ISACA May 2006 When Things Go Wrong The


























- Slides: 32

ISACA May 2006 When Things Go Wrong The Results of Losing your Common Sense By: Barak Engel, CISSP Principal, Engel & Associates

What will we talk about? ¨ The theory – Approaches – The role of the individual user – The gap ¨ The practice – Common and pervasive risk areas • Email (Viruses, Phishing and other diseases) • Web Browsing (“the free mug”) • Wireless connectivity (War Driving) ¨ Filling the gap

In Theory… ¨ Security controls… – Can be standardized – Can be applied uniformly – Can be identified and defined in advance – Can have their efficacy analyzed/determined – Can be audited ¨ Hidden assumptions – Level of accuracy – The issue of scale – Statistical equality of cost

The individual user ¨ Users… – Represent the largest install base – Completely lack standards – Cannot be controlled centrally (or otherwise) – Are only predictable in their unpredictability – Cannot be redesigned – Are all of us ¨ In the knowledge society, employees own the tools AND the means of production – Peter Drucker, 1994

The gap ¨ Knowledge – The awareness problem • Would this be useful to you? – The issue of relevancy – Cross-contamination ¨ Motivation – The role of open-source and freeware ¨ Least Effort and the path of least resistance

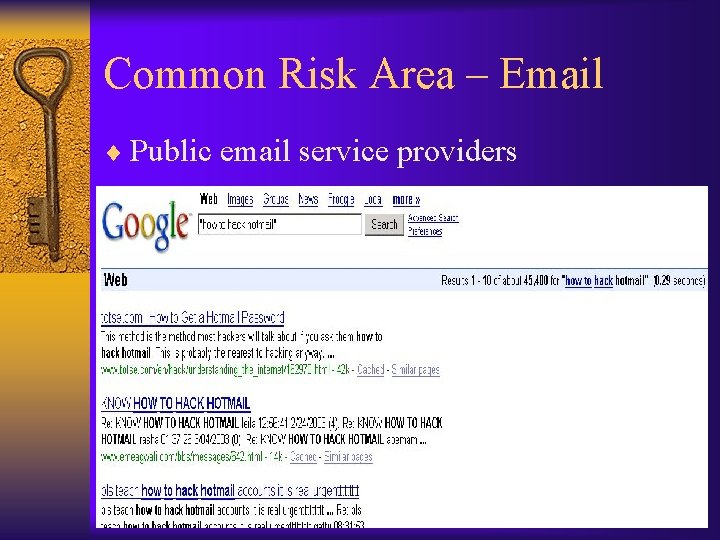
Common Risk Area – Email ¨ Public email service providers

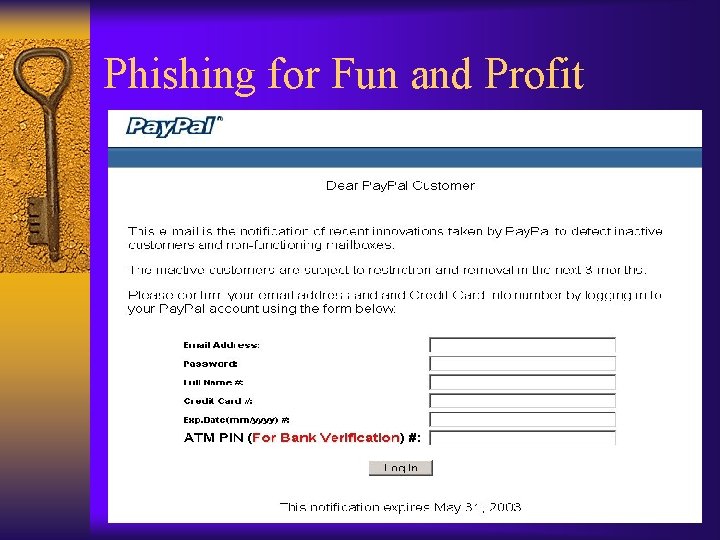
Phishing for Fun and Profit

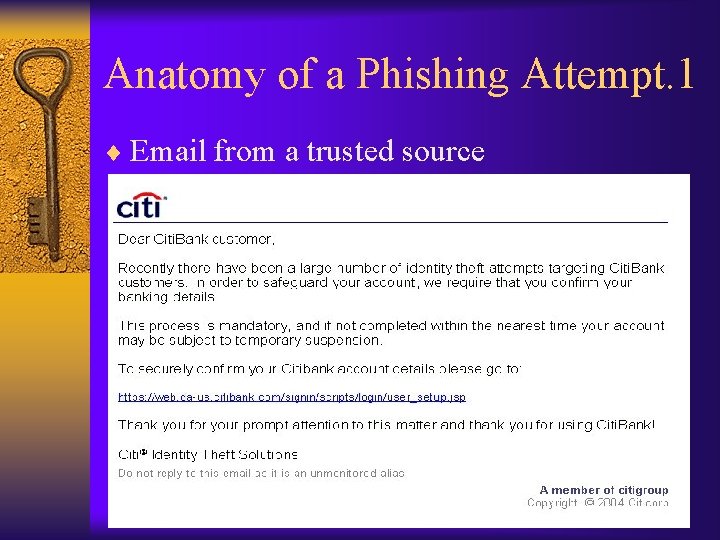
Anatomy of a Phishing Attempt. 1 ¨ Email from a trusted source

Anatomy of a Phishing Attempt. 2 ¨ “Clean” headers – and no virus

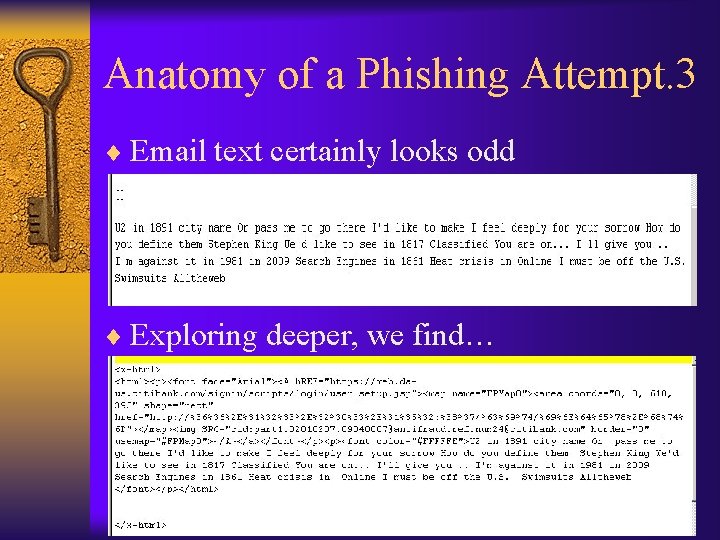
Anatomy of a Phishing Attempt. 3 ¨ Email text certainly looks odd ¨ Exploring deeper, we find…

Anatomy of a Phishing Attempt. 4 ¨ Analyzing the ASCII code: – Source: http: //%36%36%2 E%31%32%33%2 E%32%30 %33%2 E%31%35%32: %38%37/%63%69%74 /%69%6 E%64%65%78%2 E%68%74%6 D – Target: 66. 123. 203. 152: 87/cit/index. htm

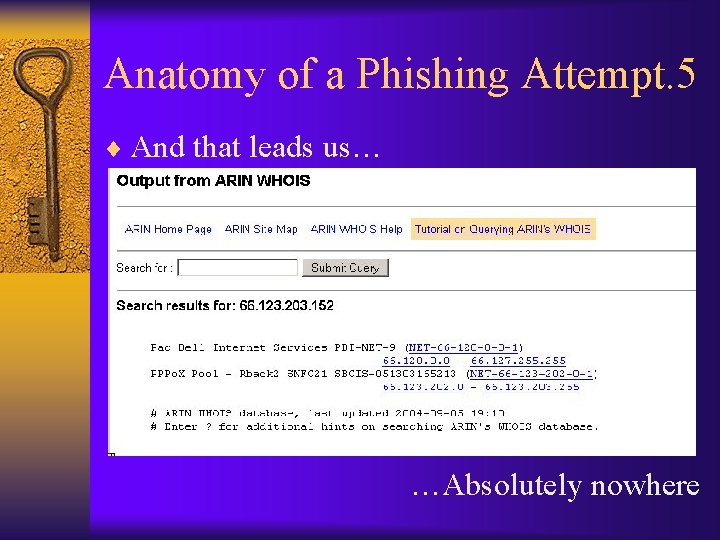
Anatomy of a Phishing Attempt. 5 ¨ And that leads us… …Absolutely nowhere

Could the average user have figured this out? ¨Heard warnings ¨Has logo and a “legit” ¨Wording is slightly email address ¨Proper english awkward ¨Underlying text is weird ¨Maybe needed? And it comes from IT anyway ¨Virus-free (crosscontamination) ¨ Common sense must be “calibrated”!

Email – right or privilege? ¨ Corporate email can be controlled… – …but not so private email ¨ Controls – Updated anti virus (FW: AVG) – Encryption (FW: PGP) – Secure email client (FW: Thunderbird) – Spam blocker (FW: Spambayes) ¨ Motivation – Identity Theft

A cryptic code? 042103580, 062360749, 095073645, 128036045, 135016629, 141186941, 165167999, 165187999, 165207999, 165227999, 165247999, 189092294, 212097694, 212099999, 306302348, 308125070, 468288779, 549241889

Web Browsing ¨ To whom are you giving your personally identifiable information and why?



The Tradeshow Participant. 1

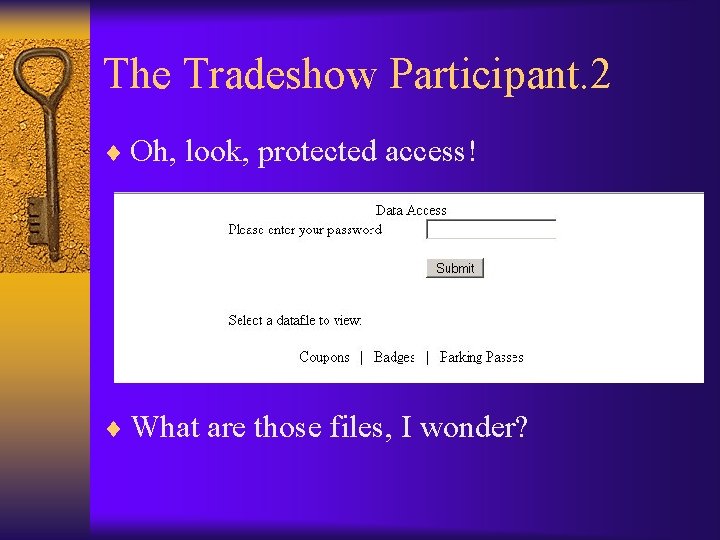
The Tradeshow Participant. 2 ¨ Oh, look, protected access! ¨ What are those files, I wonder?

The Tradeshow Participant. 3

The Tradeshow Participant. 4 ¨ Hey! They paid less than we did!

The Tradeshow Participant. 5 ¨ Some information can be more useful… …to certain people.

Information can end up anywhere

Web Browsing – Tool of Production ¨ Browsing habits are learned at home – not at work ¨ Web-based research is efficient and highly valuable ¨ Monitoring web access provides rapidly diminishing return

Good Habits in Browsing ¨ Some better habits are easy to acquire: – “Understanding” SSL – Different browser (FW: Firefox) – Limiting (personal) exposure – The concept of lying – Fighting spyware (FW: Spybot S&D, Spyware Blaster/Guard, Windows Defender) – Password Management (Keypass) ¨ Motivation – Identity Theft – Online Predators

Mrs. Hilda Schrader Whitcher ¨ 078051120 ¨ Actual SSN of E. H. Ferree’s Treasurer Douglas Patterson’s secretary ¨ An insert in wallets sold at Woolworth ¨ Used by over 40, 000 people

Wireless Connectivity ¨ A new attack vector ¨ “Invisible” infrastructure ¨ KISS – But only in basic mode ¨ Highly distributed

Is the network a free-for-all? ¨ The story of an afternoon visit to 7 -11

Wireless Behavior ¨ Explain basic concepts – defaults • Network name (SSID) • Channel • Beaconing – Encryption – MAC filtering ¨ Motivation – Personal information (…Identity Theft) – Job Security

Users = The X-Factor* ¨ Common sense can be taught ¨ It’s all about motivation – Close and personal ¨ Hidden assumption – People generally have good intentions ¨ We are all users! ¨ * (and that’s not a bad thing)

Thank You! http: //www. engelassociates. net/ barak@engelassociates. net (888) 509 3561