Definition v What is Security Policies procedures and

























- Slides: 44


Definition v What is Security? � § Policies, procedures and technical measures used to prevent unauthorized access, alteration, theft, or physical damage to information systems v What is Control? � § Methods, policies, and organizational procedures that ensure safety of organization’s assets; accuracy and reliability of its accounting records; and operational adherence to management standards 2

Why Security? § Computer security is required because most organizations can be damaged by hostile software or intruders. § There may be several forms of damage which are obviously interrelated. These include: • Damage or destruction of computer systems. • Damage or destruction of internal data. • Loss of sensitive information to hostile parties. • Use of sensitive information to steal items of monetary value. • Use of sensitive information against the organization's customers which may result in legal action by customers against the organization and loss of customers. 3

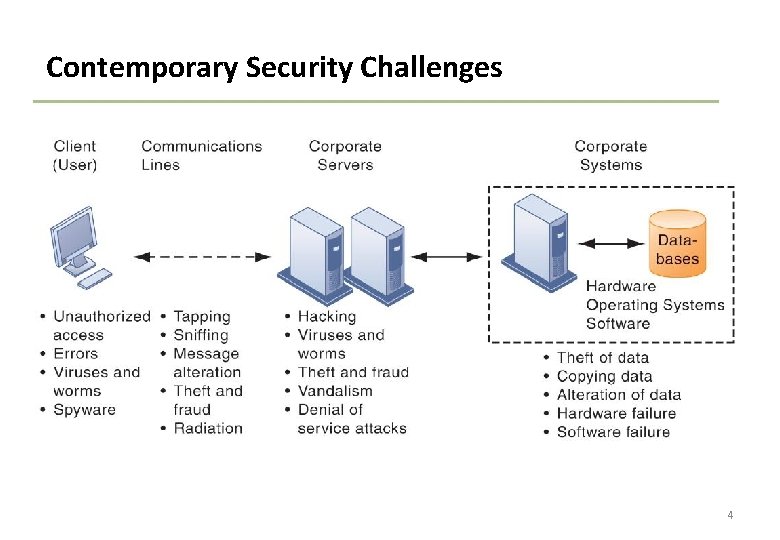
Contemporary Security Challenges 4

Malicious Software § Malware, short for malicious software, is any software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. § Malware is defined by its malicious intent, acting against the requirements of the computer user, and does not include software that causes unintentional harm due to some deficiency. § The term badware is sometimes used, and applied to both true (malicious) malware and unintentionally harmful software. 5

Malicious Software § Malware may be stealthy, intended to steal information or spy on computer users for an extended period without their knowledge, or it may be designed to cause harm, often as sabotage, or to extort payment. § 'Malware' is an umbrella term used to refer to a variety of forms of hostile or intrusive software, including computer viruses, worms, trojan horses, ransomware, spyware, adware, scareware, and other malicious programs. It can take the form of executable code, scripts, active content, and other software. 6

Malicious Software v Viruses § A virus is a program that searches out other programs and infects them by embedding a copy of itself. When the infected program executes, the embedded virus is executed, which propagates the infection. § A virus is a piece of code that spreads from one computer to another by attaching itself to other files. § The code in a virus corrupts and erases files on a user's computer, or performs other destructive or annoying tasks, when the file to which it was attached is opened or executed. https: //software 1. knoji. com/different-types-of-malicious-software/ 7

Malicious Software v Worms § A worm is a piece of code that spreads from one computer to another on its own, not by attaching itself to another file. § Like a virus, a worm can corrupt or erase files on your hard drive or perform other destructive or annoying operations. § Worms utilize networks to send copies of the original code to other computers, causing harm by consuming bandwidth or possibly deleting files or sending documents via email. https: //software 1. knoji. com/different-types-of-malicious-software/ 8

Malicious Software v Trojan horses § A Trojans, or Trojan horse, is malicious code that masquerades as a harmless file. When a user executes the Trojan, thinking it is a legitimate application, it can perform damaging or annoying operations. § It can continue to masquerade as a legitimate program, while in the background it captures input from the user and transmits the data to an attacker. https: //software 1. knoji. com/different-types-of-malicious-software/ 9

Malicious Software v Logic bombs § A logic bomb is a piece of code that sits dormant on a user's computer until it is triggered by a specific event, such as a specific date. § Once the code is trig¬gered, the logic bomb "detonates, " erasing and corrupting data on the user's computer or performing other destructive or annoying operations. 10

Malicious Software v Spyware • • Spyware is unwanted software that runs in the background to monitor system activities and send collected personal user data to a third party. Spyware is a general term used to describe software that performs certain behaviors, generally without appropriately obtaining your consent first, such as: § Advertising § Collecting personal information § Changing the configuration of your computer § Spyware is often associated with software that displays advertisements (called adware) or software that tracks personal or sensitive information. https: //software 1. knoji. com/different-types-of-malicious-software/ 11

Malicious Software v Adware • • Adware is unwanted software loaded onto a system for the purposes of presenting commercial advertisements to the user. It can run in the background and collect data about the user in order to present customized advertisements. It can also function as spyware. The user is often unaware that the adware has penetrated the system. The adware itself can create annoyances or adverse system conditions, or the adware can be a vector for introducing other types of malicious software. 12

Malicious Software v Spam • • • It is generally taken to mean unsolicited or distasteful commercial email from anonymous sources. Spam creates nuisance conditions by filling user mailboxes with unwanted or inappropriate messages, and impedes email system performance by filling up email servers' storage areas and generating excessive network traffic. Although not technically software, spam travels via email software, which is why it is often considered to be a type of malicious software. 13

Malicious Software v Keyloggers • • • A keylogger (short for keystroke logger) is software that tracks or logs the keys struck on your keyboard, typically in a covert manner so that you don’t know that your actions are being monitored. This is usually done with malicious intent to collect your account information, credit card numbers, user names, passwords, and other private data. Legitimate uses do exist for key loggers. Parents can monitor their children’s online activity or law enforcement may use it to analyze and track incidents linked to the use of personal computers, and employers can make sure their employees are working instead of surfing the web all day. https: //blogs. mcafee. com/consumer/what-is-a-keylogger 14

Hackers and Crackers v Hackers: The White Hats • Just like in the old Hollywood westerns, the good guys wear the white hats, at least metaphorically. White hat is a term often used to describe ethical hackers that stay entirely within the law. • They never access a system or network illegally, and they work tirelessly to expose holes in systems with the ultimate goal of fixing flaws and improving security. Upon finding a flaw, a white hat will usually notify the software vendor and give the company a chance to patch the flaw before making the bug public knowledge. http: //www. security-faqs. com/what-are-the-main-differences-between-hackers-and-crackers. html 15

Hackers and Crackers v Hackers: The White Hats (Cont. ) • White hats may be security professionals, hired by companies to audit network security or test software. • Using the same software tools that crackers use, a white hat seeks to improve the security of his own network by proactively attacking it as a cracker would. • White hats may even create software aimed at thwarting tools available to crackers. http: //www. security-faqs. com/what-are-the-main-differences-between-hackers-and-crackers. html 16

Hackers and Crackers v Crackers: The Black Hats • Hackers refer to the computer world’s outlaws as black hats. The opposite of the white hat, a black hat or cracker breaks into systems illegality for personal gain, vandalism, or bragging rights. • A cracker doesn’t need to be particularly knowledgeable or skillful; in fact, most of them aren’t. Few crackers are skilled enough to create their own software tools, so most rely on automated programs that they download from disreputable Web sites. http: //www. security-faqs. com/what-are-the-main-differences-between-hackers-and-crackers. html 17

Hackers and Crackers v Crackers: The Black Hats (Cont. ) • Because crackers know they are breaking the law, they do everything they can to cover their tracks. • Fortunately, security professionals catch quite a few of them because the majority of crackers lack real skill. • When the authorities do catch them, their skill with a computer is often greatly exaggerated to promote the agency making the arrest (and to sell newspapers and commercials). • It’s important to acknowledge that crackers present a serious threat: Many are technically proficient and can cause a lot of damage, and many systems are so woefully insecure that even technically inept crackers can wreak havoc on them. http: //www. security-faqs. com/what-are-the-main-differences-between-hackers-and-crackers. html 18

Hackers and Crackers v Gray Hats • A gray hat is a name given to an otherwise ethical hacker who walks a fine line between legal and illegal hacking. • Like white hats, gray hats find security holes and report them; but unlike white hats, they often publicize the flaw before giving the software developers a chance to fix the problem. • Gray hats maintain that they are improving security by compelling companies to fix software. • Gray hats may also access computer systems without permission, with the intent to find and report flaws. While it’s better to have a gray hat finding holes in your network rather than a black hat, when you’re under attack you have no way of distinguishing between the two. http: //www. security-faqs. com/what-are-the-main-differences-between-hackers-and-crackers. html 19

Framework for Security and Control v v v v v Information Systems Controls General Control and Types of General Control Application Controls Risk Assessment Security Policy Authorization Management Systems Security Profiles of a Personnel System Disaster Recovery Planning Business Continuity Planning The Role of Auditing 20

Technologies and Tools for Security v Firewall • a firewall is a network security system that controls the incoming and outgoing network traffic based on an applied rule set. • A firewall is a system designed to prevent unauthorized access to or from a private network. • Firewalls can be implemented in both hardware and software, or a combination of both. • Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. 21

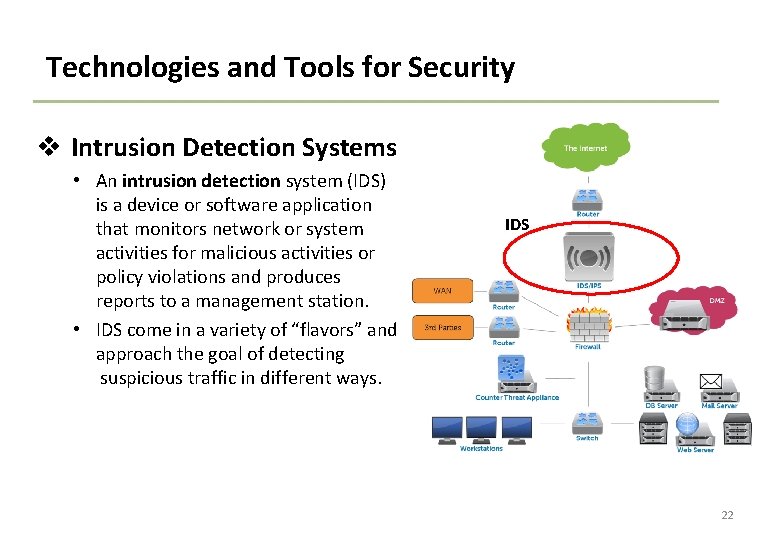
Technologies and Tools for Security v Intrusion Detection Systems • An intrusion detection system (IDS) is a device or software application that monitors network or system activities for malicious activities or policy violations and produces reports to a management station. • IDS come in a variety of “flavors” and approach the goal of detecting suspicious traffic in different ways. IDS 22

Technologies and Tools for Security v Antivirus software • Antivirus or anti-virus software (often abbreviated as AV), sometimes known as anti-malware software, is computer software used to prevent, detect and remove malicious software. • Antivirus software was originally developed to detect and remove computer viruses. However, with the proliferation of other kinds of malware, antivirus software started to provide protection from other computer threats. • In particular, modern antivirus software can protect from: keyloggers, backdoors, rootkits, trojan horses, worms, fraudtools, adware and spyware. • Some products also include protection from other computer threats, such as infected and malicious spam, phishing attacks, online identity, botnets. 23

Technologies and Tools for Security v Securing Wireless Networks • Wired Equivalent Privacy (WEP) WEP aims to provide security by encrypting data over radio waves so that it is protected as it is transmitted from one end point to another. • Wi-Fi Protected Access (WPA & WPA 2) Both WPA and WPA 2 are much more secure than WEP. The encryption keys they use change each time a device accesses the network, making it more difficult to hack than WEP. 24

Technologies and Tools for Security v Encryption and Public Key Infrastructure • A public key infrastructure (PKI) supports the distribution and identification of public encryption keys, enabling users and computers to both securely exchange data over networks such as the Internet and verify the identity of the other party. • Without PKI, sensitive information can still be encrypted (ensuring confidentiality) and exchanged, but there would be no assurance of the identity (authentication) of the other party. Any form of sensitive data exchanged over the Internet is reliant on PKI for security. 25

Technologies and Tools for Security v Encryption and Public Key Infrastructure (Cont. ) A typical PKI includes the following key elements: • A trusted party, called a certificate authority (CA), acts as the root of trust and provides services that authenticate the identity of individuals, computers and other entities. • A registration authority, often called a subordinate CA, certified by a root CA to issue certificates for specific uses permitted by the root. • A certificate database, which stores certificate requests and issues and revokes certificates. • A certificate store, which resides on a local computer as a place to store issued certificates and private keys. 26

Technologies and Tools for Security v Digital Certificate • A digital certificate is an electronic "passport" that allows a person, computer or organization to exchange information securely over the Internet using the public key infrastructure (PKI). • A digital certificate may also be referred to as a public key certificate. • A digital certificate provides identifying information, is forgery resistant and can be verified because it was issued by an official, trusted agency. • The certificate contains the name of the certificate holder, a serial number, expiration dates, a copy of the certificate holder's public key (used for encrypting messages and digital signatures) and the digital signature of the certificate-issuing authority (CA) so that a recipient can verify that the certificate is real. 27

Common Types of Computer Attacks • Without security measures and controls in place, your data might be subjected to an attack. • Some attacks are passive, meaning information is monitored; others are active, meaning the information is altered with intent to corrupt or destroy the data or the network itself. • Your networks and data are vulnerable to any of the following types of attacks if you do not have a security plan in place. https: //technet. microsoft. com/en-us/library/cc 959354. aspx 28

Common Types of Computer Attacks v Eavesdropping § In general, the majority of network communications occur in an unsecured or "cleartext" format, which allows an attacker who has gained access to data paths in your network to "listen in" or interpret (read) the traffic. § When an attacker is eavesdropping on your communications, it is referred to as sniffing or snooping. § The ability of an eavesdropper to monitor the network is generally the biggest security problem that administrators face in an enterprise. § Without strong encryption services that are based on cryptography, your data can be read by others as it traverses the network. https: //technet. microsoft. com/en-us/library/cc 959354. aspx 29

Common Types of Computer Attacks v Data Modification § After an attacker has read your data, the next logical step is to alter it. § An attacker can modify the data in the packet without the knowledge of the sender or receiver. § Even if you do not require confidentiality for all communications, you do not want any of your messages to be modified in transit. § For example, if you are exchanging purchase requisitions, you do not want the items, amounts, or billing information to be modified. https: //technet. microsoft. com/en-us/library/cc 959354. aspx 30

Common Types of Computer Attacks v Identity Spoofing (IP Address Spoofing) § Most networks and operating systems use the IP address of a computer to identify a valid entity. § In certain cases, it is possible for an IP address to be falsely assumed— identity spoofing. § An attacker might also use special programs to construct IP packets that appear to originate from valid addresses inside the corporate intranet. § After gaining access to the network with a valid IP address, the attacker can modify, reroute, or delete your data. The attacker can also conduct other types of attacks, as described in the following sections. https: //technet. microsoft. com/en-us/library/cc 959354. aspx 31

Common Types of Computer Attacks v Password-Based Attacks § A common denominator of most operating system and network security plans is password-based access control. This means your access rights to a computer and network resources are determined by who you are, that is, your user name and your password. § Older applications do not always protect identity information as it is passed through the network for validation. This might allow an eavesdropper to gain access to the network by posing as a valid user. § When an attacker finds a valid user account, the attacker has the same rights as the real user. Therefore, if the user has administrator-level rights, the attacker also can create accounts for subsequent access at a later time. https: //technet. microsoft. com/en-us/library/cc 959354. aspx 32

Common Types of Computer Attacks v Password-Based Attacks (Cont. ) § After gaining access to your network with a valid account, an attacker can do any of the following: • Obtain lists of valid user and computer names and network information. • Modify server and network configurations, including access controls and routing tables. • Modify, reroute, or delete your data. https: //technet. microsoft. com/en-us/library/cc 959354. aspx 33

Common Types of Computer Attacks v Denial-of-Service Attack § Unlike a password-based attack, the denial-of-service attack prevents normal use of your computer or network by valid users. § After gaining access to your network, the attacker can do any of the following: • Randomize the attention of your internal Information Systems staff so that they do not see the intrusion immediately, which allows the attacker to make more attacks during the diversion. • Send invalid data to applications or network services, which causes abnormal termination or behavior of the applications or services. • Flood a computer or the entire network with traffic until a shutdown occurs because of the overload. • Block traffic, which results in a loss of access to network resources by authorized users. https: //technet. microsoft. com/en-us/library/cc 959354. aspx 34

Common Types of Computer Attacks v Man-in-the-Middle Attack § As the name indicates, a man-in-the-middle attack occurs when someone between you and the person with whom you are communicating is actively monitoring, capturing, and controlling your communication transparently. § For example, the attacker can re-route a data exchange. When computers are communicating at low levels of the network layer, the computers might not be able to determine with whom they are exchanging data. § Man-in-the-middle attacks are like someone assuming your identity in order to read your message. The person on the other end might believe it is you because the attacker might be actively replying as you to keep the exchange going and gain more information. https: //technet. microsoft. com/en-us/library/cc 959354. aspx 35

Common Types of Computer Attacks v Sniffer Attack § A sniffer is an application or device that can read, monitor, and capture network data exchanges and read network packets. If the packets are not encrypted, a sniffer provides a full view of the data inside the packet. Even encapsulated (tunneled) packets can be broken open and read unless they are encrypted and the attacker does not have access to the key. § Using a sniffer, an attacker can do any of the following: • Analyze the network and gain information to eventually cause your network to crash or to become corrupted. • Read the communications. https: //technet. microsoft. com/en-us/library/cc 959354. aspx 36

Common Types of Computer Attacks v Application-Layer Attack § An application-layer attack targets application servers by deliberately causing a fault in a server's operating system or applications. § This results in the attacker gaining the ability to bypass normal access controls. The attacker takes advantage of this situation, gaining control of your application, system, or network, and can do any of the following: • Read, add, delete, or modify your data or operating system. • Introduce a virus program that uses your computers and software applications to copy viruses throughout your network. • Introduce a sniffer program to analyze your network and gain information that can eventually be used to crash or to corrupt your systems and network. • Disable other security controls to enable future attacks. https: //technet. microsoft. com/en-us/library/cc 959354. aspx 37

Common Types of Computer Attacks v Botnets § A bot is short for “robot” and is a piece of code that carries out functionality for its master, who is the author of this code. Bots are a type of malware. § It is a piece of dormant code, also known as a zombie, that is used to forward items sent to it. Item sent to bots can be spam, viruses, pornography, or attack code. The reason to send these types of items through bots is to help ensure that the original sender will not be located and identified. § When the hacker has a collection of these compromised systems, it is referred to as a botnet (network of bots). The hacker can use all of these systems to carry out powerful DDOS attacks or even rent these systems to spammers. https: //technet. microsoft. com/en-us/library/cc 959354. aspx 38

How to Stay Safe • Be aware: Use common sense when on the Internet. New attacks are released every day. • Treat all public Wi-Fi links with suspicion: It’s virtually impossible to tell the difference between a safe and an unsafe network. Best to treat them all with suspicion. • When using public Wi-Fi, avoid doing anything sensitive: Don’t buy anything, login to your financial accounts, or even send email when accessing public Wi-Fi networks. Wait until you get back home to your secure network to do those kinds of things. Better to be safe than sorry. • Make sure you are using antivirus software: It’s not a foolproof solution, but antivirus software can help repel most known attacks. Be sure to keep it updated. https: //technet. microsoft. com/en-us/library/cc 959354. aspx 39

How to Stay Safe • Think about using identity protection and monitoring services: This is a great way to protect yourself and your family from identity theft. • Use a VPN: A VPN like PRIVATE Wi-Fi allows you to use public Wi-Fi networks as if they were private and secure. A VPN is a good solution to possible man-in-themiddle attacks if you must use public Wi-Fi. https: //technet. microsoft. com/en-us/library/cc 959354. aspx 40

Thai. CERT: Thailand Computer Emergency Response Team https: //www. thaicert. or. th/about-en. html 41

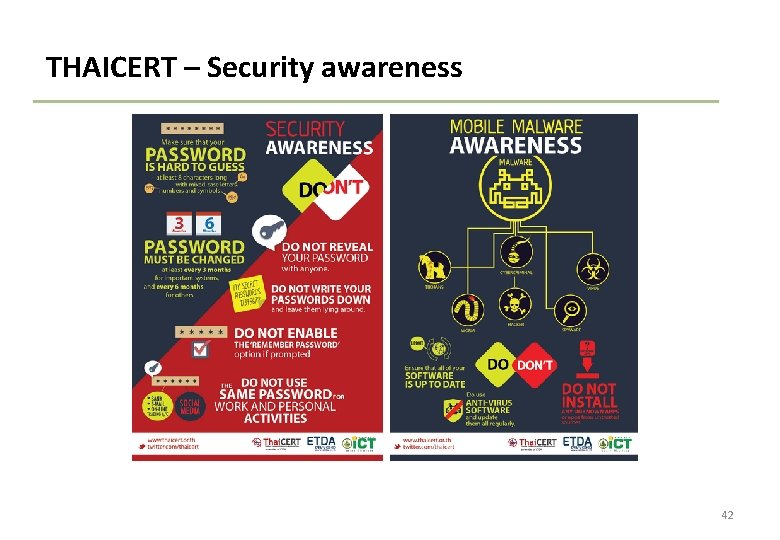
THAICERT – Security awareness 42

Q & A 1. How to stay safe from computer attacks? 2. Explain what firewall protect and what they do not protect. 43

Reference • • Turban, E. , Mclean, E. , and Wetherbe, J. (2002) Information Technology for management; transforming business in digital economy, 3 rd edition, John Wiley & Sons , New York. Turban, E. , Rainer, R. and Potter, R. (2003) Introduction to Information technology, 2 nd edition, John Wiley & Sons, New York. Stair, R. and Reynolds, G. (1999) Principles of Information Systems: a managerial approach, 4 th edition, Course Technology, Cambridge. Bocij, P. , Chafffey, D. , Greasley, A. and Hickie, S. (2006) Business Information System: Technology, development and management for the e-business, 3 rd edition, Prentice Hall, Harlow, England. 44