Computer Security Confidentiality Policies 1152022 1 Confidentiality Policies






- Slides: 29

Computer Security Confidentiality Policies 1/15/2022 1

Confidentiality Policies A confidentiality policy, or information flow policy prevents unauthorized disclosure of information. 1/15/2022 2

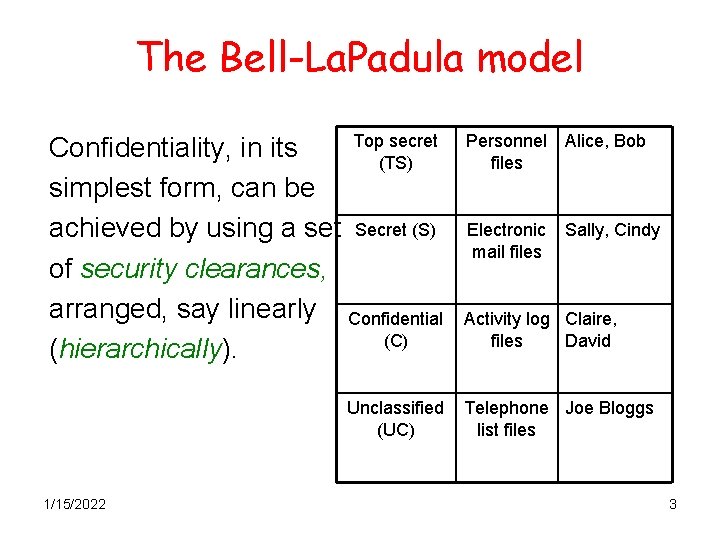
The Bell-La. Padula model Top secret Confidentiality, in its (TS) simplest form, can be achieved by using a set Secret (S) of security clearances, arranged, say linearly Confidential (C) (hierarchically). Unclassified (UC) 1/15/2022 Personnel Alice, Bob files Electronic mail files Sally, Cindy Activity log Claire, files David Telephone Joe Bloggs list files 3

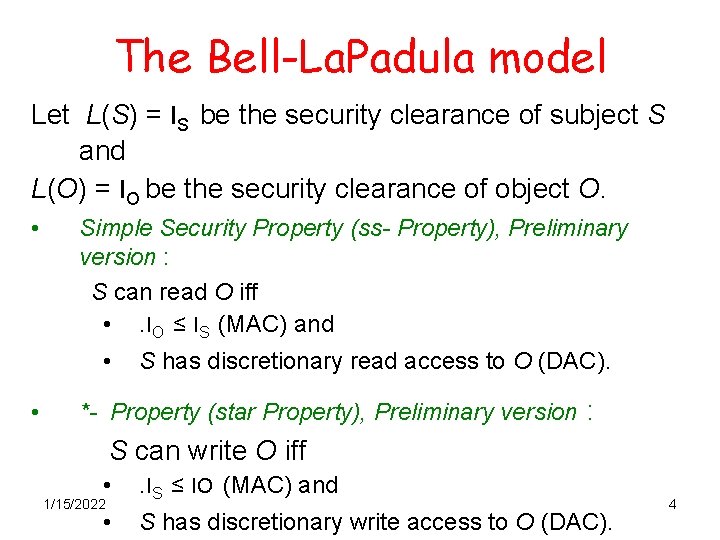
The Bell-La. Padula model Let L(S) = l. S be the security clearance of subject S and L(O) = l. O be the security clearance of object O. • Simple Security Property (ss- Property), Preliminary version : S can read O iff • . l. O ≤ l. S (MAC) and • • S has discretionary read access to O (DAC). *- Property (star Property), Preliminary version : S can write O iff • . l. S ≤ l. O (MAC) and • S has discretionary write access to O (DAC). 1/15/2022 4

Secure Systems A system S is secure if all its states satisfy the ss and * properties. Theorem. Basic Security Theorem, Preliminary version. Let S be a system with secure initial state s 0, and let T be the set of its state transformations. If every element of T 1/15/2022 preserves the ss and *properties then S is 5

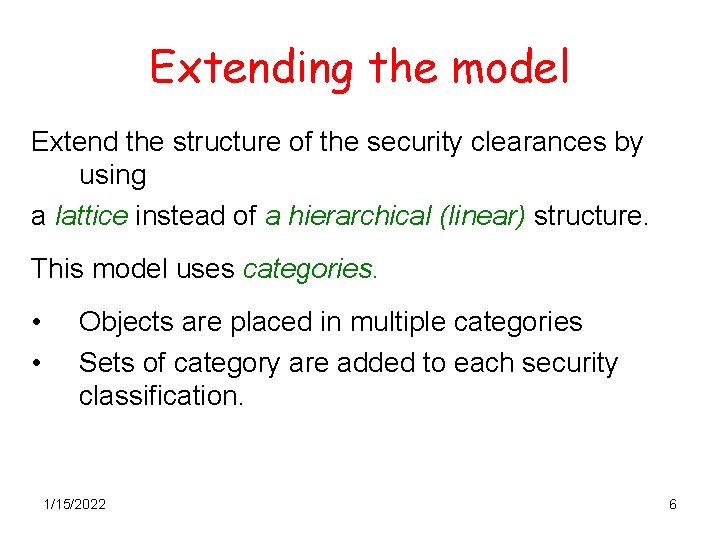
Extending the model Extend the structure of the security clearances by using a lattice instead of a hierarchical (linear) structure. This model uses categories. • • Objects are placed in multiple categories Sets of category are added to each security classification. 1/15/2022 6

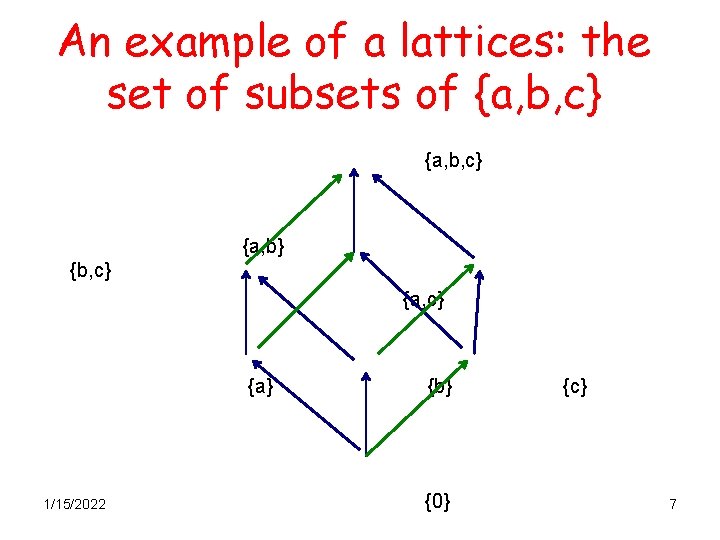
An example of a lattices: the set of subsets of {a, b, c} {a, b} {b, c} {a} 1/15/2022 {b} {0} {c} 7

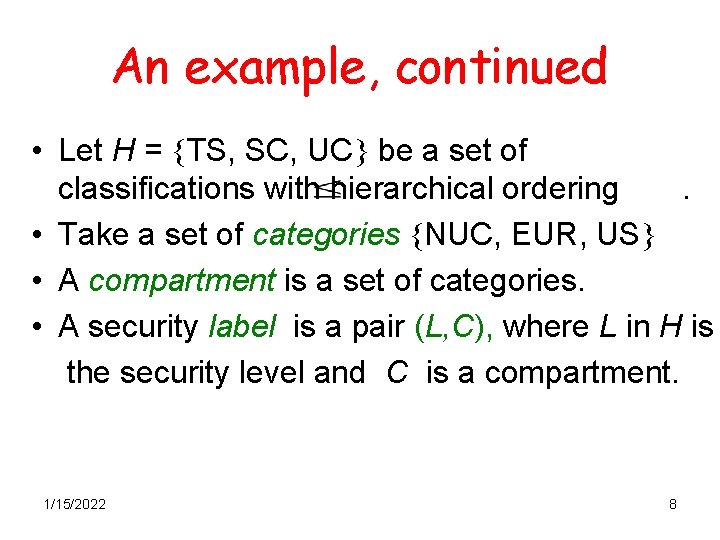
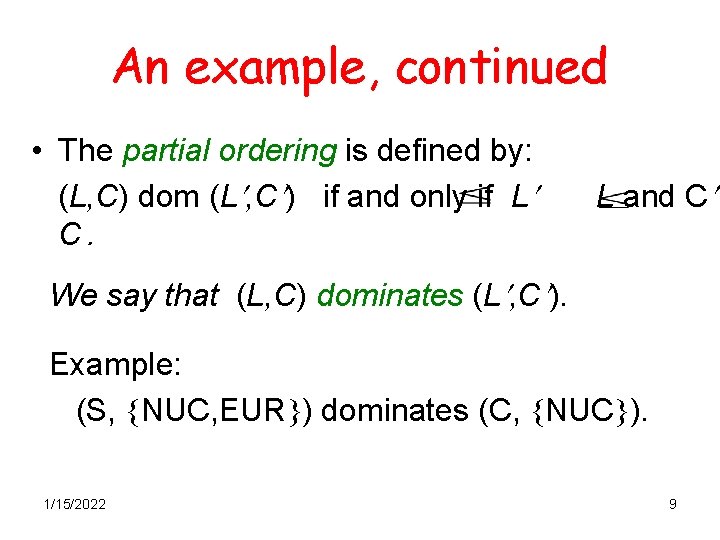
An example, continued • Let H = TS, SC, UC be a set of classifications with hierarchical ordering. • Take a set of categories NUC, EUR, US • A compartment is a set of categories. • A security label is a pair (L, C), where L in H is the security level and C is a compartment. 1/15/2022 8

An example, continued • The partial ordering is defined by: (L, C) dom (L , C ) if and only if L C. L and C We say that (L, C) dominates (L , C ). Example: (S, NUC, EUR ) dominates (C, NUC ). 1/15/2022 9

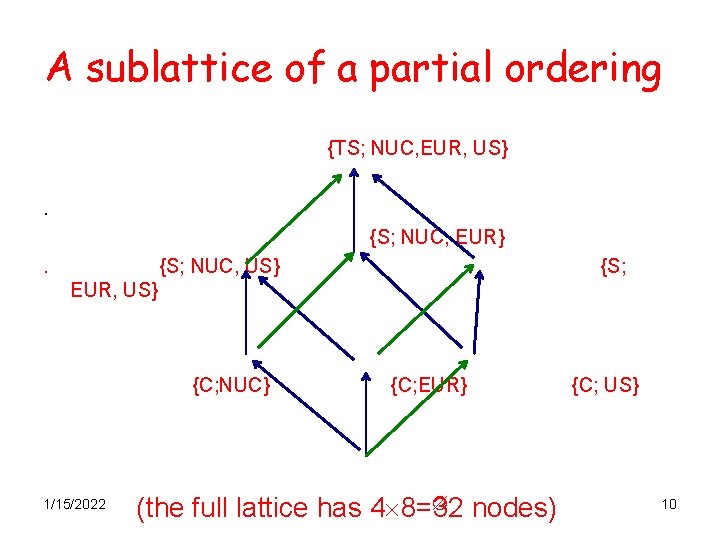
A sublattice of a partial ordering {TS; NUC, EUR, US}. {S; NUC, EUR}. {S; NUC, US} {S; EUR, US} {C; NUC} 1/15/2022 {C; EUR} nodes) (the full lattice has 4 8=32 {C; US} 10

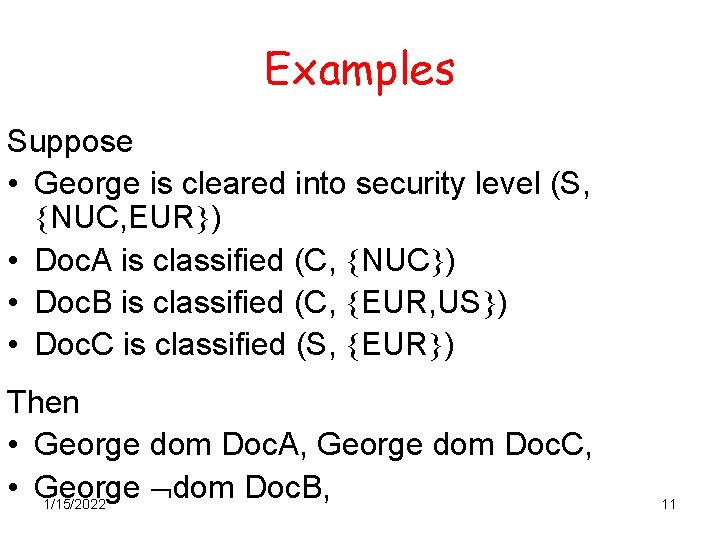
Examples Suppose • George is cleared into security level (S, NUC, EUR ) • Doc. A is classified (C, NUC ) • Doc. B is classified (C, EUR, US ) • Doc. C is classified (S, EUR ) Then • George dom Doc. A, George dom Doc. C, • George dom Doc. B, 1/15/2022 11

Bell-La. Padula (BLP) Model BLP Structure Combines, • . access permission matrices for access control, • a security lattice, for security levels, • an automaton, for access operations. Security policies are reduced to relations in the BLP structure. 1/15/2022 12

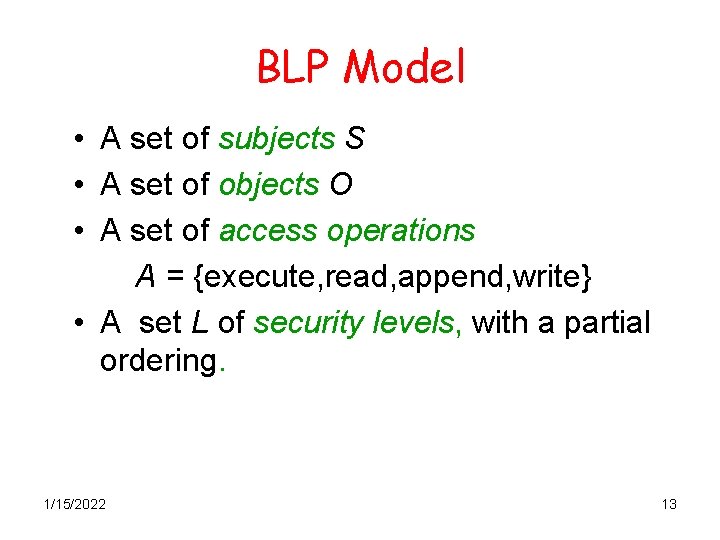
BLP Model • A set of subjects S • A set of objects O • A set of access operations A = {execute, read, append, write} • A set L of security levels, with a partial ordering. 1/15/2022 13

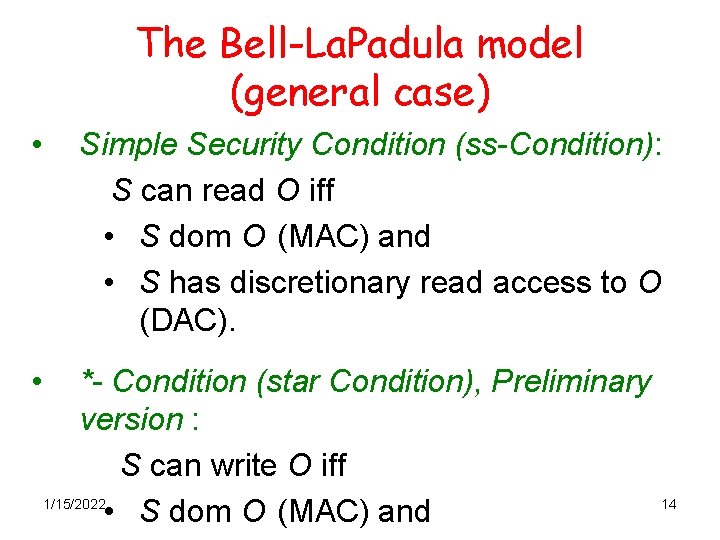
The Bell-La. Padula model (general case) • • Simple Security Condition (ss-Condition): S can read O iff • S dom O (MAC) and • S has discretionary read access to O (DAC). *- Condition (star Condition), Preliminary version : S can write O iff 1/15/2022 • S dom O (MAC) and 14

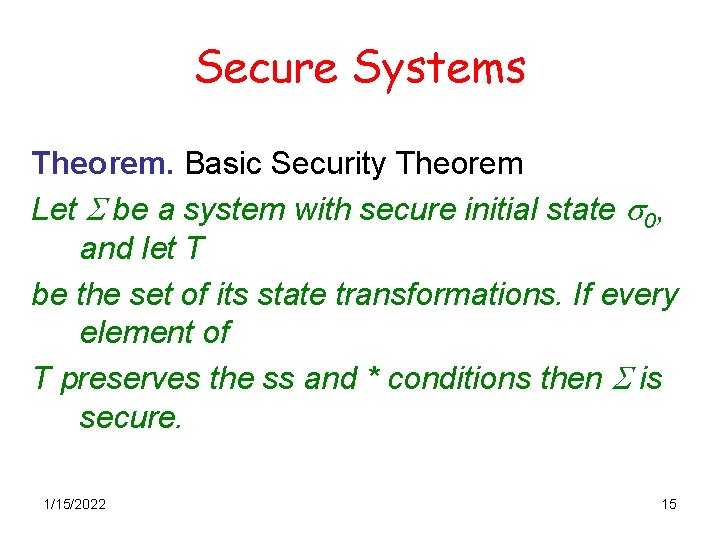
Secure Systems Theorem. Basic Security Theorem Let S be a system with secure initial state s 0, and let T be the set of its state transformations. If every element of T preserves the ss and * conditions then S is secure. 1/15/2022 15

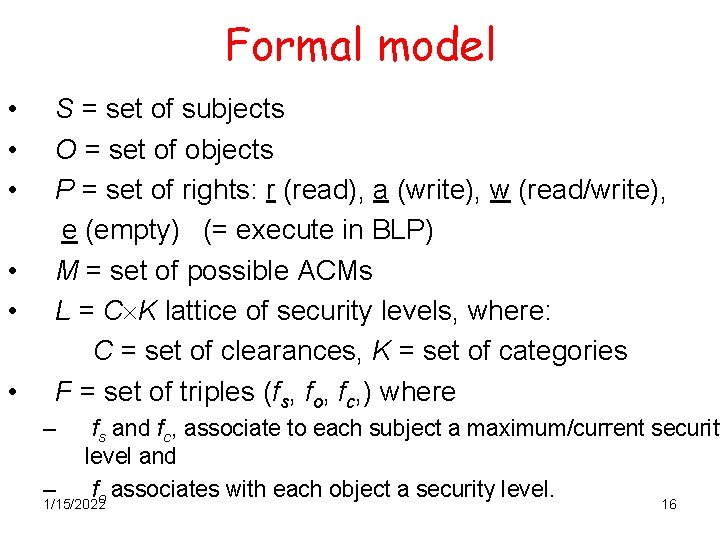
Formal model • • • S = set of subjects O = set of objects P = set of rights: r (read), a (write), w (read/write), e (empty) (= execute in BLP) M = set of possible ACMs L = C K lattice of security levels, where: C = set of clearances, K = set of categories F = set of triples (fs, fo, fc, ) where – – fs and fc, associate to each subject a maximum/current security level and fo associates with each object a security level. 1/15/2022 16

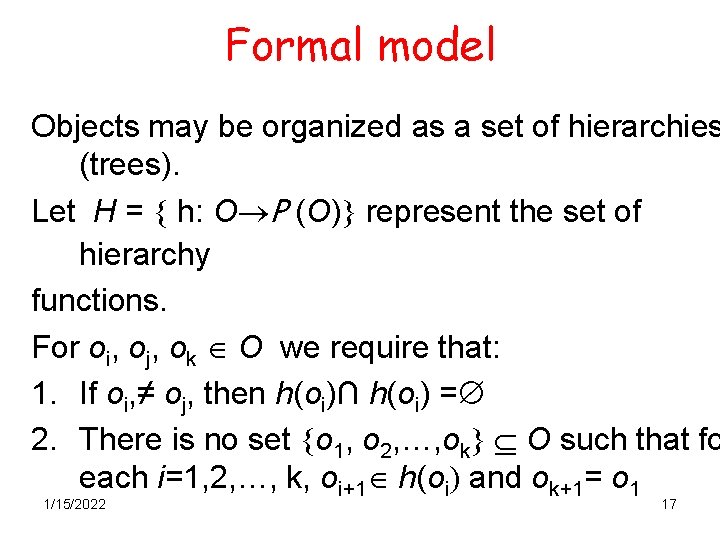
Formal model Objects may be organized as a set of hierarchies (trees). Let H = h: O P (O) represent the set of hierarchy functions. For oi, oj, ok O we require that: 1. If oi, ≠ oj, then h(oi)∩ h(oi) = 2. There is no set o 1, o 2, …, ok O such that fo each i=1, 2, …, k, oi+1 h(oi) and ok+1= o 1 1/15/2022 17

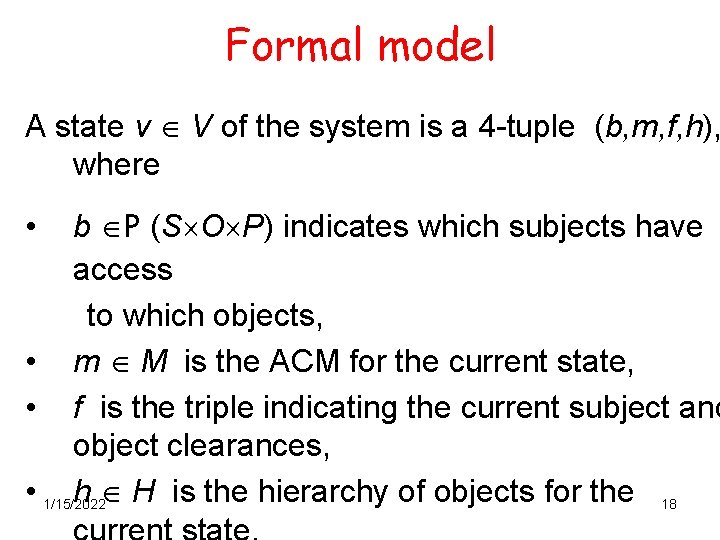
Formal model A state v V of the system is a 4 -tuple (b, m, f, h), where b P (S O P) indicates which subjects have access to which objects, • m M is the ACM for the current state, • f is the triple indicating the current subject and object clearances, • 1/15/2022 h H is the hierarchy of objects for the 18 •

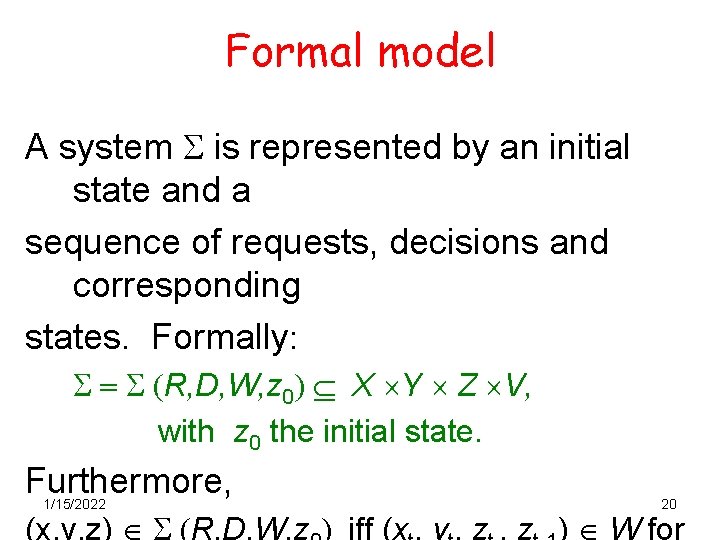
Formal model • • • R denotes the set of requests. D denotes the set of outcomes (decisions). W R D V V the set of actions of the system. The history of a system as it executes. Let N be the set of +ve integers (representing time) • X = RN are sequences of requests x (a tuple) • Y = DN are sequences of decisions y (a tuple) • Z = VN are sequences of states z (a tuple) We interpret this as follows: at some point in time t N: • The system is in state vt-1 • A subject makes a request xi • The system makes a decision yi 1/15/2022 • The system transitions into a possibly new state yi 19

Formal model A system S is represented by an initial state and a sequence of requests, decisions and corresponding states. Formally: S = S (R, D, W, z 0) X Y Z V, with z 0 the initial state. Furthermore, 1/15/2022 20 (x, y, z) S (R, D, W, z ) iff (x , y , z ) W for

An example See textbook p. 133 1/15/2022 21

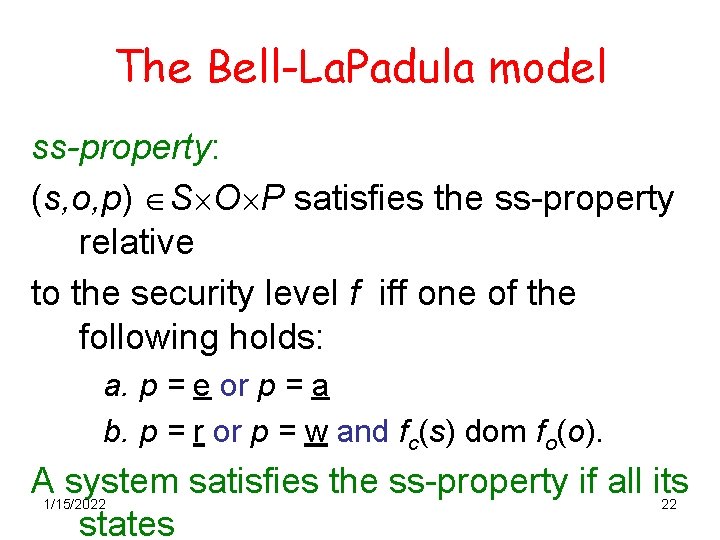
The Bell-La. Padula model ss-property: (s, o, p) S O P satisfies the ss-property relative to the security level f iff one of the following holds: a. p = e or p = a b. p = r or p = w and fc(s) dom fo(o). A system satisfies the ss-property if all its states 1/15/2022 22

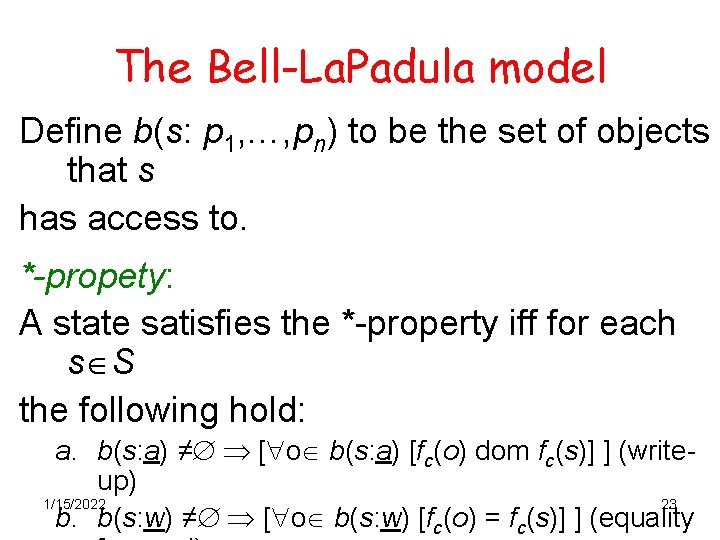
The Bell-La. Padula model Define b(s: p 1, …, pn) to be the set of objects that s has access to. *-propety: A state satisfies the *-property iff for each s S the following hold: a. b(s: a) ≠ [ o b(s: a) [fc(o) dom fc(s)] ] (writeup) 1/15/2022 23 b. b(s: w) ≠ [ o b(s: w) [fc(o) = fc(s)] ] (equality

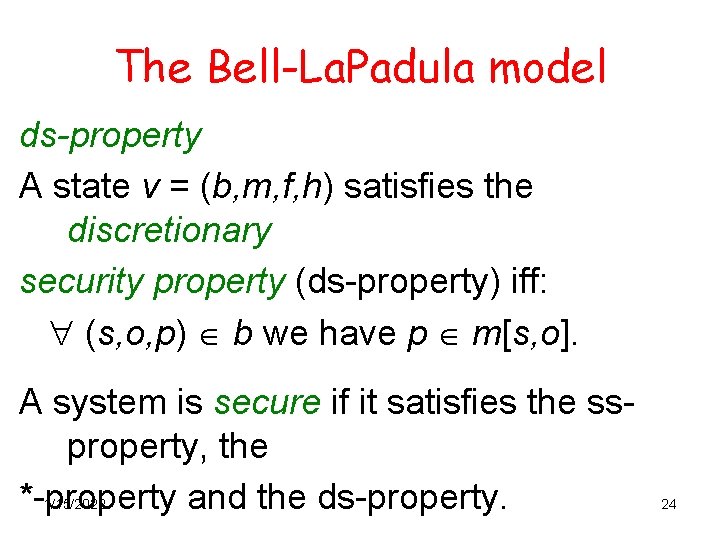
The Bell-La. Padula model ds-property A state v = (b, m, f, h) satisfies the discretionary security property (ds-property) iff: (s, o, p) b we have p m[s, o]. A system is secure if it satisfies the ssproperty, the *-property and the ds-property. 1/15/2022 24

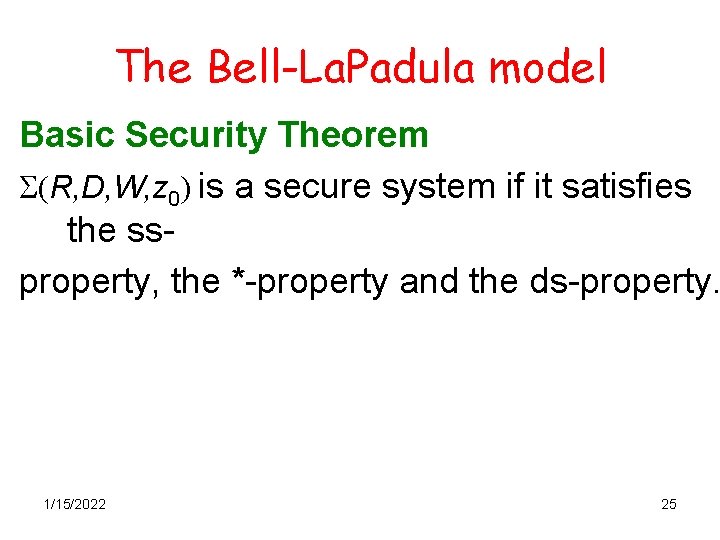
The Bell-La. Padula model Basic Security Theorem S(R, D, W, z 0) is a secure system if it satisfies the ssproperty, the *-property and the ds-property. 1/15/2022 25

Example model instantiation Multics The Multics system There are five groups of rules 1. A set of requests: to request & release access 2. A set of requests: to give access & remove access from a different subject 3. A set of requests: to create and reclassify objects 4. 1/15/2022 A set of requests: to remove objects 26

Tranquility Principle of tranquility Subjects and objects may not change their security levels once they have been instantiated. Principle of strong tranquility No change during the lifetime of the system. Principle of weak tranquility Security levels do not change in a way that 1/15/2022 violates the 27

Mc. Lean’s system Z Mc Lean reformulated the notion of a secure action and defined an alternative version of ss, * and ds Roughly: a system S satisfies these properties if given a state of S that satisfies them, the action transforms the state into a possibly new state that also satisfies them and 1/15/2022 28 eliminates any accesses present in the

Mc. Lean’s system Z Theorem S is secure if its initial state is secure and if each action satisfies the alternative versions of ss, * and ds. 1/15/2022 29
 Private securit
Private securit Security program and policies principles and practices
Security program and policies principles and practices Database security policies
Database security policies Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Types of security policies
Types of security policies Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Why is confidentiality important
Why is confidentiality important Bcc trolling email
Bcc trolling email Confidentiality using conventional encryption
Confidentiality using conventional encryption Address confidentiality program texas
Address confidentiality program texas Matthew seavey
Matthew seavey Dr rubina yasmin
Dr rubina yasmin Conventional encryption and message confidentiality
Conventional encryption and message confidentiality Potential tension between maintaining confidentiality
Potential tension between maintaining confidentiality Uams gus login
Uams gus login Ferpa confidentiality of records quiz answers
Ferpa confidentiality of records quiz answers Fidelity ethical principle
Fidelity ethical principle Confidentiality and privacy controls
Confidentiality and privacy controls Confidentiality
Confidentiality Motion to determine confidentiality of court records
Motion to determine confidentiality of court records Confidentiality
Confidentiality Confidentiality chapter 5
Confidentiality chapter 5 Medical ethics definition
Medical ethics definition Texas confidentiality laws for minors
Texas confidentiality laws for minors Confidentiality
Confidentiality Concepts of medical ethics
Concepts of medical ethics Confidentiality integrity availability
Confidentiality integrity availability Dr smith
Dr smith