LeakageResilient Cryptography New Developments and Challenges Vinod Vaikuntanathan



![Interpreting the Commandments (or, Two Leakage Models) A Simple Interpretation: Bounded Leakage [AGV 09] Interpreting the Commandments (or, Two Leakage Models) A Simple Interpretation: Bounded Leakage [AGV 09]](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-6.jpg)
![Interpreting the Commandments (or, Two Leakage Models) A Simple Interpretation: Bounded Leakage [AGV 09] Interpreting the Commandments (or, Two Leakage Models) A Simple Interpretation: Bounded Leakage [AGV 09]](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-7.jpg)



![[Ishai-Sahai-Wagner 2003] [Micali-Reyzin 2004] [Dodis-Ong-Prabhakaran-Sahai 2004] [Ishai-Prabhakaran-Sahai-Wagner 2006] [Dziembowski-Pietrzak 2008] [Akavia-Goldwasser-V. 2009] [Pietrzak 2009] [Ishai-Sahai-Wagner 2003] [Micali-Reyzin 2004] [Dodis-Ong-Prabhakaran-Sahai 2004] [Ishai-Prabhakaran-Sahai-Wagner 2006] [Dziembowski-Pietrzak 2008] [Akavia-Goldwasser-V. 2009] [Pietrzak 2009]](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-14.jpg)

![Leakage-Resilient One-way Functions Theorem [KV 09, ADW 09]: If there are Universal One-way Hash Leakage-Resilient One-way Functions Theorem [KV 09, ADW 09]: If there are Universal One-way Hash](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-17.jpg)
![Leakage-Resilient Signatures Theorem [KV 09]: λ-leakage-resilient OWF (+simulationextractable NIZK [S 99, DDOPS 01]) → Leakage-Resilient Signatures Theorem [KV 09]: λ-leakage-resilient OWF (+simulationextractable NIZK [S 99, DDOPS 01]) →](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-23.jpg)
![LR Signatures: Subsequent Results q [ADW 09]: Fiat-Shamir transform + LR OWFs → LRSigs LR Signatures: Subsequent Results q [ADW 09]: Fiat-Shamir transform + LR OWFs → LRSigs](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-24.jpg)

![LR Public-key Encryption: Subsequent Results q [NS 09]: CPA-secure → CCA-secure with the same LR Public-key Encryption: Subsequent Results q [NS 09]: CPA-secure → CCA-secure with the same](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-31.jpg)

![Continual LR Public-key Encryption Theorem: [BKKV 10] CLR-secure public-key encryption schemes that tolerate (in Continual LR Public-key Encryption Theorem: [BKKV 10] CLR-secure public-key encryption schemes that tolerate (in](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-34.jpg)
![Continual LR Public-key Encryption Other Results: q [BKKV 10]: CLR-secure signatures and IBE (with Continual LR Public-key Encryption Other Results: q [BKKV 10]: CLR-secure signatures and IBE (with](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-35.jpg)


![Foundational Questions Many Partial Results q [Ishai-Sahai-Wagner’ 03] : Any circuit → “Probing-resilient” circuit Foundational Questions Many Partial Results q [Ishai-Sahai-Wagner’ 03] : Any circuit → “Probing-resilient” circuit](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-40.jpg)

- Slides: 43

Leakage-Resilient Cryptography New Developments and Challenges Vinod Vaikuntanathan Microsoft Research & U. Toronto

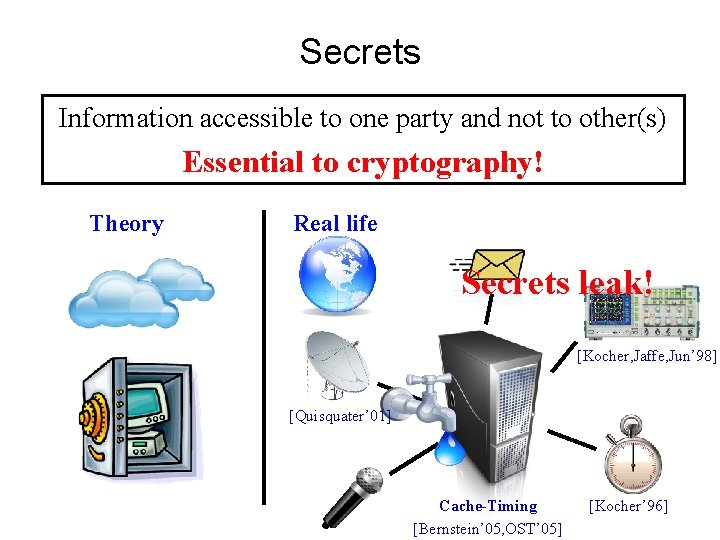
Secrets Information accessible to one party and not to other(s) Essential to cryptography! Theory Real life Secrets leak! [Kocher, Jaffe, Jun’ 98] [Quisquater’ 01] Cache-Timing [Bernstein’ 05, OST’ 05] [Kocher’ 96]

Secrets Leak So, what can we do about it?

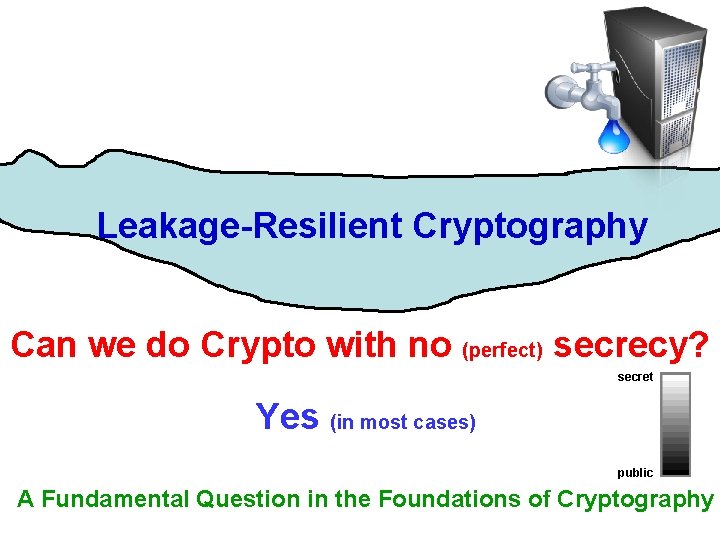
Leakage-Resilient Cryptography Can we do Crypto with no (perfect) secrecy? secret Yes (in most cases) public A Fundamental Question in the Foundations of Cryptography

Three Commandments (Axioms of Leakage) I. Secrets leak in arbitrary ways. (except: leakage is polynomial time computable, and does not betray the entire secret key) [Micali-Reyzin’ 04] II. Secrets leak from everywhere. (hard-disk, RAM, cache, registers, randomness sources, …) III. Secrets leak all the time. (No protected time periods)
![Interpreting the Commandments or Two Leakage Models A Simple Interpretation Bounded Leakage AGV 09 Interpreting the Commandments (or, Two Leakage Models) A Simple Interpretation: Bounded Leakage [AGV 09]](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-6.jpg)
Interpreting the Commandments (or, Two Leakage Models) A Simple Interpretation: Bounded Leakage [AGV 09] — — Adversary can learn any efficiently computable function L: {0, 1}* → {0, 1} λ of the secret key(*). Total leakage λ < |SK| [AGV 09, NS 09, KV 09, ADW 09, ADN+10, …] sk L(sk) 101 (*) Ideally, leakage from the entire secret state.
![Interpreting the Commandments or Two Leakage Models A Simple Interpretation Bounded Leakage AGV 09 Interpreting the Commandments (or, Two Leakage Models) A Simple Interpretation: Bounded Leakage [AGV 09]](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-7.jpg)
Interpreting the Commandments (or, Two Leakage Models) A Simple Interpretation: Bounded Leakage [AGV 09] — Adversary can learn any efficiently computable function L: {0, 1}* → {0, 1} λ of the secret key. — Total leakage λ < |SK| [AGV 09, NS 09, KV 09, ADW 09, ADN+10, …] Variations: λ q Noisy Model [NS’ 09]: H∞(SK | L(SK)) > |SK|- q Auxiliary Input Model [DKL’ 09, DGKPV’ 10]: L is an uninvertible function of SK

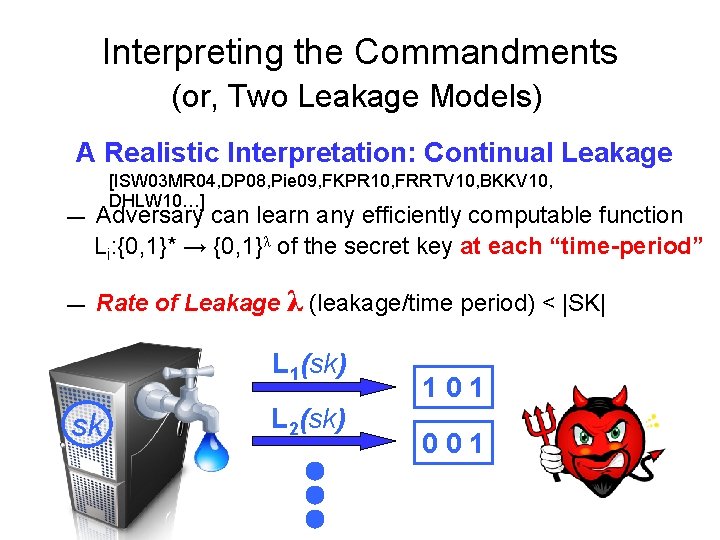
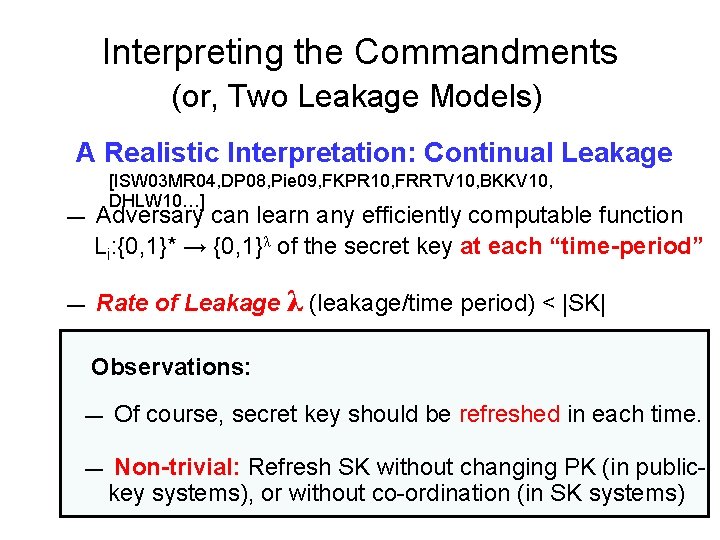
Interpreting the Commandments (or, Two Leakage Models) A Realistic Interpretation: Continual Leakage — — [ISW 03 MR 04, DP 08, Pie 09, FKPR 10, FRRTV 10, BKKV 10, DHLW 10…] Adversary can learn any efficiently computable function Li: {0, 1}* → {0, 1}λ of the secret key at each “time-period” Rate of Leakage λ (leakage/time period) < |SK| L 1(sk) sk L 2(sk) 101 001

Interpreting the Commandments (or, Two Leakage Models) A Realistic Interpretation: Continual Leakage — — [ISW 03 MR 04, DP 08, Pie 09, FKPR 10, FRRTV 10, BKKV 10, DHLW 10…] Adversary can learn any efficiently computable function Li: {0, 1}* → {0, 1}λ of the secret key at each “time-period” Rate of Leakage λ (leakage/time period) < |SK| Observations: — Of course, secret key should be refreshed in each time. — Non-trivial: Refresh SK without changing PK (in publickey systems), or without co-ordination (in SK systems)

Talk Plan PART 1: Bounded Leakage Model – One-way Functions – Digital Signatures – Public-key Encryption PART 2: Continual Leakage Model PART 3: Some Research Directions – Leakage-resilient Compilers, Tamper Resistance, …

A Brief History of Leakage in Crypto “We stand on the shoulders of giants…”

A Brief History of Leakage in Crypto q Privacy Amplification [von Neumann’ 46, …, Bennett-Brassard-Robert’ 8 — “Distill an perfectly random shared key from an imperfect one” l Bounded Storage/Retrieval Models [Maurer’ 92, …, Di Crescenzo-Lipton-Walfish’ 06, Dziembowski’ 06] Exposure-Resilient Cryptography [Rivest’ 97, Boyko’ 98, CDHKS’ 00, ISW’ 03, IPSW’ 06] — More generally, MPC, threshold crypto etc. — Leakage = a subset of bits of SK — We want to tolerate arbitrary (PPT) leakage functions (axiom 1)

A Brief History of Leakage in Crypto q Privacy Amplification [von Neumann’ 46, …, Bennett-Brassard-Robert’ 8 — “Distill an perfectly random shared key from an imperfect one” l Bounded Storage/Retrieval Models [Maurer’ 92, …, Di Crescenzo-Lipton-Walfish’ 06, Dziembowski’ 06] Exposure-Resilient Cryptography [Rivest’ 97, Boyko’ 98, CDHKS’ 00, ISW’ 03, IPSW’ 06] v Proactive Cryptography [HJKY’ 95, HJJKY’ 97, R’ 98] — “How to cope with perpetual leakage” (a continual leakage model)
![IshaiSahaiWagner 2003 MicaliReyzin 2004 DodisOngPrabhakaranSahai 2004 IshaiPrabhakaranSahaiWagner 2006 DziembowskiPietrzak 2008 AkaviaGoldwasserV 2009 Pietrzak 2009 [Ishai-Sahai-Wagner 2003] [Micali-Reyzin 2004] [Dodis-Ong-Prabhakaran-Sahai 2004] [Ishai-Prabhakaran-Sahai-Wagner 2006] [Dziembowski-Pietrzak 2008] [Akavia-Goldwasser-V. 2009] [Pietrzak 2009]](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-14.jpg)
[Ishai-Sahai-Wagner 2003] [Micali-Reyzin 2004] [Dodis-Ong-Prabhakaran-Sahai 2004] [Ishai-Prabhakaran-Sahai-Wagner 2006] [Dziembowski-Pietrzak 2008] [Akavia-Goldwasser-V. 2009] [Pietrzak 2009] [Dodis-Kalai-Lovett 2009] [Naor-Segev 2009] [Dodis-Goldwasser-Kalai-Peikert-V. 2009] [Katz-V. 2009] [Faust-Kiltz-Pietrzak-Rothblum 2009] [Alwen-Dodis-Wichs 2009] [Goldwasser-Kalai-Peikert-V. 2010] [Alwen-Dodis-Naor-Segev-Walfish-Wichs 2009] [Juma-Vahlis. 2010] [Faust-Rabin-Reyzin-Tromer-V. 2010] [Brakerski-Kalai-Katz-V. 2010] [Goldwasser-Rothblum. 2010] [Dodis-Haralambiev-Lopez-alt-Wichs. 2010] [Lewko-Waters. 2010] [Chow-Dodis-Rouselakis-Waters. 2010] [Boyle-Wichs-Segev. 2011] [Kiltz-Pietrzak. 2011]

Bounded Leakage

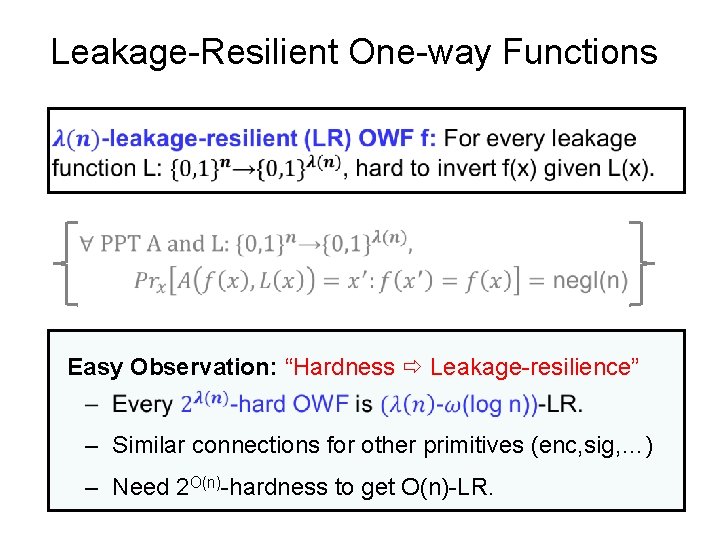
Leakage-Resilient One-way Functions Easy Observation: “Hardness Leakage-resilience” – Similar connections for other primitives (enc, sig, …) – Need 2 O(n)-hardness to get O(n)-LR.
![LeakageResilient Oneway Functions Theorem KV 09 ADW 09 If there are Universal Oneway Hash Leakage-Resilient One-way Functions Theorem [KV 09, ADW 09]: If there are Universal One-way Hash](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-17.jpg)
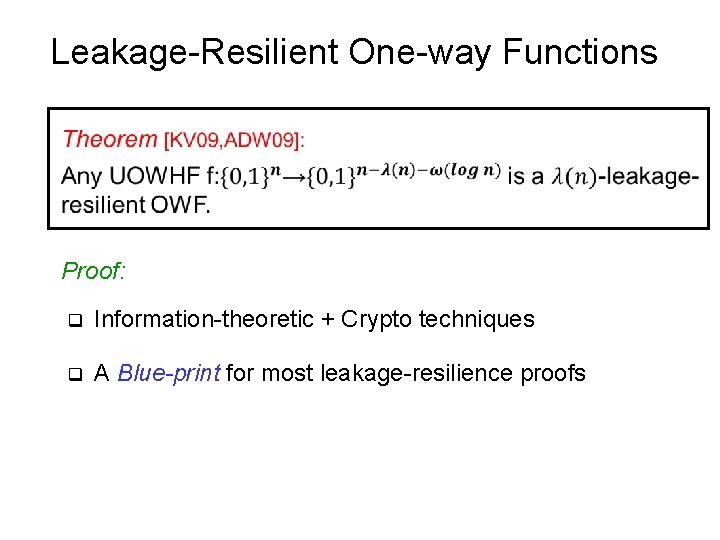
Leakage-Resilient One-way Functions Theorem [KV 09, ADW 09]: If there are Universal One-way Hash Functions, then there are LR one-way functions. – Corollary [NY 89, Rom 90]: If OWF exist, then LR OWFs exist.

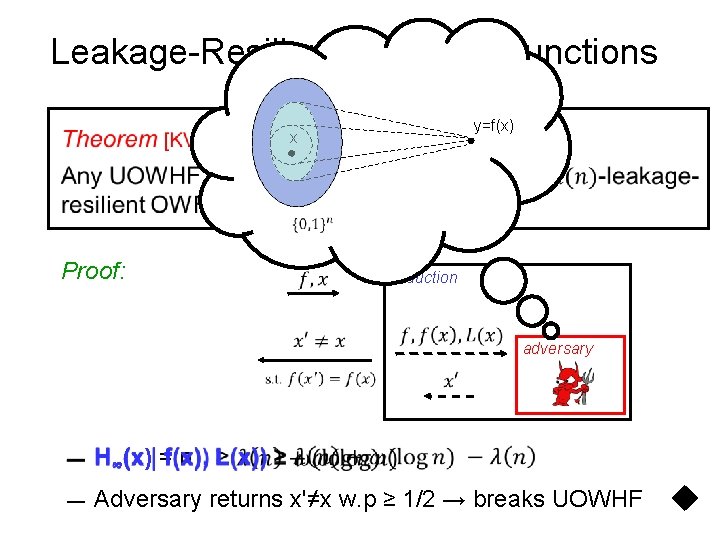
Leakage-Resilient One-way Functions Proof: q Information-theoretic + Crypto techniques q A Blue-print for most leakage-resilience proofs

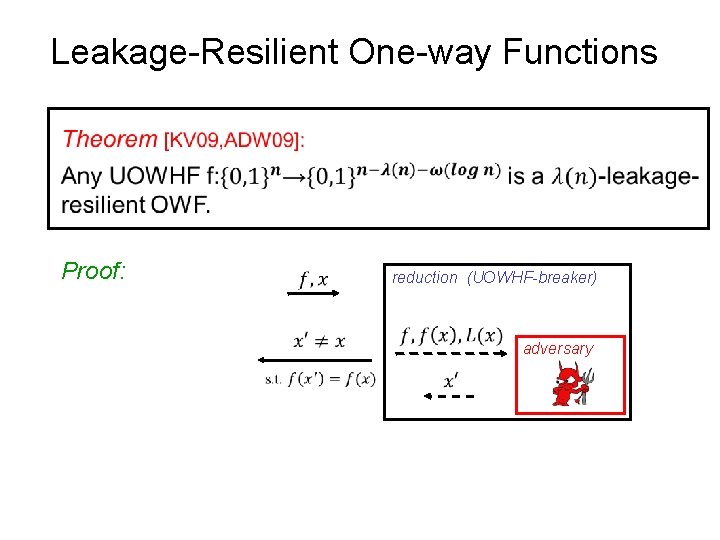
Leakage-Resilient One-way Functions Proof: reduction (UOWHF-breaker) adversary

Leakage-Resilient One-way Functions y=f(x) x Proof: reduction adversary — H∞(x) = n — Adversary returns x'≠x w. p ≥ 1/2 → breaks UOWHF

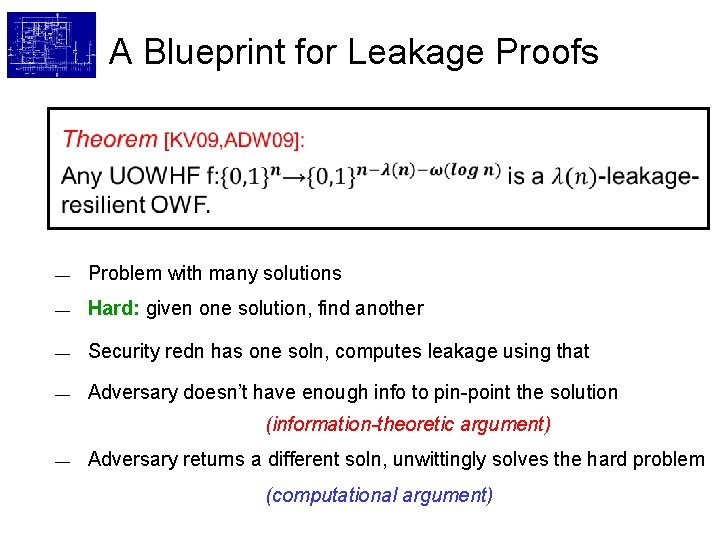
A Blueprint for Leakage Proofs — Problem with many solutions — Hard: given one solution, find another — Security redn has one soln, computes leakage using that — Adversary doesn’t have enough info to pin-point the solution (information-theoretic argument) — Adversary returns a different soln, unwittingly solves the hard problem (computational argument)

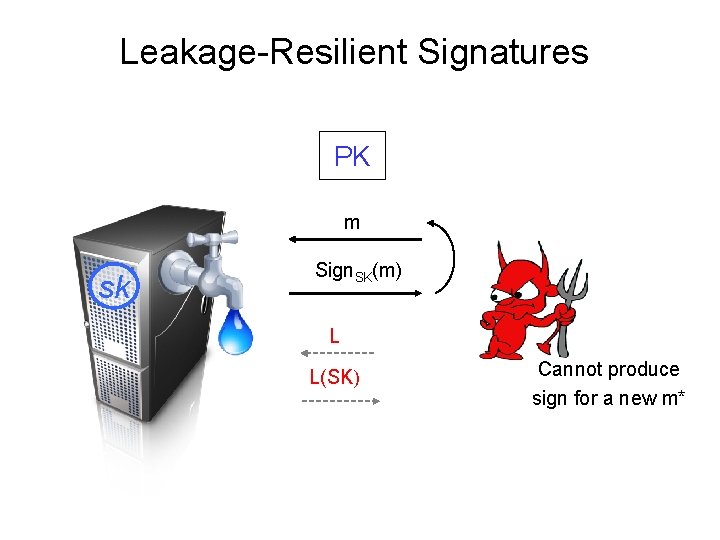
Leakage-Resilient Signatures PK m sk Sign. SK(m) L L(SK) Cannot produce sign for a new m*
![LeakageResilient Signatures Theorem KV 09 λleakageresilient OWF simulationextractable NIZK S 99 DDOPS 01 Leakage-Resilient Signatures Theorem [KV 09]: λ-leakage-resilient OWF (+simulationextractable NIZK [S 99, DDOPS 01]) →](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-23.jpg)
Leakage-Resilient Signatures Theorem [KV 09]: λ-leakage-resilient OWF (+simulationextractable NIZK [S 99, DDOPS 01]) → λ-leakage-resilient signatures similar to [Bellare-Goldwasser’ 92] PK: (f, y=f(x), CRSnizk), where f is an λ-LR OWF, SK: x Sign(m): Sim. Ext-NIZKm for “∃x s. t PK contains h(x)” Proof Idea: Sim-Ext — Signature contains no (computational) info. on SK — Forgery ⇒ extract a secret-key. — Break LR OWF.
![LR Signatures Subsequent Results q ADW 09 FiatShamir transform LR OWFs LRSigs LR Signatures: Subsequent Results q [ADW 09]: Fiat-Shamir transform + LR OWFs → LRSigs](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-24.jpg)
LR Signatures: Subsequent Results q [ADW 09]: Fiat-Shamir transform + LR OWFs → LRSigs in the random oracle model. q [DHLW 10]: Efficient LR Sigs without random oracles (using bilinear maps). q [BKKV 10, DHLW 10]: Continual LR Sigs q [LLW 10]: Continual LR Sigs where the key update phase leaks as well q [BSW 11, MTVY 11]: (continual) LR Sigs where the randomness used for signing can leak as well.

Leakage-Resilient Public-key Encryption(cpa) PK sk L L(SK) Enc(b) (b←${0, 1}) Cannot predict b

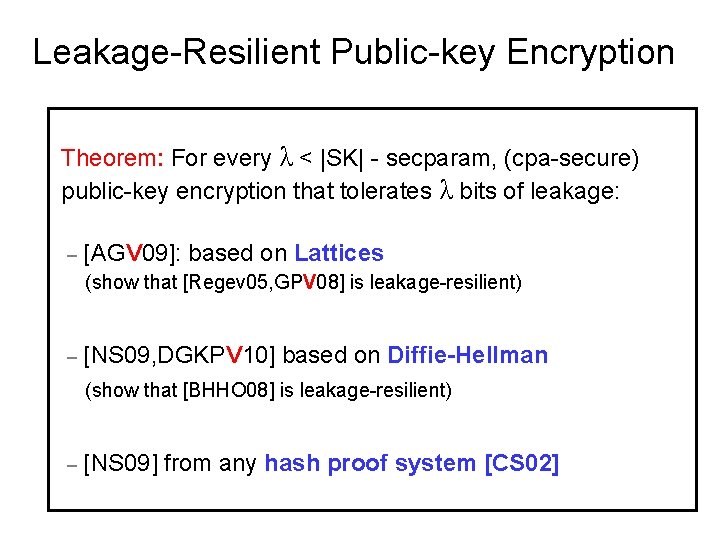
Leakage-Resilient Public-key Encryption Theorem: For every λ < |SK| - secparam, (cpa-secure) public-key encryption that tolerates λ bits of leakage: – [AGV 09]: based on Lattices (show that [Regev 05, GPV 08] is leakage-resilient) – [NS 09, DGKPV 10] based on Diffie-Hellman (show that [BHHO 08] is leakage-resilient) – [NS 09] from any hash proof system [CS 02]

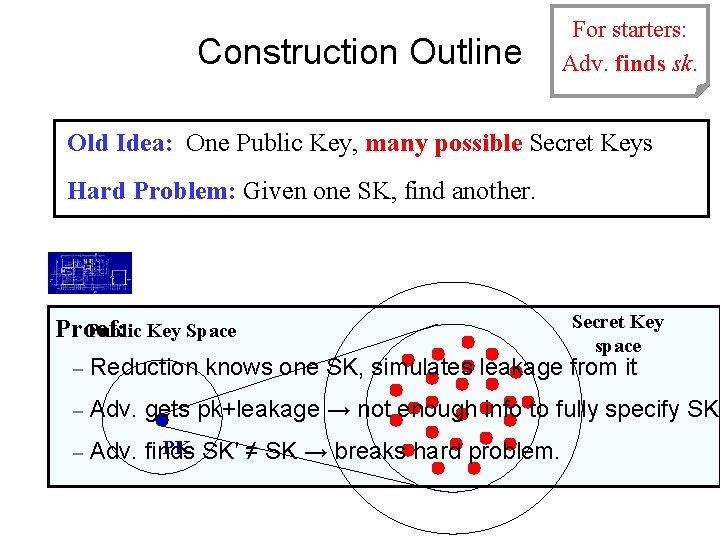
Construction Outline Adv. breaks For starters: Adv. finds sk. cpa-security Old Idea: One Public Key, many possible Secret Keys Hard Problem: Given one SK, find another. Proof: Public Key Space Secret Key space – Reduction knows one SK, simulates leakage from it – Adv. gets pk+leakage → not enough info to fully specify SK – PK SK′ ≠ SK → breaks hard problem. Adv. finds

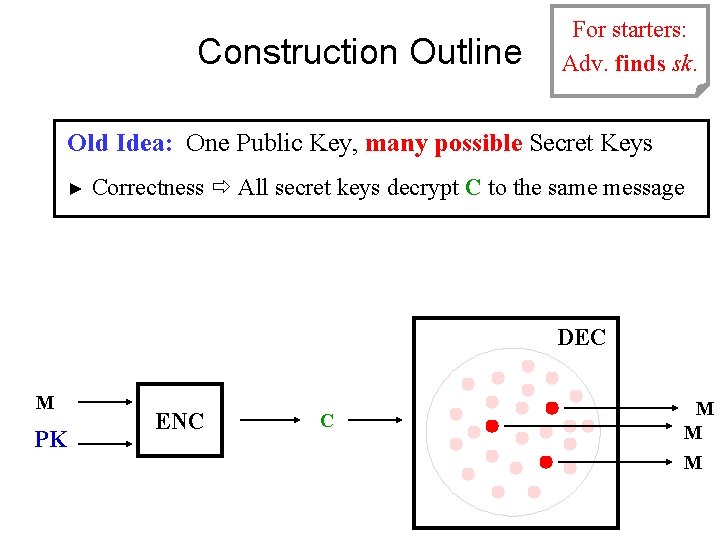
Construction Outline Adv. breaks For starters: Adv. finds sk. cpa-security Old Idea: One Public Key, many possible Secret Keys ► Correctness All secret keys decrypt C to the same message DEC M PK ENC C M M M

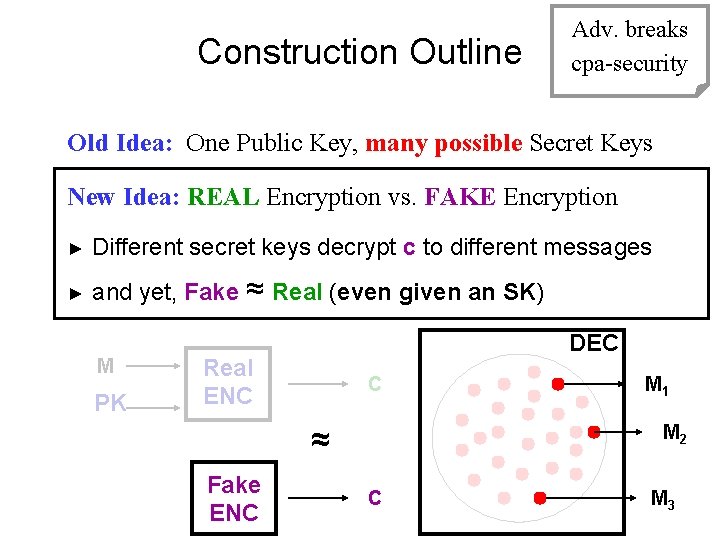
Construction Outline Adv. breaks cpa-security Old Idea: One Public Key, many possible Secret Keys New Idea: REAL Encryption vs. FAKE Encryption ► Different secret keys decrypt c to different messages ► and yet, Fake ≈ Real (even given an SK) M PK DEC Real ENC C ≈ Fake ENC M 1 M 2 C M 3

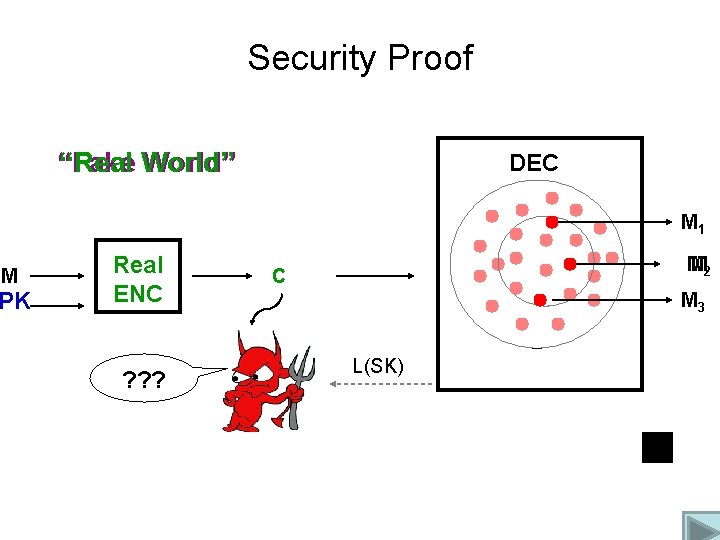
Security Proof “Fake “Real World” DEC M 1 M PK Fake Real ENC ? ? ? M M 2 C M 3 L(SK)
![LR Publickey Encryption Subsequent Results q NS 09 CPAsecure CCAsecure with the same LR Public-key Encryption: Subsequent Results q [NS 09]: CPA-secure → CCA-secure with the same](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-31.jpg)
LR Public-key Encryption: Subsequent Results q [NS 09]: CPA-secure → CCA-secure with the same leakage-resilience (idea: use Naor-Yung) q [AGV 09, ADN+10, CDRW 10]: leakage-resilient IBE (with leakage from the user secret keys). q [LW 10]: leakage-resilient IBE (with leakage from the master secret key as well), LR HIBE, ABE etc. q [BKKV 10, DHLW 10]: Continual LR Encryption q [LLW 10]: Continual LR Enc where the key update phase leaks as well q [HL 11]: “After-the-fact” Leakage

Continual Leakage

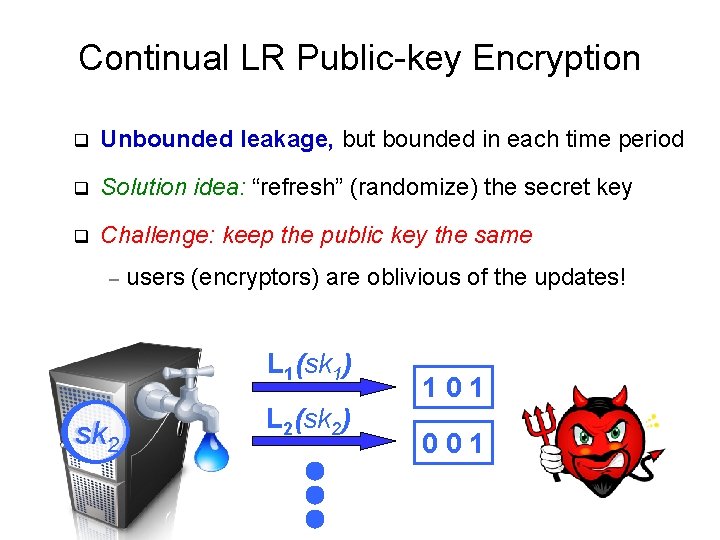
Continual LR Public-key Encryption q Unbounded leakage, but bounded in each time period q Solution idea: “refresh” (randomize) the secret key q Challenge: keep the public key the same – users (encryptors) are oblivious of the updates! L 1(sk 1) sk 12 L 2(sk 2) 101 001
![Continual LR Publickey Encryption Theorem BKKV 10 CLRsecure publickey encryption schemes that tolerate in Continual LR Public-key Encryption Theorem: [BKKV 10] CLR-secure public-key encryption schemes that tolerate (in](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-34.jpg)
Continual LR Public-key Encryption Theorem: [BKKV 10] CLR-secure public-key encryption schemes that tolerate (in every time step): (1/2 -ε)|SK| leakage, based on decisional linear – (1 -ε)|SK| leakage, based on symmetric external DH – assumptions in bilinear groups. L 1(sk 1) sk 12 L 2(sk 2) 101 001
![Continual LR Publickey Encryption Other Results q BKKV 10 CLRsecure signatures and IBE with Continual LR Public-key Encryption Other Results: q [BKKV 10]: CLR-secure signatures and IBE (with](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-35.jpg)
Continual LR Public-key Encryption Other Results: q [BKKV 10]: CLR-secure signatures and IBE (with leakage from user secret keys) q Concurrently, [DHLW 10]: efficient CLR-secure signatures, ID schemes and AKA schemes q [LLW 11]: tolerates large leakage from updates L 1(sk 1) sk 12 L 2(sk 2) 101 001

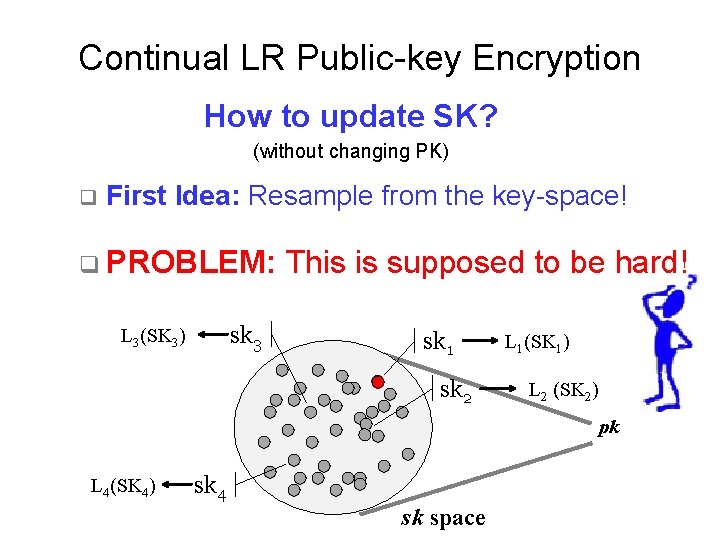
Continual LR Public-key Encryption How to update SK? (without changing PK) q First Idea: Resample from the key-space! q PROBLEM: sk 3 L 3(SK 3) This is supposed to be hard! sk 1 sk 2 L 1(SK 1) L 2 (SK 2) pk L 4(SK 4) sk 4 sk space

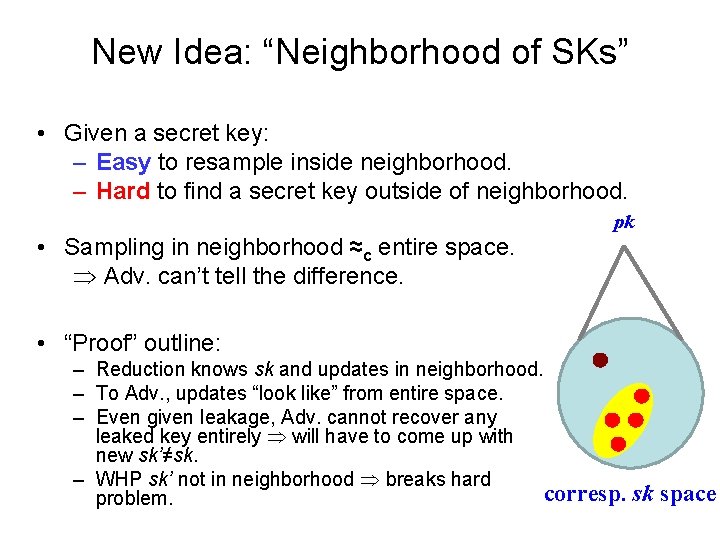
New Idea: “Neighborhood of SKs” • Given a secret key: – Easy to resample inside neighborhood. – Hard to find a secret key outside of neighborhood. pk • Sampling in neighborhood ≈c entire space. Adv. can’t tell the difference. • “Proof” outline: – Reduction knows sk and updates in neighborhood. – To Adv. , updates “look like” from entire space. – Even given leakage, Adv. cannot recover any leaked key entirely will have to come up with new sk’≠sk. – WHP sk’ not in neighborhood breaks hard corresp. sk space problem.

Some Open Questions

Foundational Questions SO FAR: Designed SPECIFIC crypto primitives (sigs. , enc. ) secure against continual leakage QUESTION: Any circuit → Continual Leakage-resilient circuit — Yao/GMW/BGW/CCD for leakage-resilient crypto — Automatically leakage-proof commonly used cryptosystems, e. g. , RSA / AES
![Foundational Questions Many Partial Results q IshaiSahaiWagner 03 Any circuit Probingresilient circuit Foundational Questions Many Partial Results q [Ishai-Sahai-Wagner’ 03] : Any circuit → “Probing-resilient” circuit](https://slidetodoc.com/presentation_image_h/72ff156ecdb32a3ab393f98e5090c6e9/image-40.jpg)
Foundational Questions Many Partial Results q [Ishai-Sahai-Wagner’ 03] : Any circuit → “Probing-resilient” circuit secure against leakage of ≤ t wires q q OPEN: [FRRTV’ 09] : Any circuit → circuit secure against AC 0 compiler against general leakagea(assuming a small piece of secure hardware) leakage functions [JV’ 10, GR’ 10] : Any circuit → circuit secure against (without secure hardware) polynomial-time leakage (assuming a small piece of secure hardware + secure memory) q [BGIRSVY’ 00, Imp’ 10] : This has connections to program obfuscation!

Practical Questions q In theory, we have practical constructions – How about truly practical constructions? (e. g. [YSPY’ 10]) – Perhaps relax the model in a meaningful way model q reality Given a side-channel attack, how much information does it leak? [SVO+10]

To Conclude… q Tons of Open Problems — Parallel Repetition for Leakage Amplification [DW, LW]: Suppose scheme S tolerates L bits. Can we “repeat it in parallel” n times and get n. L bit leakage-tolerance? — Tamper Resistance [IPSW, GLMMR, DPW, Malkin et al. ]: Many attacks, Boneh-Lipton, Shamir’s bug attacks. . . py Entro Very Active Field, Lots of work recently! Information-theoretic + Computational Techniques

Thanks! Questions? You can find me here …