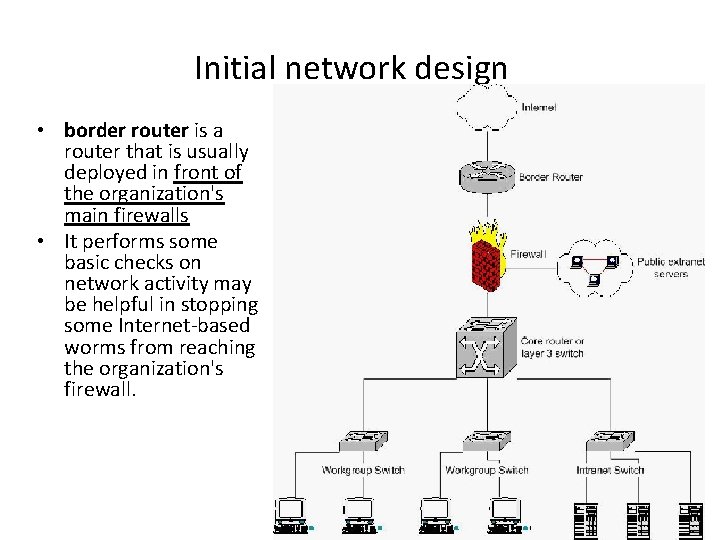
Initial network design

Initial network design • border router is a router that is usually deployed in front of the organization's main firewalls • It performs some basic checks on network activity may be helpful in stopping some Internet-based worms from reaching the organization's firewall.

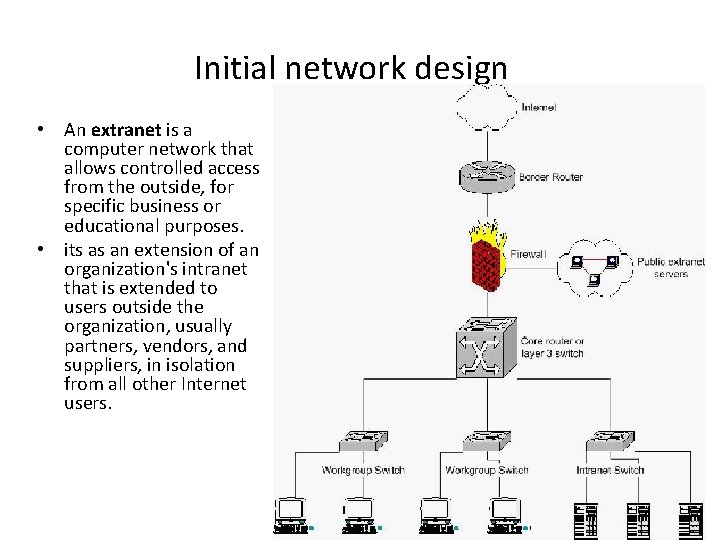
Initial network design • An extranet is a computer network that allows controlled access from the outside, for specific business or educational purposes. • its as an extension of an organization's intranet that is extended to users outside the organization, usually partners, vendors, and suppliers, in isolation from all other Internet users.

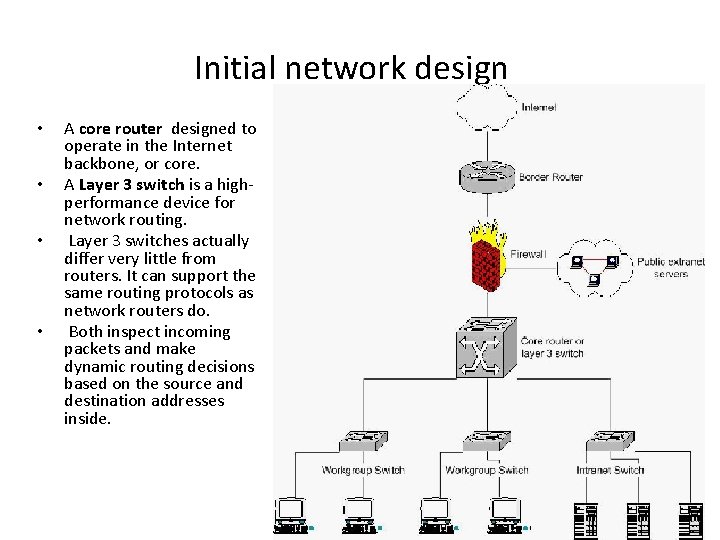
Initial network design • • A core router designed to operate in the Internet backbone, or core. A Layer 3 switch is a highperformance device for network routing. Layer 3 switches actually differ very little from routers. It can support the same routing protocols as network routers do. Both inspect incoming packets and make dynamic routing decisions based on the source and destination addresses inside.

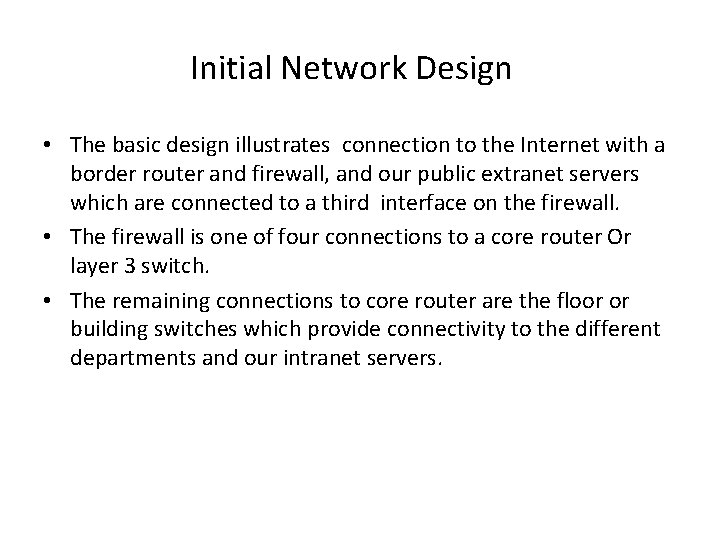
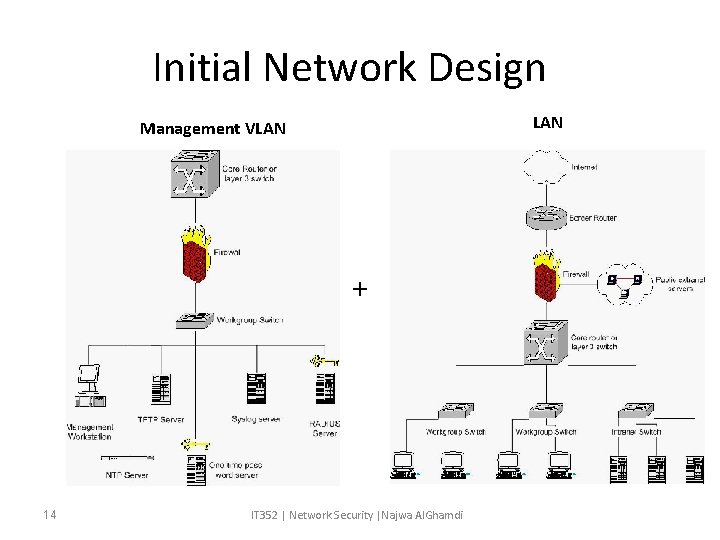
Initial Network Design • The basic design illustrates connection to the Internet with a border router and firewall, and our public extranet servers which are connected to a third interface on the firewall. • The firewall is one of four connections to a core router Or layer 3 switch. • The remaining connections to core router are the floor or building switches which provide connectivity to the different departments and our intranet servers.

Initial Network Design • This topology demonstrates how devices with similar functions and security profiles are grouped together – the public extranet servers, user workstations, and the intranet servers. • By creating separate security zones, we will be able to enforce security policy with the appropriate firewall rules and layer 3 access lists. • This design lacks is the infrastructure for managing network. • These servers will form the foundation of our network management and security, a separate management VLAN which is isolated from the rest of the network by a firewall will be created. • If this is not possible because of physical or other limitations, management should be encrypted via IPSEC.

Initial Network Design LAN Management VLAN + 14 IT 352 | Network Security |Najwa Al. Ghamdi

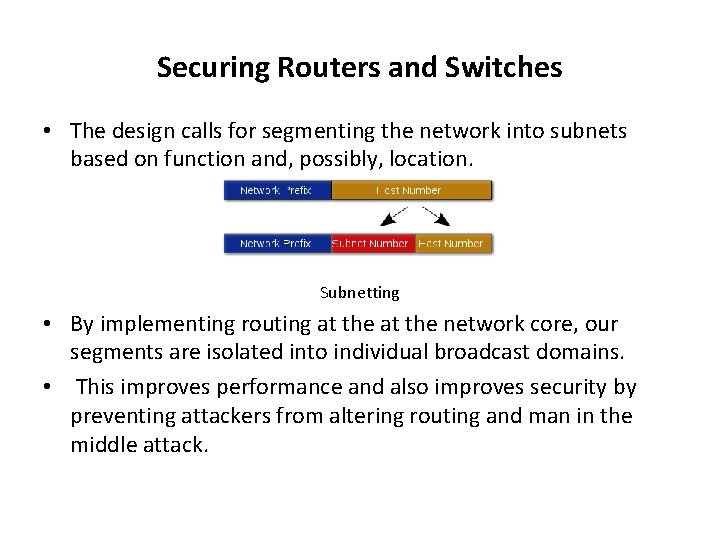
Securing Routers and Switches • The design calls for segmenting the network into subnets based on function and, possibly, location. Subnetting • By implementing routing at the network core, our segments are isolated into individual broadcast domains. • This improves performance and also improves security by preventing attackers from altering routing and man in the middle attack.

Securing Routers and Switches • Within each subnet the hosts are connected to an Ethernet switch. • A switch provides high performance and enhances security by making sniffing attacks difficult. • A hub is a less expensive alternative to a switch for layer 2 connectivity, though it is less desirable both from a performance and a security standpoint 16 IT 352 | Network Security |Najwa Al. Ghamdi

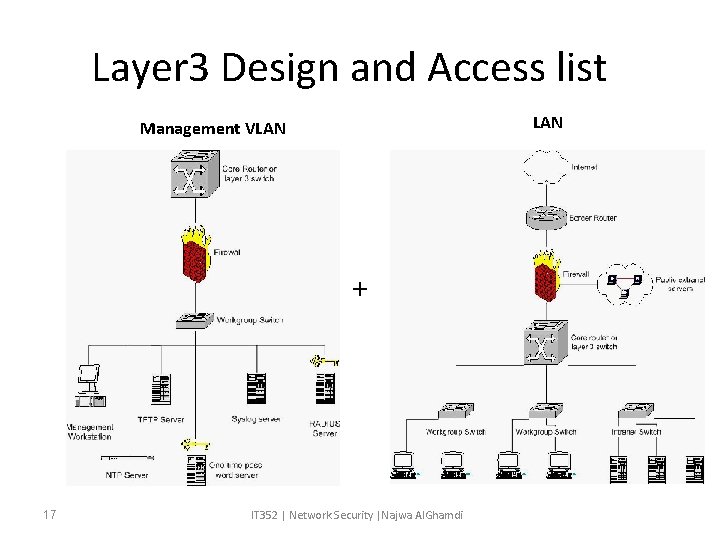
Layer 3 Design and Access list LAN Management VLAN + 17 IT 352 | Network Security |Najwa Al. Ghamdi

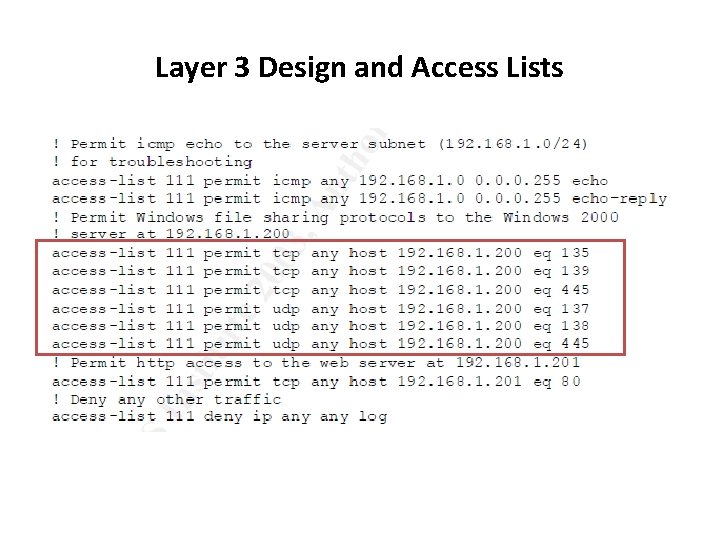
Layer 3 Design and Access Lists • layer 3 design is quite simple, with a central core router connecting the different production and management networks. • In core router , the access lists is implemented as a follows 1. For inbound traffic coming into a subnet, we will permit only appropriate incoming packets coming from certin IP addresses. 2. For outbound traffic : traffic is filtered to eliminate spoofing and minimize any malicious or illegitimate activities.

Layer 3 Design and Access Lists

Layer 3 Design and Access Lists • Example : we will want to filter traffic leaving each subnet to prevent spoofing. • The presence of incorrect source addresses could indicate either a misconfigured machine, or an attempt to launch a DOS or similar attacks. 20 IT 352 | Network Security |Najwa Al. Ghamdi

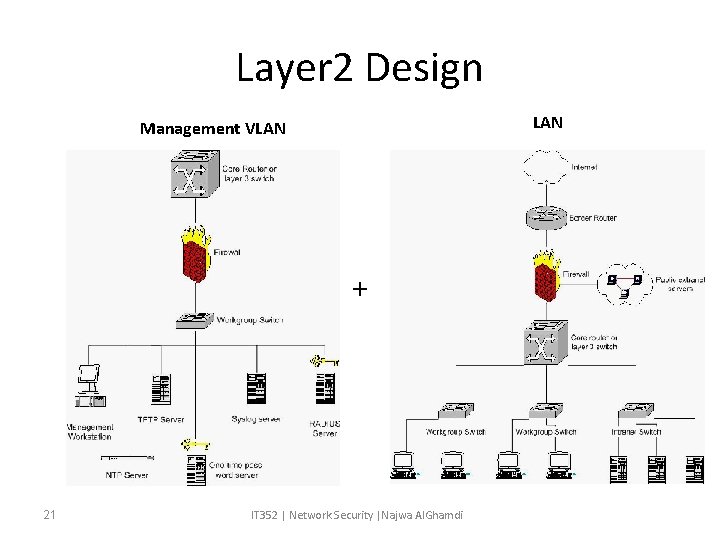
Layer 2 Design LAN Management VLAN + 21 IT 352 | Network Security |Najwa Al. Ghamdi

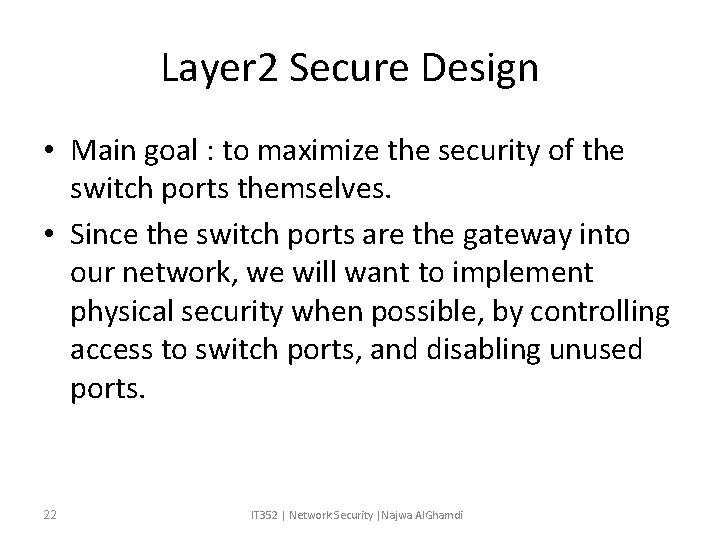
Layer 2 Secure Design • Main goal : to maximize the security of the switch ports themselves. • Since the switch ports are the gateway into our network, we will want to implement physical security when possible, by controlling access to switch ports, and disabling unused ports. 22 IT 352 | Network Security |Najwa Al. Ghamdi

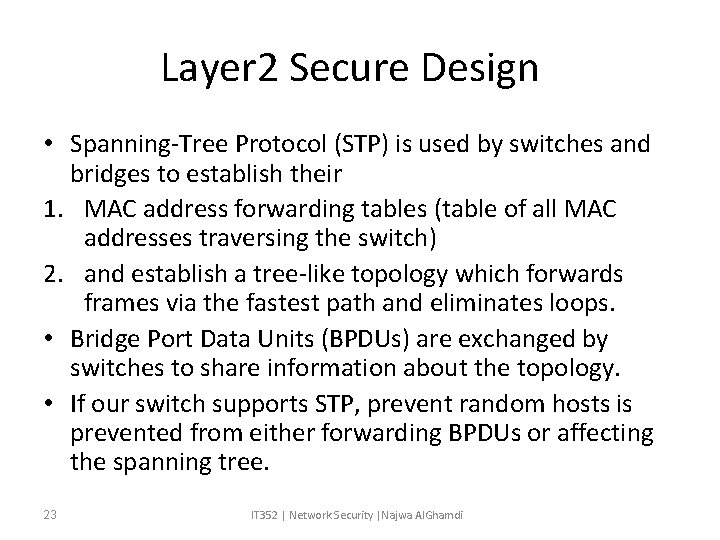
Layer 2 Secure Design • Spanning-Tree Protocol (STP) is used by switches and bridges to establish their 1. MAC address forwarding tables (table of all MAC addresses traversing the switch) 2. and establish a tree-like topology which forwards frames via the fastest path and eliminates loops. • Bridge Port Data Units (BPDUs) are exchanged by switches to share information about the topology. • If our switch supports STP, prevent random hosts is prevented from either forwarding BPDUs or affecting the spanning tree. 23 IT 352 | Network Security |Najwa Al. Ghamdi

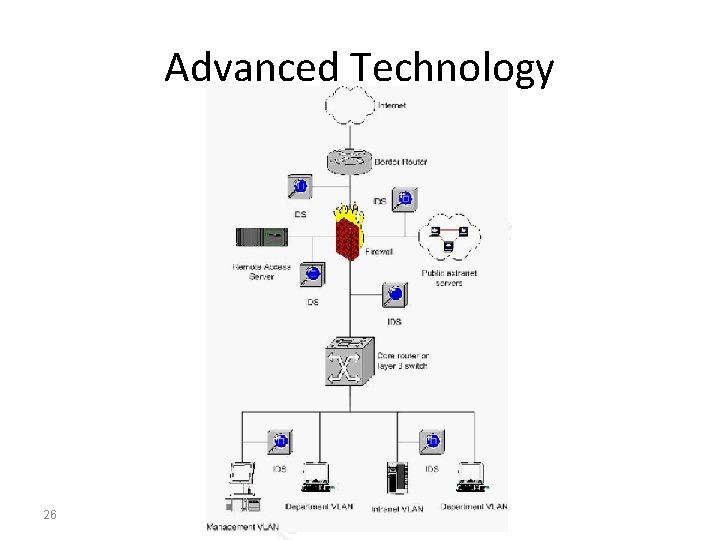
Advanced Technology • Intrusion Detection Systems (IDS) • Many experts would include IDS as part of the essential elements of securing any network. • Network IDS can alert the system administrator to attacks on the network in real time by 1. inspecting the traffic on the wire 2. and generating alerts if suspicious activities are identified 24 IT 352 | Network Security |Najwa Al. Ghamdi

Advanced Technology • Intrusion Detection Systems (IDS) • NIDS can be a 1. Regular computer running IDS software 2. Appliance type device running exclusive software 3. or even a specialized card built in to a switch or other • Once we have selected a NIDS for use in our network, we will need to place the sensors logically within the topology. 25 IT 352 | Network Security |Najwa Al. Ghamdi

Advanced Technology 26 IT 352 | Network Security |Najwa Al. Ghamdi

Advanced Technology • Suggest a technology to enhance security here. 27 IT 352 | Network Security |Najwa Al. Ghamdi