MALICIOUS OUTSIDER ACCIDENTAL DATA EXPOSURE MALICIOUS INSIDER 59










- Slides: 20



MALICIOUS OUTSIDER ACCIDENTAL DATA EXPOSURE MALICIOUS INSIDER 59% 23% 14% SOURCE OF BREACH DATA – 2013 -2017 – breachlevelindex. com



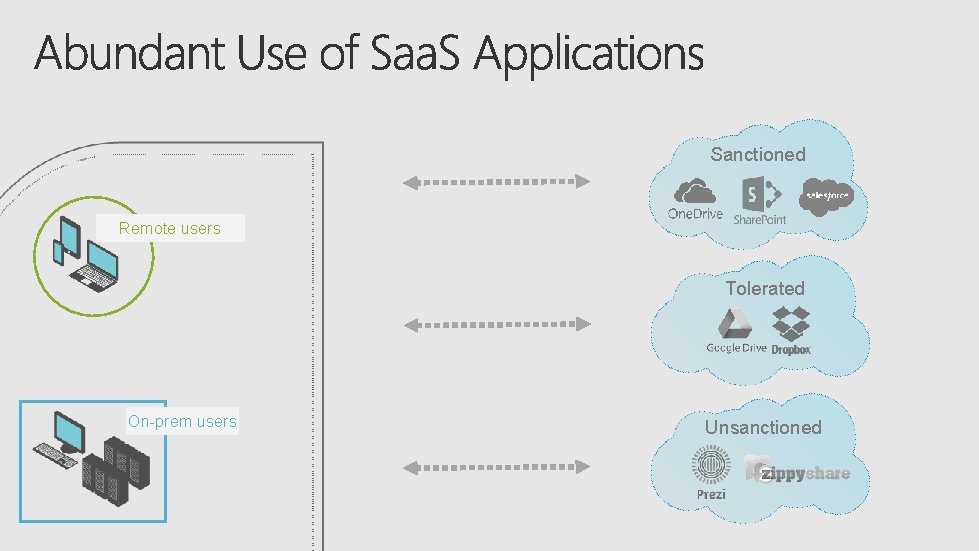
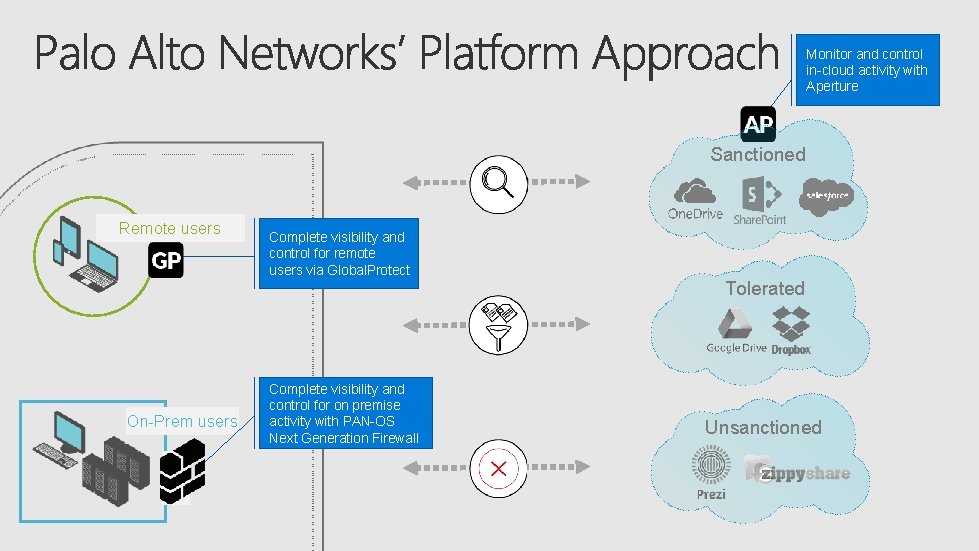
Sanctioned Remote users Tolerated On-prem users Unsanctioned

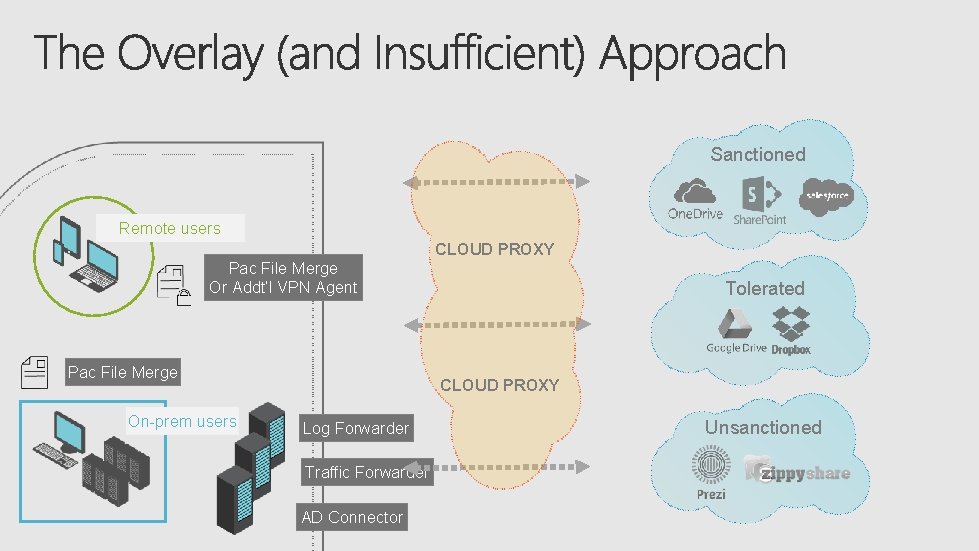
Sanctioned Remote users CLOUD PROXY Pac File Merge Or Addt’l VPN Agent Pac File Merge On-prem users Tolerated CLOUD PROXY Log Forwarder Traffic Forwarder AD Connector Unsanctioned

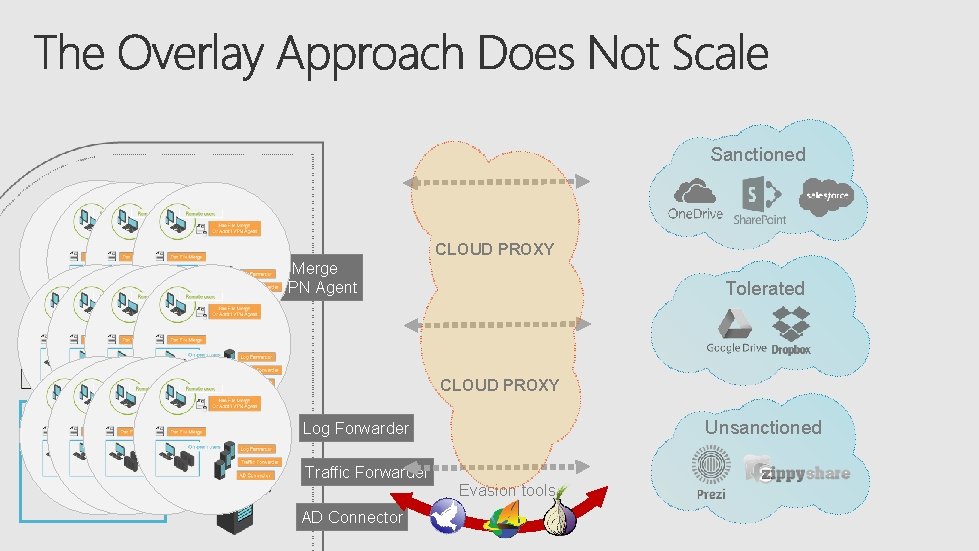
Sanctioned Remote users CLOUD PROXY Pac File Merge Or Addt’l VPN Agent Pac File Merge On-prem users Tolerated CLOUD PROXY Unsanctioned Log Forwarder Traffic Forwarder AD Connector Evasion tools

Monitor and control in-cloud activity with Aperture Sanctioned Remote users Complete visibility and control for remote users via Global. Protect Tolerated On-Prem users Complete visibility and control for on premise activity with PAN-OS Next Generation Firewall Unsanctioned

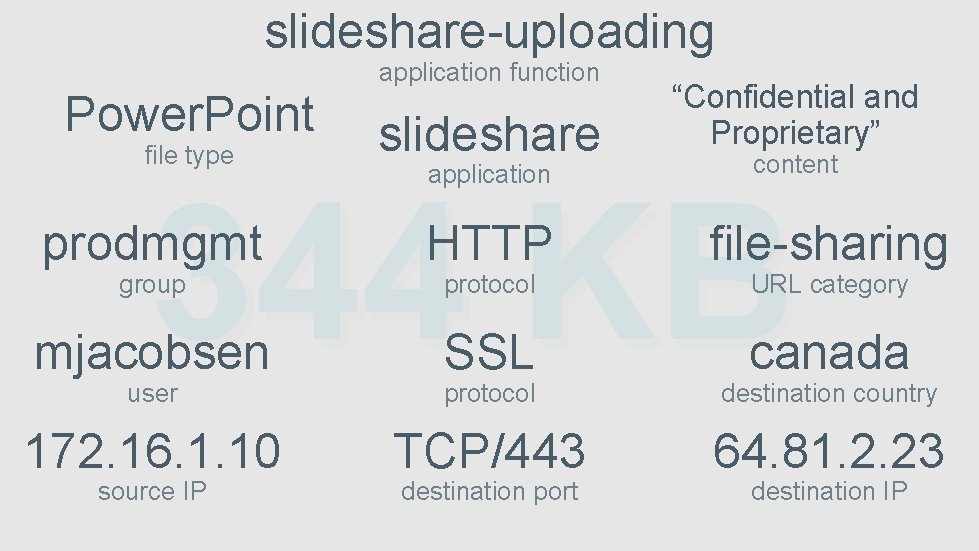
slideshare-uploading application function Power. Point file type slideshare application “Confidential and Proprietary” content 344 KB prodmgmt HTTP file-sharing mjacobsen SSL protocol canada destination country 172. 16. 1. 10 TCP/443 64. 81. 2. 23 group user source IP protocol destination port URL category destination IP

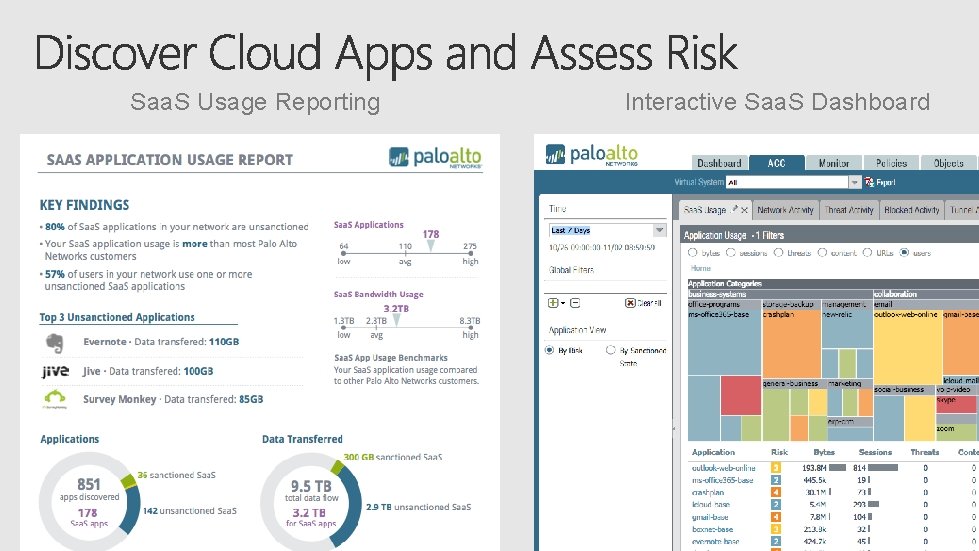
Saa. S Usage Reporting Interactive Saa. S Dashboard

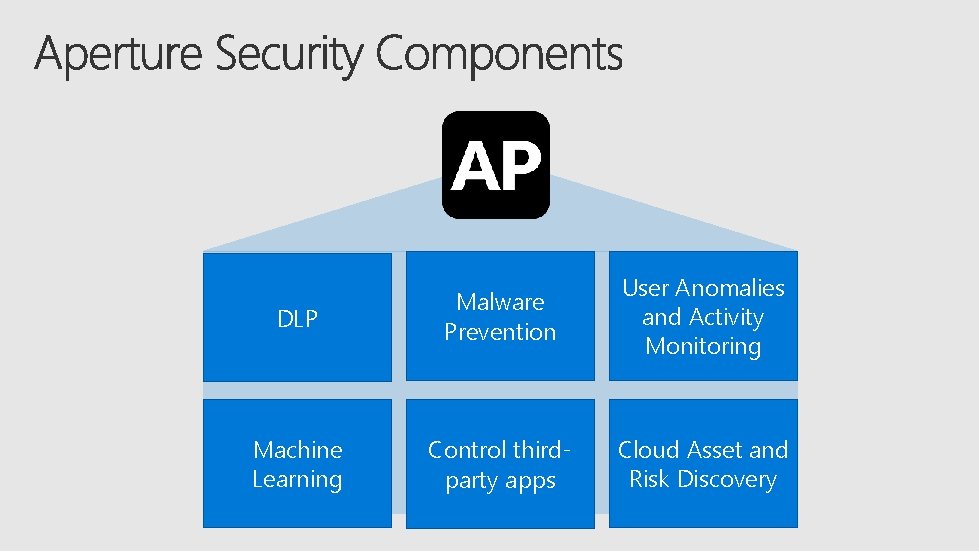
DLP Malware Prevention User Anomalies and Activity Monitoring Machine Learning Control thirdparty apps Cloud Asset and Risk Discovery

API-BASED INLINE 2500+ APPS (SAAS AND NON-SAAS) https: //applipedia. paloaltonetworks. com

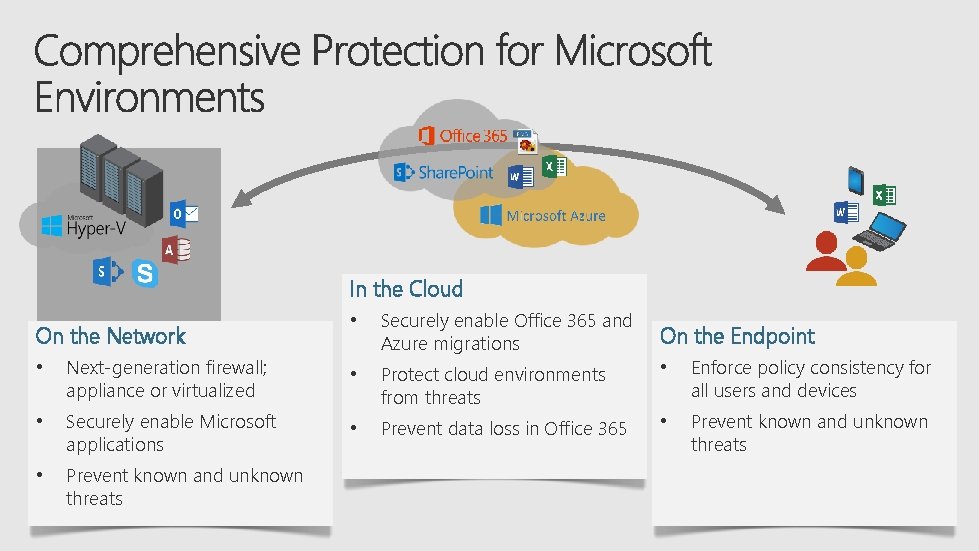
In the Cloud On the Network • Securely enable Office 365 and Azure migrations On the Endpoint • Next-generation firewall; appliance or virtualized • • Enforce policy consistency for all users and devices • Securely enable Microsoft applications Protect cloud environments from threats • Prevent data loss in Office 365 • Prevent known and unknown threats

https: //myignite. microsoft. com/evaluations https: //aka. ms/ignite. mobileapp




Email Security Threat Prevention and DLP 0 -Day Malware detection tied to Wild. Fire Detection of sensitive content and exposure Activity monitoring and anomalies Email Controls Monitoring APERTURE THREAT INTELLIGENCE CLOUD

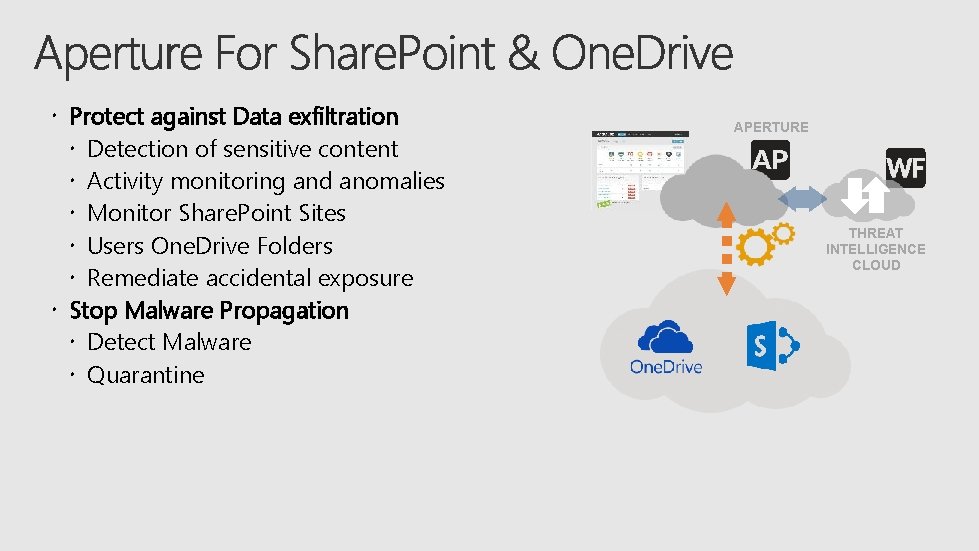
Protect against Data exfiltration Detection of sensitive content Activity monitoring and anomalies Monitor Share. Point Sites Users One. Drive Folders Remediate accidental exposure Stop Malware Propagation Detect Malware Quarantine APERTURE THREAT INTELLIGENCE CLOUD