Malicious Code CSH 6 Chapter 16 Malicious Code






























- Slides: 58

Malicious Code CSH 6 Chapter 16 “Malicious Code” Robert Guess & Eric Salveggio 1 Copyright © 2020 M. E. Kabay. All rights reserved.

Topics Ø Introduction Ø Malicious Code Threat Model Ø Survey of Malicious Code Ø Prevention of Malicious Code Attacks CSH 6 Chapter 16: “Malicious Code” 2 Copyright © 2020 M. E. Kabay. All rights reserved.

Introduction Ø Malicious code / logic q. Malware q. Hardware, software or firmware intentionally included or inserted in system for unauthorized purpose Ø Classification may be difficult q. Categories overlap because malware may have multiple functions and attributes üE. g. , virus / worm / Trojan horse / spyware Ø Some code may not be intended as malware by creators q. Context and intent determine whether code is viewed as malicious 3 Copyright © 2020 M. E. Kabay. All rights reserved.

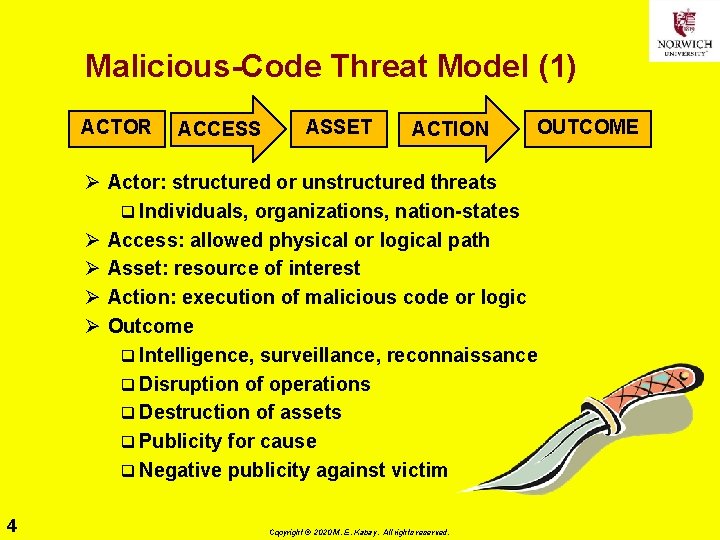
Malicious-Code Threat Model (1) ACTOR ACCESS ASSET ACTION OUTCOME Ø Actor: structured or unstructured threats q Individuals, organizations, nation-states Ø Access: allowed physical or logical path Ø Asset: resource of interest Ø Action: execution of malicious code or logic Ø Outcome q Intelligence, surveillance, reconnaissance q Disruption of operations q Destruction of assets q Publicity for cause q Negative publicity against victim 4 Copyright © 2020 M. E. Kabay. All rights reserved.

Malicious Code Threat Model (2) ØSelf-replicating Code ØActors: Origin of Malicious Code Threats ØActors: Structured Threats ØActors: Unstructured Threats ØAccess vs Action: Vector vs Payload 5 Copyright © 2020 M. E. Kabay. All rights reserved.

Self-replicating Code Ø Not inherently malicious Ø Early experiments (1960 s) had no evil intent q. Darwin (1961) involved memory worms q. Self-replicating code q. Competition → resource exhaustion 6 Copyright © 2020 M. E. Kabay. All rights reserved.

Is a Beneficial Virus Possible? Ø Ideas for beneficial self-propagating code: q. Distribute antivirus programs automatically through Internet q. Install patches on servers in networks q. Distribute useful information automatically Ø Consensus on Problems Preventing Use: q. What if there’s a bug or incompatibility in the self-propagating code? q. What if the patches are not appropriate for a specific server or network? q. What if the owner/user does not see the patch as useful? 7 Copyright © 2020 M. E. Kabay. All rights reserved.

Is Writing Malware Illegal in US? Ø No explicit law against writing malicious code Ø No illegality even in sharing such code among willing recipients Ø Current efforts to define statutes q. Based on laws banning possession of burglary tools (e. g. , lock picks) q. Require registration and licensing of locksmiths q. Would treat malware and Trojans in same way q. No significant progress to date 8 Copyright © 2020 M. E. Kabay. All rights reserved.

Actors: Origin of Malicious Code Threats Ø Structured threats q. Nation-states q. Corporate criminals q. Organized crime Ø Unstructured threats q. Rogue actors; e. g. , üIndividuals üScript kiddies 9 Copyright © 2020 M. E. Kabay. All rights reserved.

Actors: Structured Threats Ø Well-funded, systematic Ø Industrial espionage, information operations, largescale fraud & theft Ø Organized crime responsible for 90% malware q. Extortionists target online gambling q. Pump ‘n’ dump schemes cost $B q. Industrial espionage using spyware growing Ø China major player q. Major source of attacks q. PRC PLA doctrine emphasizes asymmetric warfare using information technology q. Total government control over hacking 10 Copyright © 2020 M. E. Kabay. All rights reserved.

Actors: Unstructured Threats Ø Random Ø Relatively limited Ø Does not target national security Ø Relatively minor 11 Copyright © 2020 M. E. Kabay. All rights reserved.

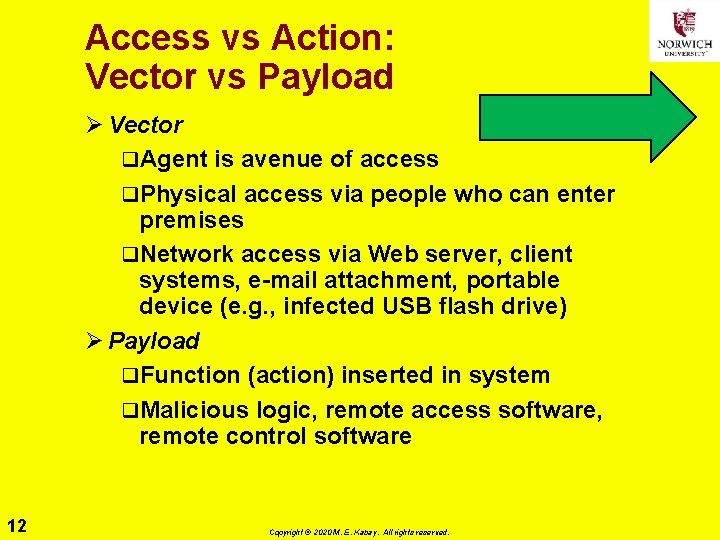
Access vs Action: Vector vs Payload Ø Vector q. Agent is avenue of access q. Physical access via people who can enter premises q. Network access via Web server, client systems, e-mail attachment, portable device (e. g. , infected USB flash drive) Ø Payload q. Function (action) inserted in system q. Malicious logic, remote access software, remote control software 12 Copyright © 2020 M. E. Kabay. All rights reserved.

Survey of Malicious Code Ø Viruses Ø Worms Ø Trojans Ø Spyware & Adware Ø Rootkits Ø Bots & Botnets Ø Malicious Mobile Code 13 Copyright © 2020 M. E. Kabay. All rights reserved.

Virus Mechanisms Ø Boot sector: sector 0 of disk Ø File infector: inserts JUMP instruction, adds code, returns to original location and continues loading Ø Macro virus: exploits weakness of MS scripting language in Word, Power. Point, Excel, Access etc. 14 Copyright © 2020 M. E. Kabay. All rights reserved.

Viruses (1) Ø Boot sector 15 Copyright © 2020 M. E. Kabay. All rights reserved.

Viruses (2) Ø Program infectors 16 Copyright © 2020 M. E. Kabay. All rights reserved.

Viruses (3) Ø Macro 17 Copyright © 2020 M. E. Kabay. All rights reserved.

1995 -1996: Early Macro Viruses Ø MS-Word macro virus (concept) released Aug 95 q. MS-Word macro viruses reached more than half all infections in the wild by 2009 Ø About 1000 types of macro viruses of all types known to date (Sep 2013) Ø MS-Excel virus discovered June 96 q. Anti-virus available within days q. Spreading more slowly than Word macro viruses because of lower rate of exchange of spreadsheets 18 Copyright © 2020 M. E. Kabay. All rights reserved.

1999 -03: Melissa Virus Friday 26 March: CERT-CC initial reports of fastspreading new MS-Word macro virus Ø Melissa written to infect Word documents Ø Uses victim's MAPI-standard e-mail address book Ø Sends copies of itself to first 50 people on list Ø E-mail message w/ subject line "Important Message From <name>” Ø Spread faster than any previous virus Ø Followed by similar e-mail-enabled viruses 19 Copyright © 2020 M. E. Kabay. All rights reserved.

Viruses (4) 20 Ø Logic Bombs q. Any malicious code, replicating or not, that delivers a payload as a result of a logic test (e. g. , specific date, absence of employee record) q. Time bombs (set off on a date or category of date) are a subset of logic bombs Ø Cross-site scripting malware q. Exploit flaws in Web application servers & client code q. In 2005, “Samy” created script that generated >1 M “friends” on My. Space using flaw in Internet Explorer to use Java. Script insertion exploit q. Sentenced to 3 years probation, 90 days community service Copyright © 2020 M. E. Kabay. All rights reserved.

Viruses (5) Ø Polymorphic viruses q Intended to defeat signaturebased antivirus tools q Modify themselves at time of replication Ø Polymorphic Engine q Encrypts code q Includes self-decryption capability q Dark Avenger wrote Mt. E (aka Mutation Engine) in late 1980 s üProgrammer from Sofia, Bulgaria üDetested Vesselin Bontchev, famous AV expert üAlso attacked researcher Sarah Gordon by name 21 Copyright © 2020 M. E. Kabay. All rights reserved.

Viruses vs Worms Ø Viruses integrate into host code q. Replicate upon execution of infected code Ø Worms are free-standing code q. Replicate via networks q. E-mail (e. g. , Outlook) especially common vector Ø Some worms have viral properties q. Integrate themselves into e-mail messages and convert them to executable files q. Frequently conceal executable file type q. Depend on default suppression of file suffix (e. g. , Anna. Kournikova. jpg. vbs. txt) 22 Copyright © 2020 M. E. Kabay. All rights reserved.

1987: IBM Christmas Tree Worm Ø E-mail sent via IBM internal e-mail network Ø Included program to draw ASCII Christmas tree on screen Ø Used recipient’s e-mail address book to mail itself to everyone on the network Ø No mechanism to prevent superinfection Ø Overloaded worldwide IBM networks Ø Messages escaped from IBM into BITNET 23 Copyright © 2020 M. E. Kabay. All rights reserved.

1988: The Morris Worm Ø Robert T. Morris (not a “Robert T. Morris, Jr”!) q. Cornell University grad student q. Son of famed NSA cryptographer Robert H. Morris q. Wrote paper on sendmail and fingerd vulnerabilities on UNIX systems q. Seems to have intended to demonstrate significance Ø Released a defective version of his demo worm q. Originally intended to replicate slowly, avoid superinfection q. In fact grew fast and superinfected systems worldwide 24 Copyright © 2020 M. E. Kabay. All rights reserved.

Morris Worm (cont’d) Ø Launched Worm at 17: 00 on 2 November 1988 Ø By 06: 00 next morning the Internet was effectively down q~6, 000 -9, 000 systems crashed or taken offline Ø Computer scientists worked feverishly all night analyzing the Worm q. Distributed fixes by telephone and fax (no ‘Net) q. Led to formation of CERT-CC® in Dec 1988 Ø Morris convicted of violating 1986 Computer Fraud and Abuse Act (18 USC § 1030) q 400 hours community service + $10 K fine 25 Copyright © 2020 M. E. Kabay. All rights reserved.

1999 -12 W. 95. Babylonia Virus/Worm Ø Extensible virus Ø Payload modified remotely Ø Trojan virus-dropper q. Disguised as Y 2 K bug fix for internet relay chat (IRC) users Ø Sent itself other users Ø Polled Internet site in Japan q. Looked for updated plugins 26 Copyright © 2020 M. E. Kabay. All rights reserved.

2000 -05: ILOVEYOU Worm Ø E-mail subject ILOVEYOU Ø E-mail attachment LOVE-LETTER-FOR-YOU. TEXT. vbs Ø Used all addresses in address book Ø Became #1 infectious code in Europe, Asia, USA Ø Variants appeared quickly Ø Created by 27 -yr-old Filipino computer student Onel de Guzman q. No local laws against spreading viruses q. Creator given job as programmer! 27 Copyright © 2020 M. E. Kabay. All rights reserved.

2000 -06: Timofonica Worm Ø E-mail enabled malware Ø Automatically sent pager message to block of Telefonica cell phones Ø Tried to delete all data on hard disk 28 Copyright © 2020 M. E. Kabay. All rights reserved.

2001 -03: Sir. Cam Worm Ø Propagated on Windows systems Ø Used standard e-mail address books Ø Infected document, converts to executable q. Most naïve users turn off suffix display q. So myfile. doc. exe looks like myfile. doc Ø Created e-mail message with random subject and randomized text asking for comment Ø Sent infected file to everyone on e-mail list Ø Documents may contain confidential info Ø See http: //www. cert. org/advisories/CA-2001 -22. html 29 Copyright © 2020 M. E. Kabay. All rights reserved.

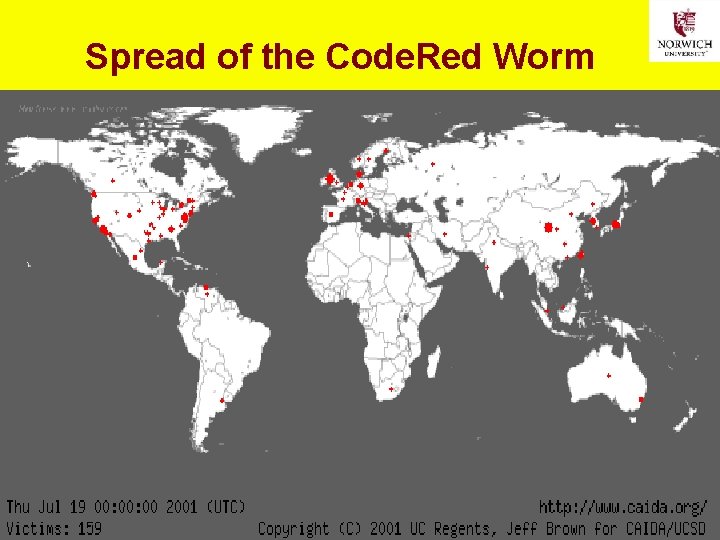
2001 -06: Code. Red Worm Ø Infected vulnerable Web servers q Windows NT or Windows 2000 or CISCO equipment q running MS-IIS software that has not been patched Ø Showed message on Web home page: HELLO! Welcome to http: //www. worm. com! Hacked By Chinese! Ø Sent copies of itself to computers in list of IP addresses Ø On 20 th through 28 th of month, tried to swamp specific target with Do. S (denial-of-service) attack q Original worm attacked numerical address of White House q Later versions received instructions from remote master computer program controlled by criminal hacker Ø See http: //www. cert. org/advisories/CA-2001 -19. html 30 Copyright © 2020 M. E. Kabay. All rights reserved.

Spread of the Code. Red Worm 31 Copyright © 2020 M. E. Kabay. All rights reserved.

Trojans Ø Named for the Trojan Horse in the Iliad Ø Overt function useful or harmless Ø Covert function unauthorized, usually harmful Ø Functionality may be associated with all types of malware q Worms q Standalone programs Ø Early Trojans included PC-Cyborg (“AIDS Information Disk”) of 1989 q Replaced autoexec. bat to count boots q On 90 th boot, encrypted file/directory names q Author, Dr Joseph Popp arrested, extradited to US from UK, but never convicted due to mental incompetence 32 Copyright © 2020 M. E. Kabay. All rights reserved.

2000 -01: Haiku Worm (Trojan) F-Secure (formerly Data Fellows) Ø E-mail enabled virus/worm Ø Carrier: detailed e-mail message about Haiku generator q. Actually works — Haiku in Windows box Ø Worm code spreads through victim's e-mail address list Ø Occasionally downloads and plays a. wav file from a Web site 33 Copyright © 2020 M. E. Kabay. All rights reserved.

Spyware & Adware Ø Software that collects user information without permission q Tracking & reporting Web usage q Monitoring use of licensed programs q Monitoring or blocking copying of music q Click-fraud (automatically clicks on ads for profit) Ø Spyware serving unwanted ads = adware Ø Legal issue is EULA (end-user license agreement) q If no clear statement of functions, spyware/adware may be violation of 18 US 1030(a) (Computer Fraud & Abuse Act of 1986) q If EULA is clear and user agrees, matter of contract law q But many users never read EULA at all… Ø Some spyware/adware difficult to uninstall (hides itself) 34 Copyright © 2020 M. E. Kabay. All rights reserved.

Rootkits Ø Program that allows covert access after installation q. Compromise application, library, kernel, hypervisor & hardware levels q. Early versions replaced Unix components q. Kernel-level rootkits run as device drivers Ø Classic examples: BO & BO 2 K q. Back Orifice by Sir Dystic of Cult of the Dead Cow (c. Dc) presented at DEF CON 6 in 1998 q. Back Orifice 2000 by Dildog of c. Dc presented at DEF CON 7 in 1999 q. Both provide “remote systems administration” q. Both used by Trojan droppers q. BO 2 K hides itself from discovery 35 Copyright © 2020 M. E. Kabay. All rights reserved.

Bots & Botnets (1) Ø Bots q Automated processes on the Internet & WWW q Carry out specific tasks; e. g. , ü Web spidering: collecting files from Web (e. g. , GOOGLE engine bots) ü Monitoring conversations on talk channels (e. g. , for suppression of profanity or automated responses to questions) Ø IRC Bots q Internet Relay Chat used for communications q IRC bots widespread for criminal activity Ø Bot Herders control 100 K bots for commercial (criminal) activity such as DDo. S, spam 36 Copyright © 2020 M. E. Kabay. All rights reserved.

Bots & Botnets (2) Nov 15, 2012 Ø Grum: 18 billion spam messages per day Ø Lethic: 28% of all spam in 2012 Ø Festi: infected 250, 000 unique IP addresses Ø Cutwail: DDo. S attacks vs 100 s Websites Ø Zeus: 944 Zeus command control (C&C) servers – botnets steal banking info Ø Spy. Eye: steal consumer banking data (~278 Spy. Eye C&C servers in use Ø Citadel: “…social network allowing users to report bugs and even suggest new features. 2012 has seen a 20 % increase in Citadel Trojan attacks” 37 Morgan, C. “The Worst Botnets of 2012. ” Storagecraft (201211 -15). Copyright © 2020 M. E. Kabay. All rights reserved. http: //www. storagecraft. com/blog/the-worst-botnets-of-2012/

Bots & Botnets (3) Ø Zero. Access: fastest growing botnet: 2 M nodes – ad-click fraud Ø TDL-4: “…removes competing malware, hides from detection and installs a master boot record. The newest variant of TDL-4 has infected approximately 250, 000 unique victims. ” Ø Flashback: 100 k Mac computers infected – collects passwords (e. g. , Google, Paypal) … infected 10 percent of home networks with Mac computers by Apr 2012 38 Morgan, C. “The Worst Botnets of 2012. ” Storagecraft (201211 -15). Copyright © 2020 M. E. Kabay. All rights reserved. http: //www. storagecraft. com/blog/the-worst-botnets-of-2012/

Malicious Mobile Code Ø Web servers host pages with active content Ø Mobile code may be written in (e. g. ) q. Active. X controls q. Java applets q. Java. Script q. Adobe Flash Ø Often involved in phishing attacks Ø See CSH 6 Chapter 17, Mobile Code. 39 Copyright © 2020 M. E. Kabay. All rights reserved.

Detection of Malicious Code ØSignature-Based ØNetwork-Based ØBehavioral ØHeuristic 40 Copyright © 2020 M. E. Kabay. All rights reserved.

Signature-Based Malware Detection Ø Oldest method of recognizing malware q. Identify known strings of code/text q. Defeated by polymorphism Ø Hashes q. Compute cryptographic hash of all executables on system; e. g. , üMD 5 üSHA-1 üDigital signature using public key cryptosystem q. Identify unauthorized changes (caused by malware) by checking table of hash values 41 Copyright © 2020 M. E. Kabay. All rights reserved.

Network-Based Malware Detection 42 Ø Look for effects of running malware; e. g. , q. Connection to unusual / characteristic server (like IRC) q. Unusual protocols (not normal for system) q. Peculiar packets (nor normal for protocol) Ø Can establish baseline for behavior q. Monitor KNOWN-CLEAN system üCritically important not to include malicious code in baseline q. Compare observed behavior with baseline q. Look for outliers & investigate deviations Copyright © 2020 M. E. Kabay. All rights reserved.

Behavioral Malware Detection Ø Monitor behavior of code q. Look for violations of security standards; e. g. , q. Attempting to modify areas of memory outside local stack of process q. Attempting to raise privilege level Ø Sandboxes q. Run code in restricted environment q. E. g. , Java sandbox Ø Virtual machines a form of sandbox q. Increasingly popular 43 Copyright © 2020 M. E. Kabay. All rights reserved.

Heuristic Malware Detection Ø Heuristic in this context means able to change / learn Ø Apply statistical modeling & theoretical behavioral models q. Computer score / metric to evaluate likelihood that program is legitimate q. Can detect new variations of malware üEven if signature not yet registered by conventional scanners Ø Modern antimalware products include option for heuristic scanning q. Should enable it! 44 Copyright © 2020 M. E. Kabay. All rights reserved.

Prevention of Malicious Code Attacks Ø Defense in Depth vs Malware Ø Operational Controls vs Malware Ø Human Controls vs Malware Ø Technical Controls vs Malware 45 Copyright © 2020 M. E. Kabay. All rights reserved.

Defense in Depth vs Malware Ø No one AV program can protect against all malware Ø Defense in depth uses multiple concurrent strategies q Operational controls q Human controls q Technical controls Ø Different approach is to define orthogonal systems q Function in only one demonstrably correct way q But no one wants singlepurpose, rigid systems 46 Copyright © 2020 M. E. Kabay. All rights reserved.

Operational Controls vs Malware Ø Written policies and procedures q. Govern introduction of programs into production environment q. Who can install programs? q. Acceptable use policies for Internet and email use (CSH 6 Chapter 48, “E-mail and Internet Use Policies”) q. How to respond to suspected attack q. See CSH 6 Chapter 47, “Operations Security & Production Controls” Ø Employment policies & procedures q. CSH 6 Chapter 45, “Employment Practices & Policies” 47 Copyright © 2020 M. E. Kabay. All rights reserved.

Human Controls vs Malware Ø Provide training on malware policies & procedures Ø Topics q. Current threats; e. g. , üAdvance-fee fraud (Nigerian 419 fraud) üSocial engineering (see CSH 6 Chapter 29, “Social Engineering & Low-Tech Attacks”) üMalicious attachments q. Detecting the threats – not ignoring AV popups! q. Proper response üContact Help Desk at once 48 Copyright © 2020 M. E. Kabay. All rights reserved.

Technical Controls vs Malware Ø Implementing Antivirus Systems Ø Host Configuration Controls & Security Ø Network-Based Security Controls Ø Network Monitoring See CSH 6 Chapter 41, “Antivirus Technology” 49 Copyright © 2020 M. E. Kabay. All rights reserved.

Implementing Antivirus Systems Ø Use both network-based & host-based systems Ø Choose products from different vendors to run concurrently Ø Run updates automatically on all systems daily at least Ø E-mail may require separate appliance/ system to control malware attachments, spam, fraud, phishing…. 50 Copyright © 2020 M. E. Kabay. All rights reserved.

Host Configuration Controls & Security 51 Ø Automatic updates / patches essential Ø Eliminate non-critical software & services q Minimize threats that target growing complexity of environment q Current software development introduces average of 4. 5 errors per 1000 lines of code q Inevitably, more code means more errors q Simplify environment to degree possible Ø Browsers q Eliminate if possible q Otherwise, apply tight security q Use secure Web proxy Copyright © 2020 M. E. Kabay. All rights reserved.

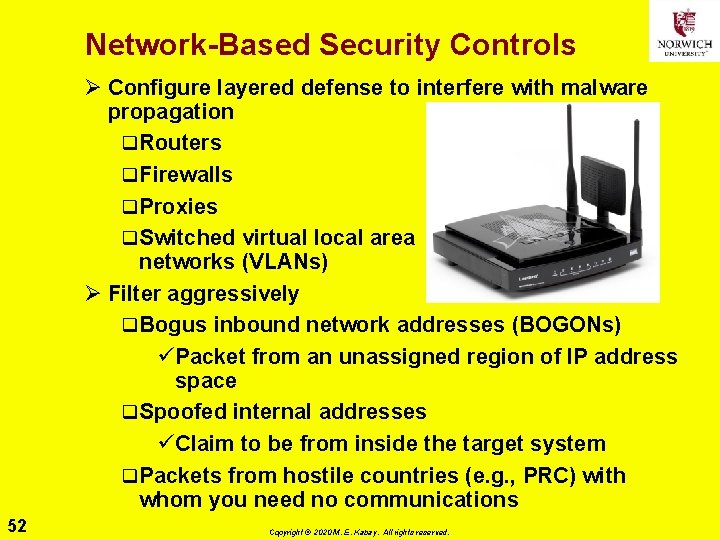
Network-Based Security Controls Ø Configure layered defense to interfere with malware propagation q Routers q Firewalls q Proxies q Switched virtual local area networks (VLANs) Ø Filter aggressively q Bogus inbound network addresses (BOGONs) üPacket from an unassigned region of IP address space q Spoofed internal addresses üClaim to be from inside the target system q Packets from hostile countries (e. g. , PRC) with whom you need no communications 52 Copyright © 2020 M. E. Kabay. All rights reserved.

Network Monitoring Ø Monitor & aggregate data from sensors q. Device logs q. Server logs q. Host logs q. Intrusion detection alerts q. Network flow data Ø Define historical database of normal behavior Ø Look for anomalies – statistical outliers 53 Copyright © 2020 M. E. Kabay. All rights reserved.

Awareness Tools 54 Ø ICSA Labs q https: //www. icsalabs. com/products Ø Virus Bulletin q http: //www. virusbtn. com/index Ø Avast! q http: //www. avast. com/virus-monitor Ø Mc. Afee Virus Information q http: //home. mcafee. com/virusinfo Ø Microsoft Malware Protection Center q http: //www. microsoft. com/security/portal/ Ø Sophos q http: //www. sophos. com/en-us/security-newstrends. aspx Ø Trend Micro q http: //us. trendmicro. com/us/trendwatch/ Copyright © 2020 M. E. Kabay. All rights reserved.

Recent Statistics (Q 2 2013) Quarterly & monthly reports always online 55 Details available through all the links Lots more info below http: //www. securelist. com/en/analysis/204792299/IT_Threat_Evolutio Copyright © 2020 M. E. Kabay. All rights reserved.

Recent Statistics (24 Sep 2013) Up to date details available online anytime. 56 http: //www. trendmicro. com/us/securityintelligence/index. html Copyright © 2020 M. E. Kabay. All rights reserved.

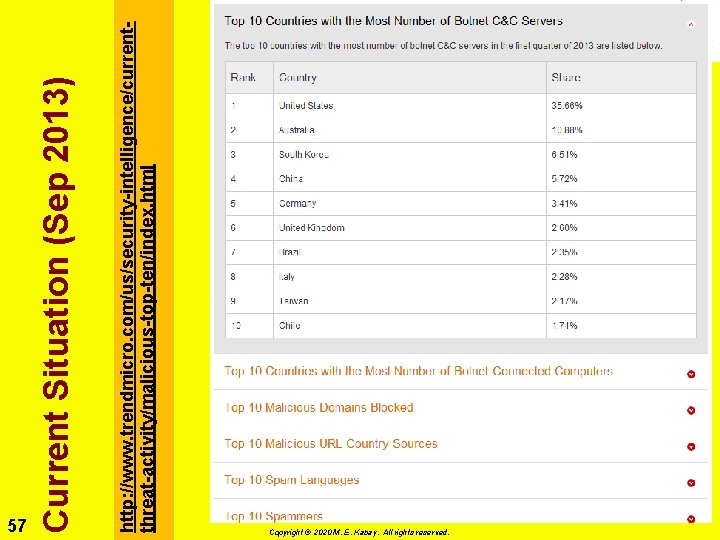
http: //www. trendmicro. com/us/security-intelligence/currentthreat-activity/malicious-top-ten/index. html Current Situation (Sep 2013) 57 Copyright © 2020 M. E. Kabay. All rights reserved.

DISCUSSION 58 Copyright © 2020 M. E. Kabay. All rights reserved.