Malicious Code Viruses and Worms ChaoHsien Chu College

















- Slides: 33

Malicious Code: Viruses and Worms Chao-Hsien Chu College of Information Sciennces and Technology The Pennsylvania State University Park, PA 16802 chu@ist. psu. edu Modified by Santoro y eor Th ce cti Pra Le arn i by ng Do ing

Malicious Code Taxonomy • Viruses – replicating malicious code • Worms – self-replicating malicious code – Mailing worms – Random scanning worms • Logic Bombs – programmed malfunctions (similar to easter eggs) • Trojan Horses – malicious program that masquerades as legitimate – Backdoors – Password stealers • Exploit code: – Autorooters – White hat penetration tools • Downloaders – loads other malicious code on a machine

Malicious Code Taxonomy • Dialers – generate money for attackers by having users unknowingly dial premium rate numbers • Code generator kits (e. g. Virus Creation Lab) • Spammer programs • Flooders – DDOS tools, Bot. Nets • Keyloggers • Rootkits – special tool set installed after an attacker has gained control of a system; modifies logs, installs backdoors, etc. • Other: – Hoax messages – Adware – Spyware – Phishing attacks

Malicious Code Example “Most people I think don’t even know what a rootkit is so why should they care about it? ” – Thomas Hesse, Sony BMG • In 2005, Sony BMG released music CDs containing extended copy protection (XCP) software. • This software was functionally a rootkit that installed hidden files with no notification to the user – a special uninstaller was required to remove the software • Simply playing the music CD in a windows machine resulted in infection NPR story: http: //www. npr. org/templates/story. php? story. Id=4989260

Virus: Definition “A computer virus is a program that recursively and explicitly copies a possibly evolved version of itself. ” – Peter Szor, 2005 Key aspects of this definition: – Recursively: operate on their own output – Explicitly: the copy is specifically intended as opposed to resulting from a side-effect of some other action – Possibly evolved: the virus may alter itself over time (metamorphism)

Virus: Environments For a sequence of symbols to execute successfully, it must match the execution environment • • • Many execution environments exist, e. g. : – MS Office macro invoking a Java method on a windows XP machine running on an x 86 processor Any given virus can only be successful if its code matches all of the various dependencies – Homogeneous environments, such as Java and MS Office provide execution environments across many lower level environments – For exploit-based dependencies, it may be difficult for a virus to spread far Dependencies: – CPU: differences between families, within a family (backward compatibility, extensions such as MMX, prefetch queue, etc. ) – Operating System: different OSs and different versions of an OS – File system: virus may modify file system metadata (e. g. FAT), NTFS stream-based hiding – File format: COM, EXE, dll, ELF, etc… – Interpreter: Office Macros, Shell languages, VBScript, Jscript, etc…

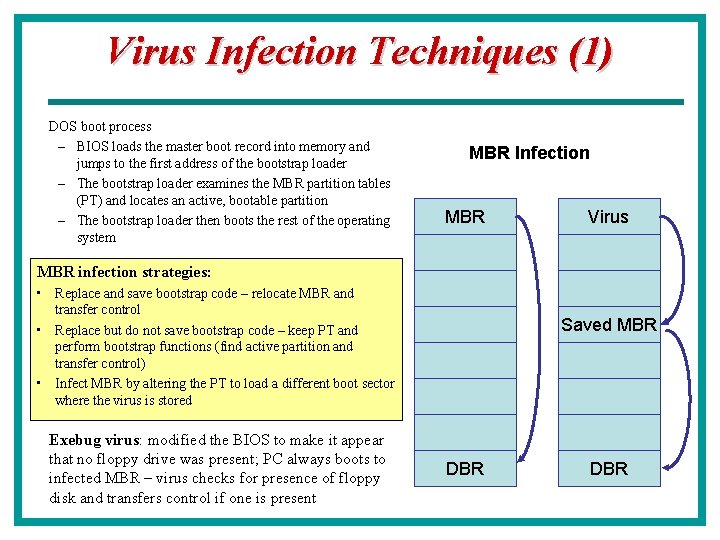
Virus Infection Techniques (1) DOS boot process – BIOS loads the master boot record into memory and jumps to the first address of the bootstrap loader – The bootstrap loader examines the MBR partition tables (PT) and locates an active, bootable partition – The bootstrap loader then boots the rest of the operating system MBR Infection MBR Virus MBR infection strategies: • Replace and save bootstrap code – relocate MBR and transfer control • Replace but do not save bootstrap code – keep PT and perform bootstrap functions (find active partition and transfer control) • Infect MBR by altering the PT to load a different boot sector where the virus is stored Exebug virus: modified the BIOS to make it appear that no floppy drive was present; PC always boots to infected MBR – virus checks for presence of floppy disk and transfers control if one is present Saved MBR DBR

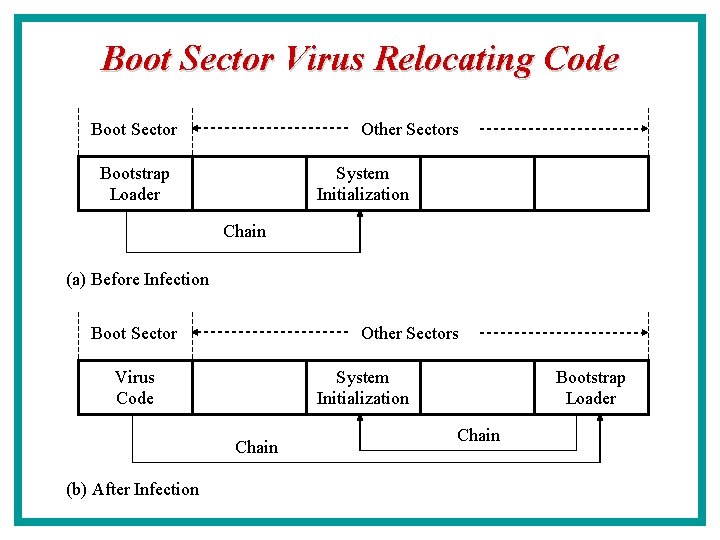
Boot Sector Virus Relocating Code Boot Sector Other Sectors Bootstrap Loader System Initialization Chain (a) Before Infection Boot Sector Other Sectors Virus Code System Initialization Chain (b) After Infection Bootstrap Loader Chain

Virus Infection Techniques (2) File Infection • Overwriting viruses – Simply overwrite a file on disk with virus code starting at first file byte – Do not change file size – Cannot be disinfected • Random overwriting viruses – Seek to random location before overwriting file contents – entry point obscuring – A challenge for scanners that look in expected locations for virus code – Execution cannot be guaranteed • Appending viruses – Virus body is appended to the end of the host file – A jump instruction is inserted in the front of the host to point to the virus – Over-written host bytes at the beginning are stored in the virus body – Once executed, the virus can “clean” the program by replacing the over-written bytes and transferring execution to the program • Pre-pending viruses – Virus code is appended before the first host instruction, guaranteeing that all virus instructions are executed before any host instructions.

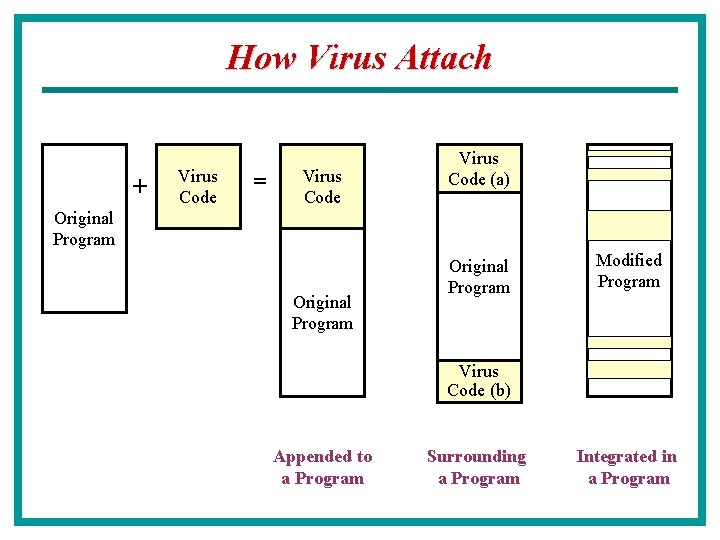
How Virus Attach + Virus Code = Virus Code (a) Original Program Modified Program Virus Code (b) Appended to a Program Surrounding a Program Integrated in a Program

Virus In-Memory Strategies (1) Direct Action – – Do not actively manifest themselves in memory Load with host program into memory Once running, they start looking for new objects to infect Simple to create Memory-Resident – Remain in memory after virus initialization – More efficient than direct action – Typical pattern: • • Virus gains control of system and allocates memory Virus relocates itself to an allocated memory block Virus hooks execution of code flow to itself Virus infects new objects

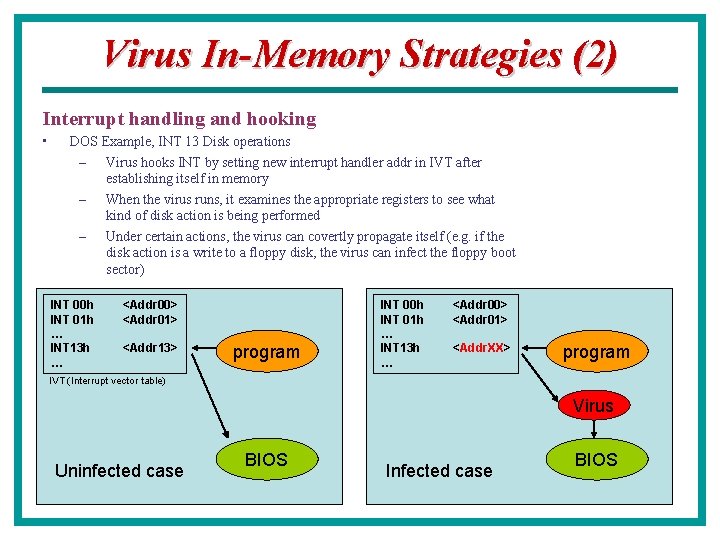
Virus In-Memory Strategies (2) Interrupt handling and hooking • DOS Example, INT 13 Disk operations – Virus hooks INT by setting new interrupt handler addr in IVT after establishing itself in memory – When the virus runs, it examines the appropriate registers to see what kind of disk action is being performed – Under certain actions, the virus can covertly propagate itself (e. g. if the disk action is a write to a floppy disk, the virus can infect the floppy boot sector) INT 00 h INT 01 h … INT 13 h … <Addr 00> <Addr 01> <Addr 13> program INT 00 h INT 01 h … INT 13 h … <Addr 00> <Addr 01> <Addr. XX> program IVT (Interrupt vector table) Virus Uninfected case BIOS Infected case BIOS

Virus In-Memory Strategies (3) Stealth advantages of hooking • INT 13 – Boot virus: can return the original version of an infected sector during a disk read (read stealth) – Appending virus: can save overwritten beginningof-file bytes in last cluster slack space (leaving file size unmodified) and use hooked code to return saved bytes if they are ever accessed.

Advanced Virus Techniques • Encryption – Constant decryptor followed by virus body – Often simple XOR based encryption is used – Decryption key can be stored in the decryptor, host or nowhere • Oligomorphism – Detection of an encrypted virus is simple if the decryptor is long and unique enough – Oligomorphic viruses change the decryptor in new generations – Can be accomplished using a set of decryptors – for a large set, detection based on the decryptor is impractical, must dynamically decrypt and detect based on decrypted body code • Polymorphism – Mutates the decryptor into potentially millions of forms (e. g. via reordering, junk instruction insertion) • Metamorphism – “body-polymorphism” – change the entire virus, rather than just the decryptor – Source code based: example: modify virus source and recompile – Binary-based: example (simple): use different registers in the same code

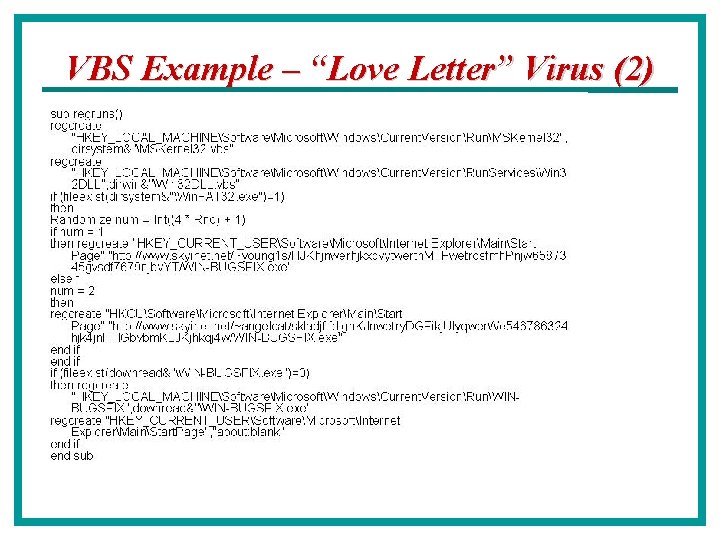
Virus Example – “Love Letter” (1) Behavioral Description (from F-Secure): • Found in the wild May 4, 2000 • Copies itself to the windows system directory as – - MSKernel 32. vbs - LOVE-LETTER-FOR-YOU. TXT. vbs and to the Windows directory as: – - Win 32 DLL. vbs • Adds keys to the registry, so that it will be executed when the system is restarted: – HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrent. VersionRunMSKernel 32 – KEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrent. VersionRun. ServicesWin 32 DLL • Replaces the Internet Explorer home page with a link that points to an executable program, "WINBUGSFIX. exe“ • Creates an HTML file called "LOVE-LETTER-FOR-YOU. HTM" in the Windows System directory. This file contains the worm and it will be sent using m. IRC whenever another person joins an IRC channel where the infected user currently is. To accomplish this the worm replaces the "script. ini" file from the m. IRC installation directory. • Mass mails itself to everyone in each Outlook address book. Registry is marked to prevent repeat mailings Subject: ILOVEYOU Body: kindly check the attached LOVELETTER coming from me. Attachment: LOVE-LETTER-FOR-YOU. TXT. vbs Source: http: //www. f-secure. com/v-descs/love. shtml • Overwrites various files with itself

Virus Example – “Love Letter” (2) Behavioral Description (from F-Secure): continued Downloaded executable is a password stealing trojan: • On startup, looks for a hidden window named ‘BAROK…’ • If the hidden window is present, the trojan exits, otherwise execution continues… • Checks for the Win. FAT 32 subkey in the following Registry key: HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrent. VersionRun • If the Win. FAT 32 subkey is not found, the trojan creates it, copies itself to the WindowsSystem directory as WINFAT 32. EXE and then it runs the file from that location. • Sets the IE startup page to 'about: blank'. • Deletes the following keys: SoftwareMicrosoftWindowsCurrent. VersionPoliciesNetworkHide. Share. Pwds SoftwareMicrosoftWindowsCurrent. VersionPoliciesNetworkDisable. Pwd. Caching. DEFAULTSoftwareMicrosoftWindowsCurrent. VersionPoliciesNetworkHide. Share. Pwds. DEFAULTSoftwareMicrosoftWindowsCurrent. VersionPoliciesNetworkDisable. Pwd. Caching • Registers a new window class and creates a hidden window titled 'BAROK. . . ' and remains resident in the Windows memory as a hidden application. • Immediately after startup and when timer counters reach certain values, the trojan sends stolen RAS passwords and all cached Windows passwords to e-mail address 'mailme@super. net. ph’ Source: http: //www. f-secure. com/v-descs/love. shtml

VBS Example – “Love Letter” Virus (1) Language Reference: MSDN Home > MSDN Library > Web Development > Scripting > Microsoft Windows Script Technologies > Script Runtime > File. System. Object > Scripting Run-Time Reference >

VBS Example – “Love Letter” Virus (2)

VBS Example – “Love Letter” Virus (3)

Worm: Definition “A worm is a program that can run by itself and can propagate a fully working version of itself to other machines. It is derived from the word tapeworm, a parasitic organism that lives inside a host and saps its resources to maintain itself. ” – Spafford, 1988

Worm Taxonomy • Target discovery – Active scanning, hitlist, passive monitoring • Propagation method – Self-propagation, embedded, secondary channel • Activation – Self-activation, scheduled, human-mediated • Payload – no payload, payloads which open back doors on victim machines, and payloads for denial of service, spam relays, reconnaissance, and damage to victim machines. Weaver, N. , V. Paxson, et al. (2003). 'A Taxonomy of Computer Worms'. Workshop on Rapid Malcode (WORM'03)

The Worm Threat • In November, 1988 the Morris Worm infected an unknown proportion of Unix systems on the Internet with repair costs estimated at $100, 000. (National Institute of Justice, 2001). Targets: sendmail, finger, rsh • On July 19 th, 2001 more than 359, 000 computers were infected with Code Red worm in less than 14 hours. Target: MS IIS web server • On January 25 th, 2003, the SQL Slammer worm infected 90% of vulnerable hosts within 10 minutes, causing network outages and disruptions to airline flights, and ATM machines. Target: MS SQL Server 2000

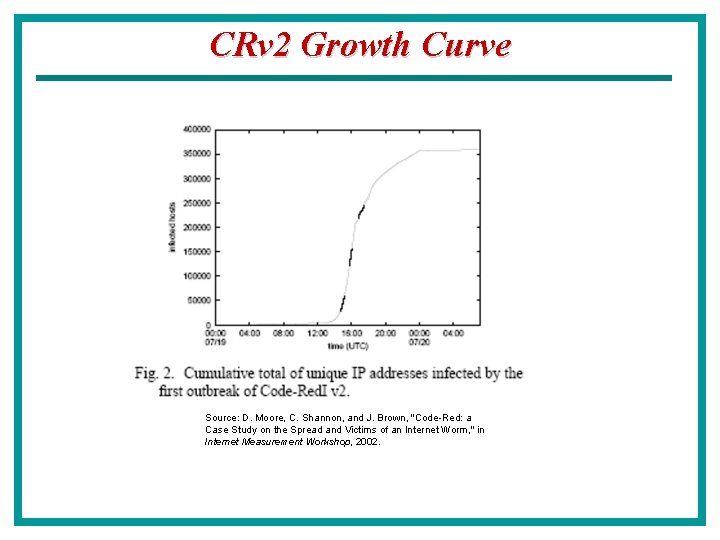
Code Red I Timeline • June 18, 2001: e. Eye Security issued an advisory regarding a buffer overflow vulnerability in the MS IIS web server • June 26: Microsoft releases a patch for the vulnerability • July 12: Code Red I is released – Memory-resident, random scanning – Time-dependent behavior: • Before 20 th day of the month: infection • 20 th – 28 th day of the month: Do. S attack against www 1. whitehouse. gov • After 28 th day of the month: dormant – Slow spread due to static random seed • July 19: random variant worm, Code Red I ver 2 is released – 359, 000 machines infected in less than 14 hours

CRv 2 Growth Curve Source: D. Moore, C. Shannon, and J. Brown, "Code-Red: a Case Study on the Spread and Victims of an Internet Worm, " in Internet Measurement Workshop, 2002.

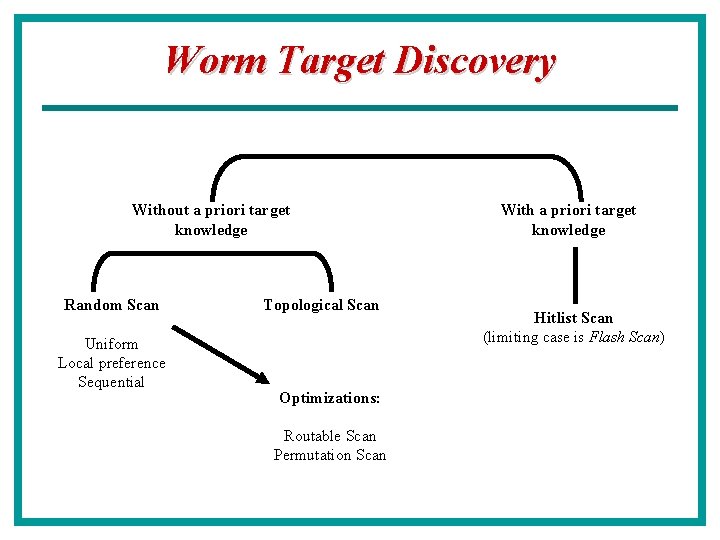
Worm Target Discovery Without a priori target knowledge Random Scan Uniform Local preference Sequential Topological Scan Optimizations: Routable Scan Permutation Scan With a priori target knowledge Hitlist Scan (limiting case is Flash Scan)

Bot and Bot. Net • Bot is a zombie computer • Bot software downloaded and installed, often as rootkit • Bots connect through TCP/IP to controller (mother ship) • Bots can be reprogrammed from controller • Botnets used to launch spam, DDOS

Bot and Bot. Net • Case study: Storm Botnet • By Sep 2007 running on between 1 and 50 million computers worldwide (at one point 8% of all Windows malware) • Vector was XSS – used phishing to get users to activate Web link • Used in varietyu of criminal activities, including DDOS and spam • Has displayed defensive behaviors • Developers not caught yet – believed to have originated in Russia • Believed that code has been sold to other hacker groups

Network Telescopes A commonly used monitor for worm activity is the network telescope Network telescopes monitor large segments of dark, or unused, address space containing few, if any, production hosts No or very little legitimate traffic is expected to be observed targeting telescope address space

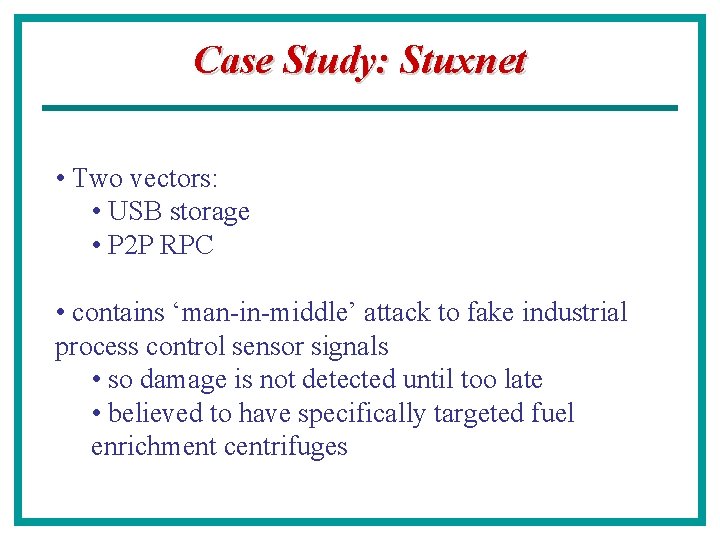
Case Study: Stuxnet • Computer worm first analyzed in July, 2010 • First known case of ‘targeted’ worm that attacks industrial control systems • spreads indiscriminately, contains payload that targets Siemens control systems • believed to have been targeted against Iran nuclear fuel enrichment program • analysts believe it was created by nation-state, possibly US/Israel

Case Study: Stuxnet • First appeared June 2009 – improved variants in March and April 2010 • Primarily found in 8 countries, but over 60% of infections in Iran • Makes itself inert if it does not detect Siemens control software • 3 -layered attack: • Windows zero-day vulnerabilities • Step 7 industrial application • Siemens PLC

Case Study: Stuxnet • Two vectors: • USB storage • P 2 P RPC • contains ‘man-in-middle’ attack to fake industrial process control sensor signals • so damage is not detected until too late • believed to have specifically targeted fuel enrichment centrifuges

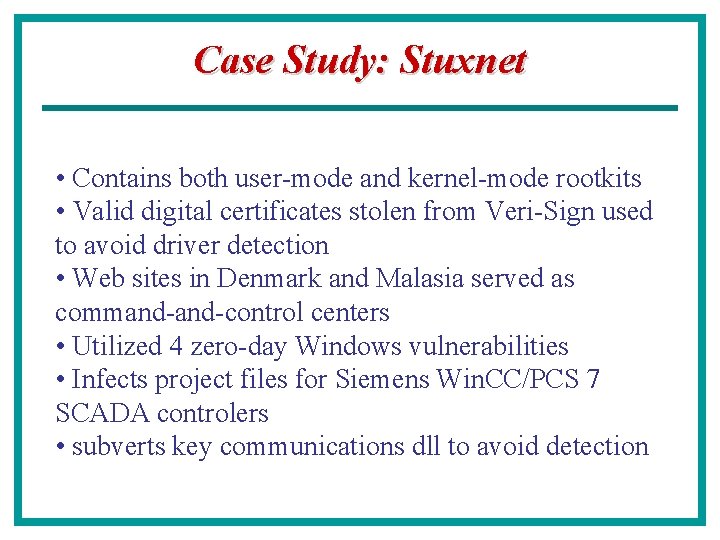
Case Study: Stuxnet • Contains both user-mode and kernel-mode rootkits • Valid digital certificates stolen from Veri-Sign used to avoid driver detection • Web sites in Denmark and Malasia served as command-control centers • Utilized 4 zero-day Windows vulnerabilities • Infects project files for Siemens Win. CC/PCS 7 SCADA controlers • subverts key communications dll to avoid detection

Case Study: Stuxnet • Stuxnet is VERY sophisticated • indicates multi-level, evolving attack strategy • believed to have been developed as a targeted cyberwarfare weapon • has raised awareness among cyber-security commands • similar attacks could target power grids, communications, oil refineries, shipyards, etc. • (see movie ‘Eagle Eye’ for hypothetical potential)