Learn how Fast Track can help securely deploy






- Slides: 35


Learn how Fast. Track can help securely deploy Microsoft 365

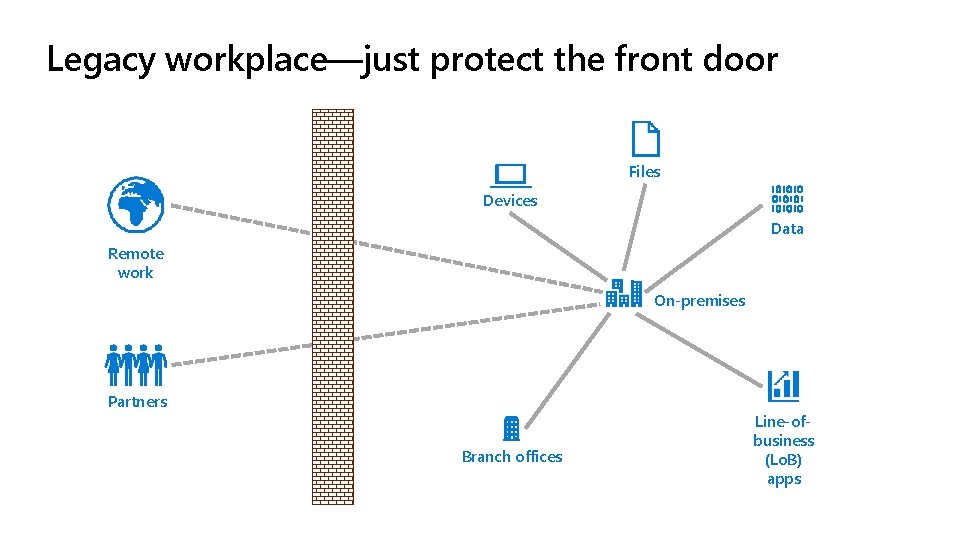
Legacy workplace—just protect the front door Files Devices Data Remote work On-premises Partners Branch offices Line-ofbusiness (Lo. B) apps

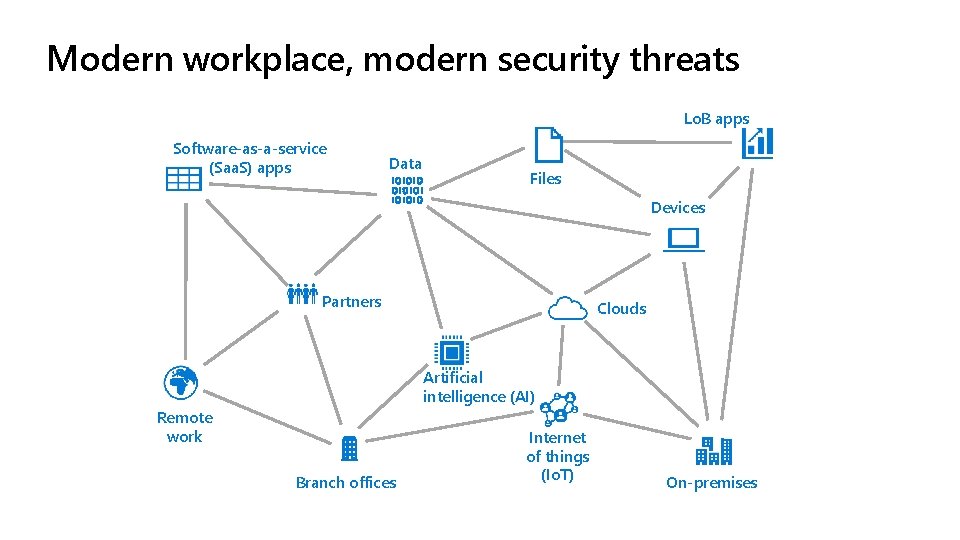
Modern workplace, modern security threats Lo. B apps Software-as-a-service (Saa. S) apps Data Files Devices Partners Clouds Artificial intelligence (AI) Remote work Branch offices Internet of things (Io. T) On-premises

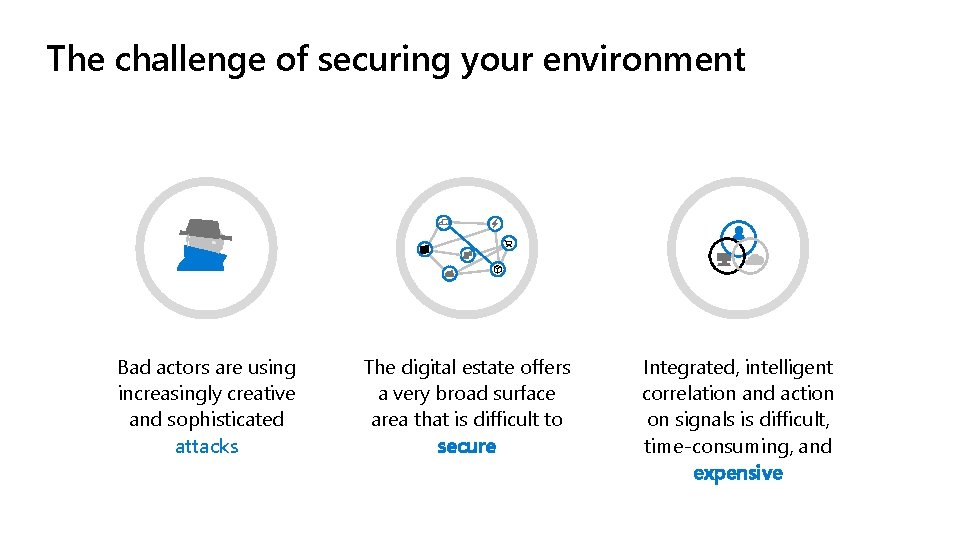
The challenge of securing your environment Bad actors are using increasingly creative and sophisticated attacks The digital estate offers a very broad surface area that is difficult to secure Integrated, intelligent correlation and action on signals is difficult, time-consuming, and expensive

The security challenges you face have never been greater

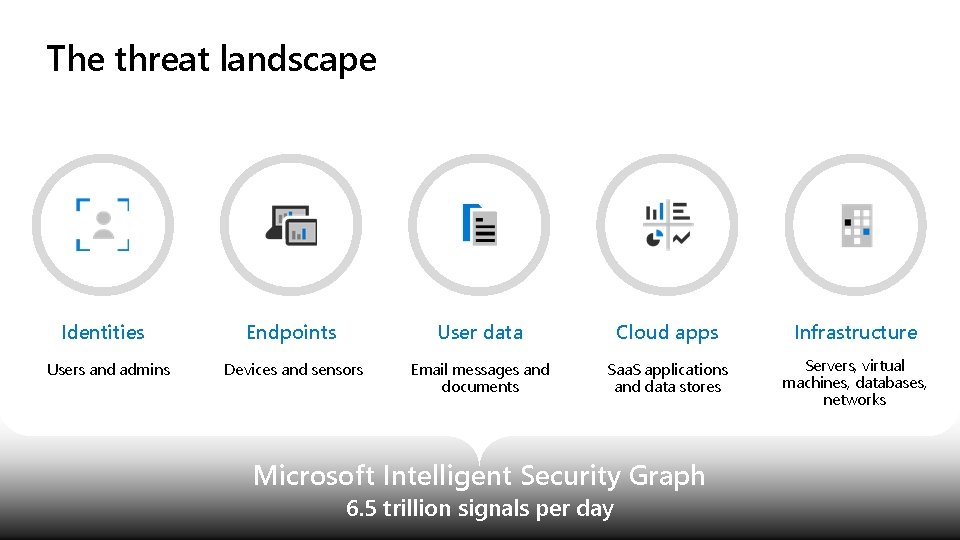
The threat landscape Identities Users and admins Endpoints User data Cloud apps Infrastructure Devices and sensors Email messages and documents Saa. S applications and data stores Servers, virtual machines, databases, networks Microsoft Intelligent Security Graph 6. 5 trillion signals per day

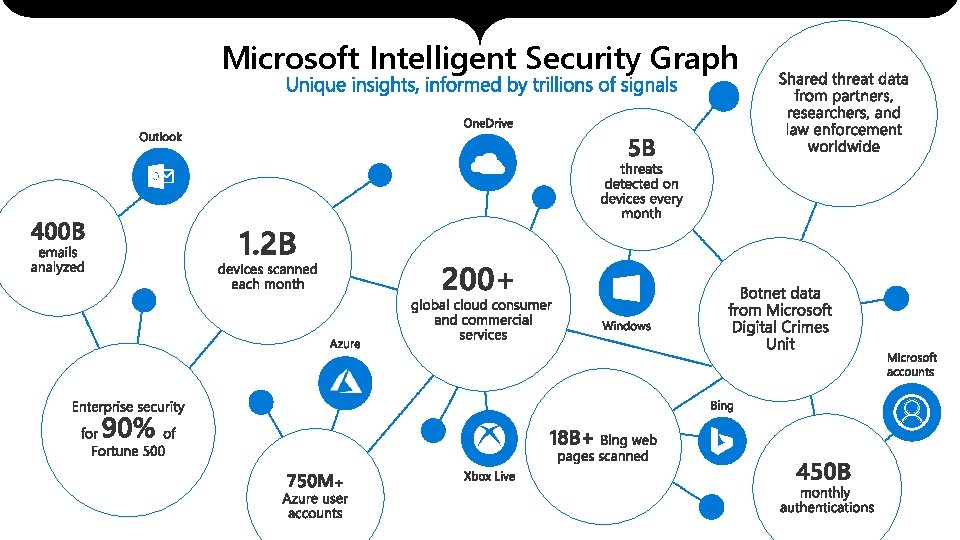
Microsoft Intelligent Security Graph

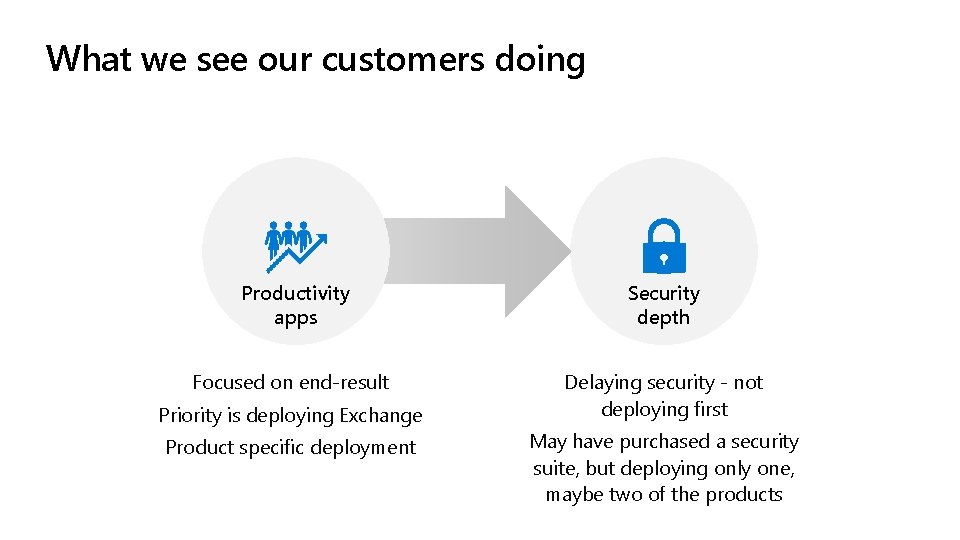
What we see our customers doing Productivity apps Security depth Focused on end-result Delaying security - not deploying first Priority is deploying Exchange Product specific deployment May have purchased a security suite, but deploying only one, maybe two of the products

must-do Security depth Deploy security first up front ü Identity and access management ü Devices ü Email and information Productivity apps ü Solutions ü Apps

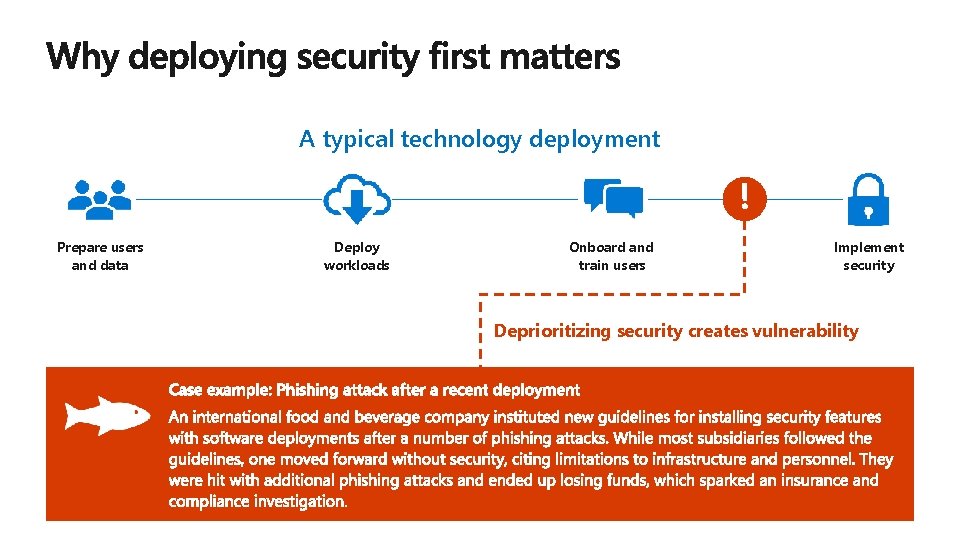
A typical technology deployment Prepare users and data Deploy workloads Onboard and train users Implement security Deprioritizing security creates vulnerability

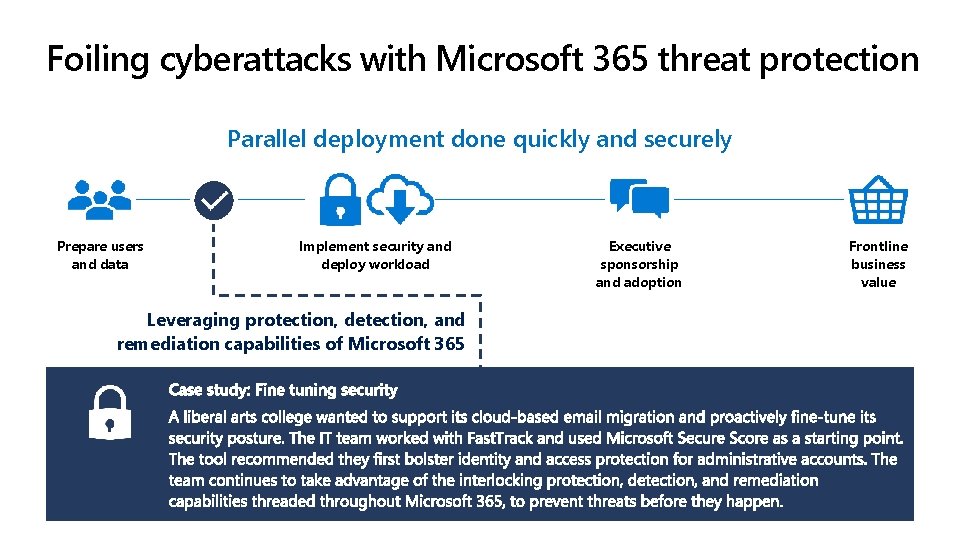
Foiling cyberattacks with Microsoft 365 threat protection Parallel deployment done quickly and securely Prepare users and data Implement security and deploy workload Leveraging protection, detection, and remediation capabilities of Microsoft 365 Executive sponsorship and adoption Frontline business value

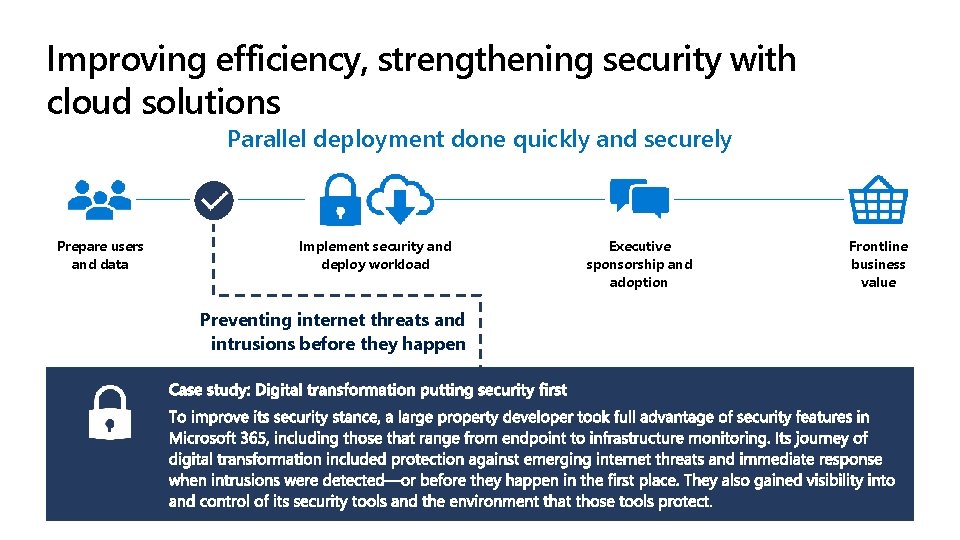
Improving efficiency, strengthening security with cloud solutions Parallel deployment done quickly and securely Prepare users and data Implement security and deploy workload Preventing internet threats and intrusions before they happen Executive sponsorship and adoption Frontline business value

Let Fast. Track for Microsoft 365 help you And yes…it is included with your eligible subscription at no additional cost

Fast. Track Your advisor to help deploy Microsoft 365 Onboard to Microsoft 365 services and migrate your data Configure identity and security capabilities Guide Windows 10 deployment Deliver app combat services Deploy chat-based collaboration and productivity apps Gain customer user adoption and realize business value Delivered by Microsoft or approved partners Included in your eligible subscription at no additional cost www. microsoft. com/Fast. Track

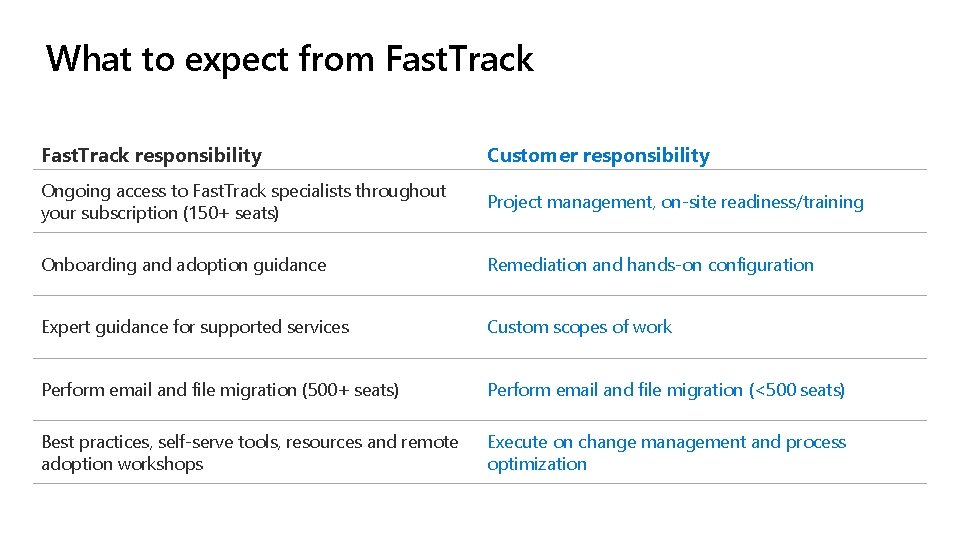
What to expect from Fast. Track responsibility Customer responsibility Ongoing access to Fast. Track specialists throughout your subscription (150+ seats) Project management, on-site readiness/training Onboarding and adoption guidance Remediation and hands-on configuration Expert guidance for supported services Custom scopes of work Perform email and file migration (500+ seats) Perform email and file migration (<500 seats) Best practices, self-serve tools, resources and remote adoption workshops Execute on change management and process optimization

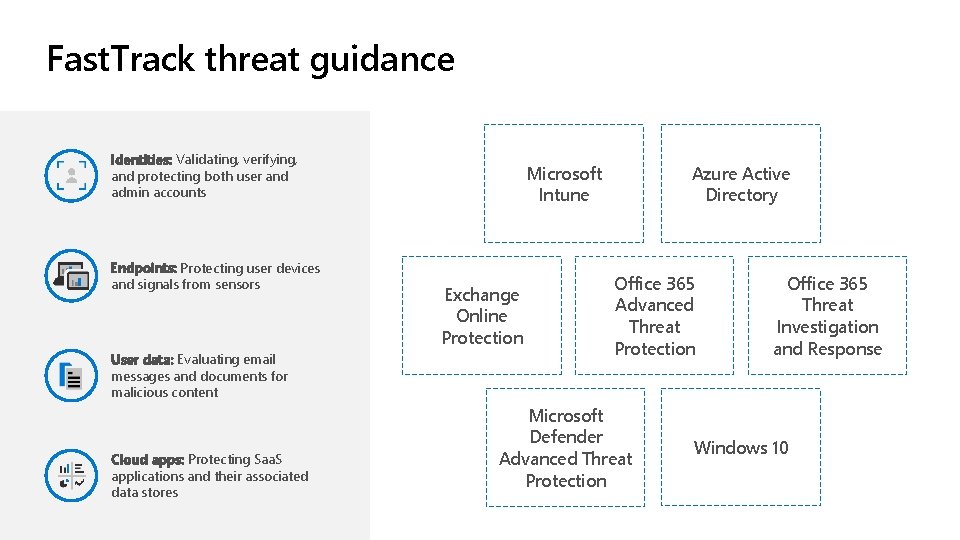
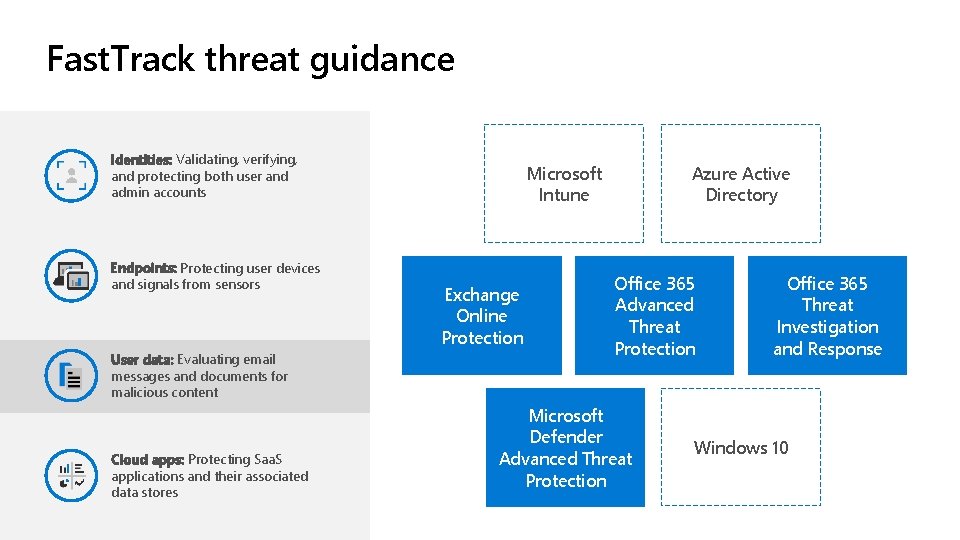
Fast. Track threat guidance Identities: Validating, verifying, and protecting both user and admin accounts Endpoints: Protecting user devices and signals from sensors User data: Evaluating email messages and documents for malicious content Cloud apps: Protecting Saa. S applications and their associated data stores Microsoft Intune Exchange Online Protection Azure Active Directory Office 365 Advanced Threat Protection Microsoft Defender Advanced Threat Protection Office 365 Threat Investigation and Response Windows 10

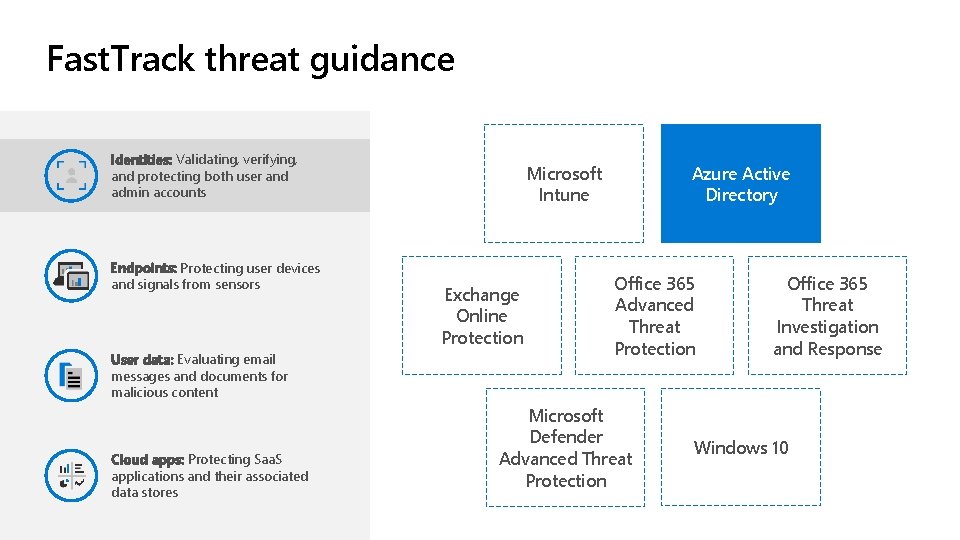
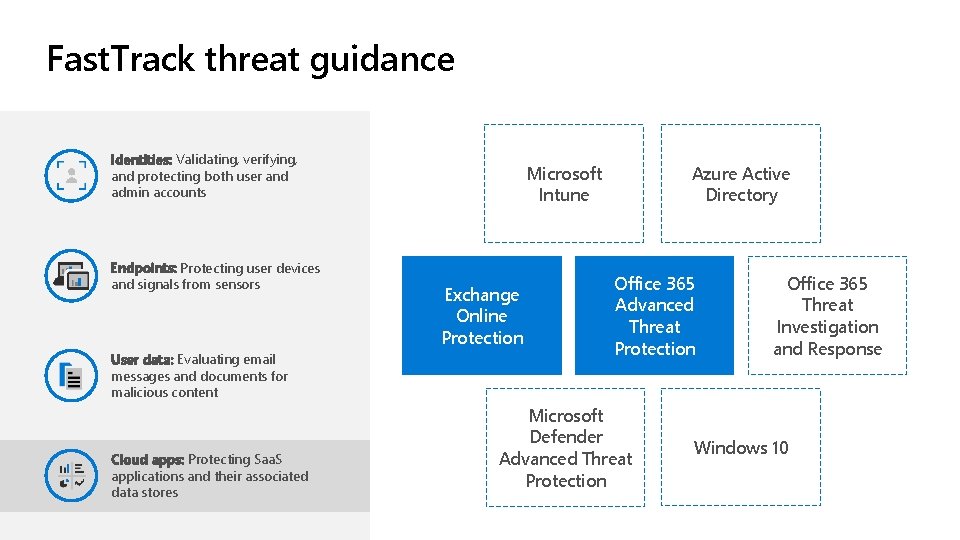
Fast. Track threat guidance Identities: Validating, verifying, and protecting both user and admin accounts Endpoints: Protecting user devices and signals from sensors User data: Evaluating email messages and documents for malicious content Cloud apps: Protecting Saa. S applications and their associated data stores Microsoft Intune Exchange Online Protection Azure Active Directory Office 365 Advanced Threat Protection Microsoft Defender Advanced Threat Protection Office 365 Threat Investigation and Response Windows 10

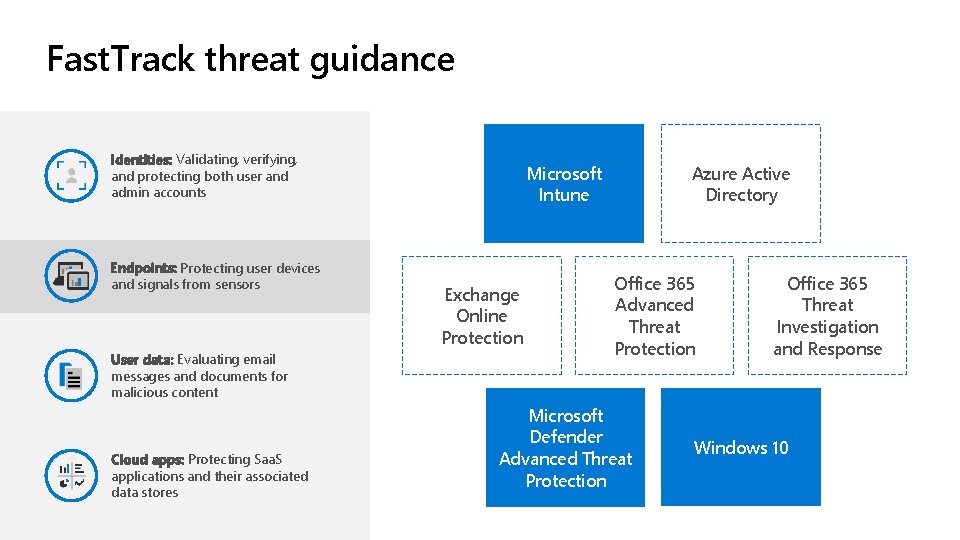
Fast. Track threat guidance Identities: Validating, verifying, and protecting both user and admin accounts Endpoints: Protecting user devices and signals from sensors User data: Evaluating email messages and documents for malicious content Cloud apps: Protecting Saa. S applications and their associated data stores Microsoft Intune Exchange Online Protection Azure Active Directory Office 365 Advanced Threat Protection Microsoft Defender Advanced Threat Protection Office 365 Threat Investigation and Response Windows 10

Fast. Track threat guidance Identities: Validating, verifying, and protecting both user and admin accounts Endpoints: Protecting user devices and signals from sensors User data: Evaluating email messages and documents for malicious content Cloud apps: Protecting Saa. S applications and their associated data stores Microsoft Intune Exchange Online Protection Azure Active Directory Office 365 Advanced Threat Protection Microsoft Defender Advanced Threat Protection Office 365 Threat Investigation and Response Windows 10

Fast. Track threat guidance Identities: Validating, verifying, and protecting both user and admin accounts Endpoints: Protecting user devices and signals from sensors User data: Evaluating email messages and documents for malicious content Cloud apps: Protecting Saa. S applications and their associated data stores Microsoft Intune Exchange Online Protection Azure Active Directory Office 365 Advanced Threat Protection Microsoft Defender Advanced Threat Protection Office 365 Threat Investigation and Response Windows 10

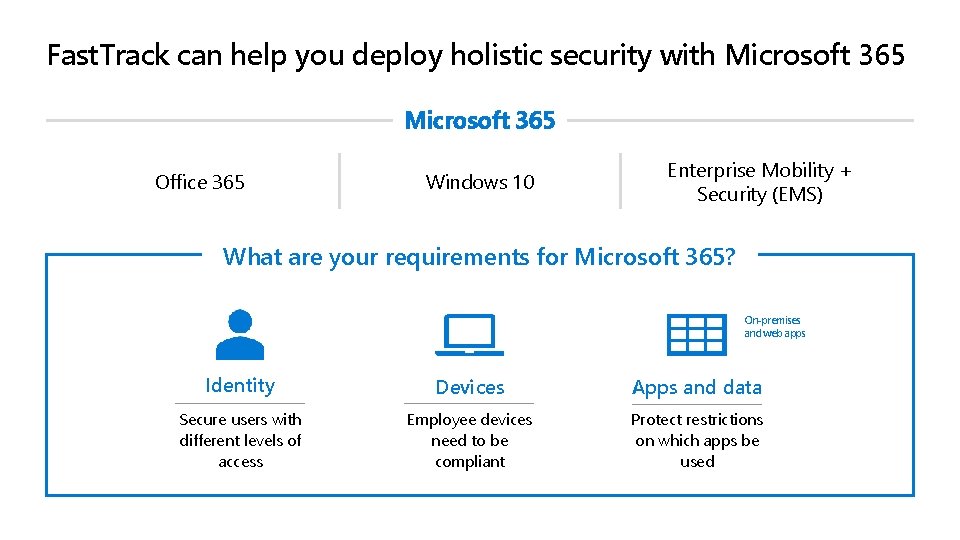
Fast. Track can help you deploy holistic security with Microsoft 365 Office 365 Windows 10 Enterprise Mobility + Security (EMS) What are your requirements for Microsoft 365? On-premises and web apps Identity Devices Apps and data Secure users with different levels of access Employee devices need to be compliant Protect restrictions on which apps be used

Microsoft security focuses on four key areas Users Devices Data Apps

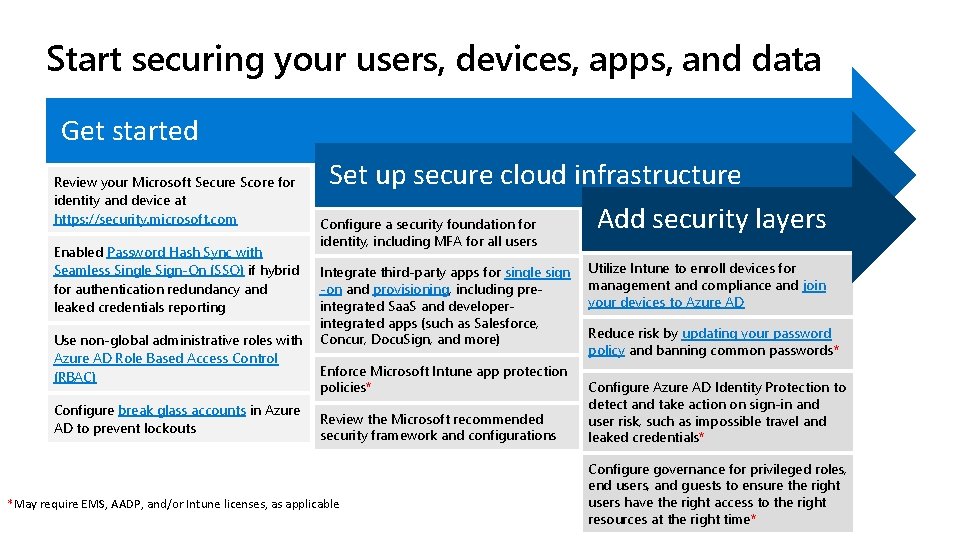
Start securing your users, devices, apps, and data Get started Review your Microsoft Secure Score for identity and device at https: //security. microsoft. com Enabled Password Hash Sync with Seamless Single Sign-On (SSO) if hybrid for authentication redundancy and leaked credentials reporting Use non-global administrative roles with Azure AD Role Based Access Control (RBAC) Configure break glass accounts in Azure AD to prevent lockouts Set up secure cloud infrastructure Add security layers Configure a security foundation for identity, including MFA for all users Integrate third-party apps for single sign -on and provisioning, including preintegrated Saa. S and developerintegrated apps (such as Salesforce, Concur, Docu. Sign, and more) Enforce Microsoft Intune app protection policies* Review the Microsoft recommended security framework and configurations *May require EMS, AADP, and/or Intune licenses, as applicable Utilize Intune to enroll devices for management and compliance and join your devices to Azure AD Reduce risk by updating your password policy and banning common passwords* Configure Azure AD Identity Protection to detect and take action on sign-in and user risk, such as impossible travel and leaked credentials* Configure governance for privileged roles, end users, and guests to ensure the right users have the right access to the right resources at the right time*

Information protection Protect assets Connect the dots Empower defenders

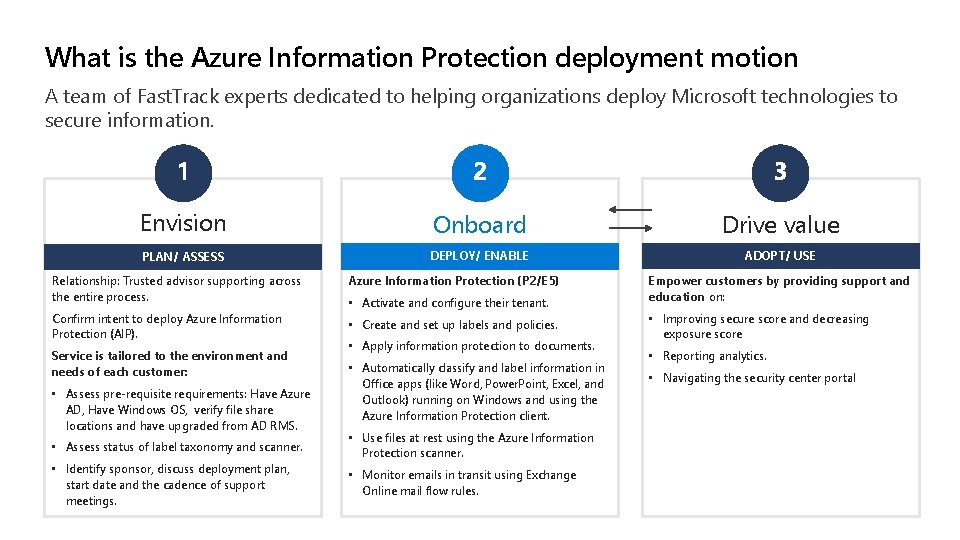
What is the Azure Information Protection deployment motion A team of Fast. Track experts dedicated to helping organizations deploy Microsoft technologies to secure information. Envision Onboard Drive value PLAN/ ASSESS DEPLOY/ ENABLE ADOPT/ USE Relationship: Trusted advisor supporting across the entire process. Azure Information Protection (P 2/E 5) Confirm intent to deploy Azure Information Protection (AIP). • Create and set up labels and policies. Service is tailored to the environment and needs of each customer: • Assess pre-requisite requirements: Have Azure AD, Have Windows OS, verify file share locations and have upgraded from AD RMS. • Assess status of label taxonomy and scanner. • Identify sponsor, discuss deployment plan, start date and the cadence of support meetings. • Activate and configure their tenant. • Apply information protection to documents. • Automatically classify and label information in Office apps (like Word, Power. Point, Excel, and Outlook) running on Windows and using the Azure Information Protection client. • Use files at rest using the Azure Information Protection scanner. • Monitor emails in transit using Exchange Online mail flow rules. Empower customers by providing support and education on: • Improving secure score and decreasing exposure score • Reporting analytics. • Navigating the security center portal

The Microsoft Defender ATP and Office 365 ATP deployment motion A team of Fast. Track experts dedicated to helping organizations deploy Microsoft technologies to secure email and endpoints Envision Onboard Drive value PLAN/ASSESS DEPLOY/ENABLE ADOPT/USE A trusted advisor supports the entire process. Office 365 ATP Confirm intent to deploy Microsoft Defender ATP and/or Office 365 ATP. Enable safe links, safe attachments, and antiphishing. Service is tailored to the environment and needs of each customer: Configure automation, investigation and response. • Assess OS version and device management (Intune, SCCM, GPO, third-party). Microsoft Defender ATP • Assess status of Windows AV services or other endpoint security software. Assess proxies and firewalls restricting network traffic. • Identify sponsor, discuss deployment plan, start date, and the cadence of support meetings. Empower customers by providing support and education on: • Improving secure score and decreasing exposure score. • Simulations and tutorials (practice scenarios, fake malware, automated investigations). • Onboard endpoint: Enable Microsoft Defender ATP service by deploying advanced threat protection agent profile. • Reporting and threat analytics. • Set Microsoft Defender ATP configuration profiles (endpoint protection, device restriction). • Navigating the security center portal. • Set Security Center settings to personalize how Microsoft Defender ATP addresses customer needs. • Threat and vulnerability management. • Advanced threat hunting.

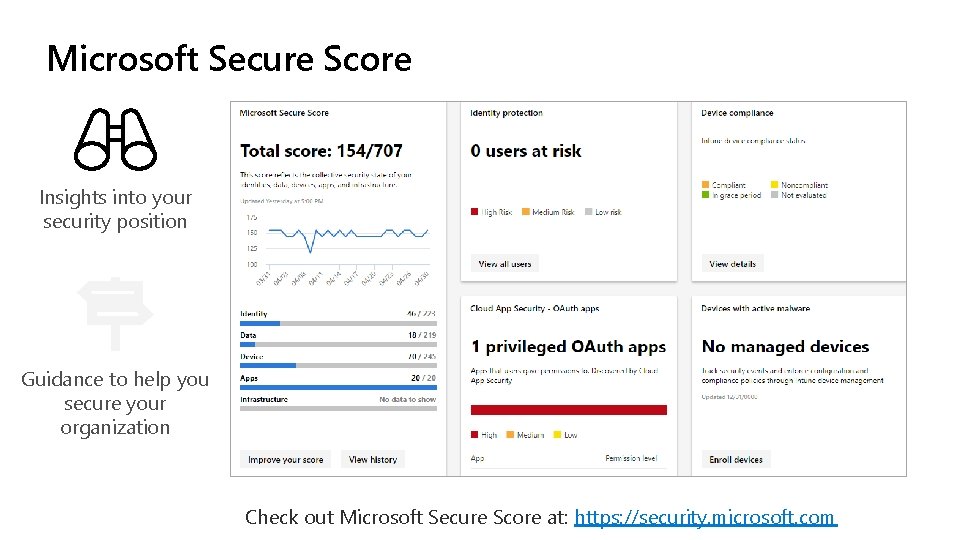
Microsoft Secure Score Insights into your security position Guidance to help you secure your organization Check out Microsoft Secure Score at: https: //security. microsoft. com

Your next steps 1 Security first—identity, devices, information 2 Visit www. microsoft. com/Fast. Track Visit the Fast. Track Booth and talk with Fast. Track security experts Sign in for additional guidance and resources Create a Success Plan to help establish implementation and user adoption goals and tactics Ask for help by submitting a Request for Assistance 3 Visit Secure Score—www. security. microsoft. com View your current security posture

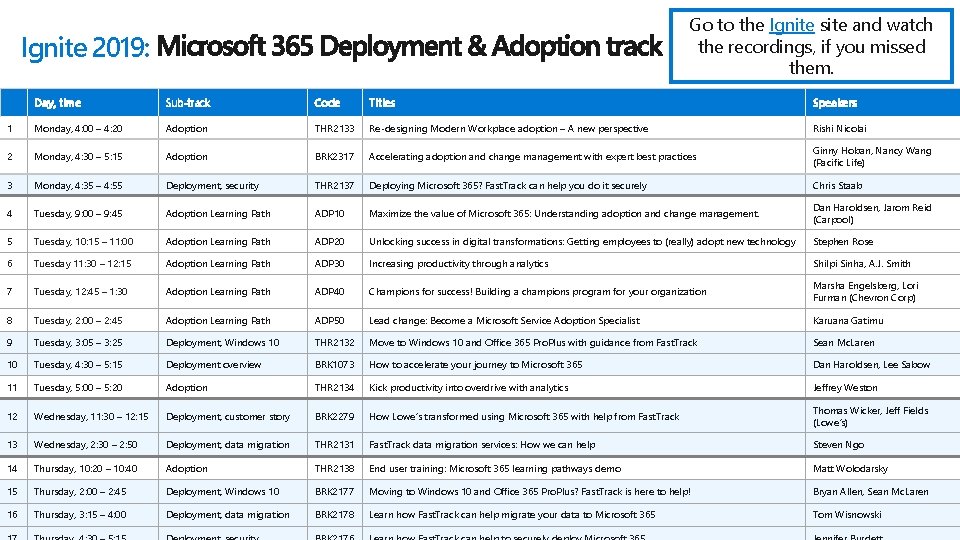
Go to the Ignite site and watch the recordings, if you missed them. Ignite 2019: Day, time Sub-track Code Titles Speakers 1 Monday, 4: 00 – 4: 20 Adoption THR 2133 Re-designing Modern Workplace adoption – A new perspective Rishi Nicolai 2 Monday, 4: 30 – 5: 15 Adoption BRK 2317 Accelerating adoption and change management with expert best practices Ginny Hoban, Nancy Wang (Pacific Life) 3 Monday, 4: 35 – 4: 55 Deployment, security THR 2137 Deploying Microsoft 365? Fast. Track can help you do it securely Chris Staab 4 Tuesday, 9: 00 – 9: 45 Adoption Learning Path ADP 10 Maximize the value of Microsoft 365: Understanding adoption and change management. Dan Haroldsen, Jarom Reid (Carpool) 5 Tuesday, 10: 15 – 11: 00 Adoption Learning Path ADP 20 Unlocking success in digital transformations: Getting employees to (really) adopt new technology Stephen Rose 6 Tuesday 11: 30 – 12: 15 Adoption Learning Path ADP 30 Increasing productivity through analytics Shilpi Sinha, A. J. Smith 7 Tuesday, 12: 45 – 1: 30 Adoption Learning Path ADP 40 Champions for success! Building a champions program for your organization Marsha Engelsberg, Lori Furman (Chevron Corp) 8 Tuesday, 2: 00 – 2: 45 Adoption Learning Path ADP 50 Lead change: Become a Microsoft Service Adoption Specialist Karuana Gatimu 9 Tuesday, 3: 05 – 3: 25 Deployment, Windows 10 THR 2132 Move to Windows 10 and Office 365 Pro. Plus with guidance from Fast. Track Sean Mc. Laren 10 Tuesday, 4: 30 – 5: 15 Deployment overview BRK 1073 How to accelerate your journey to Microsoft 365 Dan Haroldsen, Lee Sabow 11 Tuesday, 5: 00 – 5: 20 Adoption THR 2134 Kick productivity into overdrive with analytics Jeffrey Weston 12 Wednesday, 11: 30 – 12: 15 Deployment, customer story BRK 2279 How Lowe’s transformed using Microsoft 365 with help from Fast. Track Thomas Wicker, Jeff Fields (Lowe’s) 13 Wednesday, 2: 30 – 2: 50 Deployment, data migration THR 2131 Fast. Track data migration services: How we can help Steven Ngo 14 Thursday, 10: 20 – 10: 40 Adoption THR 2138 End user training: Microsoft 365 learning pathways demo Matt Wolodarsky 15 Thursday, 2: 00 – 2: 45 Deployment, Windows 10 BRK 2177 Moving to Windows 10 and Office 365 Pro. Plus? Fast. Track is here to help! Bryan Allen, Sean Mc. Laren 16 Thursday, 3: 15 – 4: 00 Deployment, data migration BRK 2178 Learn how Fast. Track can help migrate your data to Microsoft 365 Tom Wisnowski

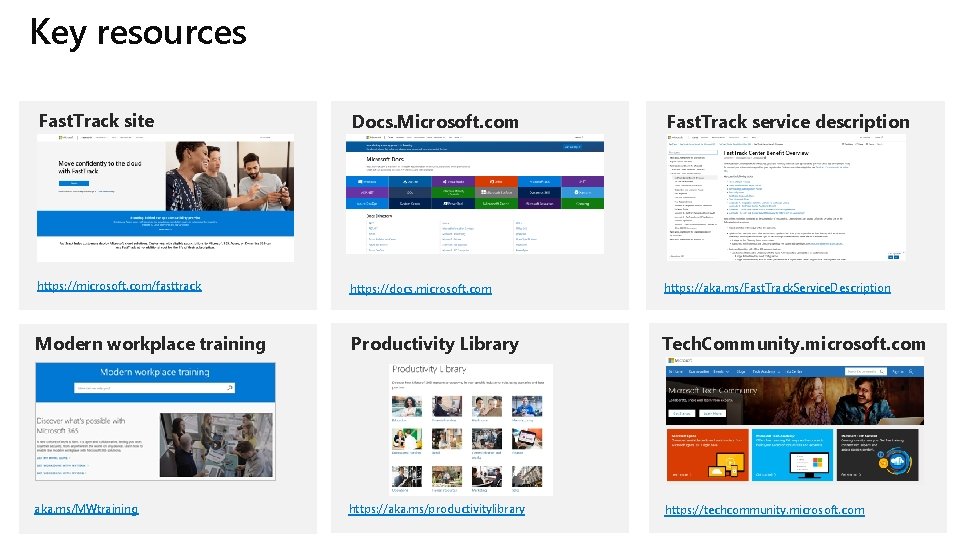
Key resources Fast. Track site Docs. Microsoft. com Fast. Track service description https: //microsoft. com/fasttrack https: //docs. microsoft. com https: //aka. ms/Fast. Track. Service. Description Modern workplace training Productivity Library Tech. Community. microsoft. com aka. ms/MWtraining https: //aka. ms/productivitylibrary https: //techcommunity. microsoft. com

Q&A

Please evaluate this session Your feedback is important to us! https: //aka. ms/ignite. mobileapp https: //myignite. techcommunity. microsoft. com/evaluations

Find this session in Microsoft Tech Community