MALICIOUS CODE INCIDENTS 1 MALICIOUS CODE INCIDENTS Definition














- Slides: 22

MALICIOUS CODE INCIDENTS 1

MALICIOUS CODE INCIDENTS Definition : Malicious code refers to a program that is covertly inserted into another program with the intent to Malicious activities. 2

MALICIOUS CODE INCIDENTS Malicious Activities Include : Destroy Run data. destructive or intrusive programs. Compromise the security or the confidentiality, integrity, and availability of the victim’s data, applications, or operating system. 3

MALICIOUS CODE INCIDENTS Types Of Threats : 1)Viruses Compiled Viruses Interpreted viruses 2)Worms Network Service Worms Mass mailing Worms 3)Trojan Horses 4

MALICIOUS CODE INCIDENTS Types Of Threats : 4)Malicious Mobile Codes Mostly Java, Active. X, Java. Script, and VBScript codes. 5)Blended Attacks Combination of 1 to 4 6) Attack Tools Backdoors Rootkits Key Loggers … 5

MALICIOUS CODE INCIDENTS Types Of Threats : 7) Tracking Cookies 8) Non-malware threats Hoax Phishing 6

MALICIOUS CODE INCIDENTS Step 1 : Preparation 1) Preparation I. III. Awareness Deployment Resources Prevention 2) I. III. Education Configuration Control 7

MALICIOUS CODE INCIDENTS Step 2: Detection and Analysis Fast spread of incident so: Rapid Detection is Necessary Precursors often appear immediately before an incident So: Group must not wait for indications Most of indications could have causes other than malware 8

MALICIOUS CODE INCIDENTS Step 2: Detection and Analysis Precursors and Reactions: An alert warns of new malicious code. Research and Block Ways of Entrance Antivirus software detects and successfully disinfects or quarantines a newly received infected file Find Reason And Mitigate Vulnerability 9

MALICIOUS CODE INCIDENTS Step 2: Detection and Analysis Special Indications of Each Malicious Code Virus Changes to templates for word processing documents, spreadsheets, etc. Deleted, corrupted, or inaccessible files Unusual items on the screen, such as odd messages and graphics 10

MALICIOUS CODE INCIDENTS Step 2: Detection and Analysis Special Indications For Each malicious Code Worm: Port scans and failed connection attempts targeted at the vulnerable service Increased network usage Trojan: Network connections between the host and unknown remote systems Unusual and unexpected ports open 11

MALICIOUS CODE INCIDENTS Step 2: Detection and Analysis Special Indications For Each malicious Code Malicious Mobile Code To spread Virus, worm, … Unexpected dialog boxes, requesting permission to do s. th Unusual graphics, such as overlapping message boxes exploit vulnerabilities Network connections between the host and unknown remote systems Receiving No Hoax Reports links to outside sources 12

MALICIOUS CODE INCIDENTS Step 3: 1)Containment Strategies All incident Prevention Activities must be done in order to stop spread of virus Other Activities : Notification Isolation Change Access rules Identification of infected hosts is not easy 13

MALICIOUS CODE INCIDENTS Step 3: 2)Eradication And Recovery Some Infected files can not be cleaned System Restore may be needed Securing system is the last step 14

MULTIPLE COMPONENT INCIDENTS 15

MULTIPLE COMPONENT INCIDENTS Definition : A Multiple Component incident is a single incident that encompasses two or more incidents. 16

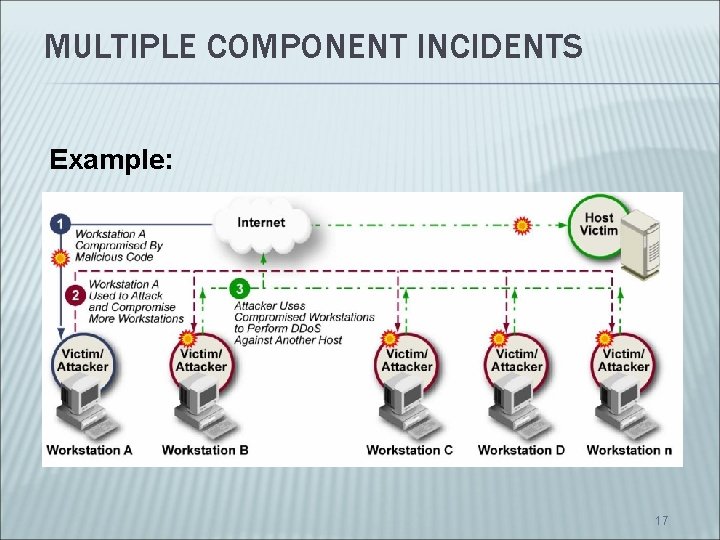
MULTIPLE COMPONENT INCIDENTS Example: 17

MULTIPLE COMPONENT INCIDENTS Step 1&2 : Preparation, Detection, Analysis Conduct exercises reviews scenarios involving multiple component incidents. Efficient incident analysis: centralized logging correlation software. 18

MULTIPLE COMPONENT INCIDENTS Step 3: Containment, Eradication, Recovery Approach : Contain the initial incident and then search for signs of other components Gauss if incident have other components Unauthorized access incidents are more likely to have multiple components 19

MULTIPLE COMPONENT INCIDENTS Step 3: Containment, Eradication, Recovery Prioritization: Components Response Another It must be separately prioritize the most urgent one factor: How current each component is may be possible to contain the whole incident by containing just one component 20

REFERENCES Computer Security Incident Handling Guide National Institute of Standard and Technology (NIST) U. S A Step-By-Step Approach on How To Set Up a CSIRT European Network and Information Security Agency (ENISA) Expectations for Computer Security Incident Response RFC 3250 Handbook for Computer Security Incident Response Teams Carnegie Mellon University , 2 nd Edition: April 2003 Defining Incident Management Processes for CSIRTs: A Work in Progress Chris Alberts, Audrey Dorofee, Georgia Killcrece, Robin Ruefle, Mark Zajicek, October 2004 21

Thanks For Your Attention 22