Computer Security Policies 322021 1 Security Policies We













- Slides: 21

Computer Security Policies. . 3/2/2021 1

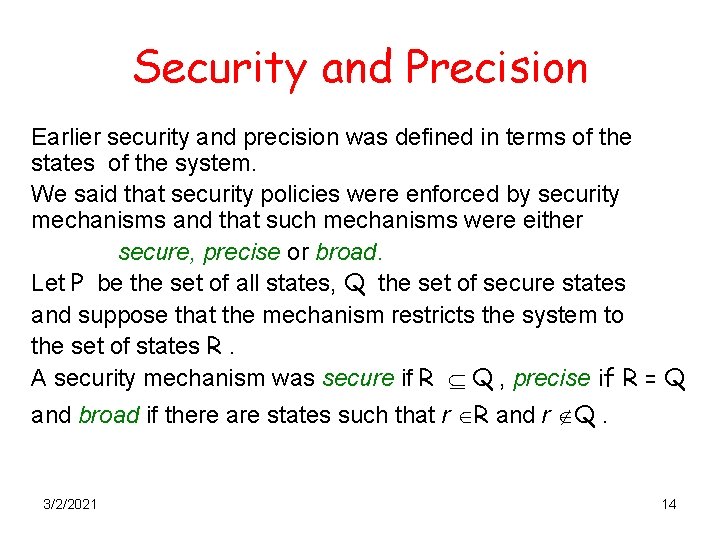
Security Policies We view a computer system as a finite-state machine Definition A security policy is a statement that partitions the states of a system into a set of authorized or secure states and a set of unauthorized or nonsecure states. A secure system is a system that starts in an authorized state and cannot enter an unauthorized state. 3/2/2021 2

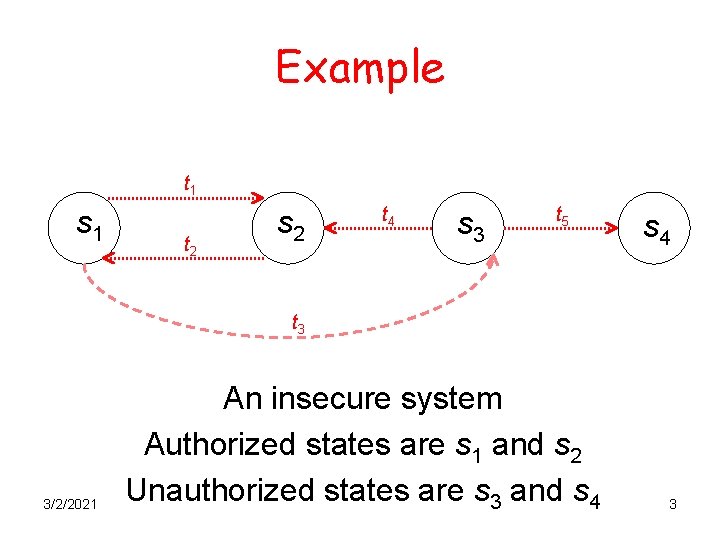
Example t 1 s 1 t 2 s 2 t 4 s 3 t 5 s 4 t 3 3/2/2021 An insecure system Authorized states are s 1 and s 2 Unauthorized states are s 3 and s 4 3

Security Policies Definition 1. 2. 3. 5. A breach of security occurs when a system enters an unauthorized state. Let X be a set of entities and I be some information. I has the property of confidentiality with respect to X if no member of X can obtain information about I. I has the property of integrity with respect to X if all members of X trust I. Let I be a resource I has the property of availability with respect to X if all member of X can access I. A security mechanism is an entity or procedure that enforces some part of a security policy. 3/2/2021 4

Types of Policies Definition 1. Military security policies or governmental security policies. 2. Commercial security policies • Confidentiality policies • Integrity policies • Transaction policies Discuss issues regarding trust. 3/2/2021 5

The role of trust is fundamental in understanding the nature of computer security. Examples –see textbook [Example 1 -2 -3 -4, pp 101 -102 (high level)& 1 -2 -3 -4 102 -103 (low-level, formal)] 3/2/2021 6

Types of Access Control • • Discretionary Access Control (DAC) or identity based access control. Mandatory Access Control (MAC) or role-based access control. An originator access control (ORCON or ORGON) bases access on the creator of an object. [Examples pp 103 -104] 3/2/2021 7

Discretionary Access Control (DAC) Access control is left to the discretion of the owner. Based on the identity of the subject. [Example –see textbook pp 104 -105 3/2/2021 8

Mandatory Access Control (MAC) The operating system enforces mandatory access controls. Neither the subject nor even the owner can determine access control. Example –see textbook 3/2/2021 9

ORiginator access CONtrol (ORCON or ORGON) The originator of the file (or its information) has control the dissemination of its information. Example –see textbook 3/2/2021 10

Policy languages • High level policy languages: independent of the mechanisms used. • Low level policy languages [Examples pp 104 -105] 3/2/2021 11

High level policy languages Express policy constraints on entities using abstraction and are independent of the security mechanisms. This requires: • An unambiguous expression of policy • A mathematical or programming formulation Details: see textbook. [Examples pp 105 -106] 3/2/2021 12

Low level policy languages A set of inputs or arguments to commands that set or check constraints on a system. For examples, see textbook [Examples pp 109 -110] 3/2/2021 13

Security and Precision Earlier security and precision was defined in terms of the states of the system. We said that security policies were enforced by security mechanisms and that such mechanisms were either secure, precise or broad. Let P be the set of all states, Q the set of secure states and suppose that the mechanism restricts the system to the set of states R. A security mechanism was secure if R Q , precise if R = Q and broad if there are states such that r R and r Q. 3/2/2021 14

Security and Precision We now consider the possibility of devising a generic procedure for developing a mechanism that is security and precise. For this, we will use programs, which will be viewed as abstract functions that “encode” the information that needs to be controlled. 3/2/2021 15

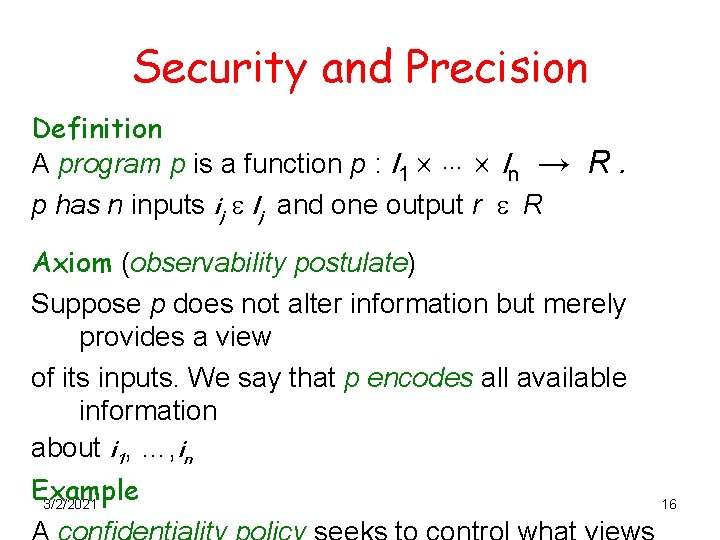
Security and Precision Definition A program p is a function p : I 1 … In → R. p has n inputs ij e Ij and one output r e R Axiom (observability postulate) Suppose p does not alter information but merely provides a view of its inputs. We say that p encodes all available information about i 1, …, in Example 3/2/2021 16

Security and Precision Definition Let p: I 1 In → R be a function 1. A protection mechanism m for p is a function m : R E I 1 In → (E is an error message) for which, when ( i 1, . . . , in ) I 1 , either a. m (i 1, . . . , ik) = p (i 1, . . . , ik) or b. m (i 1, . . . , ik) E. I That is, every “legal” input to m produces either the same value as p or an error message. The set of output values of p that are excluded by m are those 17 3/2/2021 outputs that

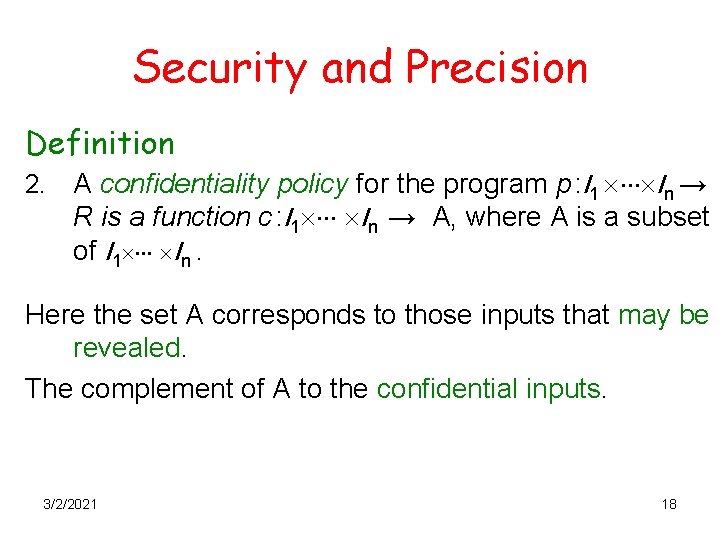
Security and Precision Definition 2. A confidentiality policy for the program p : I 1 In → R is a function c : I 1 In → A, where A is a subset of I 1 In. Here the set A corresponds to those inputs that may be revealed. The complement of A to the confidential inputs. 3/2/2021 18

Security and Precision Definitions 3. Let c be a confidentiality policy for a program p. Let m : I 1 In → R E be a security mechanism for p. The mechanism m is secure iff there is a function m’ : I 1 In → R E such that for all (i 1, . . . , in ) I 1 In: m (i 1, . . . , ik) = m’(c (i 1, . . . , ik)). That is, given any set of inputs, the protection mechanism m 3/2/2021 returns values consistent with the stated policy c 19

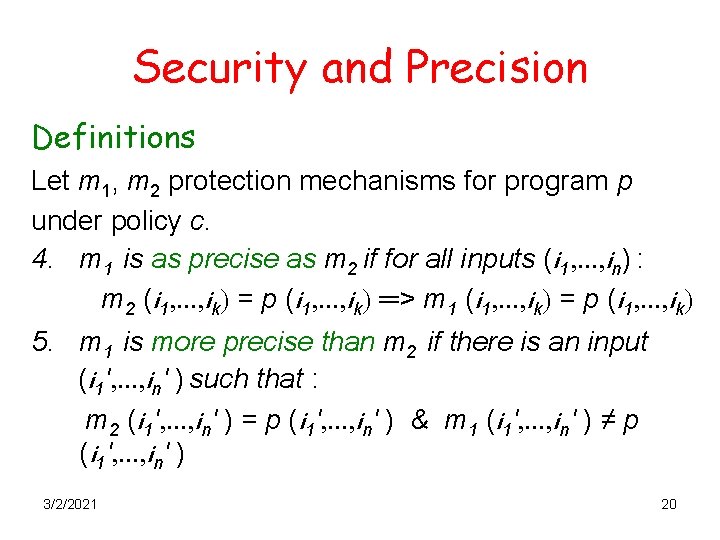
Security and Precision Definitions Let m 1, m 2 protection mechanisms for program p under policy c. 4. m 1 is as precise as m 2 if for all inputs (i 1, . . . , in) : m 2 (i 1, . . . , ik) = p (i 1, . . . , ik) ═> m 1 (i 1, . . . , ik) = p (i 1, . . . , ik) 5. m 1 is more precise than m 2 if there is an input (i 1′, . . . , in′ ) such that : m 2 (i 1′, . . . , in′ ) = p (i 1′, . . . , in′ ) & m 1 (i 1′, . . . , in′ ) ≠ p (i 1′, . . . , in′ ) 3/2/2021 20

Security and Precision Theorems 1. For any program p there exists a precise secure mechanism m* such that for all secure mechanisms m associated with p and c we have m* = m. 2. There is no effective way that determines a (maximally) precise secure mechanism for any policy and program. 3/2/2021 21